| File name: | a648ee4a4c692beb17b76ed305d1859f5be5b61452806bf5ec5fbec344f6d73f |
| Full analysis: | https://app.any.run/tasks/19b1be05-4840-4259-89ef-e8e44b5a74e2 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 16:52:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
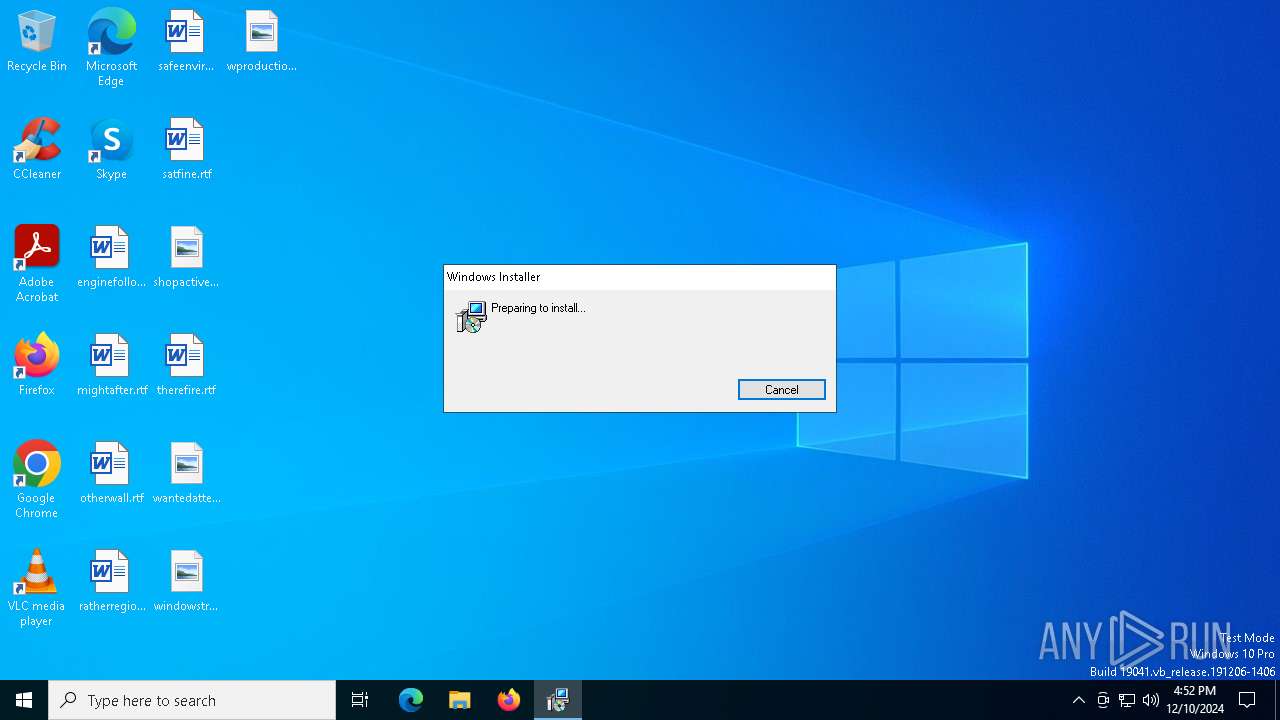
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: PDQConnectAgent, Author: PDQ.com, Keywords: Installer, Comments: This installer database contains the logic and data required to install PDQConnectAgent., Template: x64;1033, Revision Number: {85C6D84F-37EC-4D4B-94DE-DB23DEF61F1F}, Create Time/Date: Wed Nov 6 23:53:40 2024, Last Saved Time/Date: Wed Nov 6 23:53:40 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: WiX Toolset (5.0.0.0), Security: 2 |
| MD5: | 6ED5FC461C958D5D50DFE9122BAB4813 |
| SHA1: | 2B61DC170FDB99D8F1238FD933C7709A366CA70A |
| SHA256: | A648EE4A4C692BEB17B76ED305D1859F5BE5B61452806BF5EC5FBEC344F6D73F |
| SSDEEP: | 98304:f3Q8NTtWfTSdT8sMAxt9QdQ80K6/ySxzgvb41t70DaPe/0sVHhD2xGKxkFA8g//n:WLb6V |
MALICIOUS
Changes powershell execution policy (Bypass)
- pdq-connect-agent.exe (PID: 5036)
Bypass execution policy to execute commands
- powershell.exe (PID: 6384)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 4684)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1140)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 6788)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 6524)
- powershell.exe (PID: 1416)
- powershell.exe (PID: 720)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 7252)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 7312)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 4328)
- powershell.exe (PID: 7392)
- powershell.exe (PID: 7272)
- powershell.exe (PID: 7332)
- powershell.exe (PID: 7372)
- powershell.exe (PID: 7352)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6824)
- pdq-connect-agent.exe (PID: 5036)
- pdq-connect-updater.exe (PID: 2972)
Executable content was dropped or overwritten
- rundll32.exe (PID: 3700)
- rundll32.exe (PID: 6376)
- rundll32.exe (PID: 5564)
- rundll32.exe (PID: 3288)
- rundll32.exe (PID: 2452)
- pdq-connect-agent.exe (PID: 5036)
- rundll32.exe (PID: 5968)
- rundll32.exe (PID: 2072)
- csc.exe (PID: 5200)
- csc.exe (PID: 5316)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 7332)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 2800)
- msiexec.exe (PID: 6176)
- msiexec.exe (PID: 5876)
Checks Windows Trust Settings
- msiexec.exe (PID: 6776)
PDQConnect is probably used for system patching and software deployment
- sc.exe (PID: 3988)
Starts SC.EXE for service management
- rundll32.exe (PID: 2452)
The process hide an interactive prompt from the user
- pdq-connect-agent.exe (PID: 5036)
The process hides Powershell's copyright startup banner
- pdq-connect-agent.exe (PID: 5036)
The process bypasses the loading of PowerShell profile settings
- pdq-connect-agent.exe (PID: 5036)
Starts POWERSHELL.EXE for commands execution
- pdq-connect-agent.exe (PID: 5036)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6776)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5316)
- csc.exe (PID: 5200)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 7332)
Process drops legitimate windows executable
- powershell.exe (PID: 7332)
- powershell.exe (PID: 1544)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 8108)
- DismHost.exe (PID: 6056)
INFO
Reads the computer name
- msiexec.exe (PID: 6776)
- msiexec.exe (PID: 2800)
- msiexec.exe (PID: 6176)
- pdq-connect-updater.exe (PID: 2972)
Reads the software policy settings
- msiexec.exe (PID: 6600)
- msiexec.exe (PID: 6776)
- pdq-connect-agent.exe (PID: 5036)
- pdq-connect-updater.exe (PID: 2972)
An automatically generated document
- msiexec.exe (PID: 6600)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6600)
Checks proxy server information
- msiexec.exe (PID: 6600)
Checks supported languages
- msiexec.exe (PID: 6776)
- msiexec.exe (PID: 2800)
- msiexec.exe (PID: 6176)
- pdq-connect-updater.exe (PID: 2972)
- pdq-connect-agent.exe (PID: 5036)
- msiexec.exe (PID: 5876)
- csc.exe (PID: 5200)
- csc.exe (PID: 5316)
Manages system restore points
- SrTasks.exe (PID: 3832)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6776)
- pdq-connect-agent.exe (PID: 5036)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6776)
Application launched itself
- msiexec.exe (PID: 6776)
The sample compiled with english language support
- msiexec.exe (PID: 6776)
- powershell.exe (PID: 7332)
- powershell.exe (PID: 1544)
Create files in a temporary directory
- rundll32.exe (PID: 6376)
Creates files in the program directory
- rundll32.exe (PID: 3288)
- pdq-connect-agent.exe (PID: 5036)
The process uses the downloaded file
- powershell.exe (PID: 5028)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 720)
- powershell.exe (PID: 7352)
- powershell.exe (PID: 7372)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 720)
- powershell.exe (PID: 7332)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 7240)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 1140)
- powershell.exe (PID: 1544)
- powershell.exe (PID: 7332)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 1140)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7332)
- powershell.exe (PID: 1544)
Sends debugging messages
- powershell.exe (PID: 7332)
- powershell.exe (PID: 1544)
- DismHost.exe (PID: 6056)
- DismHost.exe (PID: 8108)
Reads Environment values
- DismHost.exe (PID: 8108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | PDQConnectAgent |
| Author: | PDQ.com |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install PDQConnectAgent. |
| Template: | x64;1033 |
| RevisionNumber: | {85C6D84F-37EC-4D4B-94DE-DB23DEF61F1F} |
| CreateDate: | 2024:11:06 23:53:40 |
| ModifyDate: | 2024:11:06 23:53:40 |
| Pages: | 200 |
| Words: | 2 |
| Software: | WiX Toolset (5.0.0.0) |
| Security: | Read-only recommended |
Total processes
200
Monitored processes
73
Malicious processes
5
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 2147943401 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1416 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | pdq-connect-agent.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | "C:\WINDOWS\system32\dsregcmd.exe" /status | C:\Windows\System32\dsregcmd.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: DSREG commandline tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | rundll32.exe "C:\WINDOWS\Installer\MSIC296.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1295031 77 pdqconnectupdater-setup!pdqconnectupdater_setup.CustomActions.CreateEventSource | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\WINDOWS\TEMP\RES6177.tmp" "c:\Windows\Temp\wccrio4k\CSC9668A48796D4E91B27F97F78F5BDFF2.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
Total events
161 445
Read events
161 063
Write events
352
Delete events
30
Modification events
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000003477F1EA234BDB01781A0000981A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000003477F1EA234BDB01781A0000981A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000F72834EB234BDB01781A0000981A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000F72834EB234BDB01781A0000981A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000AD8C36EB234BDB01781A0000981A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000044F038EB234BDB01781A0000981A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000751DBCEB234BDB01781A0000981A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6776) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000006C87BEEB234BDB01781A0000141B0000E8030000010000000000000000000000654AAF7768912948B89562A6C705D5C400000000000000000000000000000000 | |||
| (PID) Process: | (6824) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000007C62CAEB234BDB01A81A0000C81A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
141
Suspicious files
51
Text files
96
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6776 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6776 | msiexec.exe | C:\Windows\Installer\13a490.msi | — | |
MD5:— | SHA256:— | |||
| 6600 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_8DBAD5A433D1F9275321E076E8B744D4 | der | |
MD5:1145536E413C5B0DDAE54E072F31A013 | SHA256:E57C34491E082170AFCA154FA92EF9855D80BD5489480C3611B7FC3B005DA1C6 | |||
| 6600 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:AB26636E53659787C83DE712294DA868 | SHA256:EB5025D51F8D6FF2CCE8279D263BE7111D2444DA6709D19D3BA3DE865620E054 | |||
| 6376 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCAC1E340B4B14CF469D09F22D9DFAF491E\pdqconnectagent-setup.exe | executable | |
MD5:75F16349CAFAE8F37BD1E207E2EC83D2 | SHA256:F3BB2B9230B8A6066DFEEB172AD32AE3EA31D2D49C76BDCC8A1E2531FA61F5B7 | |||
| 6776 | msiexec.exe | C:\Windows\Installer\MSIAD6E.tmp | executable | |
MD5:E8DC682F2C486075C6ABA658971A62CC | SHA256:7AACD4C18710E9BC4FF2034895A0A0C8F80F21809FB177D520E93F7688216E6D | |||
| 6776 | msiexec.exe | C:\Windows\Installer\MSIAB1B.tmp | executable | |
MD5:45E153EF2E0AA13C55CD25FAFA3BCE90 | SHA256:2104D3C13E6B624A7D628534FCDF900730752F9FF389B0F4FE1DE77C33D8D4C1 | |||
| 6776 | msiexec.exe | C:\Windows\Installer\MSIA7AD.tmp | executable | |
MD5:45E153EF2E0AA13C55CD25FAFA3BCE90 | SHA256:2104D3C13E6B624A7D628534FCDF900730752F9FF389B0F4FE1DE77C33D8D4C1 | |||
| 3700 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCAFD2C8C54324528A9BDD0FE62F43E5015\WixToolset.Dtf.WindowsInstaller.dll | executable | |
MD5:B82B13D16E7F3D3607026F61B7295224 | SHA256:BCC548E72B190D8F39DCB19538444E2576617A21CABA6ADCB4116511E1D2DDEE | |||
| 6776 | msiexec.exe | C:\Windows\Installer\MSIAADB.tmp | executable | |
MD5:E8DC682F2C486075C6ABA658971A62CC | SHA256:7AACD4C18710E9BC4FF2034895A0A0C8F80F21809FB177D520E93F7688216E6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
42
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6600 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEA5NZ%2FZDFskqO3oXzEaXao8%3D | unknown | — | — | whitelisted |
6600 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6600 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRhtVltVOu8OqBzmsd%2B%2FeFfks3xTQQUvGsiZZ2MaObmHgXx2HIl1LjgSMACEAvcoEuhCK%2FAlHGPdKmo6gs%3D | unknown | — | — | whitelisted |
640 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
640 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6468 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6600 | msiexec.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |
Process | Message |
|---|---|
powershell.exe | PID=7332 TID=1556 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=7332 TID=1556 Waiting for m_pInternalThread to start - CCommandThread::Start
|
powershell.exe | PID=7332 TID=1556 Initialized SessionTable - DismInitializeInternal
|
powershell.exe | PID=1544 TID=4328 DismApi.dll: API Version 10.0.19041.3758 - DismInitializeInternal
|
powershell.exe | PID=1544 TID=4328 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=1544 TID=4328 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
powershell.exe | PID=1544 TID=4328 Input parameters: LogLevel: 2, LogFilePath: C:\WINDOWS\Logs\DISM\dism.log, ScratchDirectory: (null) - DismInitializeInternal
|
powershell.exe | PID=7332 TID=1556 Initialized GlobalConfig - DismInitializeInternal
|
powershell.exe | PID=7332 TID=1556 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=amd64, Number of processors=4 - DismInitializeInternal
|
powershell.exe | PID=1544 TID=4328 Initialized GlobalConfig - DismInitializeInternal
|