analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
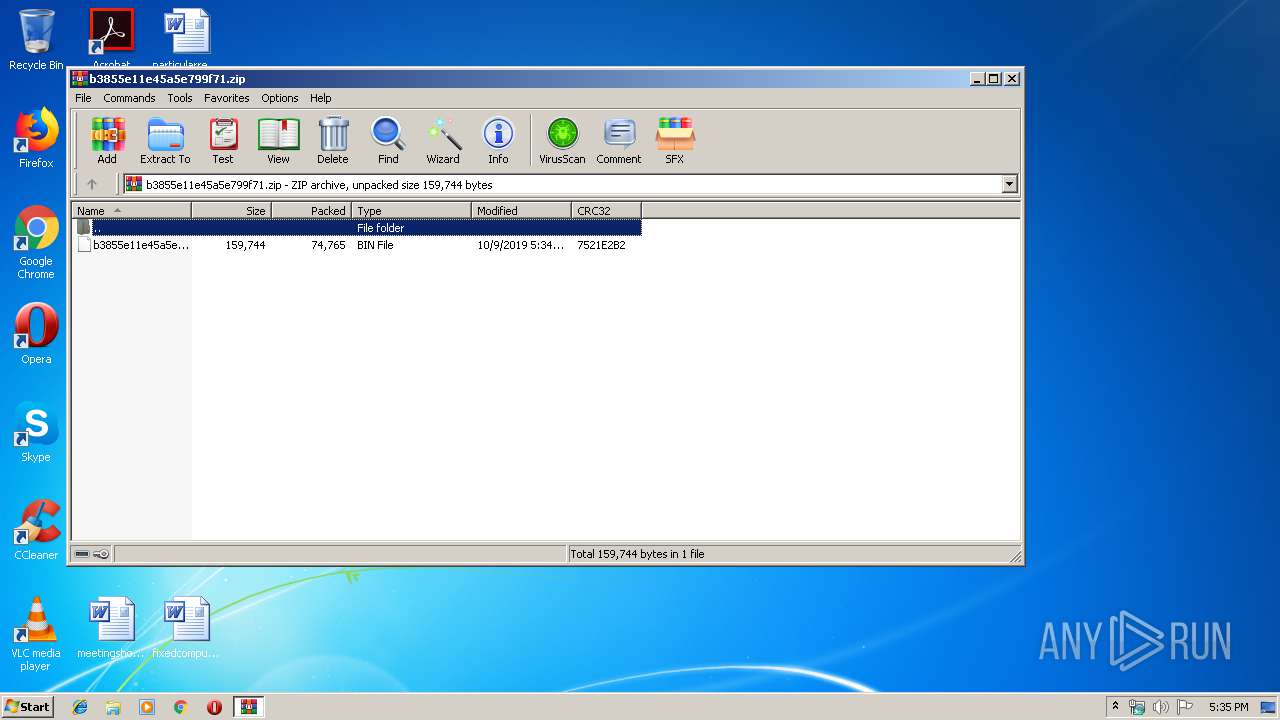
| File name: | b3855e11e45a5e799f71.zip |
| Full analysis: | https://app.any.run/tasks/346f164b-f19e-462e-a387-92a6cf0c5ec2 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 16:34:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 81EF543890E3D18950340527943820AB |
| SHA1: | 60F88D06871B168125234D4B1C5B3A8E9E5767DF |
| SHA256: | A5B626796243F67CED114A6ABF420AA724D14E136283F380447B0055BE685060 |
| SSDEEP: | 1536:0Lz5gv0YFGagfZN1UrtlwgC2XfAQYeXv3CEpjd3bTiqJ4QuGE1A9bC:koi1oXwD2XwePCEppaqR41IbC |
MALICIOUS
Application was dropped or rewritten from another process
- b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe (PID: 2368)
- b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe (PID: 2448)
SUSPICIOUS
Creates files in the program directory
- b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe (PID: 2448)
INFO
Manual execution by user
- b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe (PID: 2448)
- b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe (PID: 2368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.bin |
|---|---|
| ZipUncompressedSize: | 159744 |
| ZipCompressedSize: | 74765 |
| ZipCRC: | 0x7521e2b2 |
| ZipModifyDate: | 2019:10:09 16:34:11 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\b3855e11e45a5e799f71.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.60.0 | ||||
| 2448 | "C:\Users\admin\Desktop\b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe" | C:\Users\admin\Desktop\b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe | explorer.exe | |
User: admin Company: Azhi.Net Integrity Level: MEDIUM Description: 飞鸽传书 Version: 2.06 | ||||
| 2368 | "C:\Users\admin\Desktop\b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe" | C:\Users\admin\Desktop\b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe | — | explorer.exe |
User: admin Company: Azhi.Net Integrity Level: MEDIUM Description: 飞鸽传书 Exit code: 4294967295 Version: 2.06 | ||||
Total events
614
Read events
426
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2772.41866\b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.bin | — | |
MD5:— | SHA256:— | |||
| 2448 | b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe | C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\7c0c73cf483daf02707d115bb631954d_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:EFD2E04A66F4F528C6FBD2FEF997BEAD | SHA256:523E29B838CC62536487864105B44ED51AFE2E1CA6A75D04C2C8B4D80315AFE3 | |||
| 2448 | b3855e11e45a5e799f7160737a044ee3194e17d9bdacf8a353fc10c68a0b8b74.exe | C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\aa84eda69c22c802f2b957e48c095994_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:B123B7397FDD72215FE5E3416D057128 | SHA256:B21C9CD08CF7657837A6211AE2D80C7A8F2565CD2671525E928CE5B7D184B08A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report