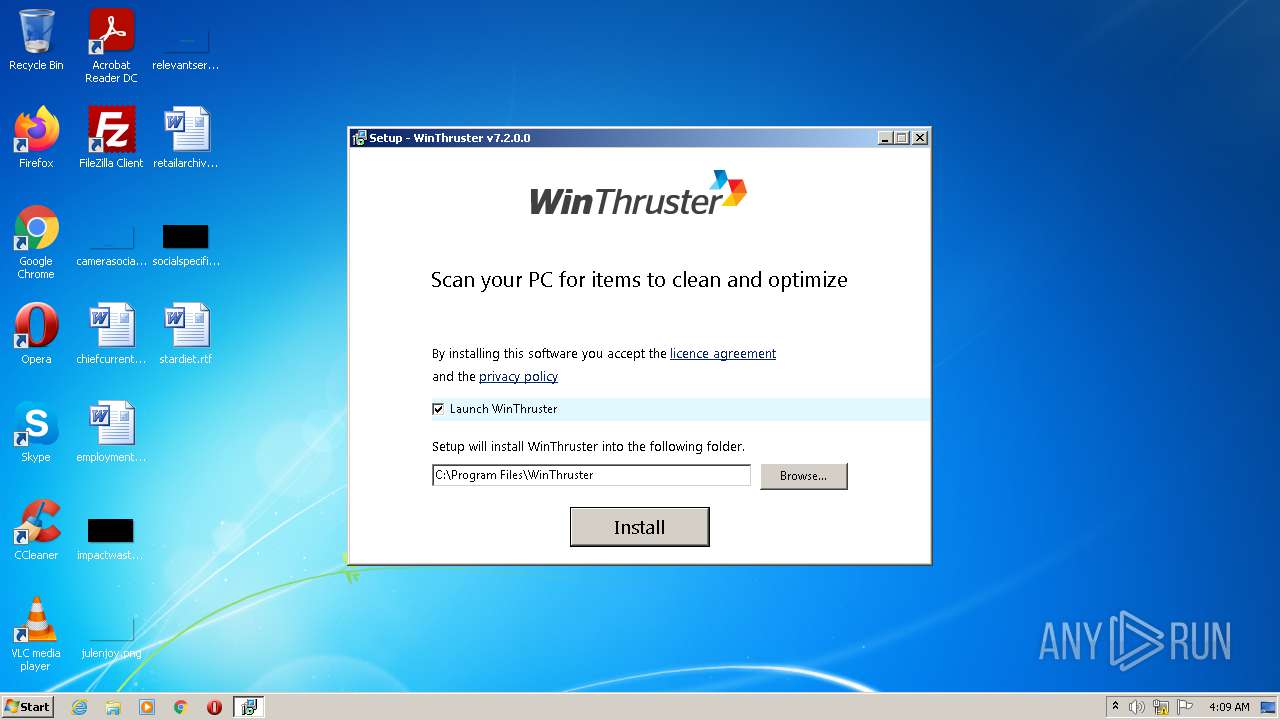
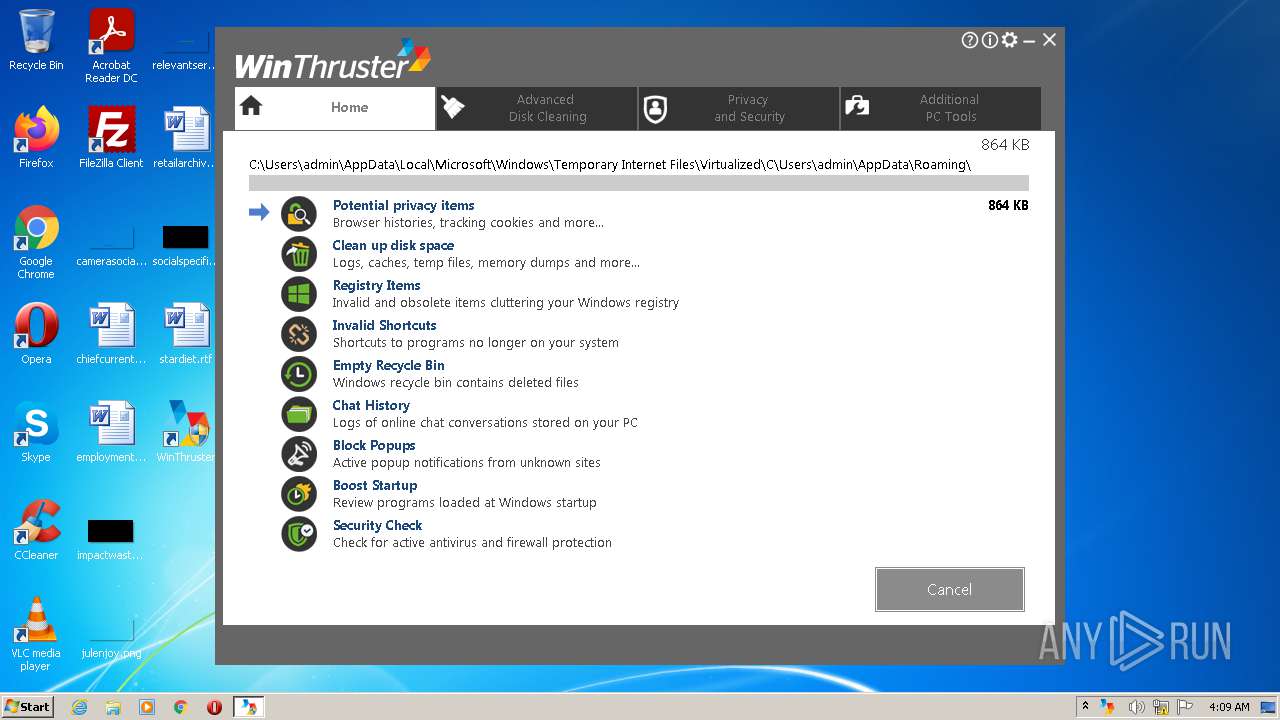
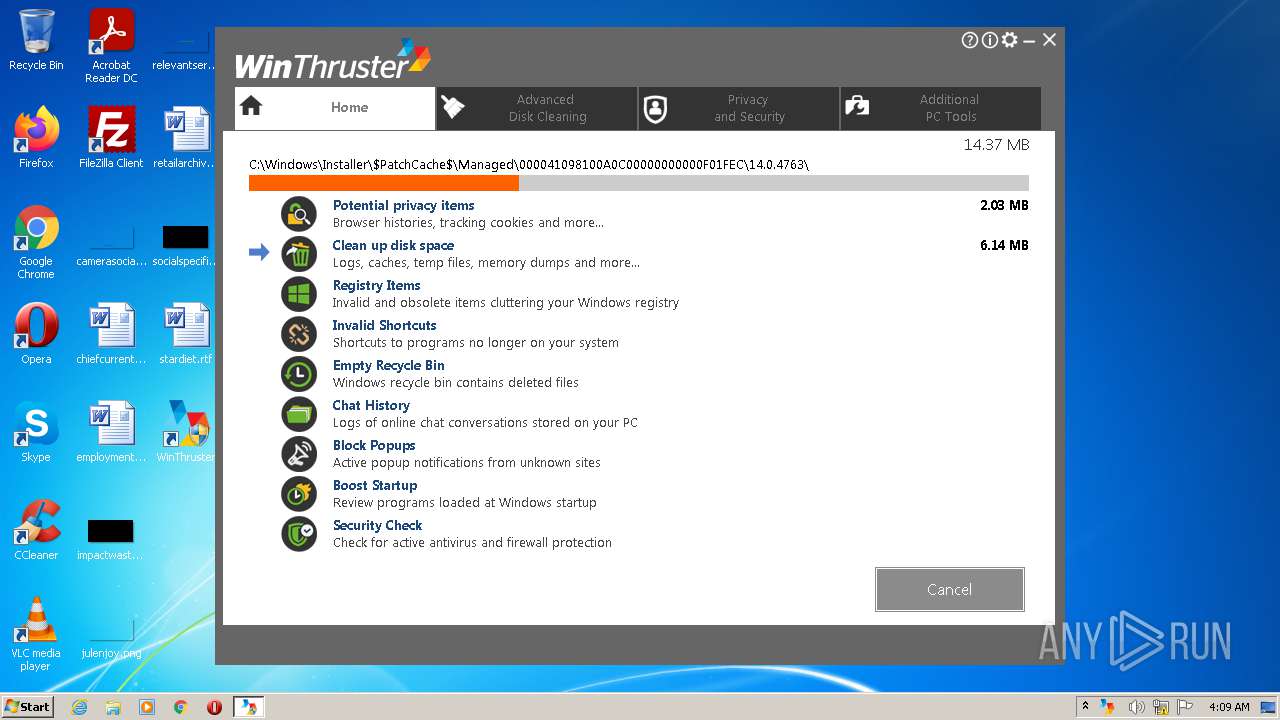
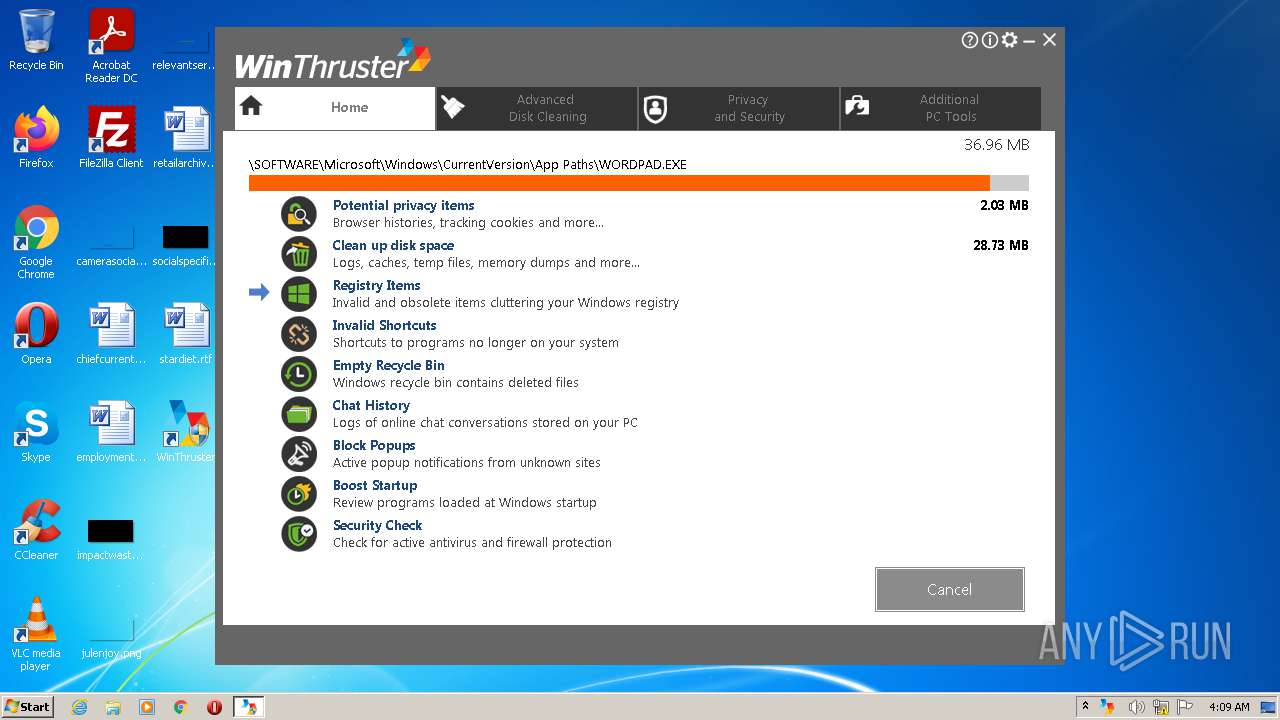
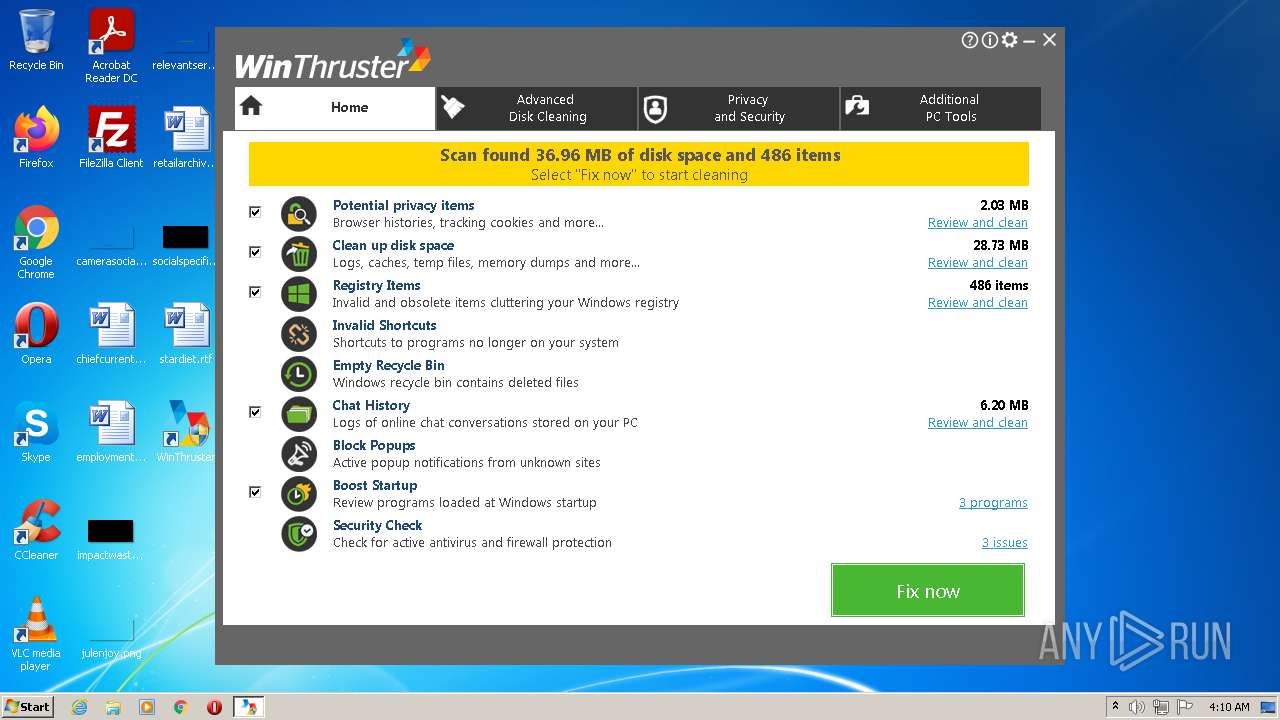
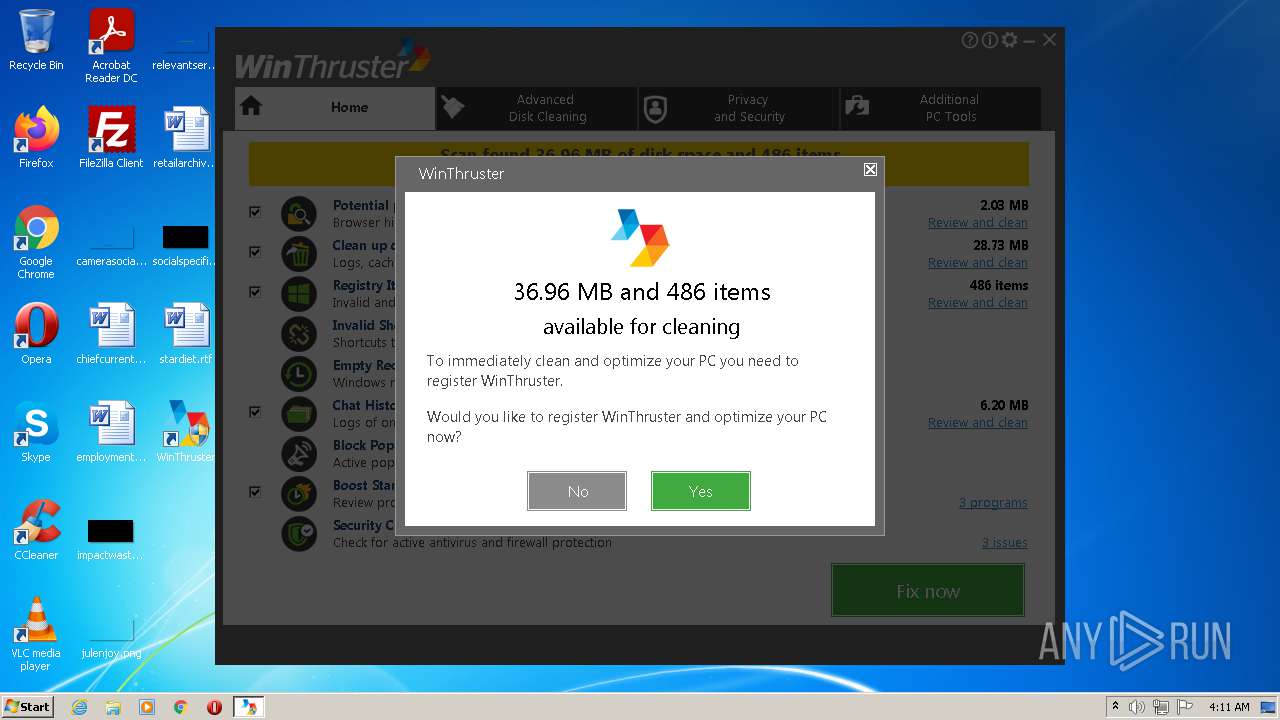
| File name: | Setup_WinThruster_2021.exe |
| Full analysis: | https://app.any.run/tasks/dd17ed70-0214-44d9-b841-eb8173b15a9f |
| Verdict: | Malicious activity |
| Analysis date: | September 25, 2021, 03:08:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D07CCEA4F401887FF1106C08C42E8110 |
| SHA1: | 79510087EE93E64CBBCB930EF6E61E620D619539 |
| SHA256: | A6936625E74D09E2118A9B0A475BF9391495F047F046F7B63CFC319ADEBBC25F |
| SSDEEP: | 98304:DEU2EBrTRE1MVZeEEsAD6bm2DH0zjIQ1cMYo8C4EsgB:AsHRoMVENfgVMR8ztQ |
MALICIOUS
Drops executable file immediately after starts
- Setup_WinThruster_2021.exe (PID: 3932)
- Setup_WinThruster_2021.exe (PID: 1020)
- chrome.exe (PID: 5368)
Application was dropped or rewritten from another process
- WinThruster.exe (PID: 1784)
- WTNotifications.exe (PID: 488)
Steals credentials from Web Browsers
- WTNotifications.exe (PID: 488)
- WinThruster.exe (PID: 1784)
Actions looks like stealing of personal data
- WinThruster.exe (PID: 1784)
- WTNotifications.exe (PID: 488)
Loads dropped or rewritten executable
- WinThruster.exe (PID: 1784)
- WTNotifications.exe (PID: 488)
Uses Task Scheduler to autorun other applications
- WinThruster.exe (PID: 1784)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3988)
SUSPICIOUS
Checks supported languages
- Setup_WinThruster_2021.exe (PID: 3932)
- Setup_WinThruster_2021.tmp (PID: 512)
- Setup_WinThruster_2021.exe (PID: 1020)
- Setup_WinThruster_2021.tmp (PID: 2960)
- WTNotifications.exe (PID: 488)
- WinThruster.exe (PID: 1784)
Reads the computer name
- Setup_WinThruster_2021.tmp (PID: 512)
- Setup_WinThruster_2021.tmp (PID: 2960)
- WTNotifications.exe (PID: 488)
- WinThruster.exe (PID: 1784)
Executable content was dropped or overwritten
- Setup_WinThruster_2021.exe (PID: 3932)
- Setup_WinThruster_2021.exe (PID: 1020)
- Setup_WinThruster_2021.tmp (PID: 2960)
- chrome.exe (PID: 5368)
Reads Windows owner or organization settings
- Setup_WinThruster_2021.tmp (PID: 2960)
Reads the Windows organization settings
- Setup_WinThruster_2021.tmp (PID: 2960)
Creates a directory in Program Files
- Setup_WinThruster_2021.tmp (PID: 2960)
Drops a file that was compiled in debug mode
- Setup_WinThruster_2021.tmp (PID: 2960)
- chrome.exe (PID: 5368)
Starts Internet Explorer
- WinThruster.exe (PID: 1784)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3544)
- iexplore.exe (PID: 1912)
Reads CPU info
- WinThruster.exe (PID: 1784)
Creates files in the program directory
- WinThruster.exe (PID: 1784)
Searches for installed software
- WTNotifications.exe (PID: 488)
- WinThruster.exe (PID: 1784)
Creates files in the user directory
- WinThruster.exe (PID: 1784)
Reads the cookies of Mozilla Firefox
- WinThruster.exe (PID: 1784)
Reads the cookies of Google Chrome
- WinThruster.exe (PID: 1784)
Check for Java to be installed
- WinThruster.exe (PID: 1784)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1828)
Creates files in the Windows directory
- WinThruster.exe (PID: 1784)
INFO
Application was dropped or rewritten from another process
- Setup_WinThruster_2021.tmp (PID: 512)
- Setup_WinThruster_2021.tmp (PID: 2960)
Creates files in the program directory
- Setup_WinThruster_2021.tmp (PID: 2960)
Creates a software uninstall entry
- Setup_WinThruster_2021.tmp (PID: 2960)
Dropped object may contain Bitcoin addresses
- Setup_WinThruster_2021.tmp (PID: 2960)
Checks supported languages
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 3544)
- schtasks.exe (PID: 3988)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2316)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 3732)
- chrome.exe (PID: 1876)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 3640)
- chrome.exe (PID: 708)
- chrome.exe (PID: 1884)
- chrome.exe (PID: 1984)
- chrome.exe (PID: 3892)
- chrome.exe (PID: 1744)
- chrome.exe (PID: 2560)
- chrome.exe (PID: 1820)
- chrome.exe (PID: 2952)
- chrome.exe (PID: 1672)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 2016)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 1660)
- chrome.exe (PID: 3080)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 544)
- chrome.exe (PID: 2644)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3576)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 3356)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3532)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 1912)
- chrome.exe (PID: 3880)
- WINWORD.EXE (PID: 240)
- chrome.exe (PID: 1556)
- chrome.exe (PID: 1616)
- chrome.exe (PID: 3120)
- chrome.exe (PID: 1816)
- chrome.exe (PID: 2528)
- chrome.exe (PID: 2952)
- chrome.exe (PID: 1240)
- chrome.exe (PID: 2816)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 760)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 2008)
- chrome.exe (PID: 3004)
- chrome.exe (PID: 3656)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 240)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2976)
- chrome.exe (PID: 3556)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 3640)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 1404)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 1608)
- chrome.exe (PID: 1876)
- chrome.exe (PID: 3784)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 3576)
- chrome.exe (PID: 1788)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 2832)
- chrome.exe (PID: 276)
- chrome.exe (PID: 1636)
- chrome.exe (PID: 2200)
- chrome.exe (PID: 2864)
- chrome.exe (PID: 3564)
- chrome.exe (PID: 3040)
- chrome.exe (PID: 1388)
- chrome.exe (PID: 2012)
- chrome.exe (PID: 324)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 912)
- chrome.exe (PID: 3740)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 3416)
- chrome.exe (PID: 3960)
- chrome.exe (PID: 1484)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 2864)
- chrome.exe (PID: 3184)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 3964)
- chrome.exe (PID: 3236)
- chrome.exe (PID: 1960)
- chrome.exe (PID: 3844)
- chrome.exe (PID: 420)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 2124)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 912)
- chrome.exe (PID: 2392)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 3852)
- chrome.exe (PID: 3260)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 2740)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 2416)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 2644)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 3600)
- chrome.exe (PID: 2620)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 876)
- chrome.exe (PID: 1552)
- chrome.exe (PID: 5740)
- chrome.exe (PID: 5076)
- chrome.exe (PID: 4524)
- chrome.exe (PID: 4216)
- chrome.exe (PID: 5368)
- chrome.exe (PID: 5784)
- chrome.exe (PID: 6084)
- chrome.exe (PID: 4352)
- chrome.exe (PID: 4696)
- chrome.exe (PID: 2024)
- chrome.exe (PID: 5788)
- chrome.exe (PID: 3172)
Changes internet zones settings
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 3976)
Reads the computer name
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 3544)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 3640)
- schtasks.exe (PID: 3988)
- chrome.exe (PID: 3080)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 3356)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 1912)
- WINWORD.EXE (PID: 240)
- chrome.exe (PID: 1556)
- chrome.exe (PID: 1816)
- chrome.exe (PID: 1616)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 3004)
- chrome.exe (PID: 3640)
- chrome.exe (PID: 912)
- chrome.exe (PID: 324)
- chrome.exe (PID: 2740)
- chrome.exe (PID: 4216)
Changes settings of System certificates
- iexplore.exe (PID: 3544)
Reads settings of System Certificates
- iexplore.exe (PID: 3544)
- iexplore.exe (PID: 2964)
- chrome.exe (PID: 2384)
- iexplore.exe (PID: 1912)
- chrome.exe (PID: 1556)
Reads the date of Windows installation
- iexplore.exe (PID: 2964)
- chrome.exe (PID: 3548)
- iexplore.exe (PID: 3976)
- chrome.exe (PID: 324)
Checks Windows Trust Settings
- iexplore.exe (PID: 3544)
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 1912)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3544)
Reads internet explorer settings
- iexplore.exe (PID: 3544)
- iexplore.exe (PID: 1912)
Creates files in the user directory
- iexplore.exe (PID: 3544)
- iexplore.exe (PID: 1912)
- WINWORD.EXE (PID: 240)
Application launched itself
- iexplore.exe (PID: 2964)
- chrome.exe (PID: 1828)
- iexplore.exe (PID: 3976)
- chrome.exe (PID: 1556)
Manual execution by user
- chrome.exe (PID: 1828)
- WINWORD.EXE (PID: 240)
- chrome.exe (PID: 1556)
Reads the hosts file
- chrome.exe (PID: 2384)
- chrome.exe (PID: 1828)
- chrome.exe (PID: 1556)
- chrome.exe (PID: 1816)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| ProductVersion: | 7.2.0.0 |
|---|---|
| ProductName: | WinThruster |
| OriginalFileName: | |
| LegalCopyright: | Solvusoft |
| FileVersion: | 7.2.0.0 |
| FileDescription: | WinThruster |
| CompanyName: | Solvusoft |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 7.2.0.0 |
| FileVersionNumber: | 7.2.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | 6 |
| OSVersion: | 6 |
| EntryPoint: | 0xb5eec |
| UninitializedDataSize: | - |
| InitializedDataSize: | 38400 |
| CodeSize: | 741376 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 2020:05:21 07:56:23+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 21-May-2020 05:56:23 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Solvusoft |
| FileDescription: | WinThruster |
| FileVersion: | 7.2.0.0 |
| LegalCopyright: | Solvusoft |
| OriginalFileName: | - |
| ProductName: | WinThruster |
| ProductVersion: | 7.2.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 21-May-2020 05:56:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000B3604 | 0x000B3800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35433 |
.itext | 0x000B5000 | 0x00001684 | 0x00001800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.9709 |
.data | 0x000B7000 | 0x000037A4 | 0x00003800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.04216 |
.bss | 0x000BB000 | 0x00006DA0 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x000C2000 | 0x00000F36 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 0x000C3000 | 0x000001A4 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 0x000C4000 | 0x0000009A | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 0x000C5000 | 0x00000018 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x000C6000 | 0x0000005D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 0x000C7000 | 0x00004800 | 0x00004800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.42505 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18295 | 1830 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4086 | 3.16547 | 864 | UNKNOWN | UNKNOWN | RT_STRING |
4087 | 3.40938 | 608 | UNKNOWN | UNKNOWN | RT_STRING |
4088 | 3.31153 | 1116 | UNKNOWN | UNKNOWN | RT_STRING |
4089 | 3.33977 | 1036 | UNKNOWN | UNKNOWN | RT_STRING |
4090 | 3.36723 | 724 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.33978 | 184 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x000BE63C |
__dbk_fcall_wrapper | 2 | 0x0000D0A0 |
TMethodImplementationIntercept | 3 | 0x00054058 |
Total processes
186
Monitored processes
138
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\retailarchives.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,10165042612298773380,2796649154448090753,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4008 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,10165042612298773380,2796649154448090753,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,10165042612298773380,2796649154448090753,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=5148 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,10165042612298773380,2796649154448090753,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=66 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4532 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 488 | "C:\Program Files\WinThruster\WTNotifications.exe" | C:\Program Files\WinThruster\WTNotifications.exe | Setup_WinThruster_2021.tmp | ||||||||||||
User: admin Company: Solvusoft Integrity Level: HIGH Description: WinThruster automatic scan and notifications Exit code: 0 Version: 7.2.0.0 Modules
| |||||||||||||||
| 512 | "C:\Users\admin\AppData\Local\Temp\is-7LFTU.tmp\Setup_WinThruster_2021.tmp" /SL5="$20138,5031305,780800,C:\Users\admin\AppData\Local\Temp\Setup_WinThruster_2021.exe" | C:\Users\admin\AppData\Local\Temp\is-7LFTU.tmp\Setup_WinThruster_2021.tmp | — | Setup_WinThruster_2021.exe | |||||||||||
User: admin Company: Solvusoft Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12459003317585271575,3155612108344469171,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3380 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1028,12459003317585271575,3155612108344469171,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2932 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,10165042612298773380,2796649154448090753,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3544 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
75 128
Read events
74 197
Write events
773
Delete events
158
Modification events
