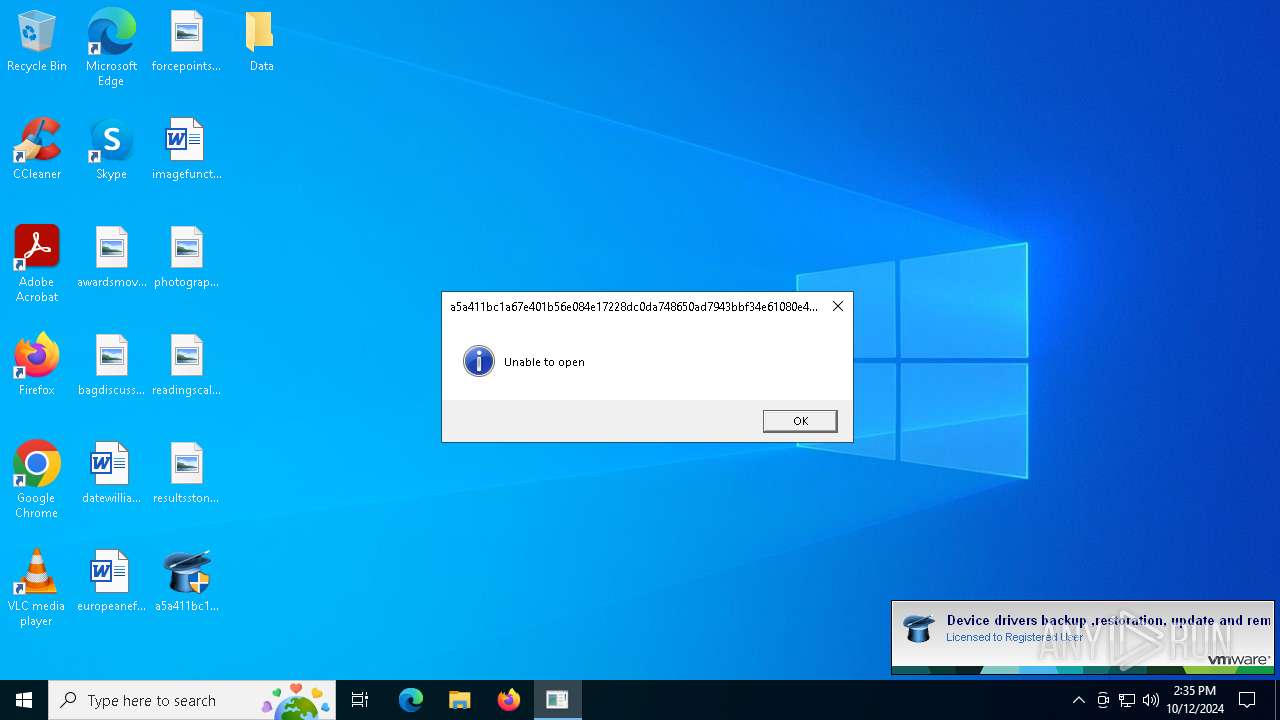
| File name: | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N |
| Full analysis: | https://app.any.run/tasks/5b539a16-654f-45ff-a850-bc2e265ec356 |
| Verdict: | Malicious activity |
| Analysis date: | October 12, 2024, 14:35:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B93E032BA59E9849CECE925043406890 |
| SHA1: | 232CA6902DCD690DE02B76787D05188CB02D4060 |
| SHA256: | A5A411BC1A67E401B56E084E17228DC0DA748650AD7943BBF34E61080E43C974 |
| SSDEEP: | 98304:9NlQ+7NuKGfxKzDR8mhww6ylfJ0YT2XeN6JbEO0OfqaUYG2TLop8wyaGFTepnCeh:OERyK |
MALICIOUS
Connects to the CnC server
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
FLOXIF has been detected (SURICATA)
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
SUSPICIOUS
Process drops legitimate windows executable
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Executable content was dropped or overwritten
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Reads security settings of Internet Explorer
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Contacting a server suspected of hosting an CnC
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
INFO
Creates files in the program directory
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Checks supported languages
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Sends debugging messages
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Reads the machine GUID from the registry
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Checks proxy server information
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Reads the computer name
- a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe (PID: 6728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:01:19 00:20:15+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 110080 |
| InitializedDataSize: | 201216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1448 |
| OSVersion: | 4 |
| ImageVersion: | 5.6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.60.0.0 |
| ProductVersionNumber: | 5.60.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Driver Magician |
| CompanyName: | GoldSolution Software, Inc. |
| FileDescription: | Device drivers backup ,restoration, update and removal tool |
| LegalCopyright: | GoldSolution Software, Inc.2003-2022 |
| LegalTrademarks: | Driver Magician |
| ProductName: | Driver Magician |
| FileVersion: | 5.6 |
| ProductVersion: | 5.6 |
| InternalName: | Driver Magician |
| OriginalFileName: | Driver Magician.exe |
| ThinAppBuildDateTime: | 20220119 170701 |
| ThinAppLicense: | Registered User |
| ThinAppVersion: | 2111.0.0-18970417 |
Total processes
125
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5592 | "C:\Users\admin\Desktop\a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe" | C:\Users\admin\Desktop\a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | — | explorer.exe | |||||||||||
User: admin Company: GoldSolution Software, Inc. Integrity Level: MEDIUM Description: Device drivers backup ,restoration, update and removal tool Exit code: 3221226540 Version: 5.60 Modules
| |||||||||||||||
| 6728 | "C:\Users\admin\Desktop\a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe" | C:\Users\admin\Desktop\a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | explorer.exe | ||||||||||||
User: admin Company: GoldSolution Software, Inc. Integrity Level: HIGH Description: Device drivers backup ,restoration, update and removal tool Exit code: 4294967295 Version: 5.60 Modules
| |||||||||||||||
Total events
693
Read events
693
Write events
0
Delete events
0
Modification events
Executable files
5
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\DummyTLS\dummyTLS.dll | executable | |
MD5:FBAD73BE2BB7279AD9C9D574D53F3DA6 | SHA256:D77791DDD644CBE84C35382B759FAF7B992C187EA435D52B02C3B21D7684A251 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\Registry.rw.tvr.transact | binary | |
MD5:554505001833BAF2A7E114CFAB0B6E22 | SHA256:F3442063623DD848E59E56AFCC0C1C60A635A85E696084E68DD4C044D5A5AF39 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\DummyTLS\dummyTLS64.dll | executable | |
MD5:19D36F1DB2A453F5D6835193BAB886EB | SHA256:1543C630D3DE78C6F110BA26FE4DB79655081468EBCFF48B2503730E76B3B4B1 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\Registry.tlog.cache | binary | |
MD5:0E11DEF84D7DFD756083095AC9BD1276 | SHA256:923B5493BF3CED557E7F014A8E6A287C809A3EAF2980C5920607A4B7E6FB18B6 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\Registry.rw.tvr | binary | |
MD5:554505001833BAF2A7E114CFAB0B6E22 | SHA256:F3442063623DD848E59E56AFCC0C1C60A635A85E696084E68DD4C044D5A5AF39 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\DummyTLS\-5616.6728.tmp | executable | |
MD5:FBAD73BE2BB7279AD9C9D574D53F3DA6 | SHA256:D77791DDD644CBE84C35382B759FAF7B992C187EA435D52B02C3B21D7684A251 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\Registry.rw.tvr.lck | binary | |
MD5:0577EA4B74DFD944026ABE8D8E4329E9 | SHA256:A30FDBE61ACA5272E6A75D73CFD065874087BF15D06027D8A547915B9FAC9EA6 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Program Files\Common Files\System\symsrv.dll | executable | |
MD5:7574CF2C64F35161AB1292E2F532AABF | SHA256:DE055A89DE246E629A8694BDE18AF2B1605E4B9B493C7E4AEF669DD67ACF5085 | |||
| 6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | C:\Users\admin\Desktop\Data\Registry.rw.tvr.lck.DESKTOP-JGLLJLD.ffffffff.15f0 | binary | |
MD5:0577EA4B74DFD944026ABE8D8E4329E9 | SHA256:A30FDBE61ACA5272E6A75D73CFD065874087BF15D06027D8A547915B9FAC9EA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6908 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6908 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6728 | a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | GET | — | 45.33.23.183:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6908 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6908 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6908 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | <?dml?>#1 p=6728/1A48h t=5616/15F0h: <link cmd=".reload /f boot_loader.exe=0x66200000">Reload</link> <b>boot_loader.exe</b> 0x66200000
|
a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | <?dml?>#2 p=6728/1A48h t=5616/15F0h: Loading packaged nt0_dll.dll...
|
a5a411bc1a67e401b56e084e17228dc0da748650ad7943bbf34e61080e43c974N.exe | <?dml?>#3 p=6728/1A48h t=5616/15F0h: <link cmd=".reload /f nt0_dll.dll=0x7FC80000">Reload</link> <b>nt0_dll.dll</b> 0x7FC80000 packaged
|