| File name: | faktura577.xls |
| Full analysis: | https://app.any.run/tasks/2c2816fd-021b-4298-8dd2-de50023e642e |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 12:25:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: openpyxl, Last Saved By: MalfindLabs, Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Jul 18 15:55:39 2022, Last Saved Time/Date: Mon Jul 18 15:58:22 2022, Security: 0 |
| MD5: | 4B0719D1907F7C4B5E599F2B5696329A |
| SHA1: | CA58CB833331AF0F6E5783460B589FF60B0D7685 |
| SHA256: | A77E9B7E7130BF95EAD698825DC9500C11F08B156F4D1AA552DA920CEAAEFC6B |
| SSDEEP: | 6144:aMHCpAjCaLf+5FTXb0VaHNJ8qi+SOkSEl8kaWOrPZ1ogL4I:aMHCgbLcJZb8qitR8rWOrPZ5 |
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 3752)
Calls Win API functions (MACROS)
- EXCEL.EXE (PID: 3752)
SUSPICIOUS
The process executes via Task Scheduler
- updater.exe (PID: 5628)
Application launched itself
- updater.exe (PID: 5628)
INFO
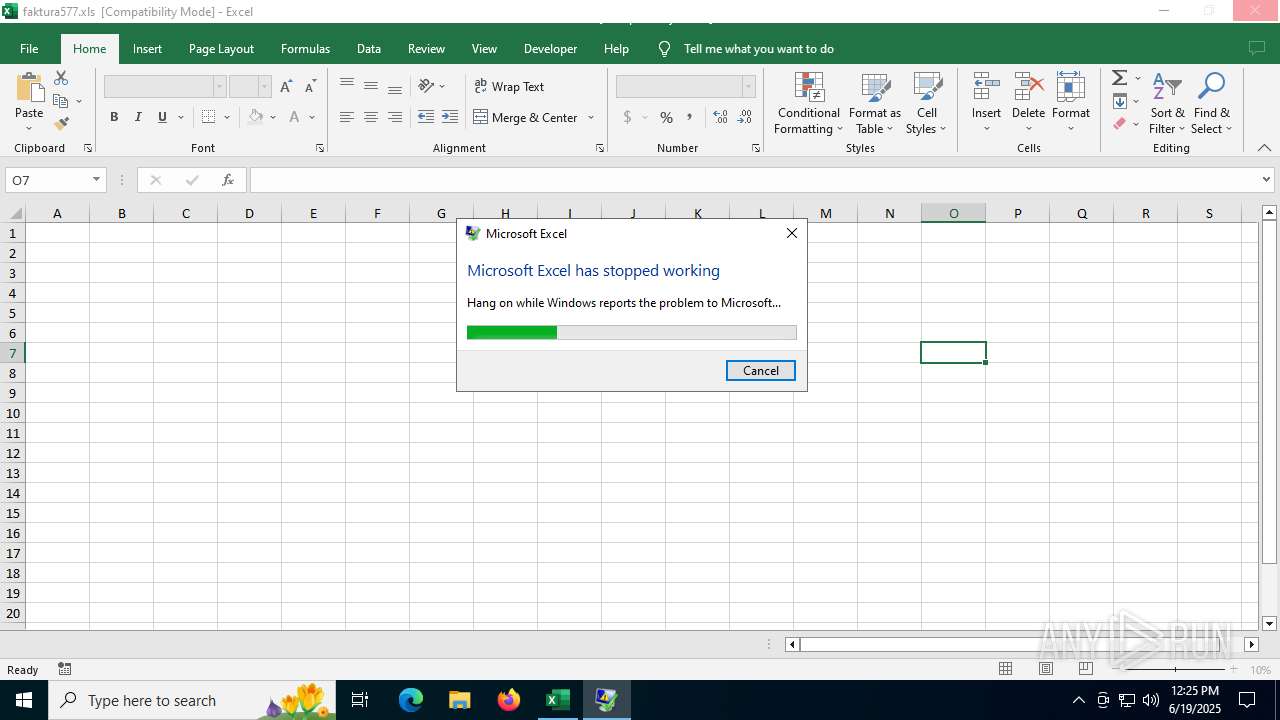
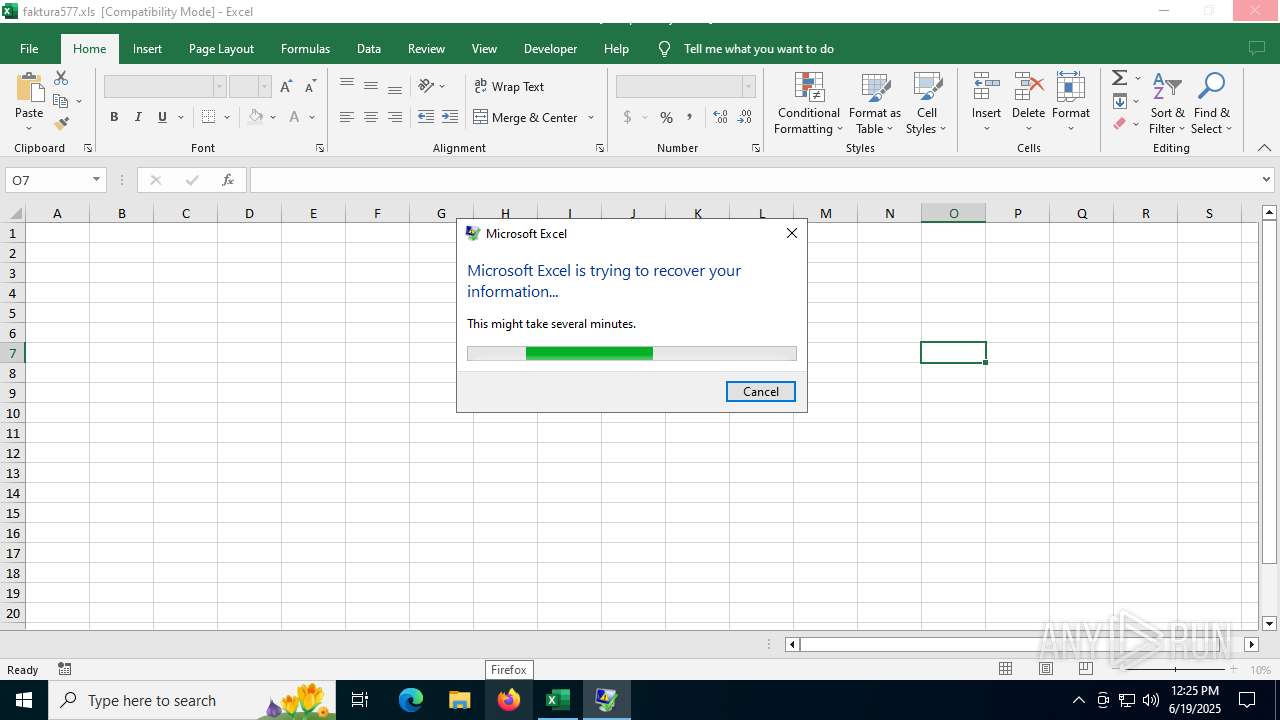
Creates files in the program directory
- DWWIN.EXE (PID: 6636)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 6636)
Reads Microsoft Office registry keys
- DWWIN.EXE (PID: 6636)
Checks proxy server information
- DWWIN.EXE (PID: 6636)
Reads the software policy settings
- DWWIN.EXE (PID: 6636)
Checks supported languages
- updater.exe (PID: 5628)
- updater.exe (PID: 6776)
Reads the computer name
- updater.exe (PID: 5628)
Process checks whether UAC notifications are on
- updater.exe (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | openpyxl |
|---|---|
| LastModifiedBy: | MalfindLabs |
| Software: | Microsoft Excel |
| CreateDate: | 2022:07:18 15:55:39 |
| ModifyDate: | 2022:07:18 15:58:22 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
145
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3752 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\AppData\Local\Temp\faktura577.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5628 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 6492 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6636 | C:\WINDOWS\system32\dwwin.exe -x -s 4608 | C:\Windows\System32\DWWIN.EXE | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6776 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
Total events
8 768
Read events
8 536
Write events
217
Delete events
15
Modification events
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 7z2 |
Value: 377A3200A80E000001000000000000003BA1AC4415E1DB0100000000 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ImmersiveWorkbookDirtySentinel |
Value: 0 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ExcelPreviousSessionId |
Value: {A5607F09-F473-4EF9-B80D-98AD68EC97D2} | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | FilePath |
Value: officeclient.microsoft.com\3E8EB904-C946-4E9D-A475-59EA8830A7E0 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | StartDate |
Value: 102EEF4415E1DB01 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | EndDate |
Value: 10EE586FDEE1DB01 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\3752 |
| Operation: | write | Name: | 0 |
Value: 0B0E10097F60A573F4F94EB80D98AD68EC97D2230046DDE995A5D4A2F8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A81DD2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3752) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
Executable files
0
Suspicious files
6
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_EXCEL.EXE_1d36ef4729d5ee8385674ece8dff4b8acaf9b67d_00000000_e5217641-5d4f-4895-8f79-0600d5f165b8\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6636 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:F6550EBE0909EF0A03E10012E874F1A8 | SHA256:B654BA806D78DC2B49115BE1B007CE2B5BC9BD86780B542667B90F5DF6D7EEEA | |||
| 3752 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:5F5BC6CCBCFF9A3D5B18A37A44D812FD | SHA256:EC07A3AFFE2E6D91853C724080AFA5C1DF7120653F70B0B17124663B31861723 | |||
| 6636 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WER81E2.tmp.WERInternalMetadata.xml | xml | |
MD5:AB9C640DD678F29C19C7207292EB60BF | SHA256:D062F650EF2C72C9A2CE78B8C5E3CEC6D097ED69452E7402EC8F694D4AC1525F | |||
| 3752 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\3E8EB904-C946-4E9D-A475-59EA8830A7E0 | xml | |
MD5:032F6ABF4D65E7E719B0E3A469708ABF | SHA256:74EB36423D0C22C3697CBACFC79B30175E37F089B12A4EEB9558DCDD6CE98FFC | |||
| 3752 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Excel\~ar6F78.xar | document | |
MD5:B0E4195BBA0E2AE7EC6CBC45A7D39714 | SHA256:69B2C3FD985C7ECA658ABC1F4AB03D899574602A71A209CE9E8A21B901ADDCCF | |||
| 6776 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\updater.log | text | |
MD5:E16DA8A3A452644A63D25DD0164609EF | SHA256:FDC7C04DCB5B6A37C9651707A784199533FB289DFA28DA393EE3C020471309CF | |||
| 3752 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\faktura577.xls | document | |
MD5:60EC8856FF482895A0DD4150C9A817BD | SHA256:62467C7943085707A634AD869618A12F4E0666DF25C2917C014C66F797CFC8D2 | |||
| 3752 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFF6183CEBC40F24A1.TMP | gmc | |
MD5:97F171955C5B264B547DE3FF5EC91877 | SHA256:BBE1256C0BD5A24A5A59A057884565987584AE2EAF659689FF994D7877E280DE | |||
| 6636 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:3BCDE3BCA04C8061FAD8EE9D5D69871D | SHA256:F3F8322643C031F7D4253783236666419D9D3275FA28BB6815ABE747777B1E16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6636 | DWWIN.EXE | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5124 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5124 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6636 | DWWIN.EXE | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2792 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3752 | EXCEL.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3752 | EXCEL.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3944 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |