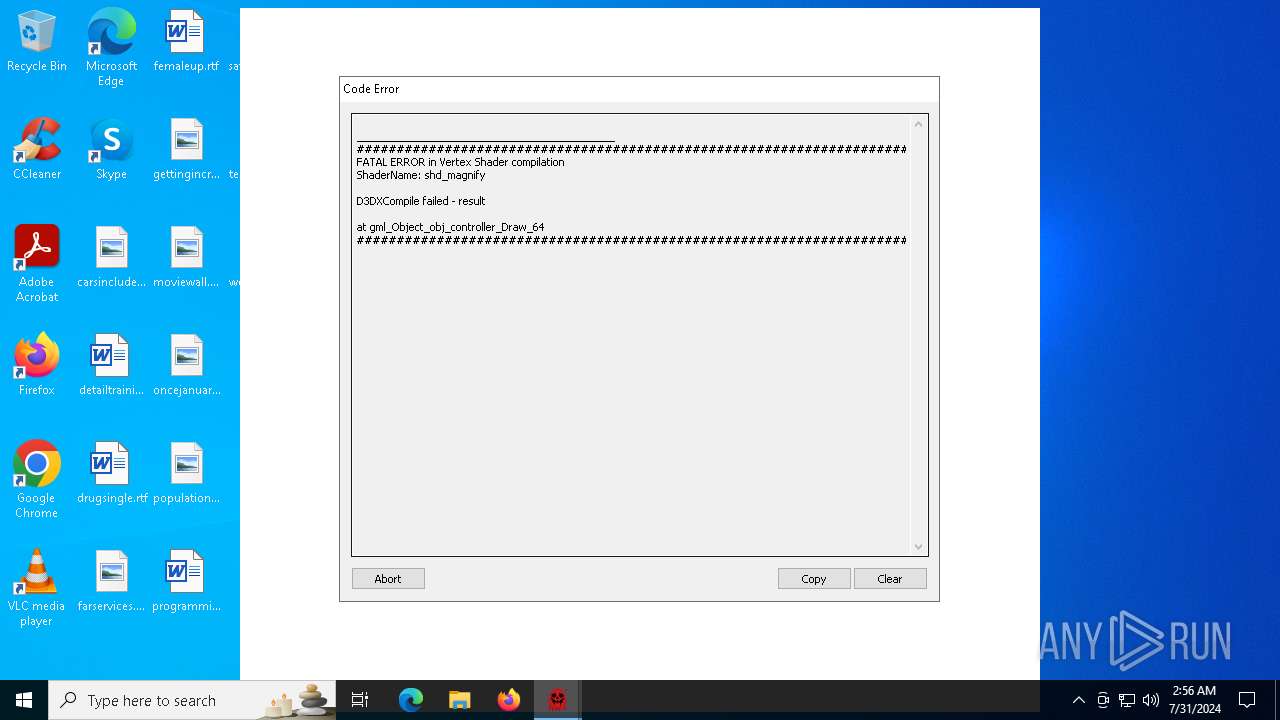
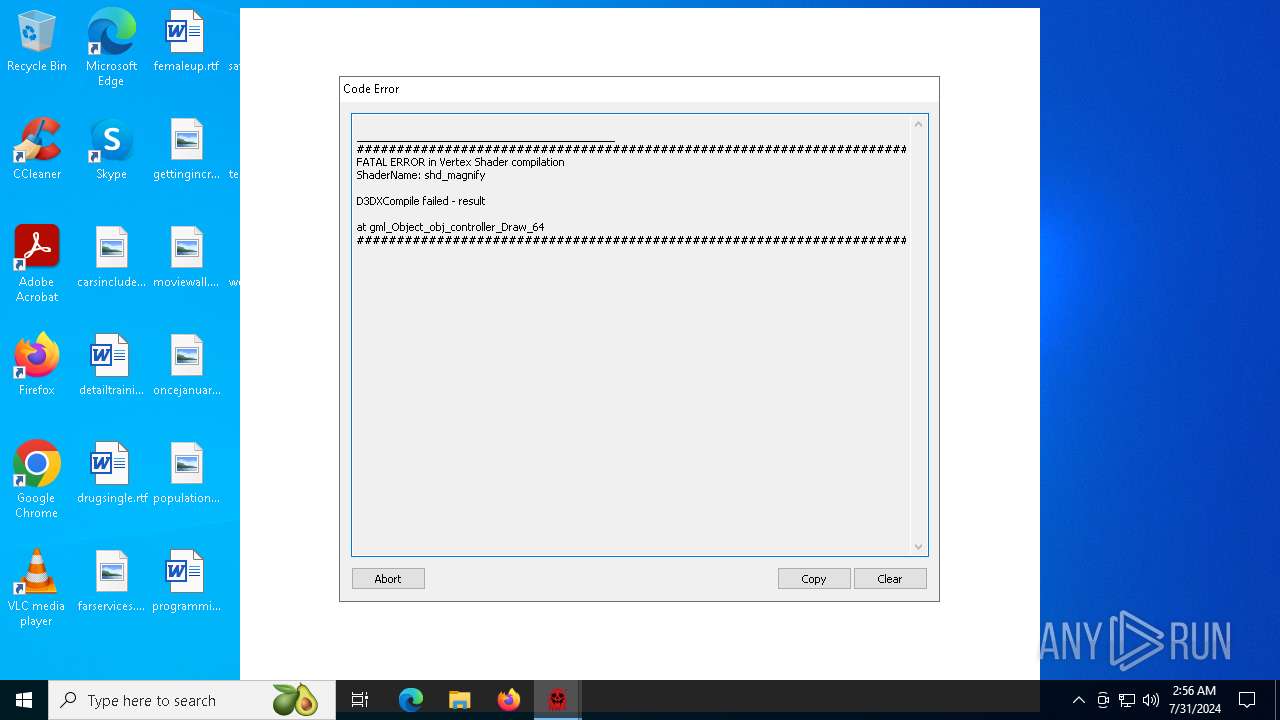
| File name: | PacMan.exe |
| Full analysis: | https://app.any.run/tasks/0b2c8b6e-1137-4596-8cf7-88c0e2b02872 |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2024, 02:56:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CFF7FAB474E2CF33B332210AF5608FD7 |
| SHA1: | 79A7FCF6B799F70E2389CE04A669D55B96F022F9 |
| SHA256: | A59BB85B74832A7AAEE6C4CFD2383F03A64A1BA06A442CC5A51DCA559BCDAE75 |
| SSDEEP: | 98304:uu46pKI0HBaS4bOItZ0Aa0Cwfxb4v37APpRQViJ8Q/jyB3cHHpqI0azJ7BSF9EP1:12OGLs |
MALICIOUS
Application was injected by another process
- csrss.exe (PID: 604)
Runs injected code in another process
- PacMan CRT.exe (PID: 7084)
Drops the executable file immediately after the start
- PacMan.exe (PID: 5696)
SUSPICIOUS
Process drops legitimate windows executable
- PacMan.exe (PID: 5696)
Executable content was dropped or overwritten
- PacMan.exe (PID: 5696)
INFO
Checks supported languages
- PacMan.exe (PID: 5696)
- PacMan CRT.exe (PID: 7084)
Reads the software policy settings
- slui.exe (PID: 6328)
Checks proxy server information
- slui.exe (PID: 6328)
Reads the computer name
- PacMan CRT.exe (PID: 7084)
Create files in a temporary directory
- PacMan.exe (PID: 5696)
Creates files or folders in the user directory
- PacMan CRT.exe (PID: 7084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:10:31 03:28:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 27136 |
| InitializedDataSize: | 4444160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x69d0 |
| OSVersion: | 6.3 |
| ImageVersion: | 6.3 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | |
| FileDescription: | |
| FileVersion: | 1.0.0.4 |
| InternalName: | Wextract |
| LegalCopyright: | |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | |
| ProductVersion: | 1.0.0.4 |
Total processes
147
Monitored processes
4
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5696 | "C:\Users\admin\AppData\Local\Temp\PacMan.exe" | C:\Users\admin\AppData\Local\Temp\PacMan.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 6328 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PacMan CRT.exe" | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PacMan CRT.exe | — | PacMan.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
Total events
1 106
Read events
1 101
Write events
5
Delete events
0
Modification events
| (PID) Process: | (7084) PacMan CRT.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: C0053E88E84EEF118001444553540000 | |||
| (PID) Process: | (7084) PacMan CRT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Version |
Value: 0A050000 | |||
| (PID) Process: | (7084) PacMan CRT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: PACMAN CRT.EXE | |||
| (PID) Process: | (7084) PacMan CRT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Id |
Value: PACMAN CRT.EXE55F7C3C10032C200 | |||
| (PID) Process: | (7084) PacMan CRT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | MostRecentStart |
Value: 0B71964AF5E2DA01 | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5696 | PacMan.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PacMan CRT.exe | executable | |
MD5:CBF5F66F38D503F4F38FF6A1601F3F4D | SHA256:844A6E4BD55FB7C88AB476734A2180E70D2298E20C0EA4B23D94F29F75FCACA2 | |||
| 7084 | PacMan CRT.exe | C:\Users\admin\AppData\Local\PacMan_CRT\noise.png | image | |
MD5:5873FB91D292F3F600B21298CAE1858D | SHA256:94242FD9E681654C34251AC793F6D1C7C54452A89249F05D039578A6D2DD8B00 | |||
| 7084 | PacMan CRT.exe | C:\Users\admin\AppData\Local\PacMan_CRT\lines.png | image | |
MD5:21C565153059BCF655E3F73966F53905 | SHA256:A8998F7DA0801BF9A17DD8372704C7EDDDCD84A4DA8A436E9EFD02F093CEBB8F | |||
| 5696 | PacMan.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\D3DX9_43.dll | executable | |
MD5:86E39E9161C3D930D93822F1563C280D | SHA256:0B28546BE22C71834501F7D7185EDE5D79742457331C7EE09EFC14490DD64F5F | |||
| 5696 | PacMan.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\data.win | binary | |
MD5:3267BFD83D96C89FF1989C582787F1E4 | SHA256:53AEFF59D147AEFD3B43BB07EE5711DE2D5224302C7BFD10B83A99E9CD73DB31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
62
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 304 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6776 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1028 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.86.251.27:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1996 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4560 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
528 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |