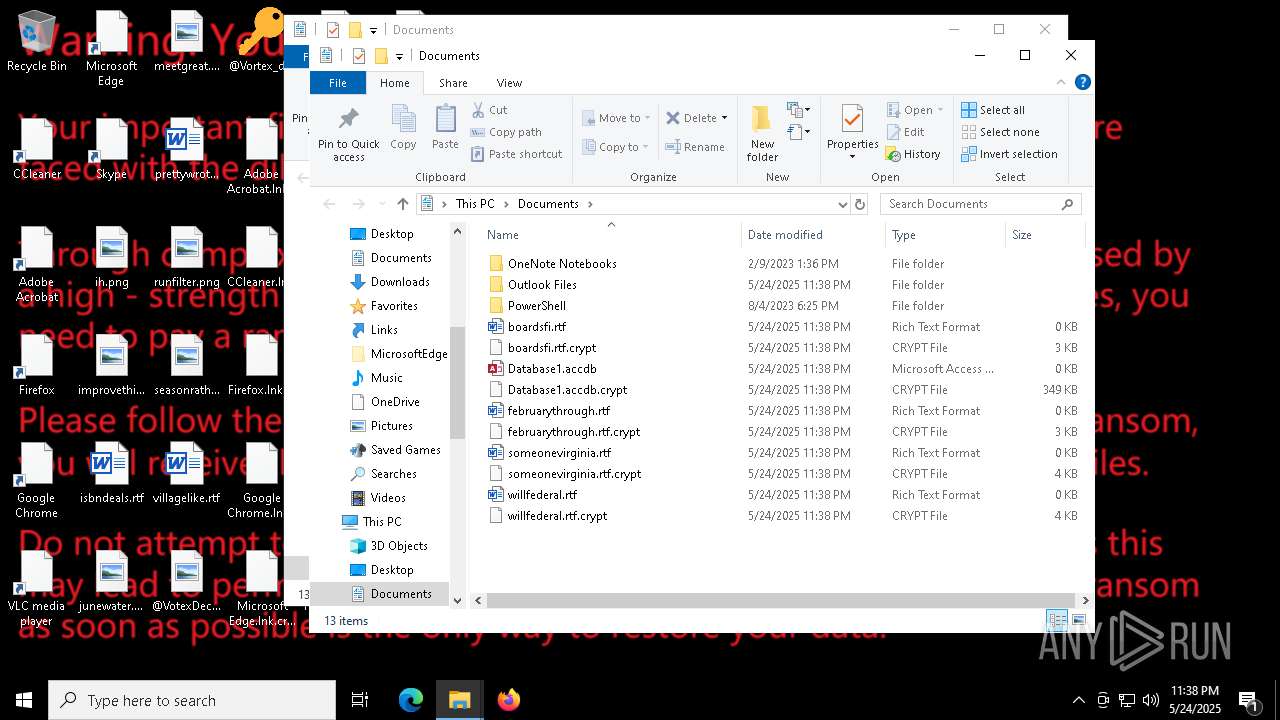
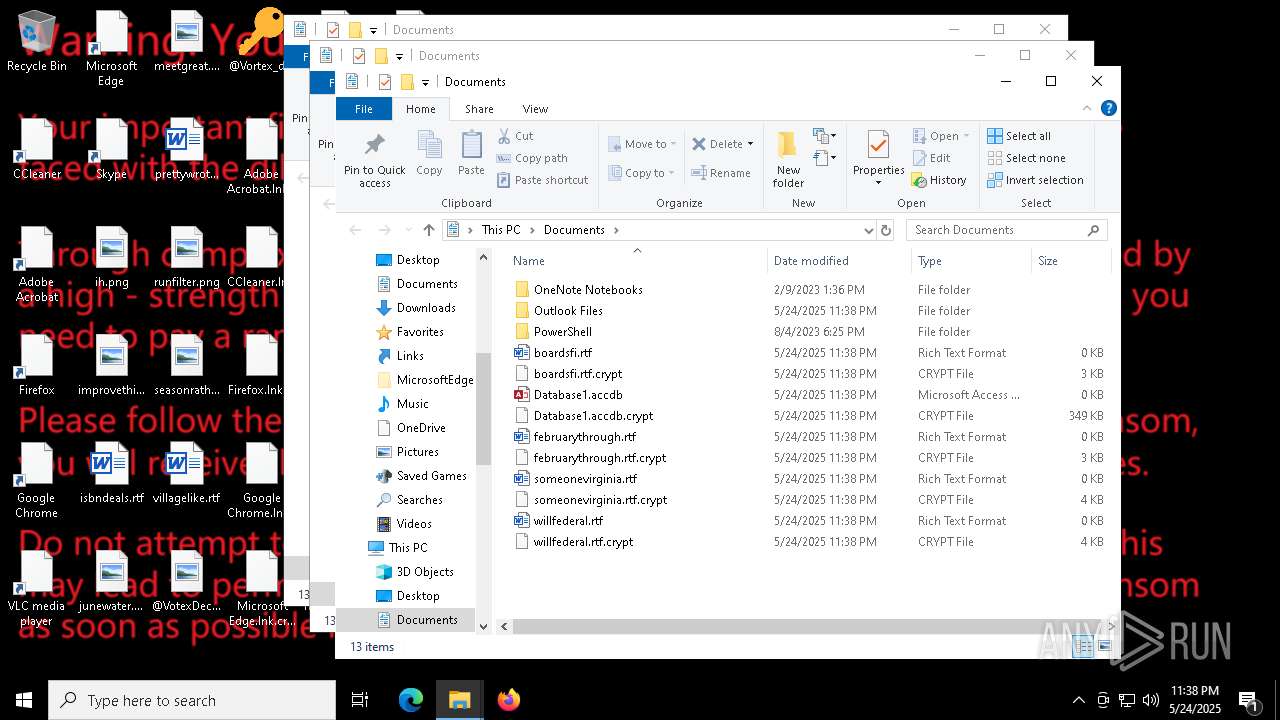
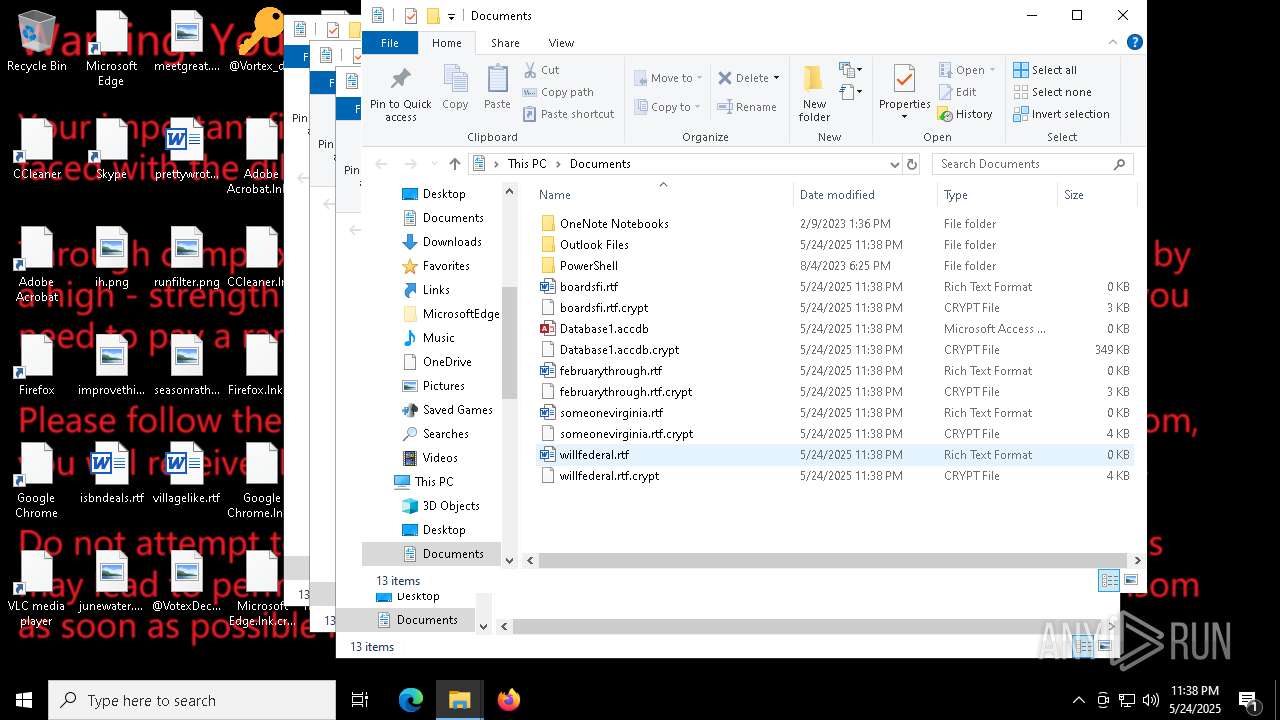
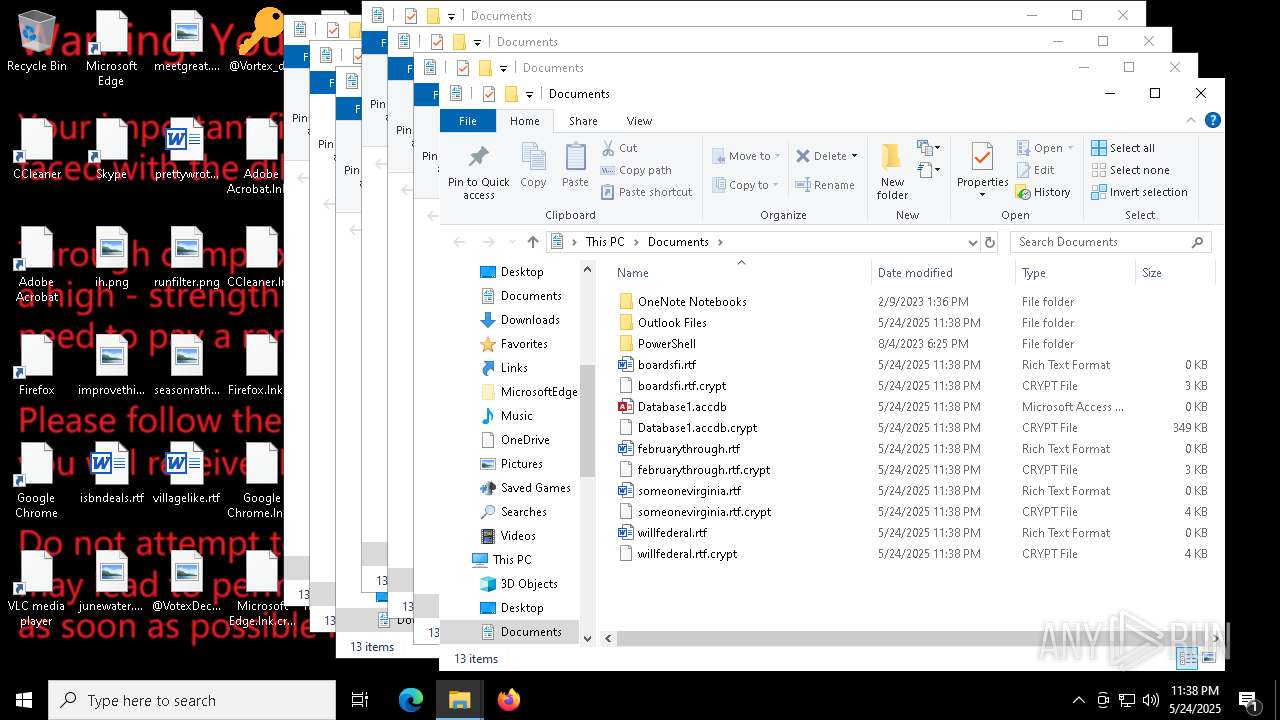
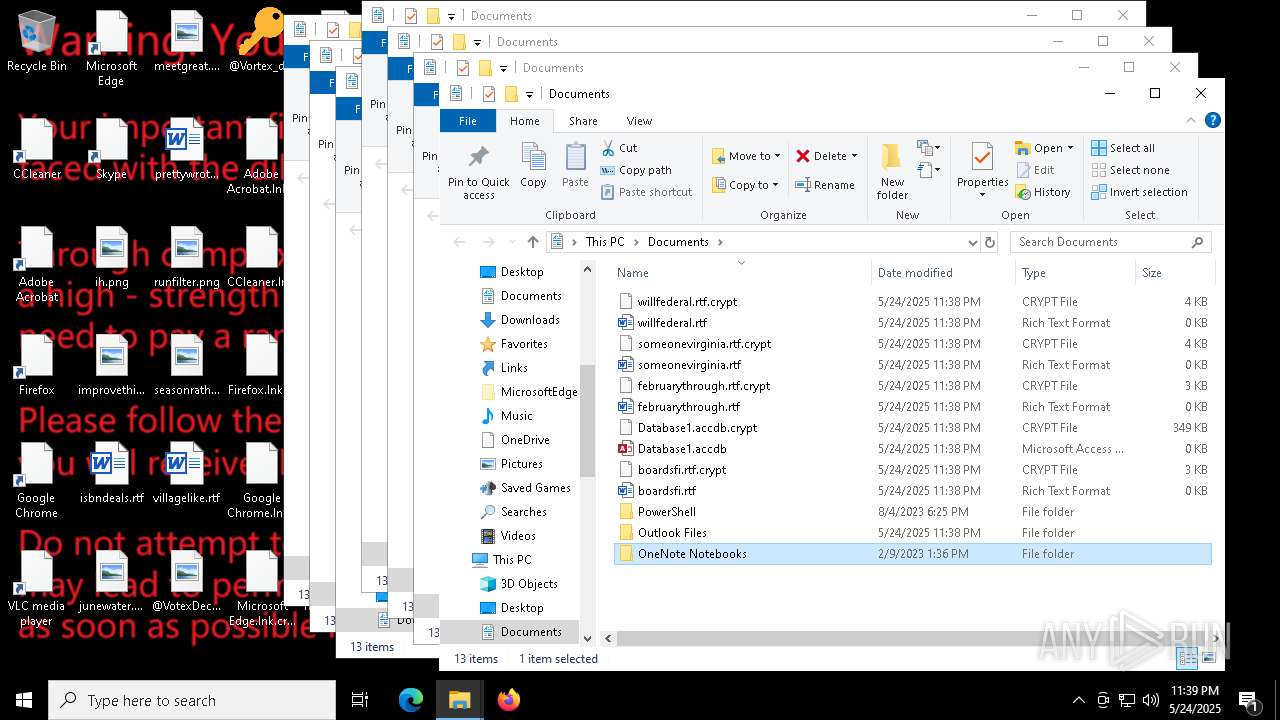
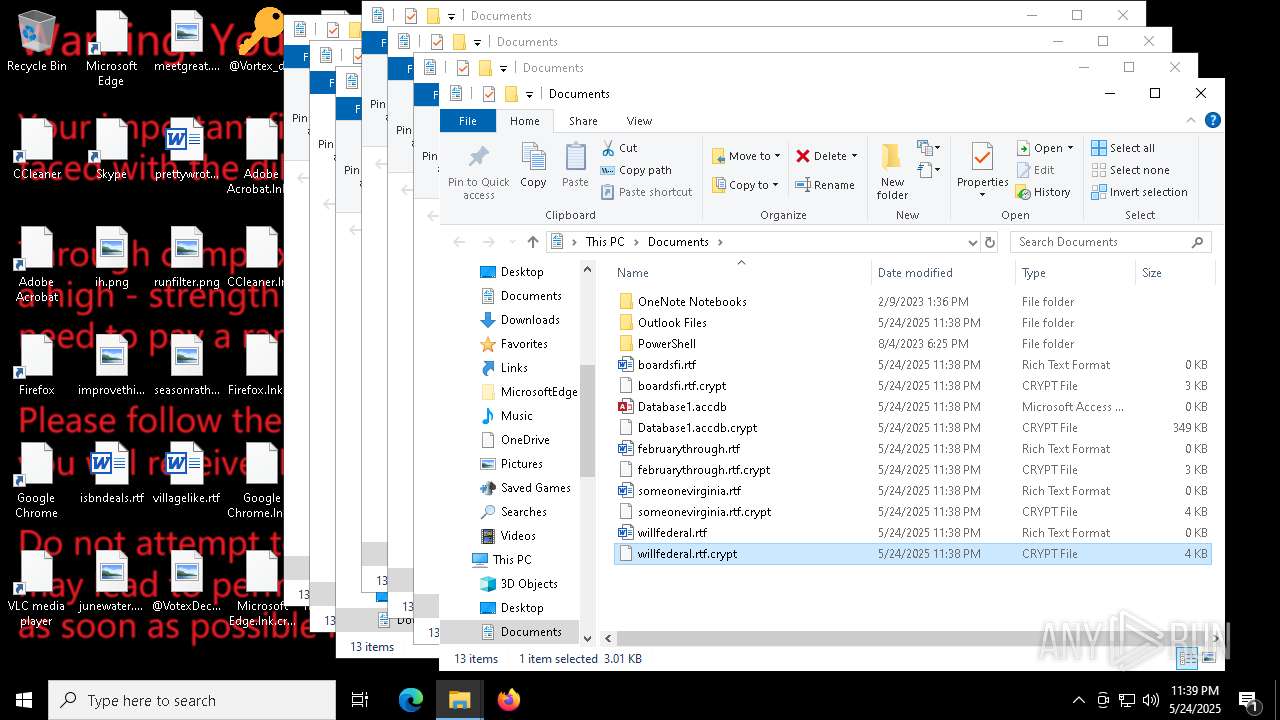
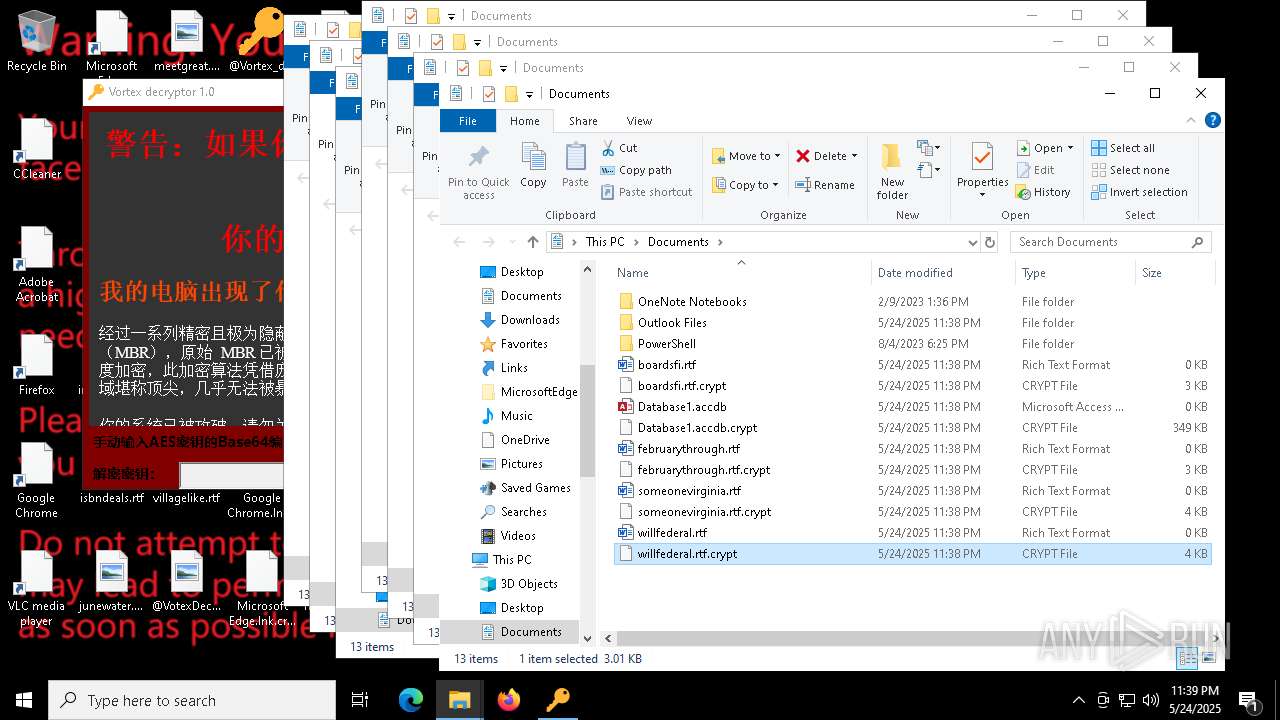
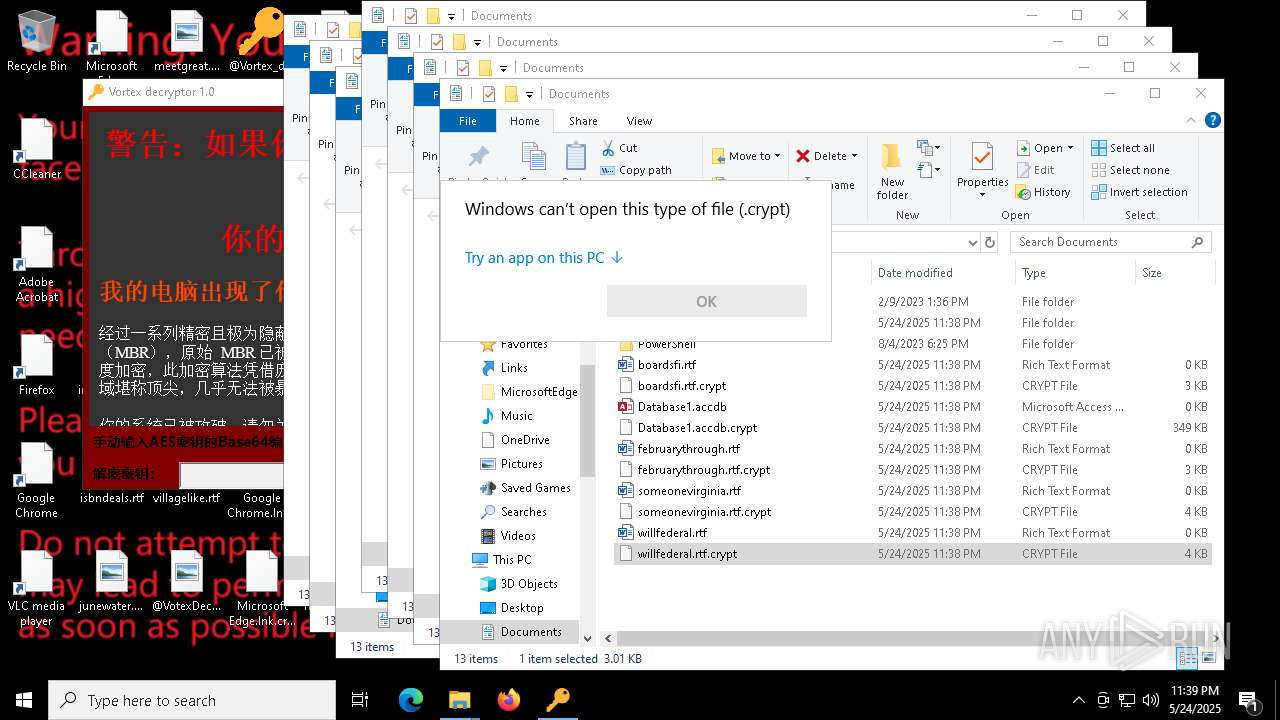
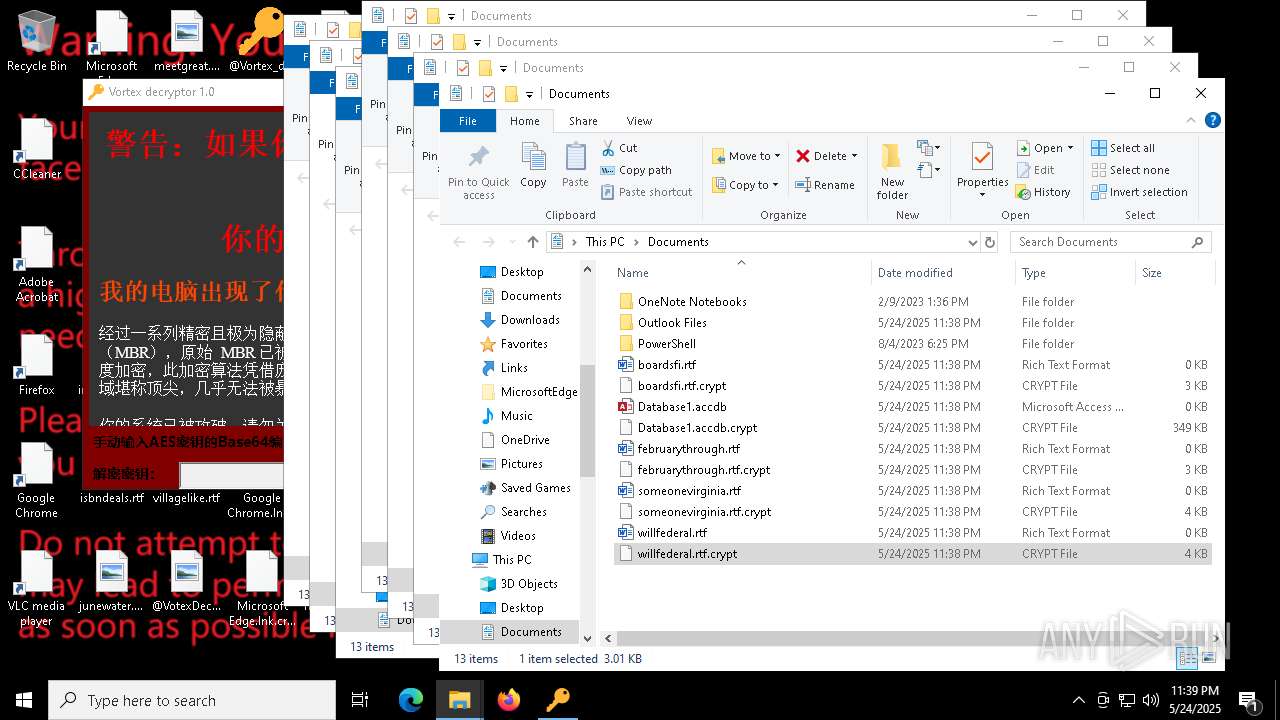
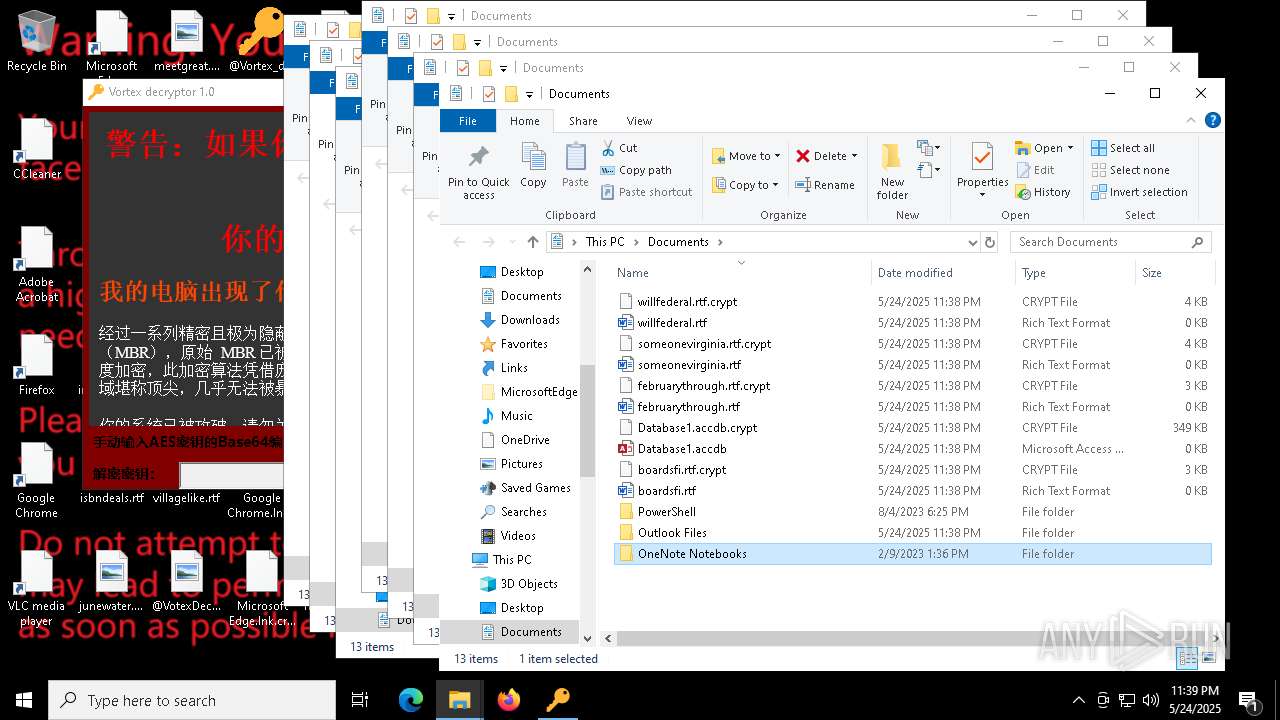
| File name: | a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3 |
| Full analysis: | https://app.any.run/tasks/f2be55f8-4594-40e2-93b1-c87a51f1997f |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 23:37:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | F0AA6259A6249EDC000EA1525EFBED27 |
| SHA1: | 14B2F93236AD2898CEF9951D27F602E929A79DC5 |
| SHA256: | A625ED01EF1EB71929A9CCCEFE6CE056BEF40E44B332F1F144CAFE552AF310A3 |
| SSDEEP: | 24576:bSEbsw1EageTz5zrNsbhjvLnxI3Ma5SXV7uzaN/uzHDeeNpg80IQTG6BznHg:bSEbsQlgeTz5zrNsbhjvLxI3Ma5SXV7L |
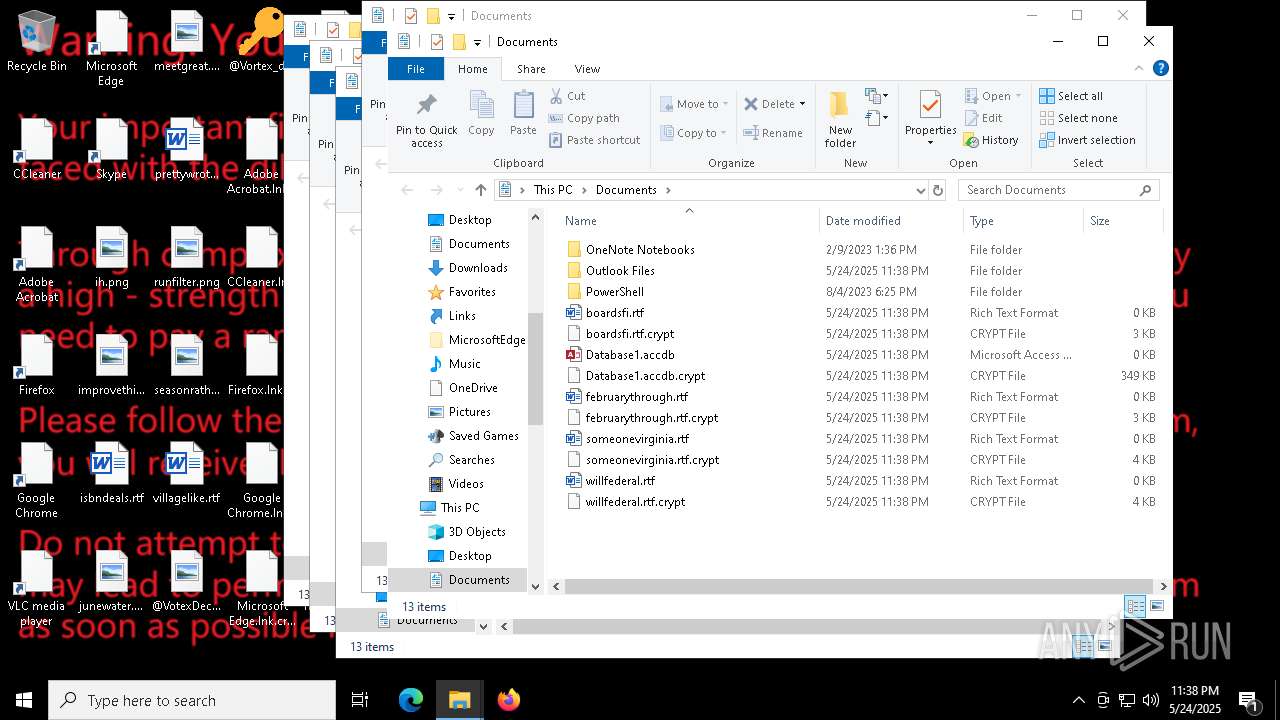
MALICIOUS
Starts CMD.EXE for self-deleting
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
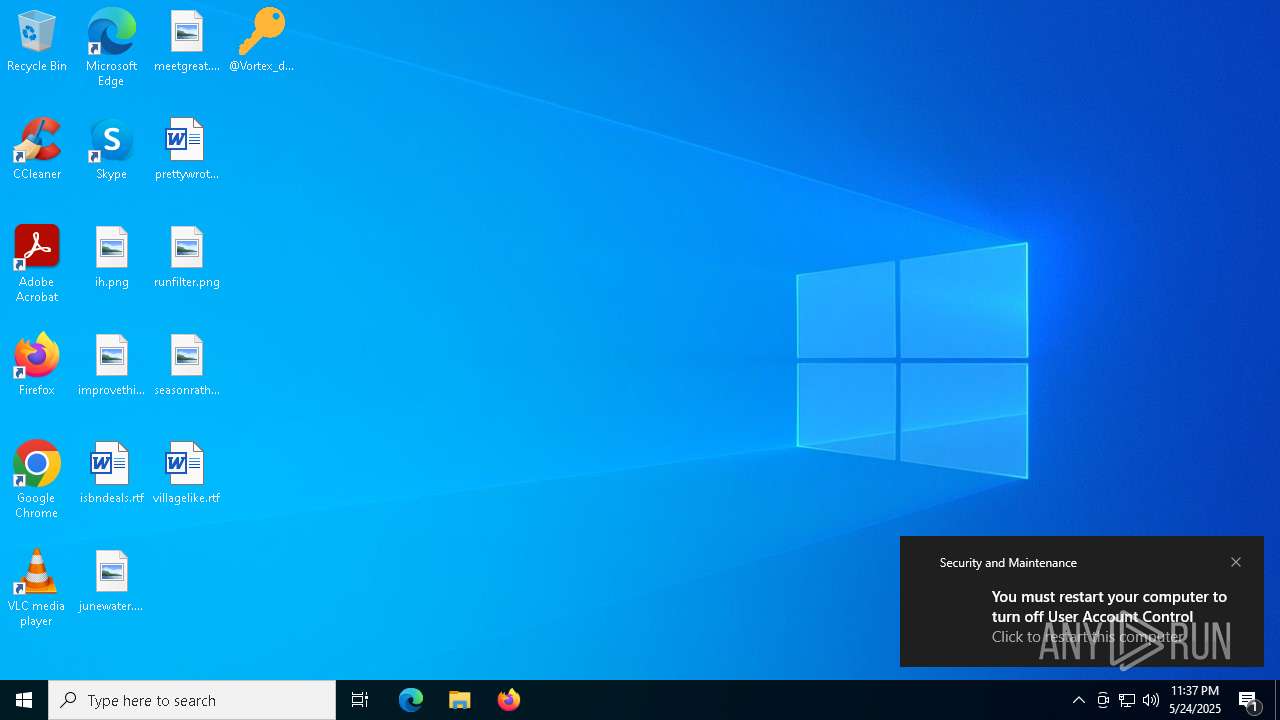
UAC/LUA settings modification
- rundll32.exe (PID: 7804)
Deletes shadow copies
- rundll32.exe (PID: 7804)
Disables task manager
- rundll32.exe (PID: 7804)
Changes the login/logoff helper path in the registry
- rundll32.exe (PID: 7804)
Antivirus name has been found in the command line (generic signature)
- icacls.exe (PID: 7412)
- takeown.exe (PID: 7456)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 7976)
Create files in the Startup directory
- rundll32.exe (PID: 7804)
SUSPICIOUS
Reads the date of Windows installation
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
Process drops legitimate windows executable
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
Reads security settings of Internet Explorer
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
- ShellExperienceHost.exe (PID: 7184)
Application launched itself
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
Creates file in the systems drive root