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 900B000045ECC8B8BAB1D701 | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: EB77589D6D33D8466B51950607035498EBF627A0C372D99544ACF91832390244 | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\WinThruster\WinThruster.exe | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 6D3A1952A65E4620ED98CB3D5FCAB52BA95D963C61DBA4B3FDA63F244FFE3796 | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\WinThruster |
| Operation: | write | Name: | Language |
Value: 1 | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\WinThruster |
| Operation: | write | Name: | InstallerName |
Value: C:\Users\admin\AppData\Local\Temp\Setup_WinThruster_2021.exe | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\WinThruster |
| Operation: | write | Name: | BuildID |
Value: WINTHRUSTER | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\WinThruster |
| Operation: | write | Name: | UpgradeID |
Value: BZDV_WINTHRUSTER | |||
| (PID) Process: | (2960) Setup_WinThruster_2021.tmp | Key: | HKEY_CURRENT_USER\Software\WinThruster |
| Operation: | write | Name: | Cv |
Value: Jan2021 | |||
Executable files
11
Suspicious files
334
Text files
548
Unknown types
140
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1020 | Setup_WinThruster_2021.exe | C:\Users\admin\AppData\Local\Temp\is-FO7MS.tmp\Setup_WinThruster_2021.tmp | executable | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\is-PQ4JE.tmp | text | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\is-MIRUQ.tmp | text | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\Dutch.ini | text | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\is-9KC6N.tmp | executable | |
MD5:— | SHA256:— | |||
| 3932 | Setup_WinThruster_2021.exe | C:\Users\admin\AppData\Local\Temp\is-7LFTU.tmp\Setup_WinThruster_2021.tmp | executable | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\is-IBAE9.tmp | text | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\is-DRBM2.tmp | executable | |
MD5:— | SHA256:— | |||
| 2960 | Setup_WinThruster_2021.tmp | C:\Program Files\WinThruster\WTNotifications.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
567
DNS requests
343
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3544 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3544 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
3544 | iexplore.exe | GET | 200 | 13.32.23.206:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3544 | iexplore.exe | GET | 200 | 13.32.23.215:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3544 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3544 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3544 | iexplore.exe | GET | 200 | 92.123.195.34:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | unknown | der | 1.16 Kb | whitelisted |
3544 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
3544 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuqL92L3tjkN67RNFF%2FEdvT6NEzAQUwBKyKHRoRmfpcCV0GgBFWwZ9XEQCEAeqcbjrVkNsdRcGhAqQnYI%3D | US | der | 471 b | whitelisted |
3544 | iexplore.exe | GET | 200 | 52.222.206.67:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3544 | iexplore.exe | 104.111.233.108:443 | www.solvusoft.com | Akamai International B.V. | NL | suspicious |
1784 | WinThruster.exe | 116.203.251.147:443 | subscriptions.avqtools.com | 334,Udyog Vihar | IN | suspicious |
3544 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3544 | iexplore.exe | 104.212.67.92:443 | www.clarity.ms | Microsoft Corporation | US | unknown |
3544 | iexplore.exe | 142.251.36.168:443 | www.googletagmanager.com | Google Inc. | US | unknown |
3544 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3544 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3544 | iexplore.exe | 13.32.23.215:80 | o.ss2.us | Amazon.com, Inc. | US | malicious |
3544 | iexplore.exe | 13.225.78.10:443 | cdn.ywxi.net | — | US | suspicious |
3544 | iexplore.exe | 52.222.206.67:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
subscriptions.avqtools.com |
| suspicious |
stats.avqtools.com |
| suspicious |
www.solvusoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
apis.google.com |
| whitelisted |
cdn.ywxi.net |
| shared |
www.googletagmanager.com |
| whitelisted |
www.clarity.ms |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3544 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3544 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2384 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |