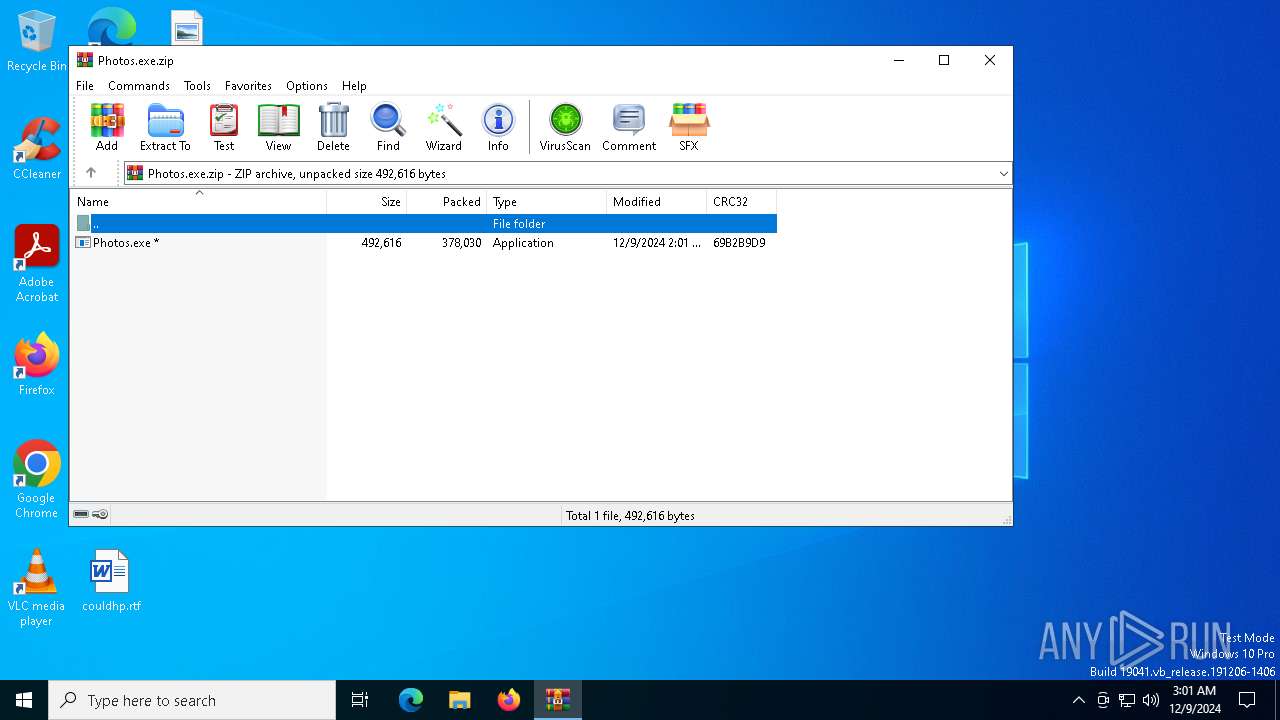
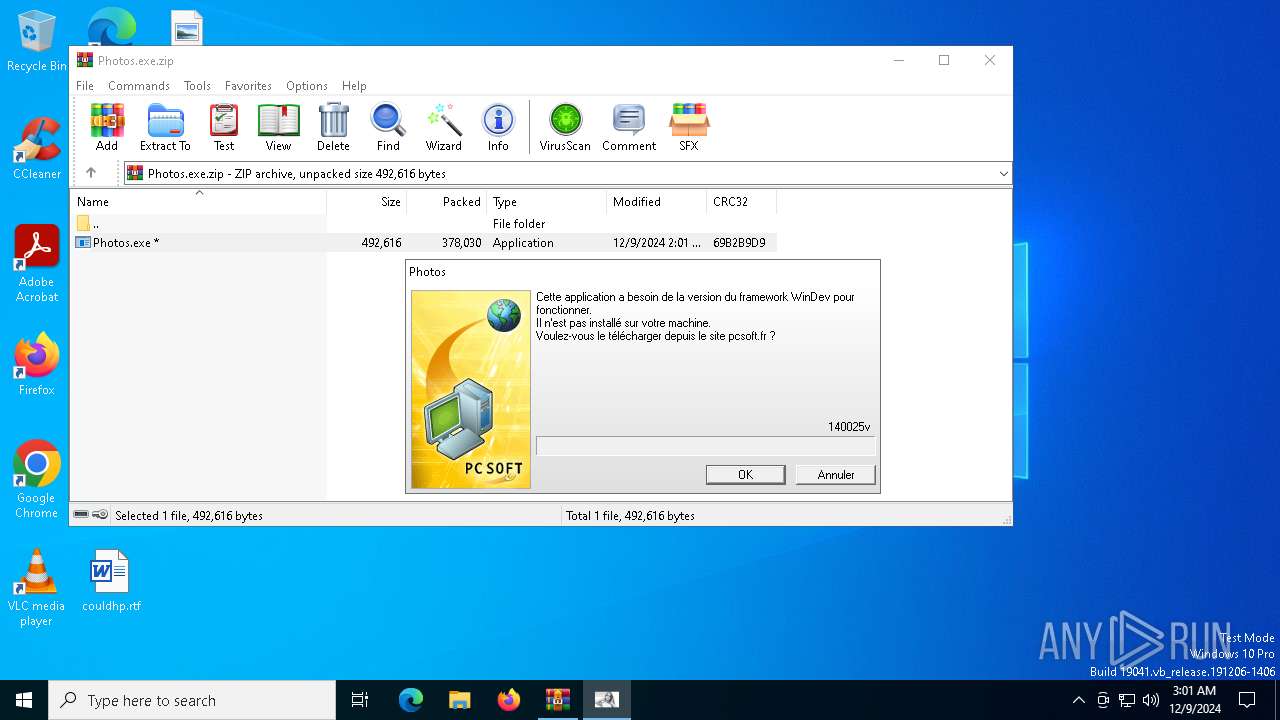
| File name: | Photos.exe.zip |
| Full analysis: | https://app.any.run/tasks/0166b197-4642-4730-a3f9-e910f3aed385 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 03:00:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 77F11E8D82BEC0715A9F1062EC539398 |
| SHA1: | CC963D5F192313E3B4E982FAAD142BA89F6A0AC2 |
| SHA256: | A72D31C9F0DC4FC589FBD1BBCD91E07DA5FAF8740BD7FBF16B31D73FD588E122 |
| SSDEEP: | 12288:YkUY3ocVidvuGWuMBlSwBs6mtkaVXOFz0cRn5IxMp:zUY3o8id2GWuMBlSwBs6mtkat0z0c55x |
MALICIOUS
Generic archive extractor
- svchost.exe (PID: 4932)
Executing a file with an untrusted certificate
- InstallFramework.exe (PID: 3692)
- InstallFramework.exe (PID: 3288)
Changes the autorun value in the registry
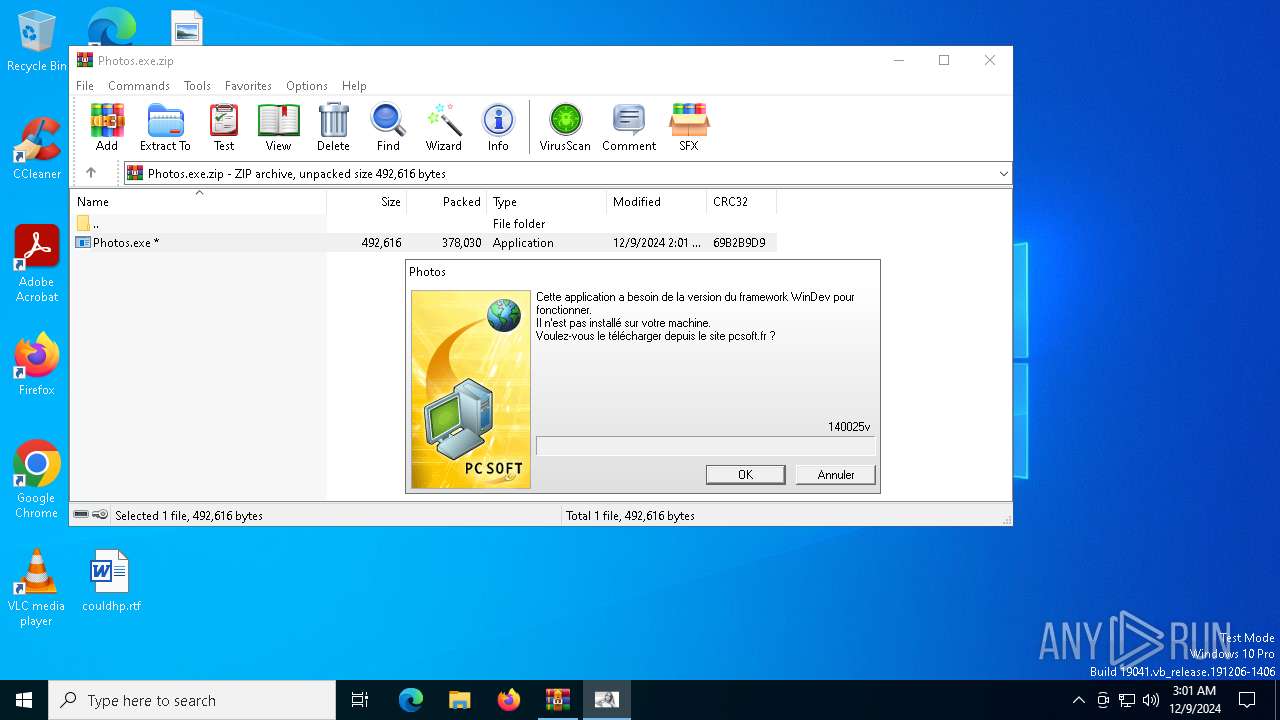
- Photos.exe (PID: 6940)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4932)
- Photos.exe (PID: 6940)
- rundll32.exe (PID: 3224)
Executable content was dropped or overwritten
- Photos.exe (PID: 6940)
- InstallFramework.exe (PID: 3288)
Connects to FTP
- Photos.exe (PID: 6940)
Connects to unusual port
- Photos.exe (PID: 6940)
- rundll32.exe (PID: 3224)
Starts itself from another location
- Photos.exe (PID: 6940)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 4932)
- consent.exe (PID: 5640)
- Photos.exe (PID: 6940)
Checks supported languages
- Photos.exe (PID: 6940)
- rundll32.exe (PID: 3224)
- InstallFramework.exe (PID: 3288)
Reads the computer name
- Photos.exe (PID: 6940)
- rundll32.exe (PID: 3224)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4932)
Reads the software policy settings
- WaaSMedicAgent.exe (PID: 7044)
- SIHClient.exe (PID: 7164)
- consent.exe (PID: 5640)
Checks proxy server information
- Photos.exe (PID: 6940)
- rundll32.exe (PID: 3224)
Creates files or folders in the user directory
- Photos.exe (PID: 6940)
Create files in a temporary directory
- Photos.exe (PID: 6940)
- InstallFramework.exe (PID: 3288)
Process checks computer location settings
- Photos.exe (PID: 6940)
Creates files in the program directory
- Photos.exe (PID: 6940)
Reads the machine GUID from the registry
- rundll32.exe (PID: 3224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:12:09 02:01:22 |
| ZipCRC: | 0x69b2b9d9 |
| ZipCompressedSize: | 378030 |
| ZipUncompressedSize: | 492616 |
| ZipFileName: | Photos.exe |
Total processes
135
Monitored processes
30
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1340 | C:\WINDOWS\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s PcaSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1888 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s NetSetupSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s Browser | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | C:\WINDOWS\System32\Upfc.exe /launchtype periodic /cv vqyZsH1S6kej6JwYolIo5w.0 | C:\Windows\System32\upfc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Updateability From SCM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s Netman | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 849
Read events
26 412
Write events
304
Delete events
133
Modification events
| (PID) Process: | (6092) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\TaskStore |
| Operation: | write | Name: | Schedule Maintenance Work |
Value: Microsoft\Windows\UpdateOrchestrator | |||
| (PID) Process: | (6092) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\TaskStore |
| Operation: | write | Name: | Schedule Work |
Value: Microsoft\Windows\UpdateOrchestrator | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDevicePnp |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDevicePnp\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDeviceContainer |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDeviceContainer\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDriverBinary |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDriverBinary\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDeviceMediaClass |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{5527aa12-63c0-68e4-5b15-565719f44db5}\Root\InventoryDeviceMediaClass\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
88
Suspicious files
9
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1176 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:1F183CE23AEAD67E14C3472B43109763 | SHA256:657A1895A158BFB57DCE6059274BD063C0273A2421C903BC8978FD3250BE3964 | |||
| 6092 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.003.etl | etl | |
MD5:A83C439448C1E67E6FFC948FEF1FCE18 | SHA256:9FAA75F166CFDD869D3549B76139DDDDDB6A50790A5C6CC81B2084A432D7D60F | |||
| 6092 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.002.etl | etl | |
MD5:DEDECFD6DDECAA969F2F735761A8363F | SHA256:6D554FD45C5A4651BA508028AF27C5AE6501E3A2E10CFF9A8A925DCB74A68702 | |||
| 1176 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:3834B4212B9F1CFEF504DA6F632C74A9 | SHA256:B8DC4CD2BE39ADBE1CF4E924580569F6C35C37BA28C375DDD513E7C7890B2E62 | |||
| 7164 | SIHClient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\51867C3735CFAECCDB556E146BB12C28 | der | |
MD5:E1E3CC4D691535D73D5E7BA76E9B14B2 | SHA256:AB97B5AE07DF03363B9F4A73AD4C1C0C9816DC21D9A4D60FFF32EB8B94AAD4C6 | |||
| 7164 | SIHClient.exe | C:\Windows\Logs\SIH\SIH.20241209.030129.443.1.etl | binary | |
MD5:A238F68C0F41833B1DA9C439DF9CE7B7 | SHA256:A51B95906676588B10D2D2C173EE33EB807B1F9EC40778B71F7D1A7919E2E0B3 | |||
| 6940 | Photos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\InstallFramework_140025v[1].exe | executable | |
MD5:19A76EDA7B7D0BA22FA8FAB03E6CFC11 | SHA256:CDC01013292ED4766341F91FEB702EE8B4248E10EC127C3E241B1CE09CDB000E | |||
| 3288 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4932.8017\WD140com.dll | executable | |
MD5:FE4CD0E2775CB64D27CCE987828BEFDD | SHA256:8FD8FEB715F5AA1C4DAC982813828241186DF15CA01310BBE1A325F393E84EBC | |||
| 3288 | InstallFramework.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4932.8017\WD140barc.dll | executable | |
MD5:EB8F13AD9760EAECEF52E6F8911F42E0 | SHA256:BAA794E8010C5002CDC7AA7EA27B120D380FCC9AFACBEC825F428B512C4E9C77 | |||
| 4932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4932.8017\Photos.exe | executable | |
MD5:754545AFCA5D10149F1138221317DA2D | SHA256:38633E676FECE37028170D8736E1BC616784ECD7FCF5D503B65030688C8E4A97 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
36
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6352 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5340 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6940 | Photos.exe | Misc activity | ET INFO .exe File requested over FTP |
6940 | Photos.exe | Misc activity | ET HUNTING PE EXE Download over raw TCP |