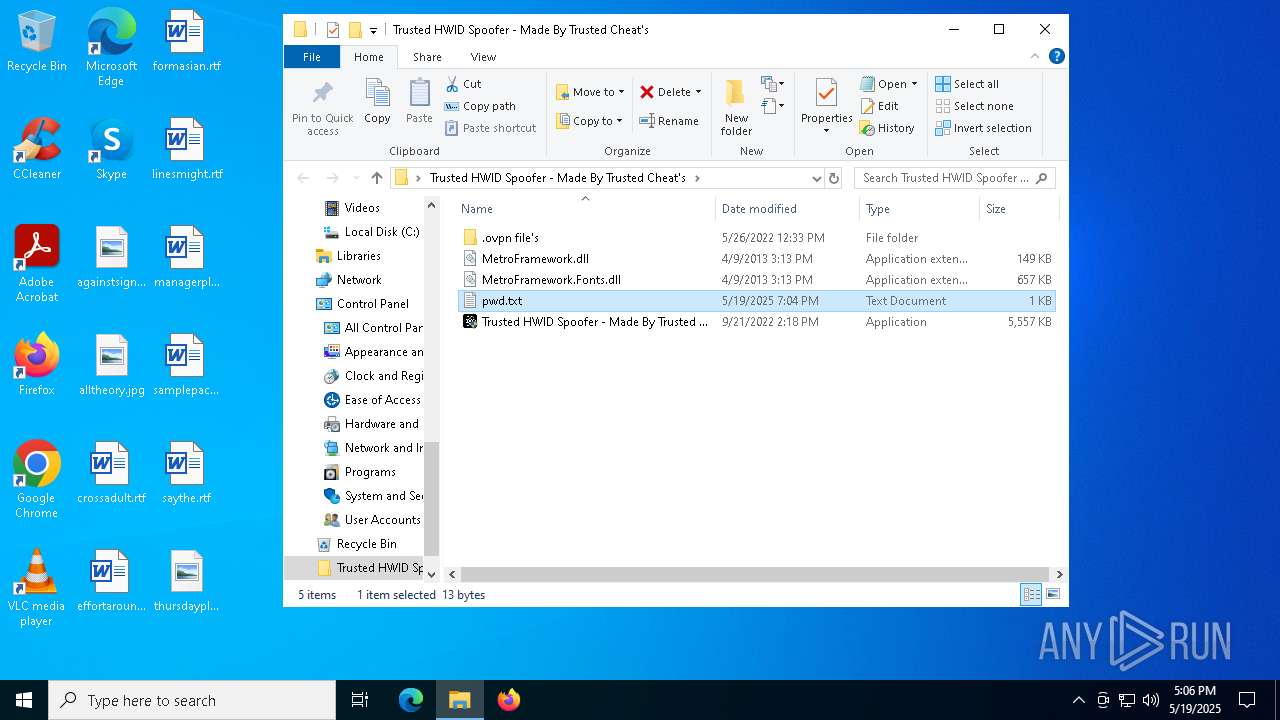
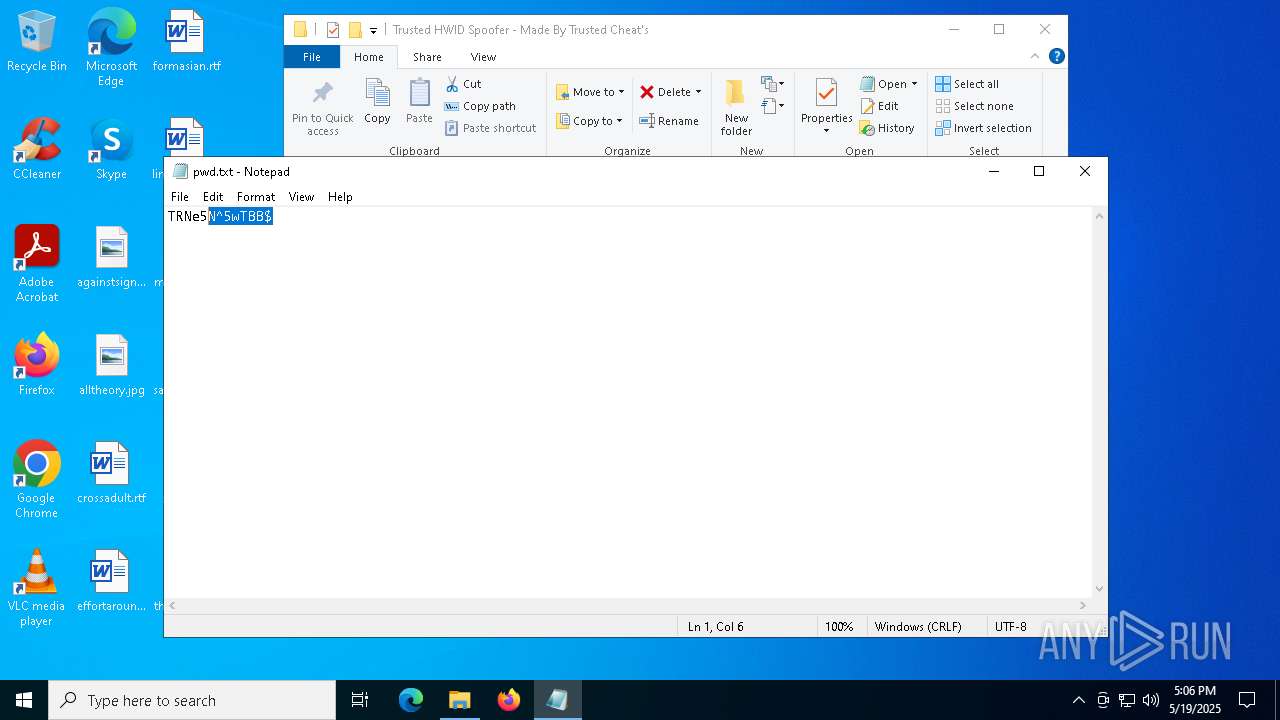
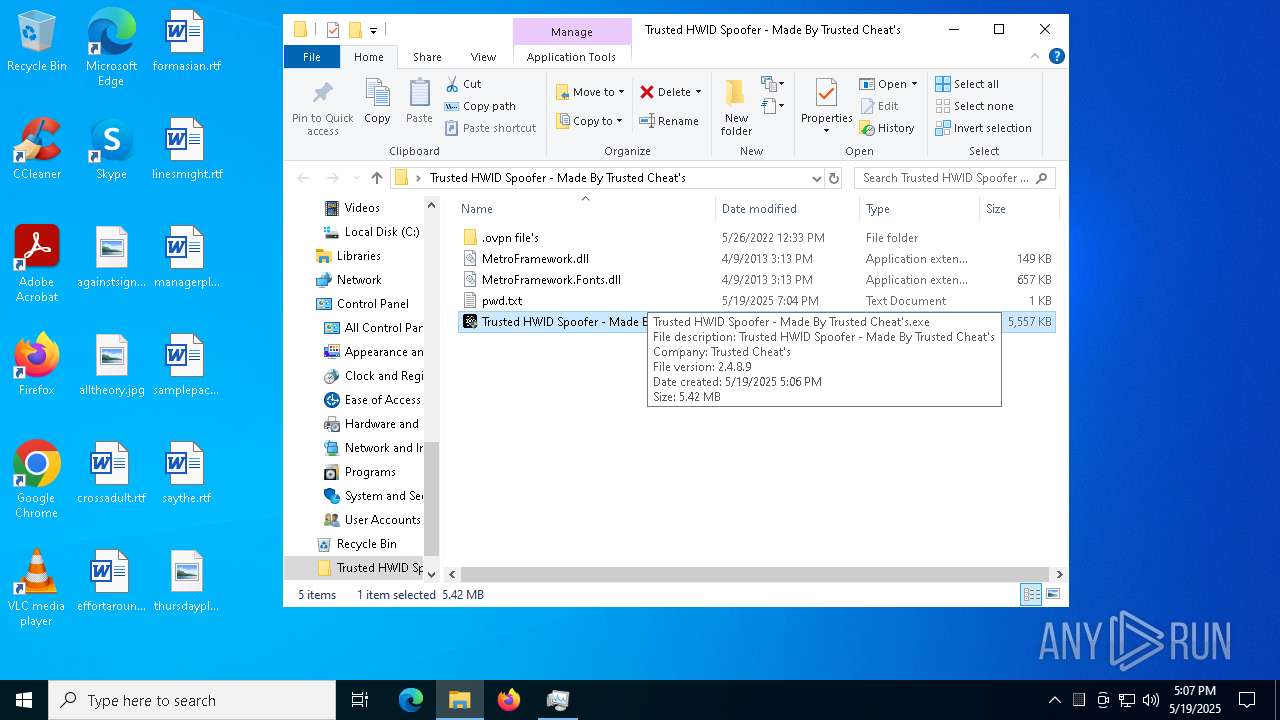
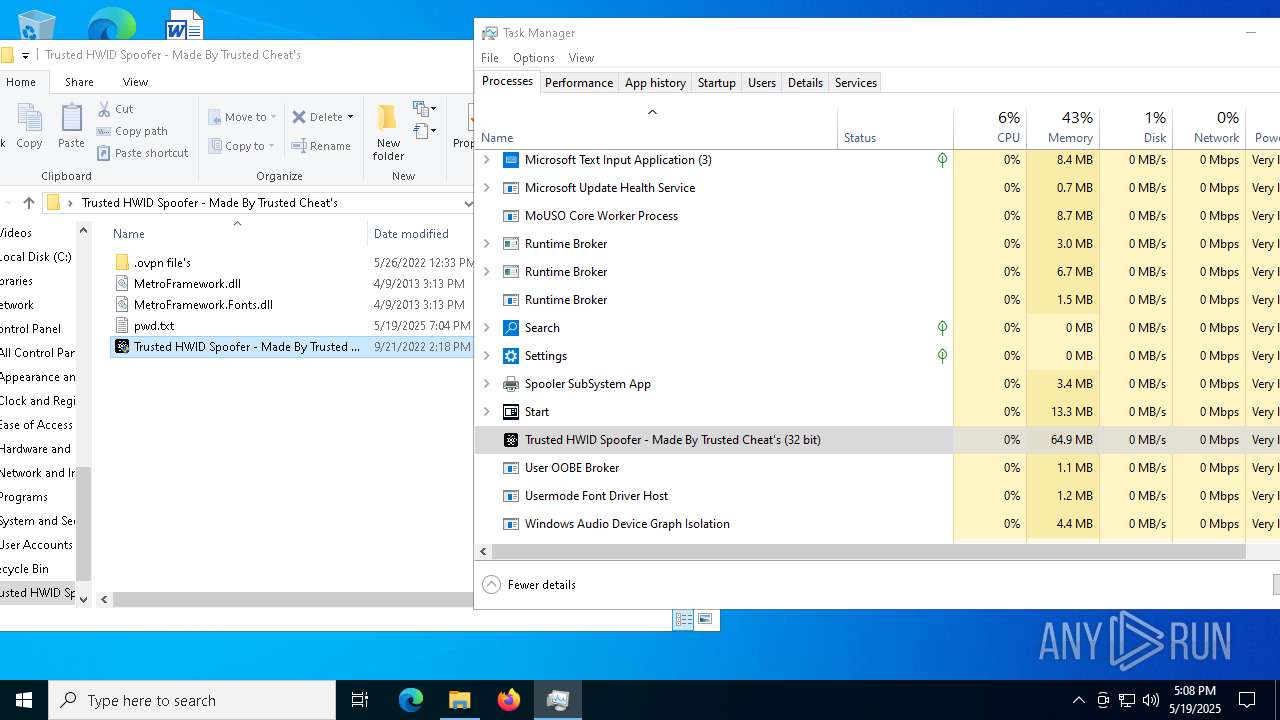
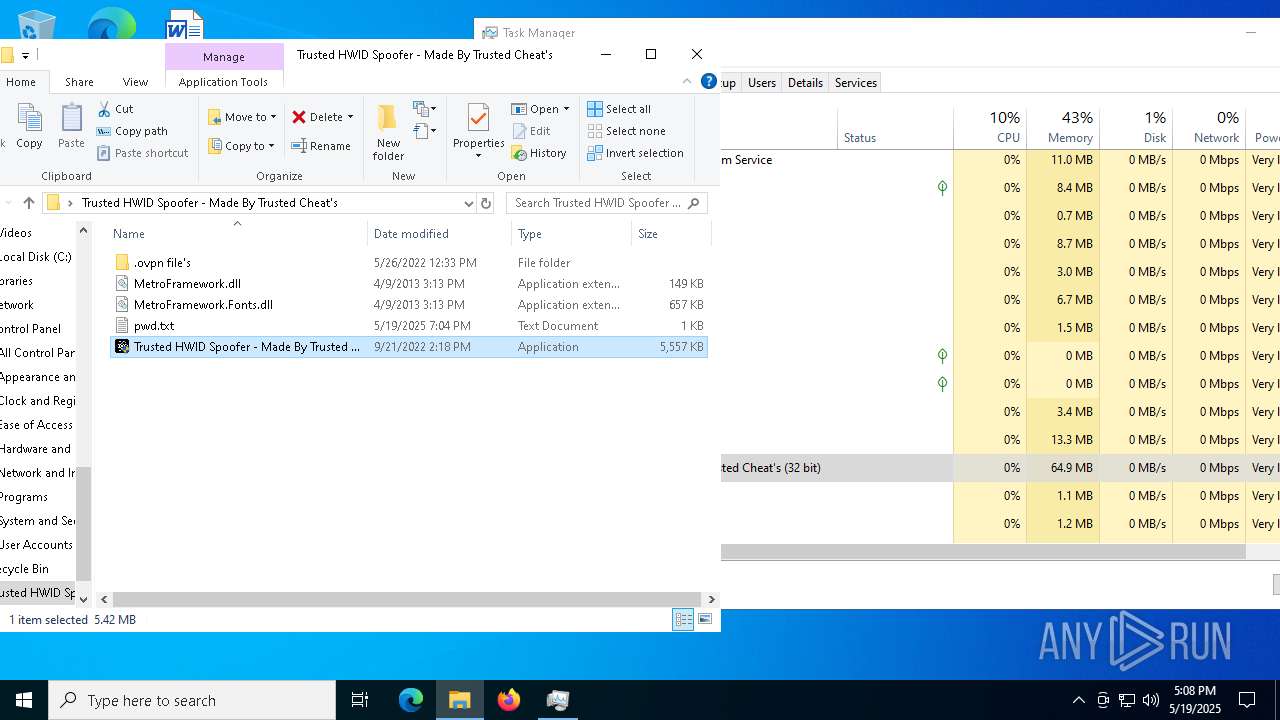
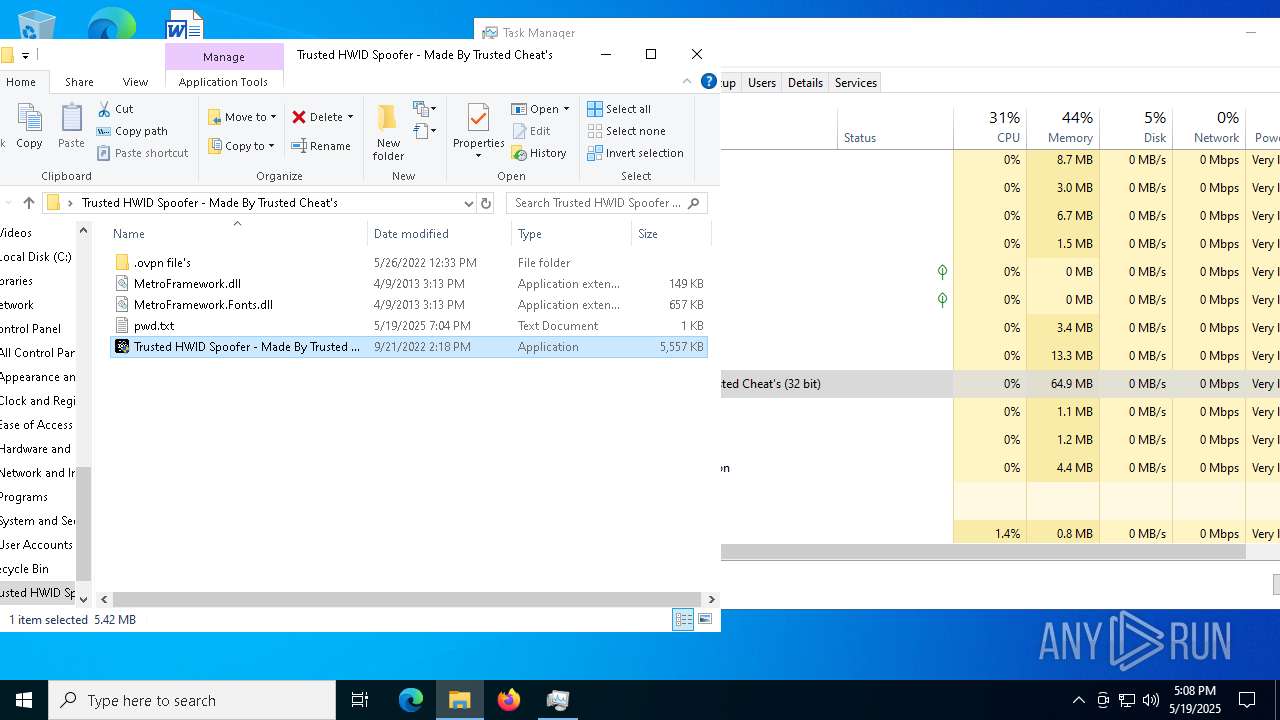
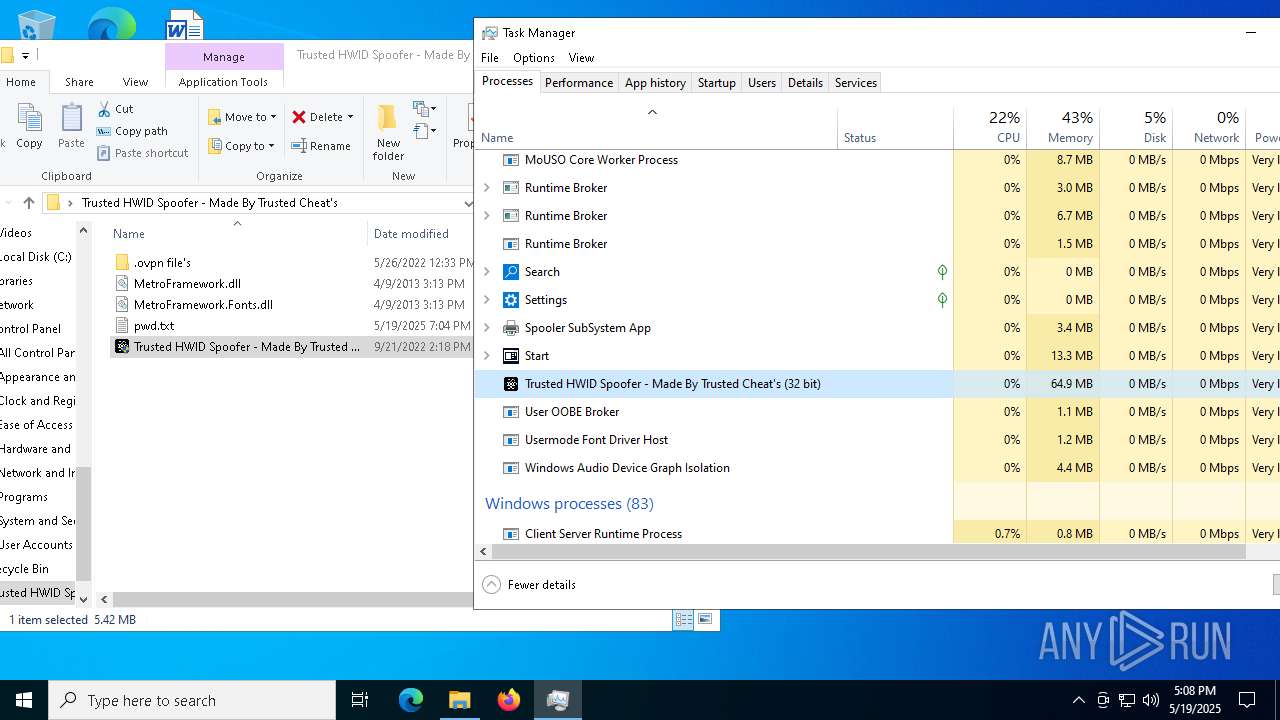
| File name: | Trusted HWID Spoofer - Made By Trusted Cheat's.zip |
| Full analysis: | https://app.any.run/tasks/49c80552-3963-4690-8cd0-27597beb5c6c |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 17:05:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 3D2B3EE80B2AD62CF5FEB9A3343D4694 |
| SHA1: | 480025B86BE91D0495BC93759208B4B06087B908 |
| SHA256: | A7013C10CAE3CED6C216C9E26FC2C122A5484B0A7BBDFECA120D7AF4DCD33828 |
| SSDEEP: | 98304:yczHSSI5HgRO9/yLvYrAs9iHTmobRc5Y4YYP4IHQ0ekmSnuT5dl/K1A5H4nbm6uf:fL4vqVBtWpLy |
MALICIOUS
No malicious indicators.SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7220)
The process creates files with name similar to system file names
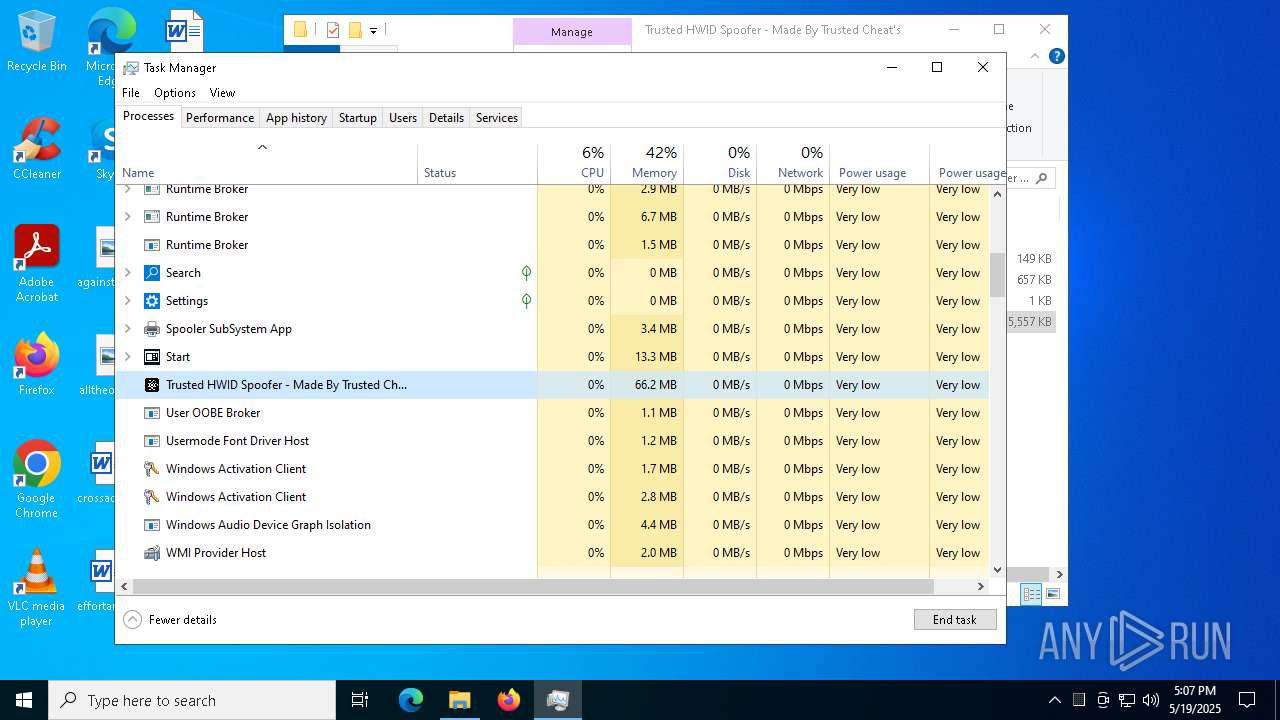
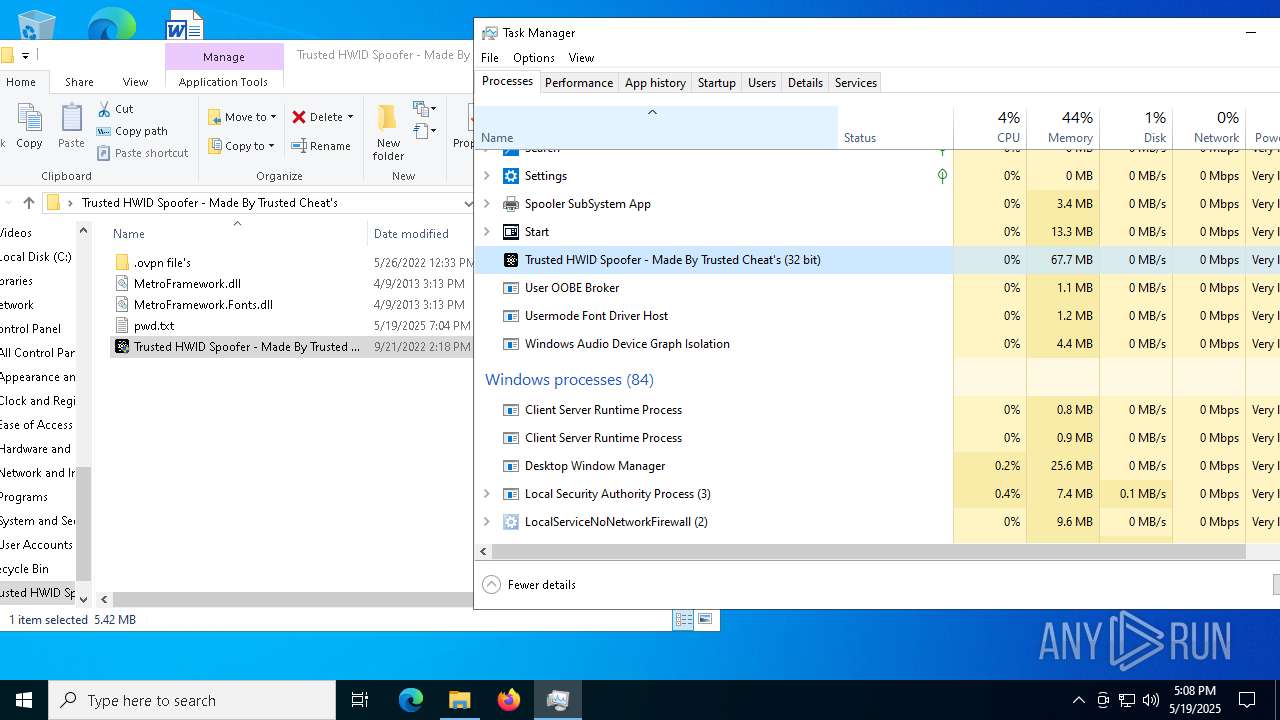
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
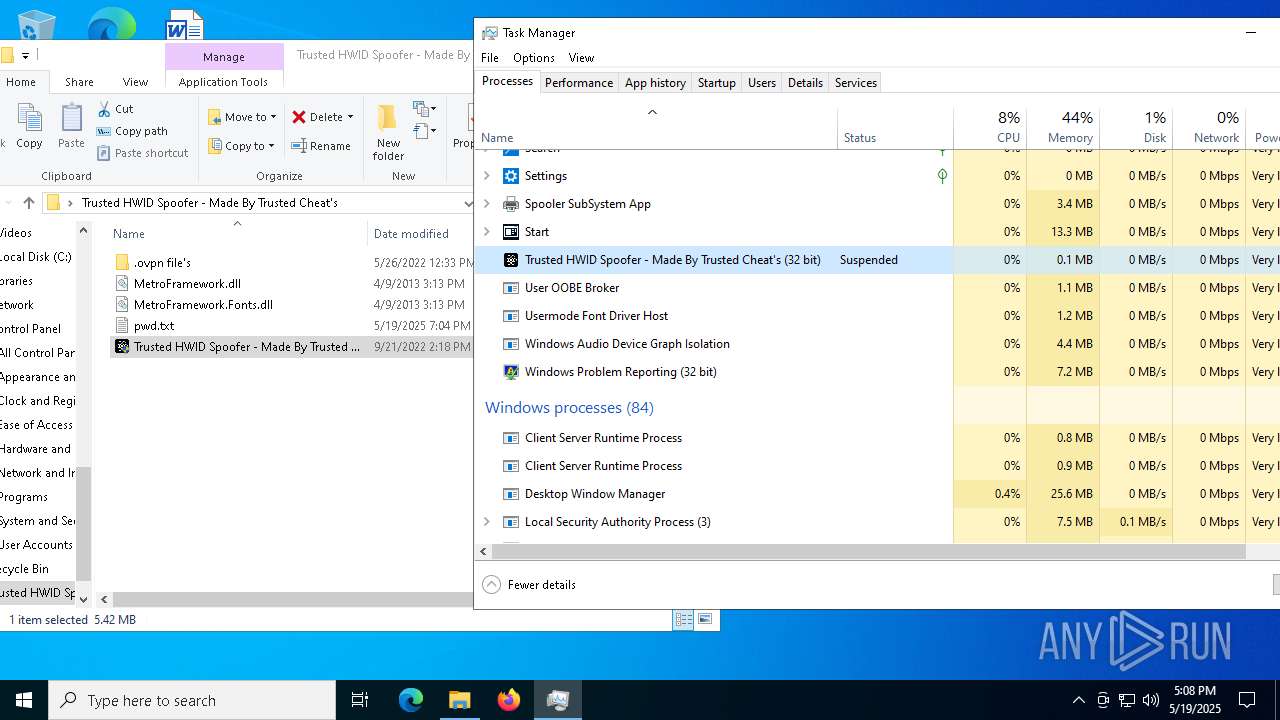
Executes application which crashes
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7212)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 4628)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7684)
INFO
Manual execution by a user
- notepad.exe (PID: 7920)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7992)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7212)
- Taskmgr.exe (PID: 720)
- Taskmgr.exe (PID: 1180)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 5744)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7864)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7684)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 4628)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7220)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7920)
- Taskmgr.exe (PID: 720)
Checks supported languages
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7212)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
Reads the computer name
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7212)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
Reads the machine GUID from the registry
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7212)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
Disables trace logs
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
Checks proxy server information
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
- slui.exe (PID: 6388)
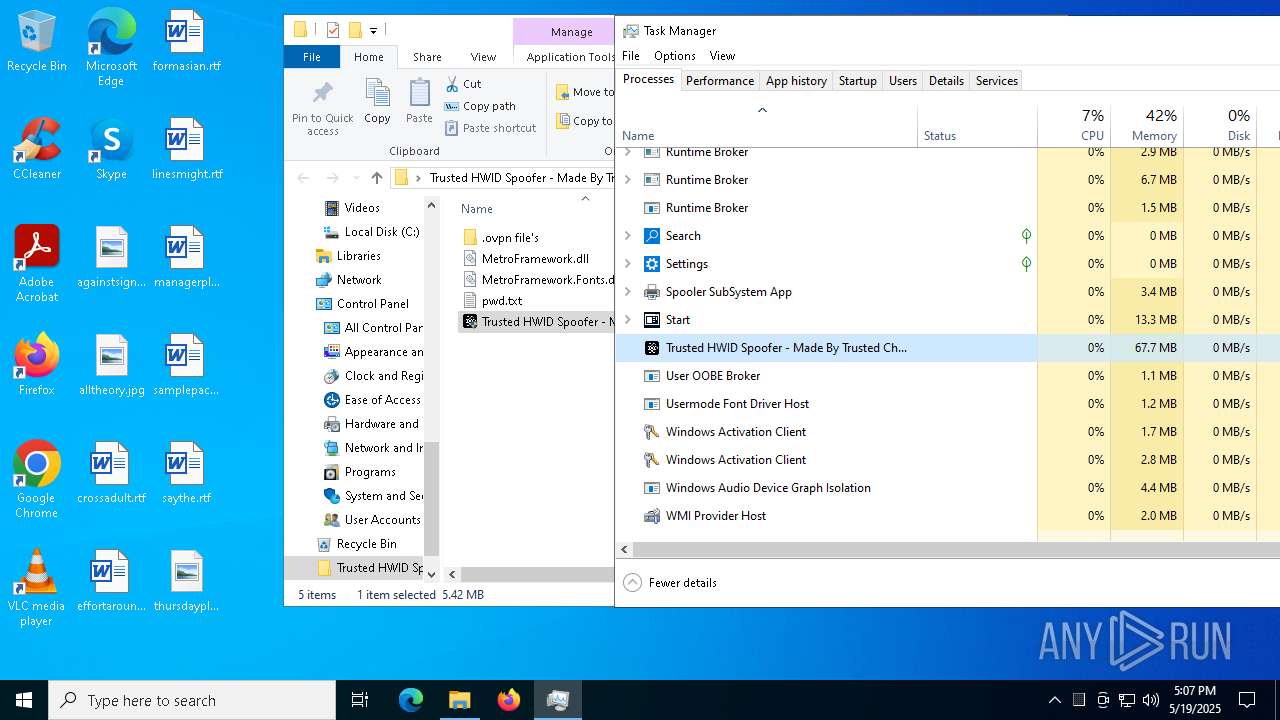
Creates files or folders in the user directory
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- WerFault.exe (PID: 7036)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
- WerFault.exe (PID: 5544)
- WerFault.exe (PID: 2644)
Confuser has been detected (YARA)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 8040)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7504)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7684)
- Trusted HWID Spoofer - Made By Trusted Cheat's.exe (PID: 7492)
Reads the software policy settings
- slui.exe (PID: 6388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:05:26 12:33:48 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
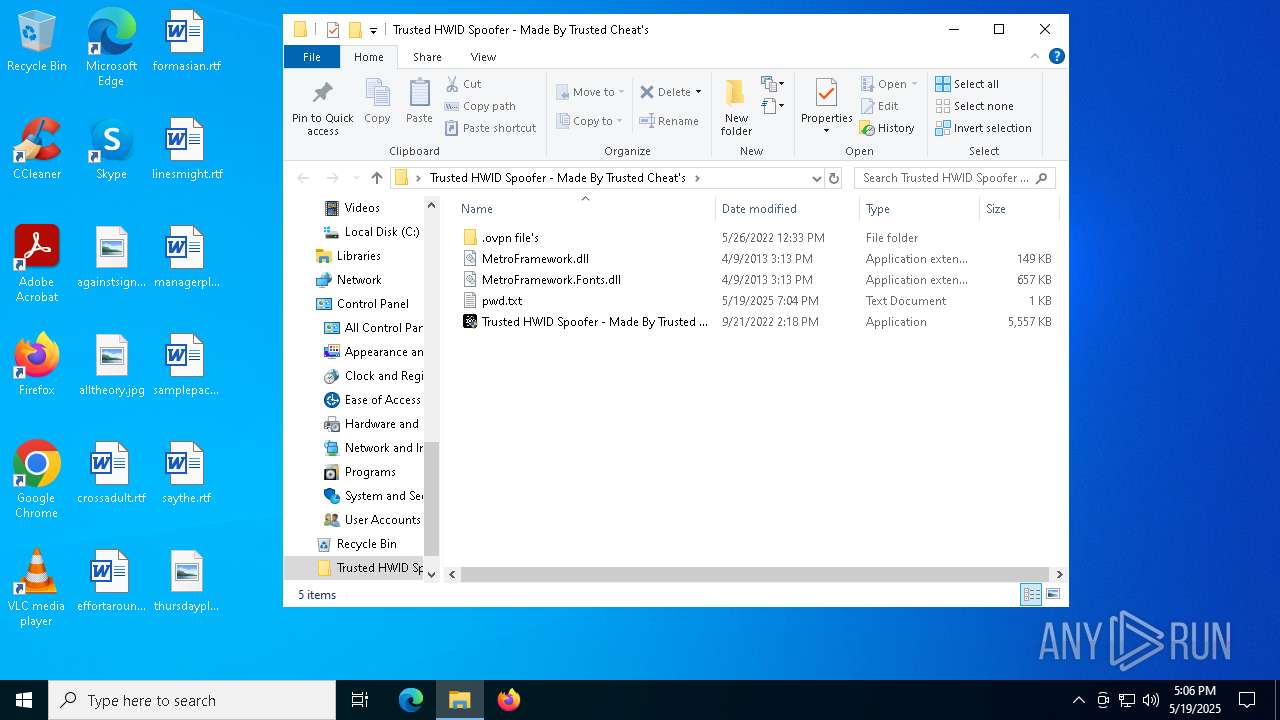
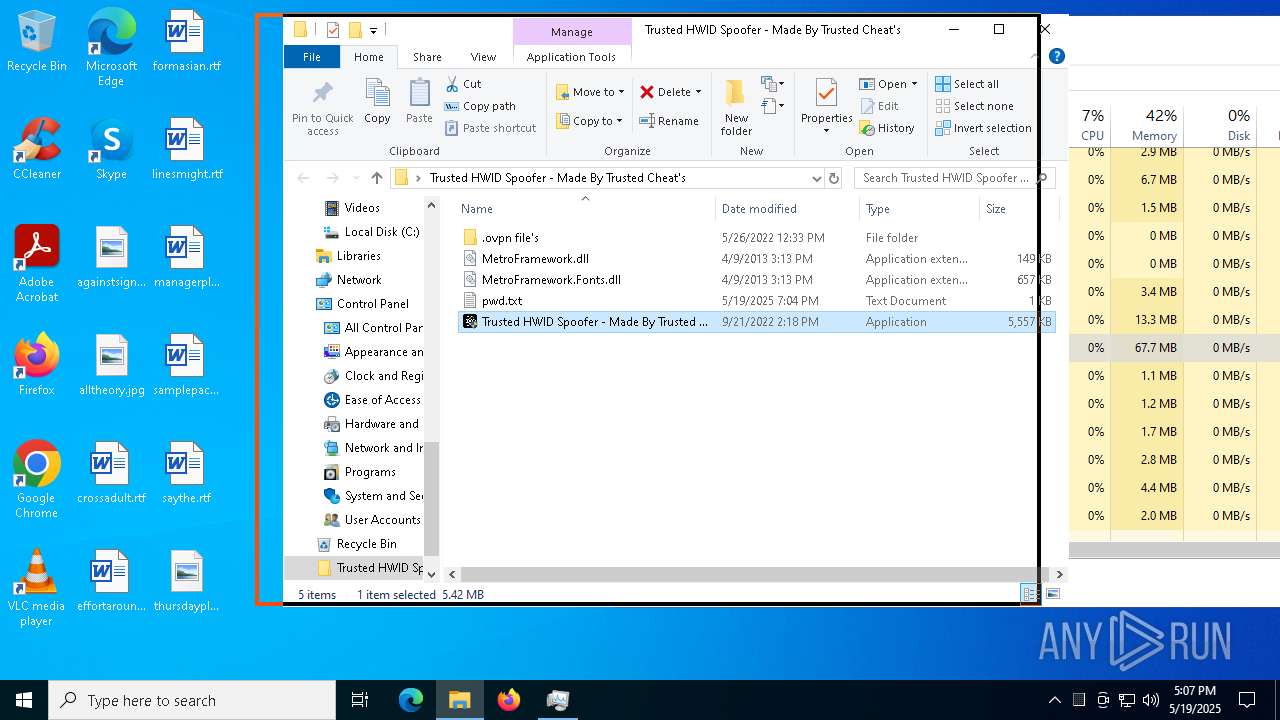
| ZipFileName: | Trusted HWID Spoofer - Made By Trusted Cheat's/.ovpn file's/ |
Total processes
167
Monitored processes
20
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4628 -s 1312 | C:\Windows\SysWOW64\WerFault.exe | — | Trusted HWID Spoofer - Made By Trusted Cheat's.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2644 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7504 -s 1644 | C:\Windows\SysWOW64\WerFault.exe | — | Trusted HWID Spoofer - Made By Trusted Cheat's.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4376 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7684 -s 1664 | C:\Windows\SysWOW64\WerFault.exe | — | Trusted HWID Spoofer - Made By Trusted Cheat's.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\Users\admin\Desktop\Trusted HWID Spoofer - Made By Trusted Cheat's\Trusted HWID Spoofer - Made By Trusted Cheat's.exe" | C:\Users\admin\Desktop\Trusted HWID Spoofer - Made By Trusted Cheat's\Trusted HWID Spoofer - Made By Trusted Cheat's.exe | explorer.exe | ||||||||||||
User: admin Company: Trusted Cheat's Integrity Level: HIGH Description: Trusted HWID Spoofer - Made By Trusted Cheat's Exit code: 3762504530 Version: 2.4.8.9 Modules
| |||||||||||||||
| 5544 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7212 -s 1316 | C:\Windows\SysWOW64\WerFault.exe | — | Trusted HWID Spoofer - Made By Trusted Cheat's.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5744 | "C:\Users\admin\Desktop\Trusted HWID Spoofer - Made By Trusted Cheat's\Trusted HWID Spoofer - Made By Trusted Cheat's.exe" | C:\Users\admin\Desktop\Trusted HWID Spoofer - Made By Trusted Cheat's\Trusted HWID Spoofer - Made By Trusted Cheat's.exe | — | explorer.exe | |||||||||||
User: admin Company: Trusted Cheat's Integrity Level: MEDIUM Description: Trusted HWID Spoofer - Made By Trusted Cheat's Exit code: 3221226540 Version: 2.4.8.9 Modules
| |||||||||||||||
| 6388 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8040 -s 1676 | C:\Windows\SysWOW64\WerFault.exe | — | Trusted HWID Spoofer - Made By Trusted Cheat's.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 992
Read events
13 921
Write events
55
Delete events
16
Modification events
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Trusted HWID Spoofer - Made By Trusted Cheat's.zip | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF7A000000280000003A04000011020000 | |||
| (PID) Process: | (7220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
3
Suspicious files
10
Text files
91
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\ca.toronto.ovpn.com.ovpn | text | |
MD5:52BC1D96AB20654019A64953BD3754EE | SHA256:892608DC26547BD3C6D18AF1C733DDAEDD9CA403D81A4DC4745AED68B990EB14 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\de.ovpn.com.ovpn | text | |
MD5:0BD8169D89775D5C6CD97FEF4F16AFCE | SHA256:96D819F92A8AB736AAE74848CFC5930A6F9A6B96A012F46EAD7A735AC228B1F4 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\at.ovpn.com.ovpn | text | |
MD5:3F06D67A811868098F06D6A9F91CB82E | SHA256:0F41DC3C58D0564E8853DCBAED03F0A05EB3AEBF019016176961747C630B4048 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\at.vienna.ovpn.com.ovpn | text | |
MD5:2FDE39221AB22B1EE738BFB7D09ACB12 | SHA256:D6393A6521AE99E676E411482C54ADFD12C918DBC7326731008479EC020CC4FD | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\au.ovpn.com.ovpn | text | |
MD5:23C34863536C4F0CF1ED3D338A317A3F | SHA256:E7DCD414B0AEEFBD5896B8CF5DB7D21190D65F05F54BC9C868D77CA330DAD84F | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\es.ovpn.com.ovpn | text | |
MD5:004B083590145A8DE50B9E6583F16F60 | SHA256:95F3D0215E4F48DDAD91D06A5E5067EEFEDF87F82A292E8CEF7A9615A0898EB4 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\de.erfurt.ovpn.com.ovpn | text | |
MD5:73B010E0BDEF4A21B77DF059A9772FDC | SHA256:17D0A875FA315B8E99444C3A291791B5523B49461A4803E761E7032FB8520057 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\au.sydney.ovpn.com.ovpn | text | |
MD5:B95CB313D45E0F28BDEA5D62C28195B1 | SHA256:868AA59165E958C6B8C7BD819E94381938F5E9F65909C64D884949023E51D011 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\ca.ovpn.com.ovpn | text | |
MD5:278A1B37942DCF35AF63ACEB4FD7A014 | SHA256:D0E5DBA3B86940C2B33C7F6025F8E65AED5A937737B3B78874C16D3244801C73 | |||
| 7220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7220.19074\Trusted HWID Spoofer - Made By Trusted Cheat's\.ovpn file's\TCP\ch.zurich.ovpn.com.ovpn | text | |
MD5:95B0944A49AC47E6F48563DF6B87D773 | SHA256:F65A62472CAABEE41C7F8AE891754BC5AE2EAA4CFC844356785D3B837D7B16BD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7700 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7700 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5984 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7700 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7700 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |