| File name: | ShiginimaSE_v4400.zip |
| Full analysis: | https://app.any.run/tasks/9b59534d-9b41-4b9b-b4ab-94f7aa764f90 |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2020, 00:39:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 93BE8F75303B0987390E2B59F606CF88 |
| SHA1: | 61CB768106E6E449158EBB2608AD1327402D9FEC |
| SHA256: | A62E5272A29A926BC236EC2FA4F06D28600006751247039EB18F50FE95038A22 |
| SSDEEP: | 196608:C+ILEa1EQ+vazOBp5W5pjVtB3NafE/Ir907J3nmNuTOt76AFV3Ng7whe:fIIXQ+vUmp5YVSrqVmftXFVdg7wE |
MALICIOUS
Application was dropped or rewritten from another process
- Shiginima Launcher SE v4400.exe (PID: 3680)
Loads dropped or rewritten executable
- javaw.exe (PID: 2548)
SUSPICIOUS
Executes JAVA applets
- Shiginima Launcher SE v4400.exe (PID: 3680)
- javaw.exe (PID: 2808)
Application launched itself
- javaw.exe (PID: 2808)
Executable content was dropped or overwritten
- javaw.exe (PID: 2808)
Creates files in the user directory
- javaw.exe (PID: 2548)
- javaw.exe (PID: 2808)
INFO
Manual execution by user
- Shiginima Launcher SE v4400.exe (PID: 3680)
Dropped object may contain Bitcoin addresses
- javaw.exe (PID: 2808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:01:31 18:08:17 |
| ZipCRC: | 0xa15bfea4 |
| ZipCompressedSize: | 1626 |
| ZipUncompressedSize: | 4188 |
| ZipFileName: | Changelog.txt |
Total processes
42
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
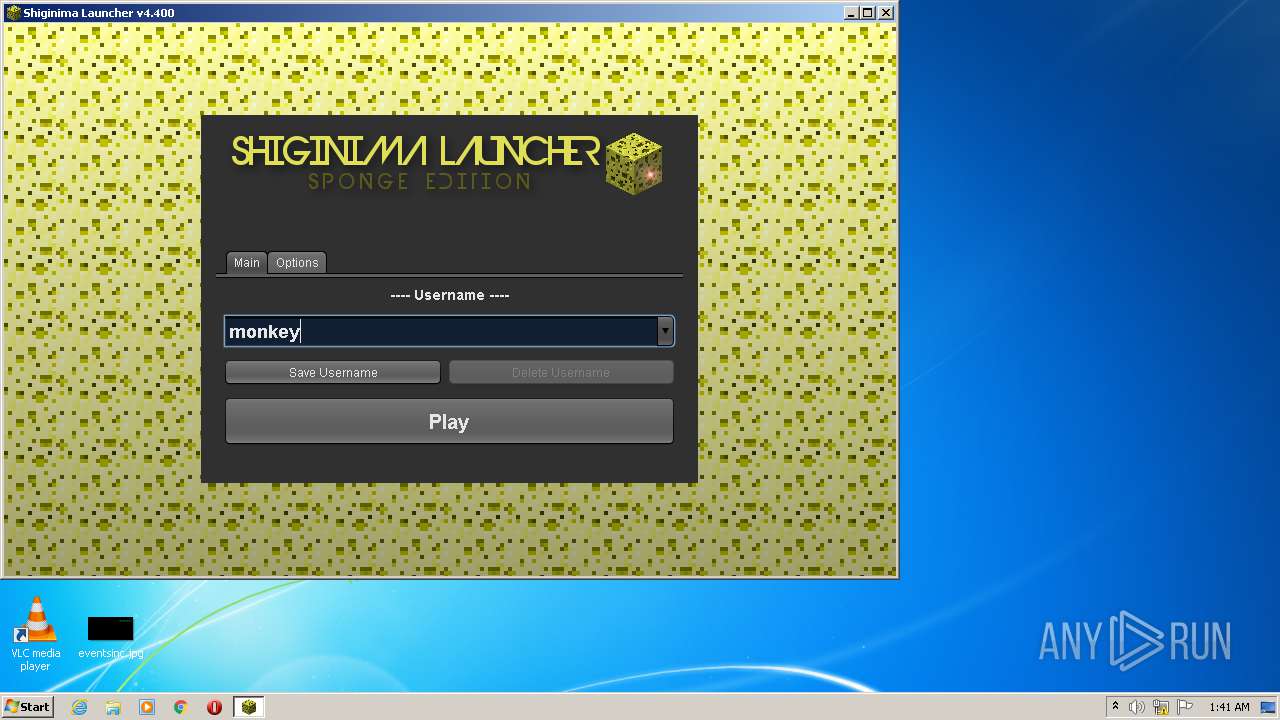
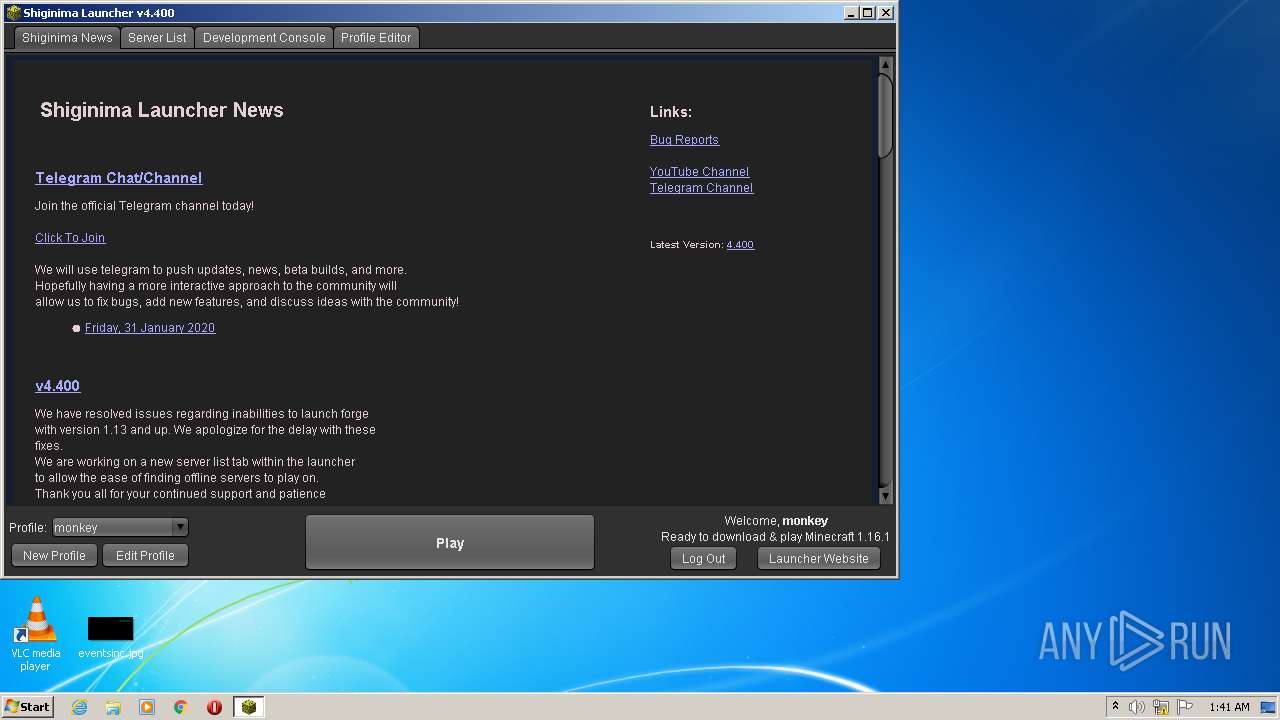
| 2548 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -Xmx512M -XX:+UseConcMarkSweepGC -XX:+CMSIncrementalMode -XX:-UseAdaptiveSizePolicy -Xmn128M -XX:HeapDumpPath=MojangTricksIntelDriversForPerformance_javaw.exe_minecraft.exe.heapdump -Xss1M -Djava.library.path=C:\Users\admin\AppData\Roaming\.minecraft\versions\1.16.1\1.16.1-natives-131551465943 -Dminecraft.launcher.brand=java-minecraft-launcher "-Dminecraft.launcher.version=Shiginima Launcher v4.400" -cp C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\patchy\1.1\patchy-1.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\oshi-project\oshi-core\1.1\oshi-core-1.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\dev\jna\jna\4.4.0\jna-4.4.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\dev\jna\platform\3.4.0\platform-3.4.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\ibm\icu\icu4j\66.1\icu4j-66.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\javabridge\1.0.22\javabridge-1.0.22.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\sf\jopt-simple\jopt-simple\5.0.3\jopt-simple-5.0.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\io\netty\netty-all\4.1.25.Final\netty-all-4.1.25.Final.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\guava\guava\21.0\guava-21.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-lang3\3.5\commons-lang3-3.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-io\commons-io\2.5\commons-io-2.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-codec\commons-codec\1.10\commons-codec-1.10.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jinput\jinput\2.0.5\jinput-2.0.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jutils\jutils\1.0.0\jutils-1.0.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\brigadier\1.0.17\brigadier-1.0.17.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\datafixerupper\3.0.25\datafixerupper-3.0.25.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\code\gson\gson\2.8.0\gson-2.8.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\authlib\1.6.25\authlib-1.6.25.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-compress\1.8.1\commons-compress-1.8.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpclient\4.3.3\httpclient-4.3.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-logging\commons-logging\1.1.3\commons-logging-1.1.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpcore\4.3.2\httpcore-4.3.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\it\unimi\dsi\fastutil\8.2.1\fastutil-8.2.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-api\2.8.1\log4j-api-2.8.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-core\2.8.1\log4j-core-2.8.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl\3.2.2\lwjgl-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-jemalloc\3.2.2\lwjgl-jemalloc-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-openal\3.2.2\lwjgl-openal-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-opengl\3.2.2\lwjgl-opengl-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-glfw\3.2.2\lwjgl-glfw-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-stb\3.2.2\lwjgl-stb-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-tinyfd\3.2.2\lwjgl-tinyfd-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\text2speech\1.11.3\text2speech-1.11.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\versions\1.16.1\1.16.1.jar net.minecraft.client.main.Main --username monkey --version 1.16.1 --gameDir C:\Users\admin\AppData\Roaming\.minecraft --assetsDir C:\Users\admin\AppData\Roaming\.minecraft\assets --assetIndex 1.16 --uuid d0763edaa9d93d2a9516280e9044d885 --accessToken d0763eda-a9d9-3d2a-9516-280e9044d885 --userType mojang --versionType release | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2808 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -classpath "C:\Users\admin\Desktop\Shiginima Launcher SE v4400.exe" net.mc.main.Main | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | Shiginima Launcher SE v4400.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\ShiginimaSE_v4400.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\Shiginima Launcher SE v4400.exe" | C:\Users\admin\Desktop\Shiginima Launcher SE v4400.exe | — | explorer.exe | |||||||||||
User: admin Company: Shiginima Integrity Level: MEDIUM Description: Shiginima Launcher SE v4.400 Exit code: 0 Version: 4.400 Modules
| |||||||||||||||
Total events
362
Read events
334
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ShiginimaSE_v4400.zip | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2896) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
37
Suspicious files
22
Text files
316
Unknown types
2 313
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2896 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2896.27206\windows\Shiginima Launcher SE v4400.exe | — | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8404922793923600196.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2040589127819941667.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio1661848046170027544.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio898994565063039099.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\versions\1.16.1\1.16.1.json | text | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_profiles.json | text | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\assets\indexes\1.16.json | text | |
MD5:— | SHA256:— | |||
| 2808 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\shig.inima | text | |
MD5:571CC0288E3F5DB4C85AE85DCD1C64CE | SHA256:36ED29282E1D008064F2C06952EDDABDF7C73B58E2BC5215A497AC4541BE6553 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2 536
TCP/UDP connections
43
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2808 | javaw.exe | GET | 200 | 198.252.102.62:80 | http://news.teamshiginima.com/ | US | html | 27.9 Kb | malicious |
2808 | javaw.exe | GET | 200 | 198.252.102.62:80 | http://servers.teamshiginima.com/ | US | html | 1.65 Kb | malicious |
2808 | javaw.exe | GET | 200 | 198.252.102.62:80 | http://servers.teamshiginima.com/placeholder.png | US | image | 643 b | malicious |
2808 | javaw.exe | GET | 200 | 198.252.102.62:80 | http://servers.teamshiginima.com/placeholder.png | US | image | 643 b | malicious |
2808 | javaw.exe | GET | 200 | 198.252.102.62:80 | http://servers.teamshiginima.com/placeholder.png | US | image | 643 b | malicious |
2808 | javaw.exe | GET | 301 | 198.252.102.62:80 | http://teamshiginima.com/launch.png | US | html | 706 b | whitelisted |
2808 | javaw.exe | GET | 200 | 143.204.201.30:80 | http://resources.download.minecraft.net/36/3660e743db2bbbcff0866d3f1e606882f1aeb6ac | US | ogg | 9.25 Kb | shared |
2808 | javaw.exe | GET | 200 | 143.204.201.30:80 | http://resources.download.minecraft.net/bc/bcc73584d83225383aaa6affce905392c96afe86 | US | ogg | 10.1 Kb | shared |
2808 | javaw.exe | GET | 200 | 143.204.201.30:80 | http://resources.download.minecraft.net/4a/4a2e3795ffd4d3aab0834b7e41903af3a8f7d197 | US | ogg | 7.82 Kb | shared |
2808 | javaw.exe | GET | 200 | 143.204.201.30:80 | http://resources.download.minecraft.net/6a/6a0e71c3d6e23485c1b0254ff0beed270bd4ba34 | US | ogg | 18.6 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2808 | javaw.exe | 198.252.102.62:80 | teamshiginima.com | SoftLayer Technologies Inc. | US | suspicious |
2808 | javaw.exe | 99.86.2.139:443 | launchermeta.mojang.com | AT&T Services, Inc. | US | unknown |
2808 | javaw.exe | 99.86.4.83:443 | libraries.minecraft.net | AT&T Services, Inc. | US | suspicious |
2808 | javaw.exe | 143.204.212.134:443 | launcher.mojang.com | — | US | unknown |
2808 | javaw.exe | 143.204.201.30:80 | resources.download.minecraft.net | — | US | suspicious |
2808 | javaw.exe | 143.204.201.32:80 | resources.download.minecraft.net | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
teamshiginima.com |
| whitelisted |
servers.teamshiginima.com |
| malicious |
news.teamshiginima.com |
| malicious |
launchermeta.mojang.com |
| whitelisted |
libraries.minecraft.net |
| shared |
launcher.mojang.com |
| whitelisted |
resources.download.minecraft.net |
| shared |