| File name: | Victoria537.zip |
| Full analysis: | https://app.any.run/tasks/b6d482b4-dadc-4426-94ba-0c219d9fe087 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 16:33:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6F1223C60CAF4053D5C68DCD62302AD8 |
| SHA1: | B84319FCEAD5F9226F23A3E5BDDB58A261AC7B9C |
| SHA256: | A66B7869D59BBF90B5994332BAC57BCBC0B377CEE9F0C59C078795EA7B4C99D1 |
| SSDEEP: | 49152:vOOdFAN5MFWWuHNc4RPdV5JpE6t86mIVB2z:vR36rWuHNc4XV5Jpi/qB2z |
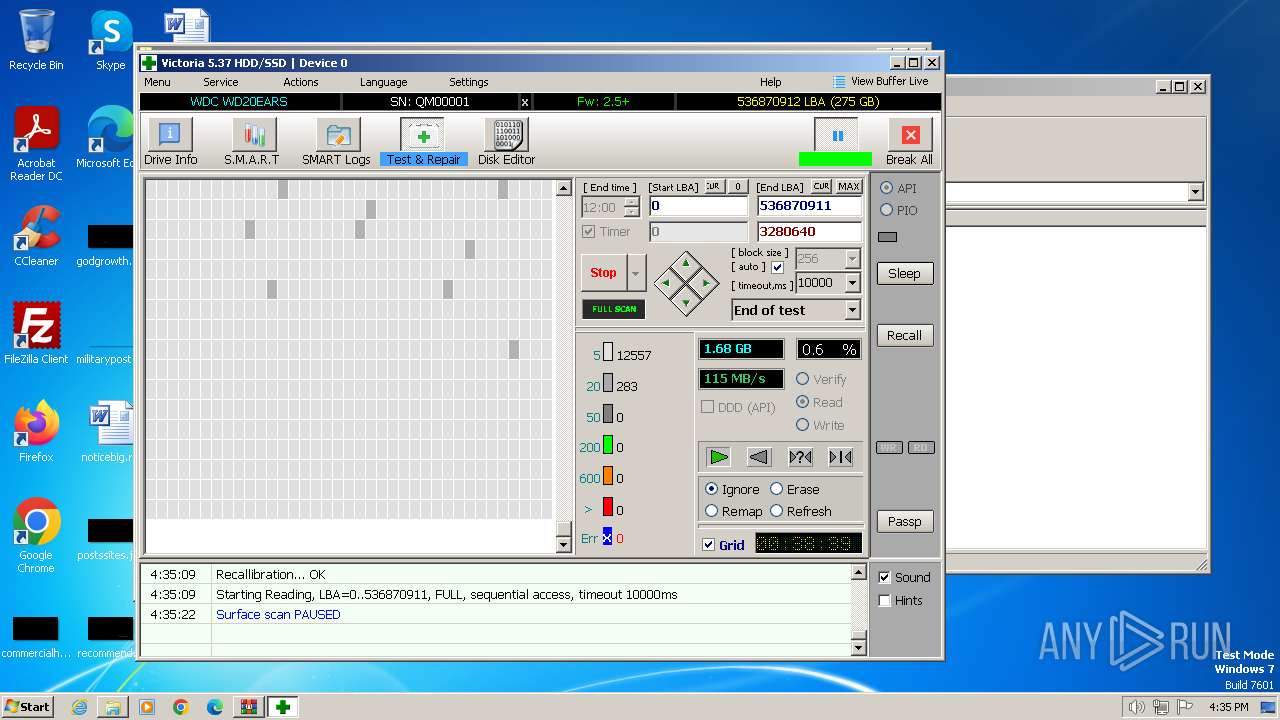
MALICIOUS
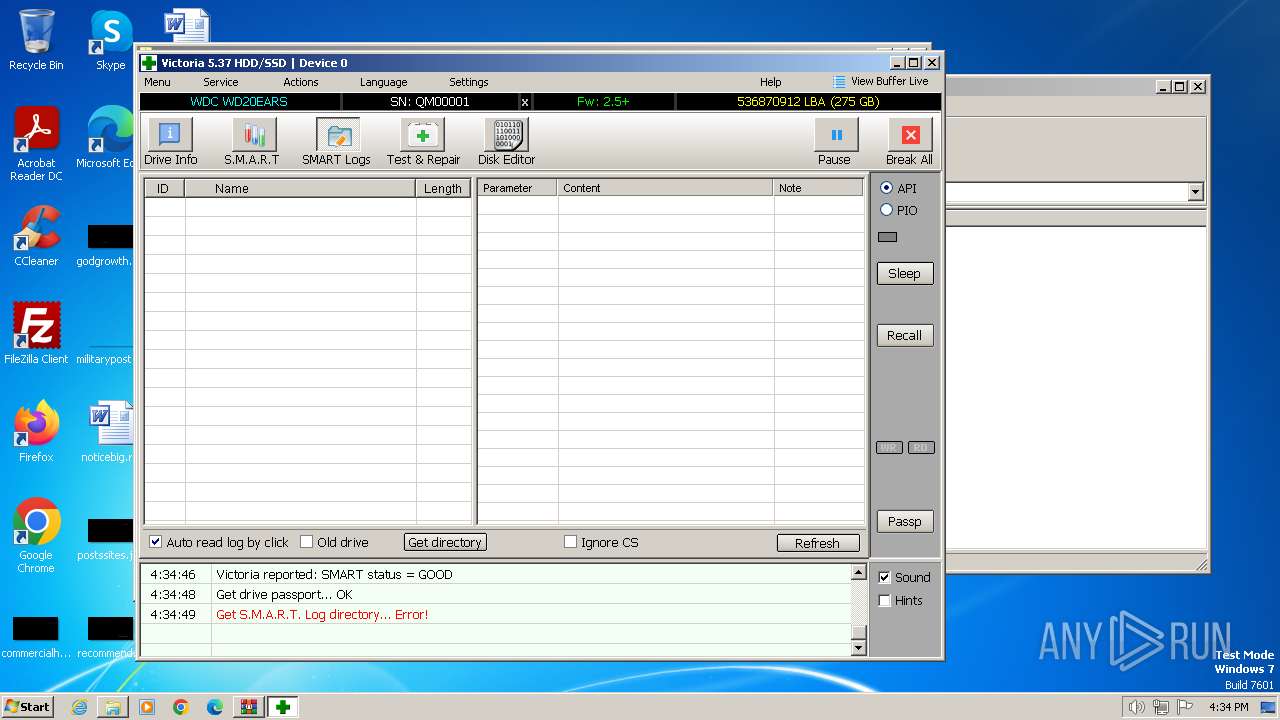
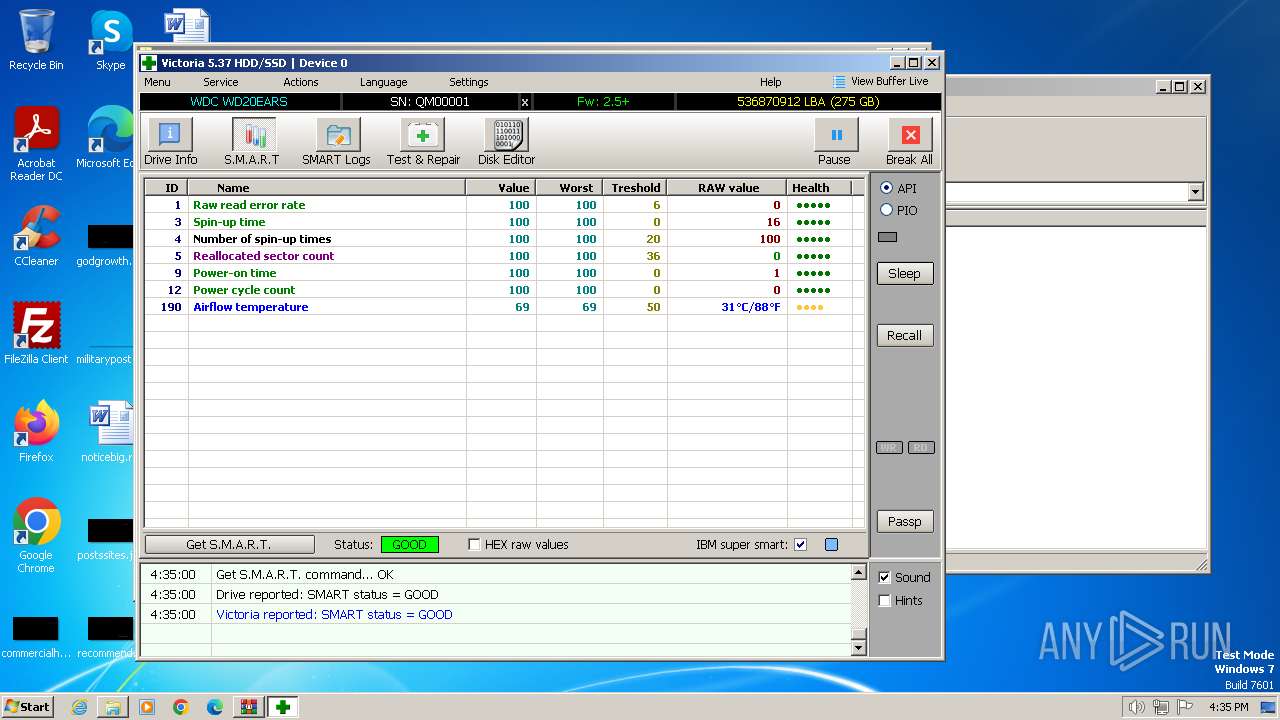
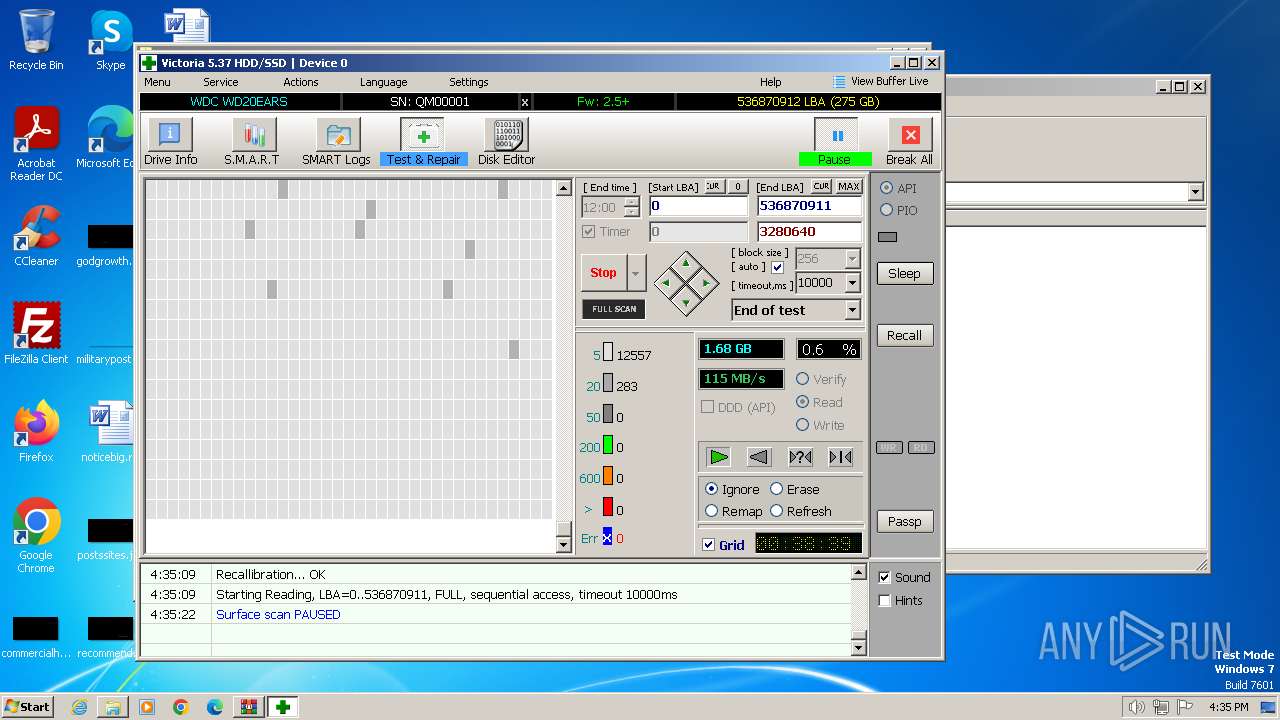
