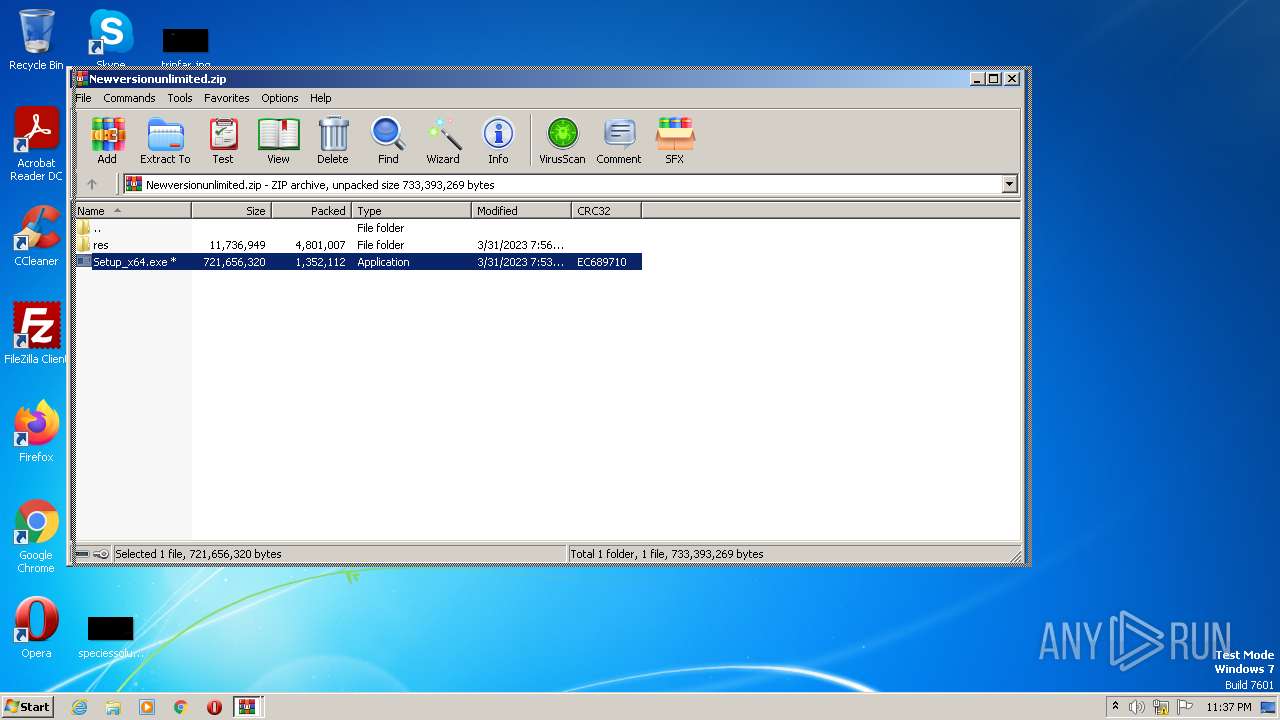
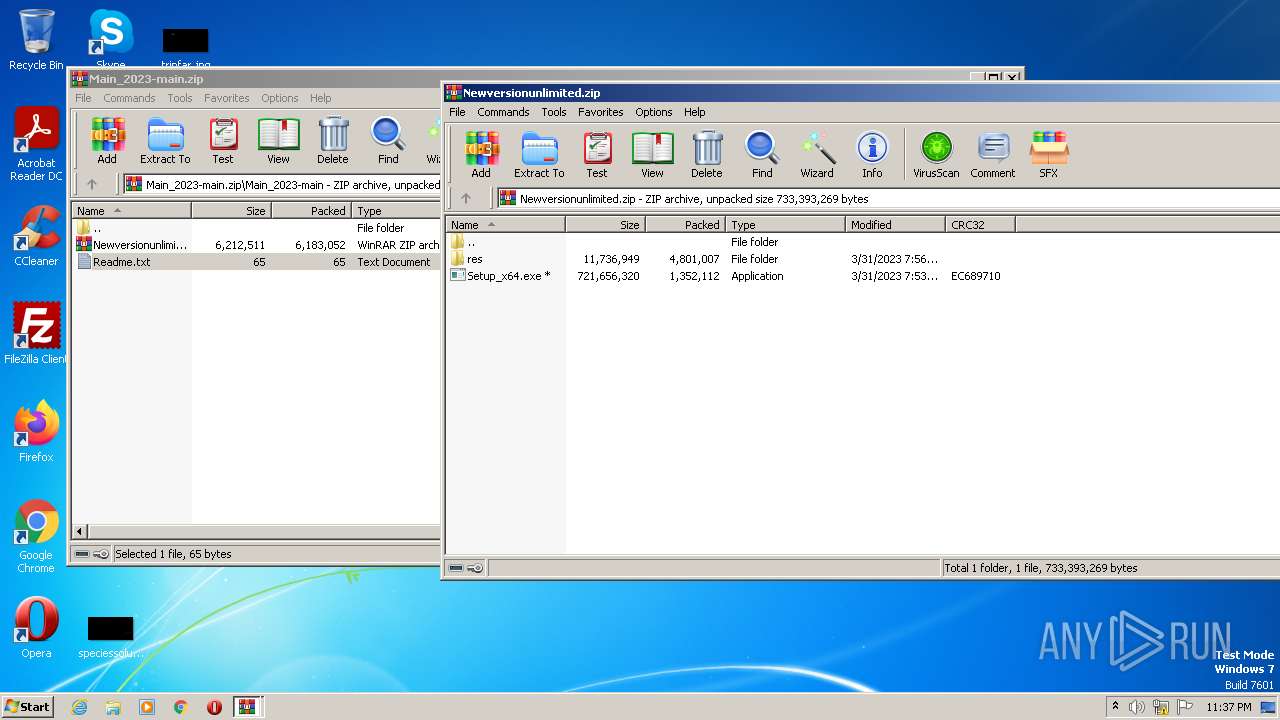
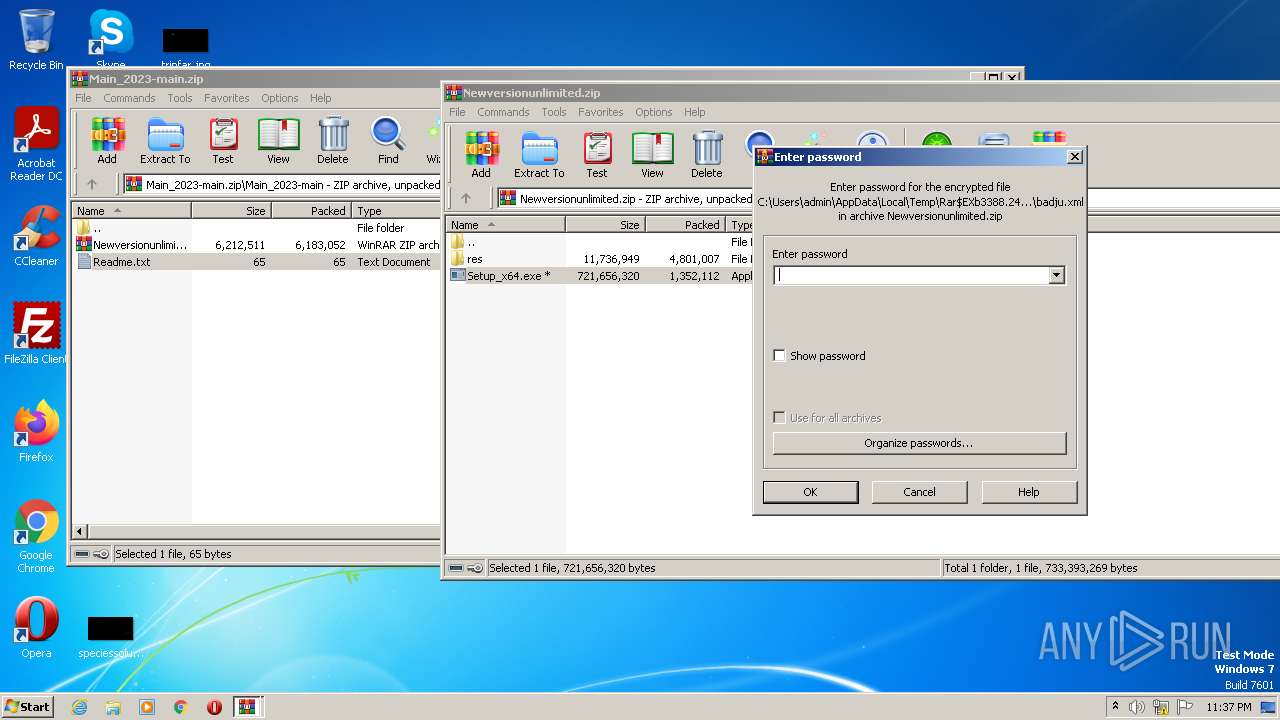
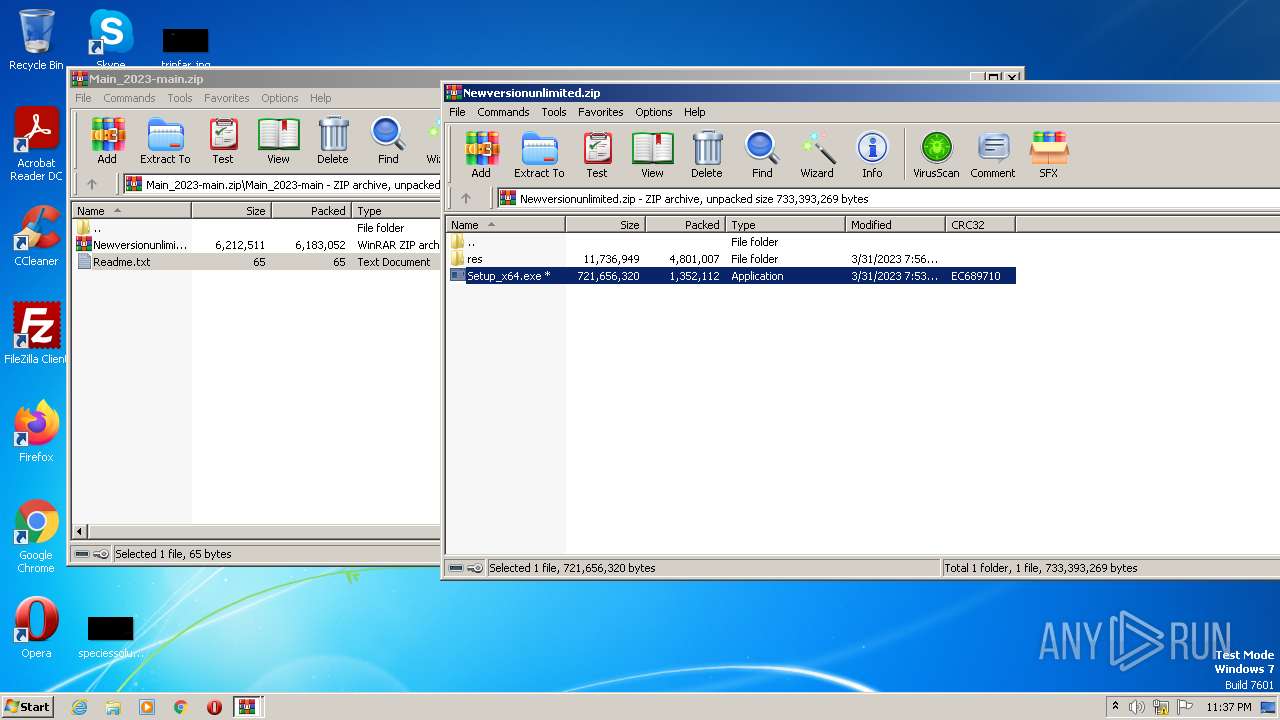
| File name: | Main_2023-main.zip |
| Full analysis: | https://app.any.run/tasks/377c80fb-153d-4012-83f4-3d079e448475 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 22:37:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | B9CA33B6D5B444414794049ECAE60670 |
| SHA1: | EE82F9A2D962D74B846E74F508E0745316FD3AE0 |
| SHA256: | A58F9796AC977F489C9394DC38E967F7EAABFC98DF3A29569F65E2C8EF85A219 |
| SSDEEP: | 98304:8/geo/CAoNuGIzMJiq1I9UYQOyirGNKjMaOS5znQ8UJ:8/geNmGgu1IHVrGNyMXWnS |
MALICIOUS
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3512)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2640)
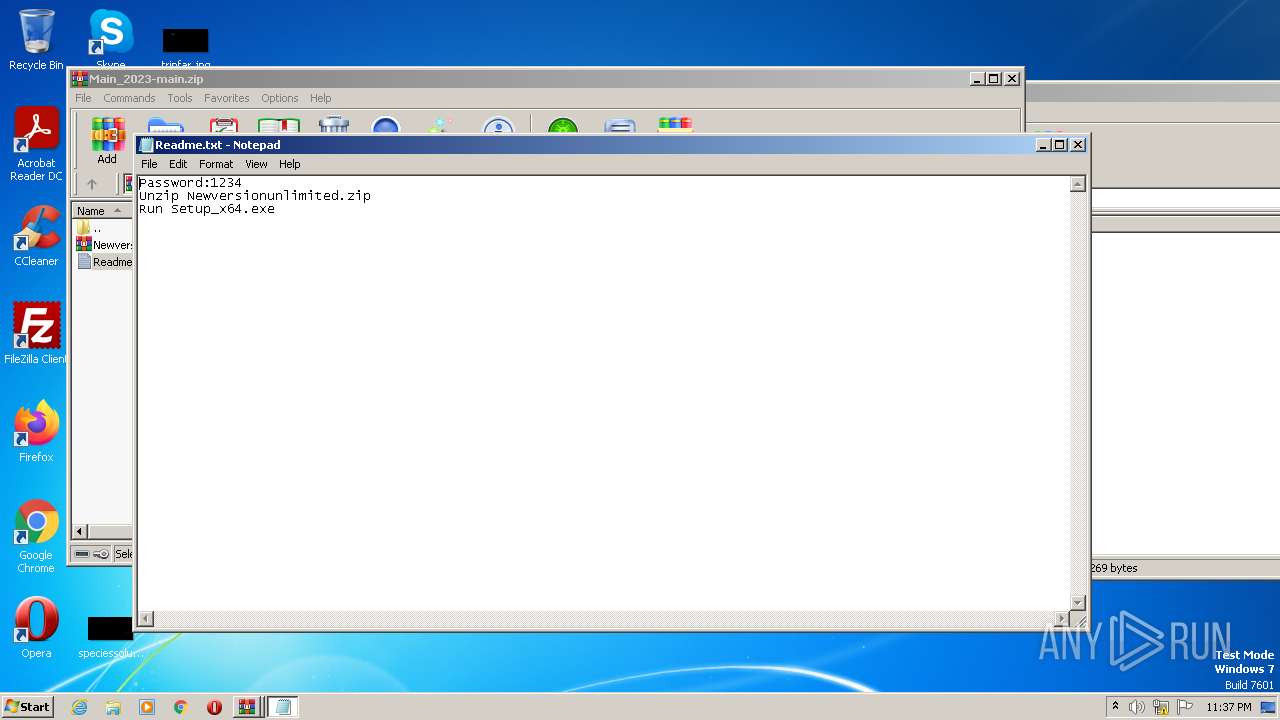
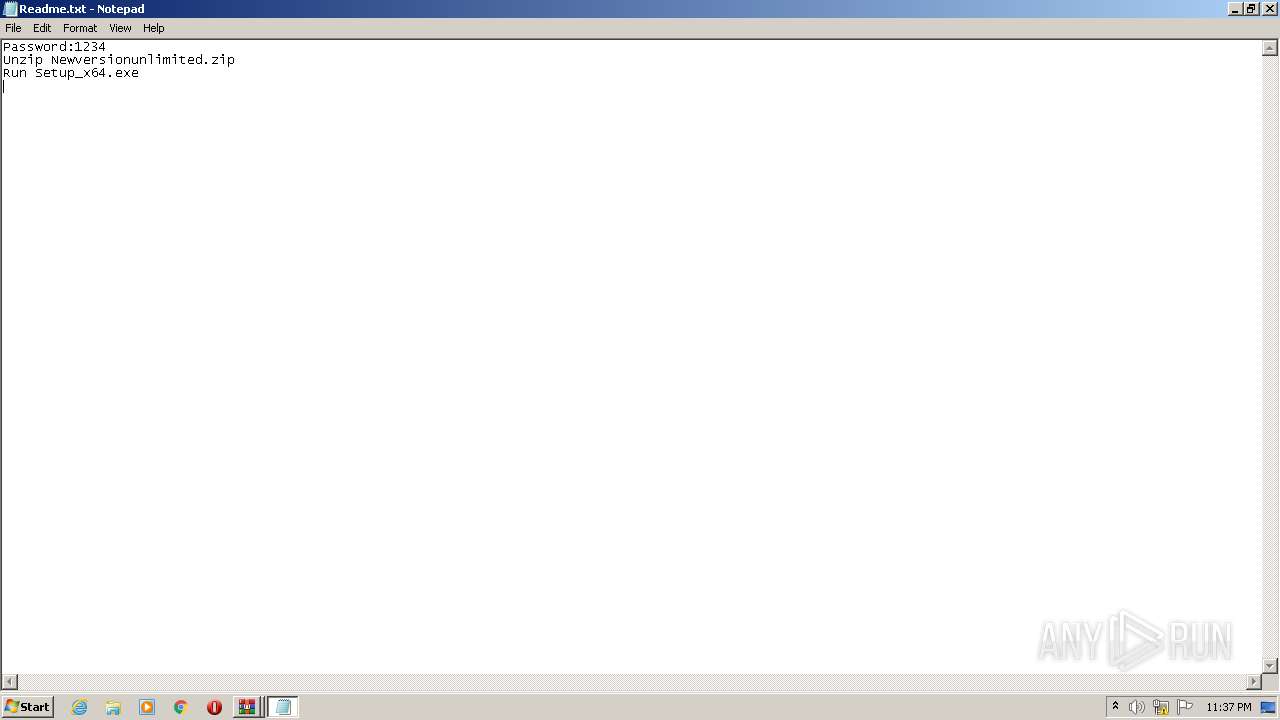
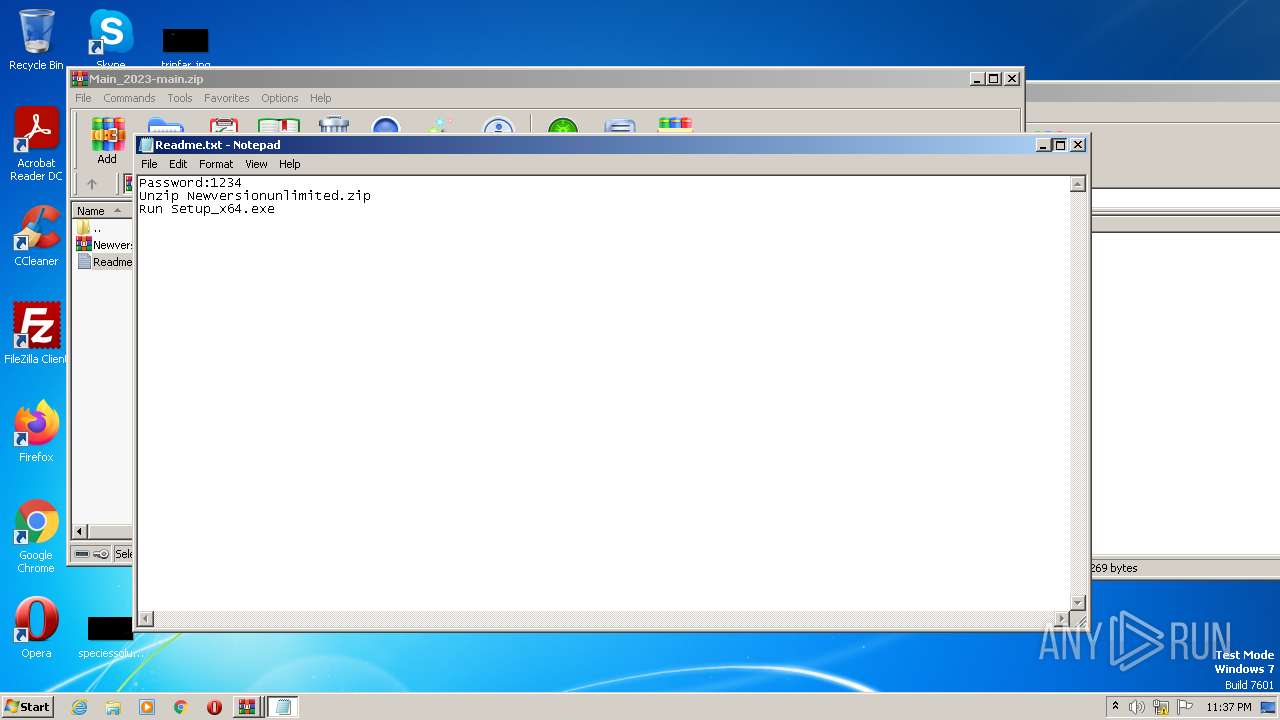
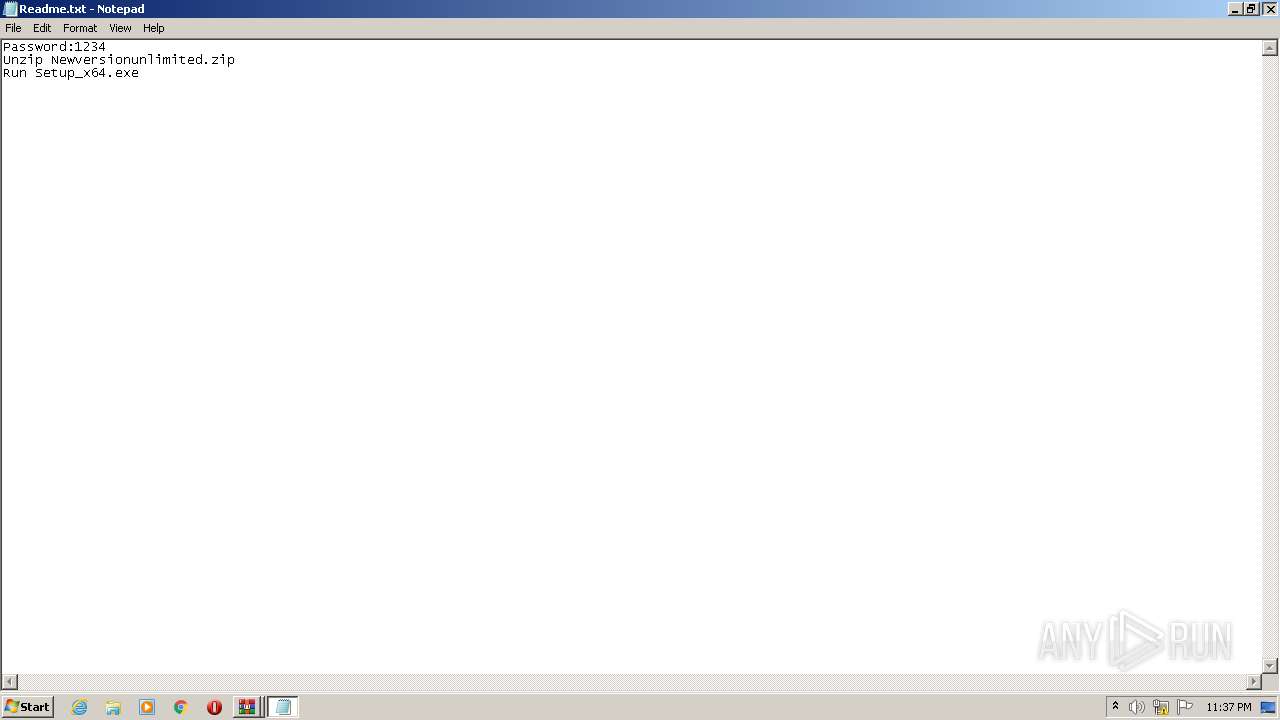
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2640)
Reads browser cookies
- RegSvcs.exe (PID: 3512)
Searches for installed software
- RegSvcs.exe (PID: 3512)
Connects to the server without a host name
- RegSvcs.exe (PID: 3512)
INFO
Checks supported languages
- Setup_x64.exe (PID: 2128)
- RegSvcs.exe (PID: 3512)
Reads the computer name
- RegSvcs.exe (PID: 3512)
The process checks LSA protection
- RegSvcs.exe (PID: 3512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Main_2023-main/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:03:31 12:28:06 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
45
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
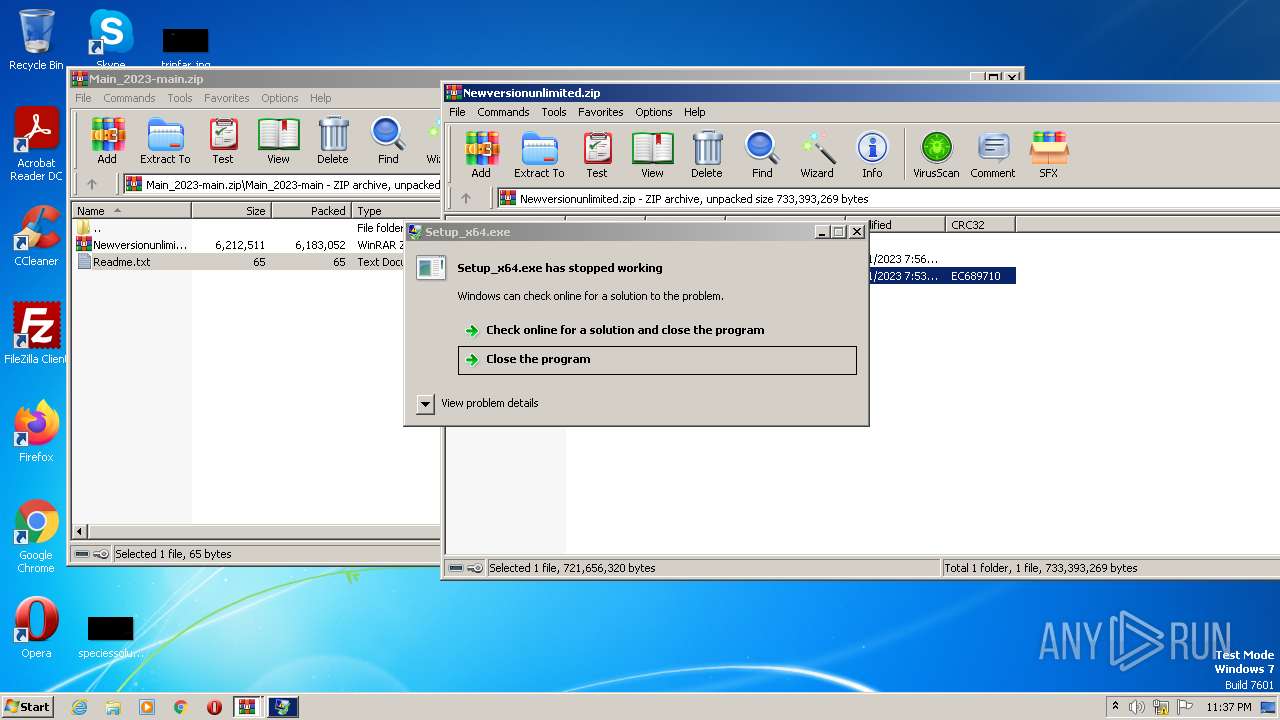
| 2128 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\Setup_x64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\Setup_x64.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 2640 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Main_2023-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2816 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\Setup_x64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\Setup_x64.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
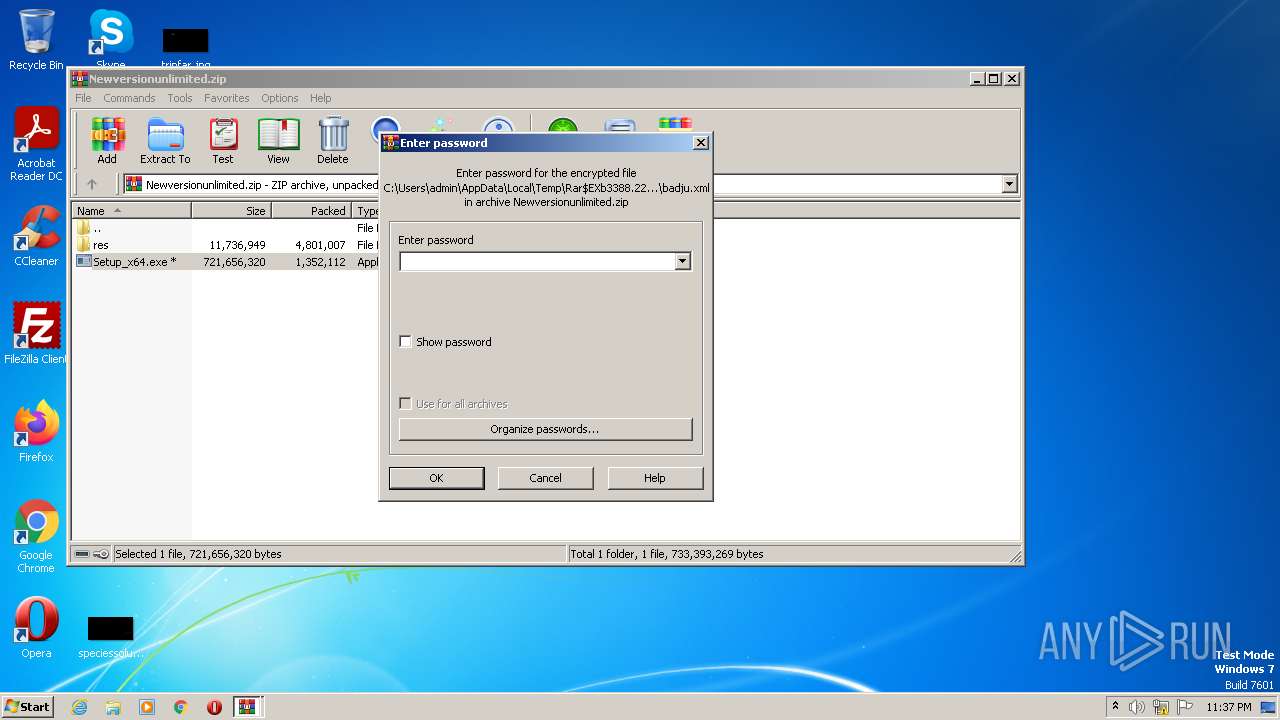
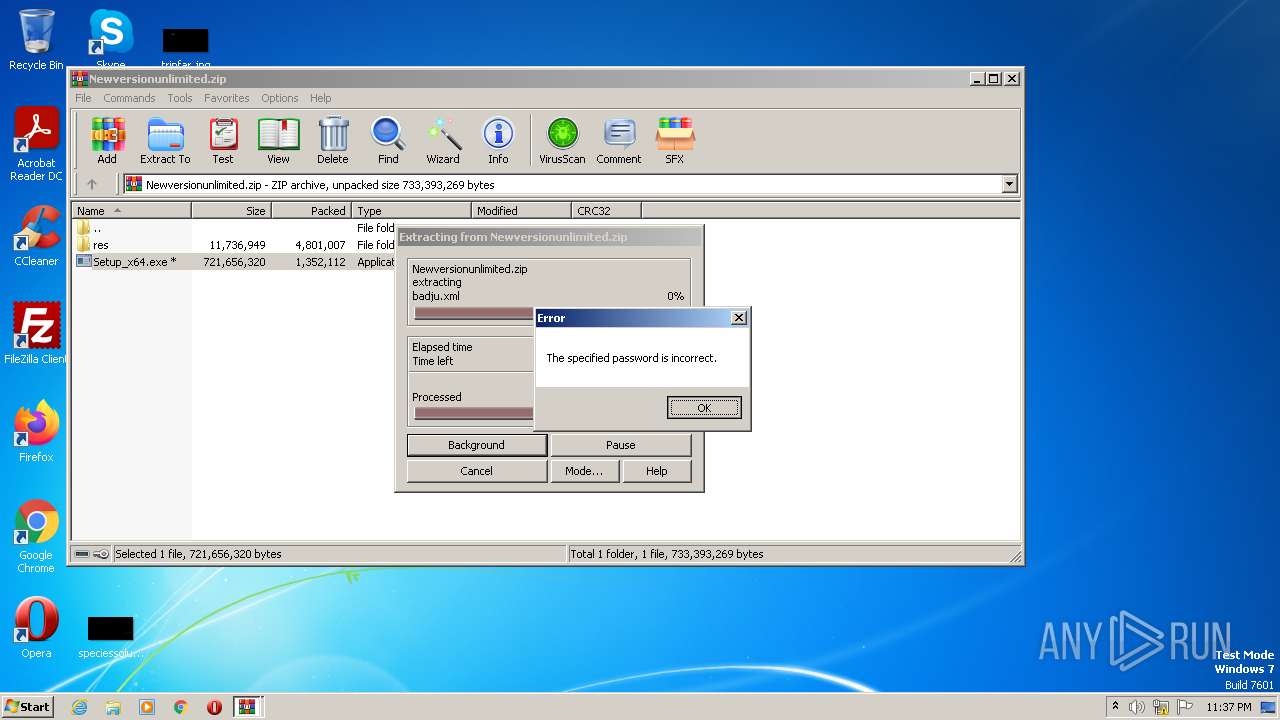
| 3388 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa2640.22834\Newversionunlimited.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3512 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Setup_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 4080 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2640.23940\Readme.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 930
Read events
4 860
Write events
70
Delete events
0
Modification events
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
2
Text files
456
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2640.23940\Readme.txt | text | |
MD5:— | SHA256:— | |||
| 2640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2640.22834\Newversionunlimited.zip | compressed | |
MD5:— | SHA256:— | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\couplesGoura.xml | xml | |
MD5:9445B31349B9DD2CC522B10954200049 | SHA256:BCE88210CE6884A453A38C73317920A8C3D13AE42700F3F717EDCF2B1D369BAF | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\broachOneill\shaleDashikiBajoire\fungo.xml | xml | |
MD5:244DEA20FA36286413B32ECD871A571A | SHA256:0D4147559C86524890FA9948213AA184761C3F9F31B520197DFF96F22241F438 | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\farle.xml | xml | |
MD5:9FAAD7B598F55A690C85B4C61CCD1F53 | SHA256:B1C23E426DBBD680CC8AEA94D45E441F72D32C7574ED8EF4FE4609B2D8261C77 | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\broachOneill\solfegePumpageCityish.xml | xml | |
MD5:F14F9BB6C60E45BB0E1F843109848F73 | SHA256:11986840B99F41F688B04E03A968BC7C984369EFE0823A9873FCCDAC62683DB7 | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\broachOneill\shaleDashikiBajoire\humidorUnsealsUnbank.xml | xml | |
MD5:416DEF4CC90C4B083BBB37E05976B814 | SHA256:992EA798C938903B33ABBC2340FD185C7607C5D20FE008455E7026882E2584BB | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\gallous.xml | xml | |
MD5:73D90406B9331510AFA76A076E879AD6 | SHA256:258CD21FEF44EA1D52B0718721DBAB7DCDFB75C3B7E2099EF10549017949361A | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\broachOneill\busto.xml | xml | |
MD5:A6440D04AA8B84A3F7B373142F46AEC8 | SHA256:774579308B68D19F8EA3252E3CB51067A816BBFCC6B7F7668993110DB438BE90 | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3388.24618\res\cravats\broachOneill\shaleDashikiBajoire\baluchKenlore.xml | xml | |
MD5:BE553E5B5288FCFC8115570B26C8C849 | SHA256:CF715DFC6CBBC90A78B8D5C9C656B818026BAA666FEDA2595865C126B68C142D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
1
DNS requests
0
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
3512 | RegSvcs.exe | POST | 200 | 82.117.255.127:80 | http://82.117.255.127/c2sock | US | text | 5 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3512 | RegSvcs.exe | 82.117.255.127:80 | — | — | US | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
3512 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
1 ETPRO signatures available at the full report