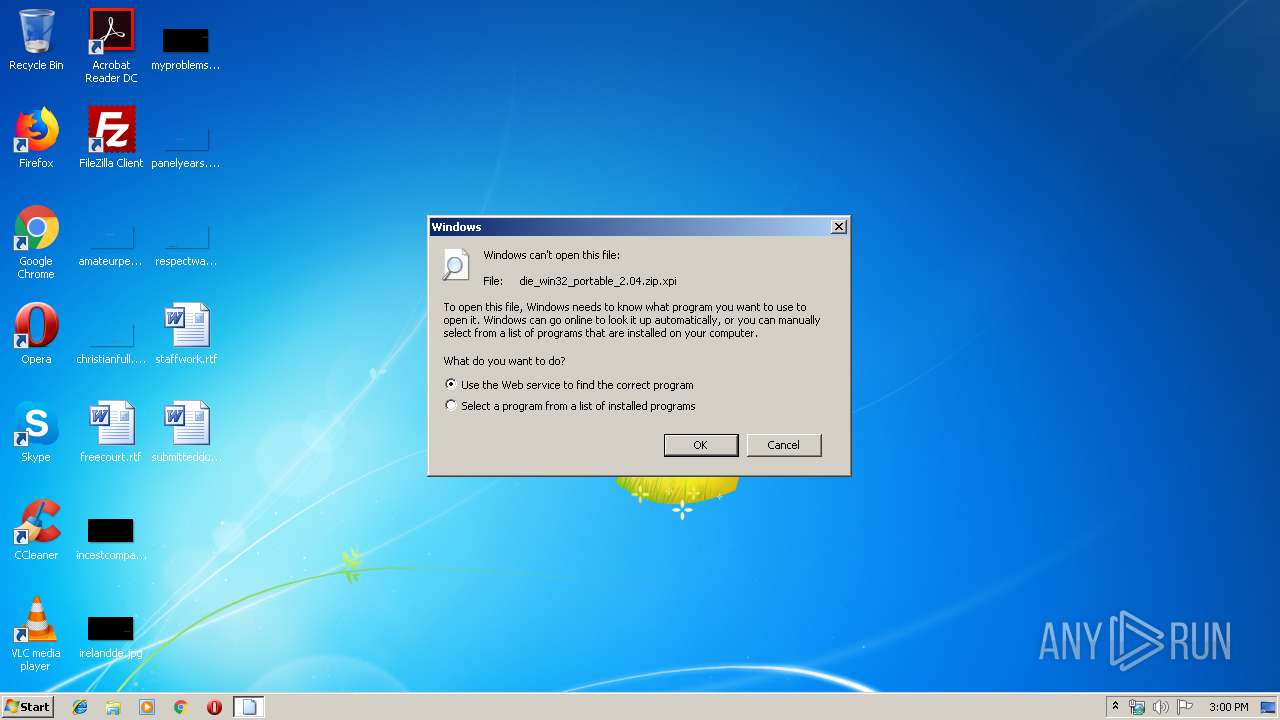
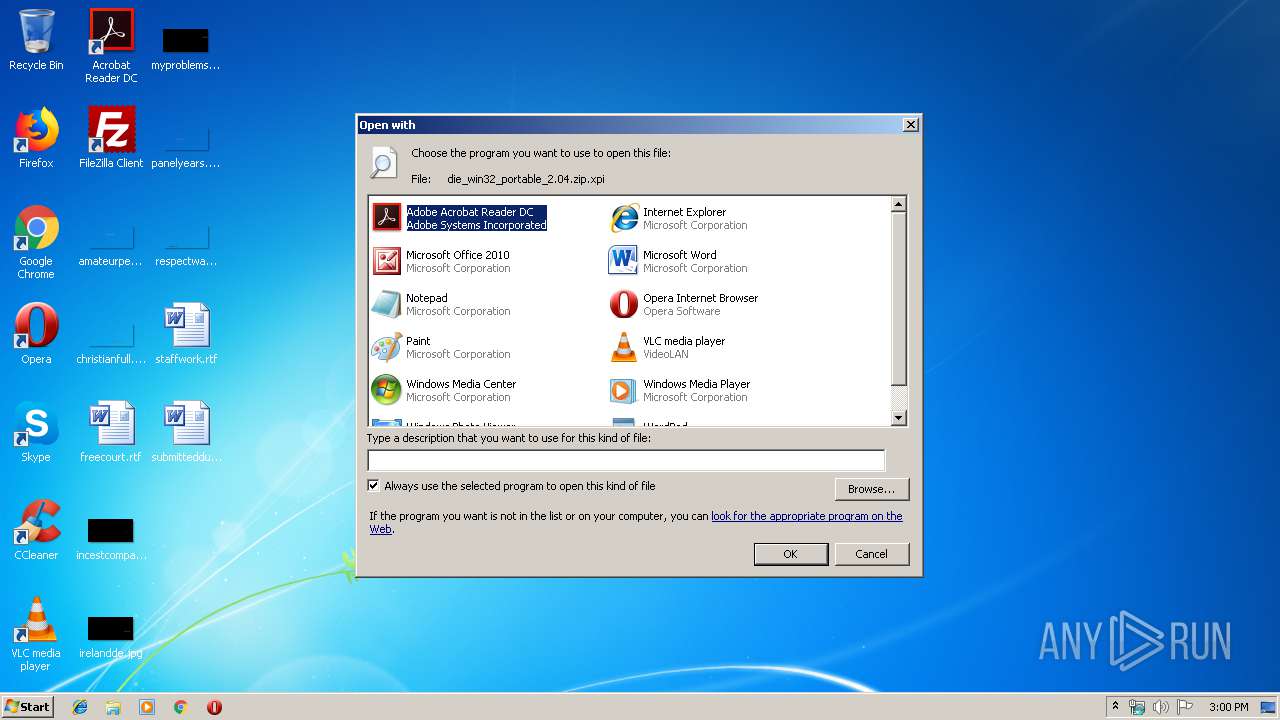
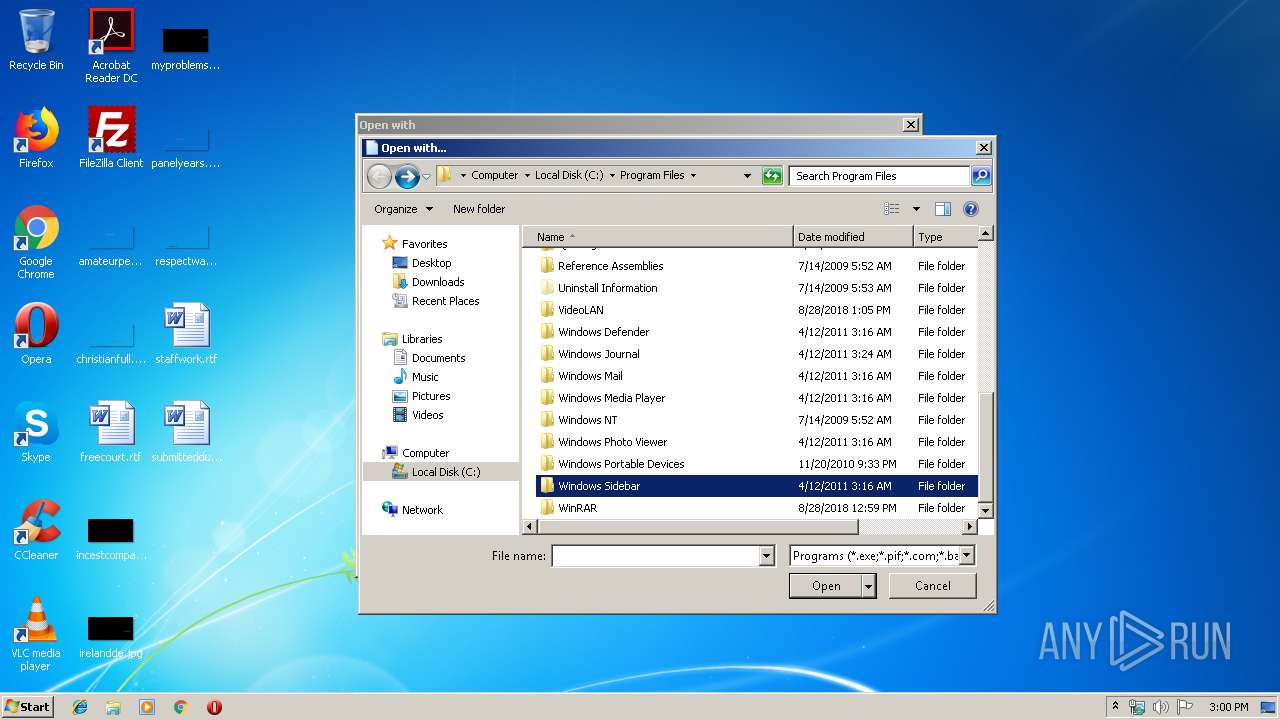
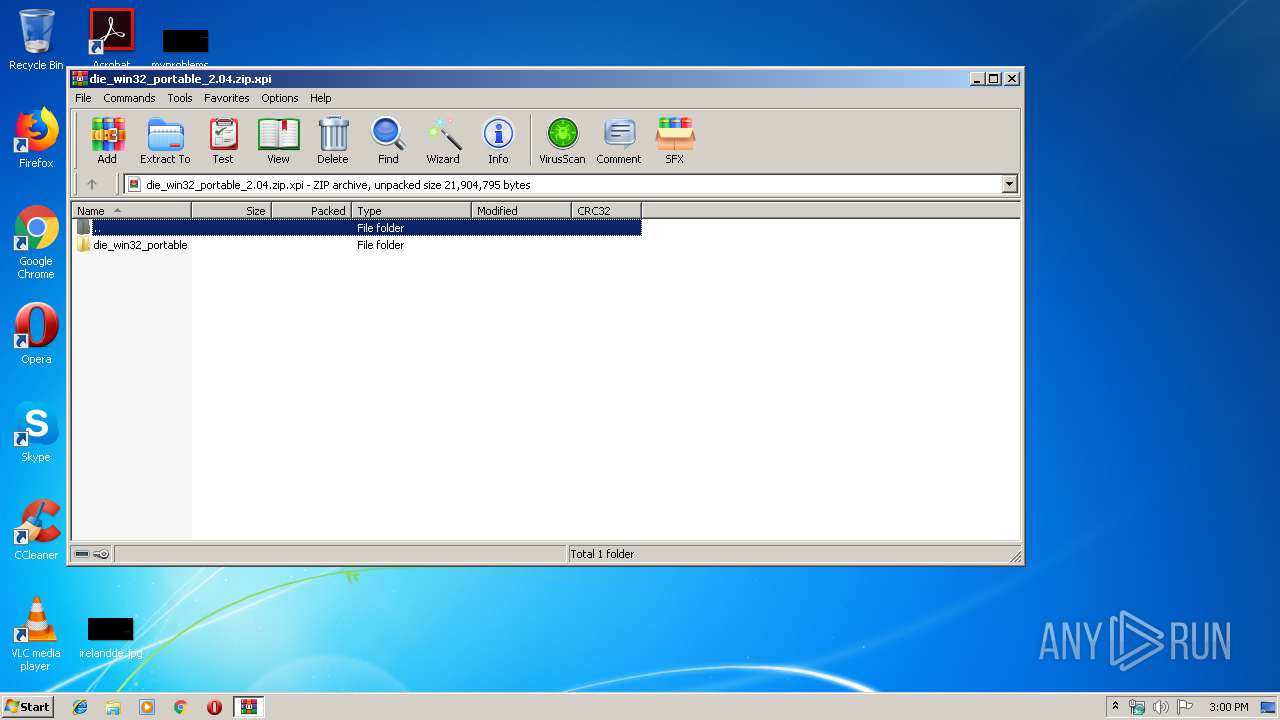
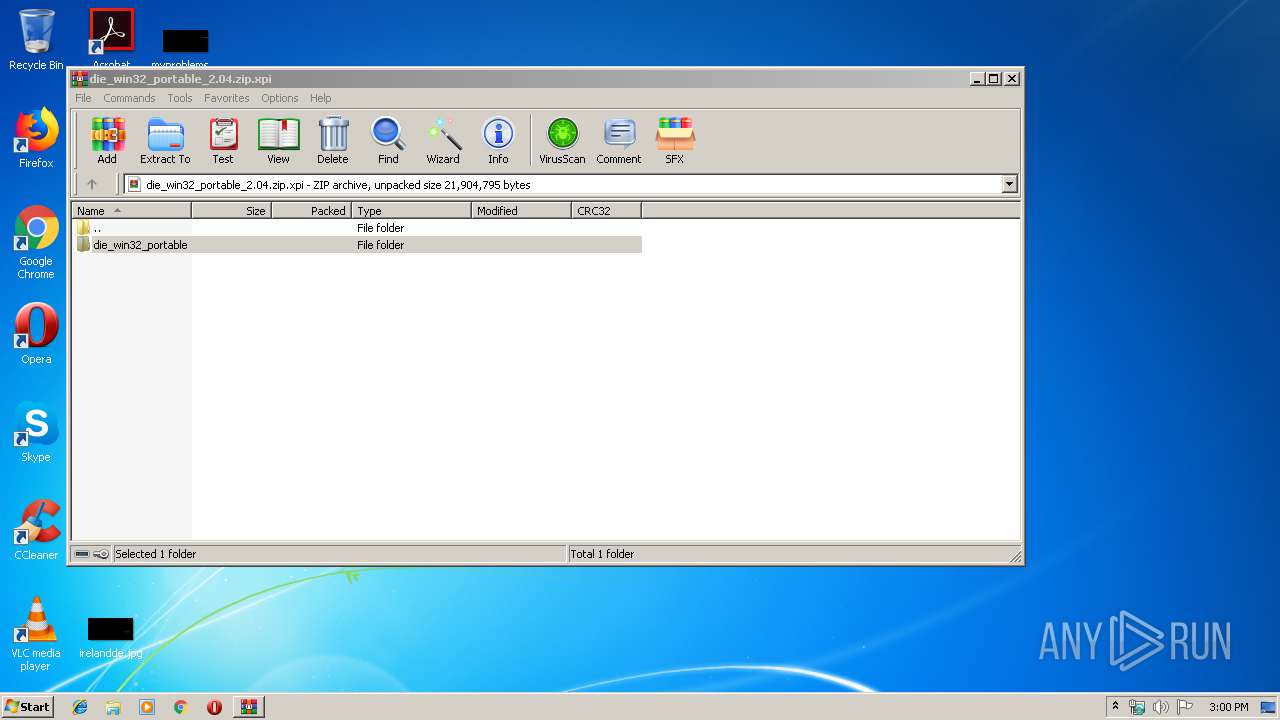
| File name: | die_win32_portable_2.04.zip |
| Full analysis: | https://app.any.run/tasks/e11c08e4-6033-4830-8570-d9b285b1b990 |
| Verdict: | Malicious activity |
| Analysis date: | September 23, 2019, 13:59:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | EEA56BAD14EC8D63FCEA679CD82CCEC0 |
| SHA1: | 4BBAC206223B8742669864A80C689BB875453CE3 |
| SHA256: | A55B795EEBFD2CB610307575D27E0D6FA154284ACD0AA16FF3967D345EDE2EA1 |
| SSDEEP: | 196608:DJmtJ5EXGlYVDU8rjEcE6hwZVU/zxh8UFcqdGaUH/ANSagnxvfhWpEJAAEO:+OG+lU8PEc0ZVUroUaSUHKoRSEJkO |
MALICIOUS
Loads dropped or rewritten executable
- diel.exe (PID: 2892)
- SearchProtocolHost.exe (PID: 596)
Application was dropped or rewritten from another process
- diel.exe (PID: 2892)
SUSPICIOUS
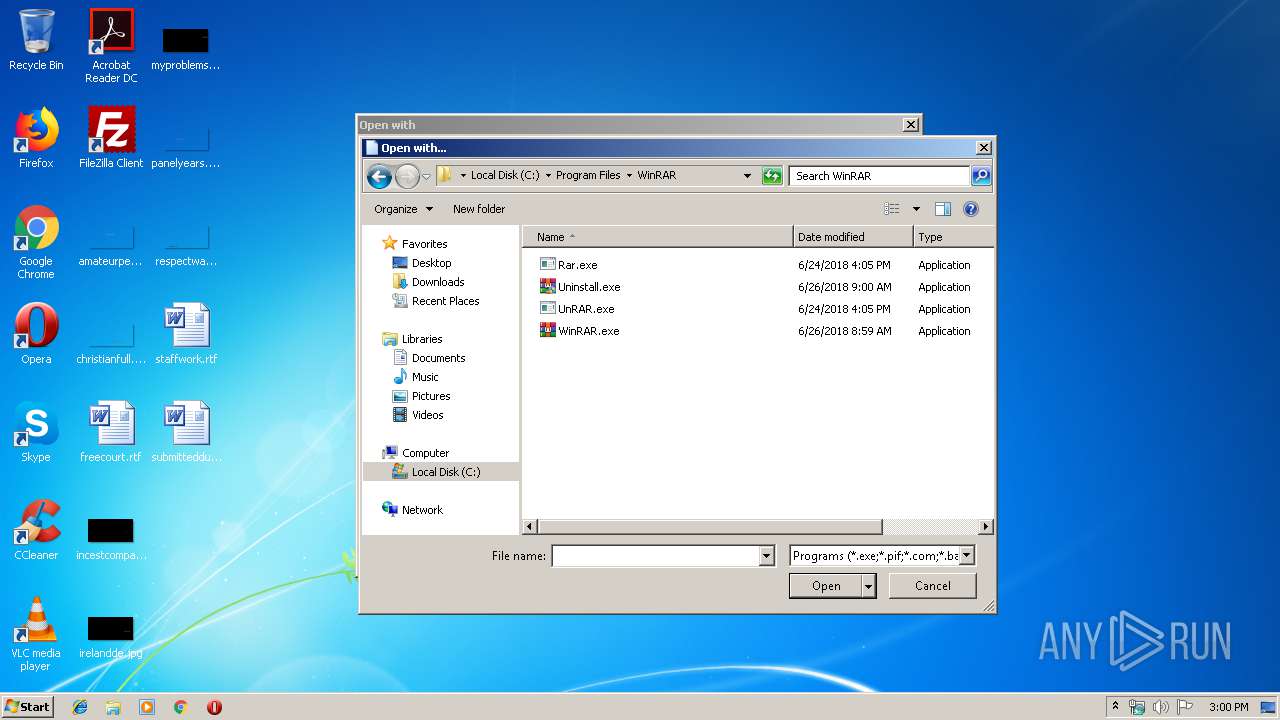
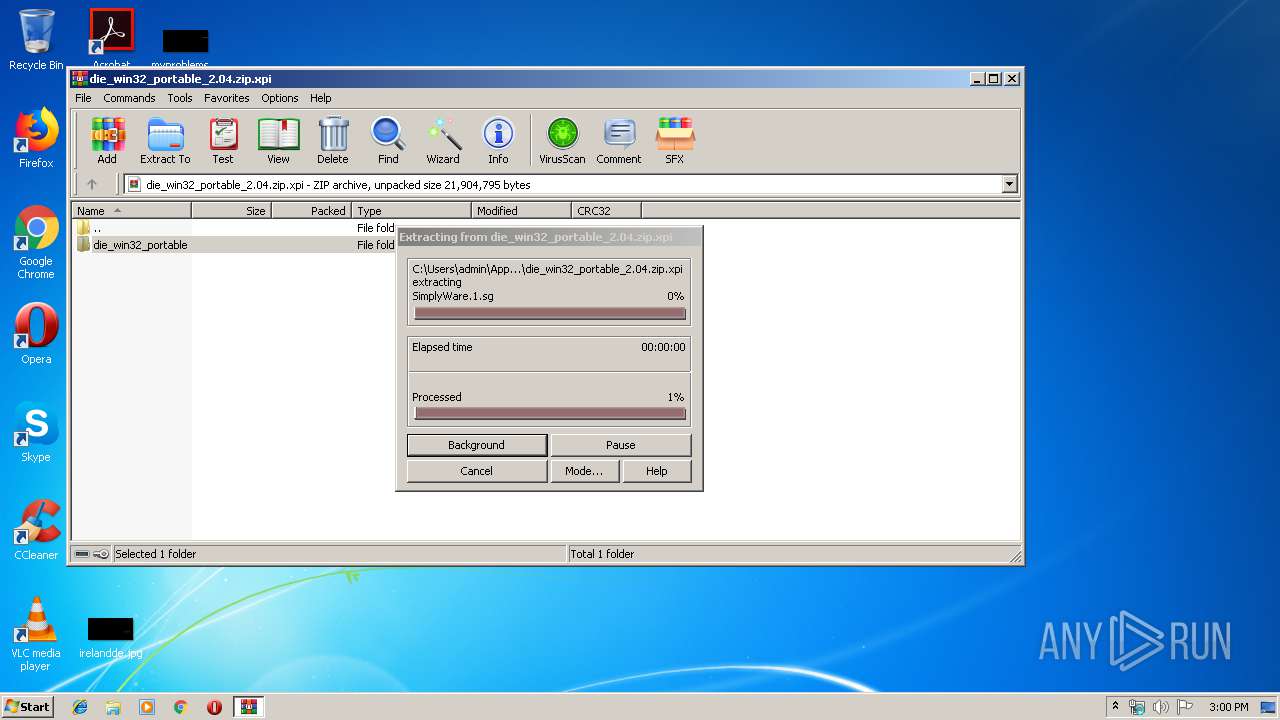
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3160)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3160)
Manual execution by user
- diel.exe (PID: 1492)
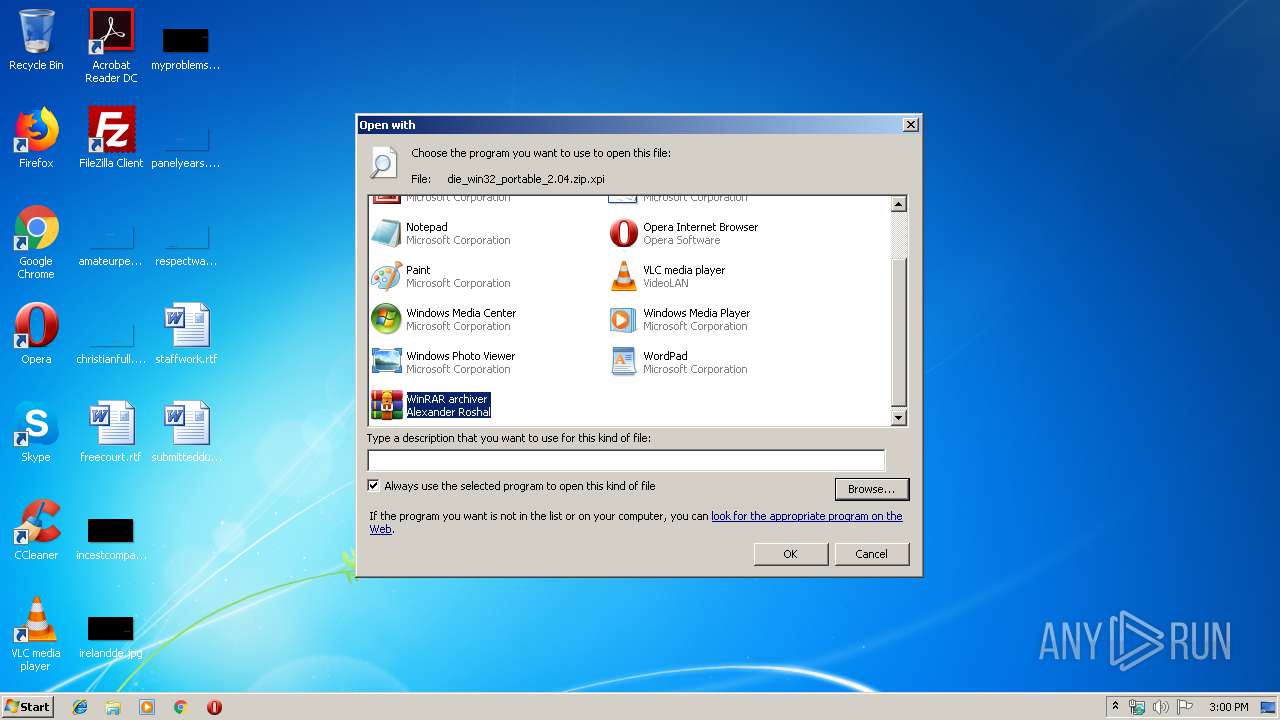
Modifies the open verb of a shell class
- rundll32.exe (PID: 3300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:06:29 21:59:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | die_win32_portable/base/ |
Total processes
36
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 596 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
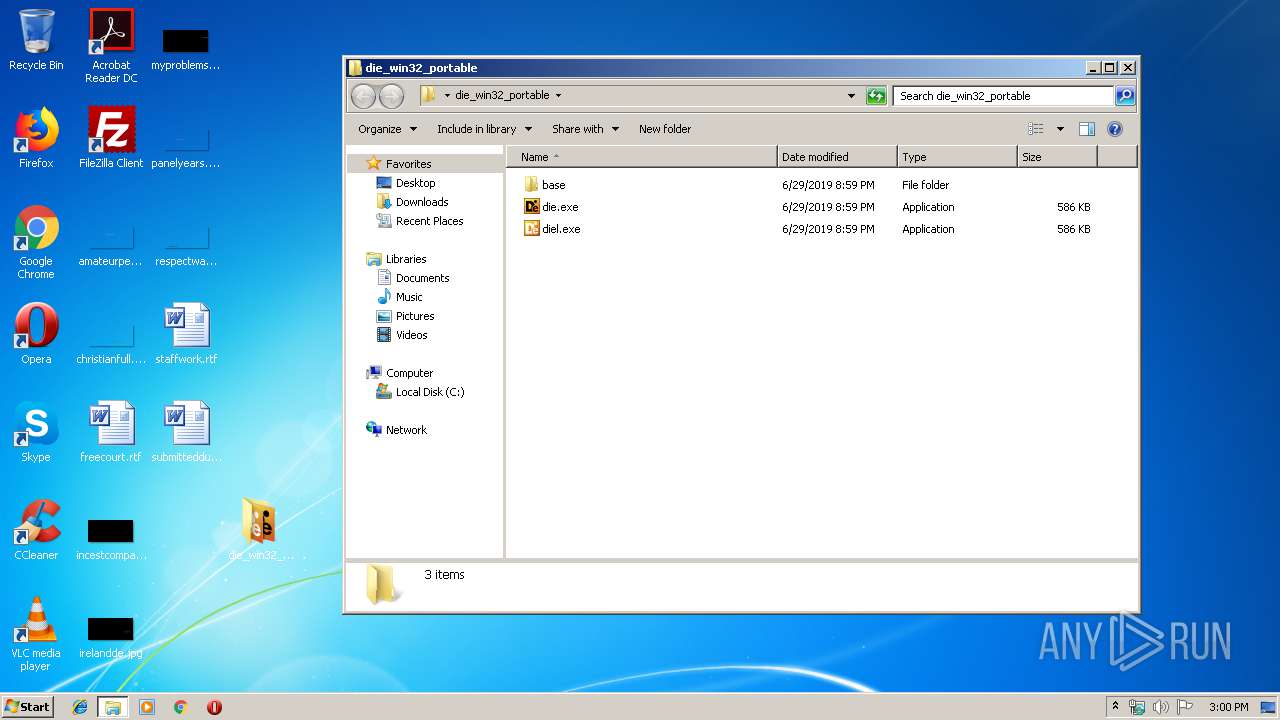
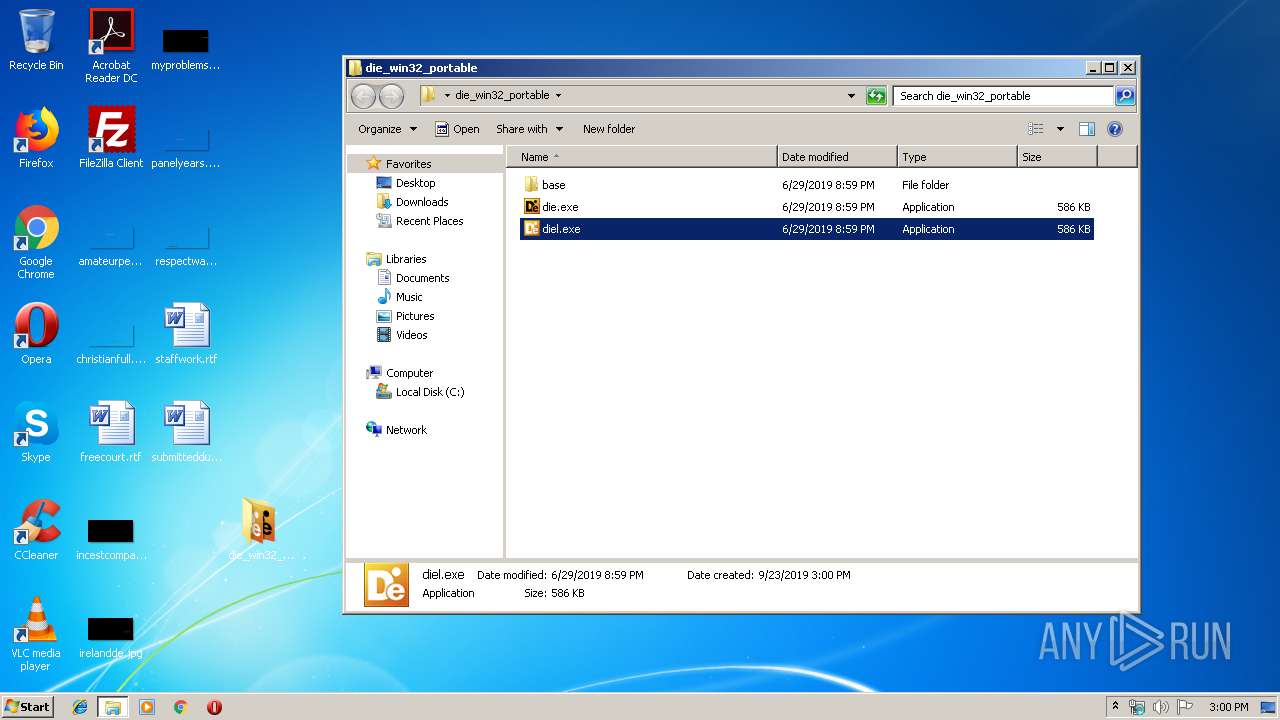
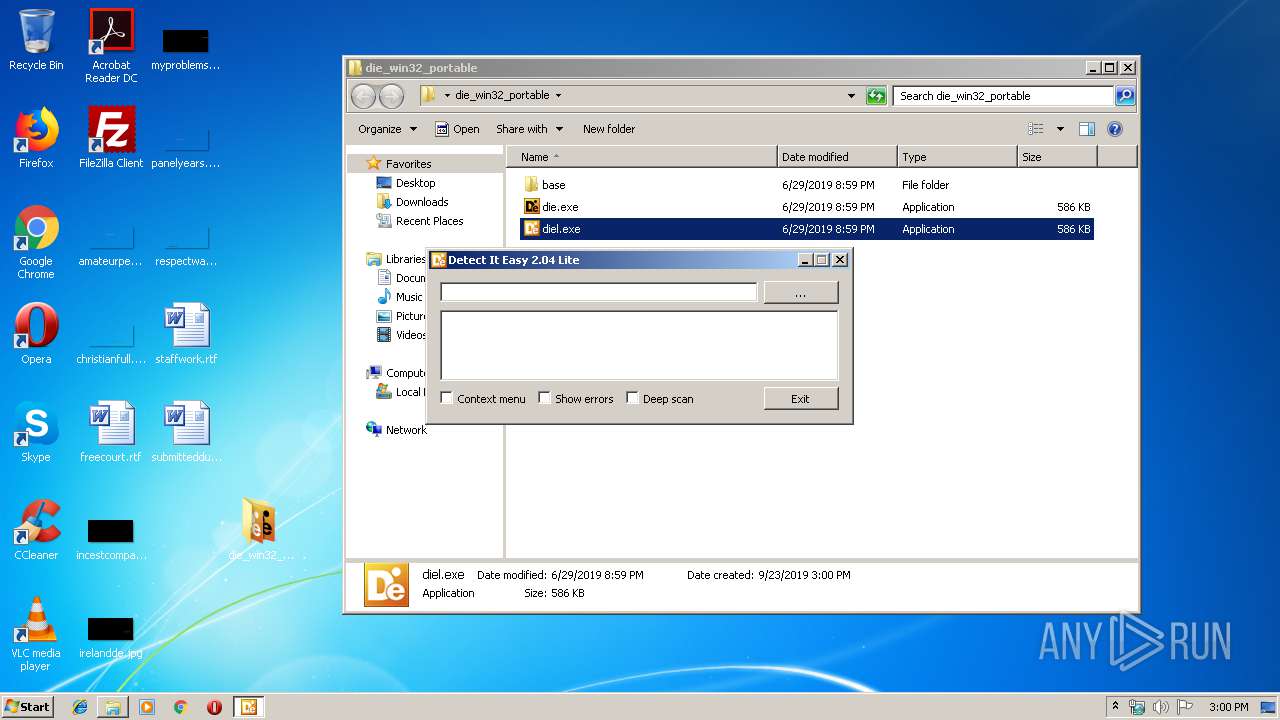
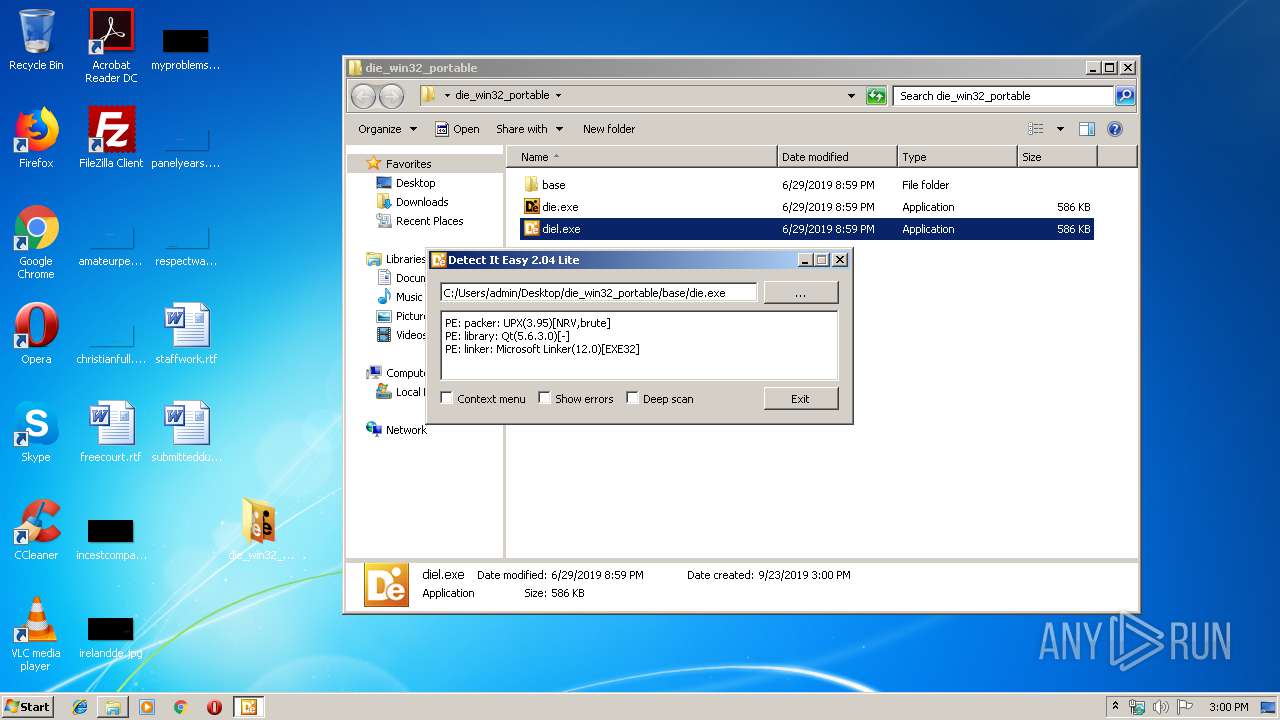
| 1492 | "C:\Users\admin\Desktop\die_win32_portable\diel.exe" | C:\Users\admin\Desktop\die_win32_portable\diel.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2892 | "C:\Users\admin\Desktop\die_win32_portable\base\diel.exe" | C:\Users\admin\Desktop\die_win32_portable\base\diel.exe | — | diel.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\die_win32_portable_2.04.zip.xpi" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3300 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\die_win32_portable_2.04.zip.xpi | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 302
Read events
2 032
Write events
268
Delete events
2
Modification events
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000070000000200000009000000080000000000000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000040000000200000003000000FFFFFFFF | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\35\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\1 |
| Operation: | write | Name: | 5 |
Value: 64003100000000008C3E021210005749343232337E3100004C0008000400EFBEEE3A90268C3E02122A000000C7000000000001000000000000000000000000000000570069006E0064006F007700730020005300690064006500620061007200000018000000 | |||
| (PID) Process: | (3300) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: 050000000400000003000000010000000000000002000000FFFFFFFF | |||
Executable files
17
Suspicious files
0
Text files
1 323
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\archives.1.sg | text | |
MD5:— | SHA256:— | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\7z.1.sg | text | |
MD5:25CF0911FEA65A5A6A3D8AFA09C3C376 | SHA256:ACECD5BE79FB377F2728651B7CBB77866914DA8CE3E8D83BFAE5A0A52CE2AA06 | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\arj | text | |
MD5:E4158633E7F2AEC1703496E43345BA7B | SHA256:AC3967DD2AEE6BF203E502E76CDA8636D4AE60BBAF0ACFC04993B060CD5778BE | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\ACE.1.sg | text | |
MD5:3EF3594E4C70D09536A57DABA4858C98 | SHA256:9B3A0C690A1BD30BFFCCF3E565423264D65378A5E286BFB8C16F2CDF00A0E067 | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\ANI.1.sg | text | |
MD5:9E5E26F72D12CC134311C49C7352D97E | SHA256:C0DFB14CD6B426CA7AD333DEBB43F5594E736D8558F7CD44CC8AA740D51E55F3 | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\ARJ.1.sg | text | |
MD5:54D0943CB2258DC1B7DA947E690C21D2 | SHA256:18B44BFB9C336354A949507BE1E67BF68759D88EDB12CA8F734C46FFB526428A | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\AAALogo.1.sg | text | |
MD5:E92C115C72DA1D351E89A3092D4EE9D9 | SHA256:4AC6B9076AD9A5ABB8849058D5E2F7EB32C5244B8D79D344D036760949D3E372 | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\Atari ST.1.sg | text | |
MD5:F43FA79DB62D33FDB8F1277F66CBBD85 | SHA256:97951632226F67EEF73377B1D234E04F27657D751BE5F08A05CEDF50E0B262DF | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\audio.1.sg | text | |
MD5:5AC64FDDEF988C97A168446A05DE1293 | SHA256:950C686E40877907C16A34A49216A10643424A1918CDCBF08B2933F9324E85BA | |||
| 3160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3160.24333\die_win32_portable\base\db\Binary\COFF library.1.sg | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report