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
- rundll32.exe (PID: 7804)
Executable content was dropped or overwritten
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
- rundll32.exe (PID: 7804)
Uses RUNDLL32.EXE to load library
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
Starts CMD.EXE for commands execution
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7812)
Executes as Windows Service
- VSSVC.exe (PID: 8120)
Takes ownership (TAKEOWN.EXE)
- rundll32.exe (PID: 7804)
The process creates files with name similar to system file names
- rundll32.exe (PID: 7804)
Uses ICACLS.EXE to modify access control lists
- rundll32.exe (PID: 7804)
INFO
Reads the computer name
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
- ShellExperienceHost.exe (PID: 7184)
Checks supported languages
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
- ShellExperienceHost.exe (PID: 7184)
Process checks computer location settings
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7588)
The sample compiled with chinese language support
- a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe (PID: 7748)
Confuser has been detected (YARA)
- rundll32.exe (PID: 7804)
Creates files in the program directory
- rundll32.exe (PID: 7804)
Creates files or folders in the user directory
- rundll32.exe (PID: 7804)
Auto-launch of the file from Startup directory
- rundll32.exe (PID: 7804)
Create files in a temporary directory
- rundll32.exe (PID: 7804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:24 22:05:51+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 11 |
| CodeSize: | 634880 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.1 |
| ProductVersionNumber: | 2.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Windows 更新程序 |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft Windows Update |
| FileVersion: | 2.0.0.1 |
| InternalName: | vcryx.exe |
| LegalCopyright: | Copyright © 2025 Microsoft Corporation |
| LegalTrademarks: | Microsoft Corporation |
| OriginalFileName: | vcryx.exe |
