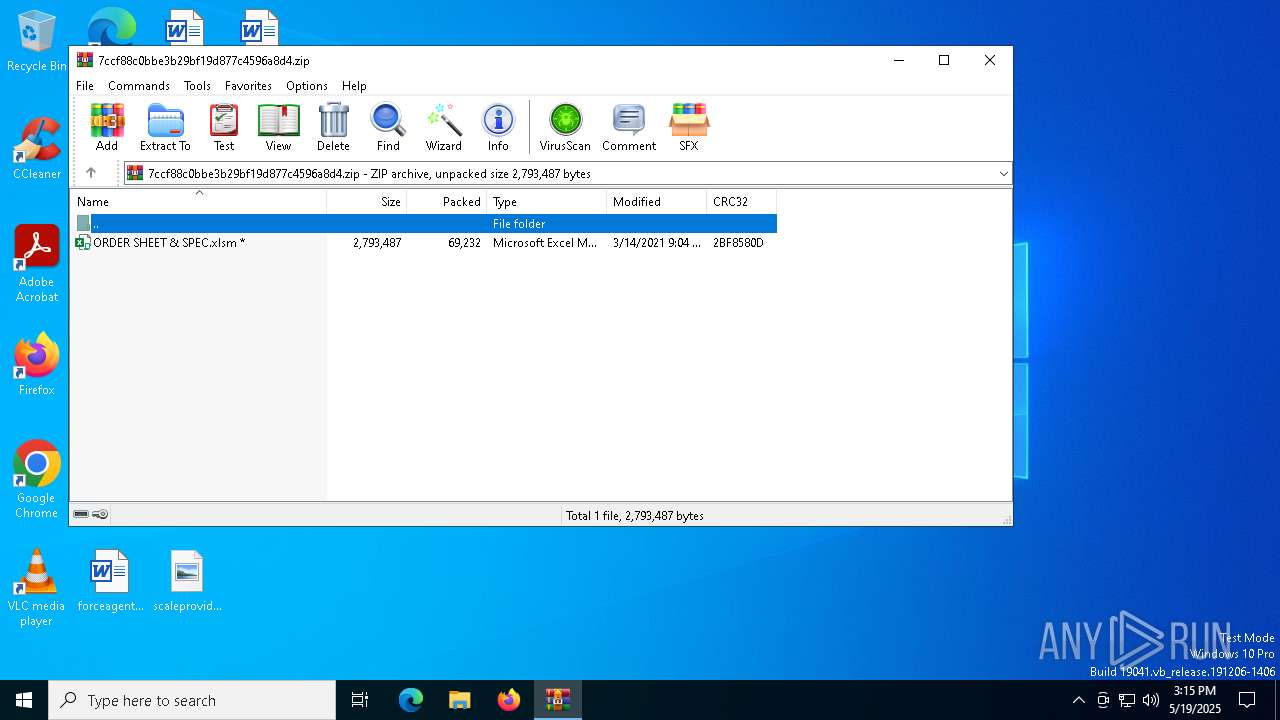
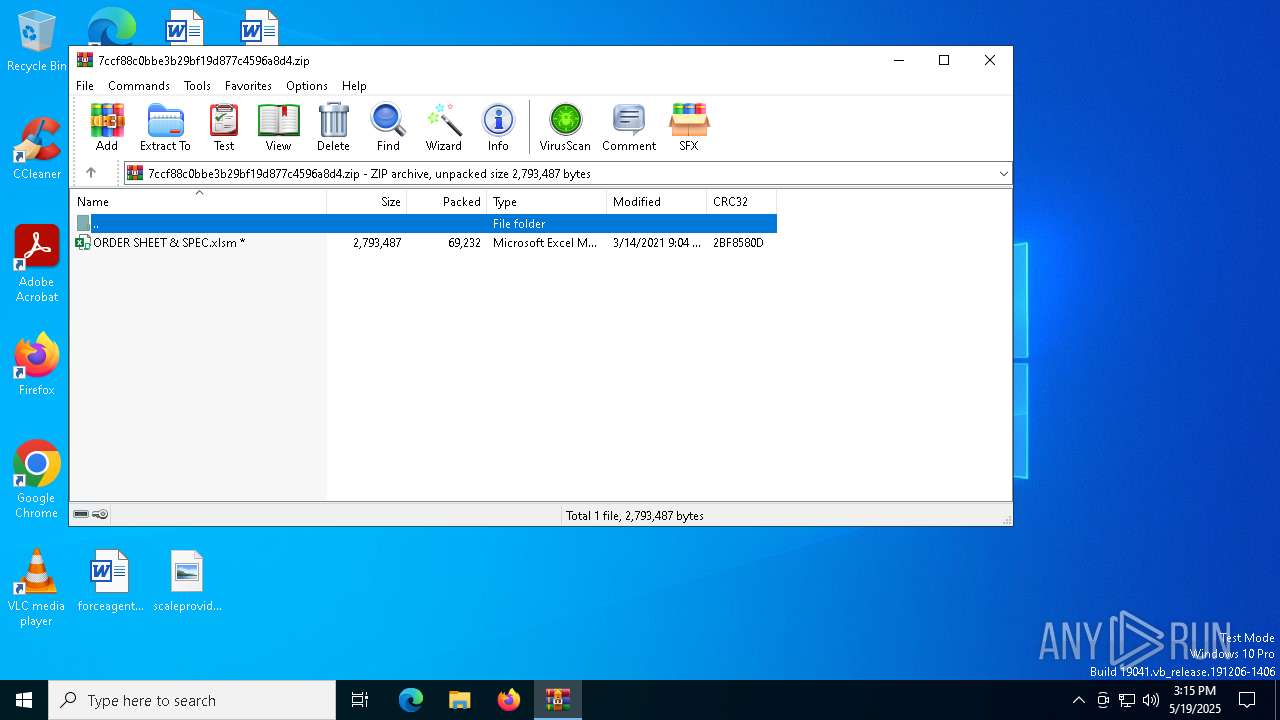
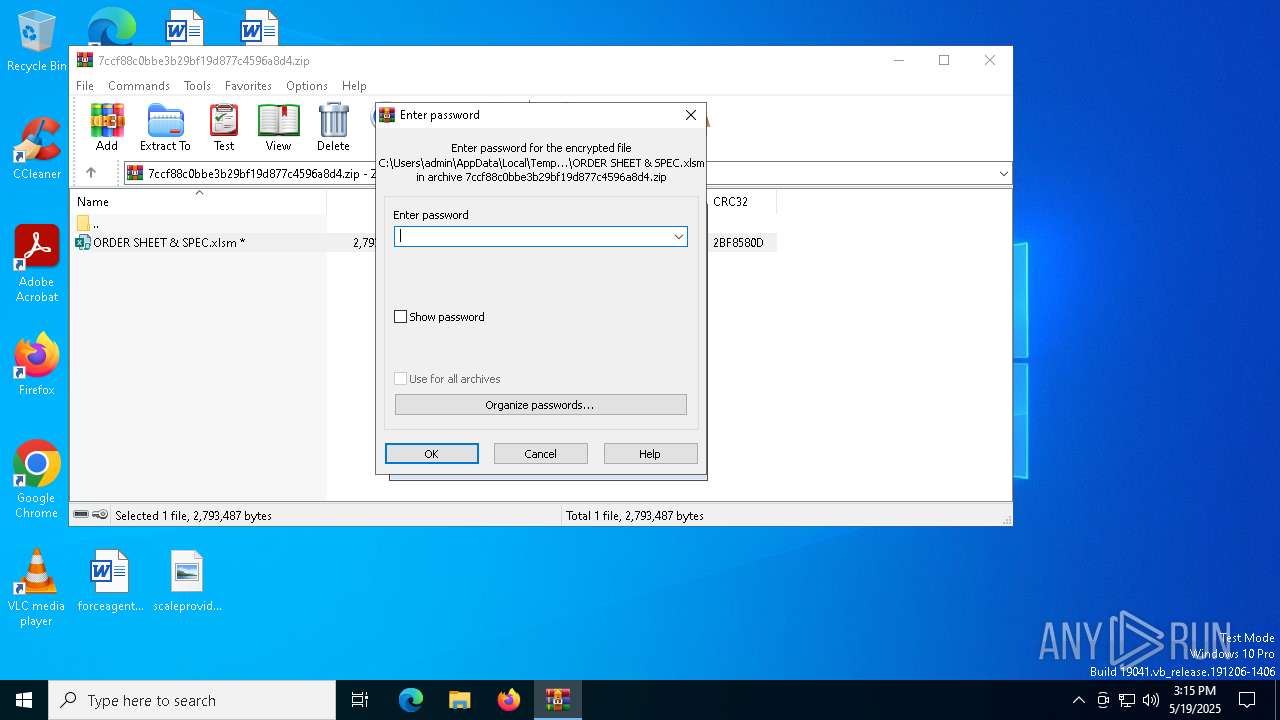
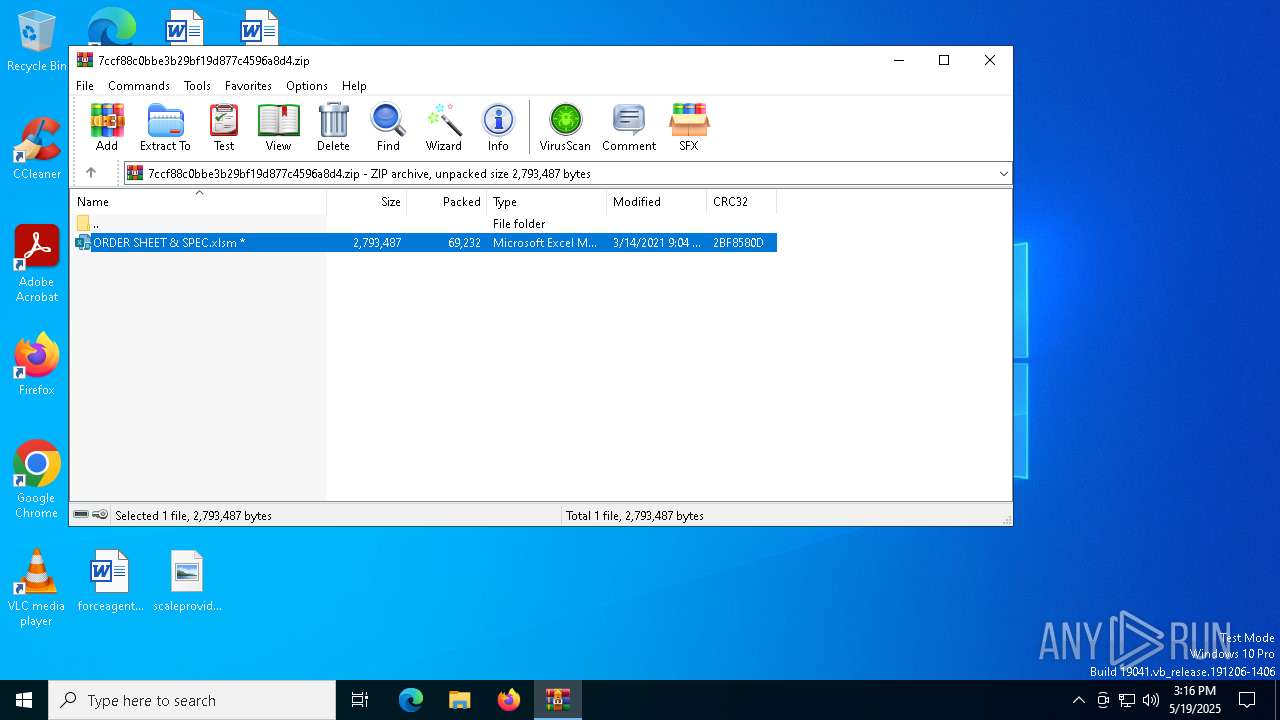
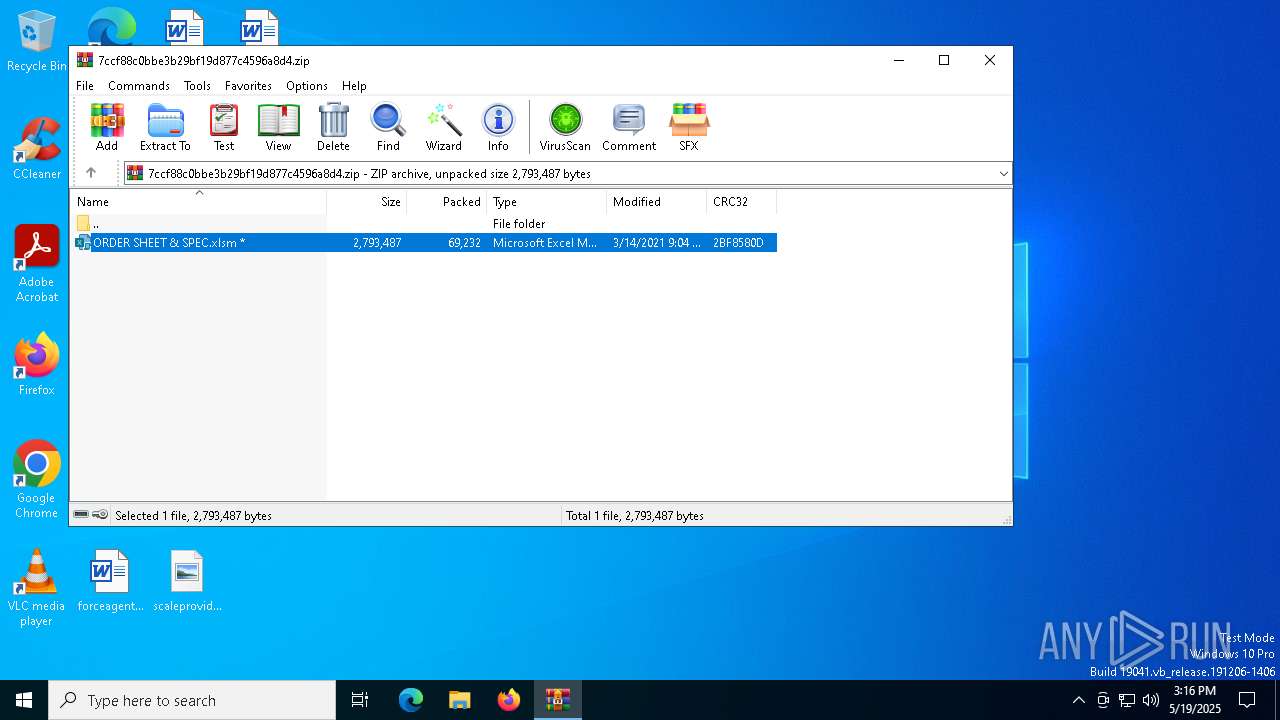
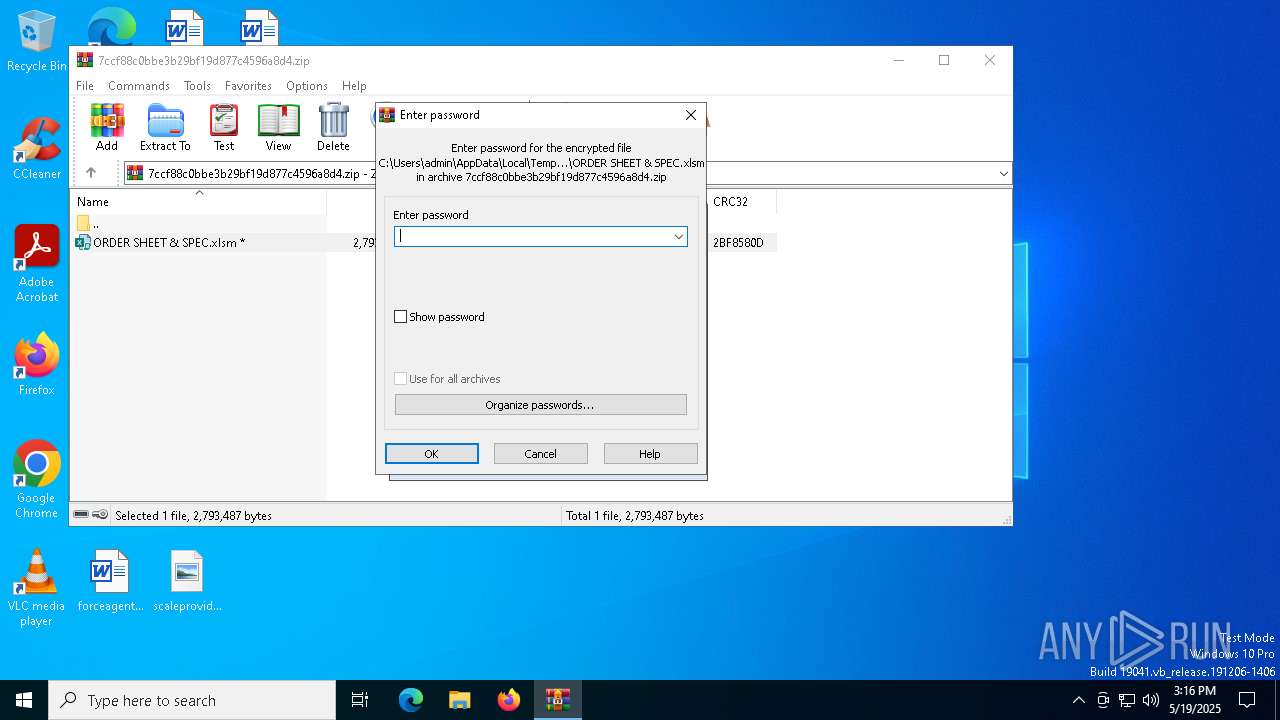
| File name: | 7ccf88c0bbe3b29bf19d877c4596a8d4.zip |
| Full analysis: | https://app.any.run/tasks/c74ad03f-de5c-44f1-bd5d-161f02073571 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 15:15:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
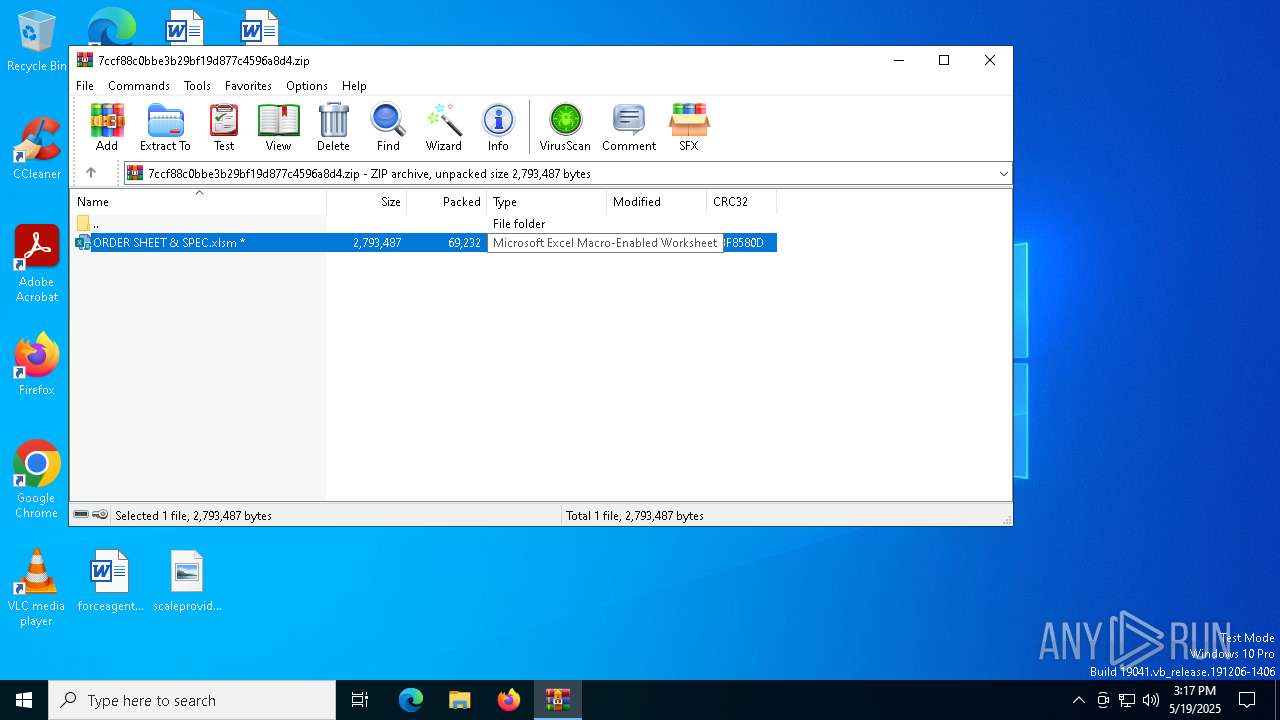
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | ADEE407A5D9F4425707FE5BD4C25AA14 |
| SHA1: | 5A99F6B3B106DAF23BA2C29F2FF94CB118703414 |
| SHA256: | A53DB45F1D4A2F36EBC0B0E268D2073BABA89CA6C1D05FE9A06EF395E8658A51 |
| SSDEEP: | 1536:jjaEudvK51sOagtBDPihqGGJRvbB8lmAqQap28rxmQ3wIUG7ChXtZlYGdf:jejdvK17JKhqNjv3p2oxzw67CVtZlYi |
MALICIOUS
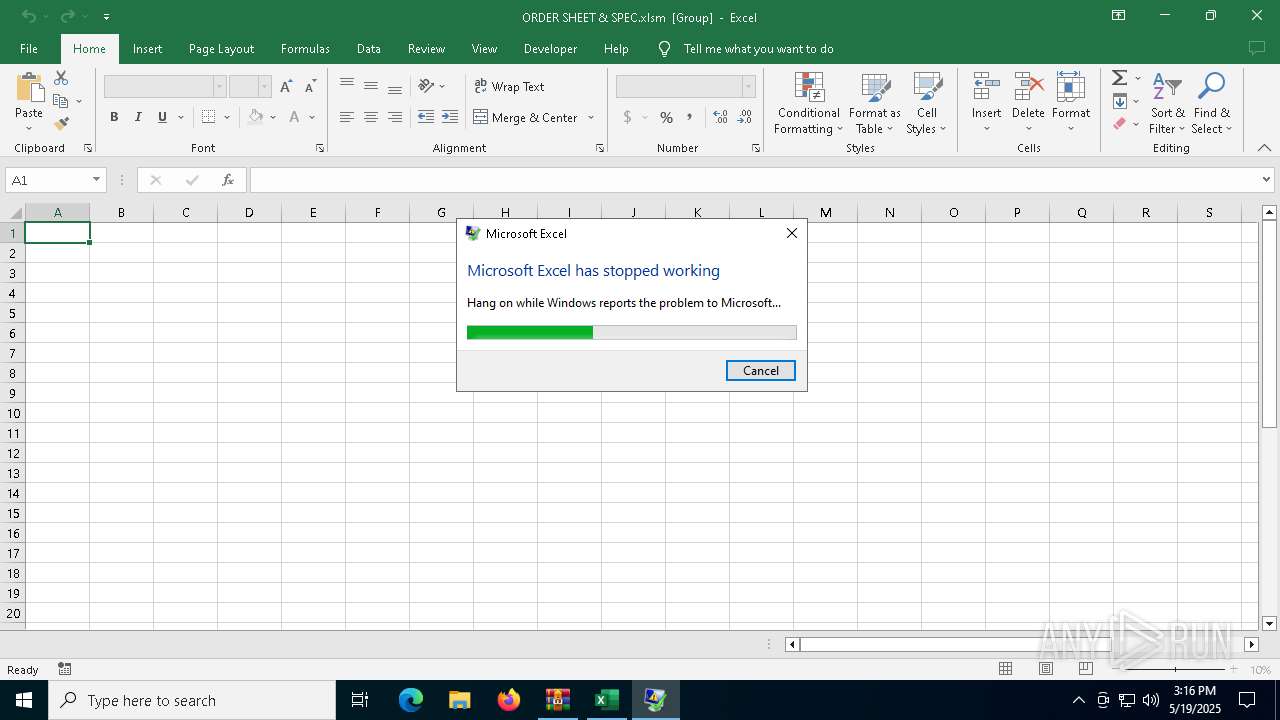
Unusual execution from MS Office
- EXCEL.EXE (PID: 7760)
- EXCEL.EXE (PID: 672)
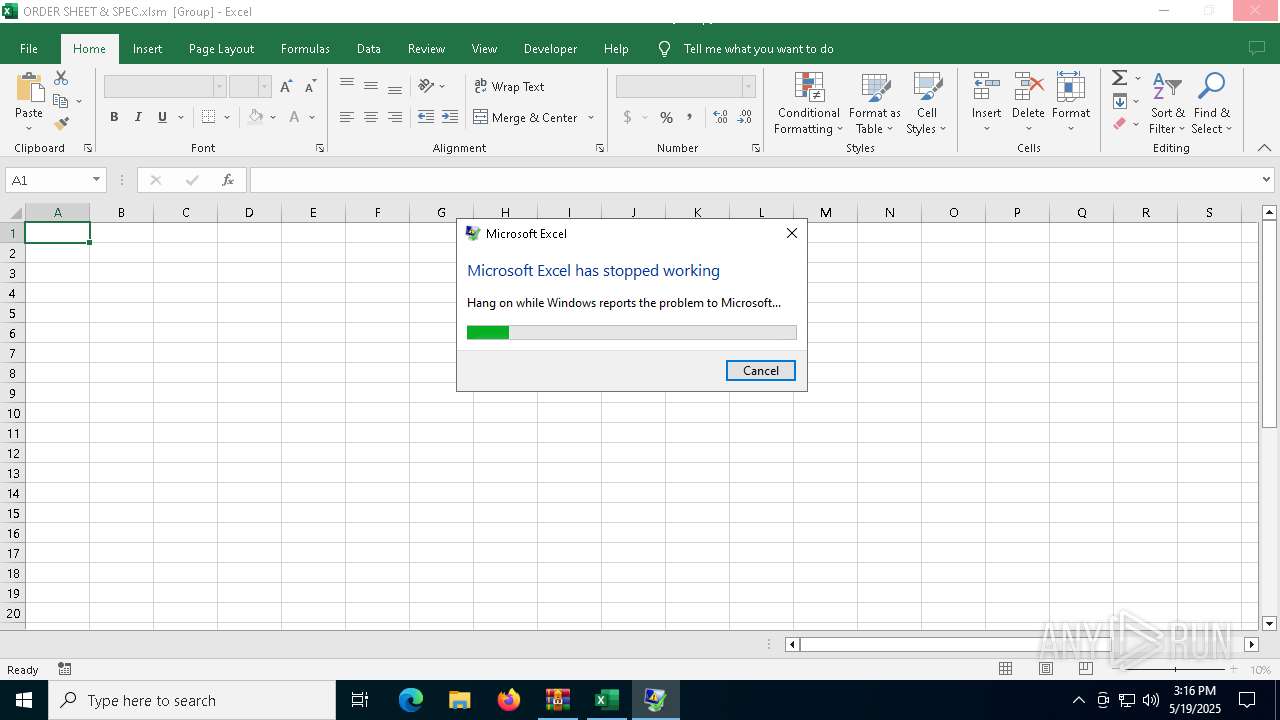
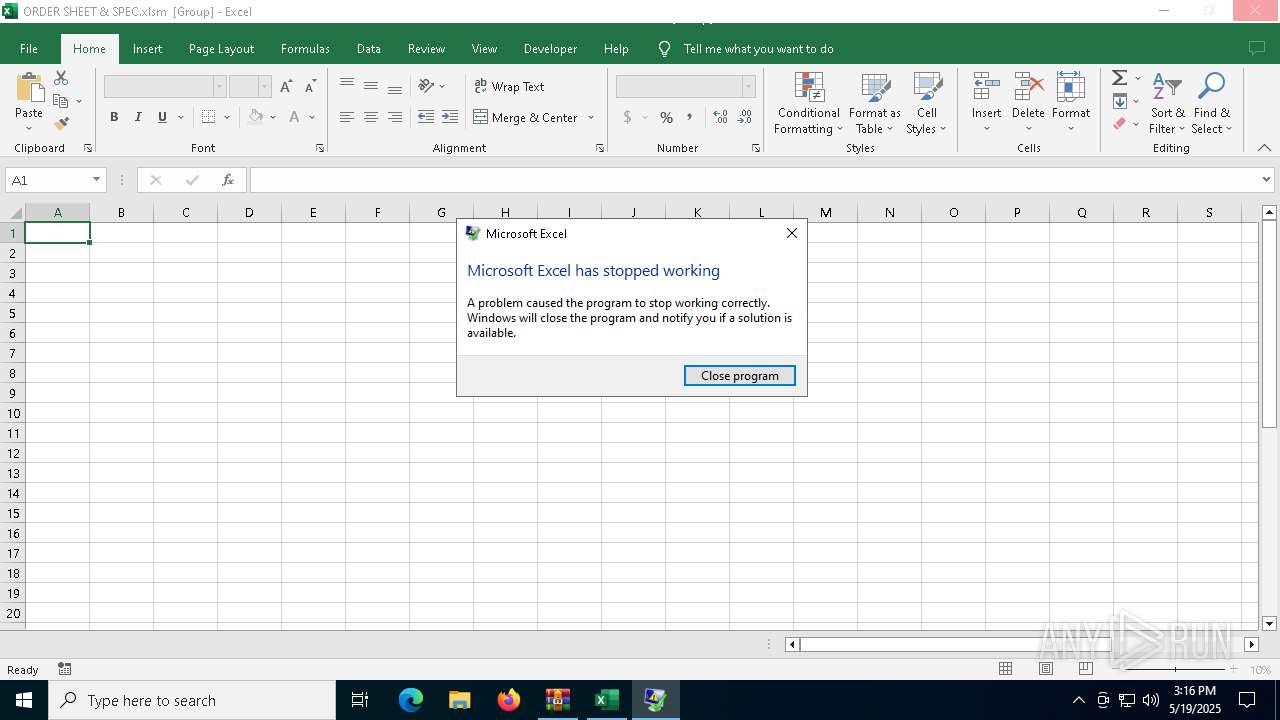
Phishing document has been detected
- WinRAR.exe (PID: 6048)
- EXCEL.EXE (PID: 7760)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6048)
Detected use of alternative data streams (AltDS)
- EXCEL.EXE (PID: 7760)
- EXCEL.EXE (PID: 672)
INFO
Creates files in the program directory
- EXCEL.EXE (PID: 7760)
- DWWIN.EXE (PID: 4560)
- DWWIN.EXE (PID: 7472)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6048)
- DWWIN.EXE (PID: 4560)
- DWWIN.EXE (PID: 7472)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 4560)
Reads the software policy settings
- DWWIN.EXE (PID: 4560)
- slui.exe (PID: 7336)
Checks proxy server information
- DWWIN.EXE (PID: 4560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:03:14 21:04:16 |
| ZipCRC: | 0x2bf8580d |
| ZipCompressedSize: | 69232 |
| ZipUncompressedSize: | 2793487 |
| ZipFileName: | ORDER SHEET & SPEC.xlsm |
Total processes
142
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb6048.12806\ORDER SHEET & SPEC.xlsm" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 960 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\system32\dwwin.exe -x -s 4604 | C:\Windows\System32\DWWIN.EXE | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\7ccf88c0bbe3b29bf19d877c4596a8d4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7304 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7472 | C:\WINDOWS\system32\dwwin.exe -x -s 5108 | C:\Windows\System32\DWWIN.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7760 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb6048.6542\ORDER SHEET & SPEC.xlsm" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 4 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
16 582
Read events
16 134
Write events
419
Delete events
29
Modification events
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7ccf88c0bbe3b29bf19d877c4596a8d4.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.xlsm\OpenWithProgids |
| Operation: | write | Name: | Excel.SheetMacroEnabled.12 |
Value: | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
26
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4560 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_EXCEL.EXE_f0ba593678c823b3c7333937273fe7d2c1fa42_00000000_a4cf5317-3a05-40f6-afee-64d1aef3bc5d\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7760 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\mso3A76.tmp | — | |
MD5:— | SHA256:— | |||
| 7760 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:FDD73F011377A18D67EAF2F227921713 | SHA256:55DE2C709E41C031DD07551722B6FD98EBCC7319F3EA215BB669DED0A1933605 | |||
| 7760 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\5B7FE4B3-F705-4735-834B-389B9A0C68EB | xml | |
MD5:85B71D3CA2582F2295823C86C4A01A0F | SHA256:BCE2A4D7CC59493662DFE0E544436B634074BD77D72BBA6EF9AEC1490FDD5111 | |||
| 4560 | DWWIN.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:5B63C0144C61100C949E65C9B4C7B790 | SHA256:51E7A9D4403161514027724D012C19E4717FD92CC87B31049944A37B40228B8E | |||
| 7760 | EXCEL.EXE | C:\ProgramData\asc.txt:script1.vbs | text | |
MD5:6196CE936B2131935E89615965438ED4 | SHA256:2EAA9D08D7E29C99D616AACCC4728F120E1E9A14816FECAB17F388665A89B6E4 | |||
| 4560 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBA83.tmp.WERInternalMetadata.xml | binary | |
MD5:098D2D57806B0F52CD7596128DB082D3 | SHA256:E93ECF8D0FD5B576E275AA94568297EE1ABFF2B90AD12453C4F2CFBAC885FBFA | |||
| 7760 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\964972EE.emf | binary | |
MD5:B59DD20DE3FDC50CD6B3C4BAF9C12DE8 | SHA256:979DDE2AED02F077C16AE53546C6DF9EED40E8386D6DB6FC36AEE9F966D2CB82 | |||
| 7760 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\1EC3AA17.emf | binary | |
MD5:1DA917FE3A7E876F3F711FE30E1F46DB | SHA256:4D4D1E7B04C99DCB8E885915068AD6F74CC2333E91580CDAE5CCAA00C427247F | |||
| 4560 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBAB3.tmp.xml | xml | |
MD5:859948896763F7AA9A57C28672344F2F | SHA256:5E7467BDF4726EB7B1340A437E78B5C102AED5D6F6A207E18AB66C9ED588B782 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
37
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7760 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4560 | DWWIN.EXE | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4560 | DWWIN.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
672 | EXCEL.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |