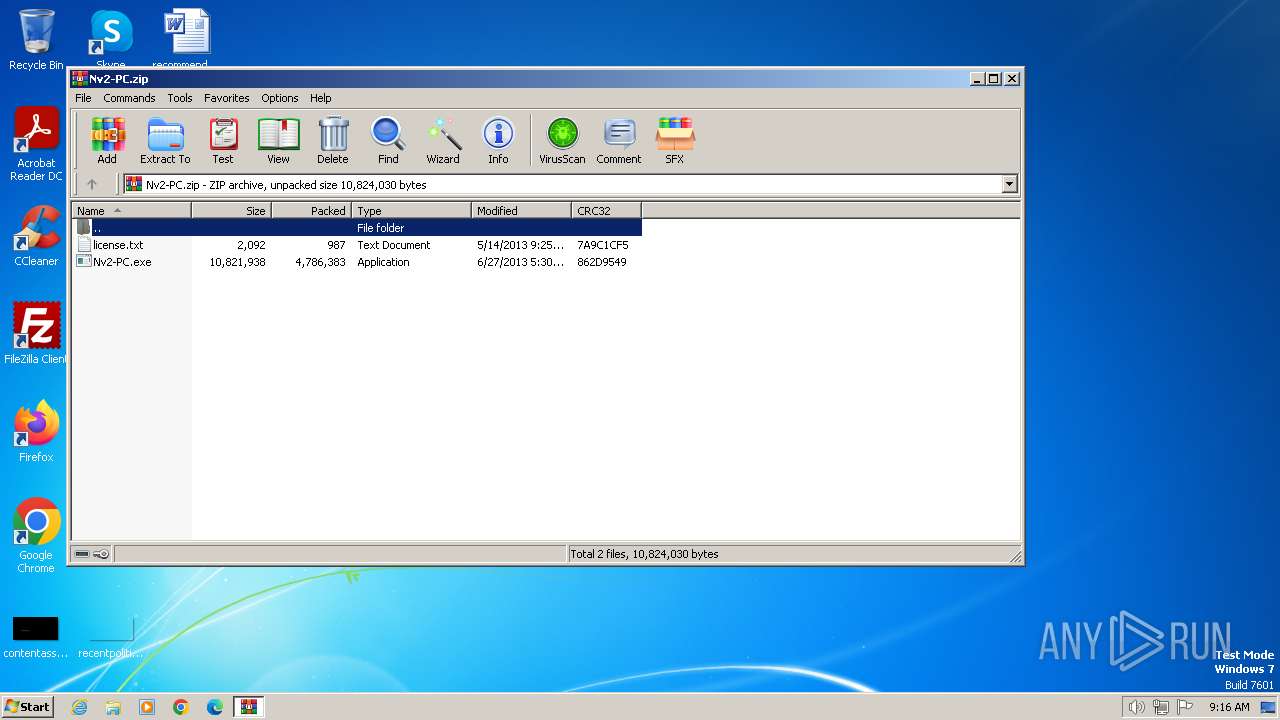
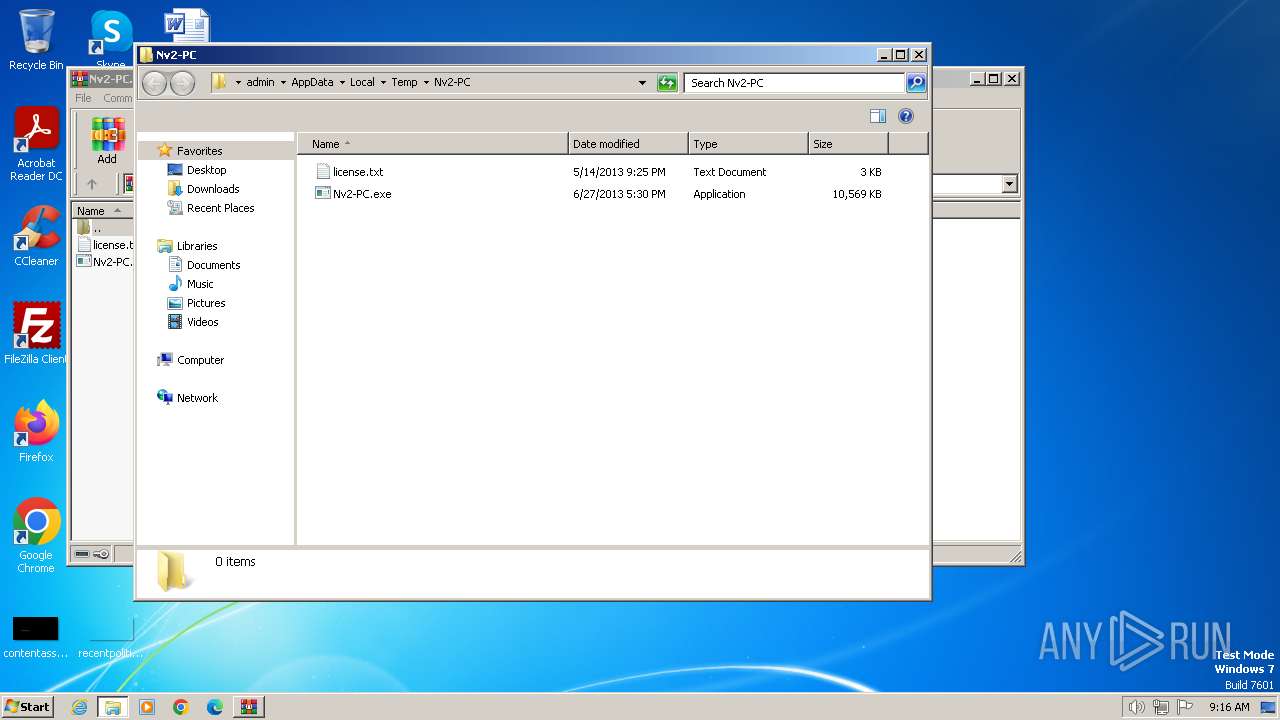
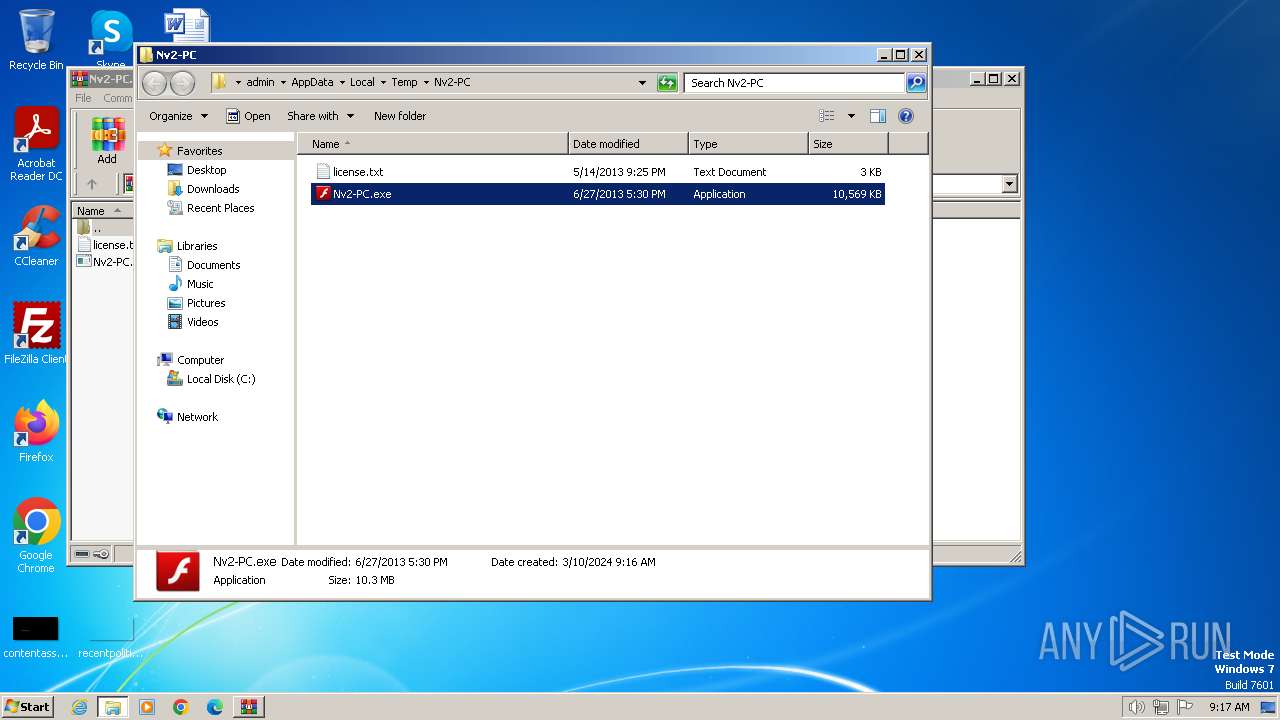
| File name: | Nv2-PC.zip |
| Full analysis: | https://app.any.run/tasks/b9368f2b-9672-4533-aadc-a566171eba45 |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2024, 09:16:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8A07CB456276C40D7167DE20DE9D2B9A |
| SHA1: | 44C07355473654CA112DD942D004EEAEA4E75BF9 |
| SHA256: | A5FD97368F47067F5A4157847F66041A8802F016B38B8C63A4E8D35BFB0B3ECC |
| SSDEEP: | 98304:pgItChwWw67OZd/9zS4paVDMl/fk6rdgSa969:aiMAYM/1S4p6O/sydgs |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2160)
Creates a writable file in the system directory
- Nv2-PC.exe (PID: 2364)
- printfilterpipelinesvc.exe (PID: 980)
SUSPICIOUS
Reads security settings of Internet Explorer
- Nv2-PC.exe (PID: 2364)
- Nv2-PC.exe (PID: 3720)
- ONENOTE.EXE (PID: 2804)
Reads the Internet Settings
- Nv2-PC.exe (PID: 2364)
- Nv2-PC.exe (PID: 3720)
- printfilterpipelinesvc.exe (PID: 980)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 2804)
Non-standard symbols in registry
- ONENOTE.EXE (PID: 2804)
Reads settings of System Certificates
- ONENOTE.EXE (PID: 2804)
INFO
Checks supported languages
- Nv2-PC.exe (PID: 3720)
- Nv2-PC.exe (PID: 2364)
- ONENOTE.EXE (PID: 2804)
- ONENOTEM.EXE (PID: 3556)
Reads the computer name
- Nv2-PC.exe (PID: 3720)
- Nv2-PC.exe (PID: 2364)
- ONENOTE.EXE (PID: 2804)
Checks proxy server information
- Nv2-PC.exe (PID: 3720)
- Nv2-PC.exe (PID: 2364)
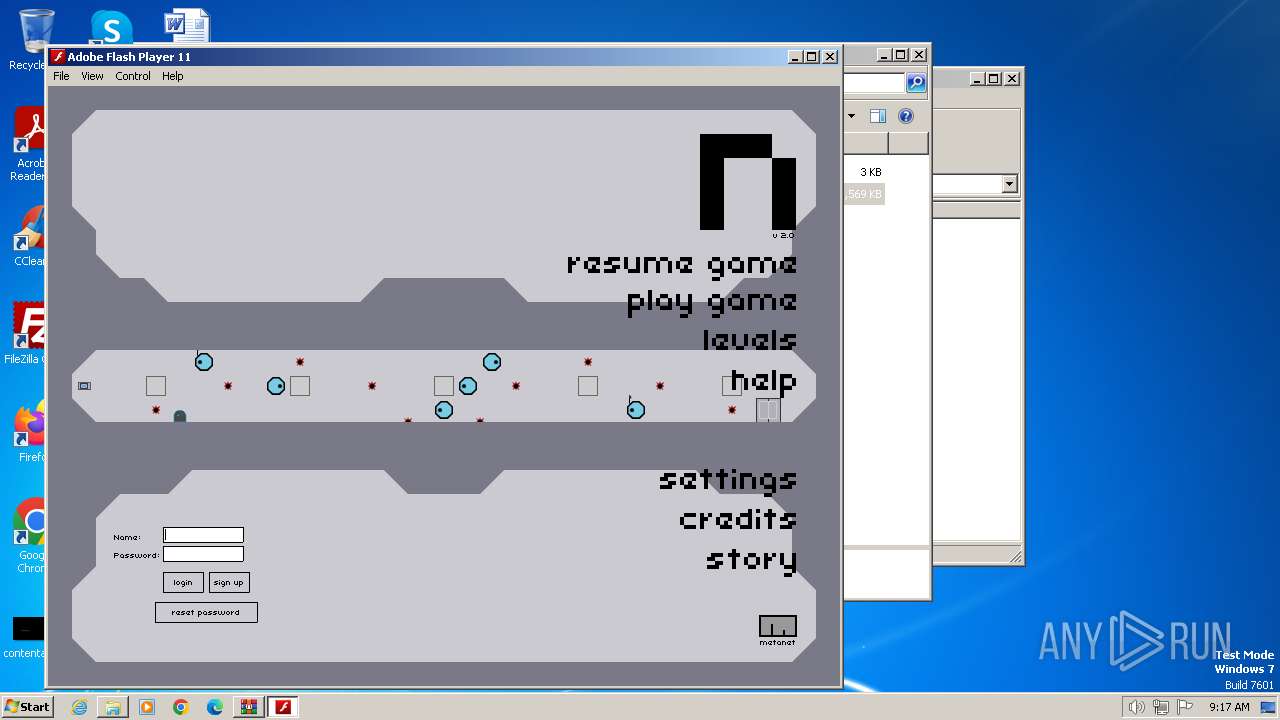
Manual execution by a user
- Nv2-PC.exe (PID: 2364)
- Nv2-PC.exe (PID: 3720)
Reads CPU info
- Nv2-PC.exe (PID: 2364)
- Nv2-PC.exe (PID: 3720)
Creates files or folders in the user directory
- Nv2-PC.exe (PID: 3720)
- Nv2-PC.exe (PID: 2364)
- printfilterpipelinesvc.exe (PID: 980)
- ONENOTE.EXE (PID: 2804)
Reads the machine GUID from the registry
- Nv2-PC.exe (PID: 3720)
- Nv2-PC.exe (PID: 2364)
- ONENOTE.EXE (PID: 2804)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2160)
Create files in a temporary directory
- Nv2-PC.exe (PID: 2364)
- ONENOTE.EXE (PID: 2804)
Reads Environment values
- ONENOTE.EXE (PID: 2804)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 2804)
- ONENOTEM.EXE (PID: 3556)
Reads the software policy settings
- ONENOTE.EXE (PID: 2804)
Process checks computer location settings
- ONENOTE.EXE (PID: 2804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2013:06:27 12:30:04 |
| ZipCRC: | 0x862d9549 |
| ZipCompressedSize: | 4786383 |
| ZipUncompressedSize: | 10821938 |
| ZipFileName: | Nv2-PC.exe |
Total processes
47
Monitored processes
6
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | C:\Windows\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 6.1.7601.24537 (win7sp1_ldr_escrow.191114-1547) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Nv2-PC.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
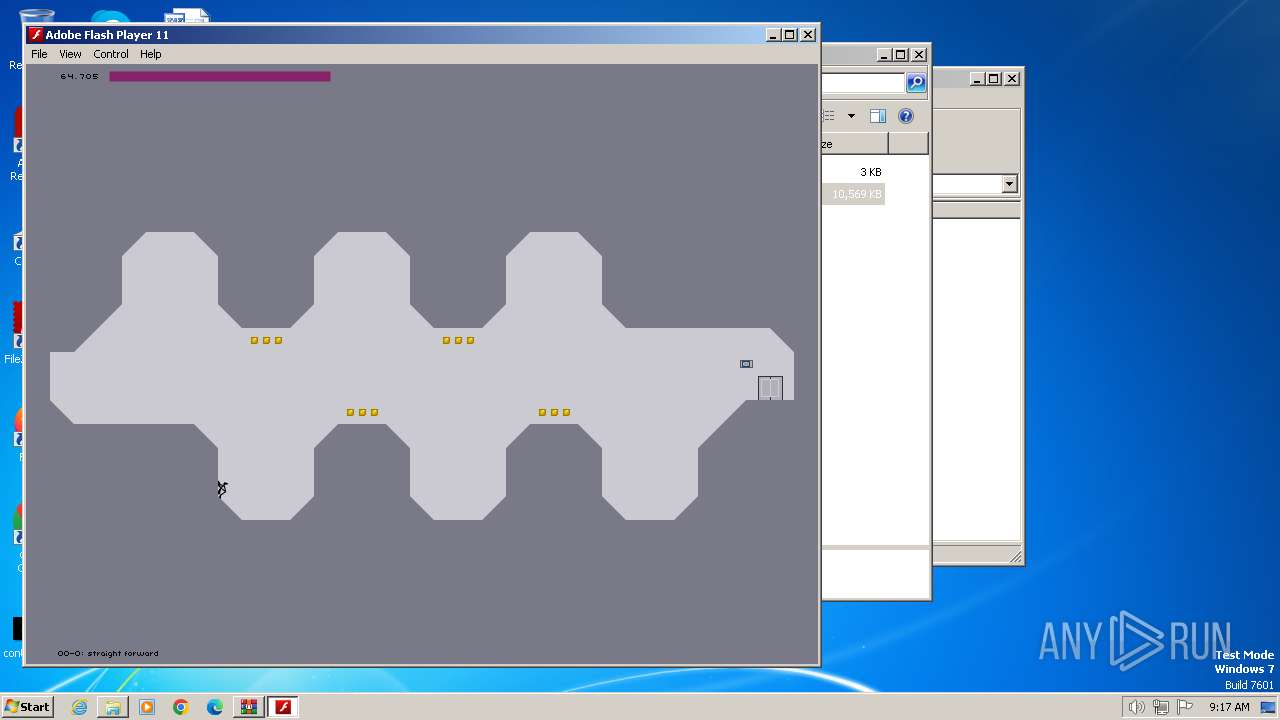
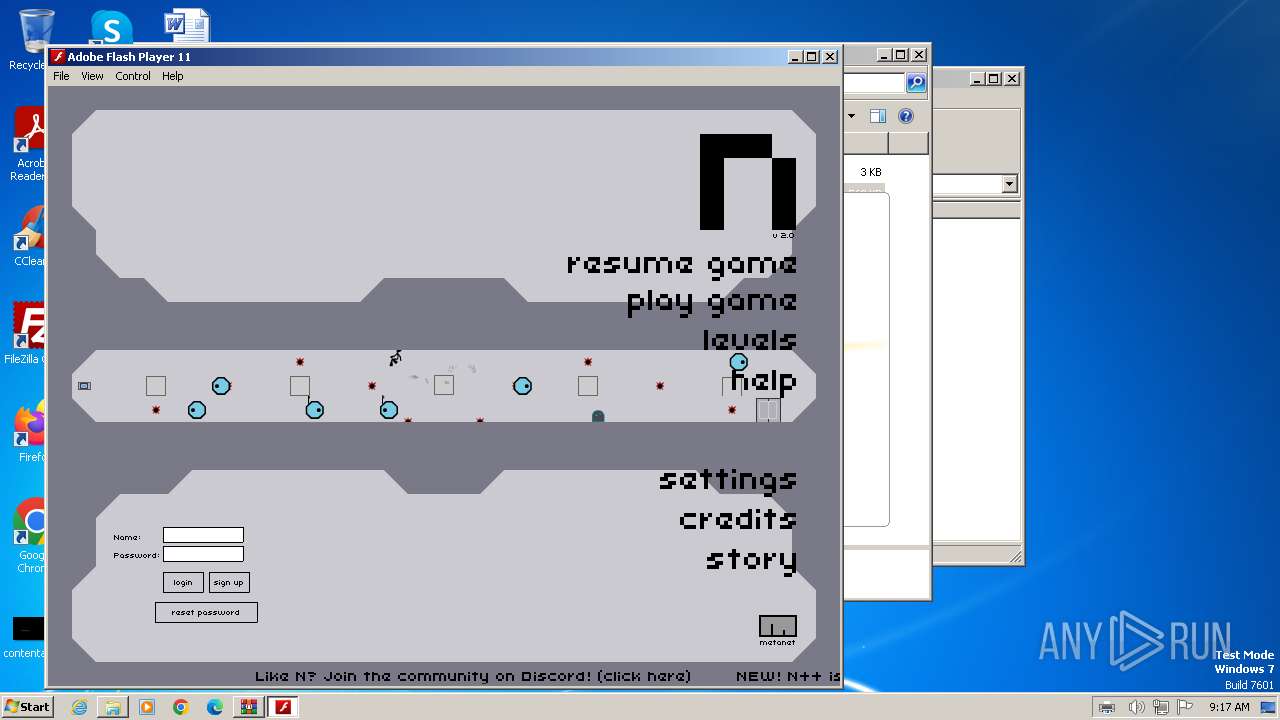
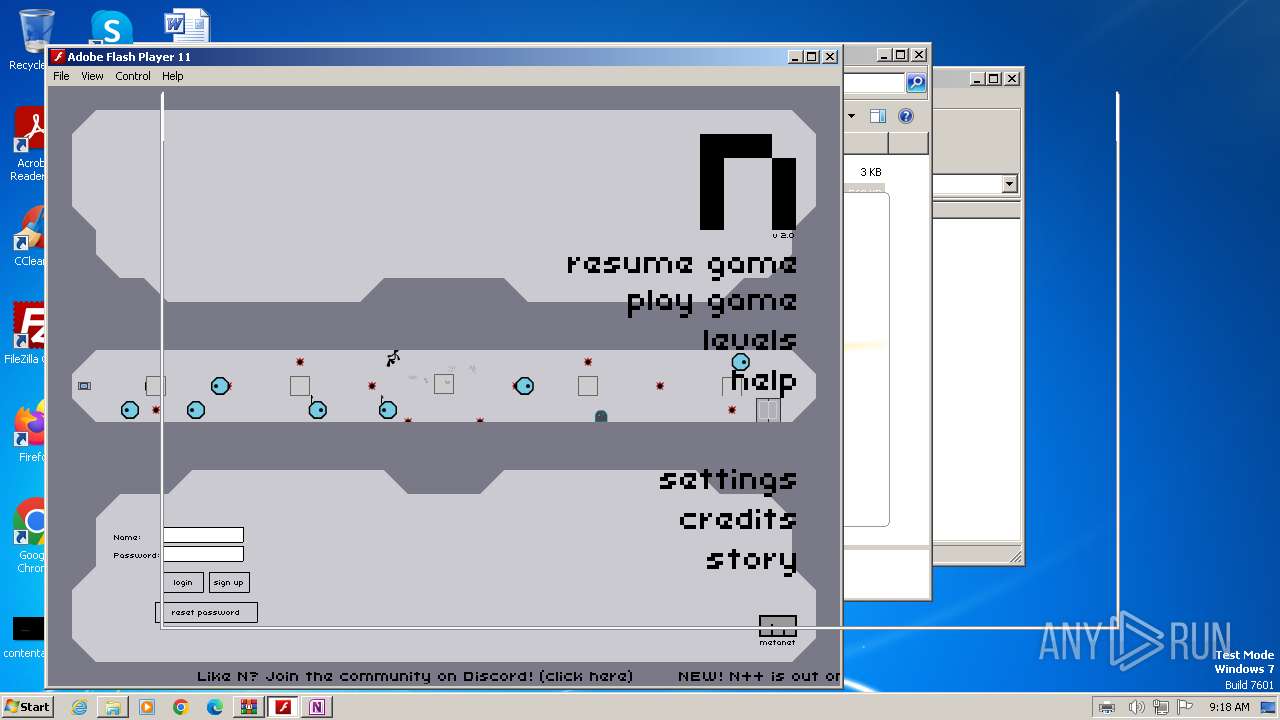
| 2364 | "C:\Users\admin\AppData\Local\Temp\Nv2-PC\Nv2-PC.exe" | C:\Users\admin\AppData\Local\Temp\Nv2-PC\Nv2-PC.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems, Inc. Integrity Level: MEDIUM Description: Adobe Flash Player 11.1 r102 Exit code: 0 Version: 11,1,102,55 Modules
| |||||||||||||||
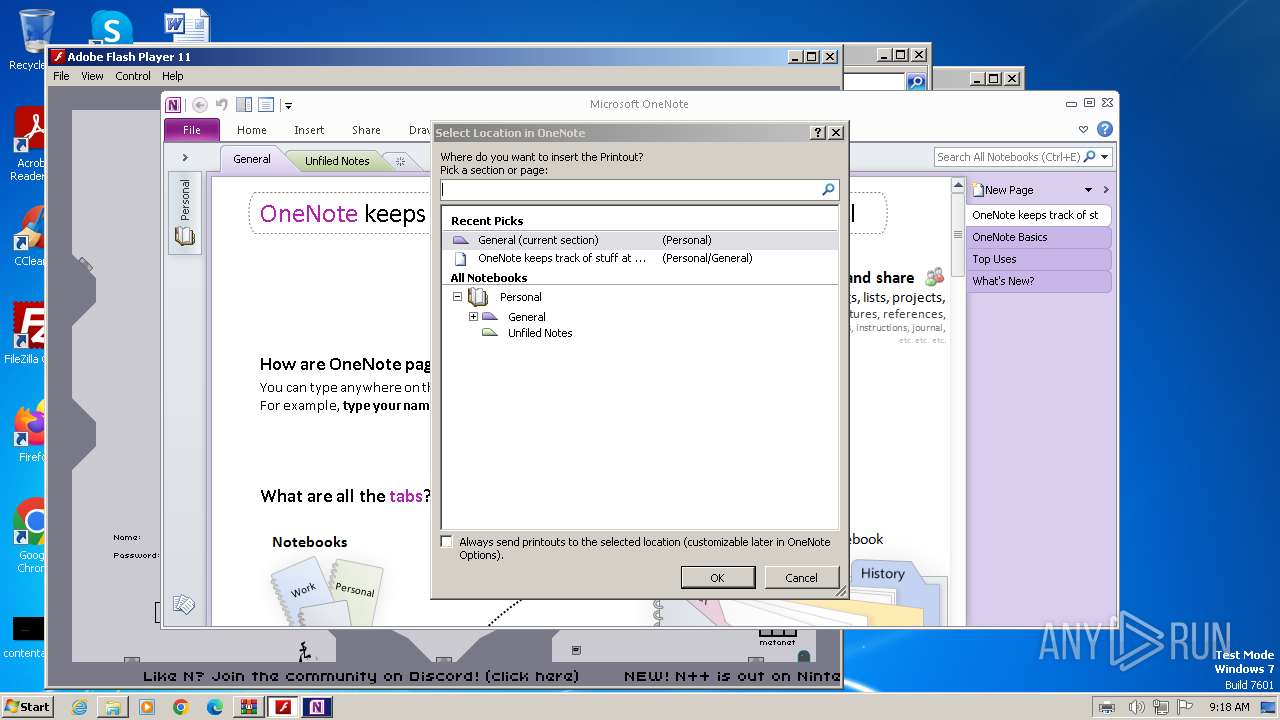
| 2804 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{B4730B4F-5B06-42A0-BDB8-A40CE4C21A5B}.xps" 133545358780260000 | C:\Program Files\Microsoft Office\Office14\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Exit code: 0 Version: 14.0.6022.1000 Modules
| |||||||||||||||
| 3556 | /tsr | C:\Program Files\Microsoft Office\Office14\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Quick Launcher Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 3720 | "C:\Users\admin\AppData\Local\Temp\Nv2-PC\Nv2-PC.exe" | C:\Users\admin\AppData\Local\Temp\Nv2-PC\Nv2-PC.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems, Inc. Integrity Level: MEDIUM Description: Adobe Flash Player 11.1 r102 Exit code: 0 Version: 11,1,102,55 Modules
| |||||||||||||||
Total events
12 779
Read events
12 635
Write events
125
Delete events
19
Modification events
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nv2-PC.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
36
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 980 | printfilterpipelinesvc.exe | C:\Windows\system32\spool\PRINTERS\PPm8egt6x1thzwqnk272exb05_.TMP | — | |
MD5:— | SHA256:— | |||
| 980 | printfilterpipelinesvc.exe | C:\Windows\system32\spool\PRINTERS\PPx3m1f34urpv46plr0y08uwqkb.TMP | — | |
MD5:— | SHA256:— | |||
| 980 | printfilterpipelinesvc.exe | C:\Windows\system32\spool\PRINTERS\PPklrqwx3wumdoytcnu0y3m02rc.TMP | — | |
MD5:— | SHA256:— | |||
| 2804 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Temp\CVR1CD5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2804 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\14.0\OneNoteOfflineCache.onecache | — | |
MD5:— | SHA256:— | |||
| 3720 | Nv2-PC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\crossdomain[1].xml | text | |
MD5:0F66B1BB0634CC202B610A0359FDFDE0 | SHA256:2ABBA8E0BDFA5E9BBC2FCAB9C60D4477A375230C14E0F291EC72737806C13E8B | |||
| 3720 | Nv2-PC.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | binary | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3720 | Nv2-PC.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\#SharedObjects\VZTUFNTU\localhost\n_account.sxx | sol | |
MD5:250B5146F696E4841010DD154CE10817 | SHA256:17CBD99E4A64C359E6201B36A170F0469571AECD6A21FD98D57C0D6401534A7B | |||
| 3720 | Nv2-PC.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | binary | |
MD5:4E442C66F85325FE25C83EE8855432CA | SHA256:C1F7F9394B37899EC9EFE36DD2C26C80837F357D86F20F67DC13F6491F0CFEA9 | |||
| 3720 | Nv2-PC.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\#local\settings.sxx | sol | |
MD5:662FE1E7665F2B4DFDD4F5DD79C6C264 | SHA256:2CCB9D5C8B6AA6E9131DB74072416AFE895A86C789642ACFE56FC8DA8181DBA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
3
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3720 | Nv2-PC.exe | GET | 200 | 163.172.57.40:80 | http://nserver.thewayoftheninja.org/crossdomain.xml | unknown | text | 524 b | unknown |
3720 | Nv2-PC.exe | GET | 200 | 16.182.39.216:80 | http://bucket.thewayoftheninja.org/news.xml?RND=6881710062219979 | unknown | xml | 2.27 Kb | unknown |
3720 | Nv2-PC.exe | GET | 200 | 188.114.97.0:80 | http://www.thewayoftheninja.org/crossdomain.xml | unknown | text | 524 b | unknown |
2364 | Nv2-PC.exe | GET | 200 | 16.182.39.216:80 | http://bucket.thewayoftheninja.org/news.xml?RND=6101710062272700 | unknown | xml | 2.27 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3720 | Nv2-PC.exe | 163.172.57.40:80 | nserver.thewayoftheninja.org | Online S.a.s. | FR | unknown |
3720 | Nv2-PC.exe | 16.182.39.216:80 | bucket.thewayoftheninja.org | — | US | unknown |
3720 | Nv2-PC.exe | 188.114.97.0:80 | www.thewayoftheninja.org | CLOUDFLARENET | NL | unknown |
2364 | Nv2-PC.exe | 16.182.39.216:80 | bucket.thewayoftheninja.org | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nserver.thewayoftheninja.org |
| unknown |
www.thewayoftheninja.org |
| unknown |
bucket.thewayoftheninja.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3720 | Nv2-PC.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
ONENOTE.EXE |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ONENOTE.EXE |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ONENOTE.EXE |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ONENOTE.EXE |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ONENOTE.EXE |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ONENOTE.EXE |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|