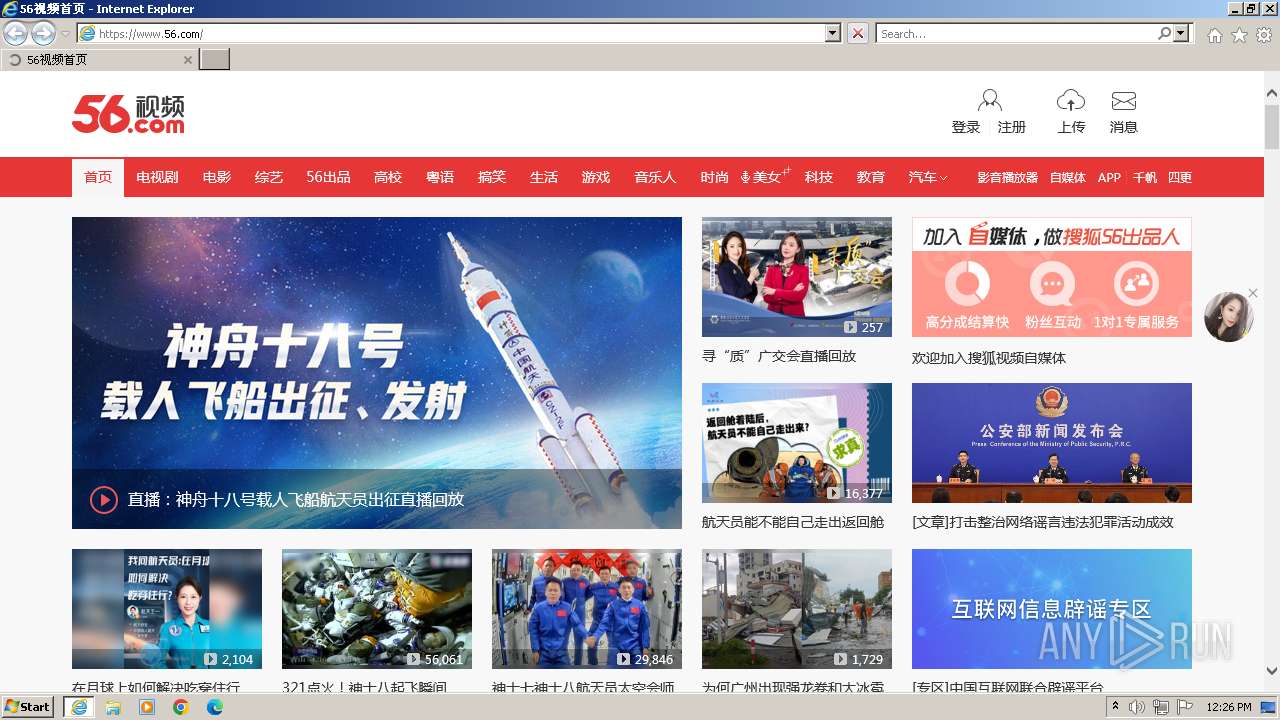
| URL: | https://hqq.ac/ |
| Full analysis: | https://app.any.run/tasks/8b74dfba-a9ec-4c6c-af0a-cf5afb7c4a5f |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2024, 11:25:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BE7CA59DE4270E11247BD9ACA1325946 |
| SHA1: | 8AE43D53AECC816B2C7BD8B03E7FFB0C5131CD50 |
| SHA256: | A6E7135F5552180CB8FA5DA697ADE983DDD7C04C10BC2D54D332D15ADDEFD48B |
| SSDEEP: | 3:N8ot:2ot |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 2028)
Checks supported languages
- wmpnscfg.exe (PID: 2028)
Application launched itself
- iexplore.exe (PID: 3976)
Manual execution by a user
- wmpnscfg.exe (PID: 2028)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2028 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2368 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Version: 32,0,0,453 Modules
| |||||||||||||||
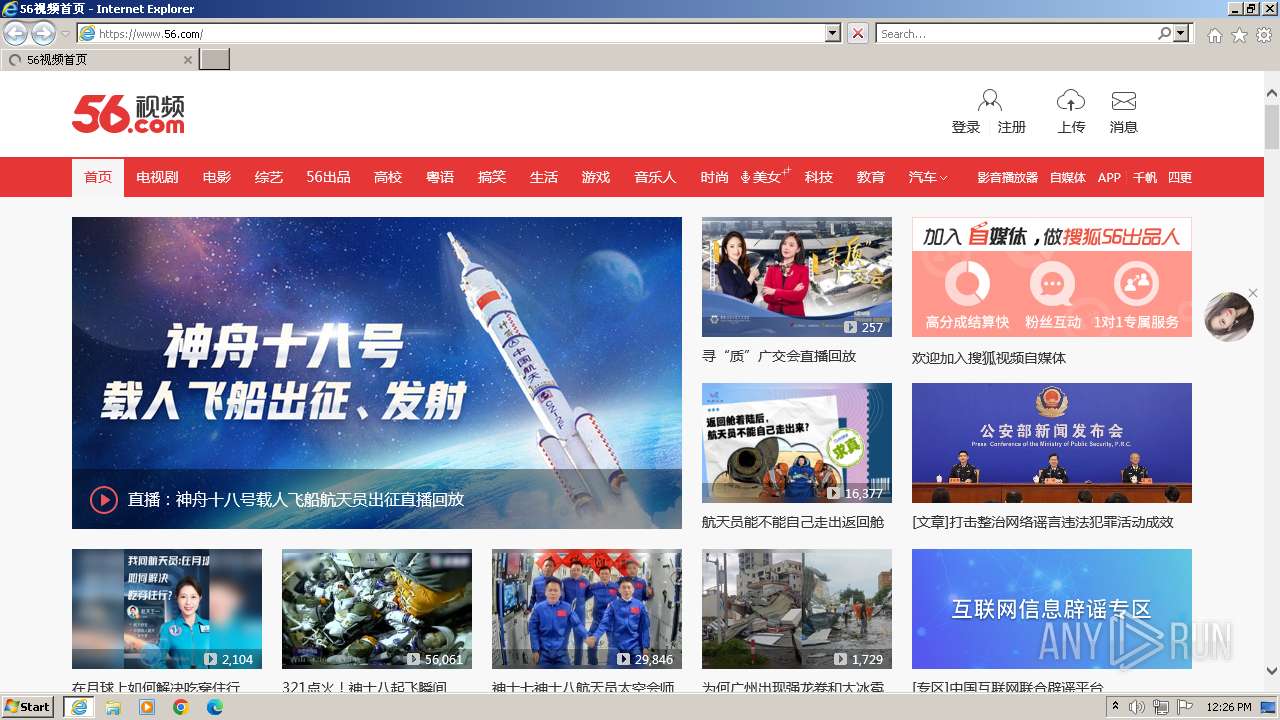
| 3976 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://hqq.ac/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4036 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3976 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
29 079
Read events
28 946
Write events
99
Delete events
34
Modification events
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31103326 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31103326 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
73
Text files
428
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8F8712BCE78D28F9C5E3E950CD93EADA_0BA2D7600D4338A6D46D0C3E7872B449 | binary | |
MD5:E80755608E95831E3DF44E0C3AE0AA84 | SHA256:559D3127D613C4CBE12838158B6C79C68F3E199B127A512B019BC2AF6559BC9B | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8F8712BCE78D28F9C5E3E950CD93EADA_88AC4858D0564F7F097CDB0BBCC4E4A9 | binary | |
MD5:07C51AAC47724FFDC04BD0EC3C32066C | SHA256:80356649754648E9859845ED0937097B16AD5F9CB0DD2102E7A84A79D72DA504 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\pagehook[1].js | binary | |
MD5:40BCC358A0D23D0BA645E11EF42A5ACA | SHA256:323D631EA846DE7CAD016B909A93ADFE4F66ABCA531263716ACCD41C2E1818DD | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:13C0200DAE16CBA7A36BE85513E452E2 | SHA256:1B3C6F378B0BD513B748E6C9B9DC890FA11BBDAE4E6F54C5B24E1D63CF104228 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\config[1].js | html | |
MD5:FFF683EB0D1DC9AB2C4B95AE19B32E5D | SHA256:332D49BB3DFD0B8D28960FBA3BDA771B598E2B48A444846B96930B353CF9A556 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:F32C01527C20AC850512733F0EFE18DC | SHA256:DF16150A1EEF6E4C84E64E711D991AAE39BA3D720334F1E49A75544827CA4A85 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FVEVT0L7.htm | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:94483185C90642361FF352293EDF4C3D | SHA256:DB3649D7DE6DD0EEB28CFABE04D95353C2184C8348910BDDDD7DCB2EB956288A | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2111EAA896E7D8FF588035032E8C9338 | SHA256:CD8539202461982E2E3EEA829A8FE3AF9534DB4FFDF55AC862753F66C42255D8 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_88AC4858D0564F7F097CDB0BBCC4E4A9 | binary | |
MD5:5C23A29E12675AB4A9725B4DBD320C86 | SHA256:D9D13F5D56B385DB0024A878DAE041FB0D3BC1588EBEB67D5D2C793DA0B991A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
91
TCP/UDP connections
206
DNS requests
63
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4036 | iexplore.exe | GET | 304 | 23.65.124.16:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fdb53f965dd08005 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 304 | 23.65.124.16:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?30bfcba95dc85498 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 163.181.92.233:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 163.181.92.233:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEA%2FTTmkOYBcvKv8sd6BrFuM%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 304 | 23.65.124.16:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b7451e9b8676f0e | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 304 | 23.65.124.16:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5fc92888093a54f7 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 163.181.92.233:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAJ%2BYV%2FN5W2THg4NuR8pUi8%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 174.35.118.62:80 | http://i3.itc.cn/20170306/36ad_498fd78c_b48c_3577_c059_654cf2be72d0_1.gif | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4036 | iexplore.exe | 190.115.19.71:443 | hqq.ac | DDOS-GUARD CORP. | BZ | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4036 | iexplore.exe | 23.65.124.16:80 | ctldl.windowsupdate.com | Akamai International B.V. | IN | unknown |
4036 | iexplore.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
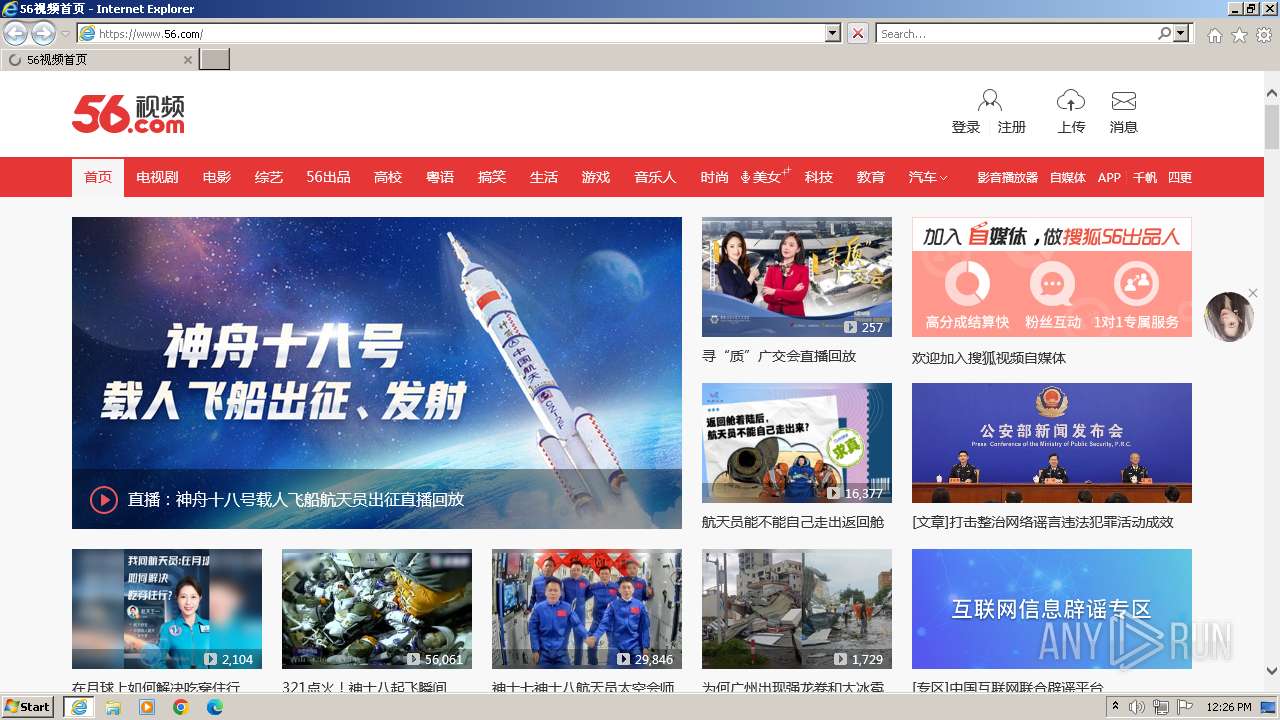
4036 | iexplore.exe | 13.75.75.123:443 | www.56.com | MICROSOFT-CORP-MSN-AS-BLOCK | HK | unknown |
4036 | iexplore.exe | 163.181.92.233:80 | ocsp.dcocsp.cn | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
3976 | iexplore.exe | 23.65.124.99:443 | www.bing.com | Akamai International B.V. | IN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hqq.ac |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.56.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.dcocsp.cn |
| whitelisted |
s2.56img.com |
| whitelisted |
css.tv.itc.cn |
| whitelisted |
js.tv.itc.cn |
| unknown |