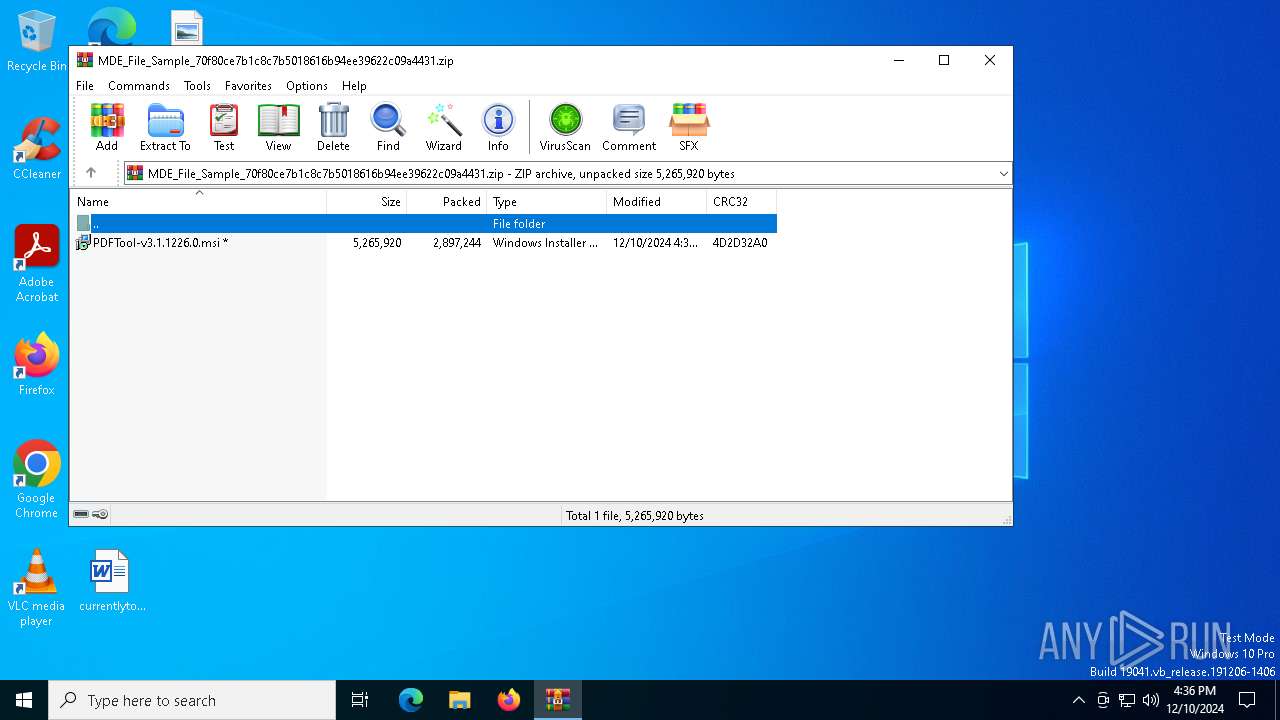
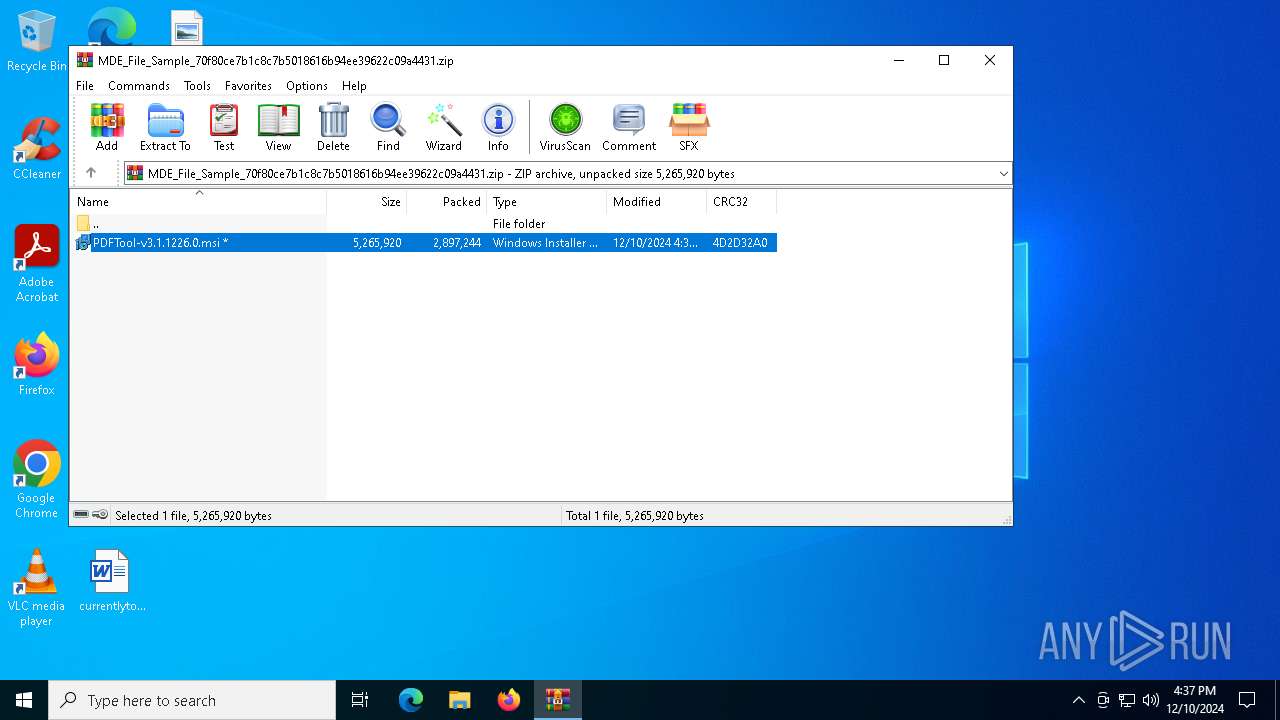
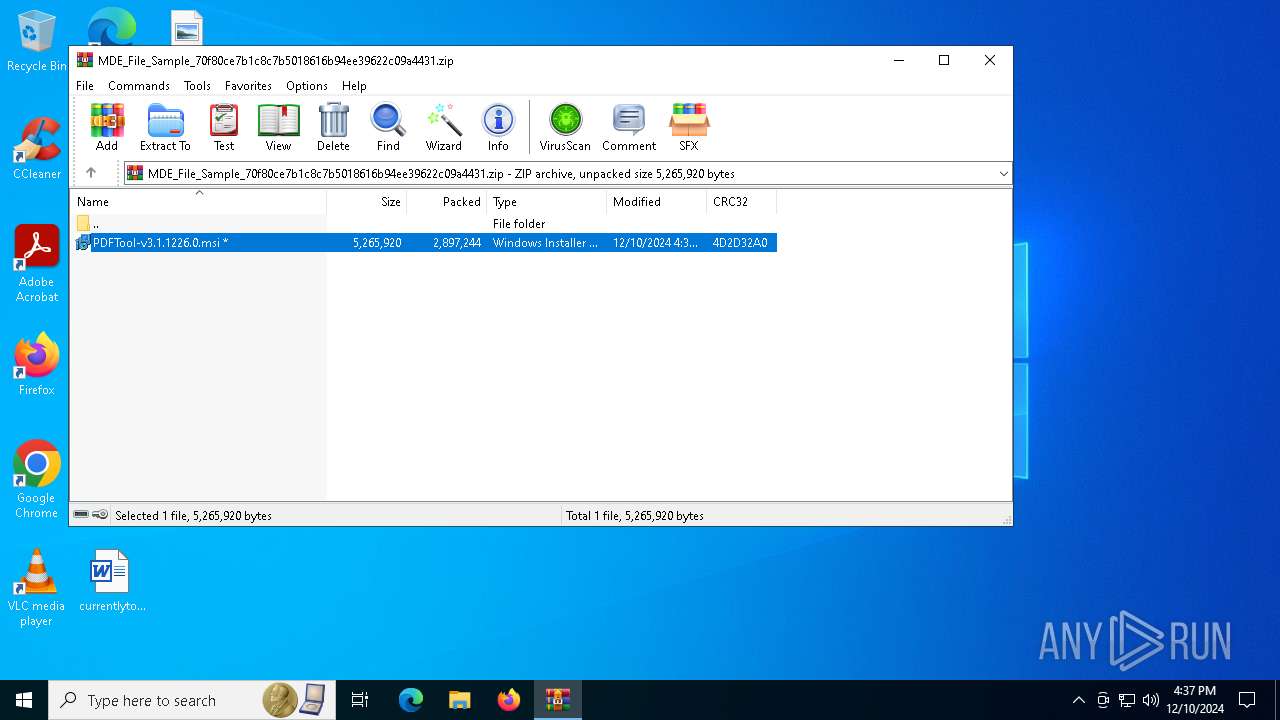
| File name: | MDE_File_Sample_70f80ce7b1c8c7b5018616b94ee39622c09a4431.zip |
| Full analysis: | https://app.any.run/tasks/949c243d-15e1-434e-98ca-188bf36480f2 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 16:36:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6E5612E3717F6AA12E3609535E4B0239 |
| SHA1: | 47CCB0B5BF3585F12F3449A8708483D1C05EF491 |
| SHA256: | A5A9F1974B8BAD0BE058DCCD73D03CBC813E144BAE0A24D87DAD73769EB40A16 |
| SSDEEP: | 98304:NtMJ19gbpADVNA+jnf40eSDx//2zXLIGS9yQcibs0uAEFNfisKu6oY9hRq6nJw00:N1QFctn |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6812)
Bypass execution policy to execute commands
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6344)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 6168)
Changes the autorun value in the registry
- msiexec.exe (PID: 5920)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6812)
