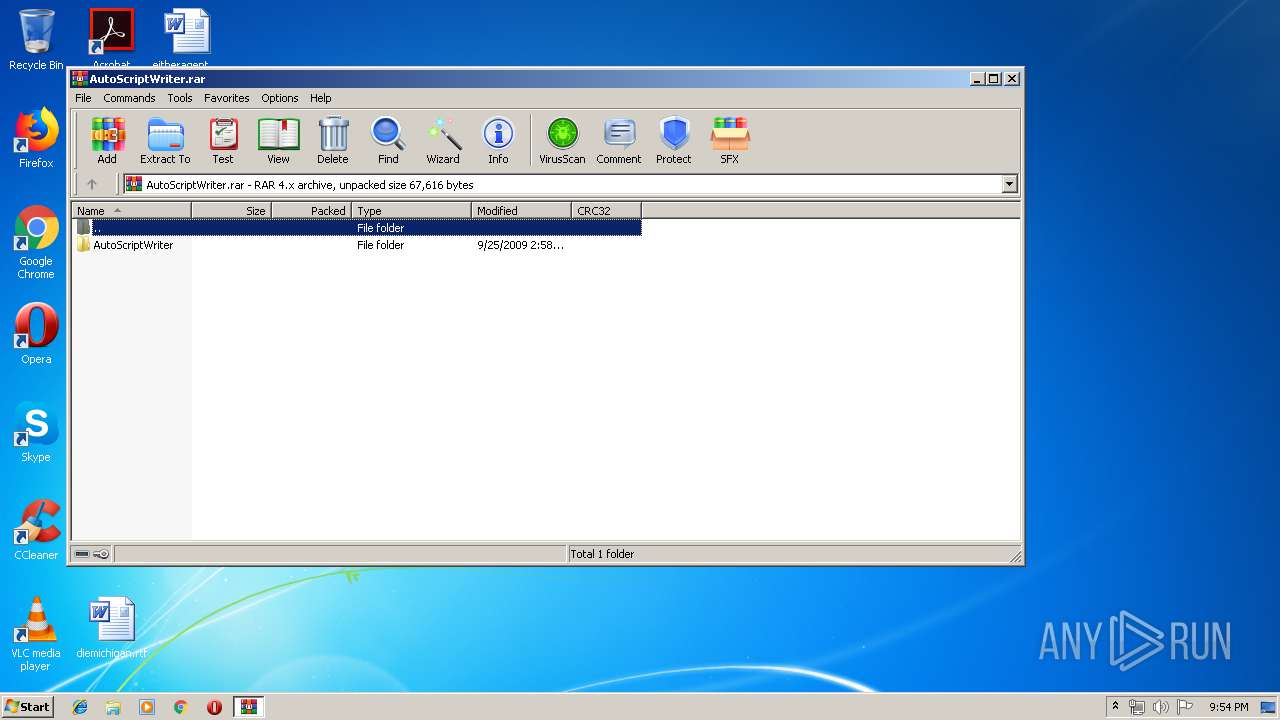
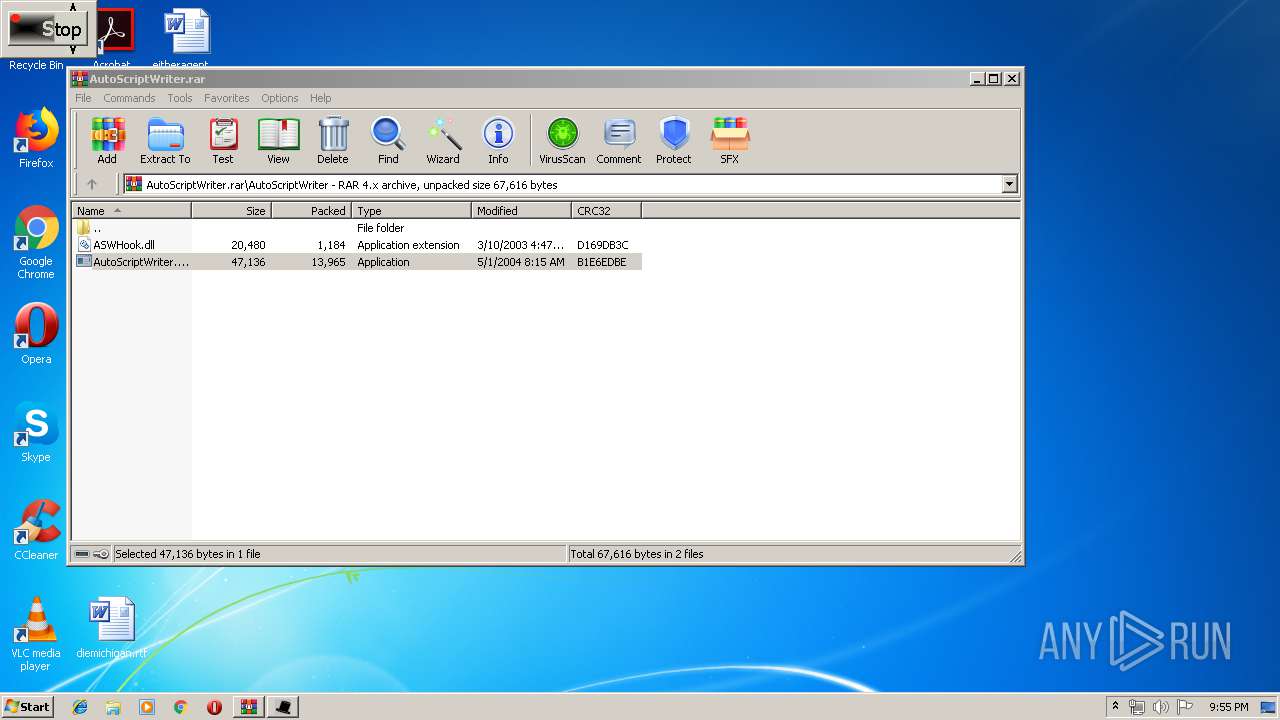
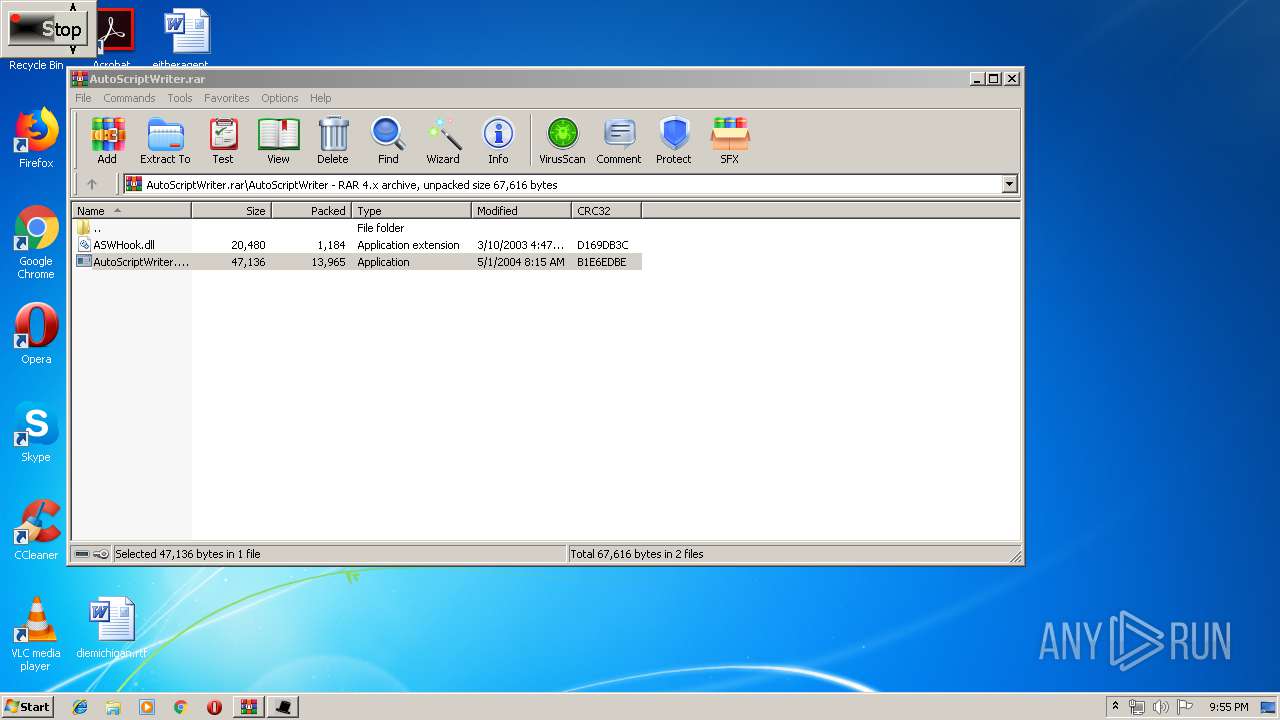
| File name: | AutoScriptWriter.rar |
| Full analysis: | https://app.any.run/tasks/7fff3827-b7a3-4c1a-9fff-d0bb4eb96dd8 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 20:54:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | D4F452DCF52261CA544221AFF43E54D5 |
| SHA1: | 5F67372B60E733139265EBC557356B680B22FE3A |
| SHA256: | A601A9871B943AF9AB6A68AFA193839657A98A49058331ABC677D0896BE2C718 |
| SSDEEP: | 384:NvV9O6ofH+Sv5PMnmrDYR0yU7Db+SGytoMIX1HOdTmwQwQACyV:D9OjHJ5MnmPYRY7OPytoxX18SwBtB |
MALICIOUS
Loads dropped or rewritten executable
- AutoScriptWriter.exe (PID: 3580)
- explorer.exe (PID: 2044)
- WinRAR.exe (PID: 3552)
Application was dropped or rewritten from another process
- AutoScriptWriter.exe (PID: 3580)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3552)
Creates files in the user directory
- notepad++.exe (PID: 3312)
- explorer.exe (PID: 2044)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1233 |
|---|---|
| UncompressedSize: | 20480 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2003:03:10 16:47:25 |
| PackingMethod: | Normal |
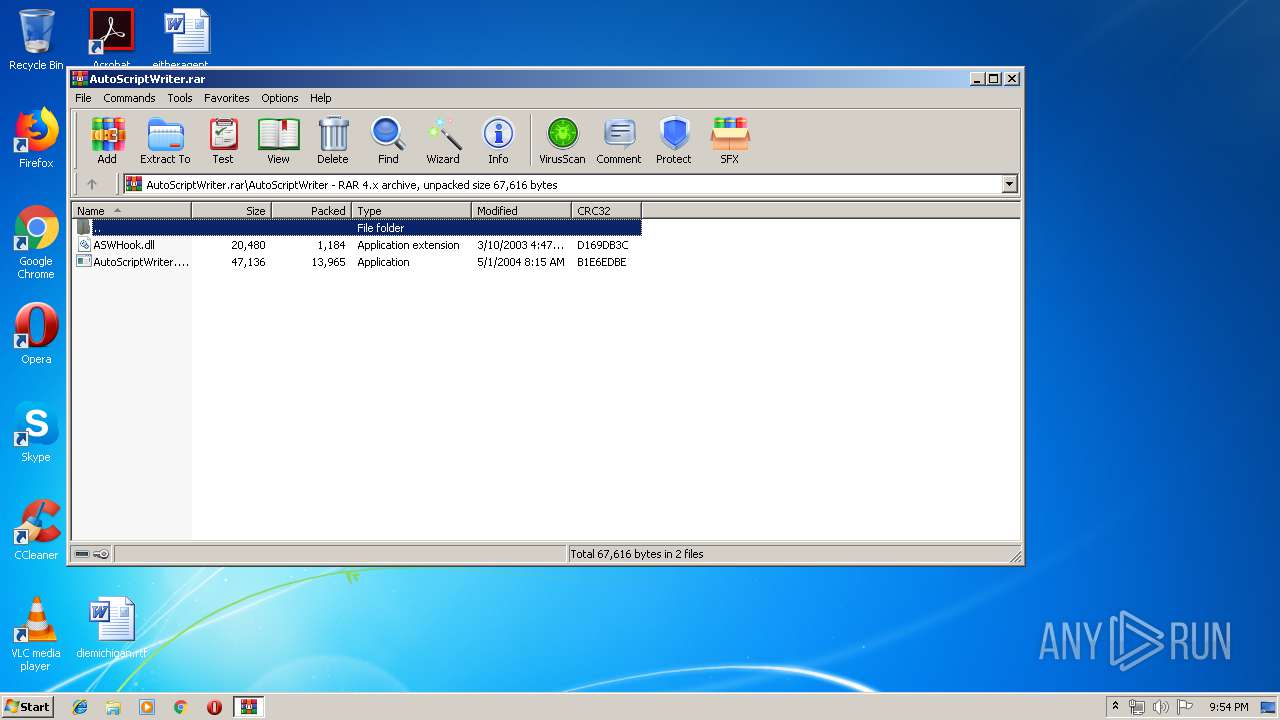
| ArchivedFileName: | AutoScriptWriter\ASWHook.dll |
Total processes
41
Monitored processes
6
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2044 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
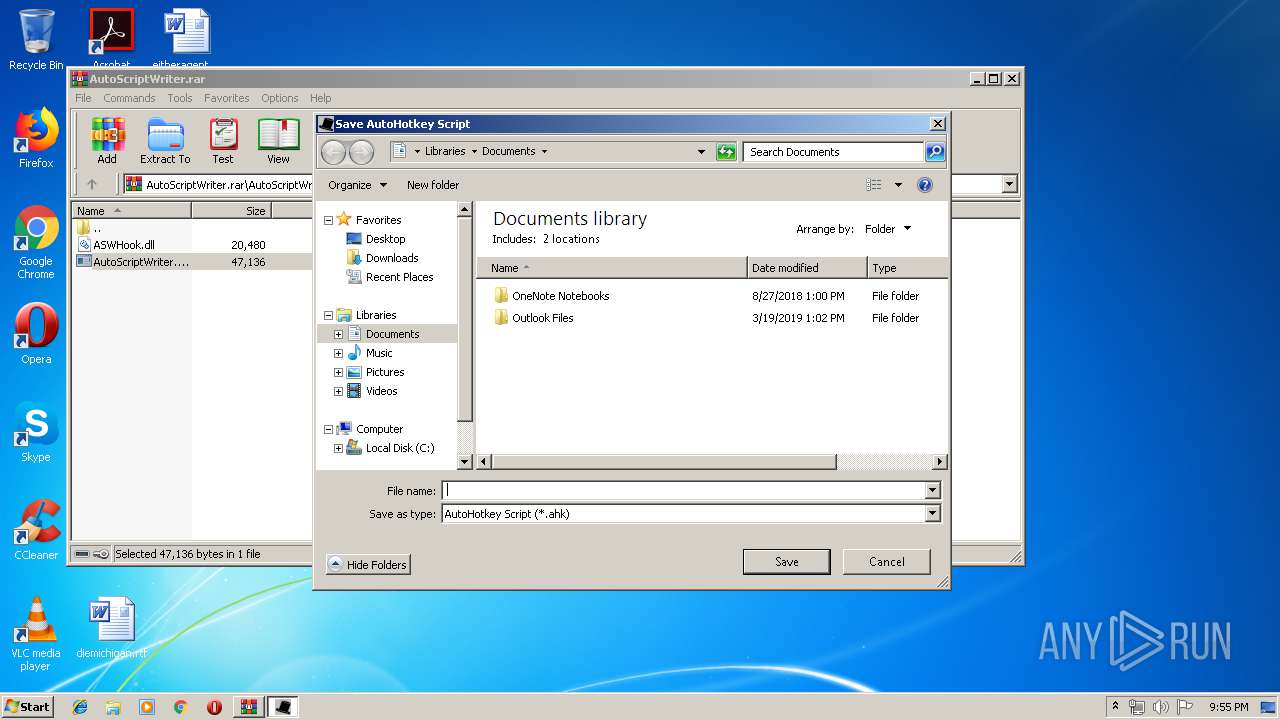
| 3312 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Documents\jj.ahk" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 3516 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3552 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AutoScriptWriter.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
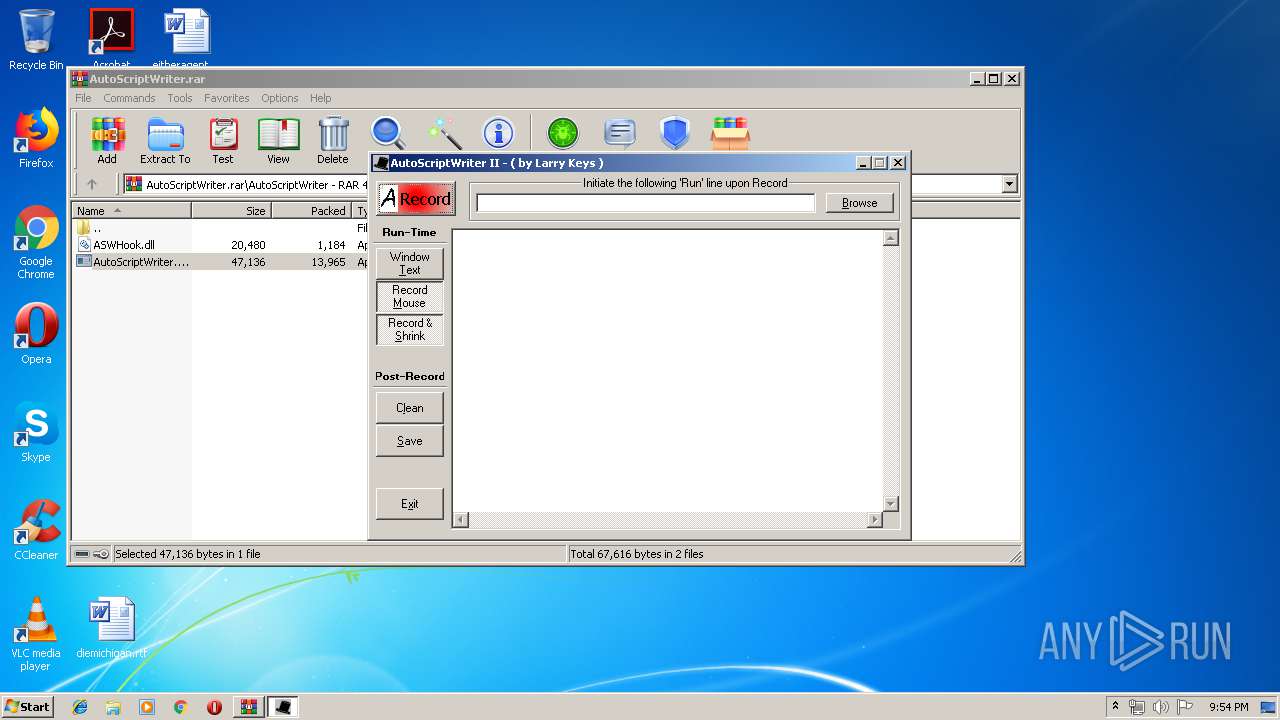
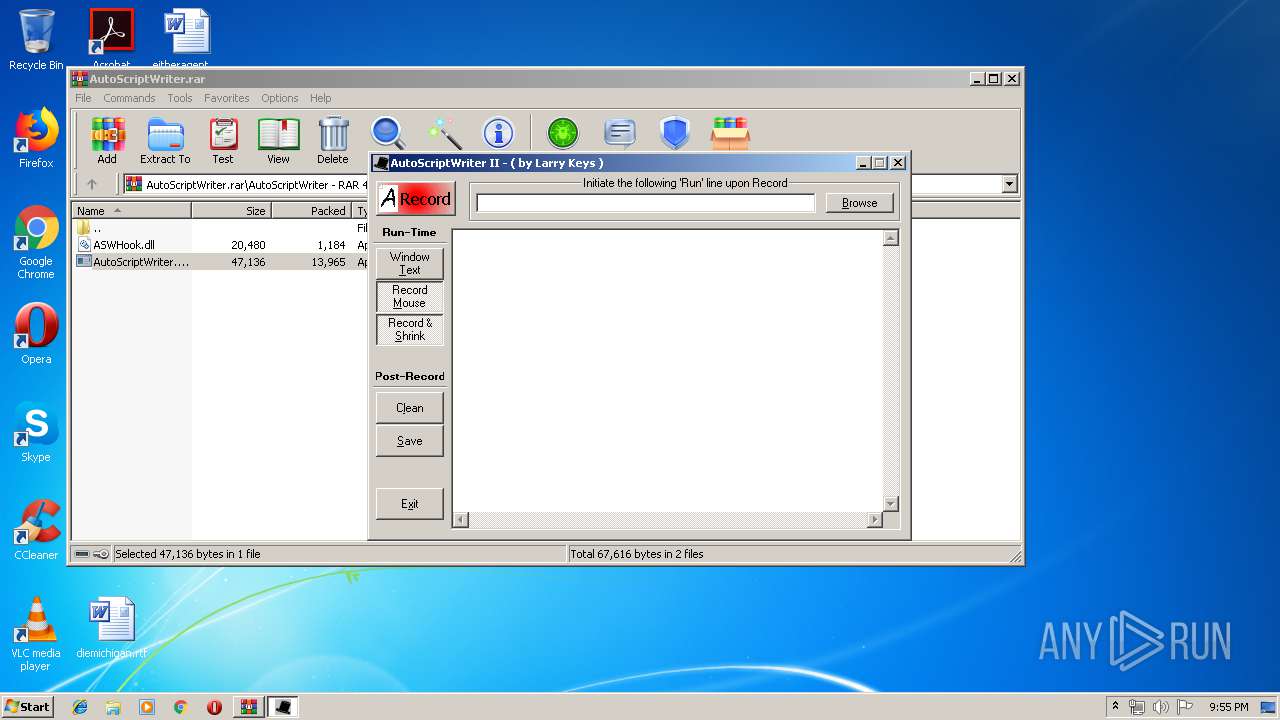
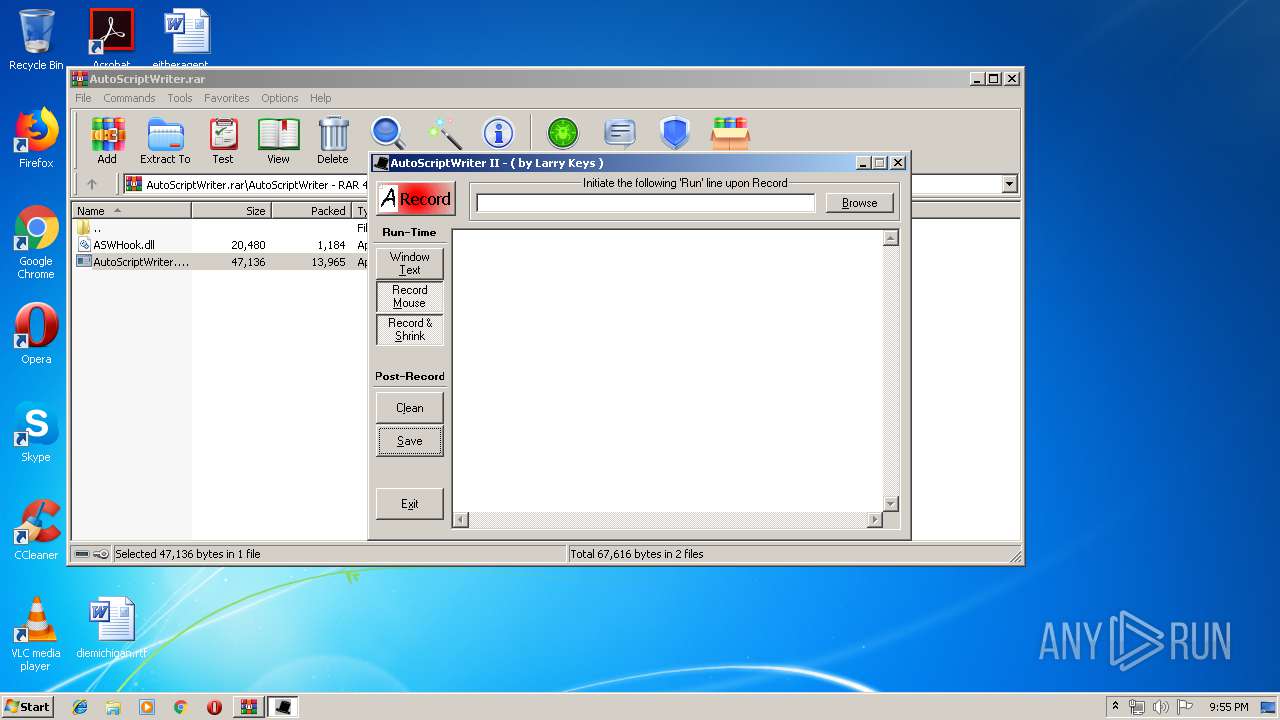
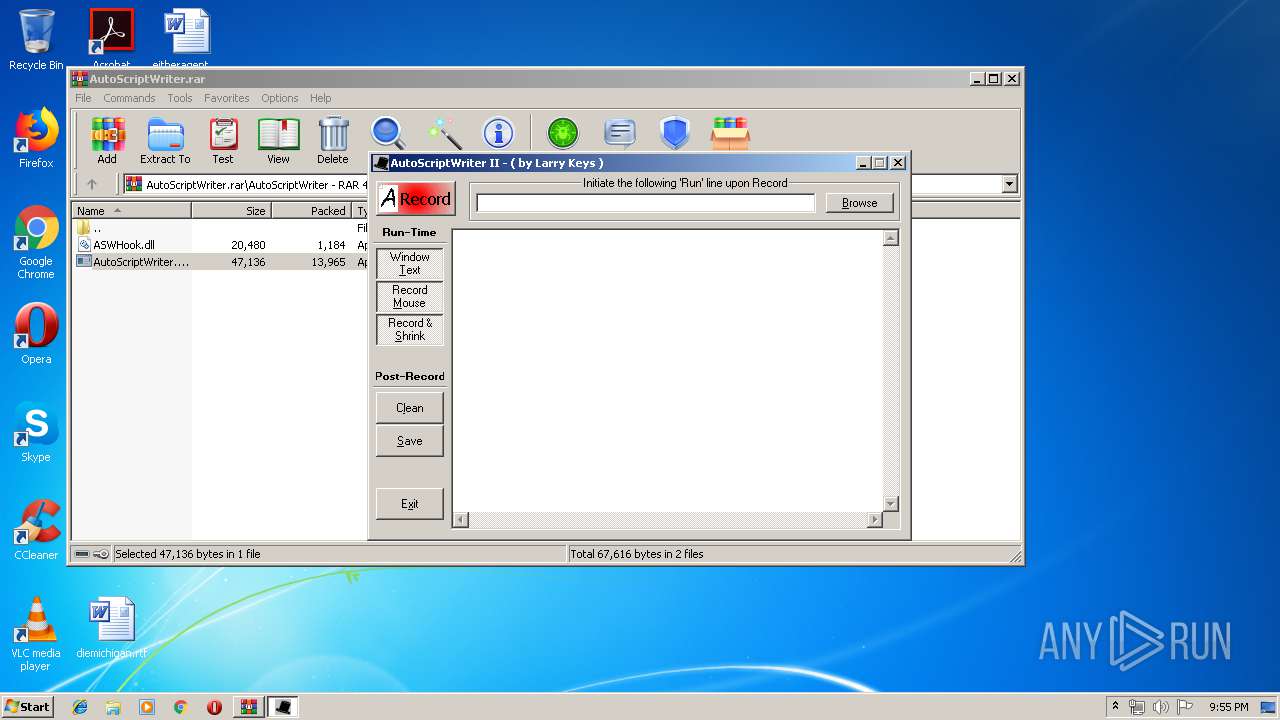
| 3580 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3552.19008\AutoScriptWriter\AutoScriptWriter.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3552.19008\AutoScriptWriter\AutoScriptWriter.exe | — | WinRAR.exe | |||||||||||
User: admin Company: DaloozaSoft Integrity Level: MEDIUM Description: Automatic AutoIt Script Writer Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
Total events
1 441
Read events
1 274
Write events
165
Delete events
2
Modification events
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AutoScriptWriter.rar | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 2044 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Documents.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3552.19008\AutoScriptWriter\ASWHook.dll | executable | |
MD5:F70072EC0E290D42769402516E9FAA81 | SHA256:5068223268F3562F649C41563EAC0300F95CBFBEF53A06EACB05A4C5FB14F261 | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\Config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3552.19008\AutoScriptWriter\AutoScriptWriter.exe | executable | |
MD5:B3FA428197881ADF33E0ACF633F2B638 | SHA256:7B700CAFE4E11F86B2C84AD479CE33EA71D0EC33ECC098076BF7CA8DA93118F4 | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:AD21A64014891793DD9B21D835278F36 | SHA256:C24699C9D00ABDD510140FE1B2ACE97BFC70D8B21BF3462DED85AFC4F73FE52F | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:44982E1D48434C0AB3E8277E322DD1E4 | SHA256:3E661D3F1FF3977B022A0ACC26B840B5E57D600BC03DCFC6BEFDB408C665904C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.190.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
— | — | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 896 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3516 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
— | — | 2.20.189.204:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
— | — | 2.20.190.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|