| URL: | zalo.me |
| Full analysis: | https://app.any.run/tasks/0125f3e0-3315-4b56-8cd7-7285a4b3ea00 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 13:33:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | A3188BB4158A5F5367B3891C769468D0 |
| SHA1: | FFB5D22153A8E74CCADB98D38330CDBA1D9B0368 |
| SHA256: | A5E1089A7D3111247334729A18612075FBC830BA735EBCB8AAA55C76D4F139F3 |
| SSDEEP: | 3:XL9:XR |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 6420)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- ZaloSetup-24.8.4.exe (PID: 2868)
Drops the executable file immediately after the start
- ZaloSetup-24.8.4.exe (PID: 2868)
Executable content was dropped or overwritten
- ZaloSetup-24.8.4.exe (PID: 2868)
Reads security settings of Internet Explorer
- ZaloSetup-24.8.4.exe (PID: 2868)
The process creates files with name similar to system file names
- ZaloSetup-24.8.4.exe (PID: 2868)
Drops 7-zip archiver for unpacking
- ZaloSetup-24.8.4.exe (PID: 2868)
Process drops legitimate windows executable
- ZaloSetup-24.8.4.exe (PID: 2868)
Application launched itself
- Zalo.exe (PID: 7124)
Uses REG/REGEDIT.EXE to modify registry
- Zalo.exe (PID: 7124)
Starts application with an unusual extension
- cmd.exe (PID: 5372)
- cmd.exe (PID: 812)
- cmd.exe (PID: 6196)
- cmd.exe (PID: 2232)
Starts CMD.EXE for commands execution
- Zalo.exe (PID: 4528)
- Zalo.exe (PID: 3004)
- Zalo.exe (PID: 1688)
- Zalo.exe (PID: 32)
Uses WMIC.EXE to obtain operating system information
- Zalo.exe (PID: 7124)
Creates a software uninstall entry
- ZaloSetup-24.8.4.exe (PID: 2868)
The process drops C-runtime libraries
- ZaloSetup-24.8.4.exe (PID: 2868)
INFO
Application launched itself
- chrome.exe (PID: 6628)
The process uses the downloaded file
- chrome.exe (PID: 6260)
- chrome.exe (PID: 6628)
- ZaloSetup-24.8.4.exe (PID: 2868)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6628)
Checks proxy server information
- ZaloSetup-24.8.4.exe (PID: 2868)
- Zalo.exe (PID: 7124)
Reads the computer name
- ZaloSetup-24.8.4.exe (PID: 2868)
- Zalo.exe (PID: 7124)
- Zalo.exe (PID: 5704)
- Zalo.exe (PID: 4748)
- ZaloCap.exe (PID: 5164)
- Zalo.exe (PID: 3004)
- Zalo.exe (PID: 32)
Create files in a temporary directory
- ZaloSetup-24.8.4.exe (PID: 2868)
- Zalo.exe (PID: 7124)
Executable content was dropped or overwritten
- chrome.exe (PID: 6628)
Checks supported languages
- ZaloSetup-24.8.4.exe (PID: 2868)
- Zalo.exe (PID: 7124)
- Zalo.exe (PID: 6424)
- Zalo.exe (PID: 4748)
- Zalo.exe (PID: 5704)
- Zalo.exe (PID: 3004)
- ZaloCap.exe (PID: 5164)
- Zalo.exe (PID: 32)
- Zalo.exe (PID: 1688)
- Zalo.exe (PID: 4528)
- chcp.com (PID: 6528)
- chcp.com (PID: 6016)
- chcp.com (PID: 3144)
- chcp.com (PID: 1748)
Creates files or folders in the user directory
- ZaloSetup-24.8.4.exe (PID: 2868)
- Zalo.exe (PID: 7124)
- Zalo.exe (PID: 5704)
- Zalo.exe (PID: 1688)
- Zalo.exe (PID: 32)
- Zalo.exe (PID: 3004)
Manual execution by a user
- Zalo.exe (PID: 6424)
Reads Environment values
- Zalo.exe (PID: 7124)
- Zalo.exe (PID: 3004)
- Zalo.exe (PID: 1688)
- Zalo.exe (PID: 32)
- Zalo.exe (PID: 4528)
Reads CPU info
- Zalo.exe (PID: 7124)
Process checks computer location settings
- Zalo.exe (PID: 7124)
- Zalo.exe (PID: 32)
- Zalo.exe (PID: 1688)
- Zalo.exe (PID: 4528)
- Zalo.exe (PID: 3004)
Changes the display of characters in the console
- chcp.com (PID: 3144)
- chcp.com (PID: 6528)
- chcp.com (PID: 6016)
- chcp.com (PID: 1748)
Reads the machine GUID from the registry
- Zalo.exe (PID: 7124)
Reads the software policy settings
- Zalo.exe (PID: 7124)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
180
Monitored processes
41
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\Zalo.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\ZaloData" --app-user-model-id=com.vng.zalo --app-path="C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\resources\app.asar" --no-sandbox --no-zygote --first-renderer-process --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2852 --field-trial-handle=1760,i,1375613178815994854,17306084403173036485,131072 --enable-features=JXL --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\Zalo.exe | — | Zalo.exe | |||||||||||
User: admin Company: VNG Corp. Integrity Level: MEDIUM Description: Zalo Version: 24.8.4 Modules
| |||||||||||||||
| 608 | wmic os get osarchitecture | C:\Windows\SysWOW64\wbem\WMIC.exe | — | Zalo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\SysWOW64\cmd.exe | — | Zalo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\Zalo.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\ZaloData" --app-user-model-id=com.vng.zalo --app-path="C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\resources\app.asar" --no-sandbox --no-zygote --node-integration-in-worker --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3068 --field-trial-handle=1760,i,1375613178815994854,17306084403173036485,131072 --enable-features=JXL --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Zalo\Zalo-24.8.4\Zalo.exe | — | Zalo.exe | |||||||||||
User: admin Company: VNG Corp. Integrity Level: MEDIUM Description: Zalo Version: 24.8.4 Modules
| |||||||||||||||
| 1748 | chcp | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2232 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\SysWOW64\cmd.exe | — | Zalo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5164 --field-trial-handle=1852,i,4387884595927114575,882339059087300039,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
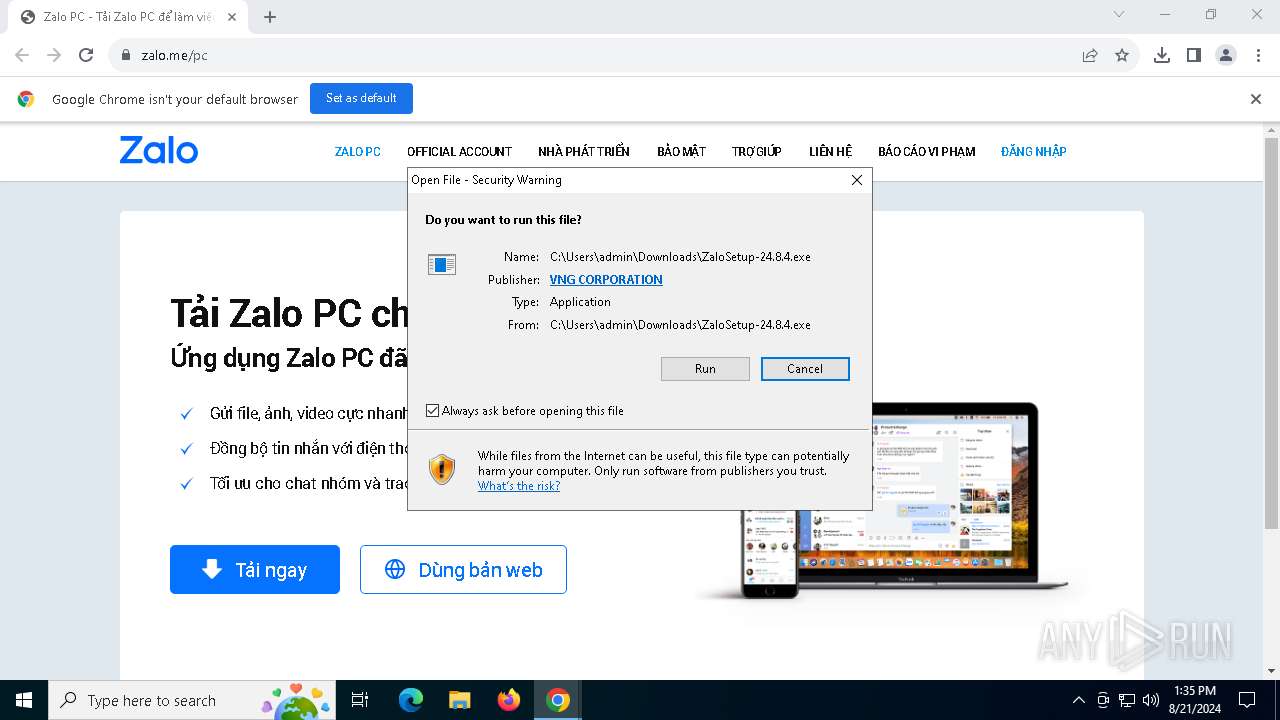
| 2868 | "C:\Users\admin\Downloads\ZaloSetup-24.8.4.exe" | C:\Users\admin\Downloads\ZaloSetup-24.8.4.exe | chrome.exe | ||||||||||||
User: admin Company: VNG Corp. Integrity Level: MEDIUM Description: Zalo - Nhắn gửi yêu thương Exit code: 0 Version: 24.8.4 Modules
| |||||||||||||||
Total events
25 453
Read events
25 339
Write events
88
Delete events
26
Modification events
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6628) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
151
Suspicious files
332
Text files
68
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF11ee64.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF11ee74.TMP | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 6628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF11efeb.TMP | text | |
MD5:4320BE33704F77FF4DF4921358D2C50C | SHA256:8FDF7387C47EB272670EFF935D71492F03EAFAA55A8B22C05658BB0F1AC472EE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
81
DNS requests
61
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2584 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
6448 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2228 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2584 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2636 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2212 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6628 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6888 | chrome.exe | 49.213.95.248:80 | zalo.me | VNG Corporation | VN | unknown |
6888 | chrome.exe | 49.213.95.248:443 | zalo.me | VNG Corporation | VN | unknown |
6888 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | unknown |
6888 | chrome.exe | 49.213.95.43:443 | stc-zaloprofile.zdn.vn | VNG Corporation | VN | unknown |
6888 | chrome.exe | 222.255.114.102:443 | stc-sp.zadn.vn | VNPT Corp | VN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
zalo.me |
| whitelisted |
accounts.google.com |
| whitelisted |
stc-zaloprofile.zdn.vn |
| whitelisted |
stc-sp.zadn.vn |
| whitelisted |
za.zdn.vn |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2868 | ZaloSetup-24.8.4.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2868 | ZaloSetup-24.8.4.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2868 | ZaloSetup-24.8.4.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2868 | ZaloSetup-24.8.4.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2868 | ZaloSetup-24.8.4.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
Process | Message |
|---|---|
ZaloCap.exe | Logger configuration: "CONF: :/texts/log_conf.txt # LOG_LEVEL: ALL # LOG_FILES: C:/Users/admin/AppData/Roaming/ZaloApp/scrshot.log|StdOutput\n\twith pattern: #TIME | #MESSAGE"
|
ZaloCap.exe | Logger configuration after reading settings: "CONF: :/texts/log_conf.txt # LOG_LEVEL: ALL # LOG_FILES: C:/Users/admin/AppData/Roaming/ZaloApp/scrshot.log|StdOutput\n\twith pattern: #TIME | #MESSAGE"
|
ZaloCap.exe | " 2024/08/21 - 13:35:44:125 | App started"
|
ZaloCap.exe | " 2024/08/21 - 13:35:44:188 | class NS_ScrollCaptureApp::TrickLoaderThread::run | Start"
|
ZaloCap.exe | param = ("C:\\Users\\admin\\AppData\\Local\\Programs\\Zalo\\Zalo-24.8.4\\plugins\\capture\\ZaloCap.exe", "zalo2017")
|
ZaloCap.exe | " 2024/08/21 - 13:35:44:190 | class MainWindow::connectEvents | Connecting communication module & app ..."
|
ZaloCap.exe | " 2024/08/21 - 13:35:47:136 | class NS_ScrollCaptureApp::TrickLoaderThread::run | End"
|