- msiexec.exe (PID: 6168)
- msiexec.exe (PID: 6484)
Executes as Windows Service
- VSSVC.exe (PID: 6800)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5920)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6168)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 6168)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6168)
The process executes Powershell scripts
- msiexec.exe (PID: 6168)
Process drops legitimate windows executable
- msiexec.exe (PID: 5920)
Node.exe was dropped
- msiexec.exe (PID: 6168)
Checks Windows Trust Settings
- msiexec.exe (PID: 6168)
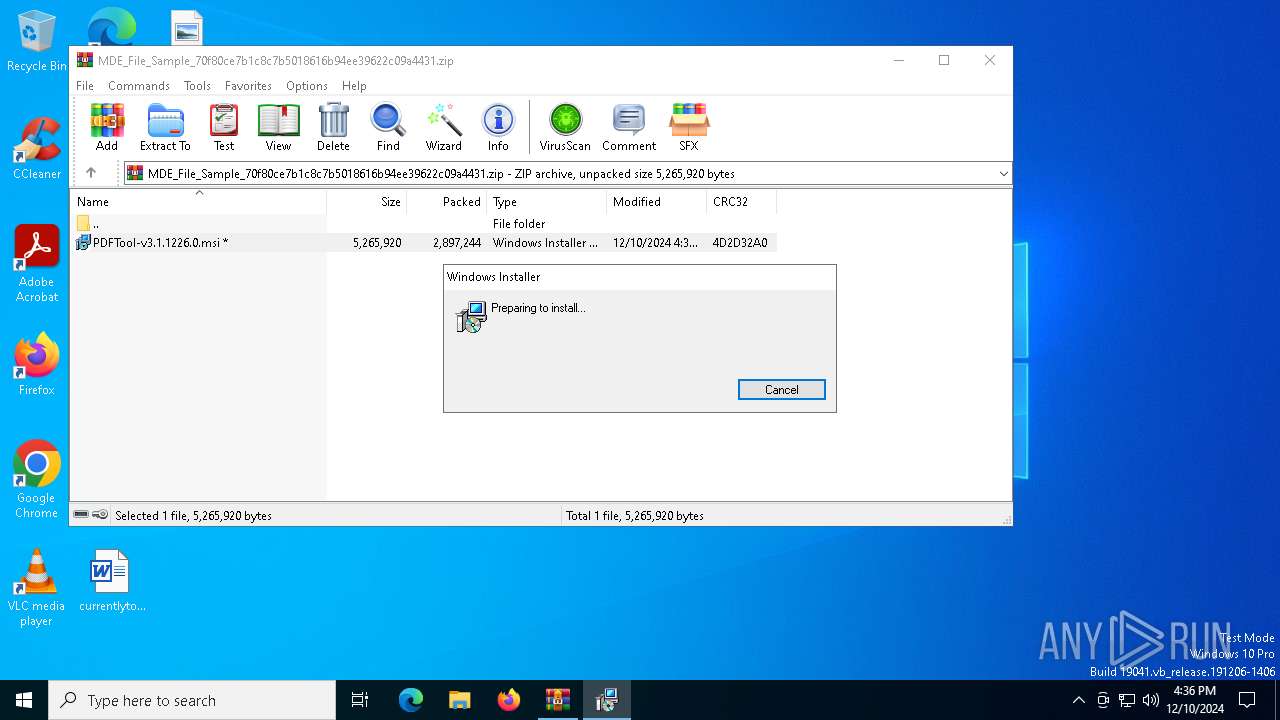
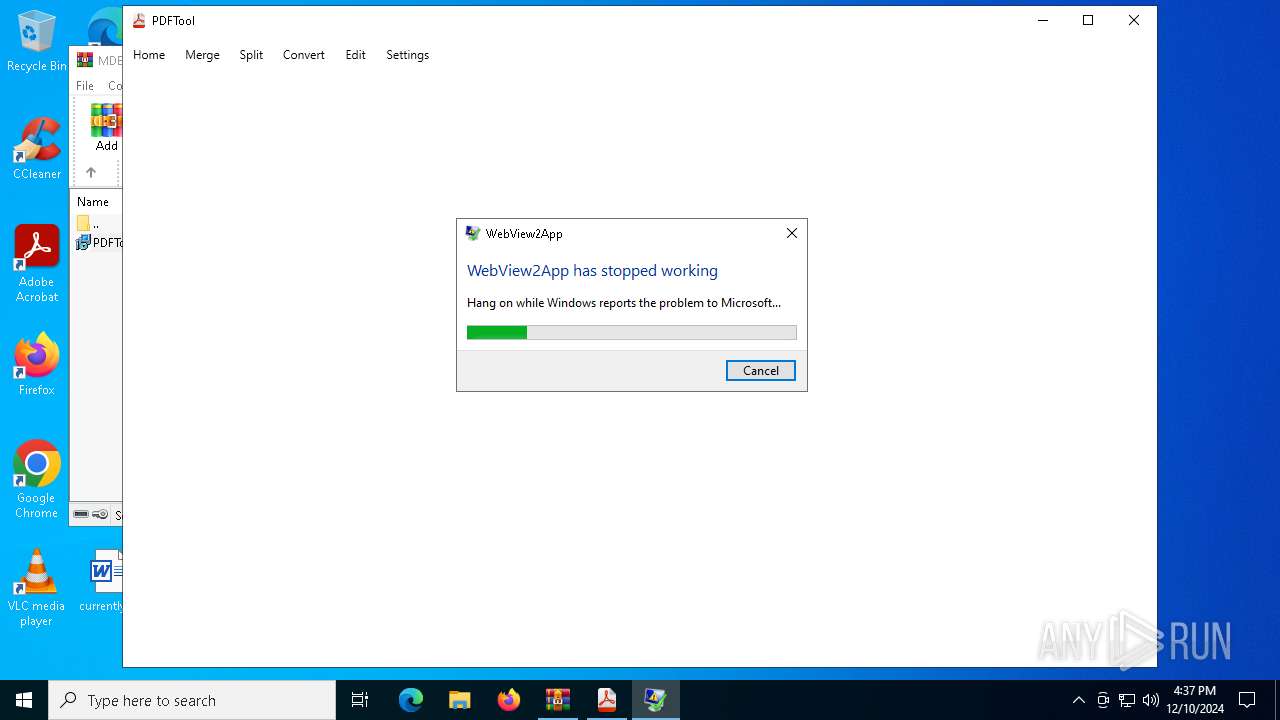
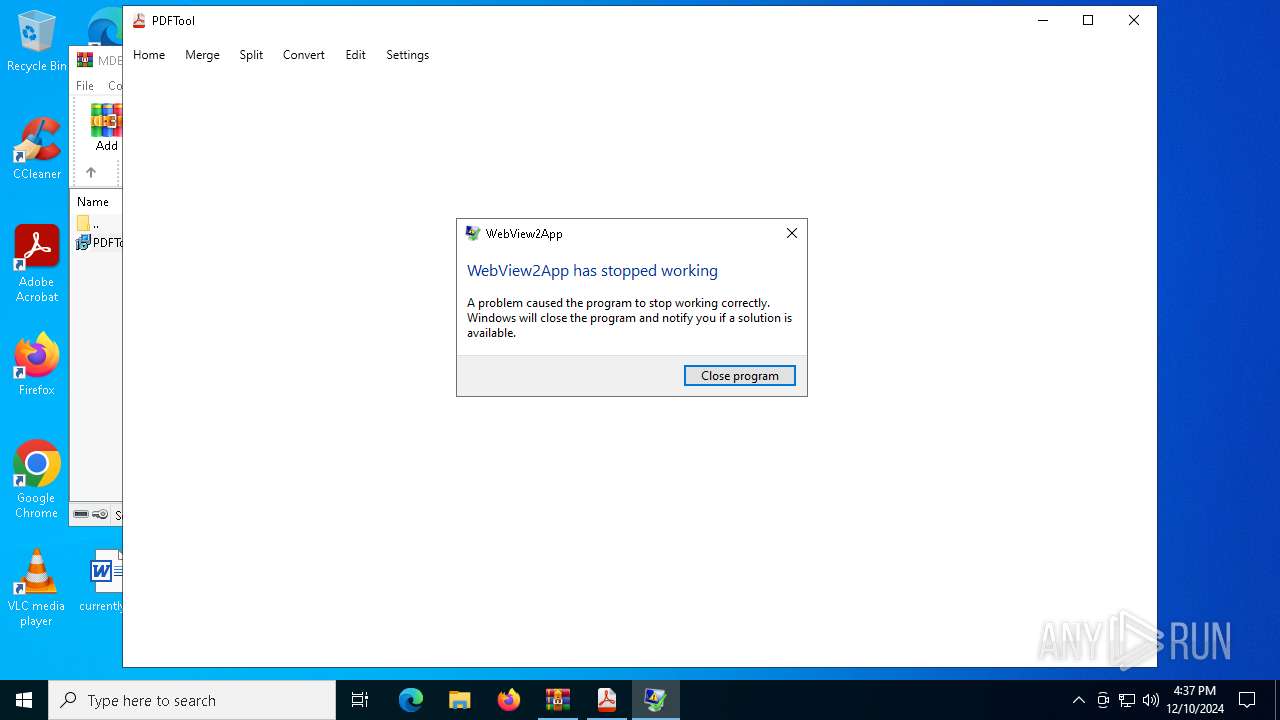
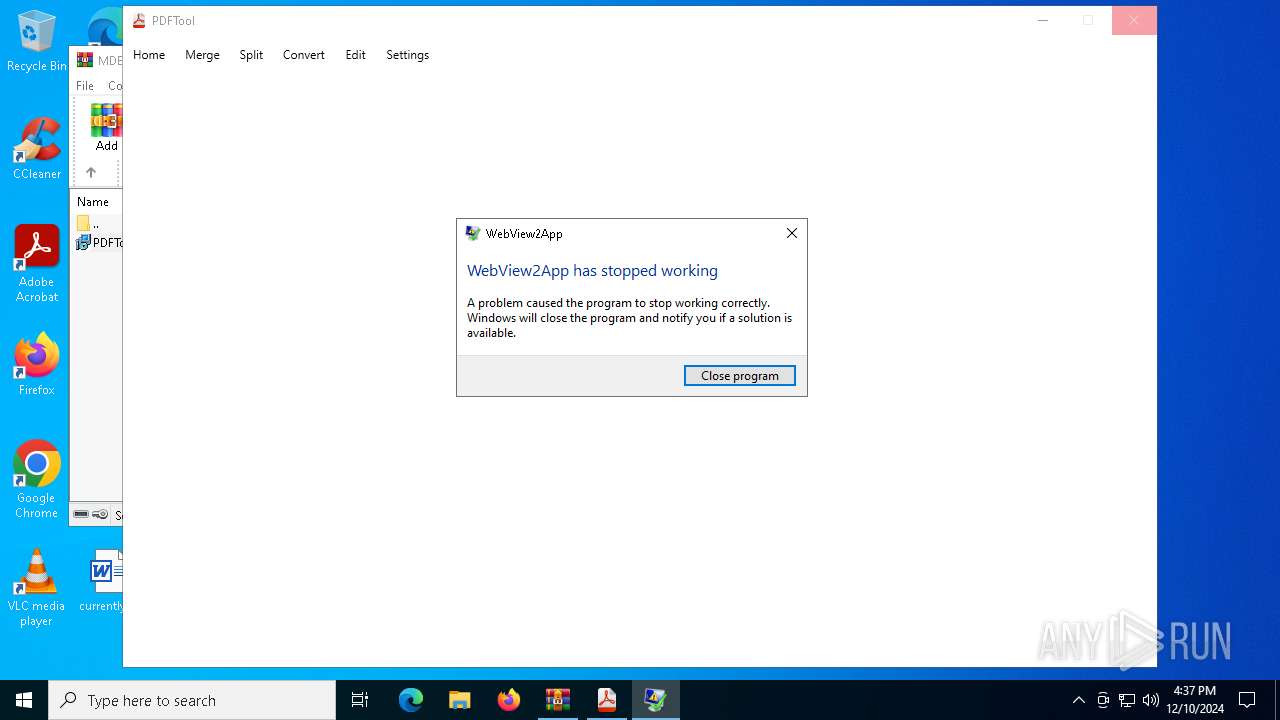
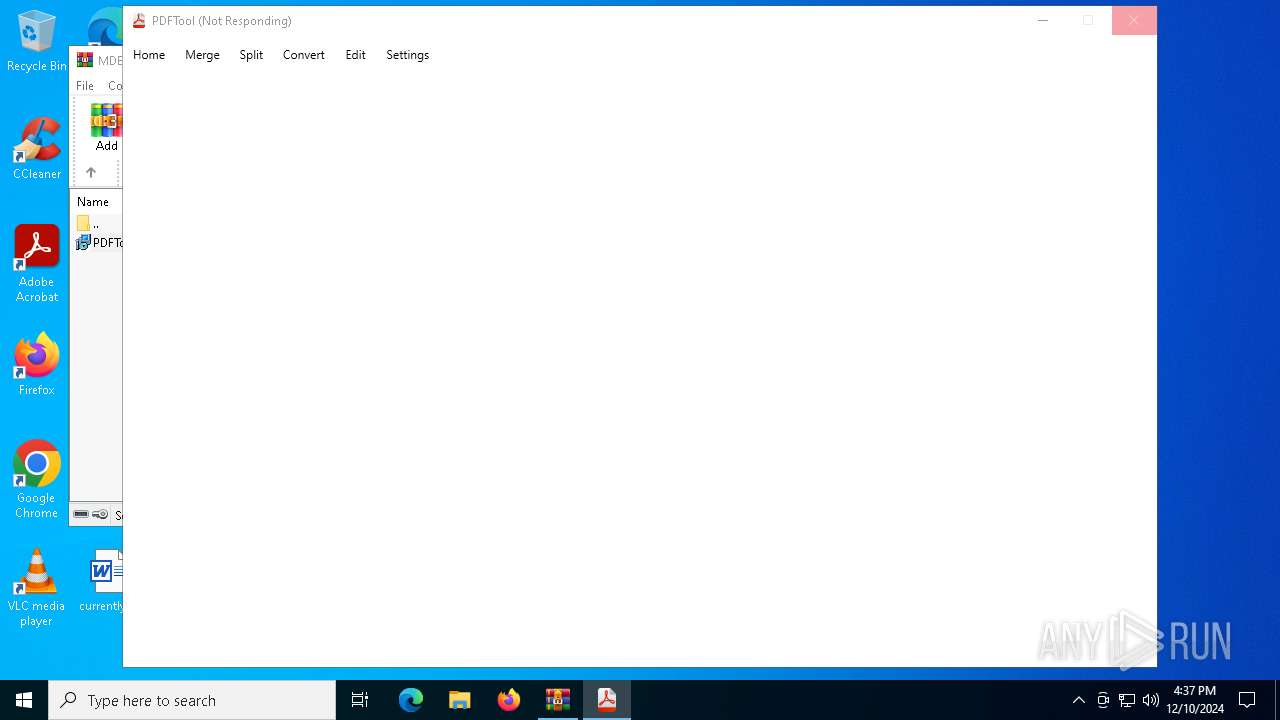
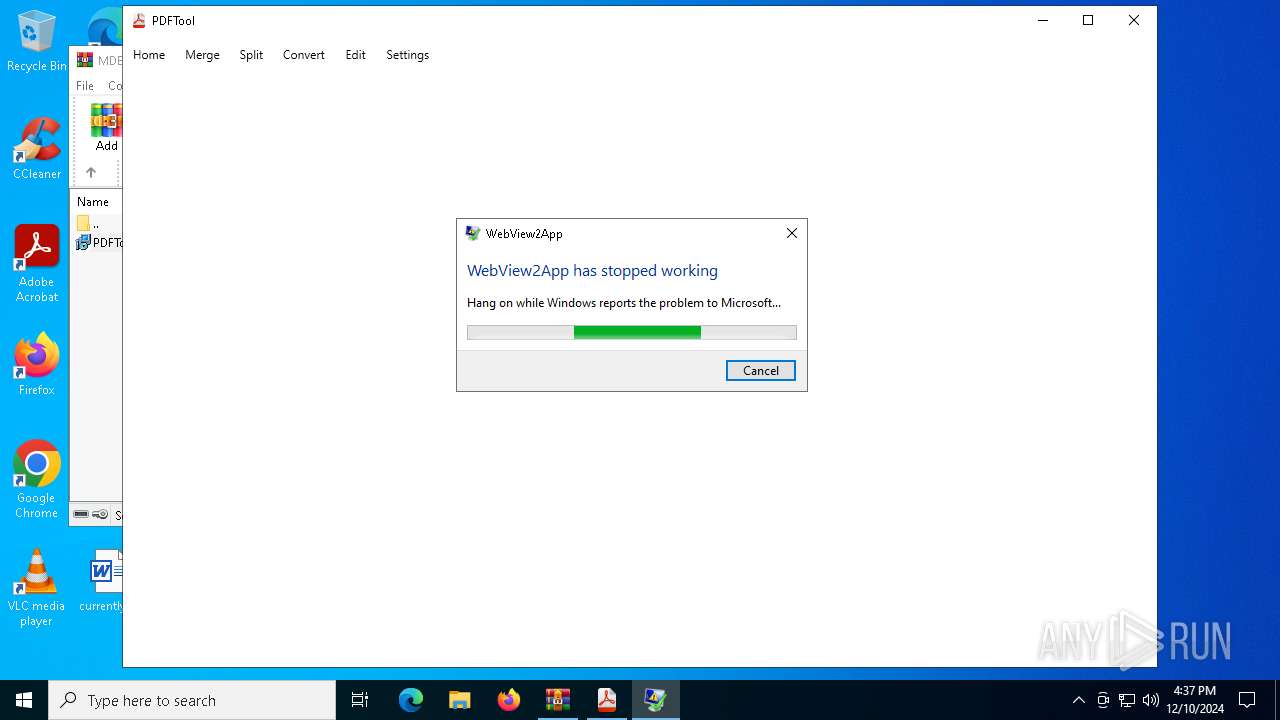
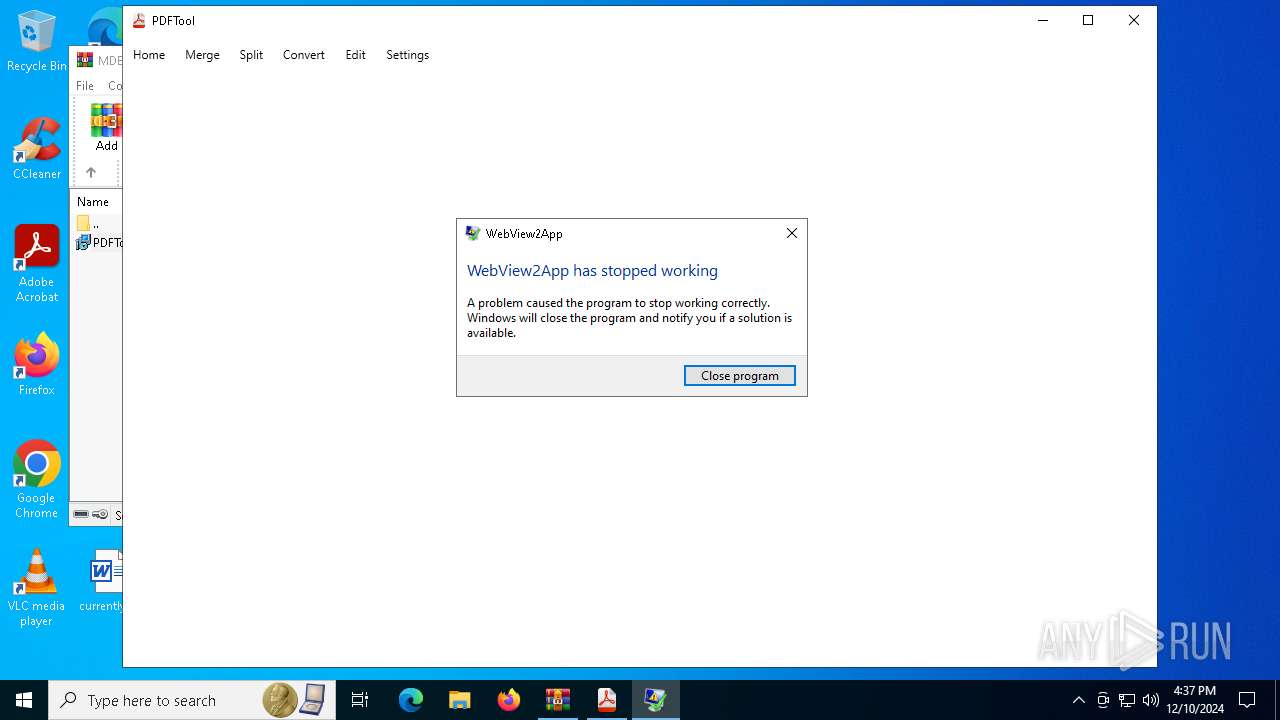
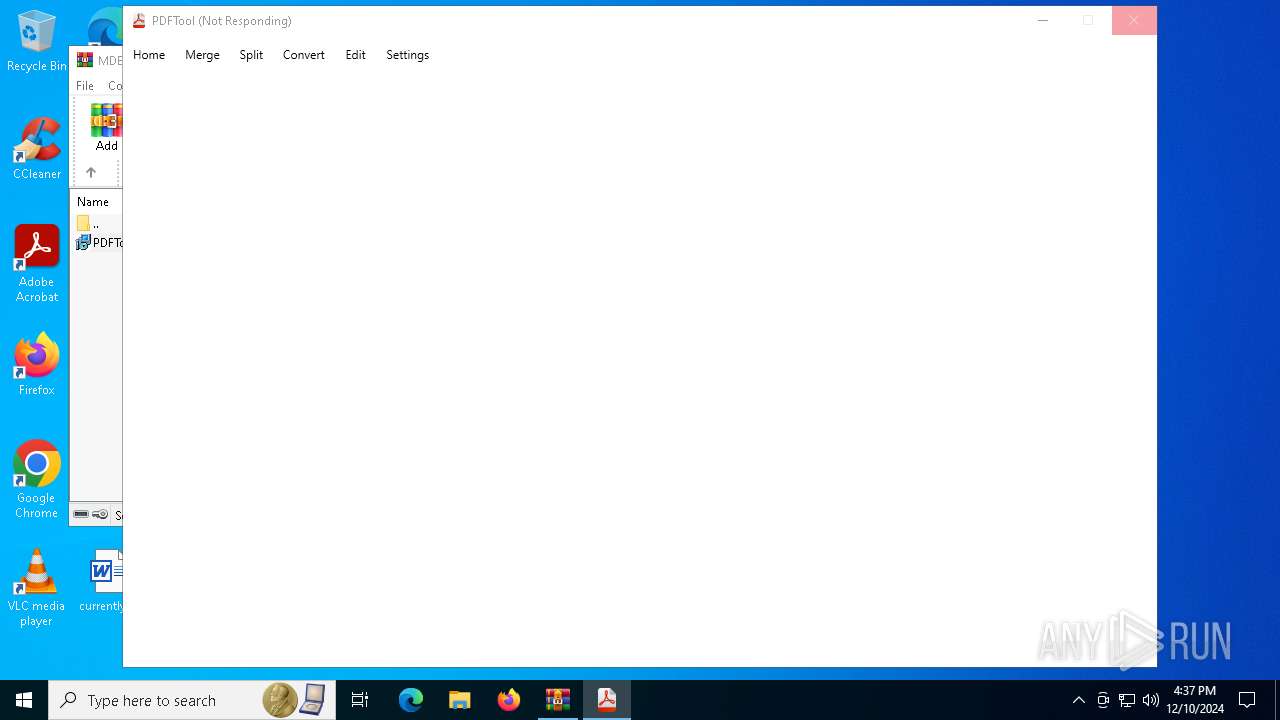
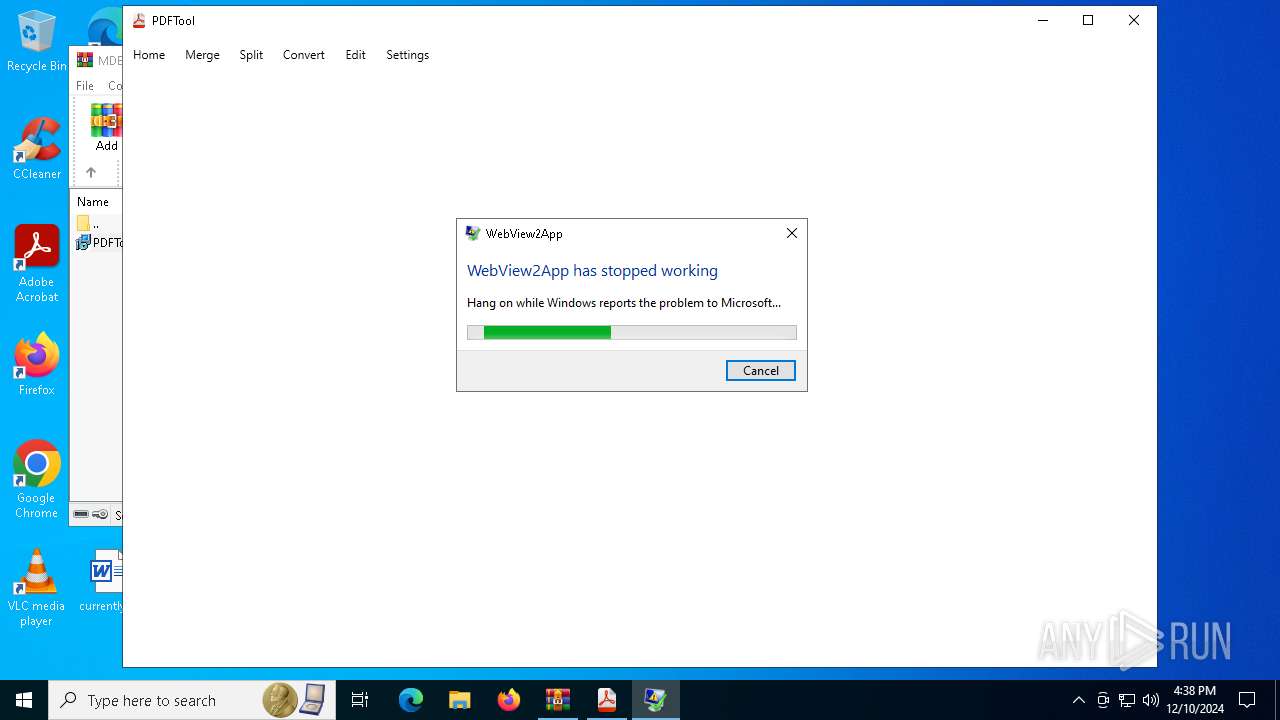
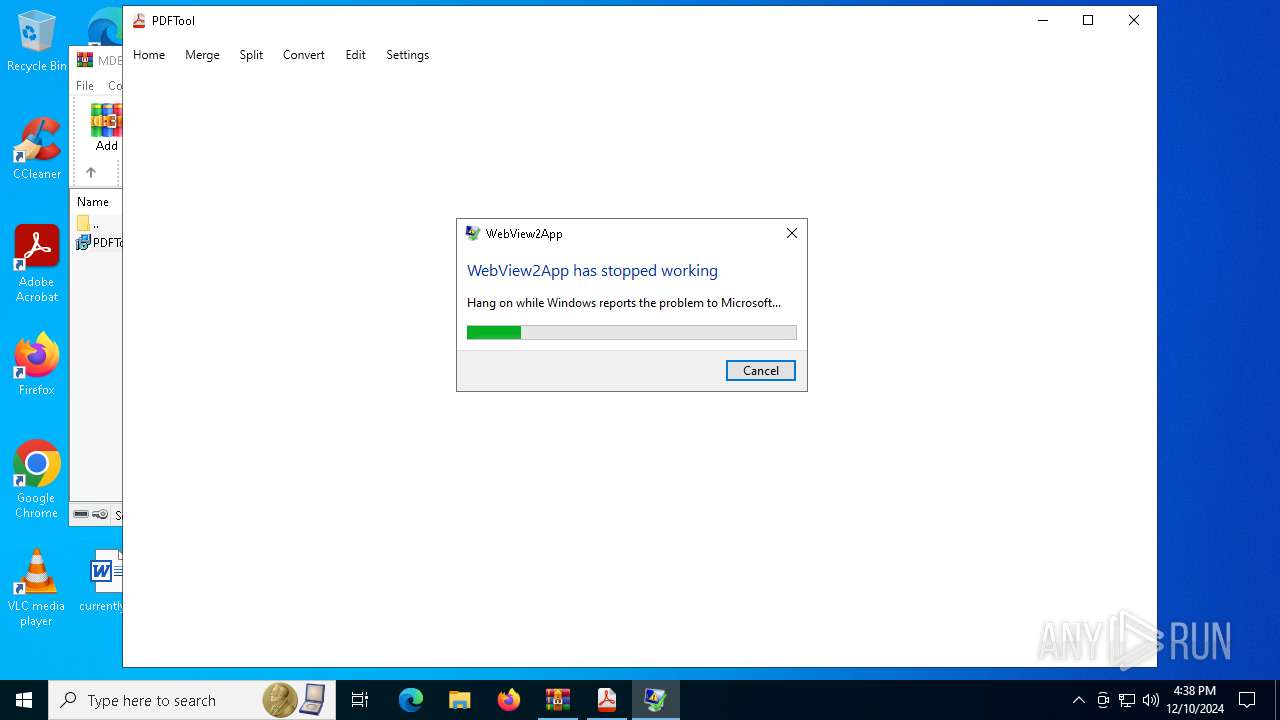
Executes application which crashes
- PDFTool.exe (PID: 4504)
- PDFTool.exe (PID: 6088)
- PDFTool.exe (PID: 1296)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6284)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6344)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6812)
Reads the software policy settings
- msiexec.exe (PID: 6284)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6344)
- WerFault.exe (PID: 6352)
- msiexec.exe (PID: 6168)
Creates files or folders in the user directory
- msiexec.exe (PID: 6284)
Checks proxy server information
- msiexec.exe (PID: 6284)
- msiexec.exe (PID: 6168)
- WerFault.exe (PID: 4320)
- WerFault.exe (PID: 2928)
The process uses the downloaded file
- WinRAR.exe (PID: 6812)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6284)
- msiexec.exe (PID: 5920)
- msiexec.exe (PID: 6168)
- msiexec.exe (PID: 5256)
Reads the computer name
- msiexec.exe (PID: 5920)
- msiexec.exe (PID: 6484)
- PDFTool.exe (PID: 6088)
- PDFTool.exe (PID: 1296)
Checks supported languages
- msiexec.exe (PID: 6484)
- msiexec.exe (PID: 5920)
- msiexec.exe (PID: 6168)
- PDFTool.exe (PID: 4504)
- PDFTool.exe (PID: 6088)
- PDFTool.exe (PID: 1296)
The sample compiled with english language support
- msiexec.exe (PID: 6284)
- msiexec.exe (PID: 5920)
- msiexec.exe (PID: 6168)
- msiexec.exe (PID: 5256)
Manages system restore points
- SrTasks.exe (PID: 6012)
Disables trace logs
- powershell.exe (PID: 3928)
Reads Environment values
- msiexec.exe (PID: 6168)
- msiexec.exe (PID: 6484)
- msiexec.exe (PID: 4952)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6168)
- PDFTool.exe (PID: 4504)
- PDFTool.exe (PID: 6088)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6344)
Process checks computer location settings
- msiexec.exe (PID: 6484)
Sends debugging messages
- PDFTool.exe (PID: 4504)
- PDFTool.exe (PID: 6088)
- PDFTool.exe (PID: 1296)
Manual execution by a user
- PDFTool.exe (PID: 6088)
- PDFTool.exe (PID: 1296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:10 16:35:38 |
| ZipCRC: | 0x4d2d32a0 |
| ZipCompressedSize: | 2897244 |
| ZipUncompressedSize: | 5265920 |
| ZipFileName: | PDFTool-v3.1.1226.0.msi |
Total processes
150
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe" | C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WebView2App Version: 3.1.1226.0 Modules
| |||||||||||||||
| 1740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | C:\Windows\syswow64\MsiExec.exe -Embedding BE4FC888F7FE178E30ED8A1505025E1F C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2928 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1296 -s 1732 | C:\Windows\SysWOW64\WerFault.exe | PDFTool.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3928 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssD930.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msiD257.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scrD258.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scrD259.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4504 -s 1768 | C:\Windows\SysWOW64\WerFault.exe | PDFTool.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4504 | "C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe" /register | C:\Users\admin\AppData\Local\PDFTool\PDFTool.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WebView2App Exit code: 3762504530 Version: 3.1.1226.0 Modules
| |||||||||||||||
| 4952 | C:\Windows\syswow64\MsiExec.exe -Embedding BC05E77ADDA2021E23EE6ADC2101BAB8 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXb6812.46176\PDFTool-v3.1.1226.0.msi" | C:\Windows\System32\msiexec.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 497
Read events
42 143
Write events
325
Delete events
29
Modification events
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_70f80ce7b1c8c7b5018616b94ee39622c09a4431.zip | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
Executable files
45
Suspicious files
61
Text files
24
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6812.40174\PDFTool-v3.1.1226.0.msi | — | |
MD5:— | SHA256:— | |||
| 5920 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 5920 | msiexec.exe | C:\Windows\Installer\13cf0b.msi | — | |
MD5:— | SHA256:— | |||
| 6168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msiD257.txt | — | |
MD5:— | SHA256:— | |||
| 6168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scrD258.ps1 | — | |
MD5:— | SHA256:— | |||
| 6168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scrD259.txt | — | |
MD5:— | SHA256:— | |||
| 6168 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pssD930.ps1 | — | |
MD5:— | SHA256:— | |||
| 6284 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI88DB.tmp | executable | |
MD5:D0C9613582605F3793FDAD7279DE428B | SHA256:8BD84F1156EBDFA44AFAAC8A4579BA56A8C7513E3D51E00822167EA144923726 | |||
| 6284 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI897A.tmp | executable | |
MD5:D0C9613582605F3793FDAD7279DE428B | SHA256:8BD84F1156EBDFA44AFAAC8A4579BA56A8C7513E3D51E00822167EA144923726 | |||
| 6284 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:6434BC38E600C59D17DA45FA5C03536E | SHA256:9216A09756302848CC1119804D21F4F8AE57283EA198EBD058E9FF4D24E140D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
55
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6580 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6284 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEXkmCboMU2WPdtTtg%3D%3D | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3988 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6168 | msiexec.exe | GET | 200 | 13.32.29.103:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
6284 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
3988 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6072 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6072 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.65:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
PDFTool.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|