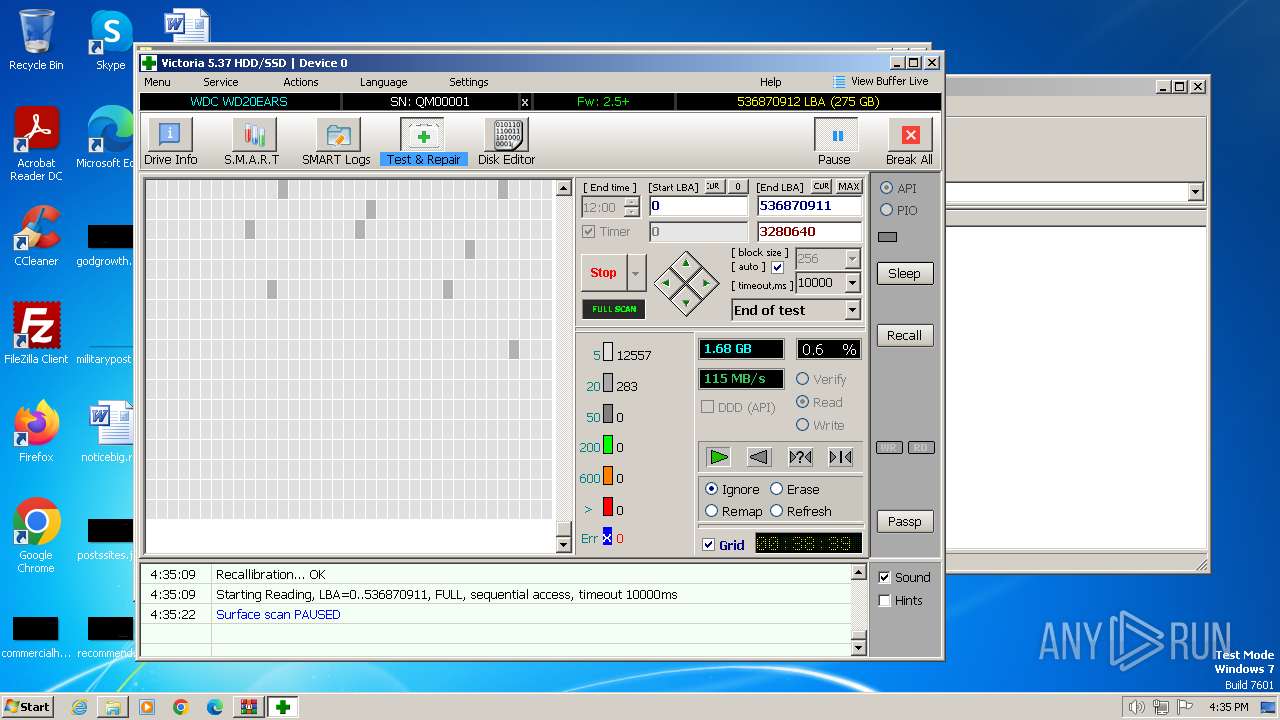
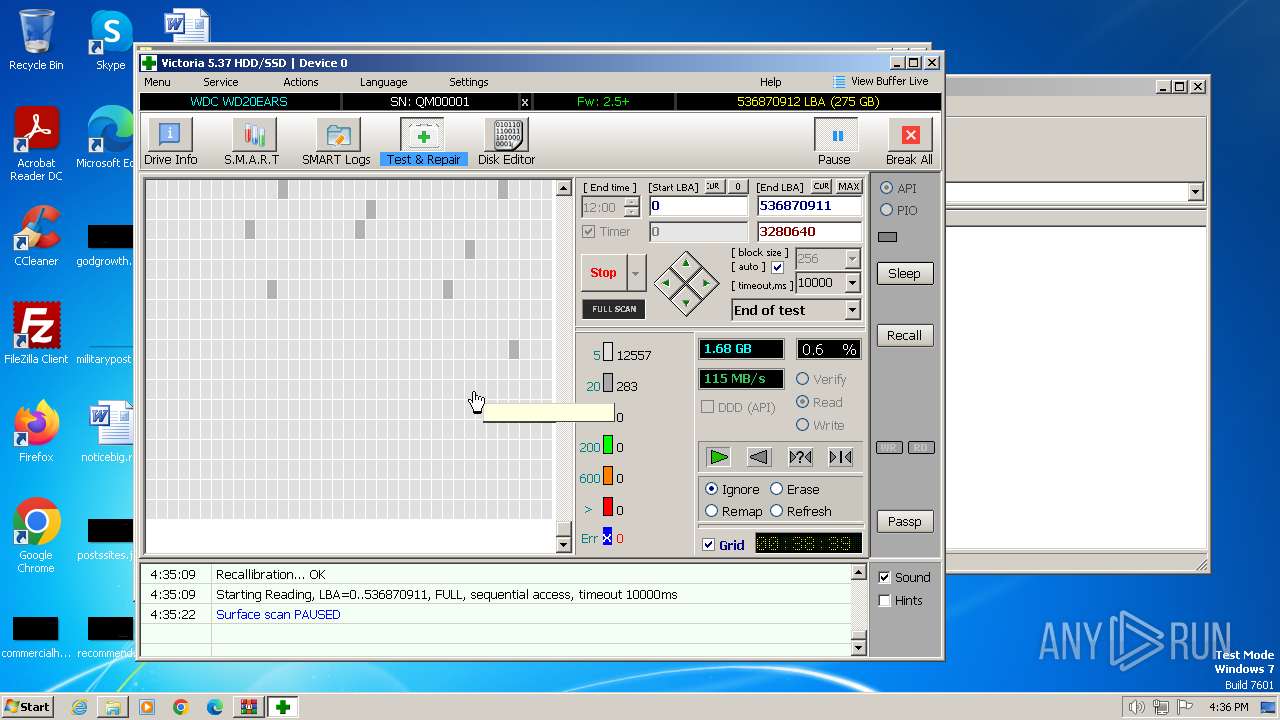
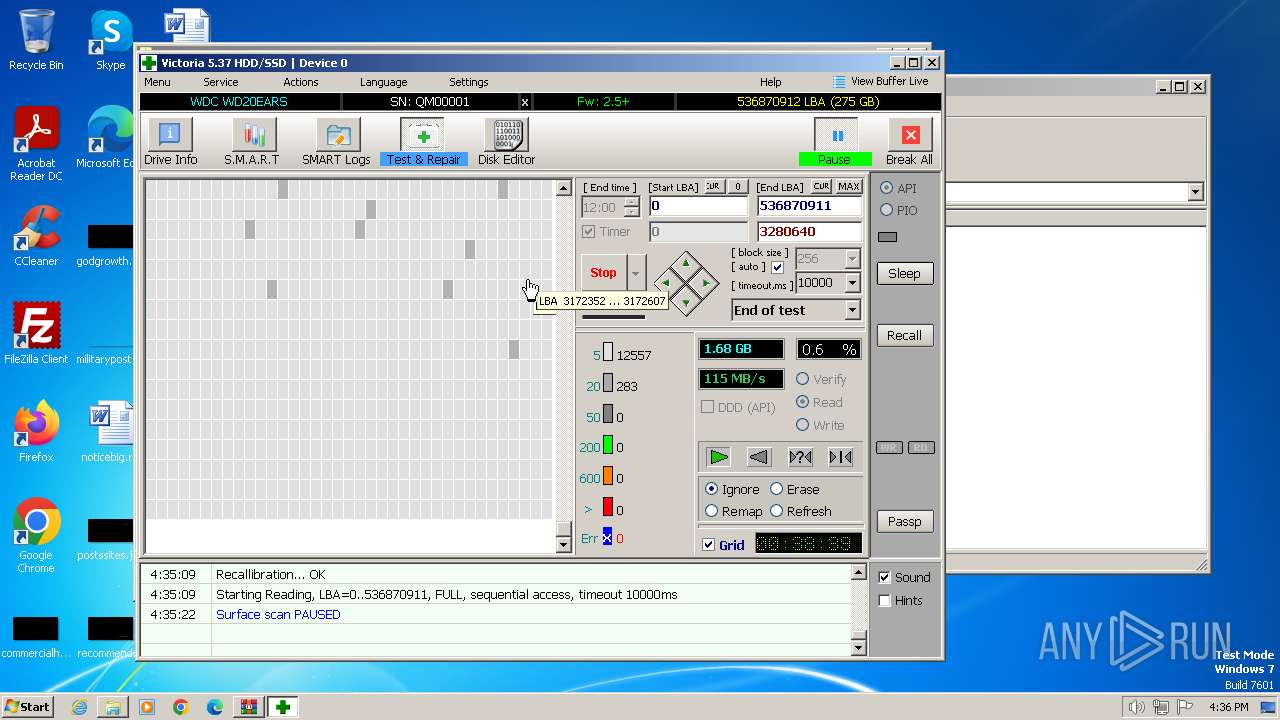
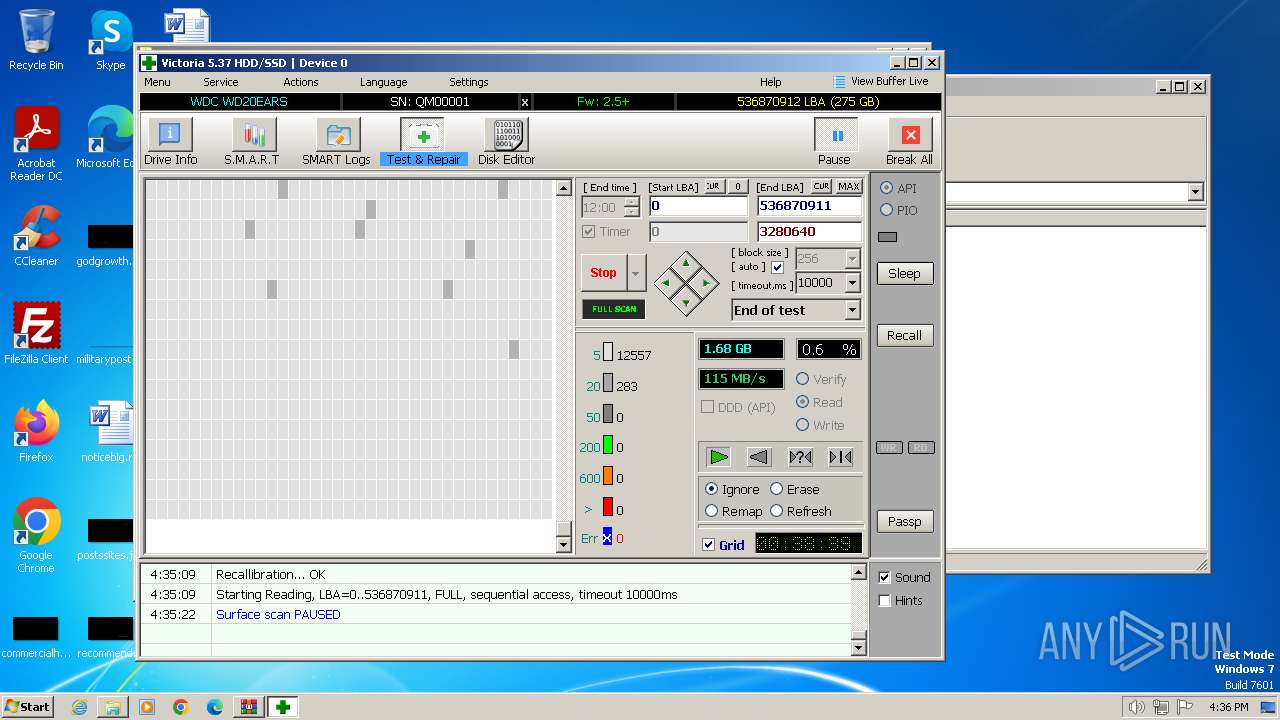
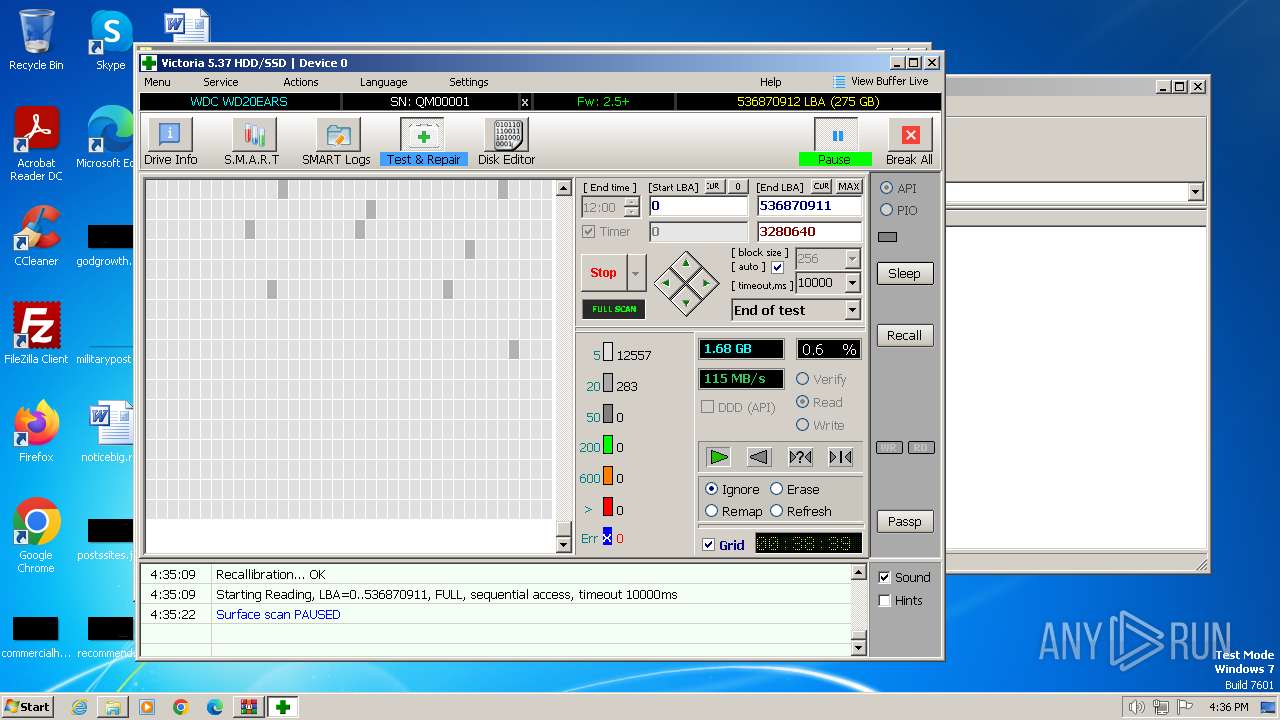
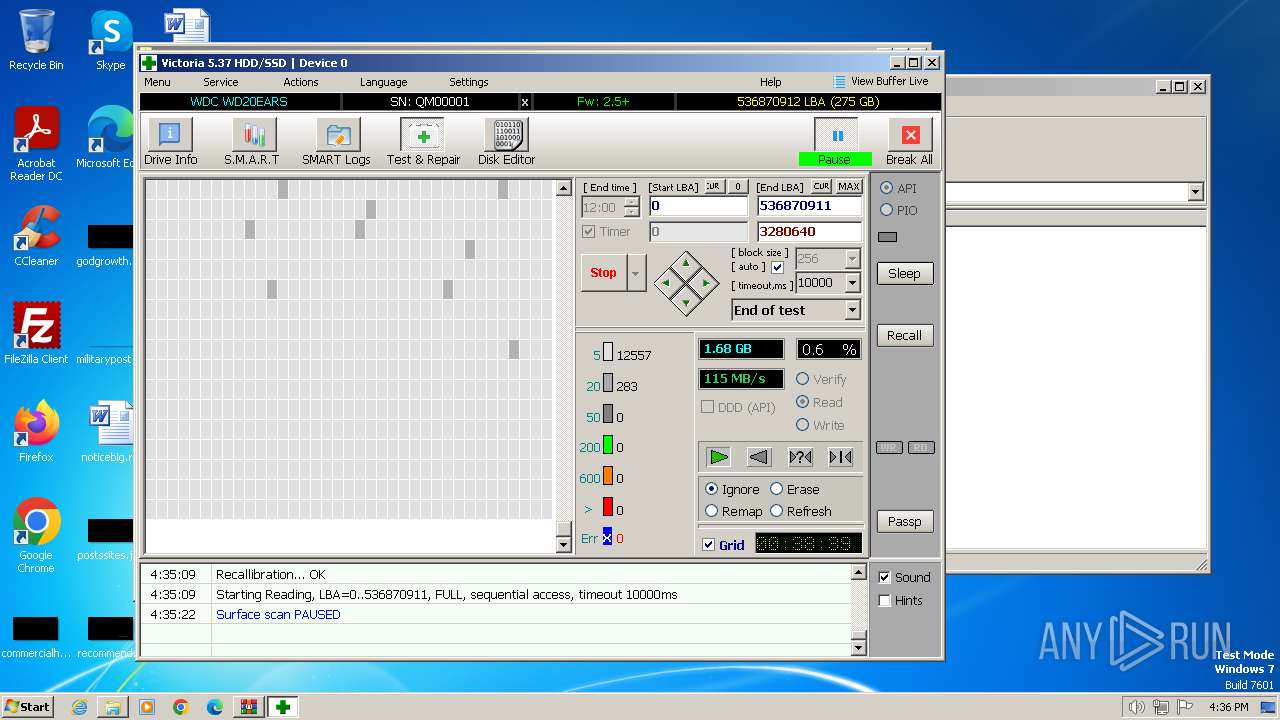
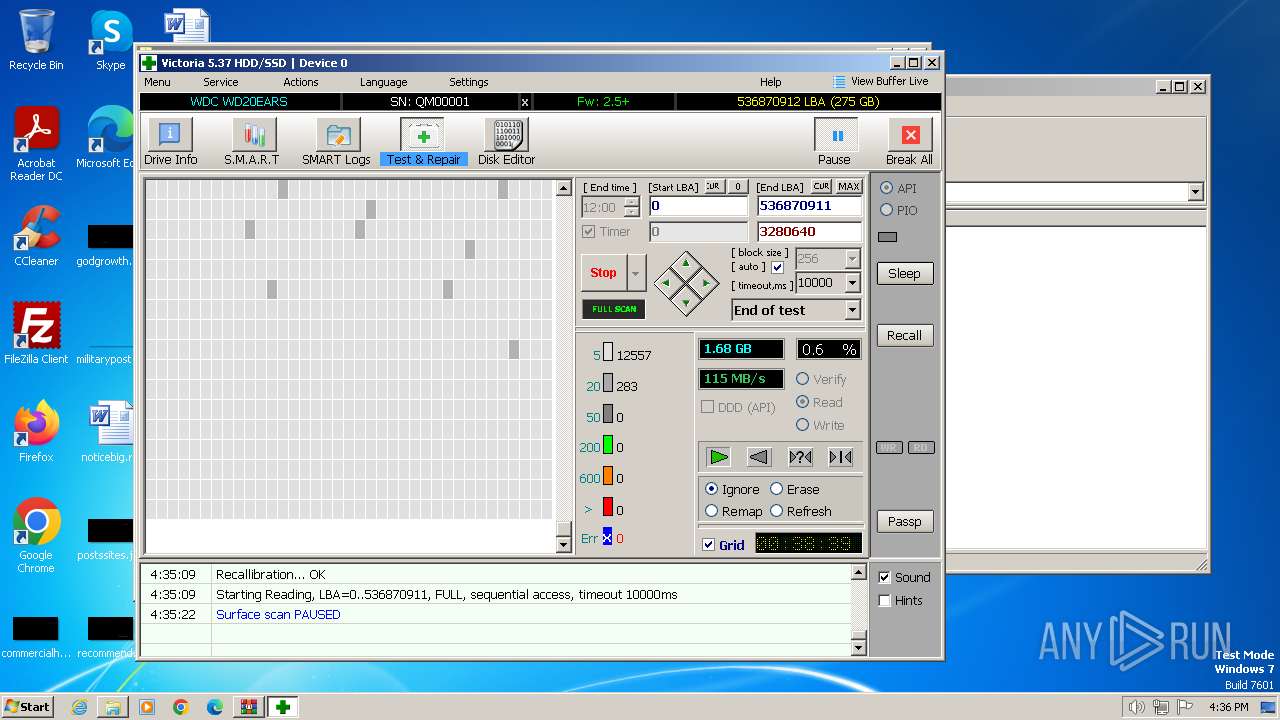
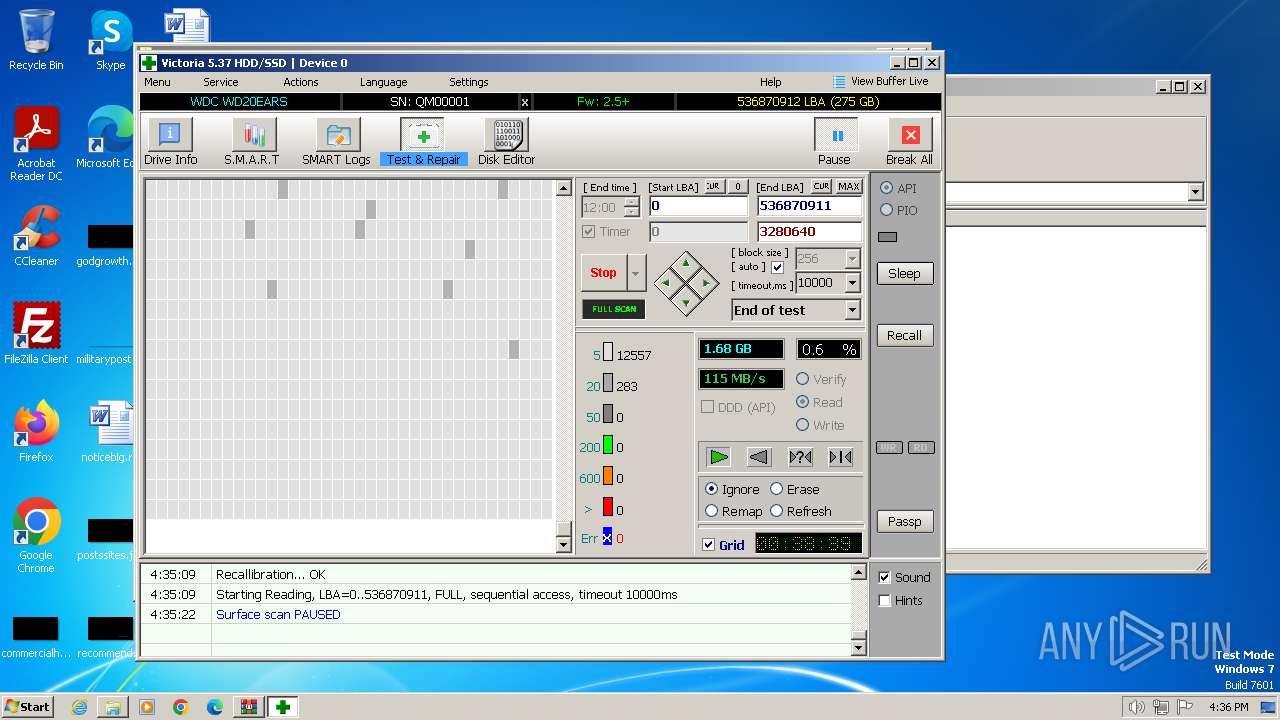
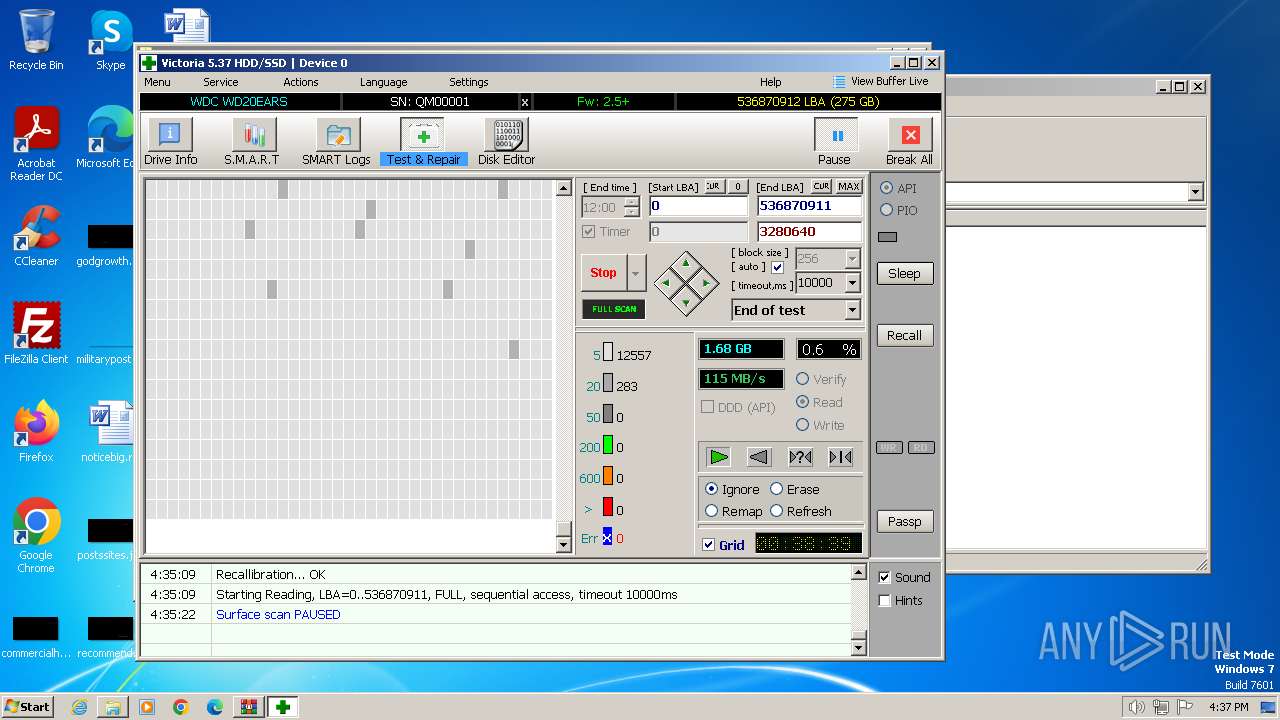
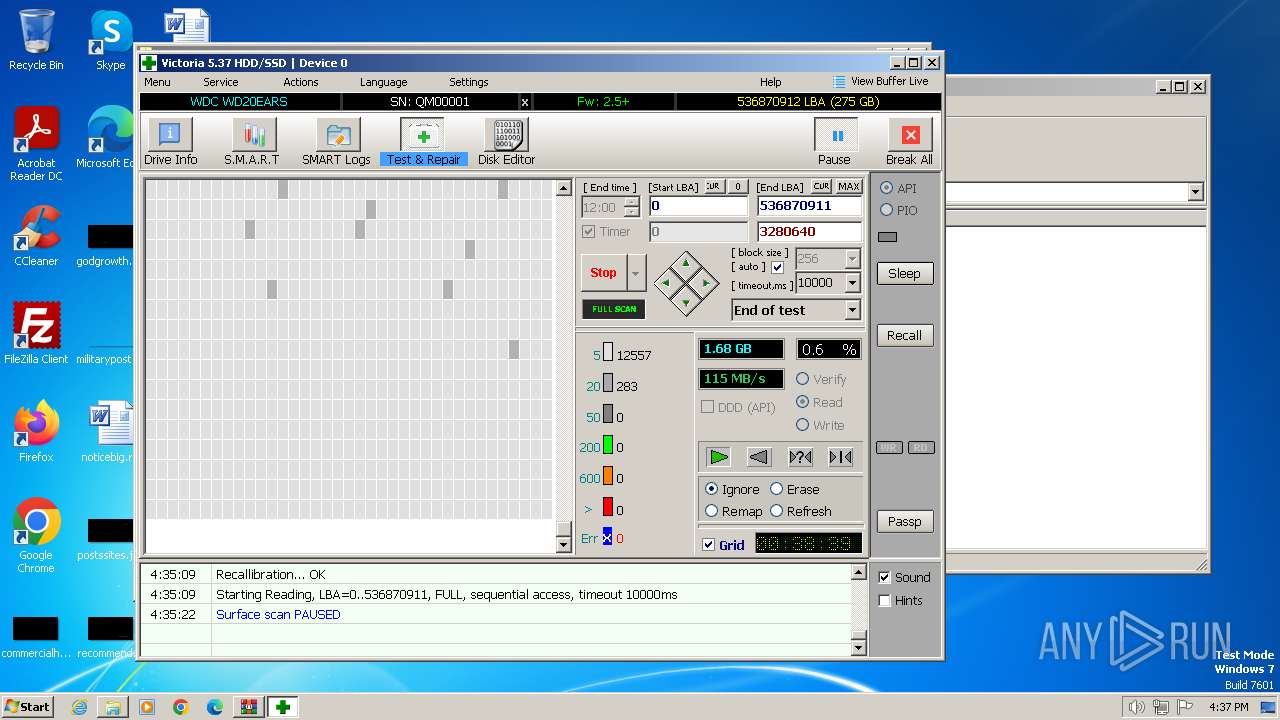
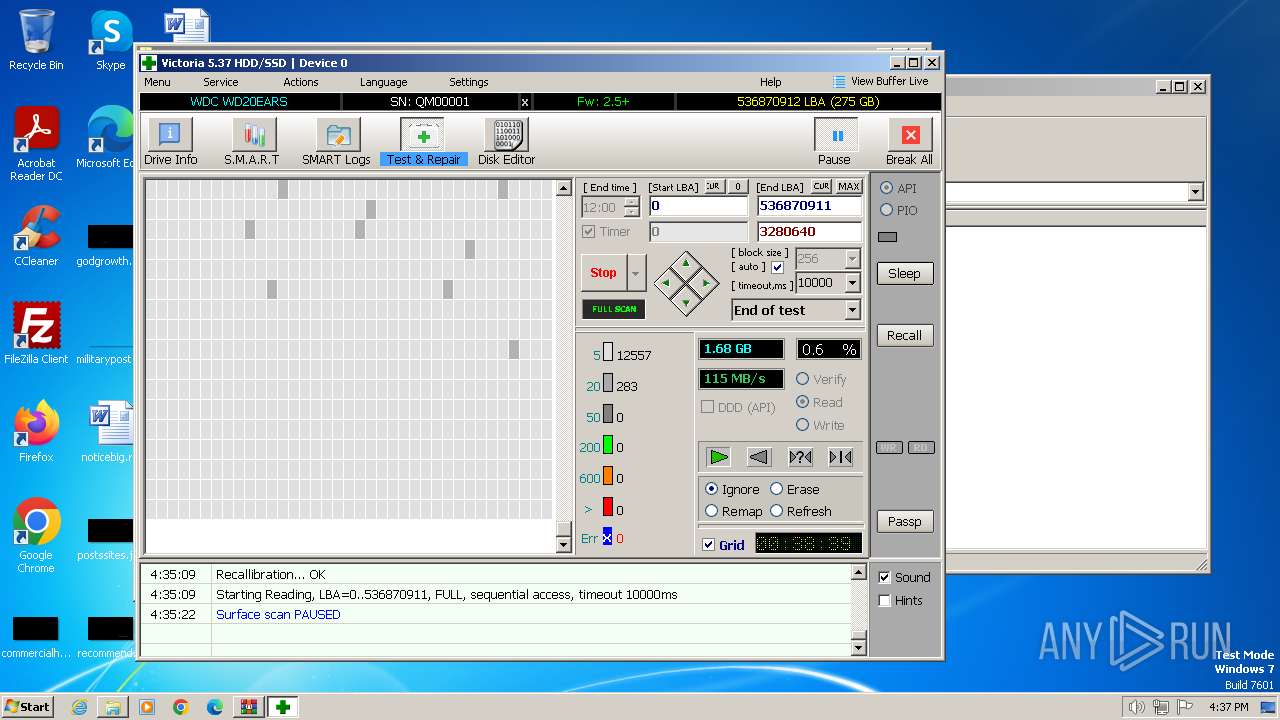
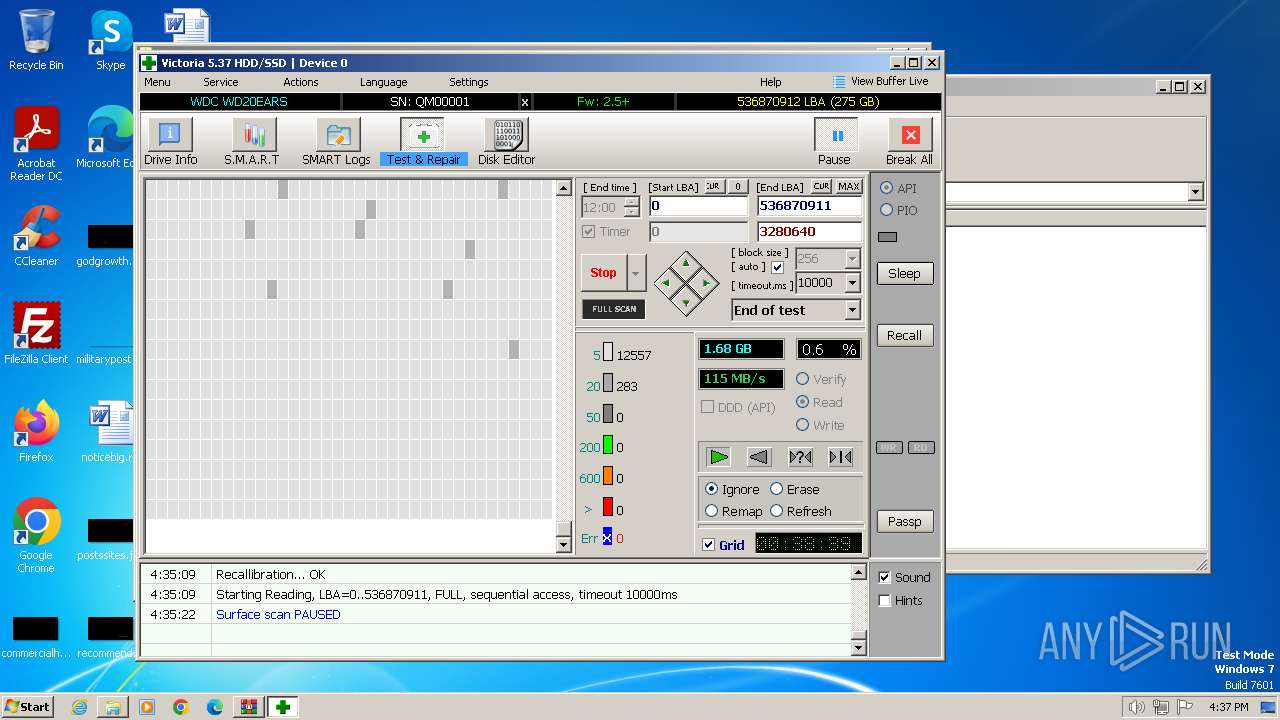
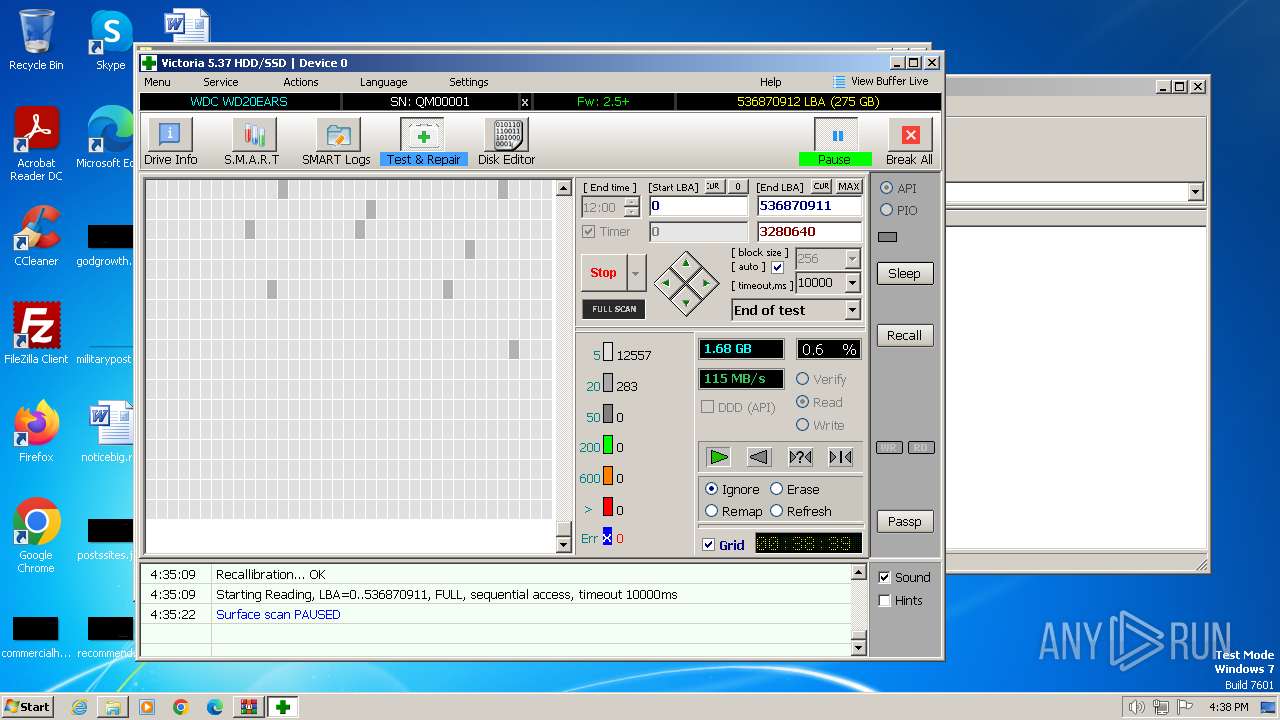
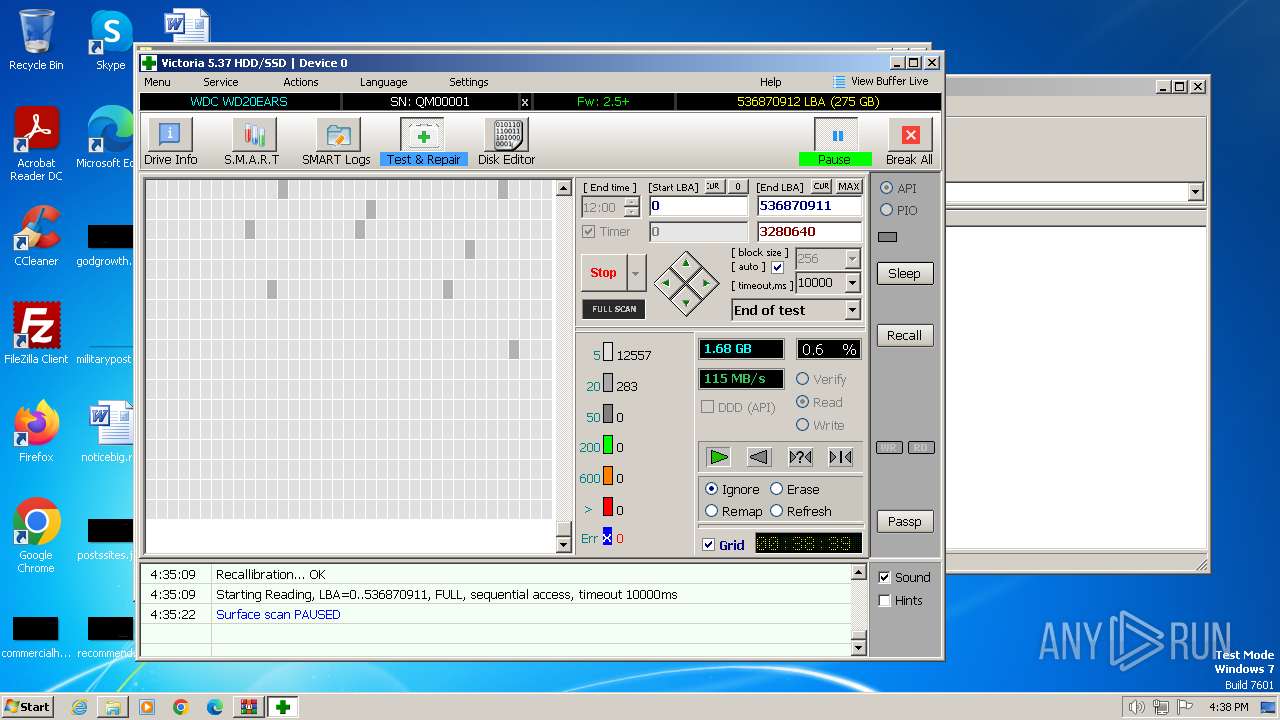
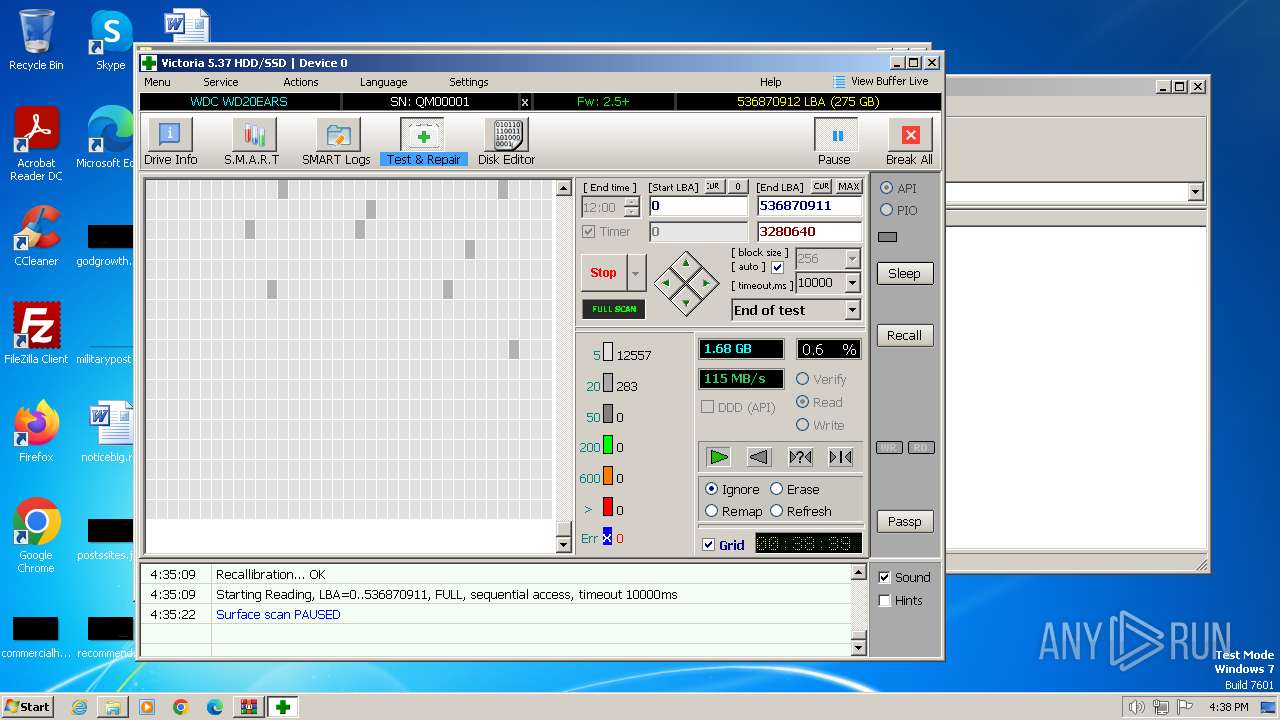
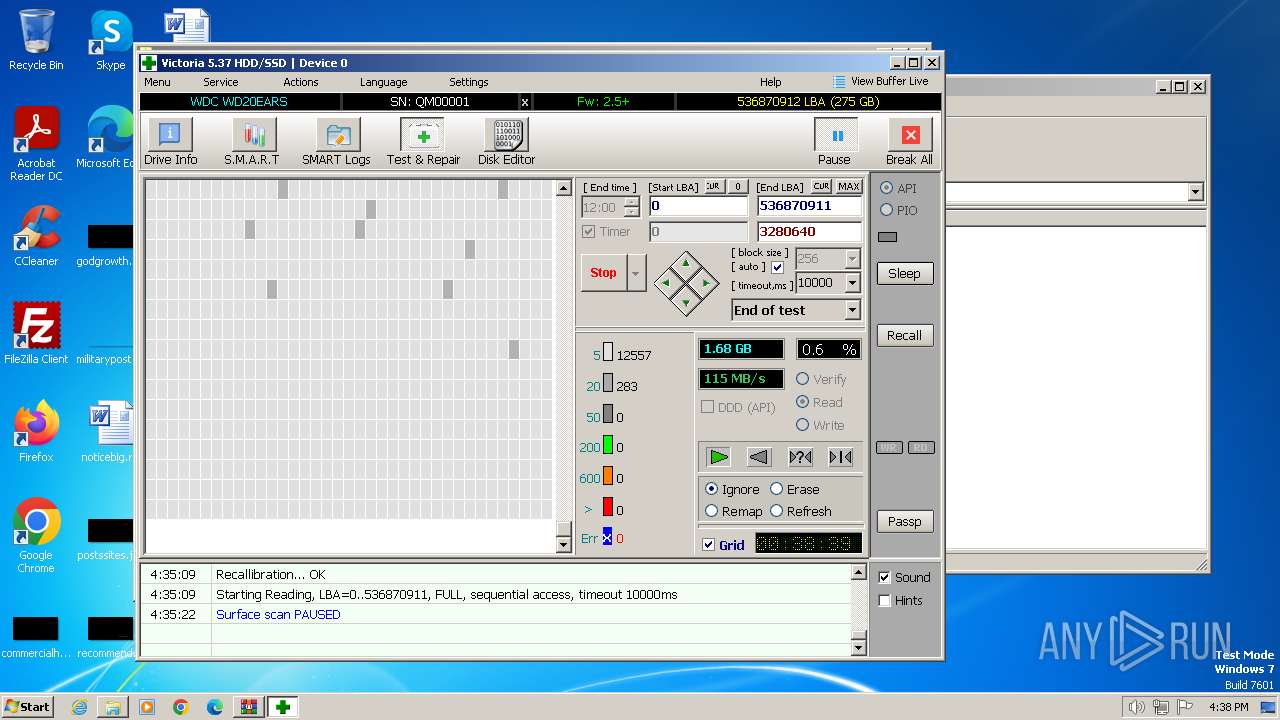
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
- Victoria.exe (PID: 2624)
Creates a writable file in the system directory
- Victoria.exe (PID: 2624)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3668)
- Victoria.exe (PID: 2624)
Creates files in the driver directory
- Victoria.exe (PID: 2624)
Executable content was dropped or overwritten
- Victoria.exe (PID: 2624)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
Manual execution by a user
- Victoria.exe (PID: 3216)
- Victoria.exe (PID: 2624)
Checks supported languages
- Victoria.exe (PID: 2624)
Reads the computer name
- Victoria.exe (PID: 2624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:10:14 16:59:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Victoria537/ |
Total processes
43
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2624 | "C:\Users\admin\Desktop\Victoria537\Victoria.exe" | C:\Users\admin\Desktop\Victoria537\Victoria.exe | explorer.exe | ||||||||||||
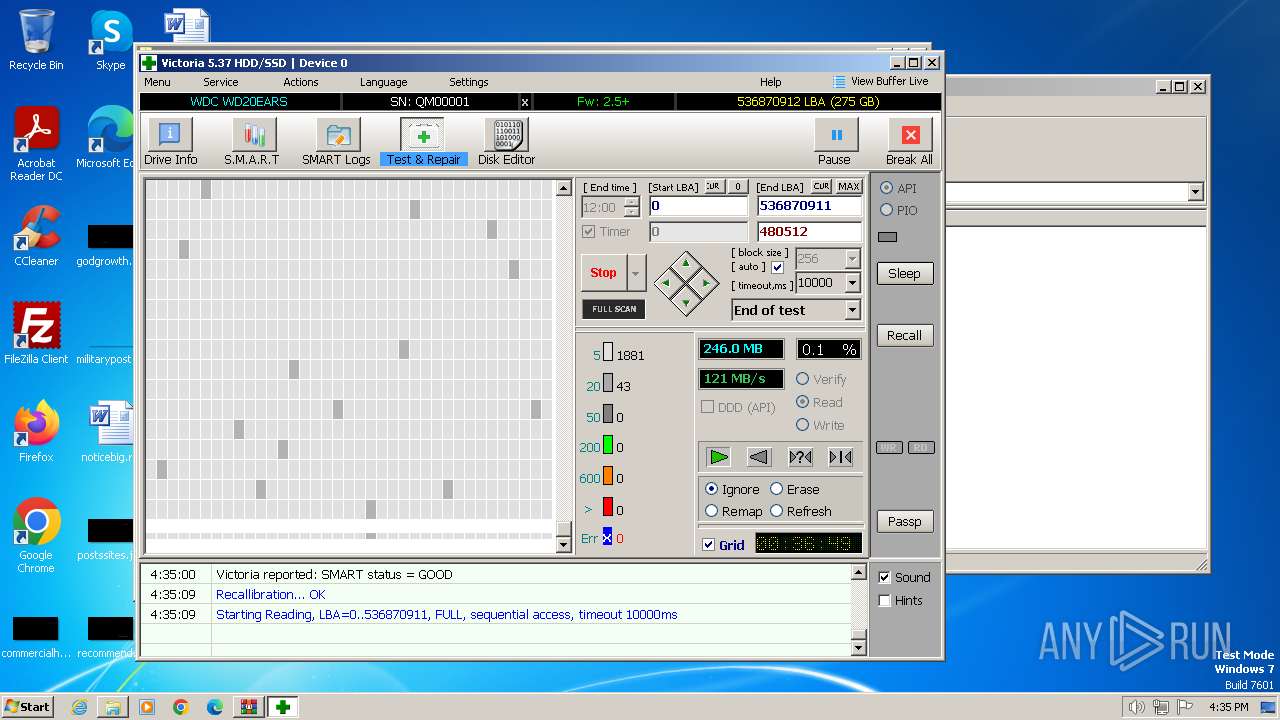
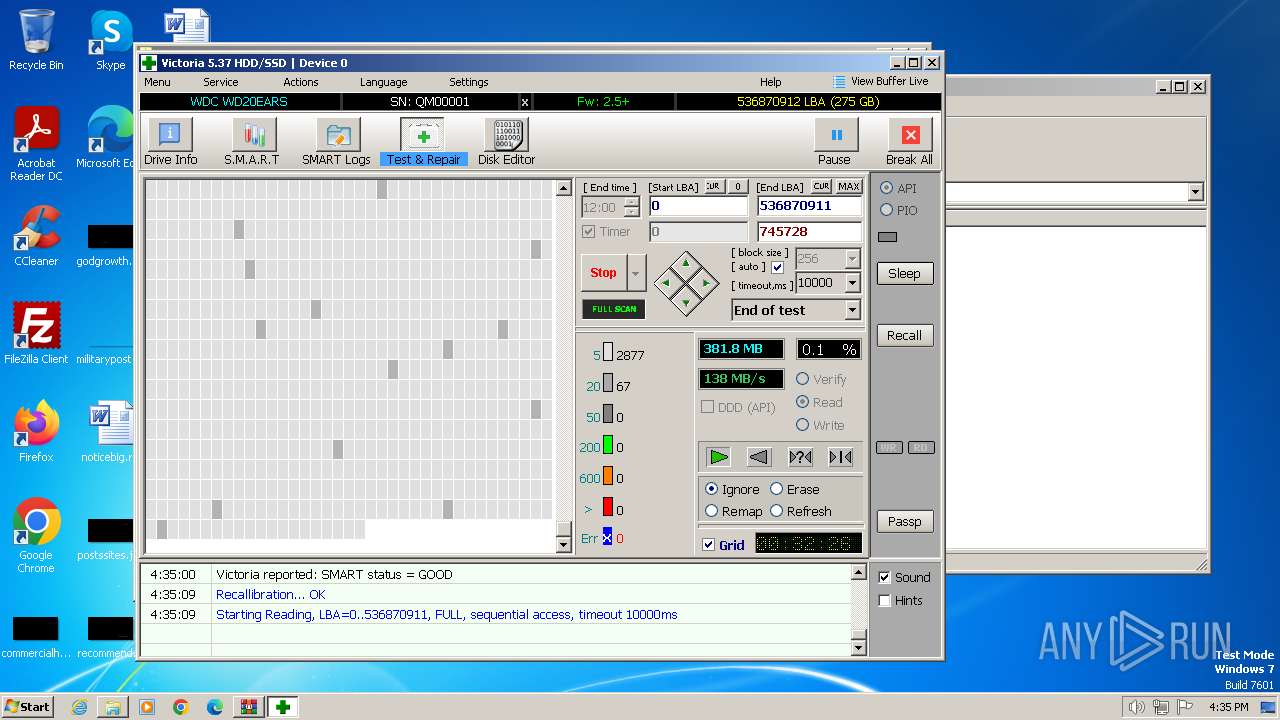
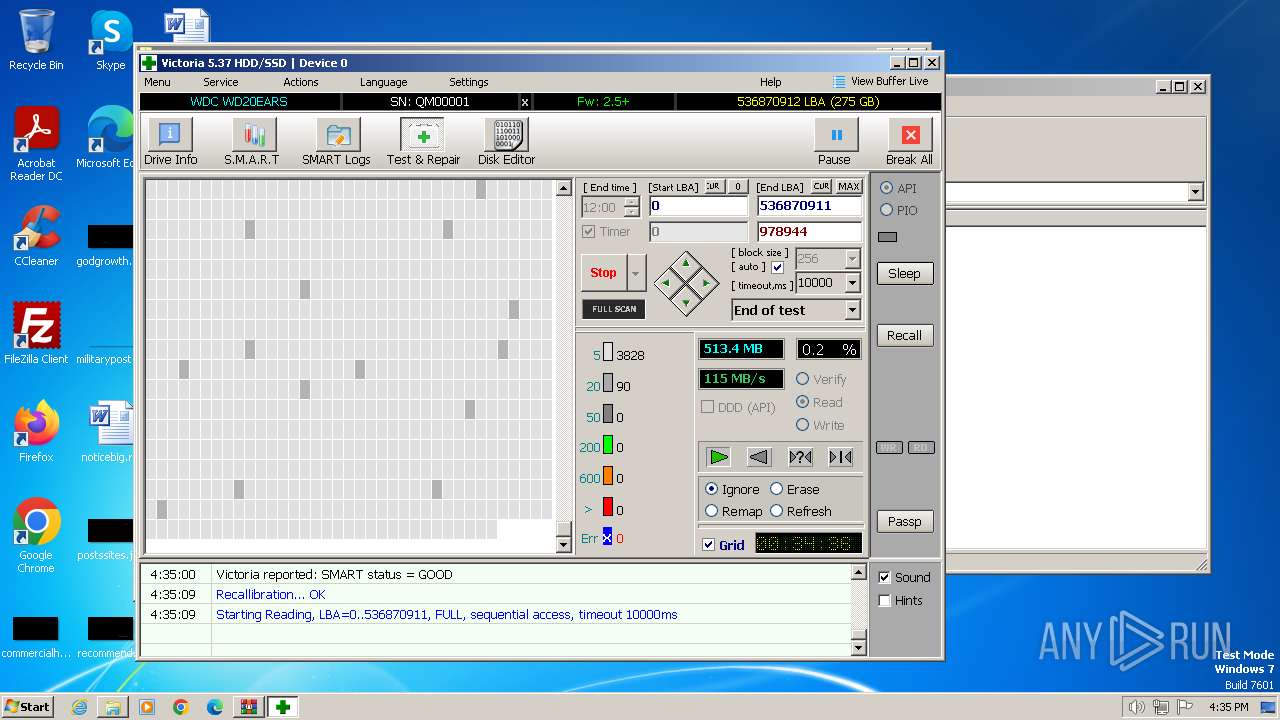
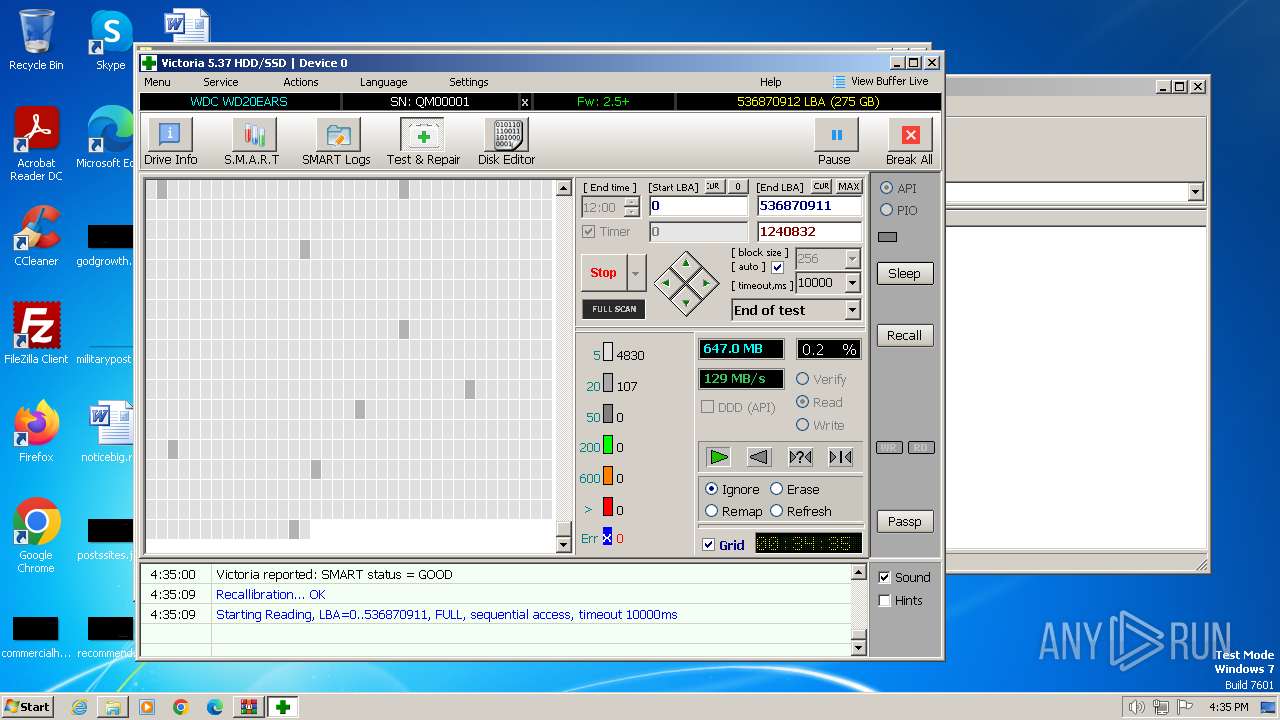
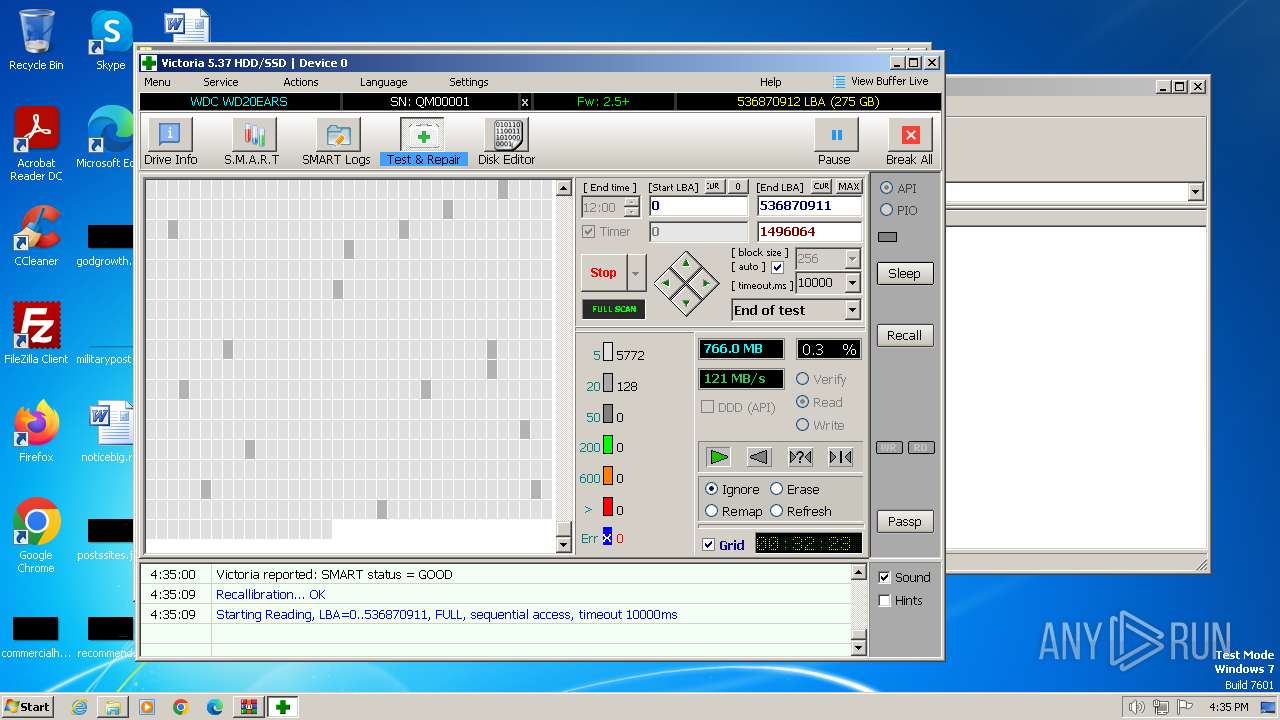
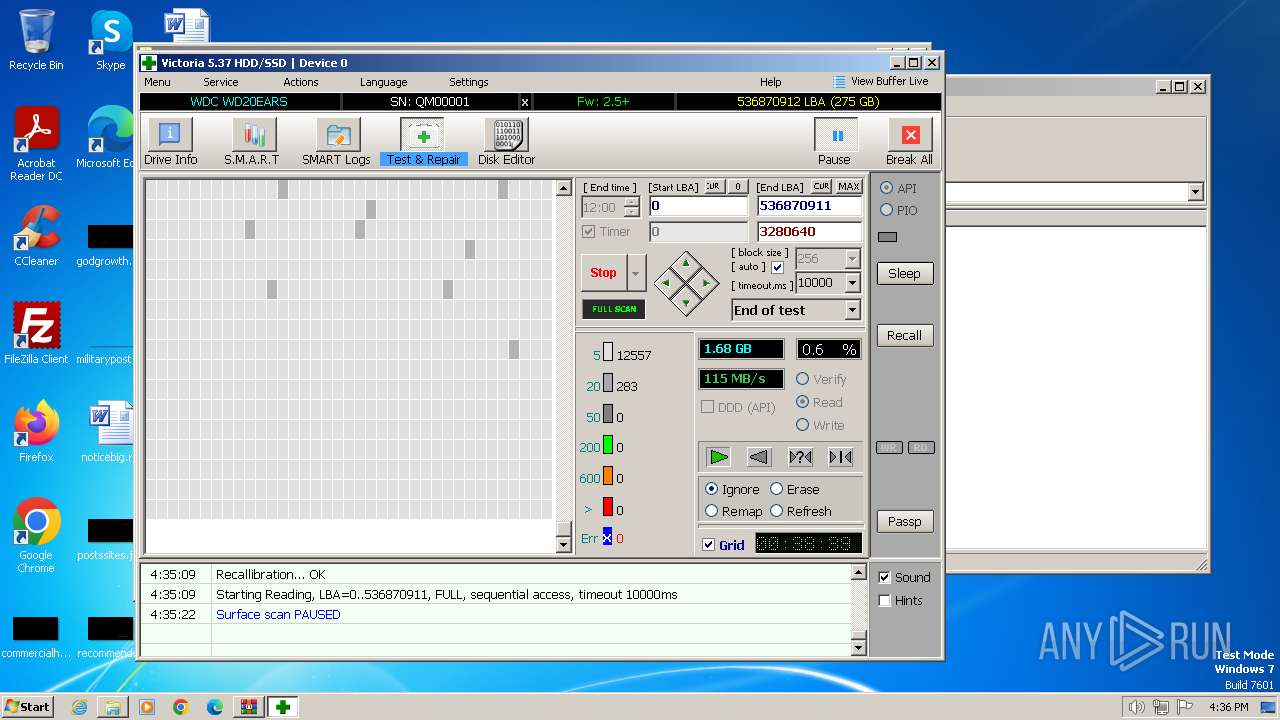
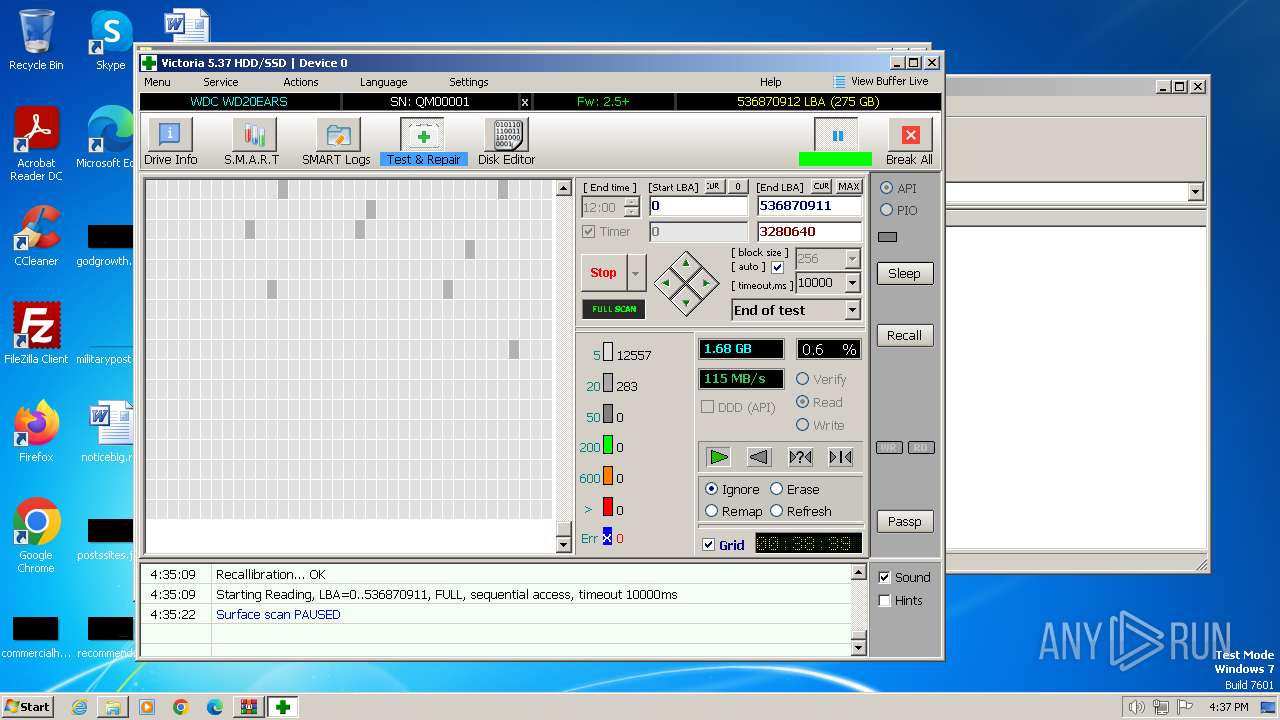
User: admin Company: HDD.BY Integrity Level: HIGH Description: HDD/SSD low-level test, repair & benchmark utility Exit code: 0 Version: 5.3.7.0 Modules
| |||||||||||||||
| 3216 | "C:\Users\admin\Desktop\Victoria537\Victoria.exe" | C:\Users\admin\Desktop\Victoria537\Victoria.exe | — | explorer.exe | |||||||||||
User: admin Company: HDD.BY Integrity Level: MEDIUM Description: HDD/SSD low-level test, repair & benchmark utility Exit code: 3221226540 Version: 5.3.7.0 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Victoria537.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 883
Read events
3 864
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Victoria537.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
1
Text files
18
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\Help\Ukraine\dcomemo.rtf | text | |
MD5:1464993B633F1F6B0EEAB7469076A369 | SHA256:1AFE0C42931656985A5955514D49A250EE07FD2A9DE67FCDD45C9F492A11ABD7 | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\Help\Ukraine\vichlp.rtf | text | |
MD5:43FED3D6537208C280FAEC0FF8242692 | SHA256:FBDAE514E6F648554C58D7B6C3D1F154791DFAAC94223B88F7881471020E7933 | |||
| 2624 | Victoria.exe | C:\Windows\system32\Drivers\PortTalk.sys | executable | |
MD5:7D5A2D755B6C6579F63657B527D6FF1B | SHA256:A2B44785FA6BE4A2A723B06B906F6C48DEAD63ACC0F787CF9A0890EED47F9D0C | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\Help\Ukraine\whatsnew.rtf | text | |
MD5:9F5FC0015ACE5BCB72D208C8CC53663A | SHA256:119300AD57FE8B92C7E6CFBD0621B39D9C65833BEA92D075B4F22BFC295B7F06 | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\Help\Русский\whatsnew.rtf | text | |
MD5:9F5FC0015ACE5BCB72D208C8CC53663A | SHA256:119300AD57FE8B92C7E6CFBD0621B39D9C65833BEA92D075B4F22BFC295B7F06 | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\LNG\English.lng | text | |
MD5:1FC68FD20E3E589D8F9DEB05279620B7 | SHA256:0969ADA3E06388B76778CF92287BD3F4FEA90455C99C95682A33E96411AC9ABC | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\Help\English\dcomemo.rtf | text | |
MD5:B37C2599A7E0EE739136EC4342616FCD | SHA256:DDDCEEE9CCBBCACFAD9F4C9E04608DDE42E43158985D6BEBE761E2C1957D0908 | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\LNG\Ukraine.lng | text | |
MD5:378E4D25078B093E10914BCC2D678E0A | SHA256:AEBA810A306CB5B2D397CD1FED4E6D717CCFF3B6C30E015BCEFCD9F1430E8D57 | |||
| 2624 | Victoria.exe | C:\Users\admin\Desktop\Victoria537\LOGS\eventlog.txt | text | |
MD5:4724E99A53523C35075C8873AB7CAEFA | SHA256:036468C75F5371CEE4BDDC2DF6EDFCC229B51CE8B1C774FF0E8FEFBA949D3980 | |||
| 3668 | WinRAR.exe | C:\Users\admin\Desktop\Victoria537\LNG\Español.lng | text | |
MD5:9C1A4869B6BE1974FFAC76AF96F1B4B4 | SHA256:585A86F13D2C91500ECB2AFB1E6D4F81E5B00FE6B7A218A1756D04EF0F7E7697 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |