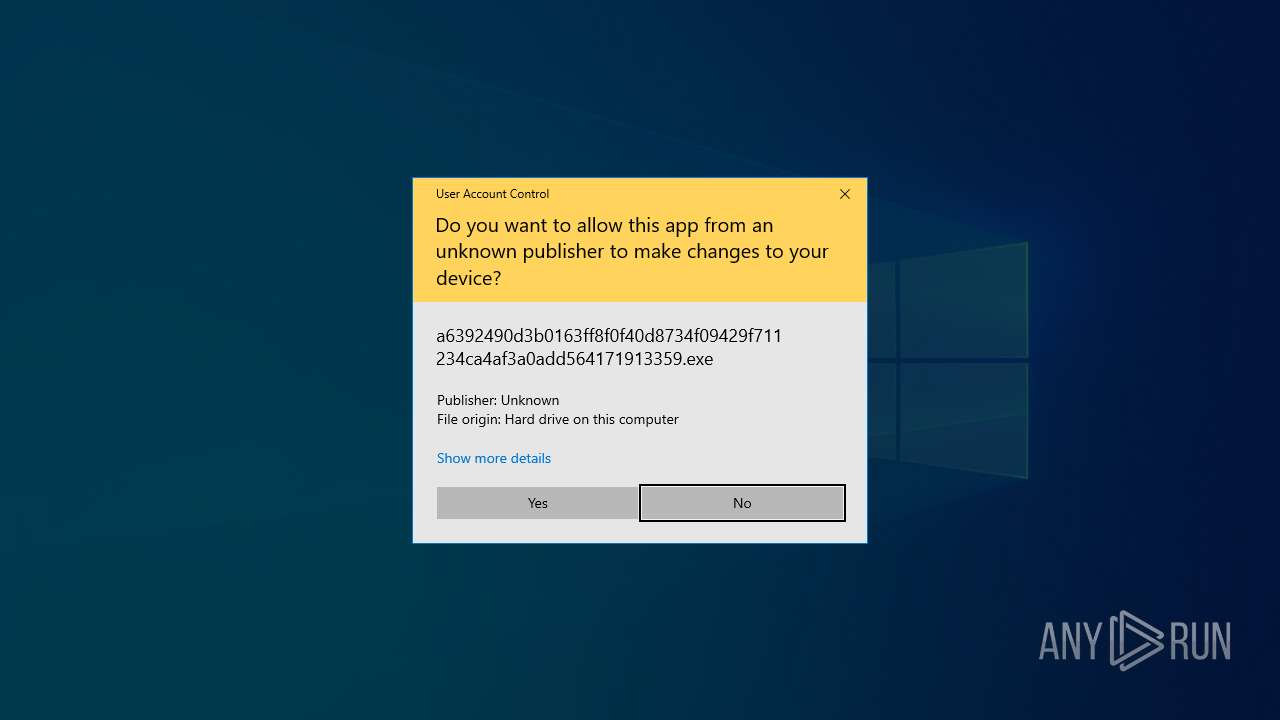
| File name: | a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe |
| Full analysis: | https://app.any.run/tasks/e4740feb-0db1-4644-895b-edc4ad3a723d |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 08:36:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 292EA56DEFD8561F16D4FD74A6D242DD |
| SHA1: | D82A089F259F74A4C40FA46DAD5E457627F0894C |
| SHA256: | A6392490D3B0163FF8F0F40D8734F09429F711234CA4AF3A0ADD564171913359 |
| SSDEEP: | 3072:sO9to0Fh8bZVVQYL29kDIQwRSCy1MFvIqY:sG8bZVVQYL299QwTy1M+q |
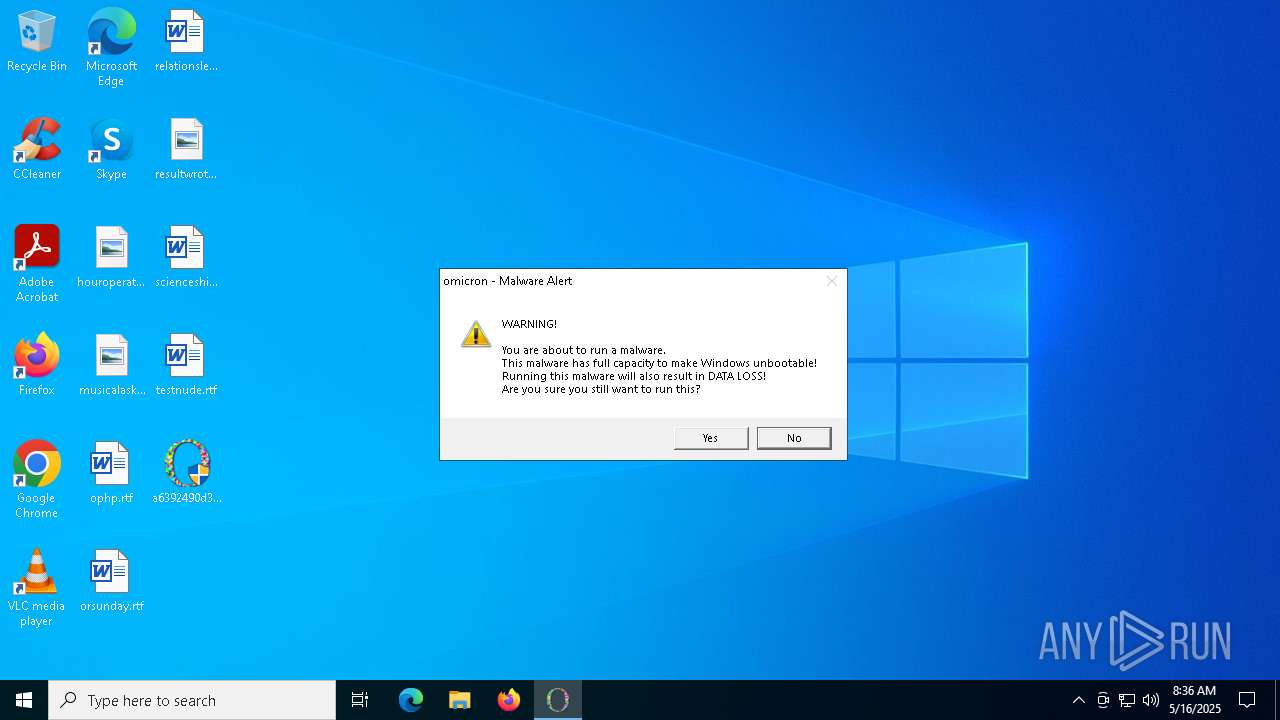
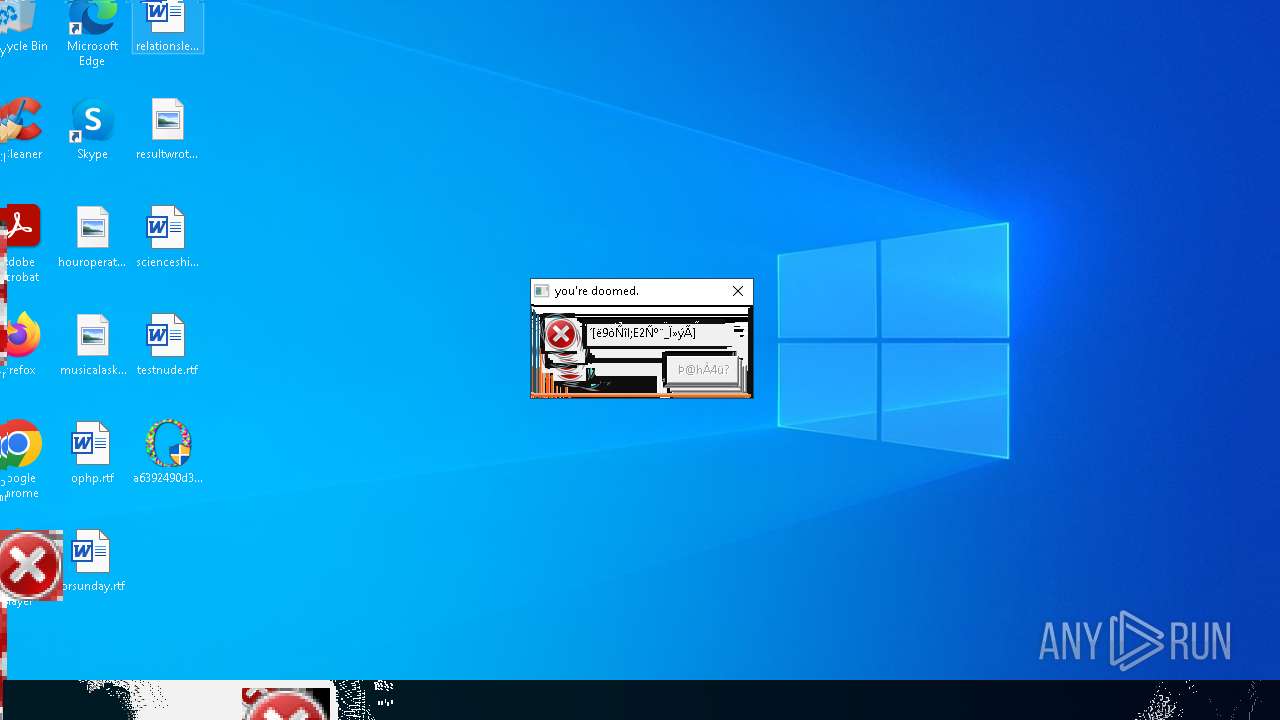
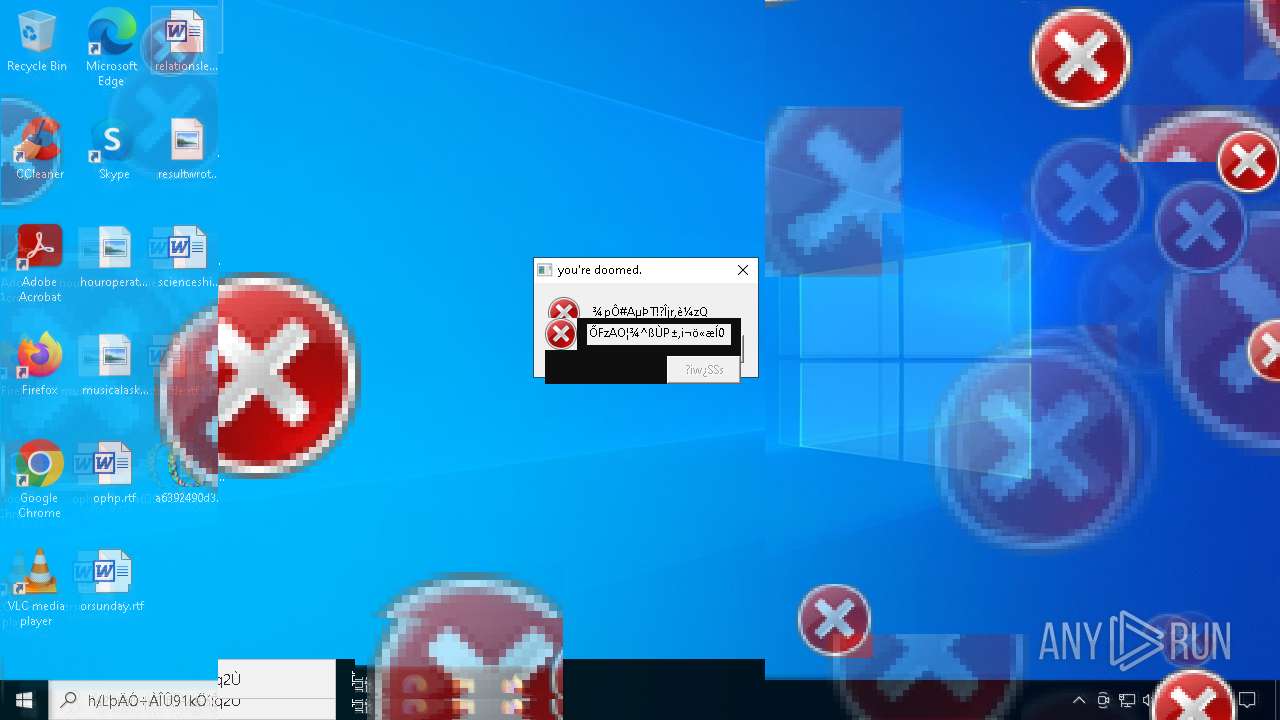
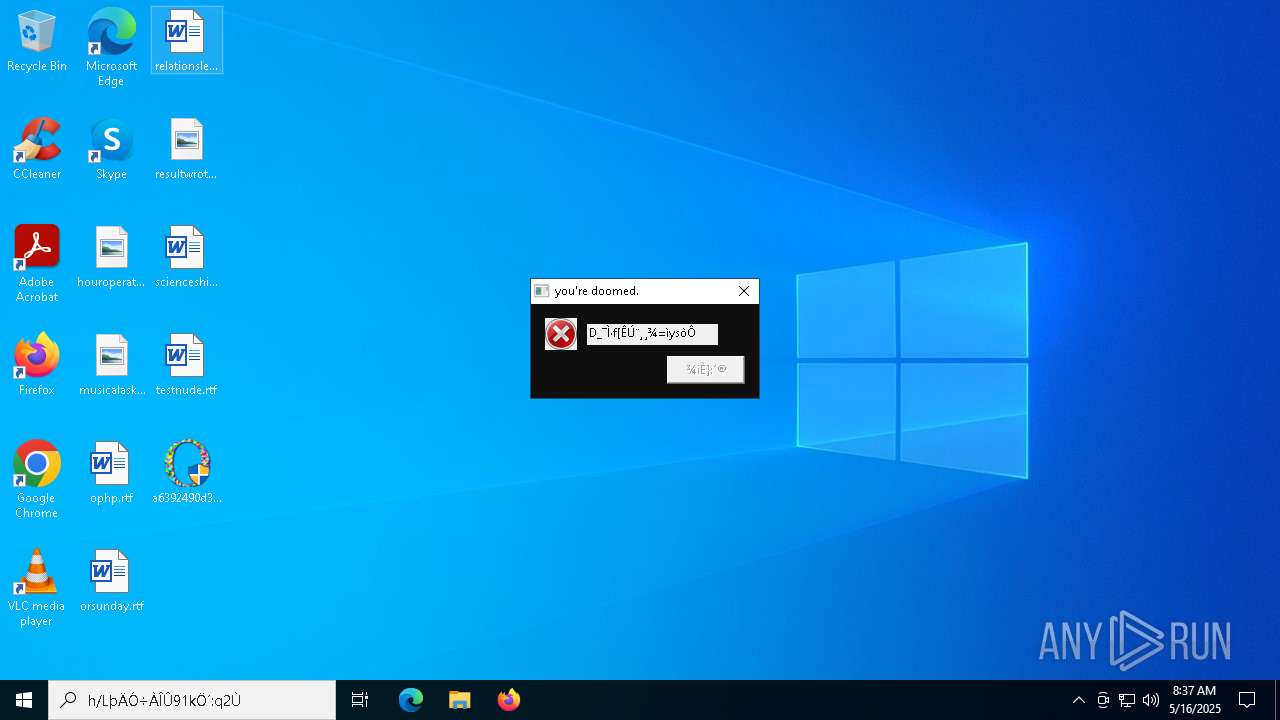
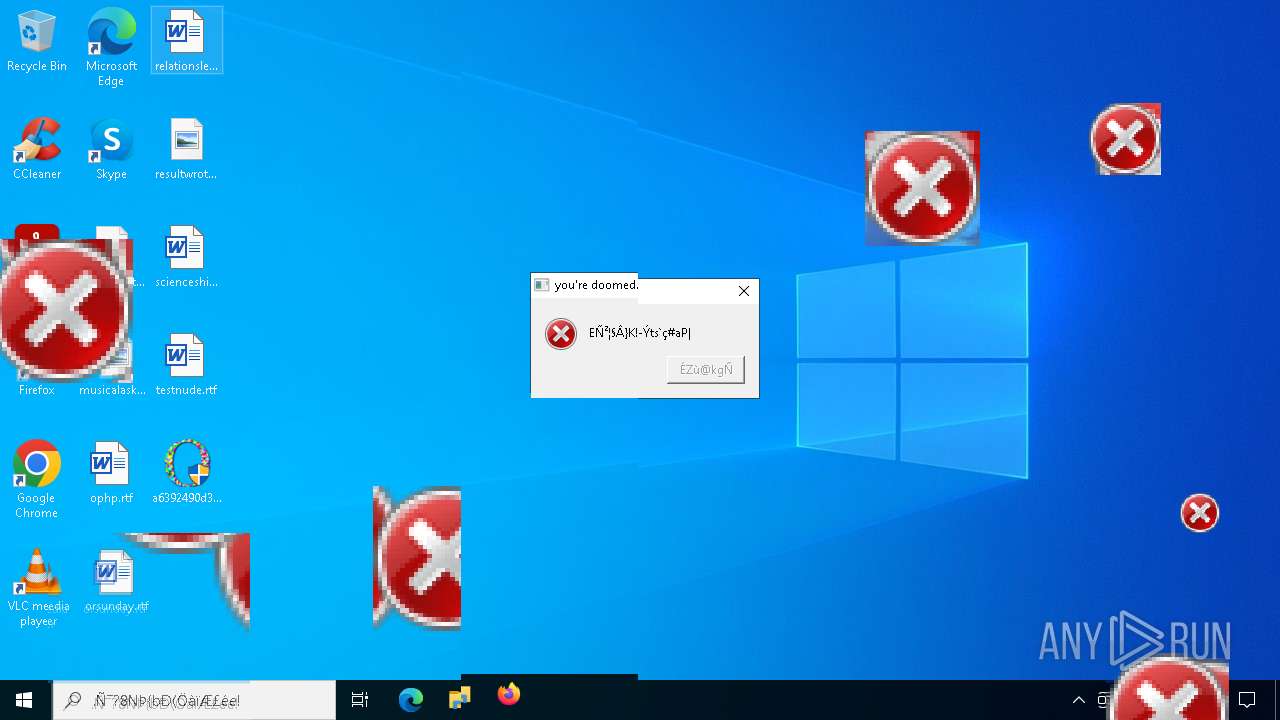
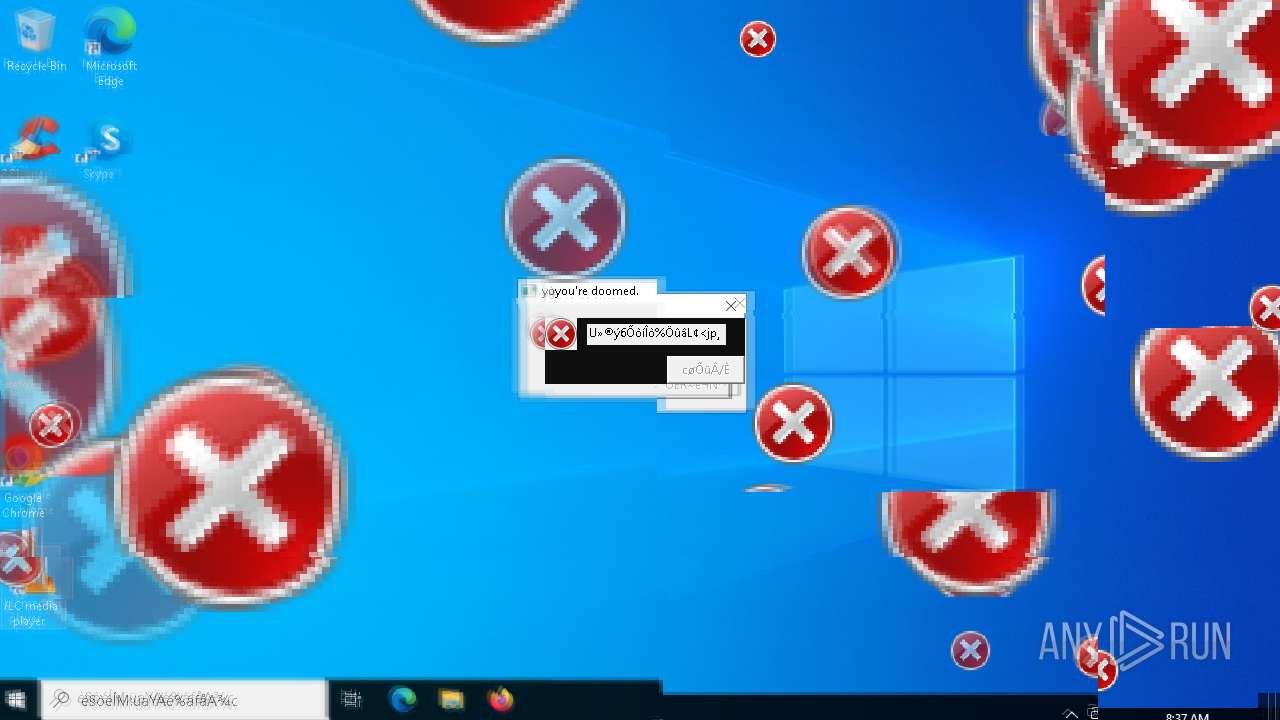
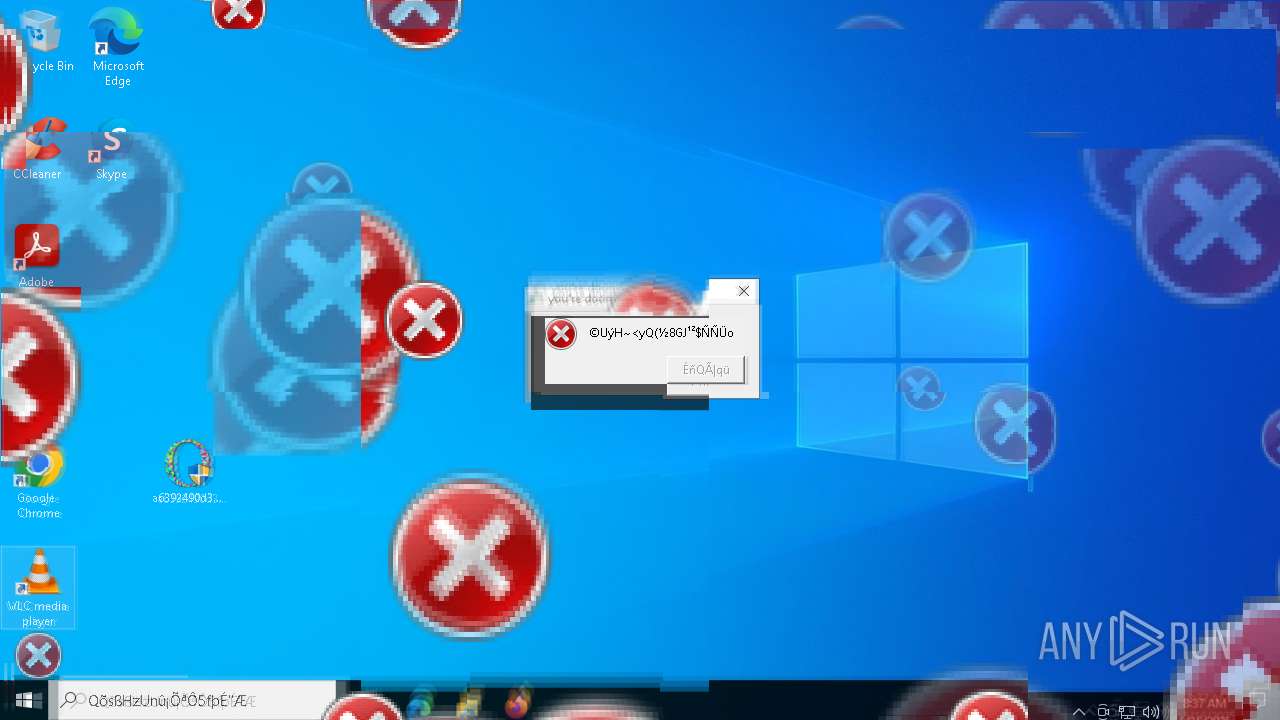
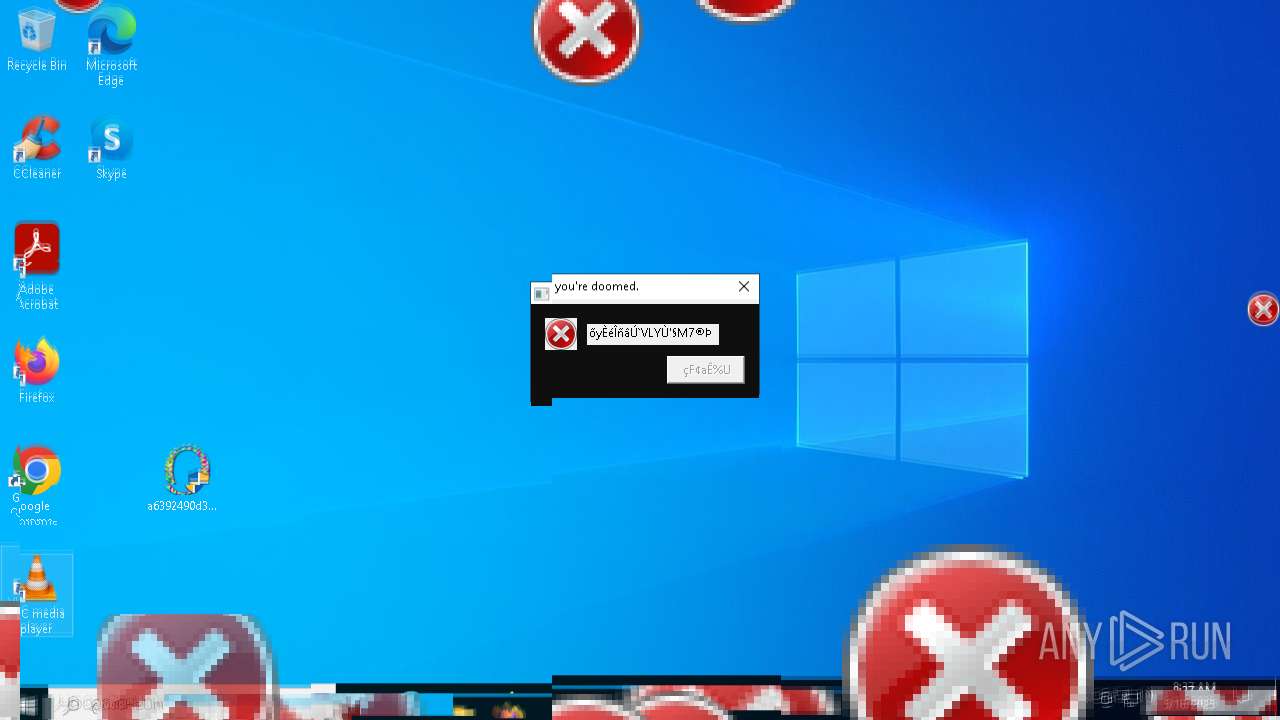
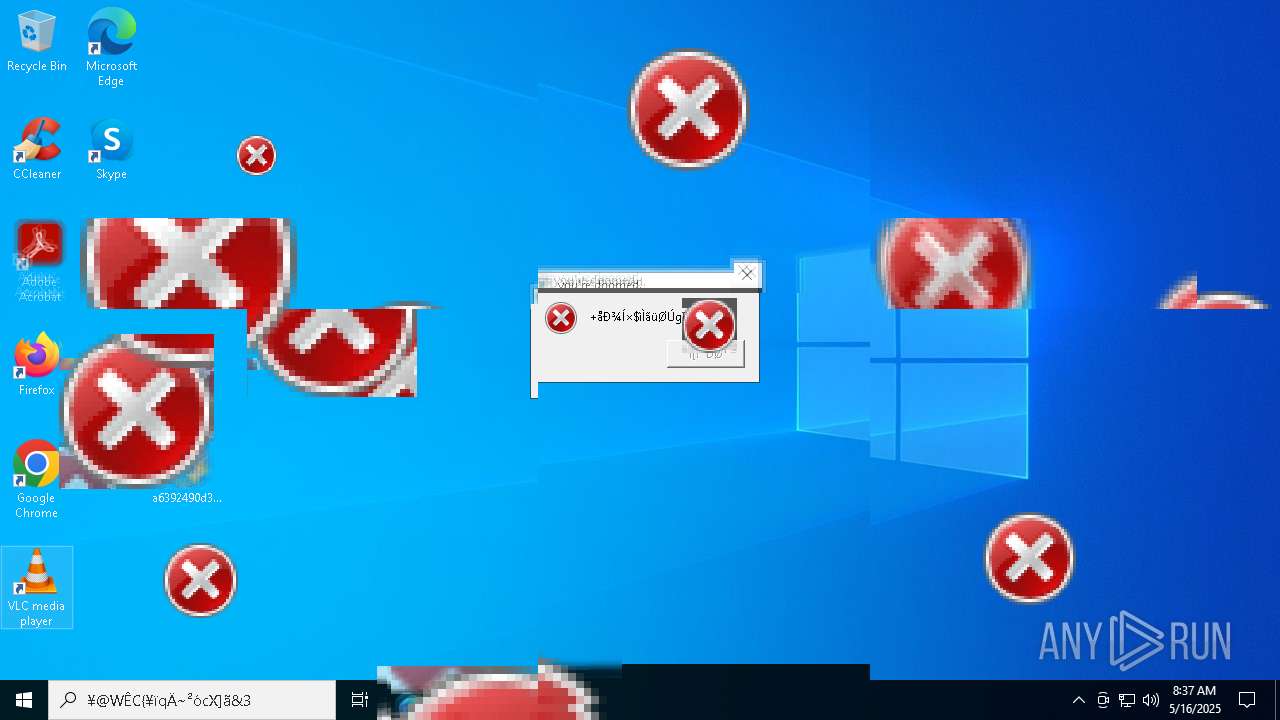
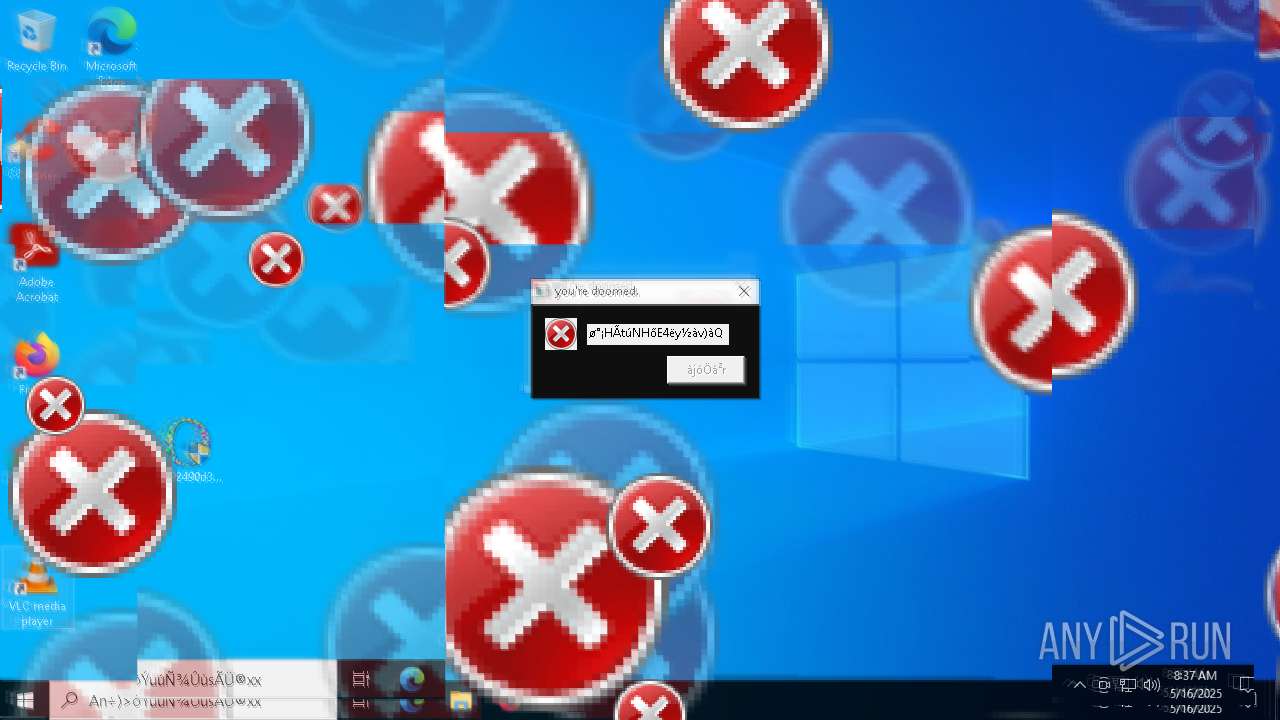
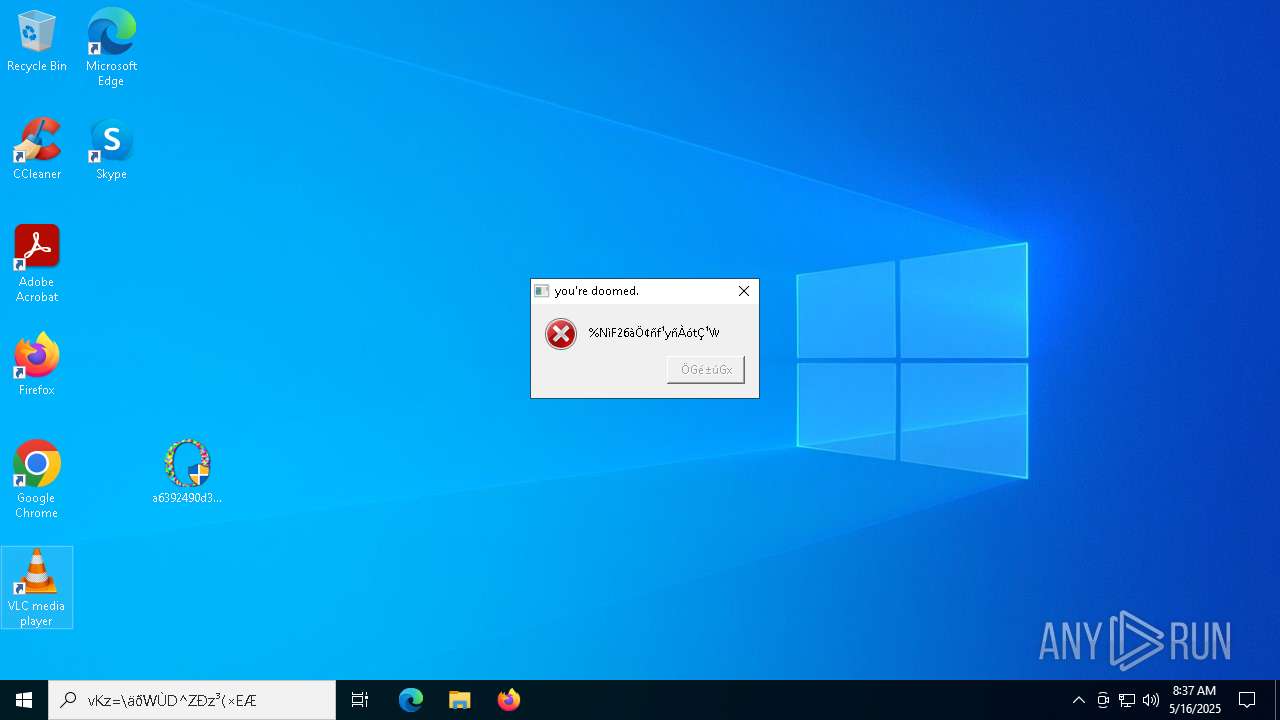
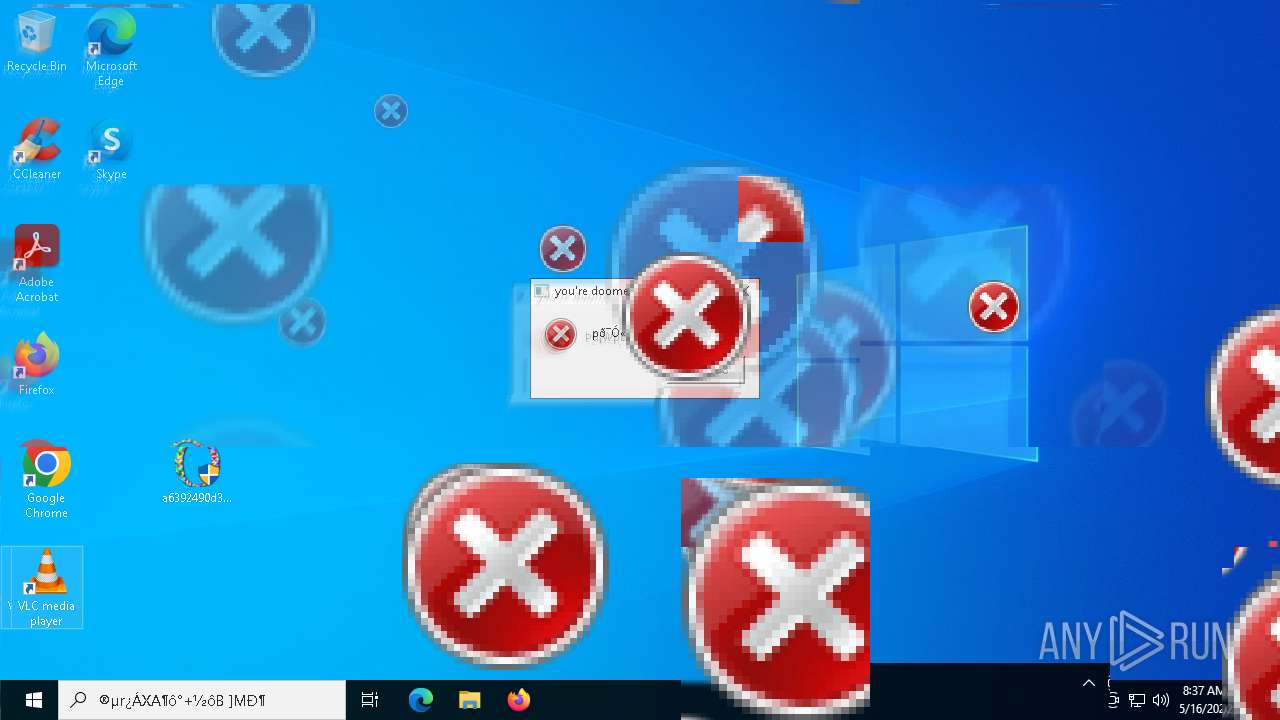
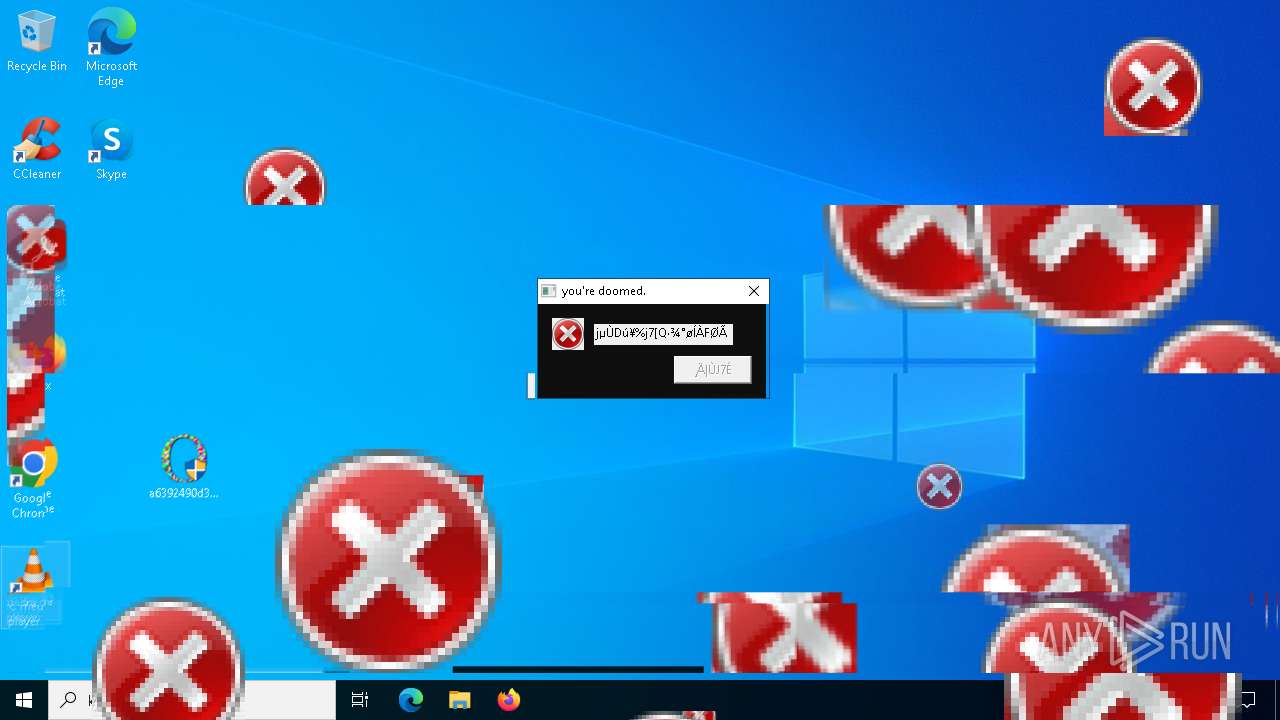
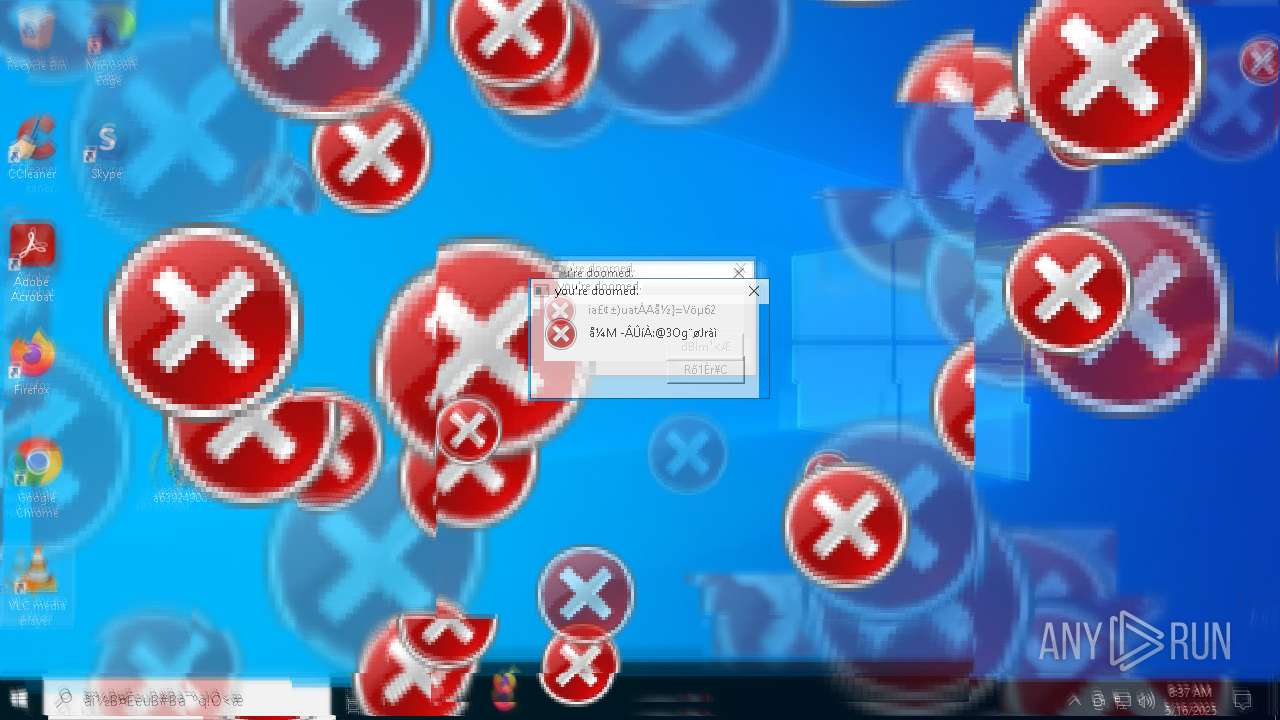
MALICIOUS
DISKWRITER has been found (auto)
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
SUSPICIOUS
Reads the date of Windows installation
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 7808)
- cmd.exe (PID: 7772)
Reads security settings of Internet Explorer
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
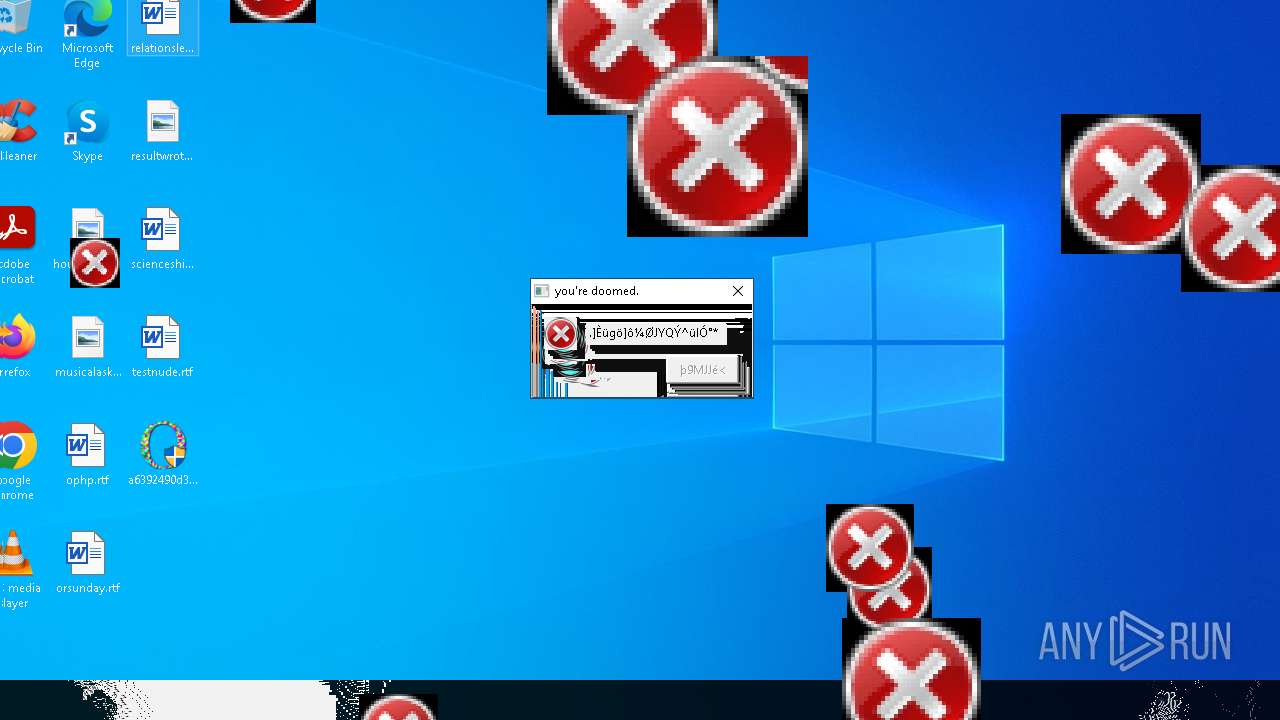
There is functionality for taking screenshot (YARA)
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Starts CMD.EXE for commands execution
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5544)
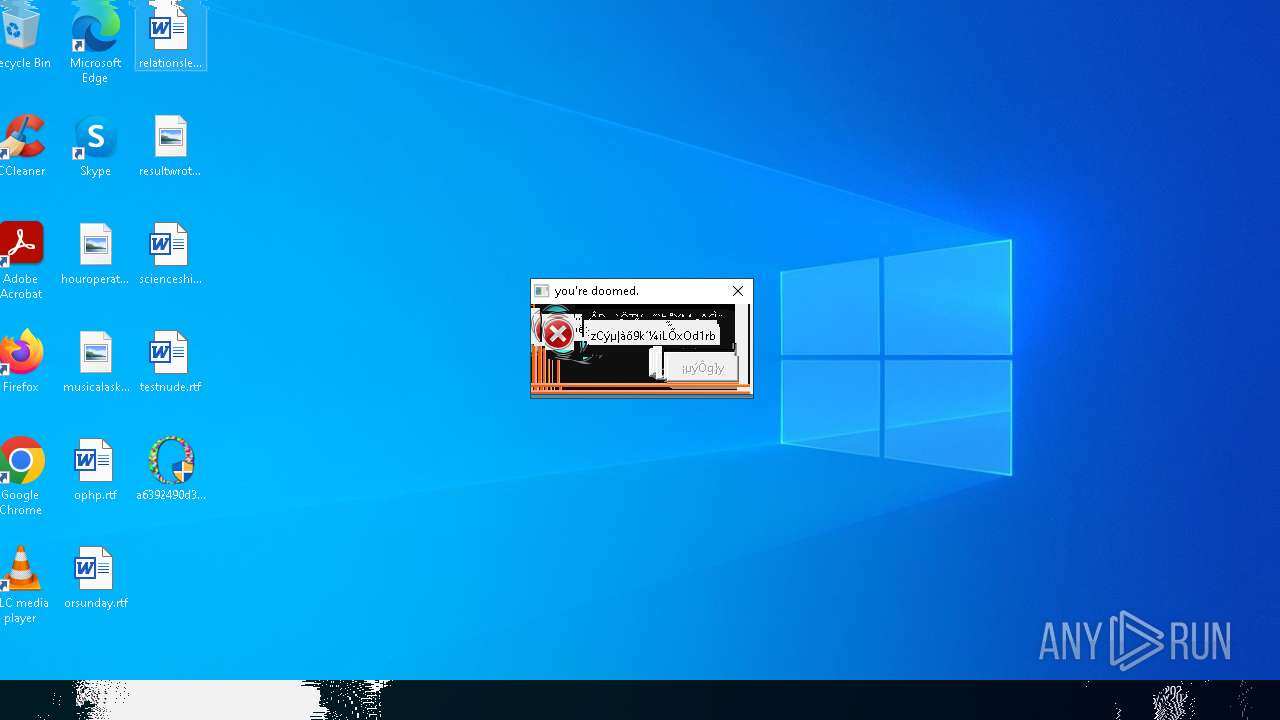
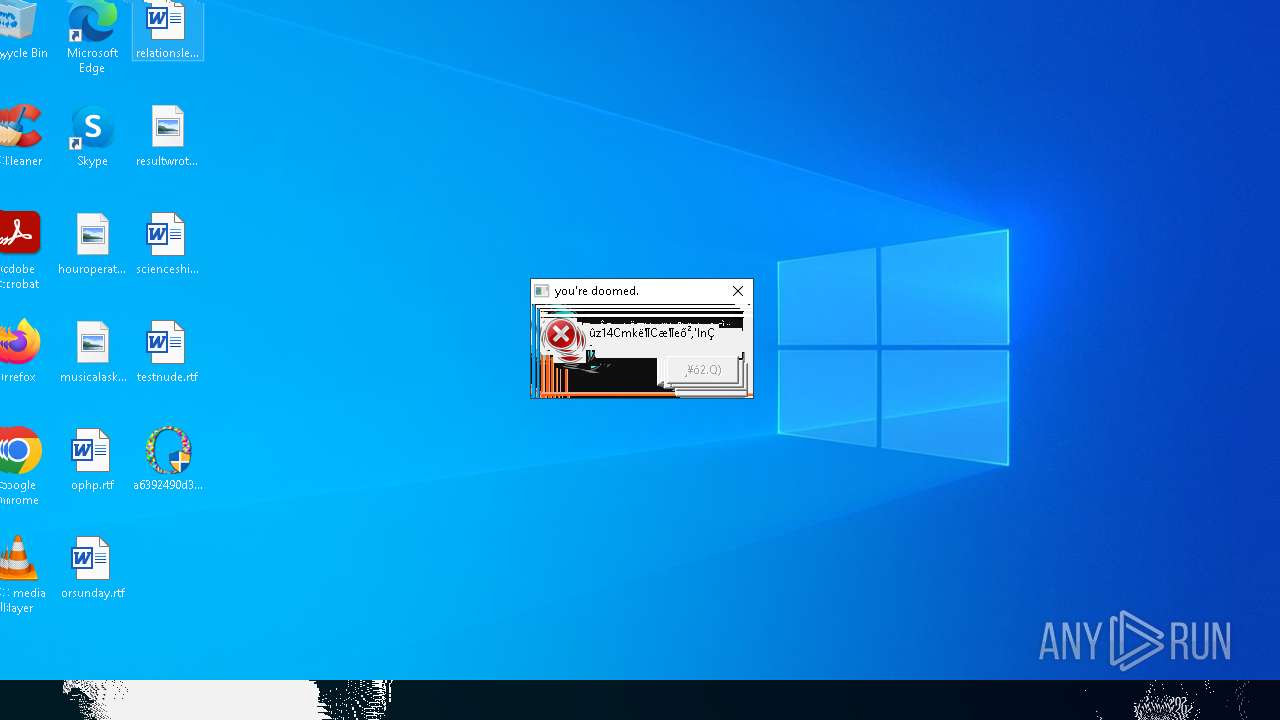
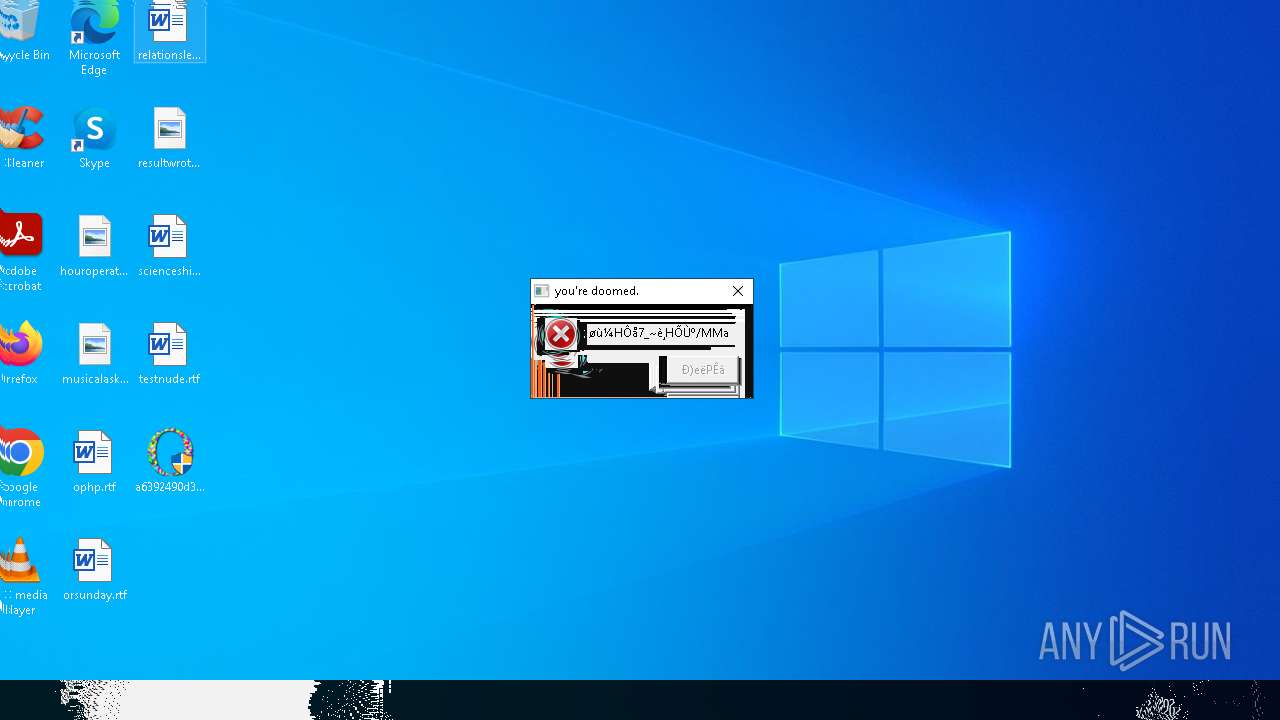
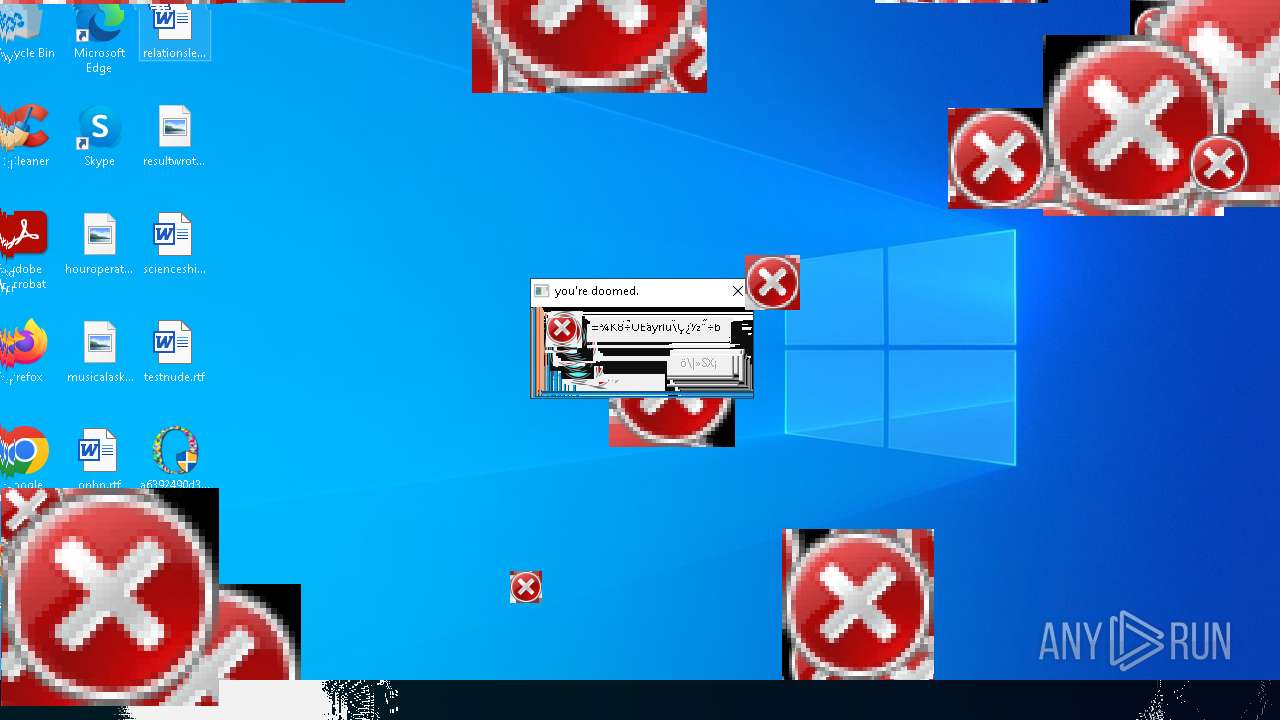
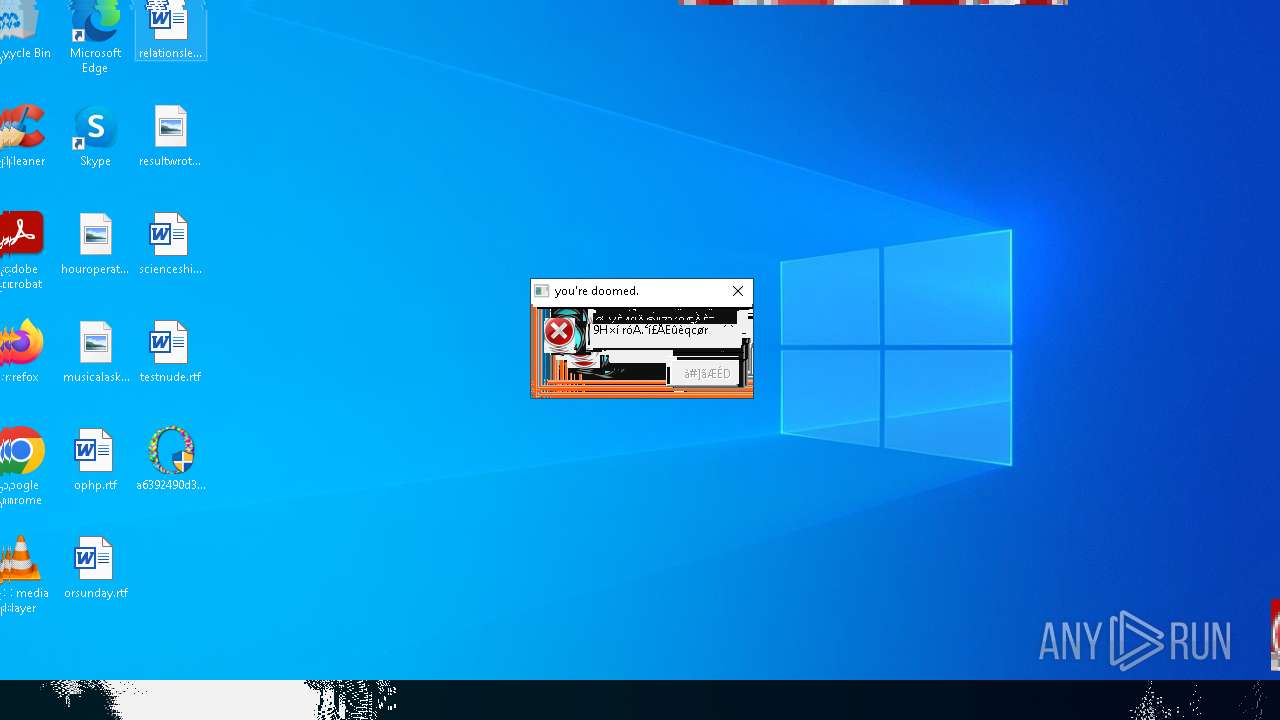
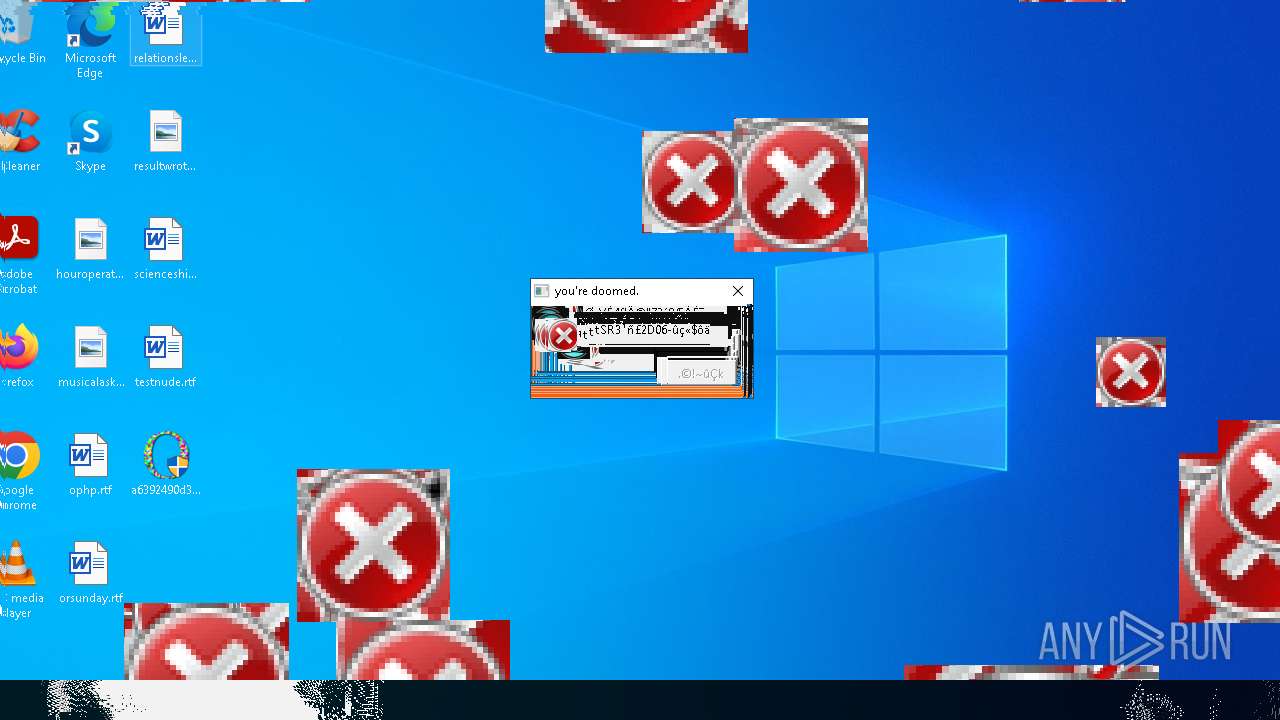
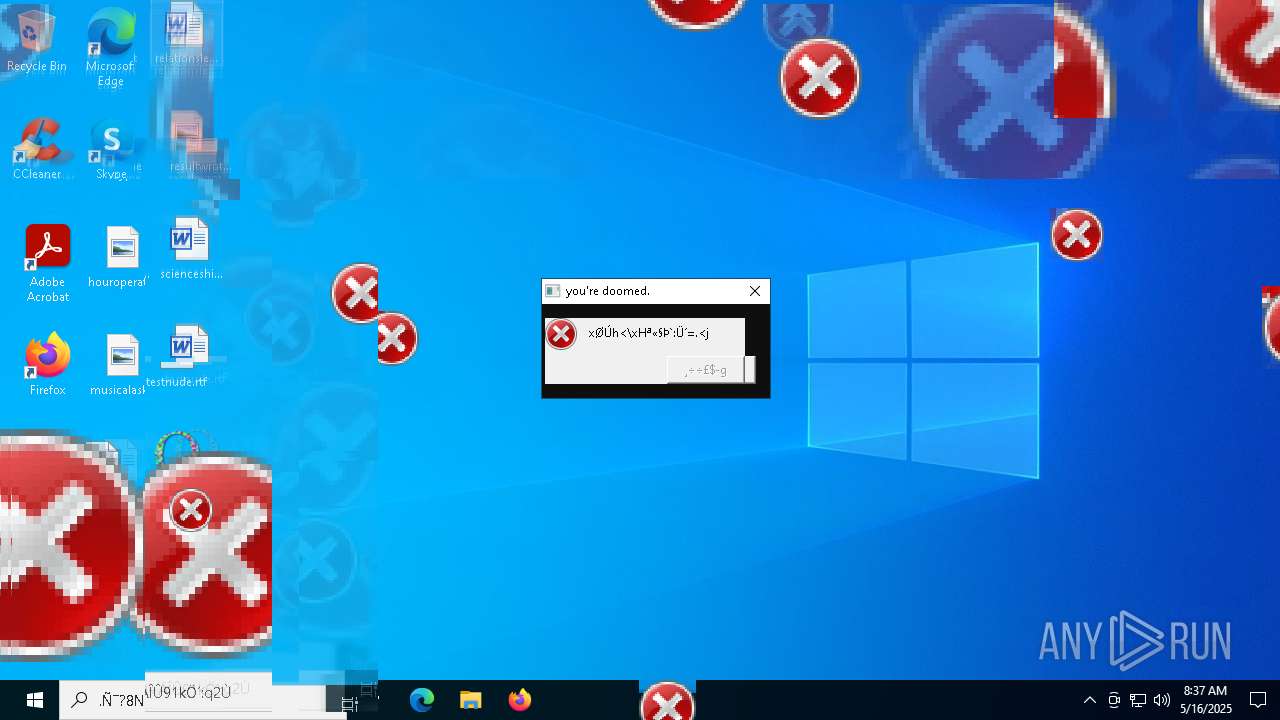
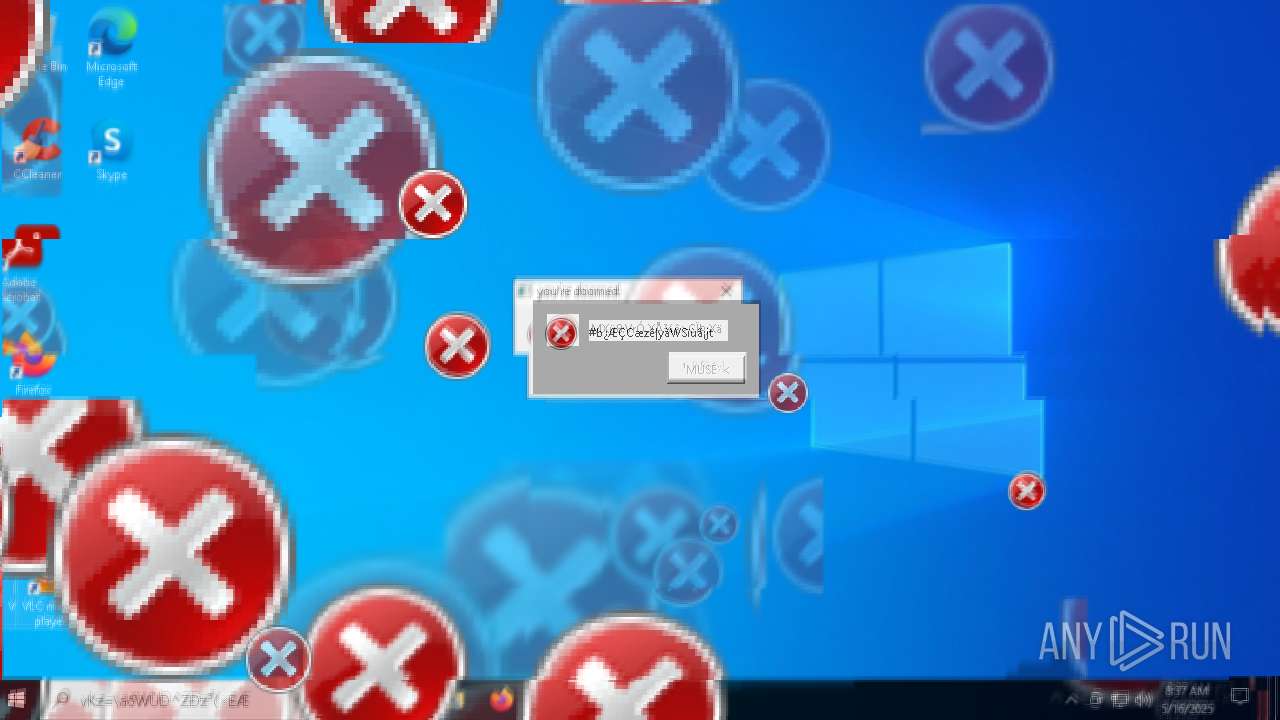
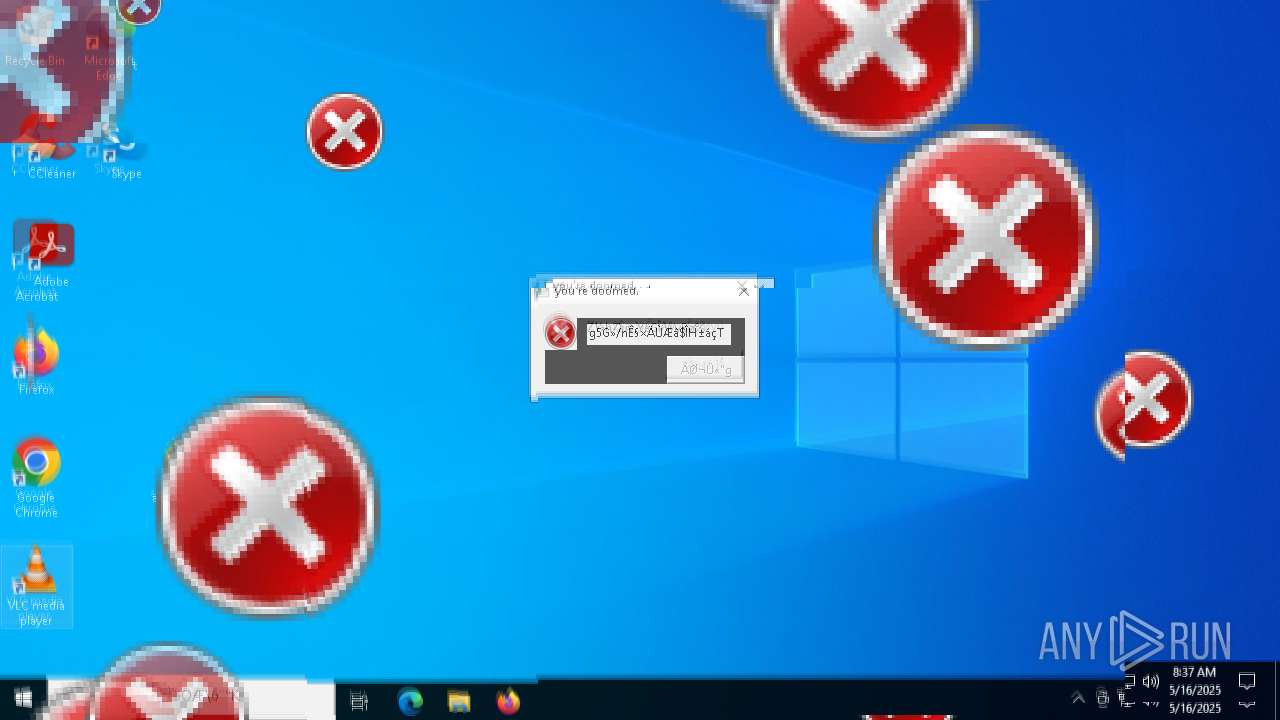
Executes application which crashes
- SearchApp.exe (PID: 5972)
- SearchApp.exe (PID: 7428)
- SearchApp.exe (PID: 7328)
INFO
Reads the computer name
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Checks supported languages
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Reads the machine GUID from the registry
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Process checks computer location settings
- a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe (PID: 7464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2068:09:08 20:36:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 29696 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9202 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
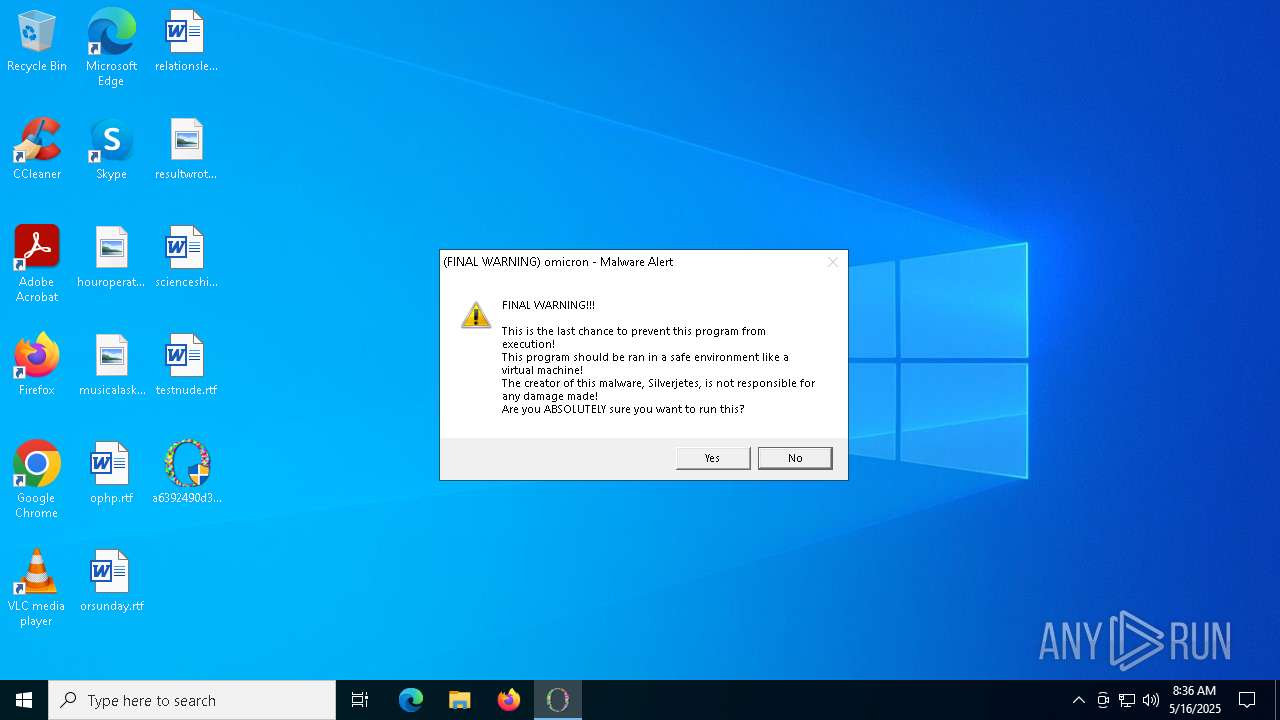
| Comments: | malware |
| CompanyName: | Silverjetes |
| FileDescription: | omicron.exe |
| FileVersion: | 1.0.0.0 |
| InternalName: | omicron.exe |
| LegalCopyright: | Copyright © Silverjetes, 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | omicron.exe |
| ProductName: | omicron.exe |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
181
Monitored processes
43
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "5892" "3704" "3644" "3700" "0" "0" "0" "0" "0" "0" "0" "0" | C:\Windows\System32\wermgr.exe | — | SearchApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "8084" "3492" "3380" "3524" "0" "0" "0" "0" "0" "0" "0" "0" | C:\Windows\System32\wermgr.exe | — | SearchApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "C:\Windows\System32\cmd.exe" /c del "%SYSTEMROOT%" /s /q | C:\Windows\System32\cmd.exe | — | a6392490d3b0163ff8f0f40d8734f09429f711234ca4af3a0add564171913359.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4220 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | takeown /f "C:\Program Files (x86)"*.* | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | reg delete HKLM\SYSTEM\CurrentControlSet\Services /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5020 | C:\WINDOWS\system32\WerFault.exe -u -p 7328 -s 2776 | C:\Windows\System32\WerFault.exe | — | SearchApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 356
Read events
23 163
Write events
420
Delete events
2 773
Modification events
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Data\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Networking\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Networking 4.0.0.0\Linkage |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Networking 4.0.0.0\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Networking 4.0.0.0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET Data Provider for Oracle\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET Data Provider for SqlServer\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET Memory Cache 4.0\Linkage |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET Memory Cache 4.0\Performance |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4620) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET Memory Cache 4.0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
16
Text files
49
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7428 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\TempState\CortanaUnifiedTileModelCache.dat~RF11688b.TMP | — | |
MD5:— | SHA256:— | |||
| 7832 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Microsoft.Window_39fd55c4ee7446c589da1ab3e959162ed453fcb_ce03743e_3456620f-23cc-46e6-b5dd-055b21bb28fa\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7832 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\SearchApp.exe.7428.dmp | — | |
MD5:— | SHA256:— | |||
| 8084 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133918582594646542.txt~RF117b19.TMP | — | |
MD5:— | SHA256:— | |||
| 1196 | cmd.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.001.etl | etl | |
MD5:7B6AE1FC101B8E2ECC57A4363F6CC737 | SHA256:946C66C377D9DFDB0F664D5AD6DE4B415B870AD0D4A334576235EC787ECBF8D4 | |||
| 8084 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{94c1599c-2780-486e-87c9-c9c3043c5884}\apps.csg | binary | |
MD5:5475132F1C603298967F332DC9FFB864 | SHA256:0B0AF873EF116A51FC2A2329DC9102817CE923F32A989C7A6846B4329ABD62CD | |||
| 8084 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{94c1599c-2780-486e-87c9-c9c3043c5884}\settings.csg | binary | |
MD5:411D53FC8E09FB59163F038EE9257141 | SHA256:1844105BB927DBC405685D3BF5546BE47FA2FC5846B763C9F2BA2B613EC6BC48 | |||
| 8084 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\GEH\POF-8084.dmp | — | |
MD5:— | SHA256:— | |||
| 7428 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\TempState\CortanaUnifiedTileModelCache.dat | binary | |
MD5:8E240A454B23534A5D4E20837AD42FFE | SHA256:98DFD3CFF9FD85E1724D0689EBD908A6B04A2A75F653182A00818A01C386A45A | |||
| 7832 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6EA7.tmp.xml | xml | |
MD5:2E2B59A4E79391A9F3CFC5972DEA18C9 | SHA256:06669EB6677B8C48029994F68575C362991F26C7A2E3012B172AEA471282FDFE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |