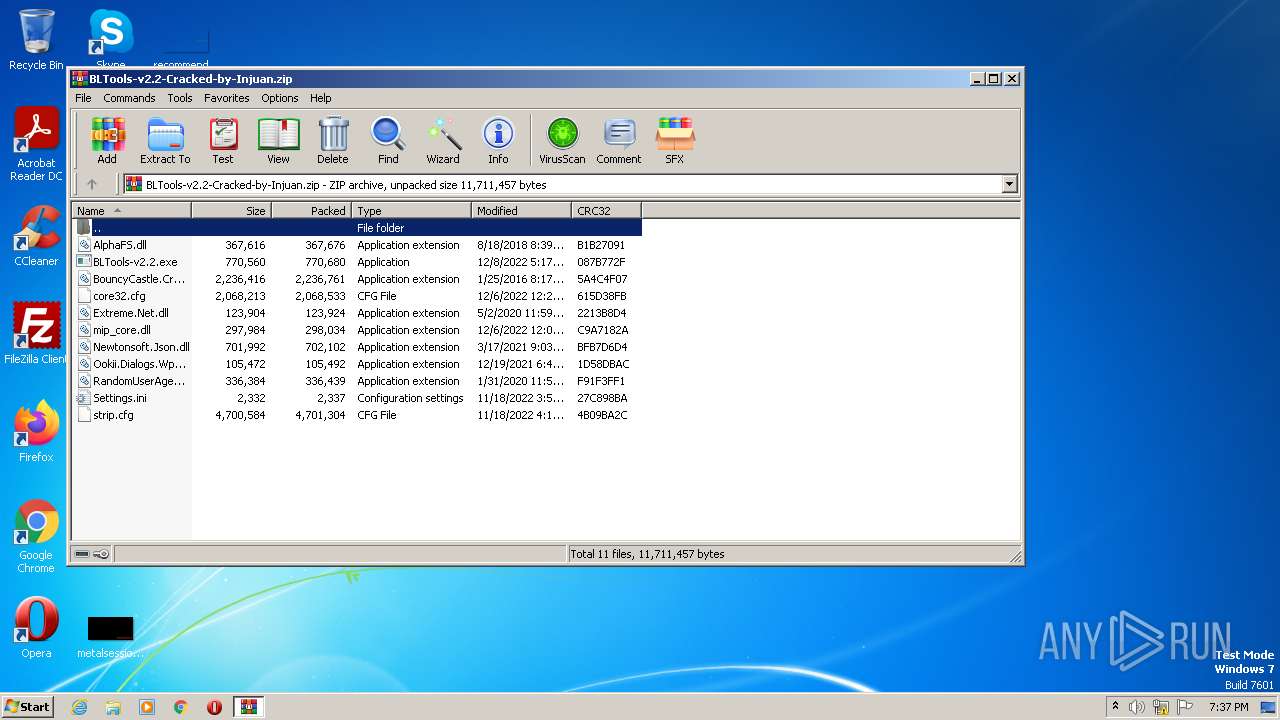
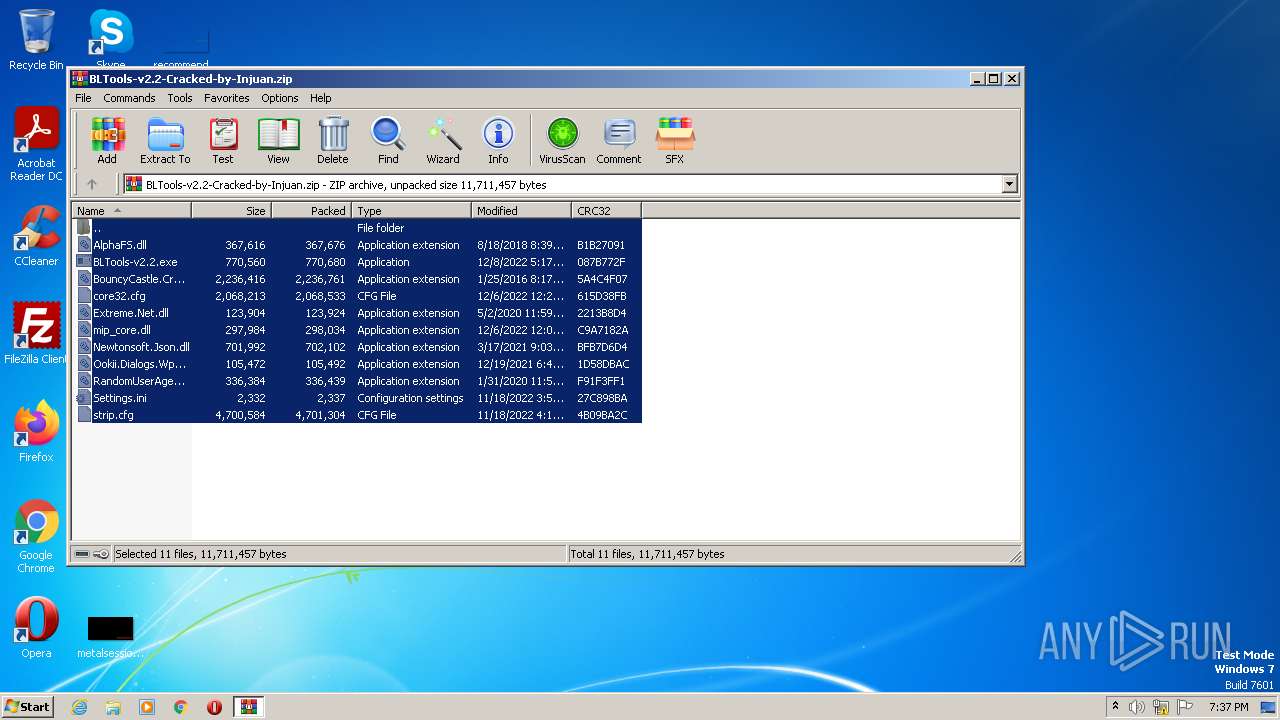
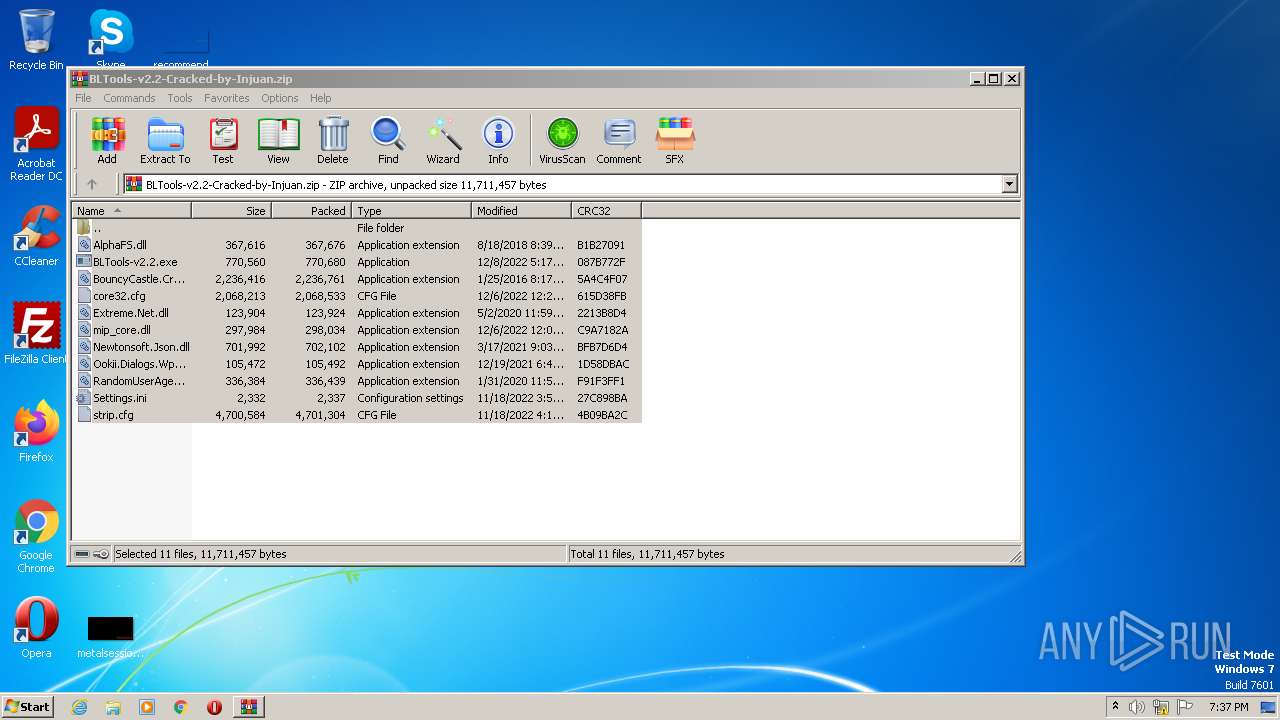
| File name: | BLTools-v2.2-Cracked-by-Injuan.zip |
| Full analysis: | https://app.any.run/tasks/b77a572b-b248-44ac-a43e-330e1e838c15 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 18:37:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D0B708E456AB1BB46EDFD06F877DCD8B |
| SHA1: | AC3021C7FBFEF4B5644D0B42936D09104F5E9977 |
| SHA256: | A5C52E2F9CF2CC5C398BD56F9475D6AAC94E13B3160480A85AFFD82CB97CADF6 |
| SSDEEP: | 196608:DWbxs/7JmdJ37Fb4ujXfnXzhvg+S2HO2zvvf2vA7RG66AsbcKCMbLznldwrM:DWbxs/7cdddRjLhvgv2HO2rf2VhFNLzZ |
MALICIOUS
Application was dropped or rewritten from another process
- BLTools-v2.2.exe (PID: 3892)
- UserOOBE.exe (PID: 1832)
- winsrvhost.exe (PID: 1624)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1936)
- BLTools-v2.2.exe (PID: 3892)
- winsrvhost.exe (PID: 1624)
- svchost.exe (PID: 860)
Create files in the Startup directory
- BLTools-v2.2.exe (PID: 3892)
SUSPICIOUS
Executable content was dropped or overwritten
- BLTools-v2.2.exe (PID: 3892)
The process creates files with name similar to system file names
- BLTools-v2.2.exe (PID: 3892)
Reads the BIOS version
- UserOOBE.exe (PID: 1832)
INFO
Manual execution by a user
- BLTools-v2.2.exe (PID: 3892)
Checks supported languages
- BLTools-v2.2.exe (PID: 3892)
- winsrvhost.exe (PID: 1624)
- UserOOBE.exe (PID: 1832)
Reads the computer name
- BLTools-v2.2.exe (PID: 3892)
- winsrvhost.exe (PID: 1624)
Creates files or folders in the user directory
- BLTools-v2.2.exe (PID: 3892)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2644)
The process checks LSA protection
- BLTools-v2.2.exe (PID: 3892)
- winsrvhost.exe (PID: 1624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | AlphaFS.dll |
|---|---|
| ZipUncompressedSize: | 367616 |
| ZipCompressedSize: | 367676 |
| ZipCRC: | 0xb1b27091 |
| ZipModifyDate: | 2018:08:18 20:39:52 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
40
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 860 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1624 | C:\Users\admin\AppData\Local\\winsrvhost\\winsrvhost.exe BLEnJfF6YWFyyAnQK1FONPEf4JGlmJT7T1PmIl6YE3X3dneEn9vrE8uYjwkEQfbA | C:\Users\admin\AppData\Local\winsrvhost\winsrvhost.exe | BLTools-v2.2.exe | ||||||||||||
User: admin Company: Microsoft® Integrity Level: MEDIUM Description: winsrvhost Exit code: 0 Version: 10.0.19045.549 Modules
| |||||||||||||||
| 1832 | C:\Users\admin\AppData\Local\\UserOOBE\\UserOOBE.exe ,. | C:\Users\admin\AppData\Local\UserOOBE\UserOOBE.exe | — | BLTools-v2.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: UserOOBE Exit code: 0 Version: 10.0.19045.548 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\BLTools-v2.2-Cracked-by-Injuan.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3892 | "C:\Users\admin\Desktop\BLTools-v2.2.exe" | C:\Users\admin\Desktop\BLTools-v2.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 064
Read events
3 026
Write events
38
Delete events
0
Modification events
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
24
Suspicious files
0
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\BLTools-v2.2.exe | executable | |
MD5:— | SHA256:— | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\core32.cfg | executable | |
MD5:C0AC0367A40430AF221B8C03417C2A73 | SHA256:4C01DED1E8E7171E860EBE7B2BB949A2BCDD9B7AAD7E5905A8F2A393670F20EC | |||
| 3892 | BLTools-v2.2.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winsrvhost.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\mip_core.dll | executable | |
MD5:797F15C89FC3DC9D052061202C9D65CF | SHA256:6A2DF4801D1B40E34B9B1BE91B0AAA6E49DA66FD5ED09254D83AF2EC86C8D81C | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\RandomUserAgent.dll | executable | |
MD5:839CD4CE1930EEE45F55F6259468D649 | SHA256:53331BFF5E585C471FAD6789313A2A8A687A586CC0A8D006B24085B91ED7FC9A | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\Settings.ini | text | |
MD5:9A07F774B316B2184B0702FE503B530A | SHA256:A8755CC114A77A7FED9FA5DF6BD6539CEB965CDAD9C7DACAB14F1E5ED0CEE715 | |||
| 2644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2644.22063\strip.cfg | executable | |
MD5:EF5EE302110F10993A991FD9A2350594 | SHA256:F368811F3BB071D6EE006731FE819A0B7D8CD7ED5FD8110AEB5CB0DA22A3A3A7 | |||
| 3892 | BLTools-v2.2.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\UserOOBE.lnk | lnk | |
MD5:DA38BF2C736CB4162D4856606F4B8E63 | SHA256:57FEE7412C86A596113A8B3DCBCFB1DB4CDBF6130EDFDA5058F27DE9639ACFCD | |||
| 3892 | BLTools-v2.2.exe | C:\Users\admin\AppData\Local\UserOOBE\UserOOBE.exe | executable | |
MD5:C0AC0367A40430AF221B8C03417C2A73 | SHA256:4C01DED1E8E7171E860EBE7B2BB949A2BCDD9B7AAD7E5905A8F2A393670F20EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1624 | winsrvhost.exe | GET | 302 | 162.216.242.206:80 | http://stlaip742915.ddnsgeek.com/ | unknown | html | 163 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1624 | winsrvhost.exe | 162.216.242.206:80 | stlaip742915.ddnsgeek.com | DYNU | US | malicious |
— | — | 185.247.224.98:443 | sllaap12925.ddnsgeek.com | Flokinet Ltd | SC | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stlaip742915.ddnsgeek.com |
| malicious |
sllaap12925.ddnsgeek.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1624 | winsrvhost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP User-Agent (Mozilla) - Possible Spyware Related |
1624 | winsrvhost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2 ETPRO signatures available at the full report