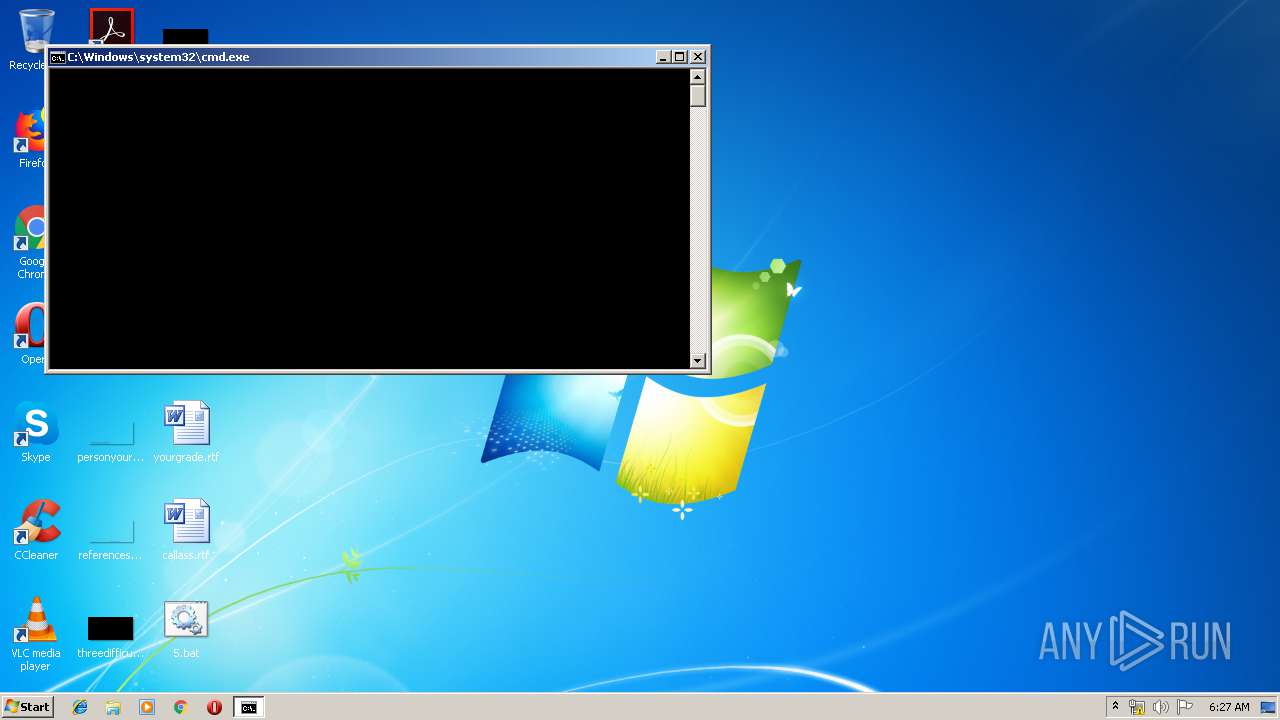
| File name: | 5.bat |
| Full analysis: | https://app.any.run/tasks/54d81a19-197b-42f8-8a4e-bcb1b27109f3 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2019, 05:27:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 8FEC728C50D4775ECB1E6490109052B1 |
| SHA1: | 2E1A92A6671AEF7A5268A96FAED6DC191CD02417 |
| SHA256: | A5AE9146FB009435A838109A4C9A688CB79601AF4127B84EB163BCEBC5EF0D4C |
| SSDEEP: | 48:dJZk7y4qK3TweGaTweGORTeCBrTJWeG5TJe+NGjWF4cf/FHk:dwZqKjkykORTX8llsjGPHk |
MALICIOUS
Application was dropped or rewritten from another process
- Rar.exe (PID: 3900)
- Rar.exe (PID: 2360)
- Rar.exe (PID: 3828)
- Rar.exe (PID: 2188)
- Rar.exe (PID: 2452)
- Rar.exe (PID: 2704)
SUSPICIOUS
Starts CMD.EXE for commands execution
- mshta.exe (PID: 3008)
- cmd.exe (PID: 1028)
Starts MSHTA.EXE for opening HTA or HTMLS files
- cmd.exe (PID: 2608)
Executable content was dropped or overwritten
- cmd.exe (PID: 1028)
Application launched itself
- cmd.exe (PID: 1028)
Starts application with an unusual extension
- cmd.exe (PID: 1028)
INFO
Reads internet explorer settings
- mshta.exe (PID: 3008)
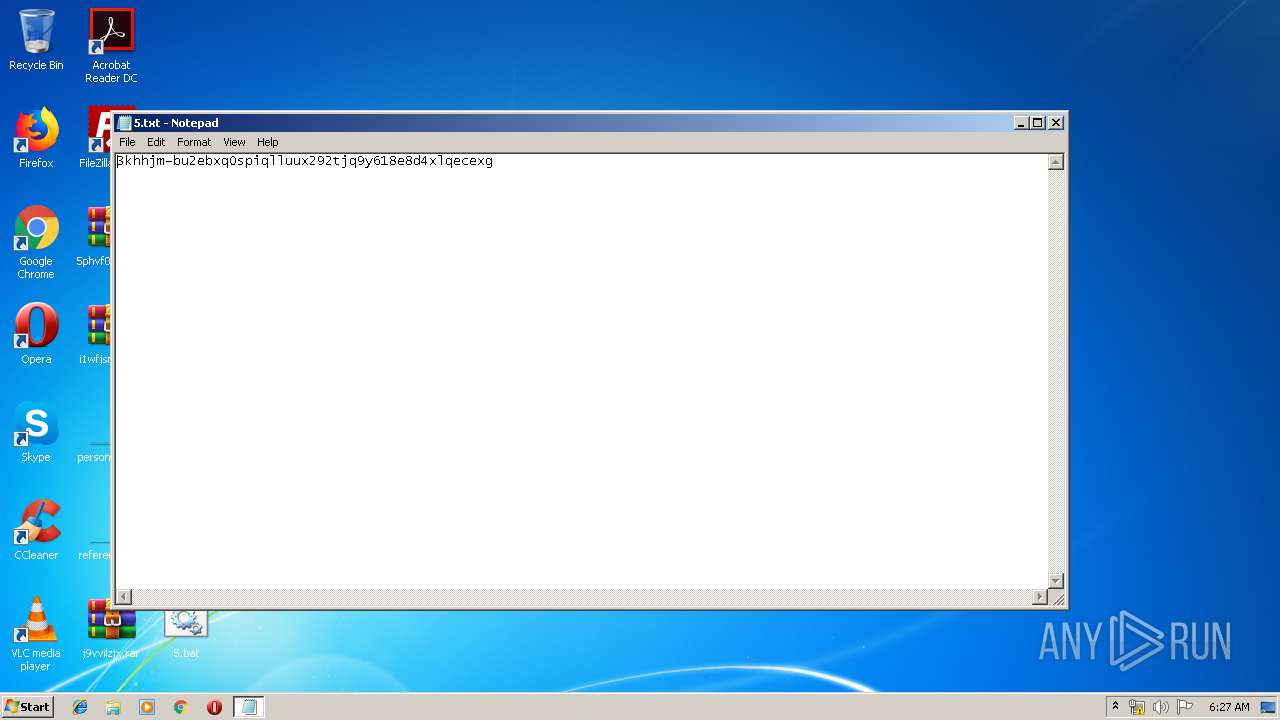
Manual execution by user
- NOTEPAD.EXE (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
73
Monitored processes
39
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | more +1 2.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | more +1 1.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | cmd /c ""C:\Users\admin\Desktop\5.bat" h" | C:\Windows\system32\cmd.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1132 | C:\Windows\system32\cmd.exe /c dir h /a-d /b /s *.exe *.jpg *.doc *.rtf | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1208 | more +1 3.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | more +1 1.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | more +1 3.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1900 | more +1 3.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1912 | more +1 3.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2044 | more +1 1.txt | C:\Windows\system32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
291
Read events
283
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3008) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3660) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 110 | |||
| (PID) Process: | (3660) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 110 | |||
| (PID) Process: | (3660) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (3660) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
Executable files
1
Suspicious files
6
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1028 | cmd.exe | C:\Users\admin\Desktop\a.tmp | — | |
MD5:— | SHA256:— | |||
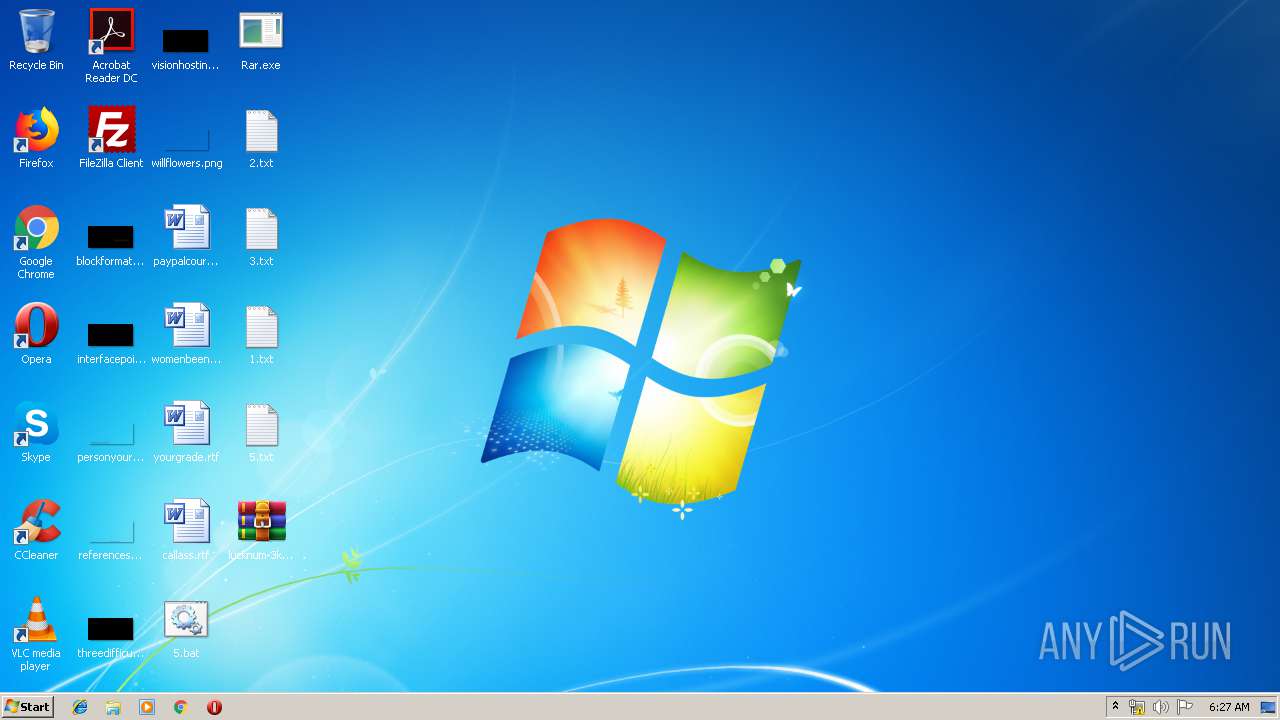
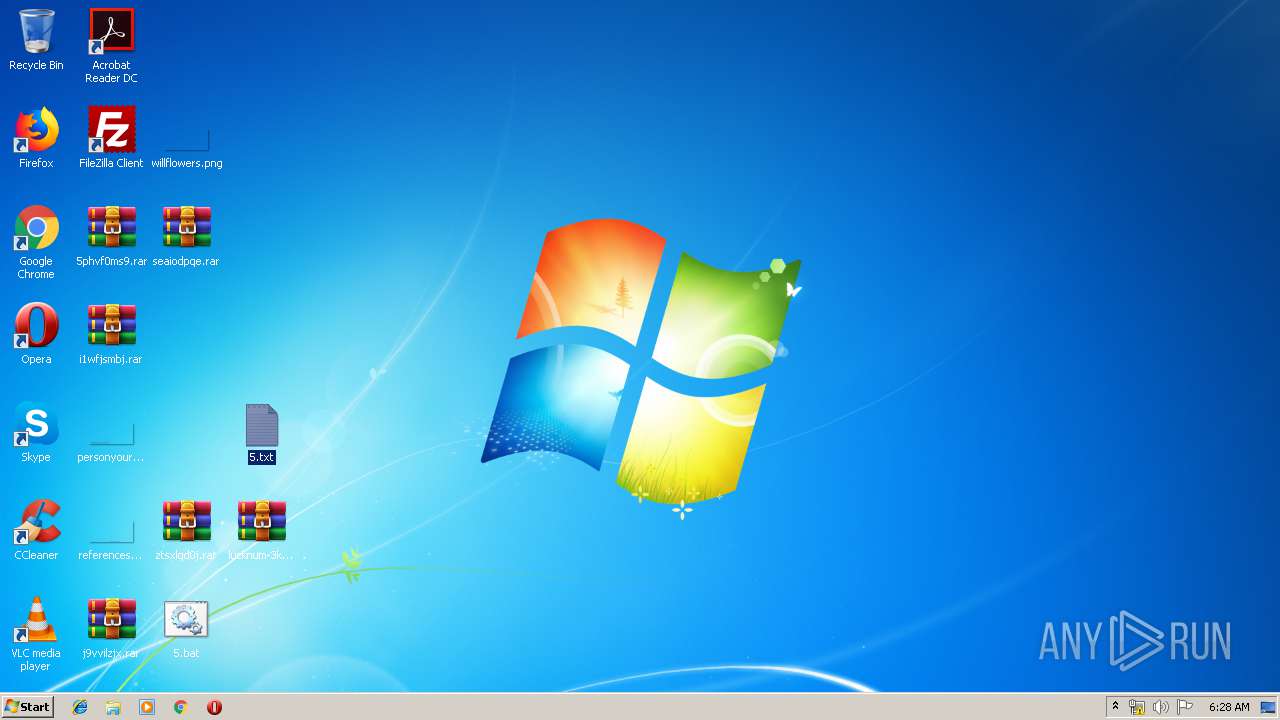
| 2188 | Rar.exe | C:\Users\admin\Desktop\seaiodpqe.rar | compressed | |
MD5:— | SHA256:— | |||
| 3828 | Rar.exe | C:\Users\admin\Desktop\i1wfjsmbj.rar | compressed | |
MD5:— | SHA256:— | |||
| 2452 | Rar.exe | C:\Users\admin\Desktop\ztsxlqd0j.rar | compressed | |
MD5:— | SHA256:— | |||
| 2704 | Rar.exe | C:\Users\admin\Desktop\j9vvilzjx.rar | compressed | |
MD5:— | SHA256:— | |||
| 1028 | cmd.exe | C:\Users\admin\Desktop\2.txt | text | |
MD5:— | SHA256:— | |||
| 1028 | cmd.exe | C:\Users\admin\Desktop\3.txt | text | |
MD5:— | SHA256:— | |||
| 1028 | cmd.exe | C:\Users\admin\Desktop\1.txt | text | |
MD5:— | SHA256:— | |||
| 3900 | Rar.exe | C:\Users\admin\Desktop\lucknum-3khhjm.rar | compressed | |
MD5:— | SHA256:— | |||
| 1028 | cmd.exe | C:\Users\admin\Desktop\4.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report