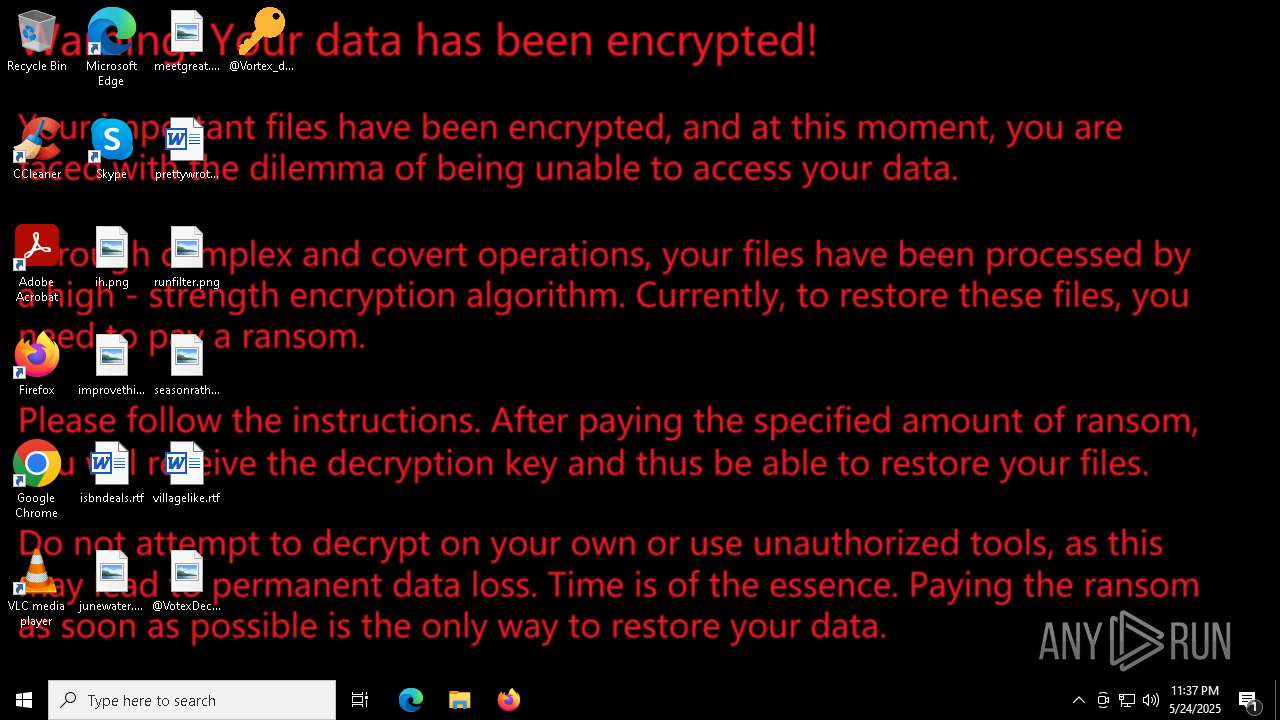
| ProductName: | VortexCryX |
| ProductVersion: | 2.0.0.1 |
| AssemblyVersion: | 2.0.0.1 |
Total processes
170
Monitored processes
42
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "icacls.exe" "C:\Windows\System32\ntoskrnl.exe" /grant Everyone:F | C:\Windows\System32\icacls.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "vssadmin.exe" delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "takeown.exe" /f "C:\Windows\System32\hal.dll" /A | C:\Windows\System32\takeown.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "takeown.exe" /f "C:\Windows\System32\ntoskrnl.exe" /A | C:\Windows\System32\takeown.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | "takeown.exe" /f "C:\Windows\System32\mmc.exe" /A | C:\Windows\System32\takeown.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 937
Read events
61 844
Write events
33
Delete events
60
Modification events
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | RestrictRun |
Value: 1 | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | rundll32.exe |
Value: rundll32.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | msedge.exe |
Value: msedge.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | WeChat.exe |
Value: WeChat.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | shutdown.exe |
Value: shutdown.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | ReAgentc.exe |
Value: ReAgentc.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | Rundl132.exe |
Value: Rundl132.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | @Vortex_decryptor.exe |
Value: @Vortex_decryptor.exe | |||
| (PID) Process: | (7804) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\RestrictRun |
| Operation: | write | Name: | notepad.exe |
Value: notepad.exe | |||
Executable files
26
Suspicious files
4 703
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7976 | ReAgentc.exe | C:\Windows\System32\Recovery\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 7804 | rundll32.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 7804 | rundll32.exe | C:\Windows\System32\ntoskrnl.exe.crypt | — | |
MD5:— | SHA256:— | |||
| 7748 | a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe | C:\Windows\System32\vncy.dll | executable | |
MD5:E3B6CC3C498BBDA9DAA79A6B13FDB3D4 | SHA256:4DB7B61B130A3922C44FA0F7FE277FB5C0A13945E00133CF51CCD04FA8021B93 | |||
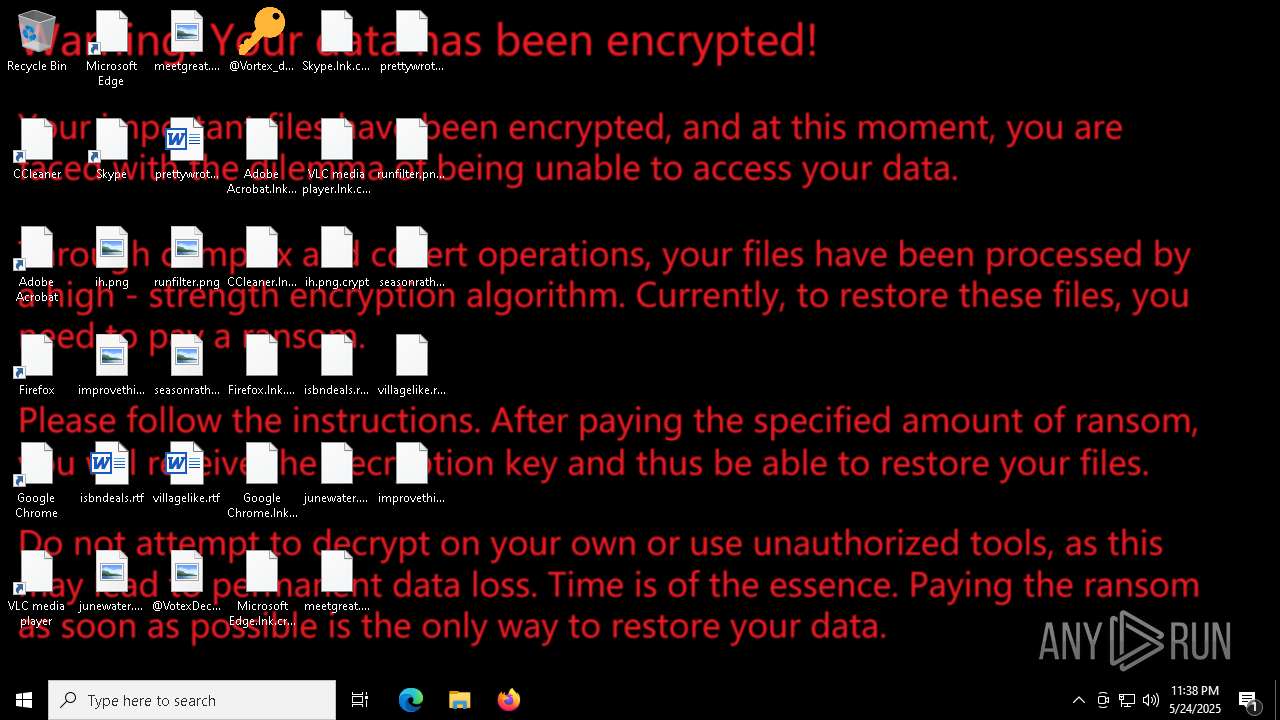
| 7804 | rundll32.exe | C:\Users\admin\Desktop\@Vortex_decryptor.exe | executable | |
MD5:11EB860092E385B1F86E7C95341FD1ED | SHA256:CDF3391C79A288054327C7CCCC1AE1B4C7953267ACAE2997F38220BABE6676BD | |||
| 7804 | rundll32.exe | C:\Rundl132.exe | executable | |
MD5:8A09DFD7C6659D7D8639D6EC8304941A | SHA256:087BBDBC253BB88B662717C7007881E370868074B5BD9323FE182E2E4D7FD67F | |||
| 7748 | a625ed01ef1eb71929a9cccefe6ce056bef40e44b332f1f144cafe552af310a3.exe | C:\vcry.dll | executable | |
MD5:08BD5F30E2867DBA15155037FB7A6B68 | SHA256:3B42AAA50154492DAF3DD9F925ECC8EE688F9F166105CFCACB87F921B170093E | |||
| 7976 | ReAgentc.exe | C:\Windows\Logs\ReAgent\ReAgent.log | text | |
MD5:45469FA2AC111A665DA56D93D709A791 | SHA256:C208C80451526960CE8BA315C9F6F800AF92E0C7445AFD6337B64CAB7AF794AF | |||
| 7976 | ReAgentc.exe | \\?\Volume{2f5c5e71-85a9-11eb-90a8-9a9b76358421}\EFI\Microsoft\Recovery\BCD | binary | |
MD5:4BA8706489035586D67A88E64096A8E2 | SHA256:0E5EFBFA96BF45E3DDA6F034DB4226DE2F48FA10F2F517648B4CB8B5E61B8AB3 | |||
| 7804 | rundll32.exe | C:\bin\AES_Key.bin.Encrypt | binary | |
MD5:1A06C3FF9B2F7E01E47E3C9D3367129E | SHA256:730F5AFAF095EA0014266459D7112ACED4A49A0DE25472E6205014234ABB0CC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
50
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.76:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.76:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.72:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.17:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.160.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.20:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
904 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |