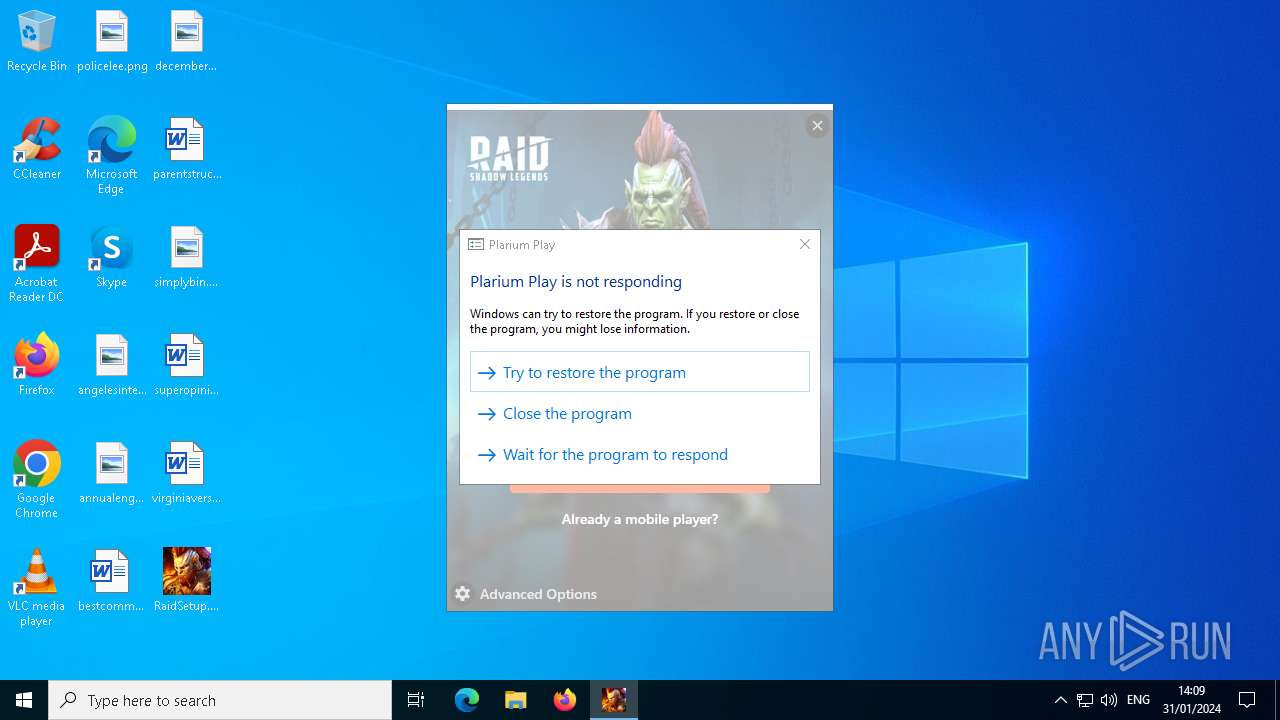
| File name: | RaidSetup.exe |
| Full analysis: | https://app.any.run/tasks/6242db60-14b1-4485-8edc-5bc474c76edc |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2024, 14:06:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F942A895DC434A520F450B3409043670 |
| SHA1: | 0B38E50826B922B6CDED39F2205202A911373778 |
| SHA256: | A61A828FF1E6E04CCEDF25A258118DC83A0497852F53B773D515D24D11AEF5BB |
| SSDEEP: | 98304:NLbkHLWqniKHqv6REMNPp3VWFogiiV6znaQKO8KbJaYIKIUc5TGBX:ssYD |
MALICIOUS
Drops the executable file immediately after the start
- RaidSetup.exe (PID: 208)
- RaidSetup.exe (PID: 5820)
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6280)
- RaidSetup.exe (PID: 6456)
SUSPICIOUS
Executable content was dropped or overwritten
- RaidSetup.exe (PID: 208)
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 5820)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6280)
- RaidSetup.exe (PID: 6456)
The process creates files with name similar to system file names
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Process drops legitimate windows executable
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Reads the date of Windows installation
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
Searches for installed software
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
INFO
Checks supported languages
- RaidSetup.exe (PID: 208)
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 5820)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6280)
- RaidSetup.exe (PID: 6456)
Create files in a temporary directory
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 208)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Reads the computer name
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Reads the machine GUID from the registry
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Creates files or folders in the user directory
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Reads Environment values
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Checks proxy server information
- RaidSetup.exe (PID: 3188)
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Reads the software policy settings
- RaidSetup.exe (PID: 6844)
- RaidSetup.exe (PID: 6456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:09:17 07:33:38+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 299008 |
| InitializedDataSize: | 594432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2df71 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.9.0.0 |
| ProductVersionNumber: | 8.9.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Plarium |
| FileDescription: | Plarium Play |
| FileVersion: | 8.9.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Plarium. All rights reserved. |
| OriginalFileName: | PlariumPlaySetup.exe |
| ProductName: | Plarium Play |
| ProductVersion: | 8.9.0 |
Total processes
143
Monitored processes
7
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Users\admin\Desktop\RaidSetup.exe" | C:\Users\admin\Desktop\RaidSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: MEDIUM Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
| 3188 | "C:\Users\admin\AppData\Local\Temp\{3D56F786-90D5-450D-90F5-6A2E9A9ED0FA}\.cr\RaidSetup.exe" -burn.clean.room="C:\Users\admin\Desktop\RaidSetup.exe" -burn.filehandle.attached=600 -burn.filehandle.self=596 | C:\Users\admin\AppData\Local\Temp\{3D56F786-90D5-450D-90F5-6A2E9A9ED0FA}\.cr\RaidSetup.exe | RaidSetup.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: MEDIUM Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
| 5820 | "C:\Users\admin\Desktop\RaidSetup.exe" -reload | C:\Users\admin\Desktop\RaidSetup.exe | RaidSetup.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: HIGH Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
| 6280 | "C:\Users\admin\Desktop\RaidSetup.exe" | C:\Users\admin\Desktop\RaidSetup.exe | RaidSetup.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: HIGH Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
| 6456 | "C:\WINDOWS\Temp\{D28D8AC5-0576-4EDF-8272-E87414052389}\.cr\RaidSetup.exe" -burn.clean.room="C:\Users\admin\Desktop\RaidSetup.exe" -burn.filehandle.attached=536 -burn.filehandle.self=568 | C:\Windows\Temp\{D28D8AC5-0576-4EDF-8272-E87414052389}\.cr\RaidSetup.exe | RaidSetup.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: HIGH Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
| 6604 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 6844 | "C:\WINDOWS\Temp\{D3A6A22C-8E62-4217-B49C-B18531DEFCA9}\.cr\RaidSetup.exe" -burn.clean.room="C:\Users\admin\Desktop\RaidSetup.exe" -burn.filehandle.attached=712 -burn.filehandle.self=716 -reload | C:\Windows\Temp\{D3A6A22C-8E62-4217-B49C-B18531DEFCA9}\.cr\RaidSetup.exe | RaidSetup.exe | ||||||||||||
User: admin Company: Plarium Integrity Level: HIGH Description: Plarium Play Exit code: 0 Version: 8.9.0 Modules
| |||||||||||||||
Total events
8 936
Read events
8 919
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3188) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3188) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3188) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3188) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6844) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6844) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6844) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6844) RaidSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6456) RaidSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 7 | |||
Executable files
21
Suspicious files
2
Text files
91
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 208 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{3D56F786-90D5-450D-90F5-6A2E9A9ED0FA}\.cr\RaidSetup.exe | executable | |
MD5:72F14C782A21B1A51CD0FF56DD5E40D5 | SHA256:33A01BFB0739537B63399A89CAB736853E6F61D038EA98DCAE209E0D3866F518 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\mbapreq.dll | executable | |
MD5:FE7E0BD53F52E6630473C31299A49FDD | SHA256:2BEA14D70943A42D344E09B7C9DE5562FA7E109946E1C615DD584DA30D06CC80 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\1038\mbapreq.wxl | xml | |
MD5:17FB605A2F02DA203DF06F714D1CC6DE | SHA256:55CF62D54EFB79801A9D94B24B3C9BA221C2465417A068950D40A67C52BA66EF | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\BootstrapperCore.dll | executable | |
MD5:B0D10A2A622A322788780E7A3CBB85F3 | SHA256:F2C2B3CE2DF70A3206F3111391FFC7B791B32505FA97AEF22C0C2DBF6F3B0426 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\mbapreq.thm | xml | |
MD5:A20778EC90A094A62A6C3A6AB2A6DC7D | SHA256:F8C3A03F47F0B9B3C20F0522A2481DA28C77FECDBB302F8DD8FBED87758CBAEA | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\mbapreq.wxl | xml | |
MD5:4D2C8D10C5DCCA6B938B71C8F02CA8A8 | SHA256:C63DE5F309502F9272402587A6BE22624D1BC2FEACD1BD33FB11E44CD6614B96 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\1028\mbapreq.wxl | xml | |
MD5:1D4B831F77EFEC96FFBC70BC4B59B8B5 | SHA256:1B93556F07C35AC0564D57E0743CCBA231950962C6506C8D4A74A31CD66FD04C | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\1032\mbapreq.wxl | xml | |
MD5:074D5921AF07E6126049CB45814246ED | SHA256:B8E90E20EDF110AAAAEA54FBC8533872831777BE5589E380CFDD17E1F93147B5 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\mbapreq.png | image | |
MD5:A356956FD269567B8F4612A33802637B | SHA256:A401A225ADDAF89110B4B0F6E8CF94779E7C0640BCDD2D670FFCF05AAB0DAD03 | |||
| 3188 | RaidSetup.exe | C:\Users\admin\AppData\Local\Temp\{2E67B42E-2A1C-455C-A269-49B1FC884B18}\.ba\1040\mbapreq.wxl | xml | |
MD5:50261379B89457B1980FF19CFABE6A08 | SHA256:A40C94EB33F8841C79E9F6958433AFFD517F97B4570F731666AF572E63178BB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
34
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6844 | RaidSetup.exe | GET | — | 216.58.212.142:80 | http://google.com/generate_204 | unknown | — | — | unknown |
1612 | svchost.exe | GET | — | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6492 | msedge.exe | GET | 302 | 104.85.1.163:443 | https://go.microsoft.com/fwlink/?linkid=2133855&bucket=15 | unknown | — | — | unknown |
2624 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707187846&P2=404&P3=2&P4=GkWljMQM3ecMqgUu9fSpDfCxGsr2EP4GqvPnfq0cgNqUrpffNYbxwf5Tqs1fdlAv%2fRHbIaVcJk%2bCcDnxMV9qpg%3d%3d | unknown | — | — | unknown |
2624 | svchost.exe | GET | — | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707187846&P2=404&P3=2&P4=GkWljMQM3ecMqgUu9fSpDfCxGsr2EP4GqvPnfq0cgNqUrpffNYbxwf5Tqs1fdlAv%2fRHbIaVcJk%2bCcDnxMV9qpg%3d%3d | unknown | — | — | unknown |
2624 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707187846&P2=404&P3=2&P4=GkWljMQM3ecMqgUu9fSpDfCxGsr2EP4GqvPnfq0cgNqUrpffNYbxwf5Tqs1fdlAv%2fRHbIaVcJk%2bCcDnxMV9qpg%3d%3d | unknown | binary | 1.09 Kb | unknown |
6844 | RaidSetup.exe | GET | 204 | 216.58.212.142:80 | http://google.com/generate_204 | unknown | — | — | unknown |
6456 | RaidSetup.exe | GET | — | 216.58.212.142:80 | http://google.com/generate_204 | unknown | — | — | unknown |
6456 | RaidSetup.exe | GET | 204 | 216.58.212.142:80 | http://google.com/generate_204 | unknown | — | — | unknown |
6456 | RaidSetup.exe | GET | 200 | 104.18.14.253:443 | https://desktop.plarium.com/8.9.0/en/installer | unknown | text | 37.7 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1612 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3188 | RaidSetup.exe | 104.18.14.253:443 | collector.plarium.com | CLOUDFLARENET | — | unknown |
6844 | RaidSetup.exe | 104.18.14.253:443 | collector.plarium.com | CLOUDFLARENET | — | unknown |
6844 | RaidSetup.exe | 216.58.212.142:80 | google.com | GOOGLE | US | whitelisted |
1612 | svchost.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5612 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4188 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6492 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6492 | msedge.exe | 23.211.9.234:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
6492 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
collector.plarium.com |
| unknown |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
desktop.plarium.com |
| unknown |
cdn01.x-plarium.com |
| unknown |
www.google-analytics.com |
| whitelisted |