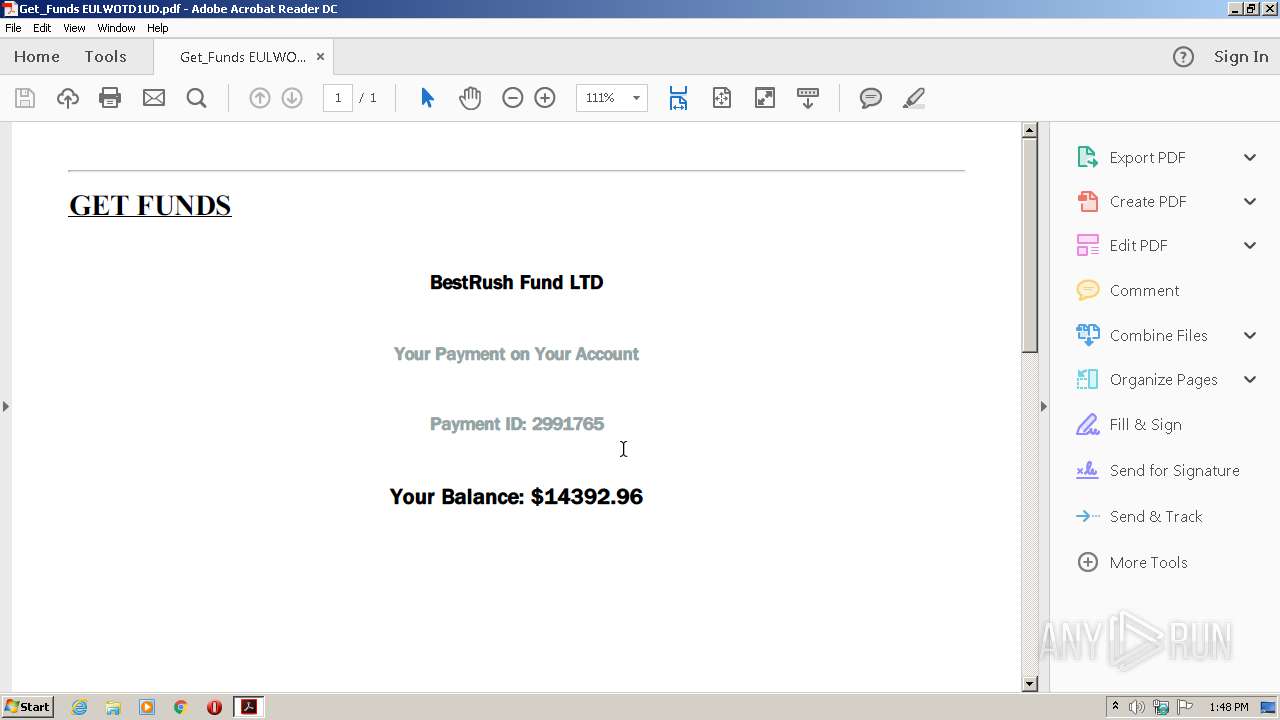
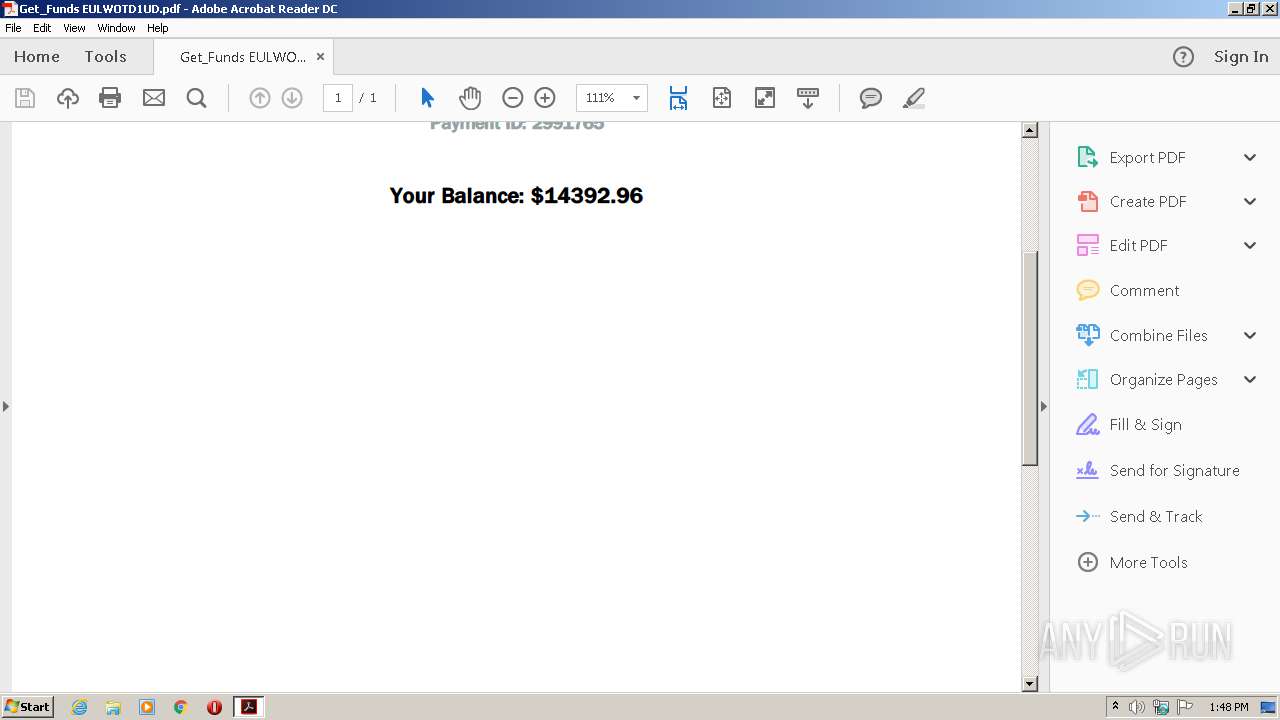
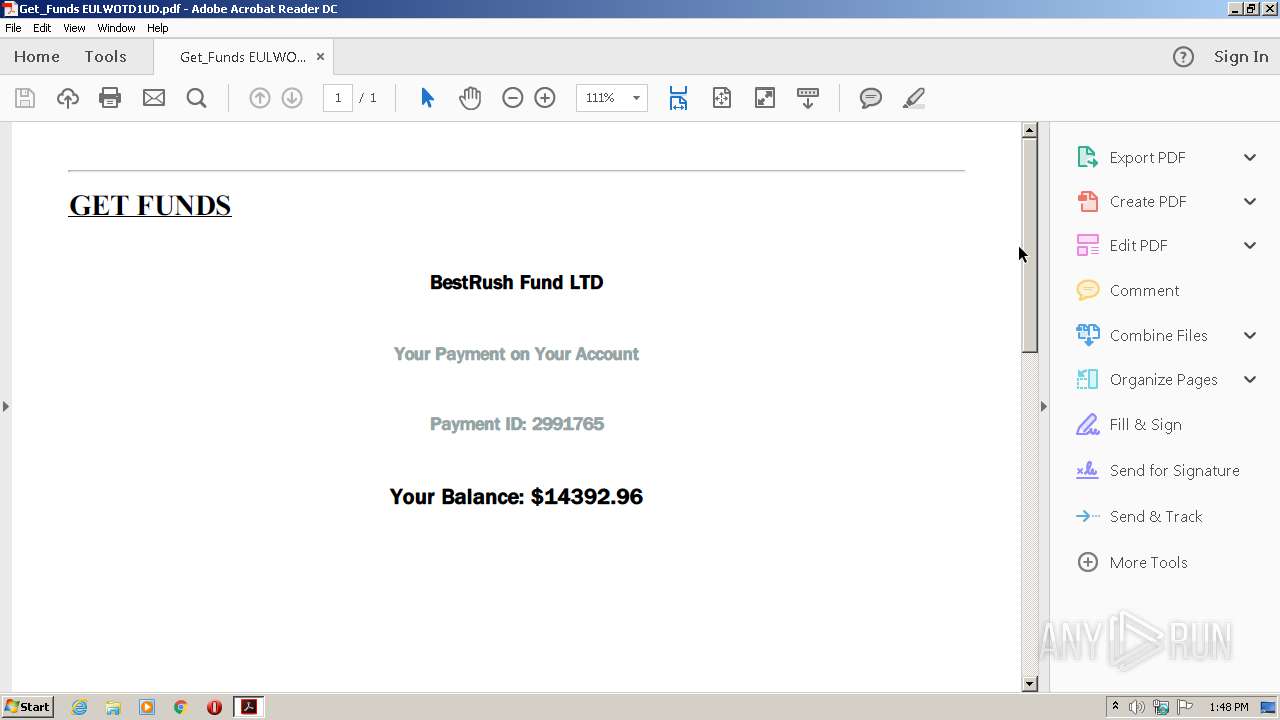
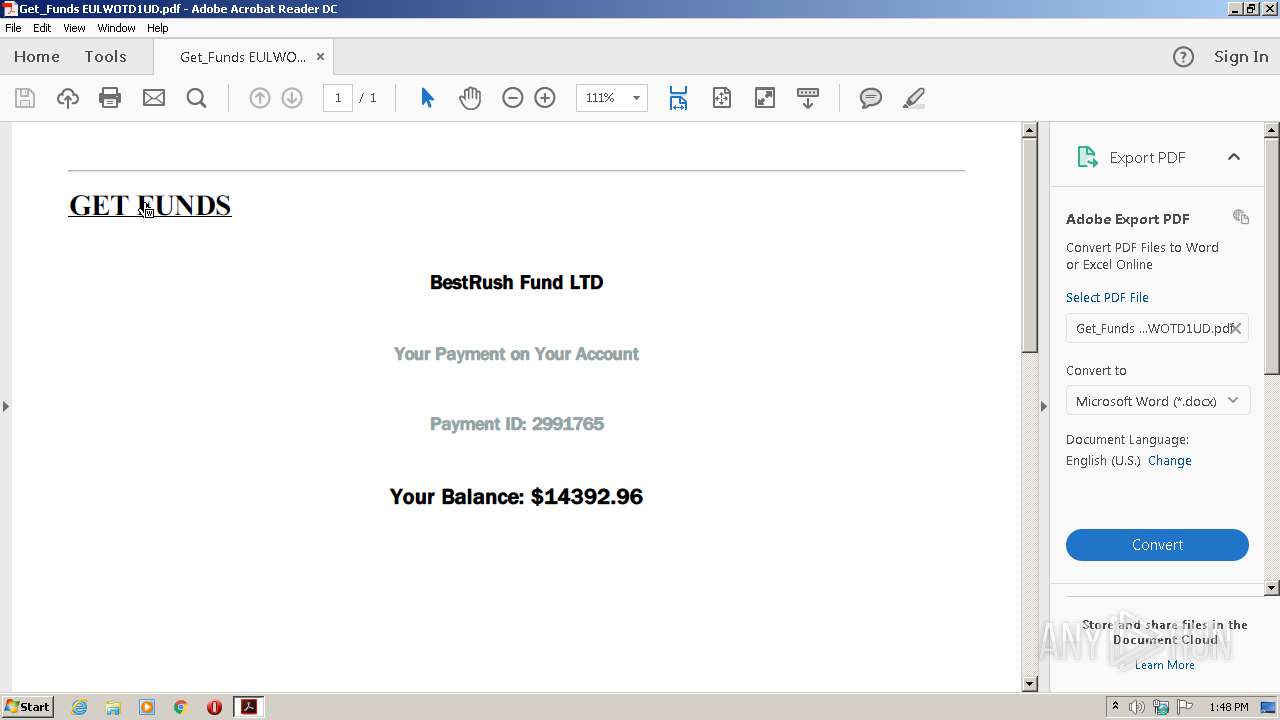
| File name: | Get_Funds EULWOTD1UD.pdf |
| Full analysis: | https://app.any.run/tasks/33dcef9a-f78f-47f9-b05f-016a848a0481 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 12:47:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4 |
| MD5: | 7F6E9DEAD3E0F5A2D7212CB852635097 |
| SHA1: | 415A80D31FCCB0C56B3ECD78D8C3576264D30B40 |
| SHA256: | A5FF634CCB16D3BF1DDE872B02AFEF82E4E821C38BF73875DE2738801BB3B62E |
| SSDEEP: | 384:N05gEhWvjI5utCUSfA+K6SP0KFOCUSUWG:NHEhWc5ueA+bDwG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 2548)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 2548)
Creates files in the program directory
- AdobeARM.exe (PID: 3624)
INFO
Reads Internet Cache Settings
- AcroRd32.exe (PID: 1580)
- iexplore.exe (PID: 888)
- AcroRd32.exe (PID: 2548)
- iexplore.exe (PID: 2108)
Creates files in the user directory
- iexplore.exe (PID: 2108)
- iexplore.exe (PID: 888)
Application launched itself
- chrome.exe (PID: 2060)
- AcroRd32.exe (PID: 2548)
- RdrCEF.exe (PID: 2724)
- iexplore.exe (PID: 888)
Reads the hosts file
- chrome.exe (PID: 896)
- RdrCEF.exe (PID: 2724)
- chrome.exe (PID: 2060)
Reads settings of System Certificates
- AcroRd32.exe (PID: 2548)
- iexplore.exe (PID: 2108)
- iexplore.exe (PID: 888)
Changes internet zones settings
- iexplore.exe (PID: 888)
Manual execution by user
- chrome.exe (PID: 2060)
Reads internet explorer settings
- iexplore.exe (PID: 2108)
Adds / modifies Windows certificates
- iexplore.exe (PID: 888)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 888)
Changes settings of System certificates
- iexplore.exe (PID: 888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| Title: | b3xv%^Nl5457 |
| Creator: | !boGy5458 |
| Producer: | XCKi0qU5456 |
| CreateDate: | 2020:09:29 18:35:20+03:00 |
| Author: | DEtxg5453 |
| Keywords: | g483eP8o9jvDLW9lJ45455 |
| Subject: | 1AjZBfZ@05454 |
| PageCount: | 1 |
XMP
| XMPToolkit: | Image::ExifTool 11.61 |
|---|---|
| Creator: | !boGy5458 |
| Subject: | 1AjZBfZ@05454 |
| Title: | b3xv%^Nl5457 |
| Author: | DEtxg5453 |
| CreationDate: | 2016:02:14 17:49:29 |
| Keywords: | g483eP8o9jvDLW9lJ45455 |
| ModDate: | 2019:06:09 17:47:07 |
| Producer: | XCKi0qU5456 |
Total processes
66
Monitored processes
29
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12367154981970140584,6991681143647006526,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1830717574273161033 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1288 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
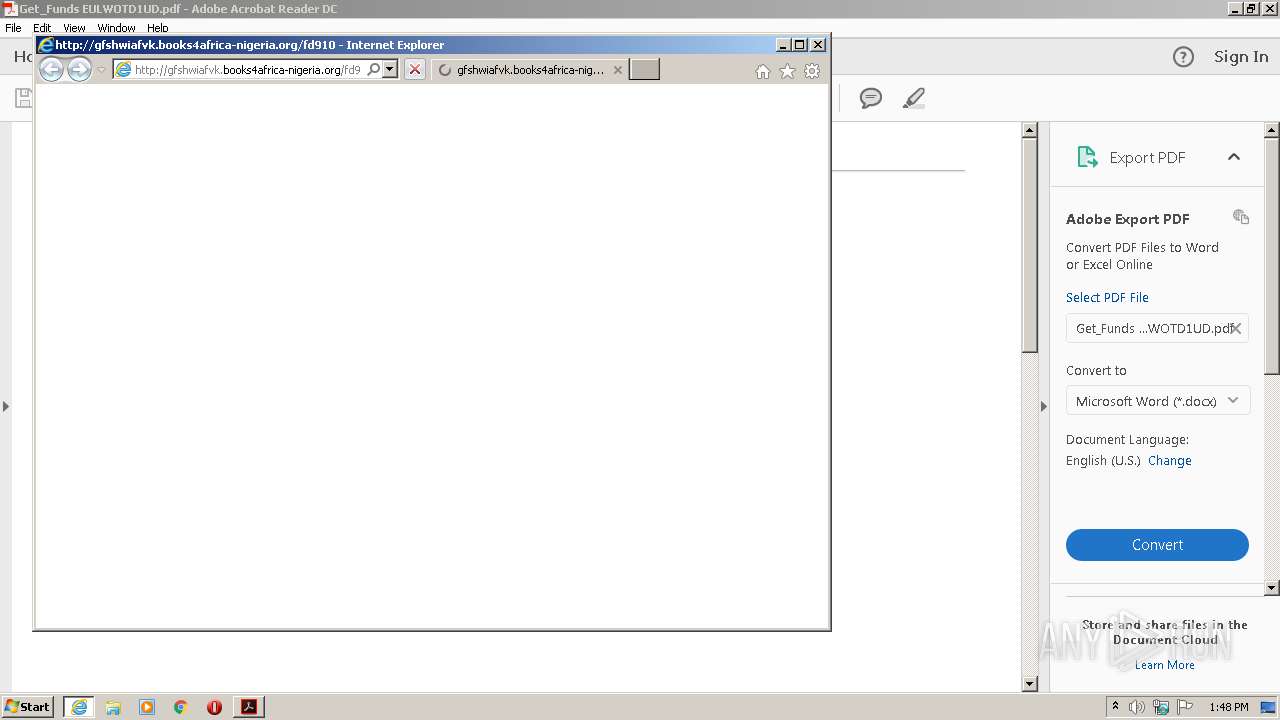
| 888 | "C:\Program Files\Internet Explorer\iexplore.exe" http://gfshwiafvk.books4africa-nigeria.org/fd910 | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12367154981970140584,6991681143647006526,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=14197743786690927546 --mojo-platform-channel-handle=1604 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1028,12367154981970140584,6991681143647006526,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3274509687237809162 --mojo-platform-channel-handle=1252 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12367154981970140584,6991681143647006526,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15077570978051337089 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2476 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1580 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Get_Funds EULWOTD1UD.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12367154981970140584,6991681143647006526,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=589311182141124782 --mojo-platform-channel-handle=3988 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:888 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Get_Funds EULWOTD1UD.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
Total events
1 543
Read events
1 323
Write events
213
Delete events
7
Modification events
| (PID) Process: | (1580) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1580) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (1580) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (2548) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (2548) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2548) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2548) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {17FE9752-0B5A-4665-84CD-569794602F5C} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF |
Value: 01000000000000001C8BF6FD2797D601 | |||
| (PID) Process: | (2548) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (888) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 267632461 | |||
| (PID) Process: | (888) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840616 | |||
Executable files
0
Suspicious files
64
Text files
108
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 2548 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\CabAD61.tmp | — | |
MD5:— | SHA256:— | |||
| 2548 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\TarAD62.tmp | — | |
MD5:— | SHA256:— | |||
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rmnnkfl_ra90fh_17w.tmp | — | |
MD5:— | SHA256:— | |||
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rwzk51d_ra90fg_17w.tmp | — | |
MD5:— | SHA256:— | |||
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rskggch_ra90ff_17w.tmp | — | |
MD5:— | SHA256:— | |||
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Reoov7o_ra90fe_17w.tmp | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBC26.tmp | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBC27.tmp | — | |
MD5:— | SHA256:— | |||
| 1580 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
100
DNS requests
62
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
888 | iexplore.exe | GET | 404 | 162.0.235.113:80 | http://gfshwiafvk.books4africa-nigeria.org/favicon.ico | CA | — | — | suspicious |
2548 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
2548 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2548 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2108 | iexplore.exe | GET | 200 | 162.0.235.113:80 | http://gfshwiafvk.books4africa-nigeria.org/fd910 | CA | html | 3.51 Kb | suspicious |
2108 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA4LlRp06p%2FpM0CCf5afOMs%3D | US | der | 279 b | whitelisted |
2548 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 151.139.236.246:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | US | der | 1.58 Kb | whitelisted |
2108 | iexplore.exe | GET | 200 | 151.139.236.246:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | US | der | 1.63 Kb | whitelisted |
2108 | iexplore.exe | GET | 200 | 151.139.236.246:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | US | der | 1.58 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2548 | AcroRd32.exe | 2.16.177.91:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
2548 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
888 | iexplore.exe | 162.0.235.113:80 | gfshwiafvk.books4africa-nigeria.org | AirComPlus Inc. | CA | suspicious |
2548 | AcroRd32.exe | 2.21.36.203:443 | armmf.adobe.com | GTT Communications Inc. | FR | suspicious |
— | — | 162.0.235.113:80 | gfshwiafvk.books4africa-nigeria.org | AirComPlus Inc. | CA | suspicious |
2108 | iexplore.exe | 172.67.206.123:443 | gianipumplin.club | — | US | suspicious |
2108 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2108 | iexplore.exe | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
2108 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
2108 | iexplore.exe | 5.254.23.213:443 | cache.betweendigital.com | — | RO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
gfshwiafvk.books4africa-nigeria.org |
| suspicious |
gianipumplin.club |
| suspicious |
parking-static.jino.ru |
| suspicious |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
888 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |