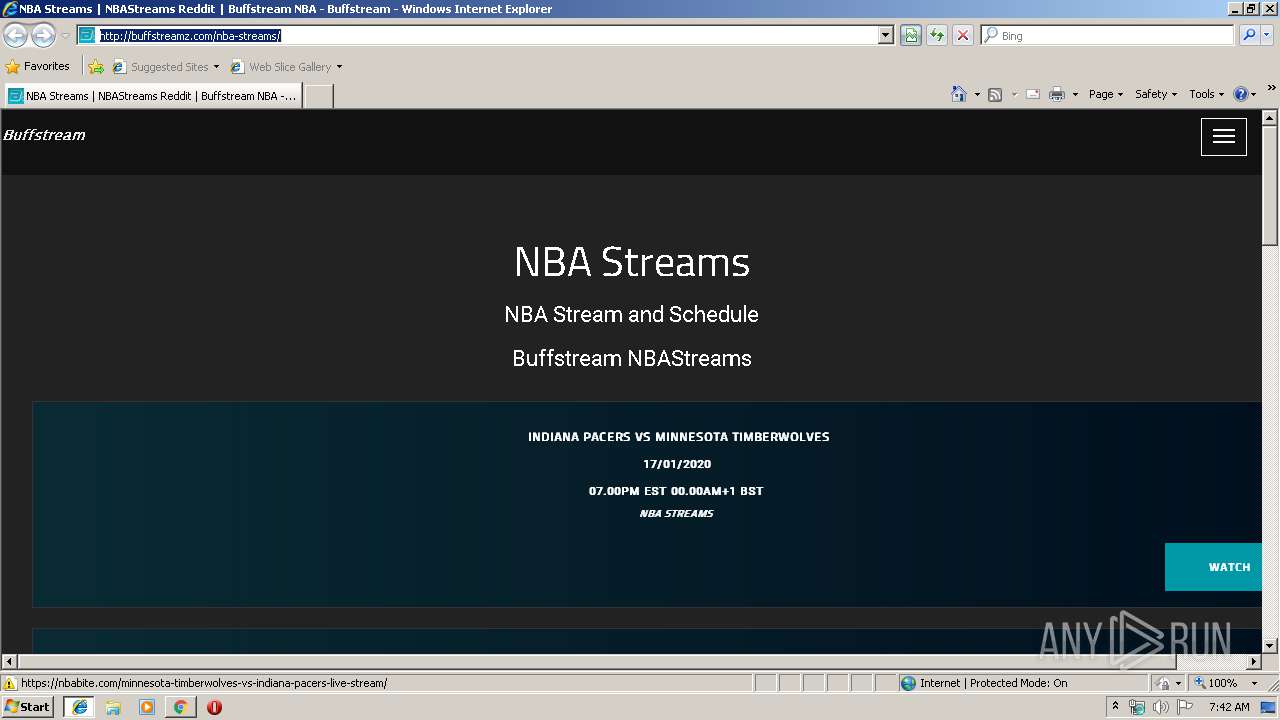
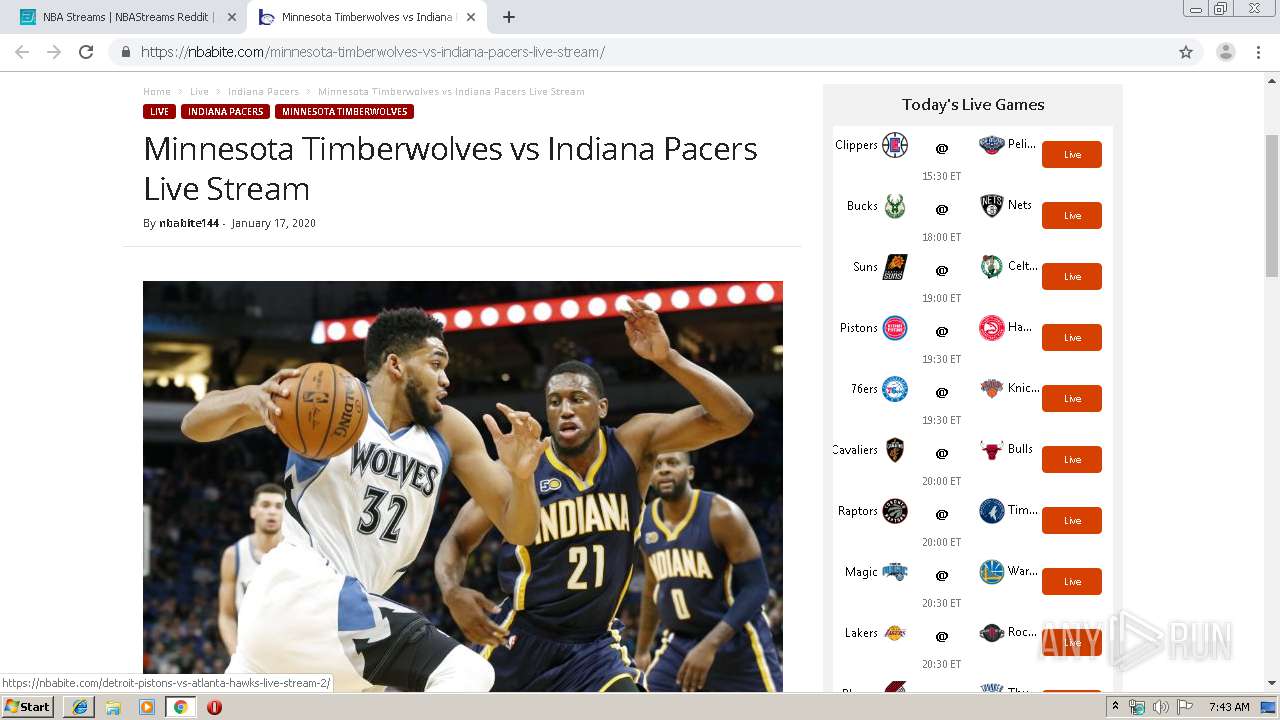
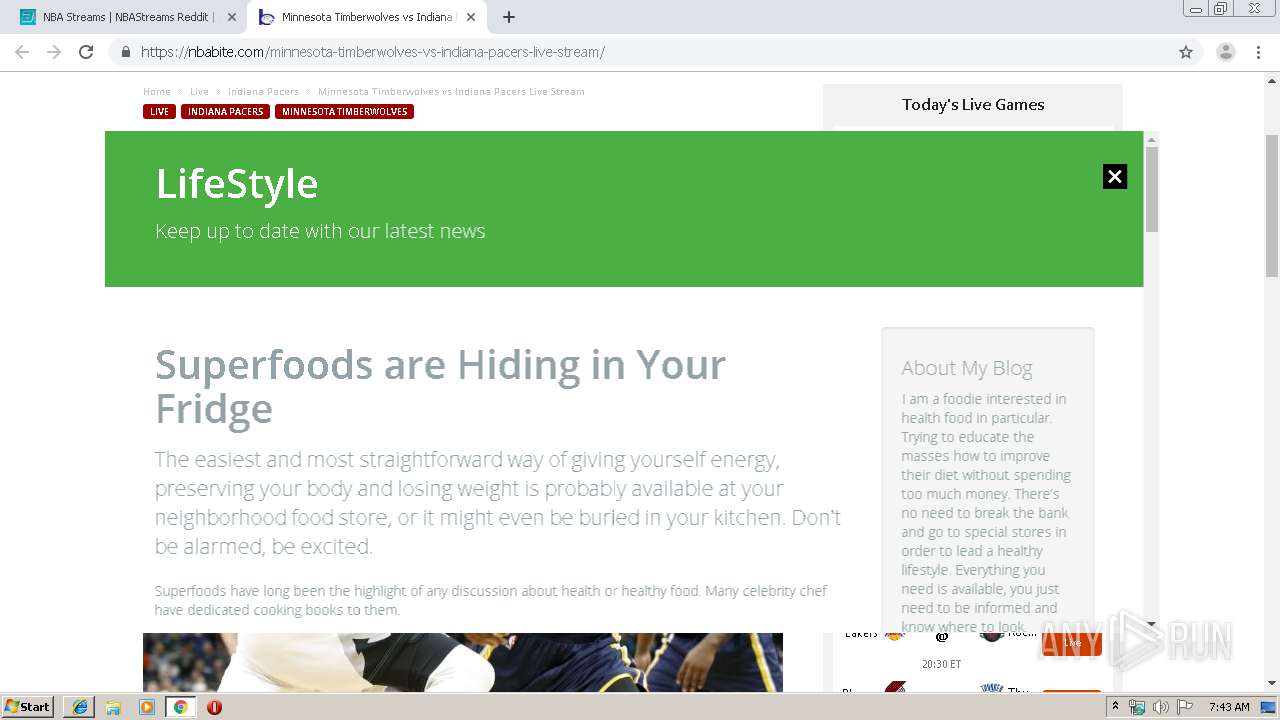
| URL: | http://buffstreamz.com/nba-streams |
| Full analysis: | https://app.any.run/tasks/40f9fe8f-51dd-4a20-9d31-b9a9fc21f2ca |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2020, 07:42:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 93699A6CAD32B997708E28D8341E64C9 |
| SHA1: | 69D8BC49C101FF610E0AFB4BBF9F9543DB3D05F5 |
| SHA256: | A6E3B2B6F1BE0F318DBBA1B2651BE4FD58C954DC9E8D6D3105F8ACF78AC09EE9 |
| SSDEEP: | 3:N1KcWKxhKLBVEIW:Cc/xhKVVEIW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 4084)
INFO
Application launched itself
- iexplore.exe (PID: 3332)
- chrome.exe (PID: 4084)
Reads settings of System Certificates
- iexplore.exe (PID: 1764)
- chrome.exe (PID: 492)
Creates files in the user directory
- iexplore.exe (PID: 3332)
- iexplore.exe (PID: 1764)
- chrome.exe (PID: 4084)
Changes internet zones settings
- iexplore.exe (PID: 3332)
Reads Internet Cache Settings
- iexplore.exe (PID: 1764)
Manual execution by user
- chrome.exe (PID: 4084)
Reads the hosts file
- chrome.exe (PID: 4084)
- chrome.exe (PID: 492)
Reads internet explorer settings
- iexplore.exe (PID: 1764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
47
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11978791203925379177 --renderer-client-id=44 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=764 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3192810817115830659 --mojo-platform-channel-handle=3700 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=3439276534819420282 --mojo-platform-channel-handle=4048 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3071412528568402752 --mojo-platform-channel-handle=3312 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13997455409422090407 --mojo-platform-channel-handle=1616 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=797875891629847894 --mojo-platform-channel-handle=2408 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17497224372045797469 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6547531253693779388 --mojo-platform-channel-handle=4064 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15298260996530809298 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3676 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,8681117437135470185,6936422518938339660,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14752385082726193699 --mojo-platform-channel-handle=2520 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 135
Read events
944
Write events
183
Delete events
8
Modification events
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {1943643D-39C6-11EA-AB41-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E40701000600120007002A0027008600 | |||
Executable files
0
Suspicious files
91
Text files
425
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3332 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U4NP2E50\custom.min[1].css | text | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
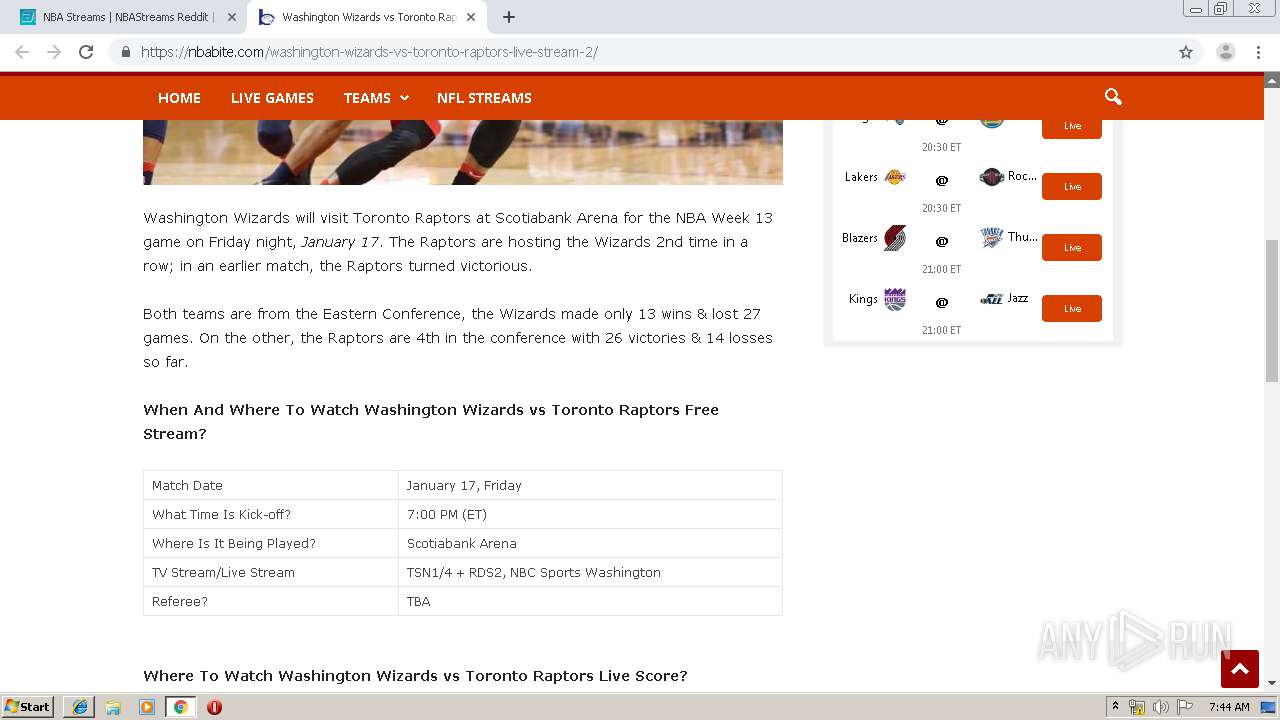
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\6O2BSNHX\nba-streams[1].htm | html | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@buffstreamz[1].txt | text | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U4NP2E50\style[1].css | text | |
MD5:— | SHA256:— | |||
| 1764 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\HDUHJ4F4\css[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
79
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/basketball.css | US | text | 2.03 Kb | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/custom.min.css | US | text | 932 b | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/custom.min.css | US | text | 932 b | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/js/tooltipjs.js | US | text | 74 b | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/basketball.css | US | text | 2.03 Kb | malicious |
1764 | iexplore.exe | GET | 404 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/BebasNeue-webfont.eot? | US | html | 222 b | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/nba-streams/ | US | html | 2.85 Kb | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/style.css | US | text | 3.21 Kb | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/assets/css/basketball.css | US | text | 2.03 Kb | malicious |
1764 | iexplore.exe | GET | 200 | 104.18.38.160:80 | http://buffstreamz.com/nba-streams/ | US | html | 2.85 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3332 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1764 | iexplore.exe | 104.18.38.160:80 | buffstreamz.com | Cloudflare Inc | US | unknown |
1764 | iexplore.exe | 216.58.205.234:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
1764 | iexplore.exe | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1764 | iexplore.exe | 216.58.207.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1764 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
1764 | iexplore.exe | 104.17.65.4:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
1764 | iexplore.exe | 23.210.248.44:80 | s7.addthis.com | Akamai International B.V. | NL | whitelisted |
3332 | iexplore.exe | 104.18.38.160:80 | buffstreamz.com | Cloudflare Inc | US | unknown |
492 | chrome.exe | 172.217.22.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
buffstreamz.com |
| malicious |
ajax.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |