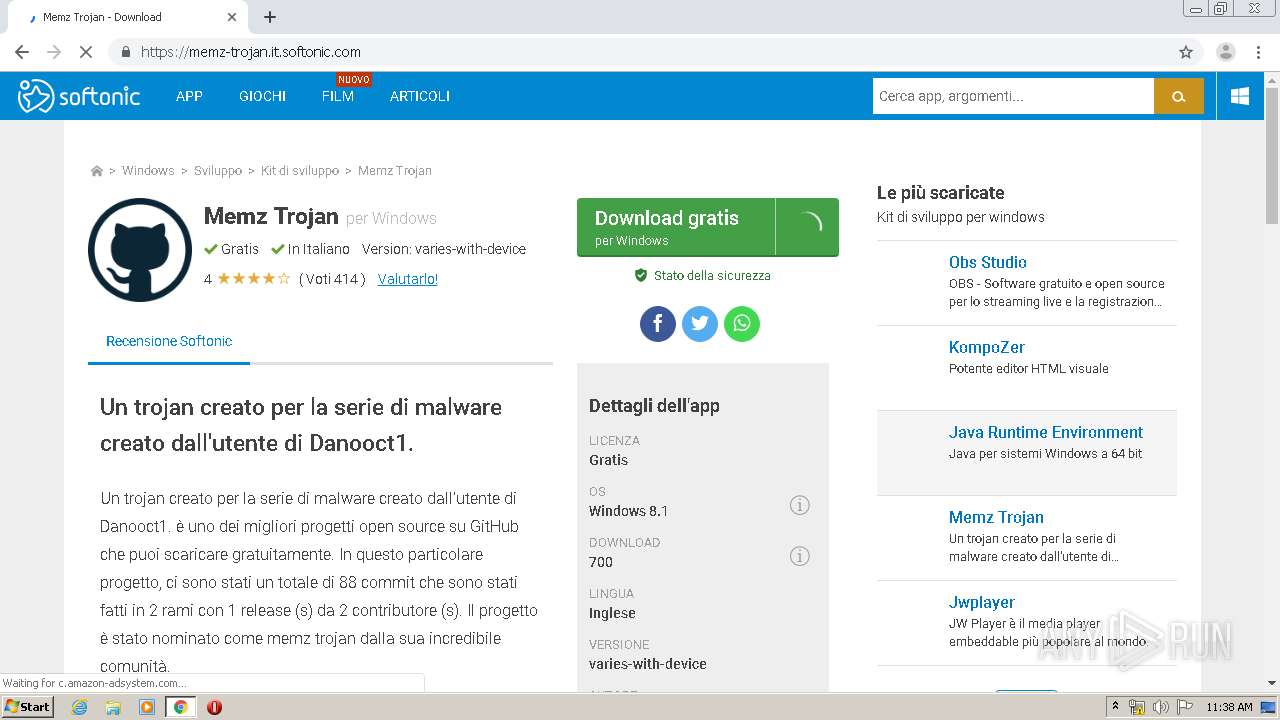
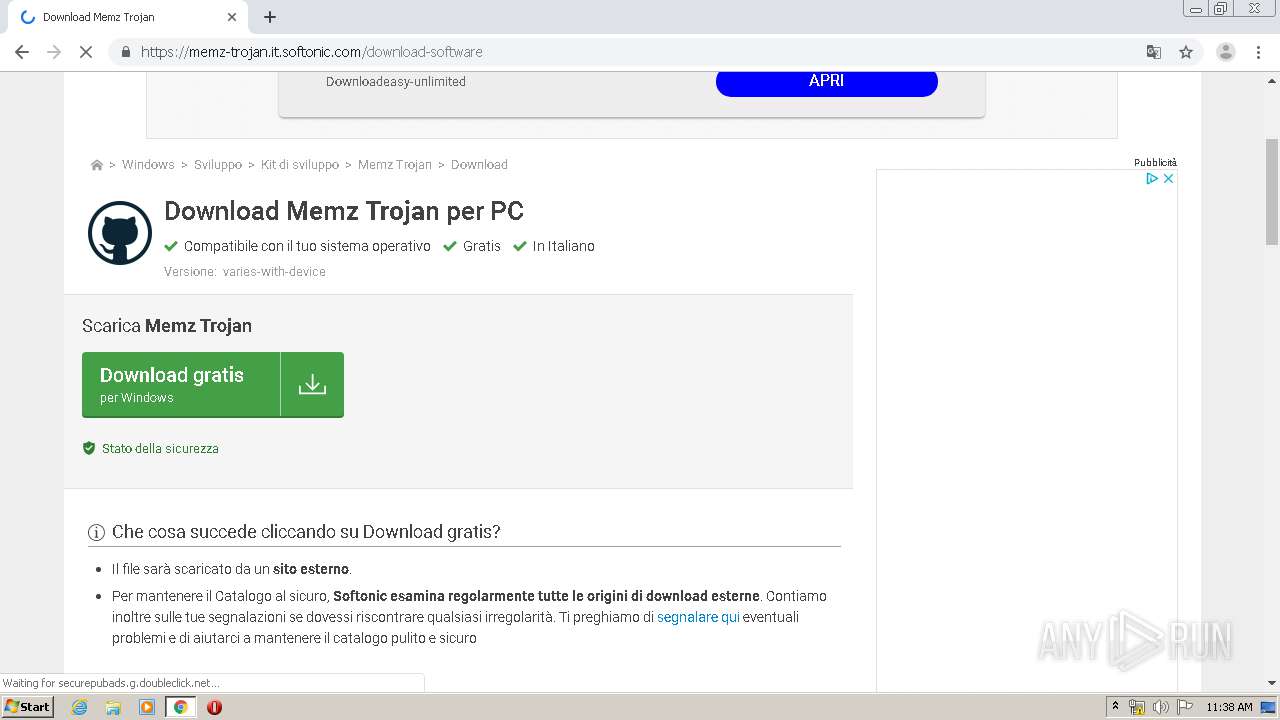
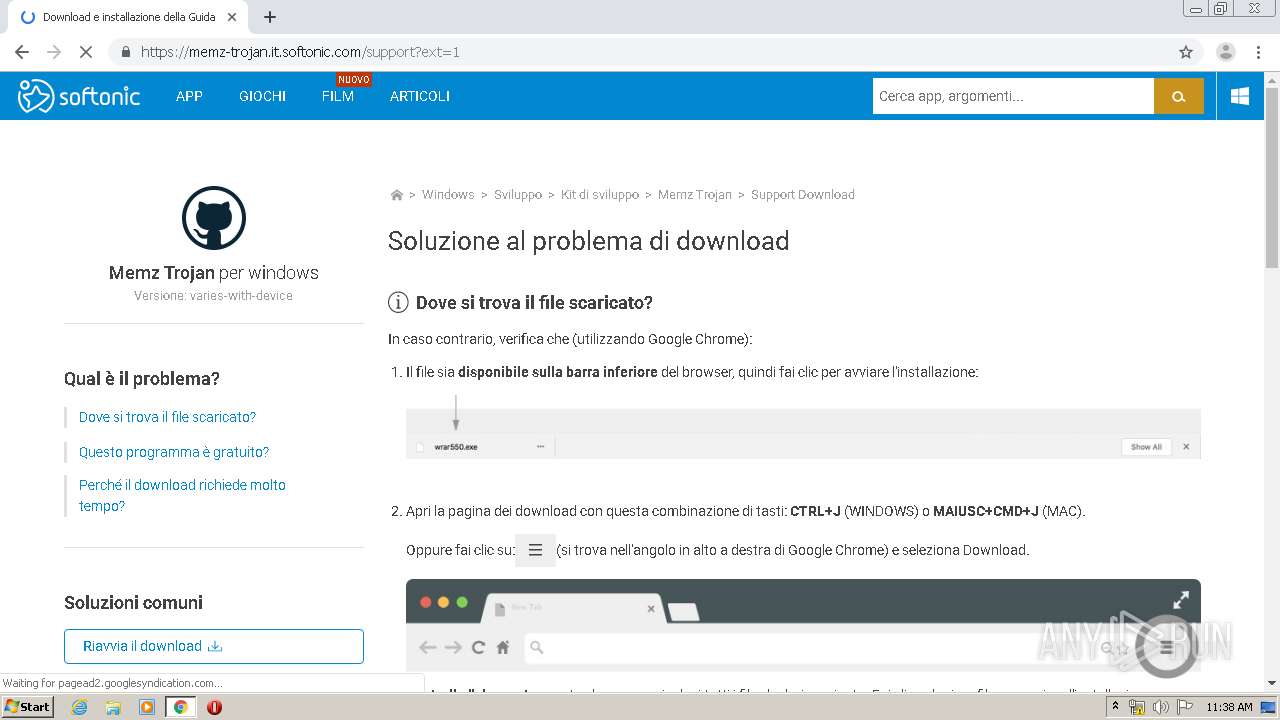
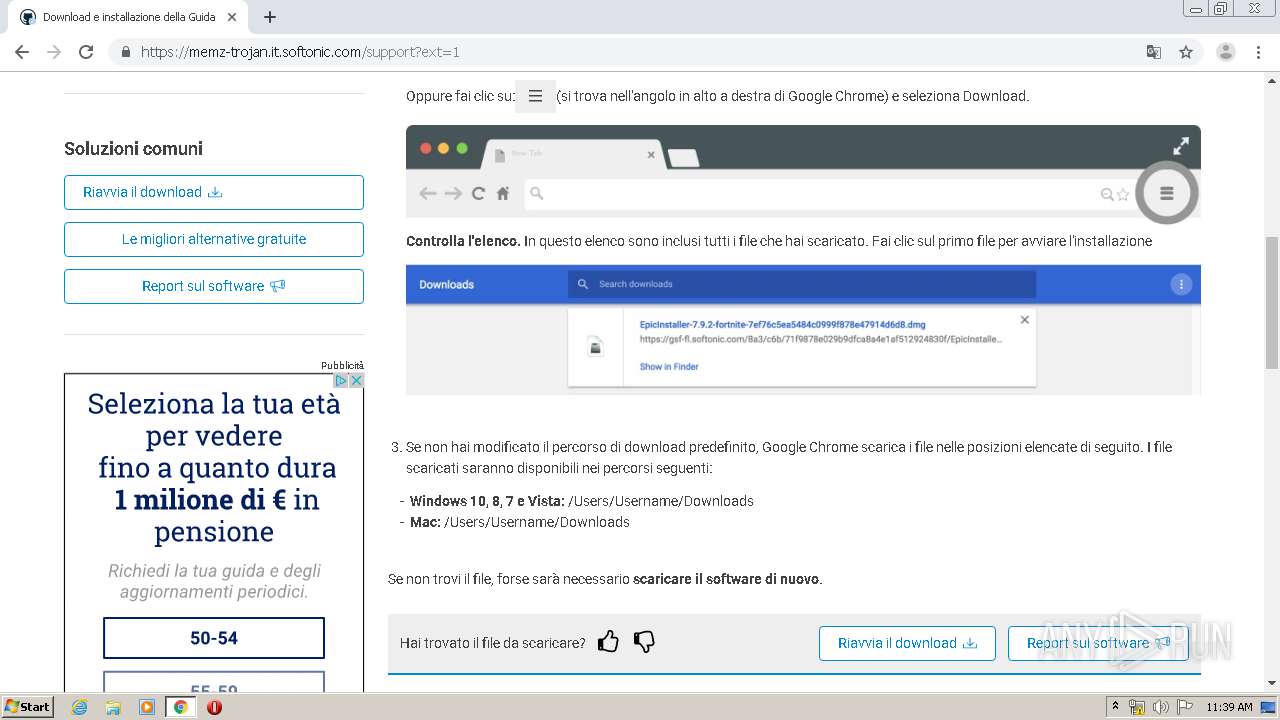
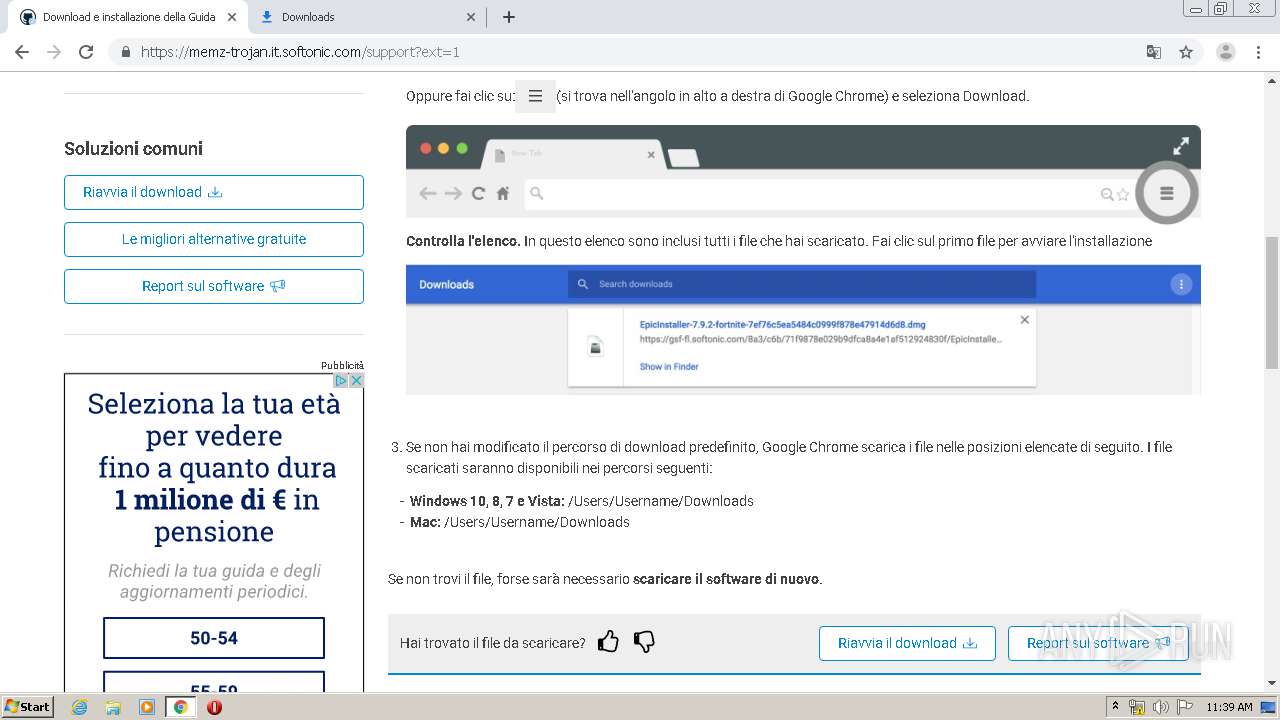
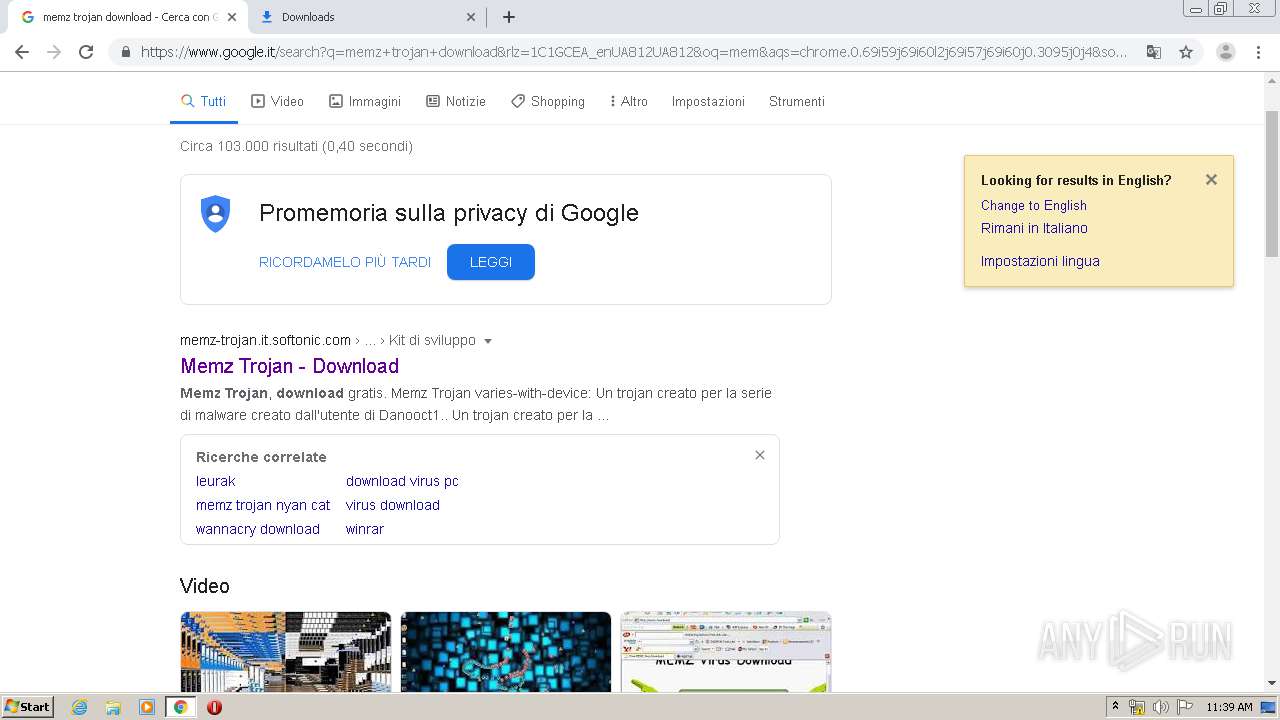
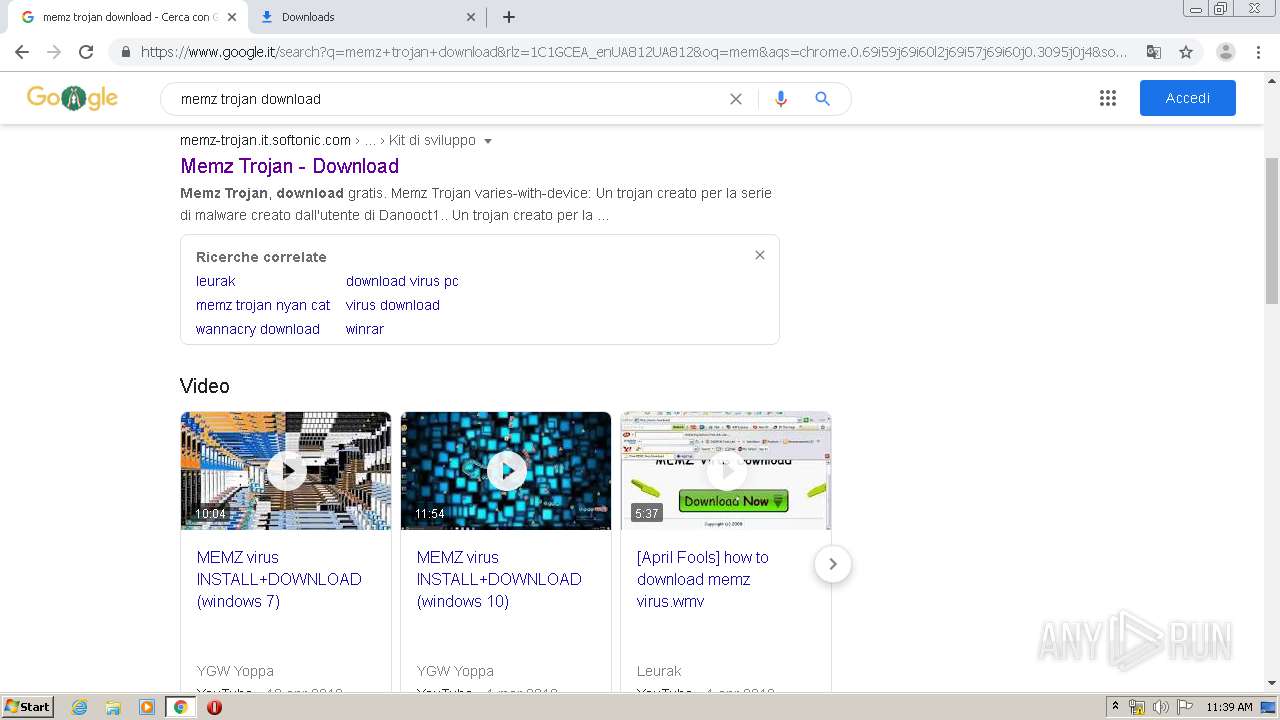
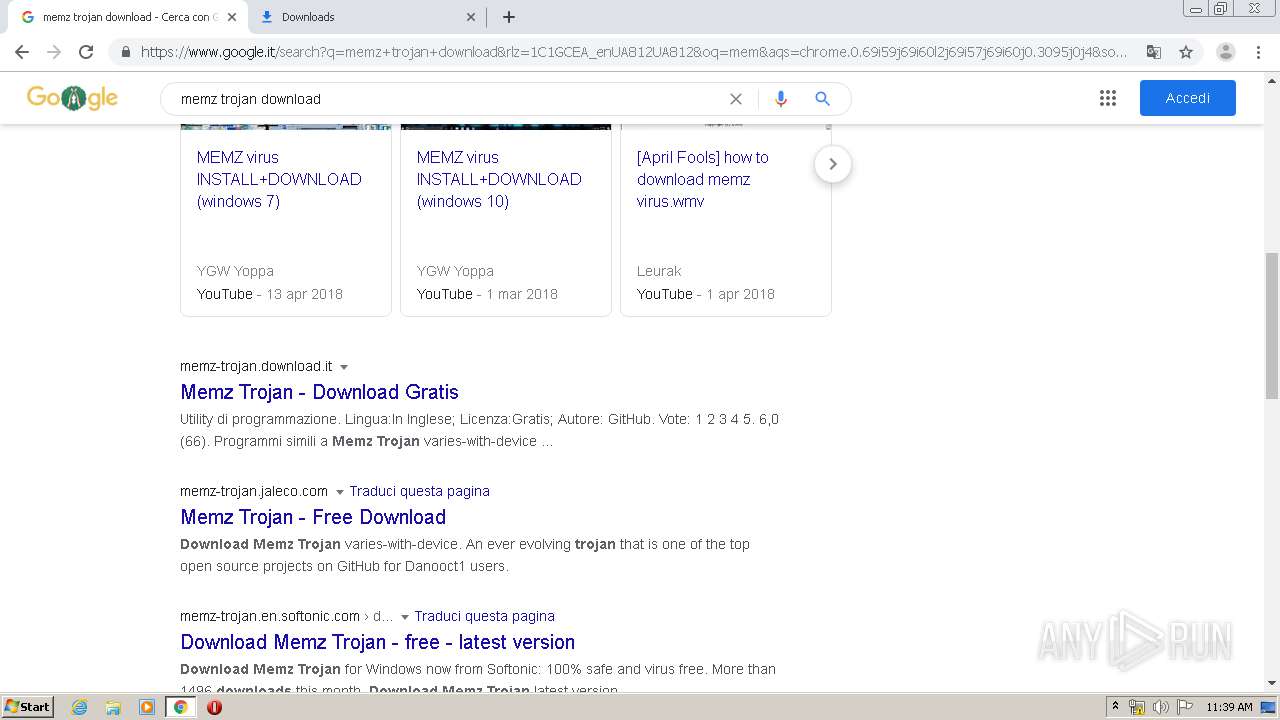
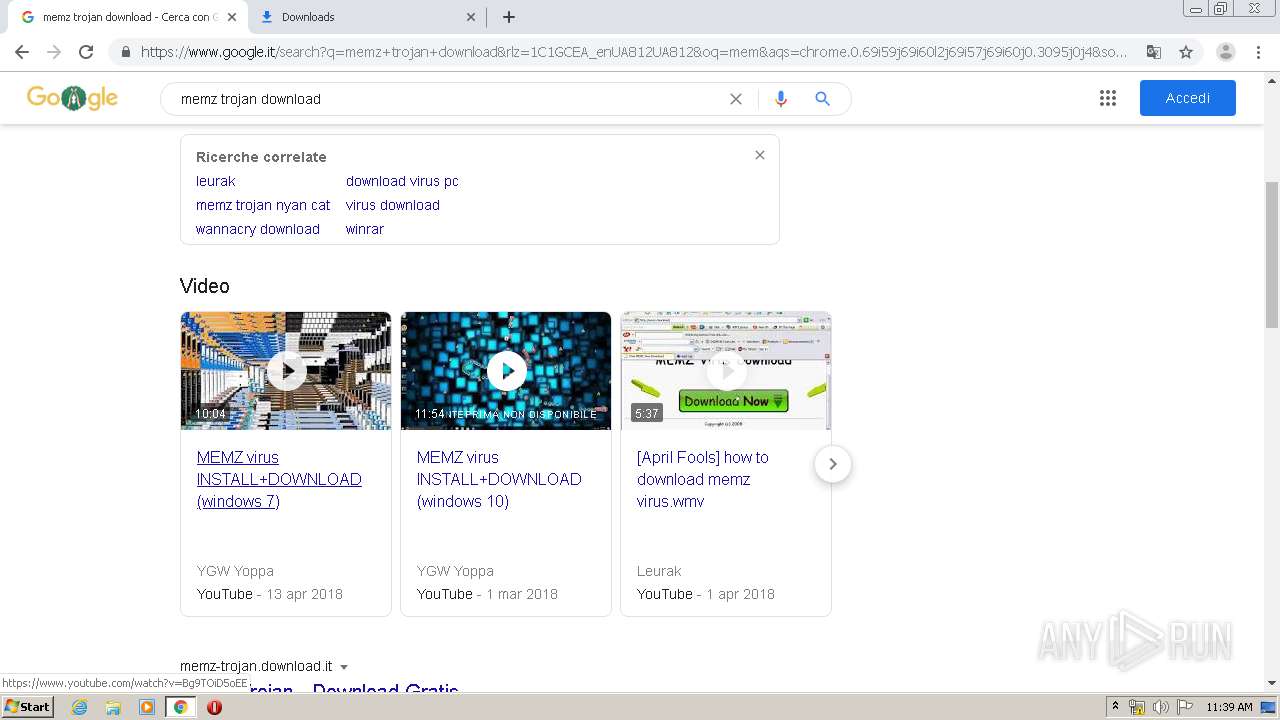
| URL: | https://memz-trojan.en.softonic.com/ |
| Full analysis: | https://app.any.run/tasks/94893a6f-214d-45fe-a8d6-c90f2f6cb361 |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2020, 10:35:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A05A75CBA0F744395ACCFA2E333C42E3 |
| SHA1: | C868C3BC51AD1D4870AF4F99ADD094AE5510A678 |
| SHA256: | A75FDA23DD7CE9A0B99CFB71FFF50FA03286337324BD9C600DDF2AD271AF147C |
| SSDEEP: | 3:N8VtIIHLGK3:2VqALGK3 |
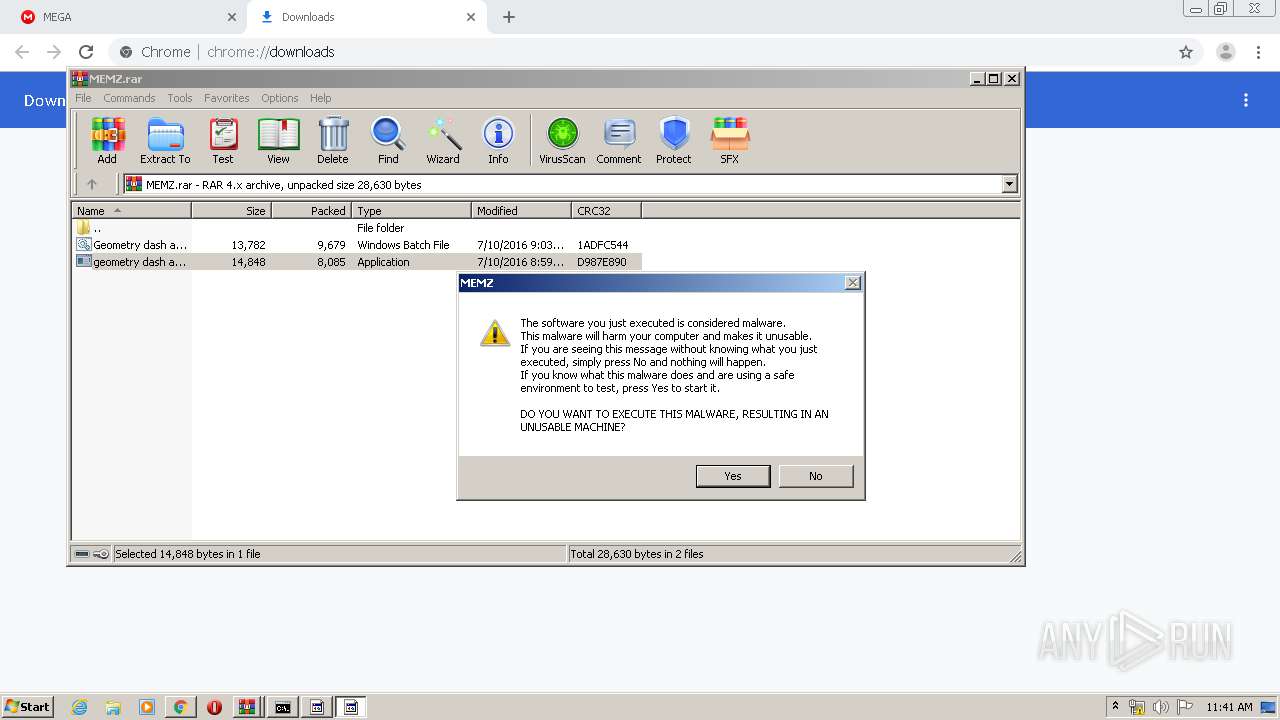
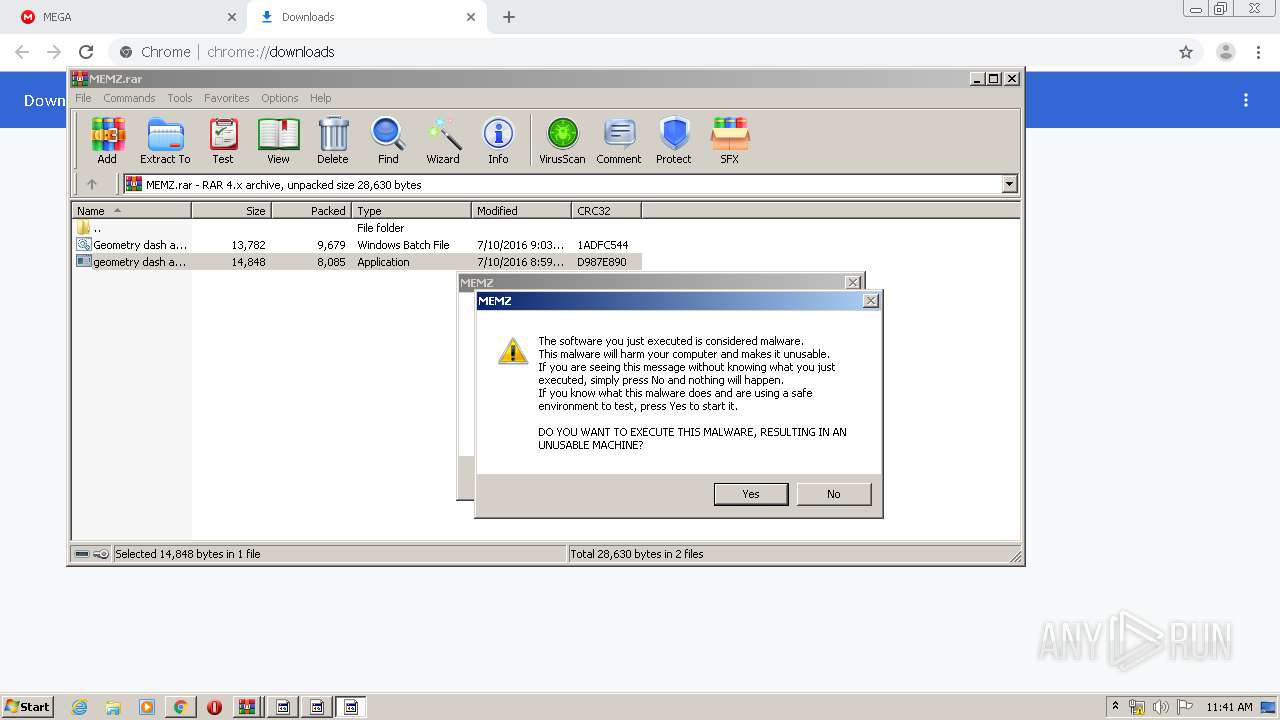
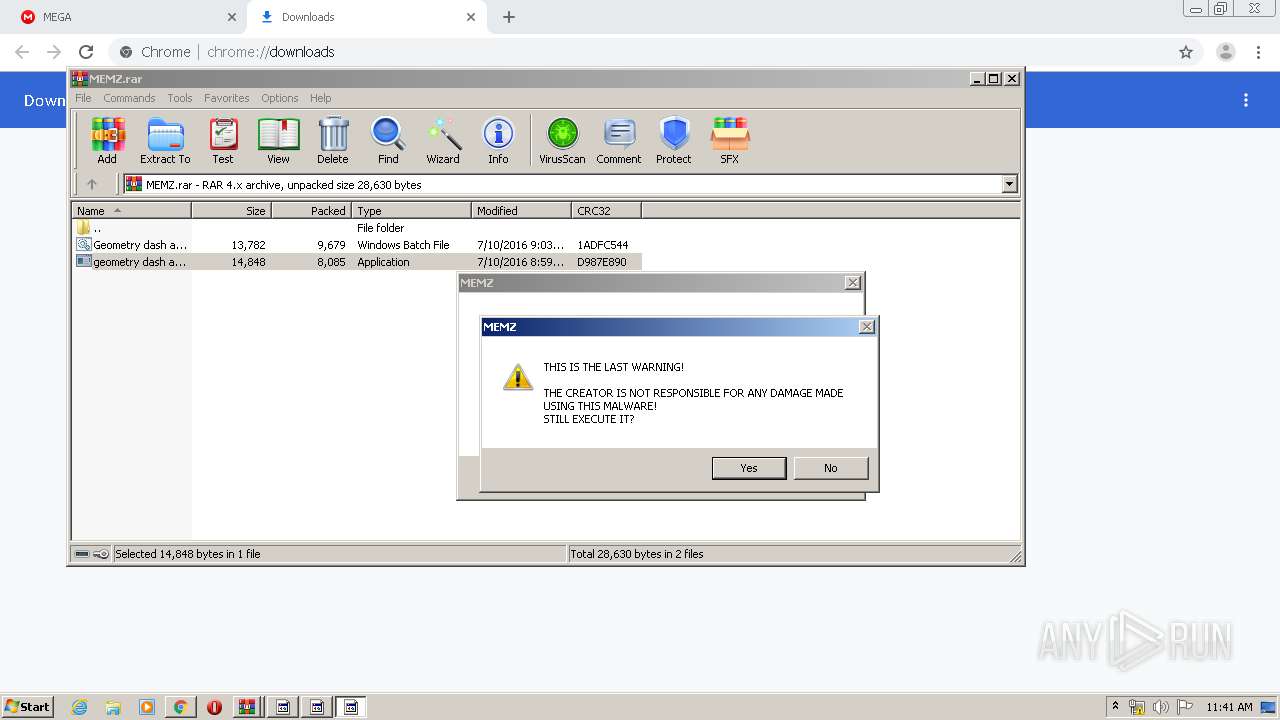
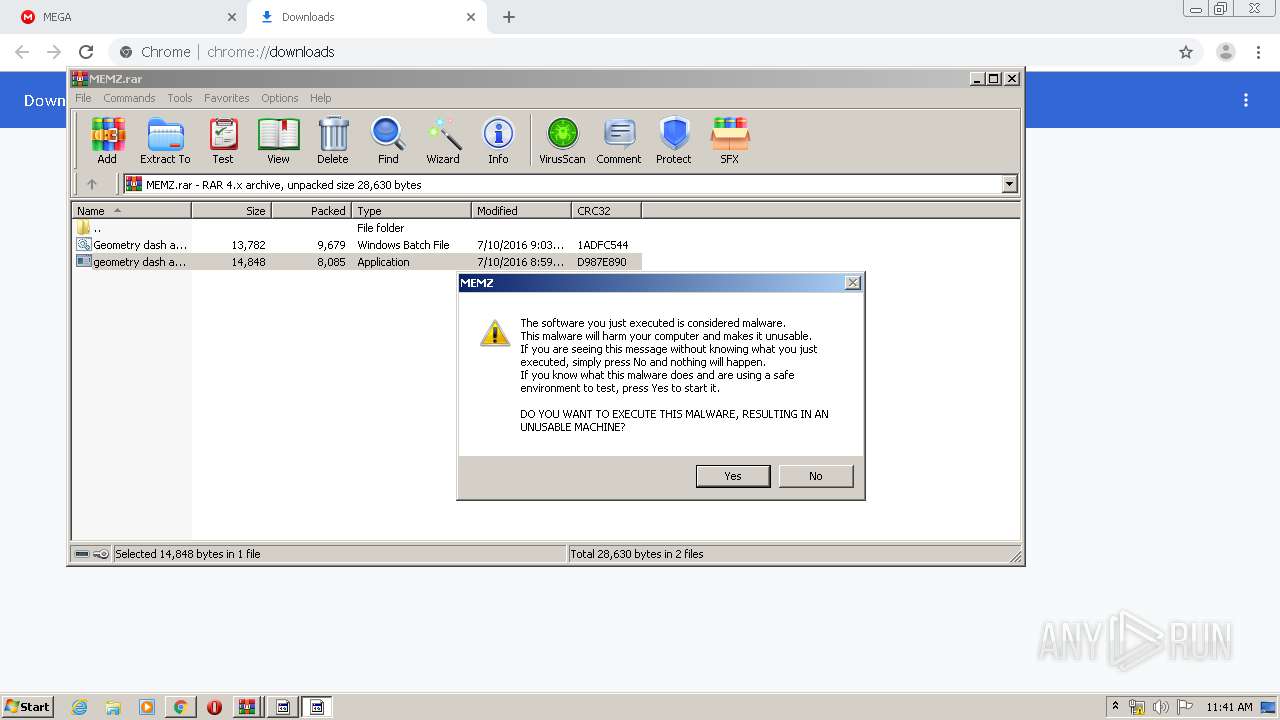
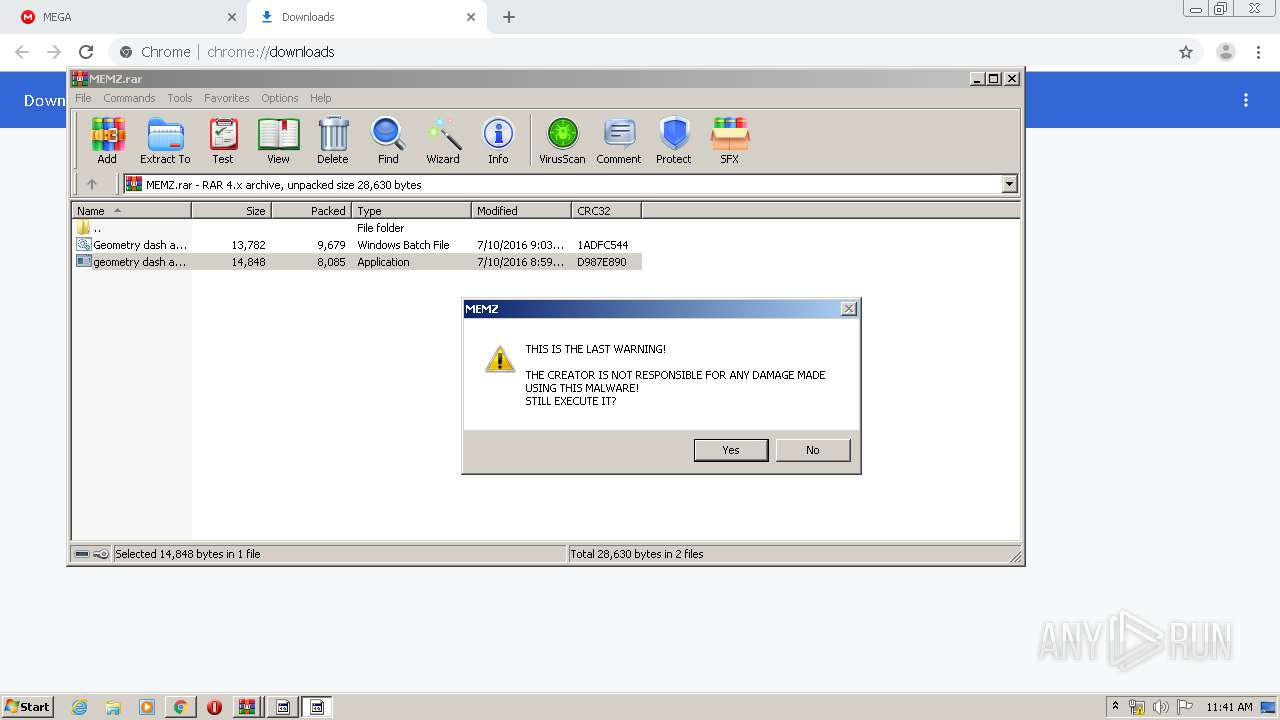
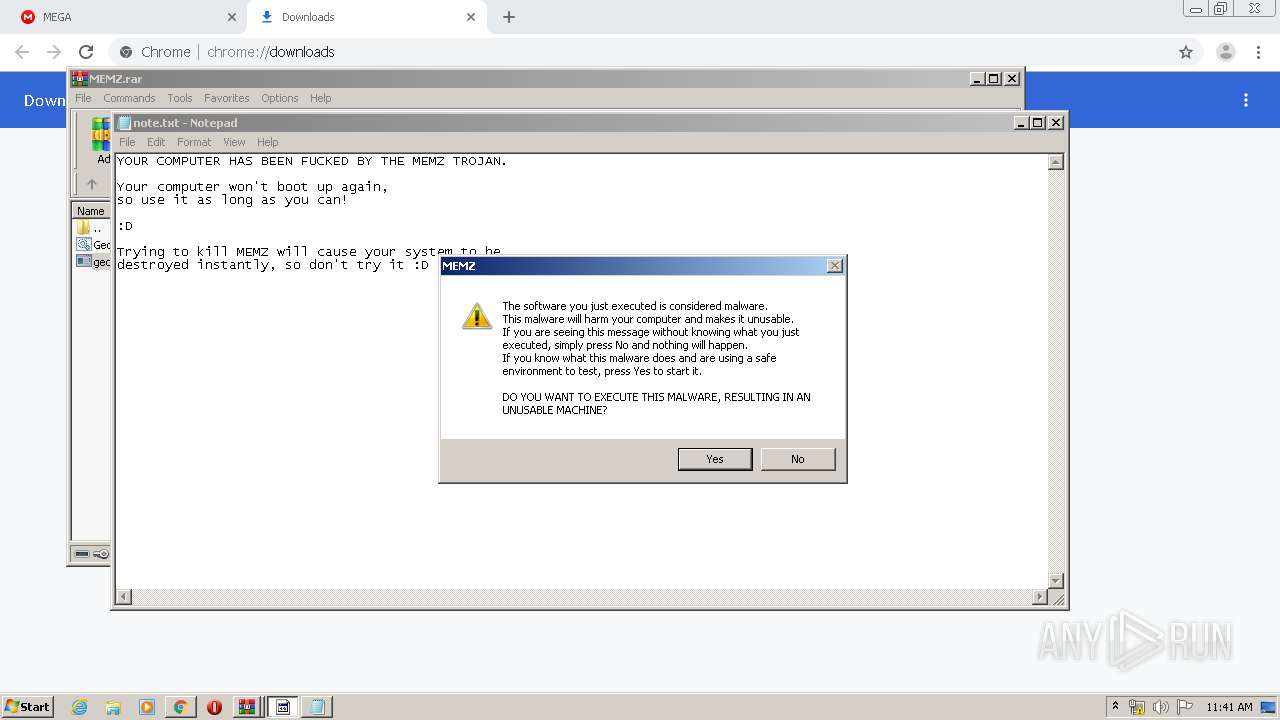
MALICIOUS
Application was dropped or rewritten from another process
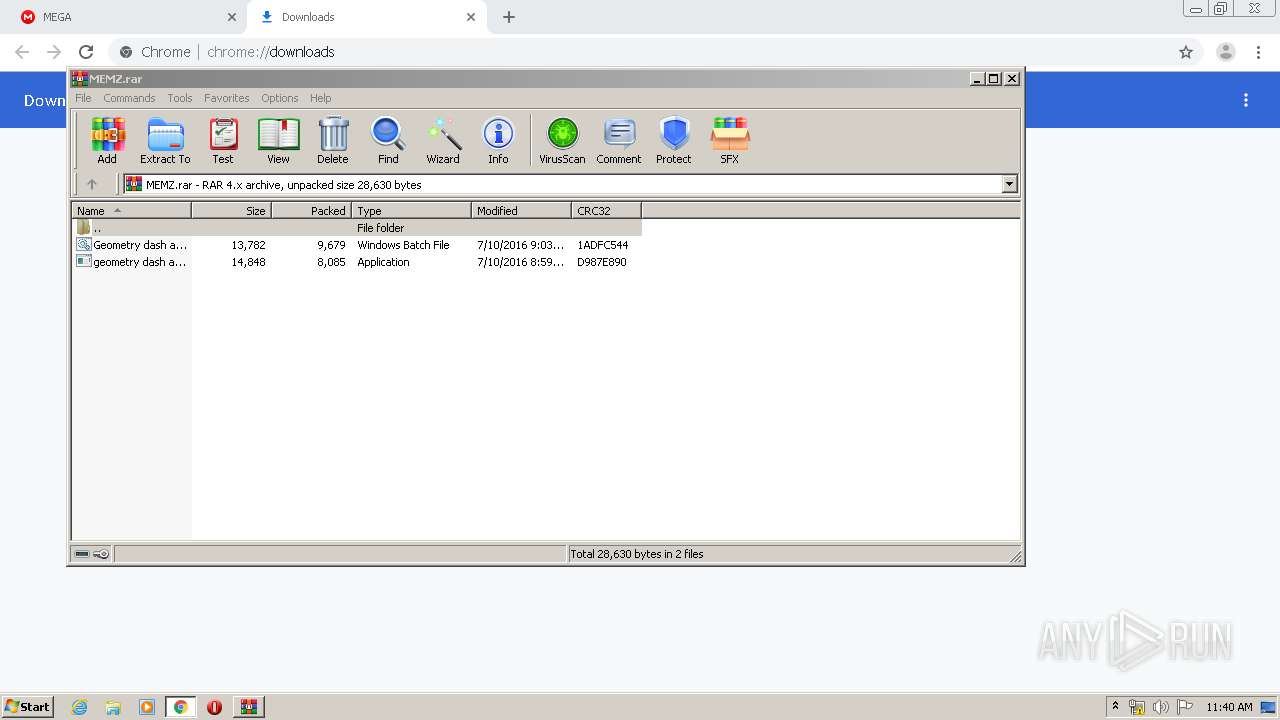
- geometry dash auto speedhack.exe (PID: 3324)
- geometry dash auto speedhack.exe (PID: 2420)
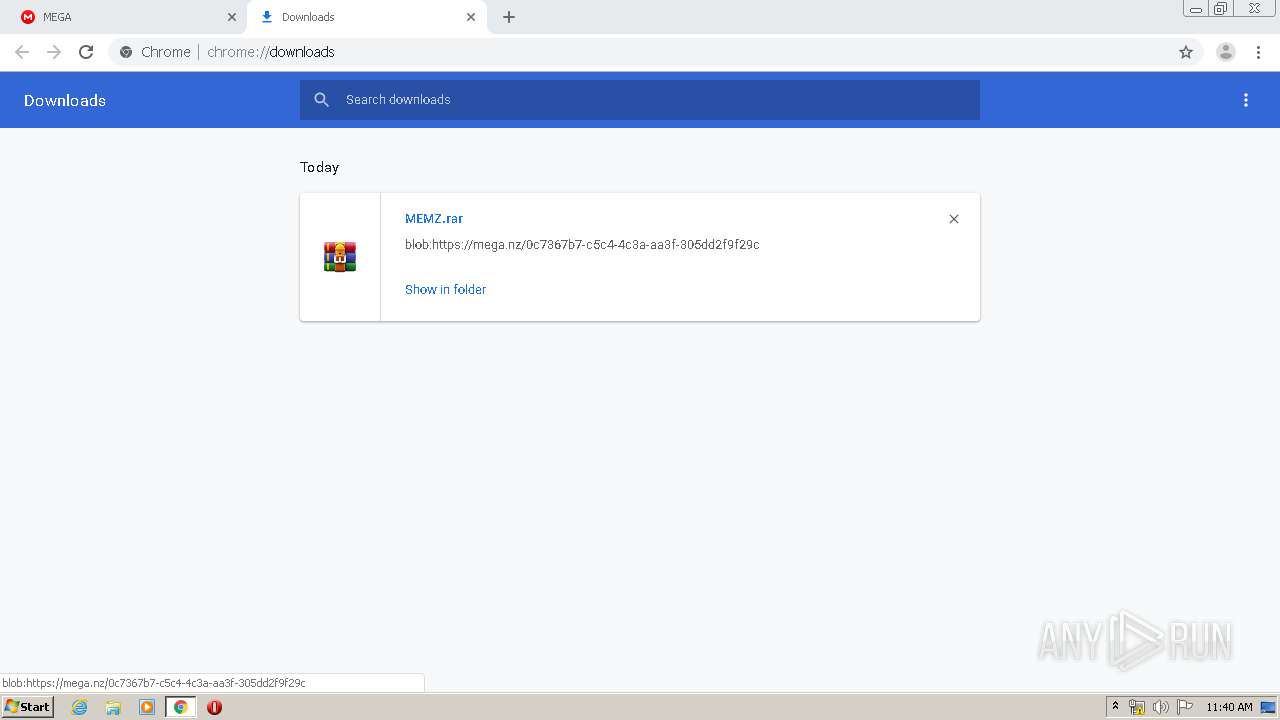
- MEMZ.exe (PID: 1920)
- geometry dash auto speedhack.exe (PID: 3056)
- geometry dash auto speedhack.exe (PID: 1212)
- MEMZ.exe (PID: 2708)
- geometry dash auto speedhack.exe (PID: 1216)
- geometry dash auto speedhack.exe (PID: 3440)
- MEMZ.exe (PID: 3720)
- geometry dash auto speedhack.exe (PID: 3896)
- geometry dash auto speedhack.exe (PID: 3856)
- geometry dash auto speedhack.exe (PID: 2556)
- geometry dash auto speedhack.exe (PID: 1380)
Low-level write access rights to disk partition
- geometry dash auto speedhack.exe (PID: 1380)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2504)
- cscript.exe (PID: 3944)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3256)
Modifies files in Chrome extension folder
- chrome.exe (PID: 676)
Creates files in the user directory
- cscript.exe (PID: 3944)
Executes scripts
- cmd.exe (PID: 1792)
Application launched itself
- geometry dash auto speedhack.exe (PID: 3440)
Low-level read access rights to disk partition
- geometry dash auto speedhack.exe (PID: 1380)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 2328)
Changes internet zones settings
- iexplore.exe (PID: 2388)
Application launched itself
- iexplore.exe (PID: 2388)
- chrome.exe (PID: 676)
Reads the hosts file
- chrome.exe (PID: 944)
- chrome.exe (PID: 676)
Reads internet explorer settings
- iexplore.exe (PID: 2328)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2388)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2328)
Manual execution by user
- chrome.exe (PID: 676)
Changes settings of System certificates
- iexplore.exe (PID: 2388)
Creates files in the user directory
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 2328)
Reads settings of System Certificates
- chrome.exe (PID: 944)
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
141
Monitored processes
95
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2375186322294366945 --renderer-client-id=43 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4340 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=1339904867519949853 --mojo-platform-channel-handle=992 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11504844344059162160 --renderer-client-id=49 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4712 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2495071736303971331 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2496 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11446238262135940267 --mojo-platform-channel-handle=3544 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=6167941891473713938 --mojo-platform-channel-handle=1644 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,3779294977267137137,8493396984121358407,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11411762737478379962 --renderer-client-id=44 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1212 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.29011\geometry dash auto speedhack.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.29011\geometry dash auto speedhack.exe | — | geometry dash auto speedhack.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.29011\geometry dash auto speedhack.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.29011\geometry dash auto speedhack.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
4 457
Read events
4 026
Write events
394
Delete events
37
Modification events
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3053902228 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30816457 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
484
Text files
521
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA913.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA924.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAAEA.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAAFB.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAAFC.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarAAEB.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarAAFD.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarAAFE.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAB1F.tmp | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAB20.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
342
DNS requests
245
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2328 | iexplore.exe | GET | 200 | 95.101.72.176:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEEHB063uNMc6dPCqTOMgIPs%3D | US | der | 471 b | whitelisted |
2328 | iexplore.exe | GET | 304 | 67.26.75.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2328 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2328 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 143.204.208.79:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 95.101.72.176:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 143.204.208.79:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2328 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2328 | iexplore.exe | 35.227.233.104:443 | memz-trojan.en.softonic.com | — | US | malicious |
2328 | iexplore.exe | 151.101.2.133:443 | sc.sftcdn.net | Fastly | US | malicious |
2328 | iexplore.exe | 216.58.212.162:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
2328 | iexplore.exe | 104.108.60.76:443 | images.sftcdn.net | Akamai Technologies, Inc. | NL | unknown |
2328 | iexplore.exe | 99.86.0.120:443 | c.amazon-adsystem.com | AT&T Services, Inc. | US | unknown |
2328 | iexplore.exe | 143.204.201.25:443 | cdn-magiclinks.trackonomics.net | — | US | suspicious |
2328 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2328 | iexplore.exe | 95.101.72.176:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2328 | iexplore.exe | 216.58.212.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
memz-trojan.en.softonic.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
sc.sftcdn.net |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
images.sftcdn.net |
| whitelisted |
cdn-magiclinks.trackonomics.net |
| whitelisted |