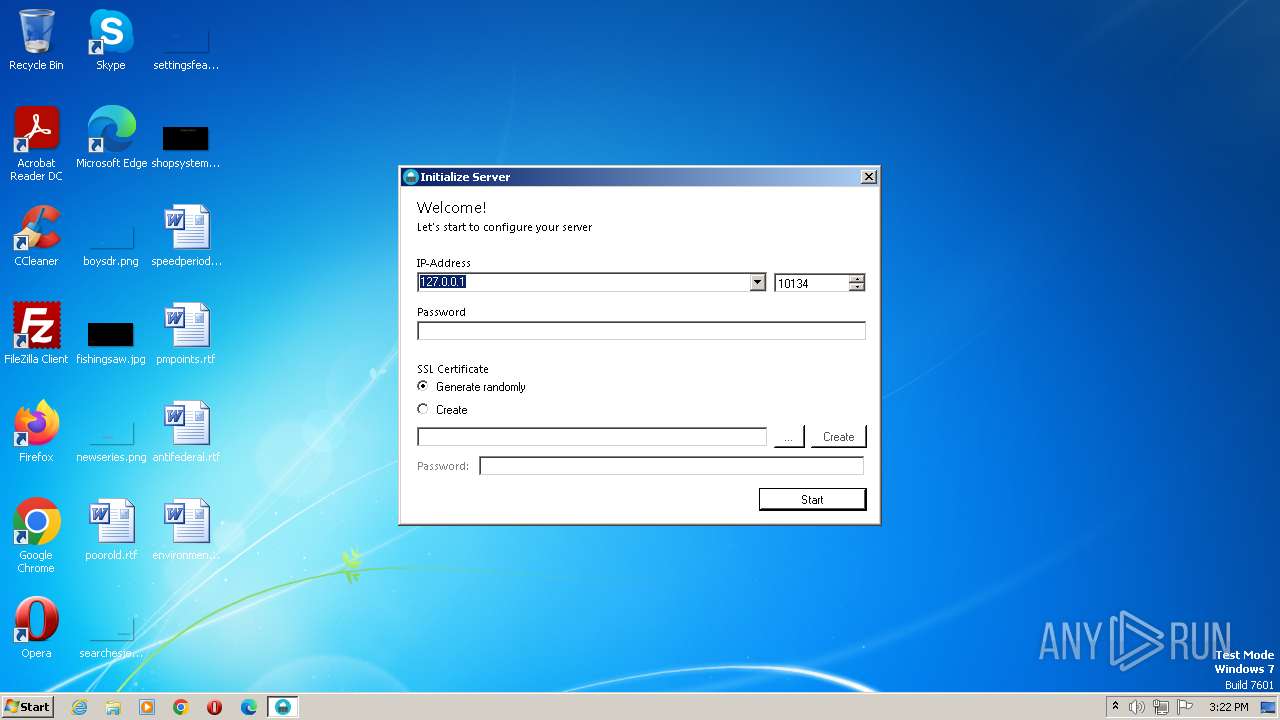
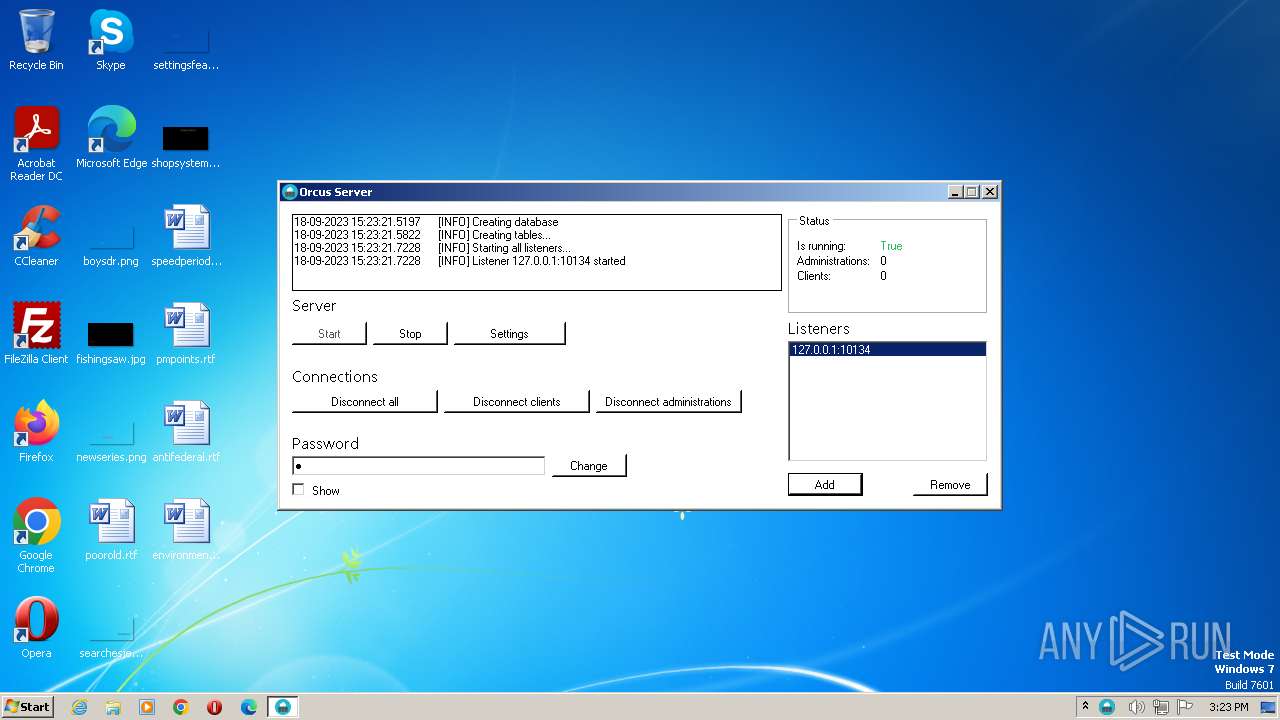
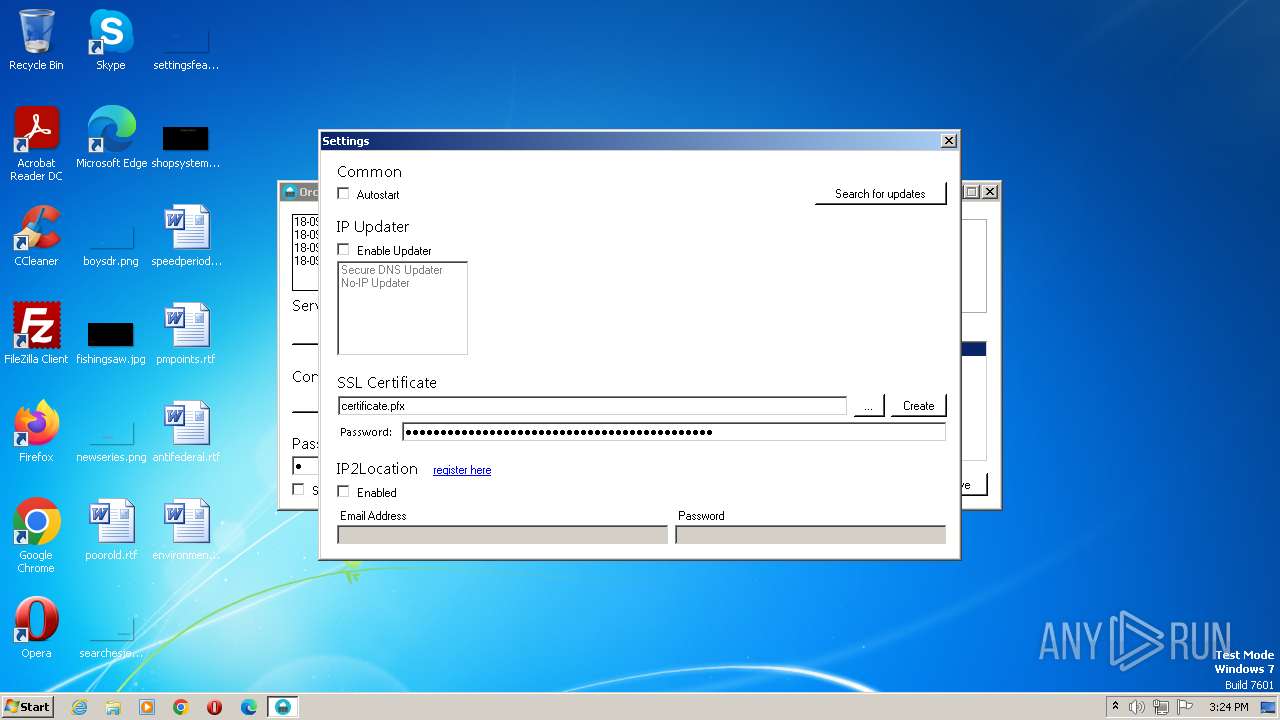
| File name: | Orcus.Server.exe |
| Full analysis: | https://app.any.run/tasks/afa301ec-d23e-4d19-aef2-15341f772be5 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2023, 14:22:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 423C84C4E8FE8FA7685CEED43ACF8335 |
| SHA1: | 7270183B6507932681257B9D9033F51600C4704D |
| SHA256: | A5E07A905FA95FD8E7370FC706682D823AB9B8974F5867E96F1BE9C4E16E0557 |
| SSDEEP: | 98304:9rVrVr1r4rg+4mRF42/986wgzMOr4KqU2TitpA+OxXIKZExcZr+:jmfZ986wiZ4K15I+fxcA |
MALICIOUS
Loads dropped or rewritten executable
- Orcus.Server.exe (PID: 1212)
SUSPICIOUS
Reads the Internet Settings
- Orcus.Server.exe (PID: 1212)
Reads Internet Explorer settings
- Orcus.Server.exe (PID: 1212)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 1548)
- Orcus.Server.exe (PID: 1212)
Reads the computer name
- wmpnscfg.exe (PID: 1548)
- Orcus.Server.exe (PID: 1212)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1548)
- Orcus.Server.exe (PID: 1212)
Checks proxy server information
- Orcus.Server.exe (PID: 1212)
Creates files or folders in the user directory
- Orcus.Server.exe (PID: 1212)
Reads Environment values
- Orcus.Server.exe (PID: 1212)
Creates files in the program directory
- Orcus.Server.exe (PID: 1212)
Create files in a temporary directory
- Orcus.Server.exe (PID: 1212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| AssemblyVersion: | 1.3.0.30063 |
|---|---|
| ProductVersion: | 1.3.0 |
| ProductName: | Orcus.Server |
| OriginalFileName: | Orcus.Server.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © Orcus Technologies 2016 |
| InternalName: | Orcus.Server.exe |
| FileVersion: | 1.3.0 |
| FileDescription: | Orcus Server |
| CompanyName: | Orcus Technologies |
| Comments: | The server clients and administrations can connect to |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.3.0.0 |
| FileVersionNumber: | 1.3.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x332d2e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 113152 |
| CodeSize: | 3345920 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2016:06:08 14:42:09+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1212 | "C:\Users\admin\AppData\Local\Temp\Orcus.Server.exe" | C:\Users\admin\AppData\Local\Temp\Orcus.Server.exe | explorer.exe | ||||||||||||
User: admin Company: Orcus Technologies Integrity Level: MEDIUM Description: Orcus Server Exit code: 0 Version: 1.3.0 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
661
Read events
644
Write events
14
Delete events
3
Modification events
| (PID) Process: | (1548) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{096BDD15-1C2C-475C-80AB-4903765C2694}\{E4D71D1B-ACB9-4D6D-B851-7FD6A7F963E8} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1548) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{096BDD15-1C2C-475C-80AB-4903765C2694} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1548) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{8CE4457A-FA41-492C-8E21-D50AA6CB104B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1212) Orcus.Server.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1212) Orcus.Server.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1212) Orcus.Server.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000004F010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
14
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\certificate.pfx | binary | |
MD5:F7582E53B6940CEB7B9E362D70DA4DD6 | SHA256:77A4C017F21CF5800CC3CFBDFF82614AC16214D563EF633959939FF38F23E0FB | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\config.ini | text | |
MD5:52C5BBD9893B9D8DA779062F51A630B2 | SHA256:5047A3ECB8FCBC1A19A69821CA3533BB7EE0244E86CF87EF8368D43B6DC9A177 | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\settings.json | binary | |
MD5:05A9ED3F9CF75B1D4662E1FEE2692503 | SHA256:92165B18451C99F0E87F35B944BFAC98FAF23C4957EA7633EA784F59D21067F4 | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\log.txt | text | |
MD5:568BB6905C72307A20499FAEF5902AF9 | SHA256:F33570C20B617803F3C3FD69E00D3F7A91E3B89B4591237AD76637EE345007B1 | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\18ea4418e41e10c273475bd555acc31f_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:C0C47476E618A0AE21C033408829A1AD | SHA256:96E61CFDB89B118BA6B9E6097BD788F95E0623EC0FC472367470950983948A73 | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\database.sqlite-journal | binary | |
MD5:01983D086EB7EC96EE5F2D303FE49207 | SHA256:AEF9AB69981E1F80E974A4FB59925E27F8045C34E966DB186A3679EA271E75BD | |||
| 1212 | Orcus.Server.exe | C:\Users\admin\AppData\Local\Temp\Costura\2C9662276C8B885676D4578FFA67621B\32\sqlite3.dll | executable | |
MD5:D8AEC01FF14E3E7AD43A4B71E30482E4 | SHA256:DA1D608BE064555AB3D3D35E6DB64527B8C44F3FA5DDD7C3EC723F80FC99736E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1212 | Orcus.Server.exe | 5.101.152.161:443 | www.orcus.pw | Beget LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.orcus.pw |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
Process | Message |
|---|---|
Orcus.Server.exe | Writing Section: [DATA_MANAGER]
|
Orcus.Server.exe | Writing Key: EnabledNamedPipe=true
|
Orcus.Server.exe | Writing Key: DownloadDataBuffer=4096
|
Orcus.Server.exe | Writing Key: WaitTimeout=30000
|
Orcus.Server.exe | Writing Key: CheckForDeadConnectionsRequestAnswer=20000
|
Orcus.Server.exe | Writing Key: NamedPipeConnectionTimeout=4000
|
Orcus.Server.exe | Writing Key: Version=2
|
Orcus.Server.exe | Writing Key: MaxParallelTransfers=10
|
Orcus.Server.exe | Writing Key: PatchDay=3
|
Orcus.Server.exe | Writing Key: CheckForDeadConnections=true
|