| File name: | HMA Checker &_40; WORK 100_&_41;.rar |
| Full analysis: | https://app.any.run/tasks/9dd07c61-68f9-4d2e-ae23-81ab6286d0ed |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 14:06:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 47D1316F41E7ED0BA59268E2B27751E8 |
| SHA1: | 53EA0304CE4CDB501EA5C380FA8AA66448407496 |
| SHA256: | A534365FE9104ABFB60A12E827FA2FC2220A52486E3FF1298C4220CBFD3E3EC5 |
| SSDEEP: | 12288:sP9ipFqjOT/lZ5wwhk38juNbcXGIniYgLK8yz:+9ipFqKzj5wwhosuNbWMS8yz |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
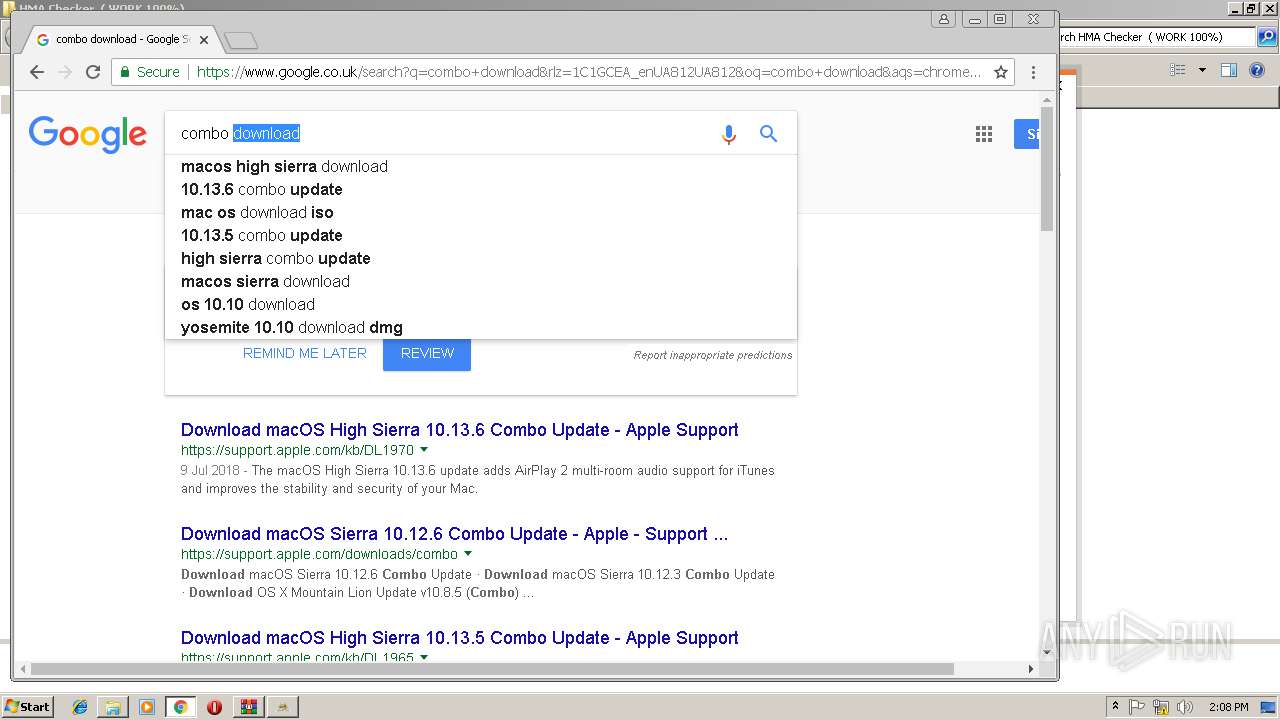
Application launched itself
- chrome.exe (PID: 408)
Reads settings of System Certificates
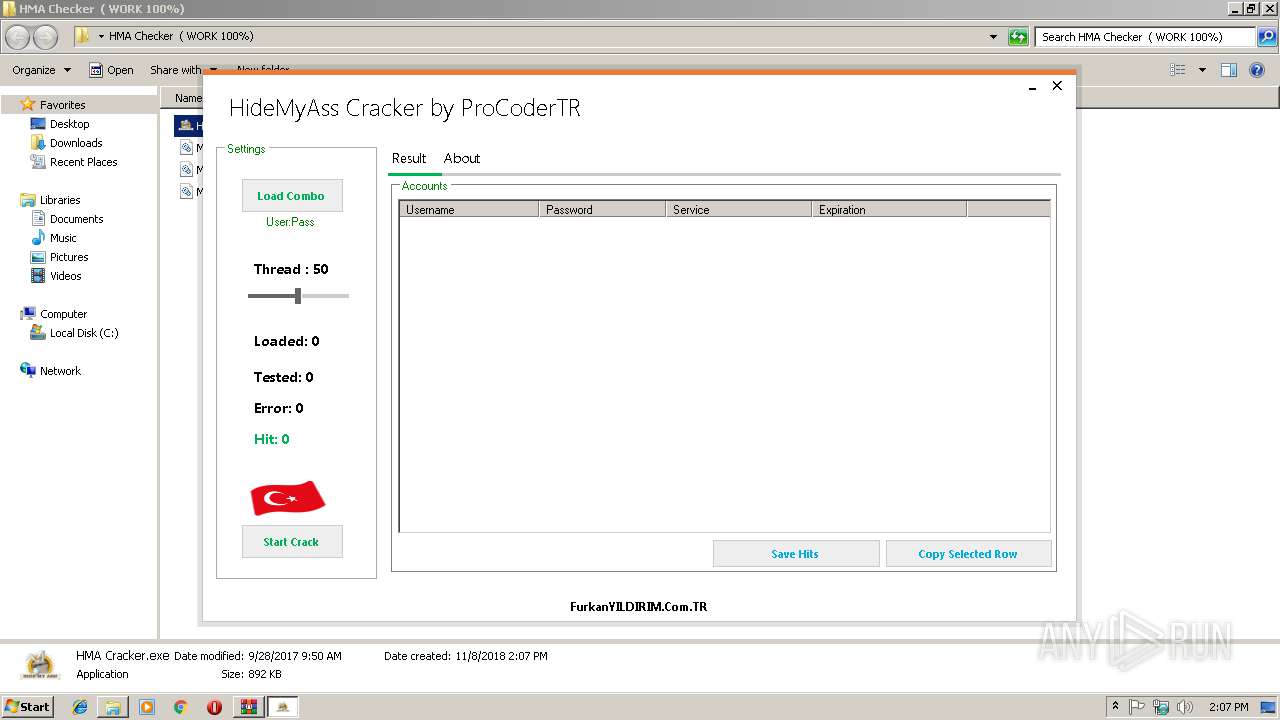
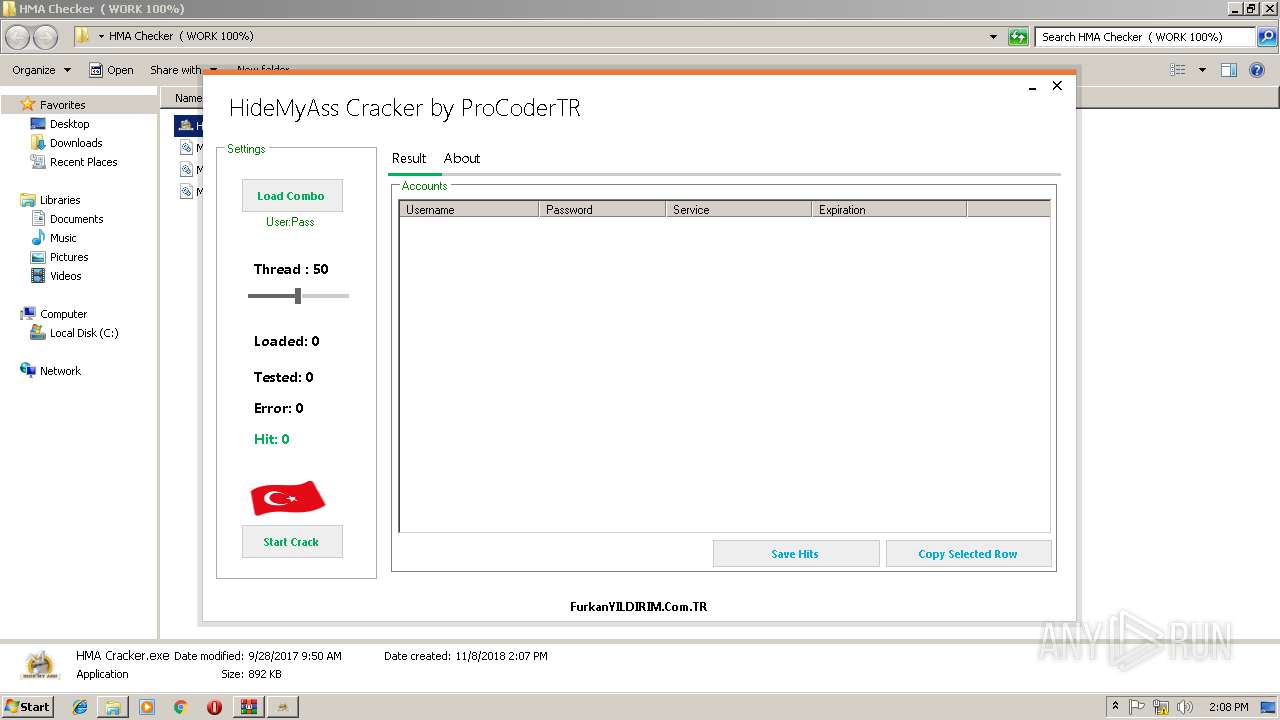
- HMA Cracker.exe (PID: 3232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 200393 |
|---|---|
| UncompressedSize: | 913408 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:09:28 09:50:05 |
| PackingMethod: | Normal |
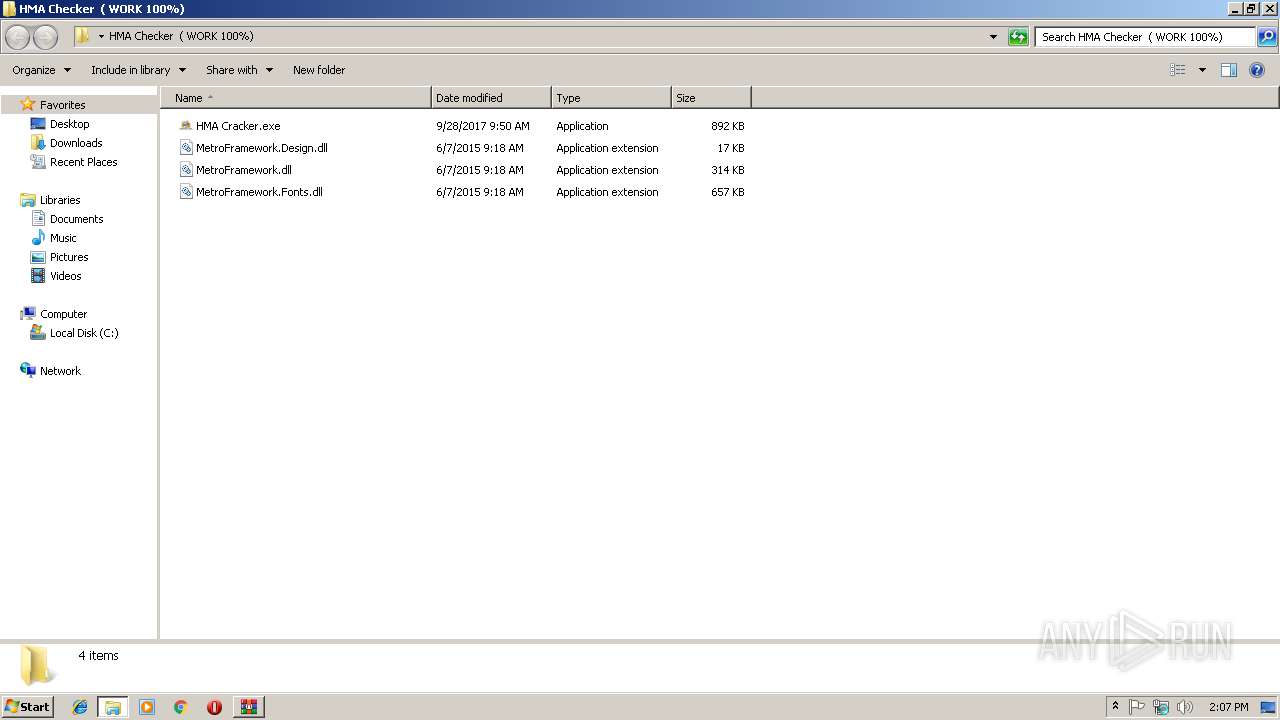
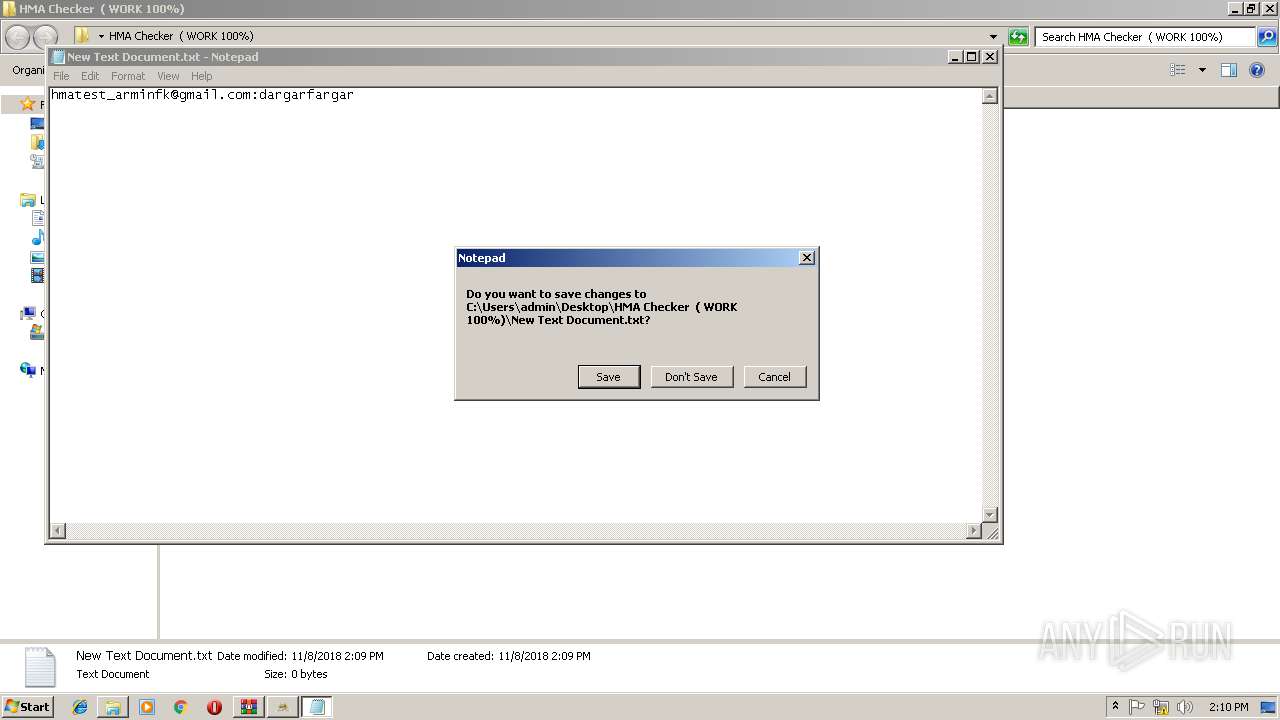
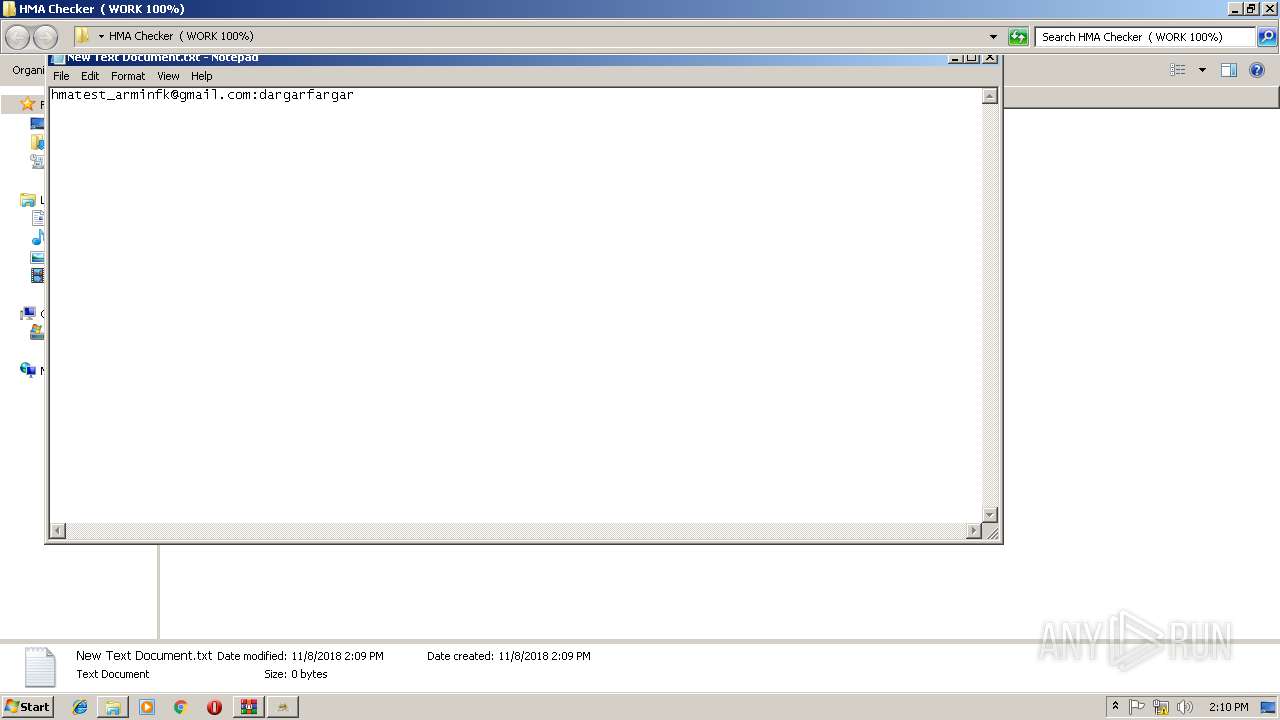
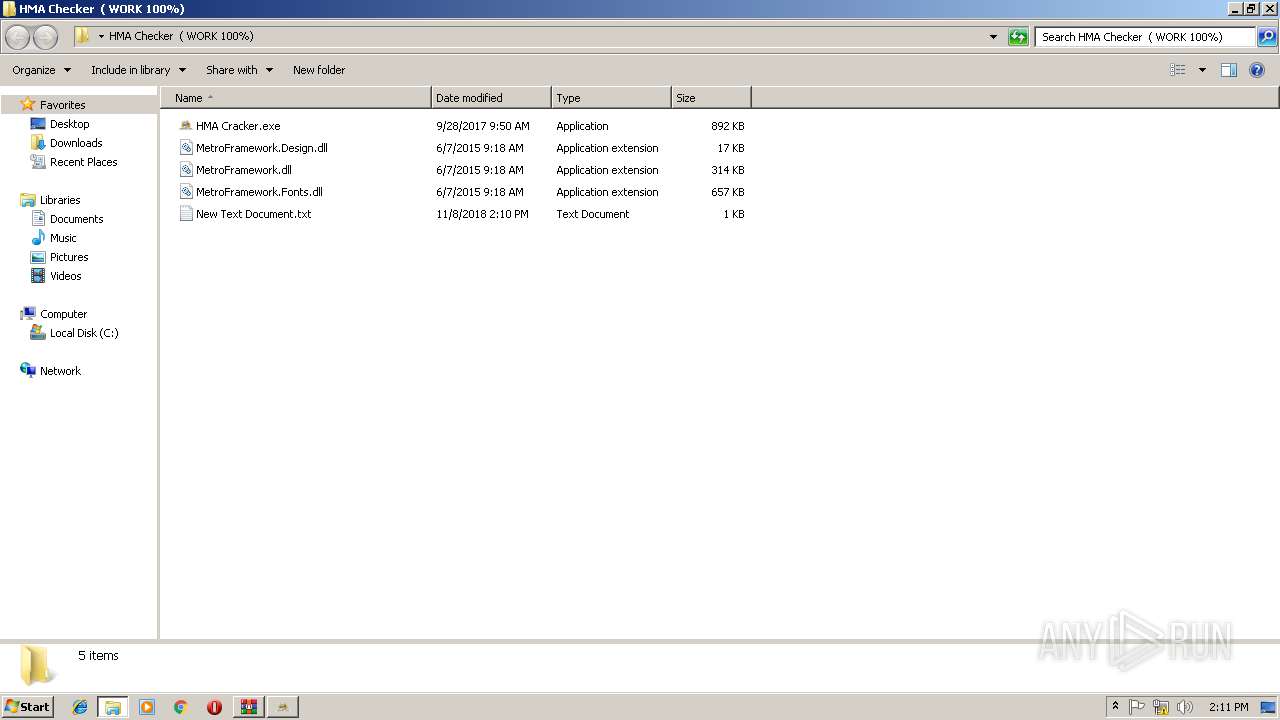
| ArchivedFileName: | HMA Checker ( WORK 100%)\HMA Cracker.exe |
Total processes
52
Monitored processes
16
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=F49FD40278A8275C28A068D6D337BB96 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=F49FD40278A8275C28A068D6D337BB96 --renderer-client-id=6 --mojo-platform-channel-handle=3528 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=448 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=A4B2F2E25628BA274C02C58B944AD1A9 --mojo-platform-channel-handle=3776 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --service-pipe-token=BE12F90F41B1C2E68F61874F31C4A450 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=BE12F90F41B1C2E68F61874F31C4A450 --renderer-client-id=5 --mojo-platform-channel-handle=1872 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=232488190049376EE382C6F665C89D3B --mojo-platform-channel-handle=3828 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --service-pipe-token=8B2924C64BEDEE2807E8A80BE4D0D6F0 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8B2924C64BEDEE2807E8A80BE4D0D6F0 --renderer-client-id=3 --mojo-platform-channel-handle=2092 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=622B8DB3FD5978A830EFD2843B47B939 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=622B8DB3FD5978A830EFD2843B47B939 --renderer-client-id=9 --mojo-platform-channel-handle=2132 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=956,7239995839572071717,7879249341911079855,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=48BA342BDE49A5F3AF3A6D6F10D0CB74 --mojo-platform-channel-handle=3540 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HMA Checker &_40; WORK 100_&_41;.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 207
Read events
1 091
Write events
112
Delete events
4
Modification events
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HMA Checker &_40; WORK 100_&_41;.rar | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
Executable files
0
Suspicious files
74
Text files
88
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
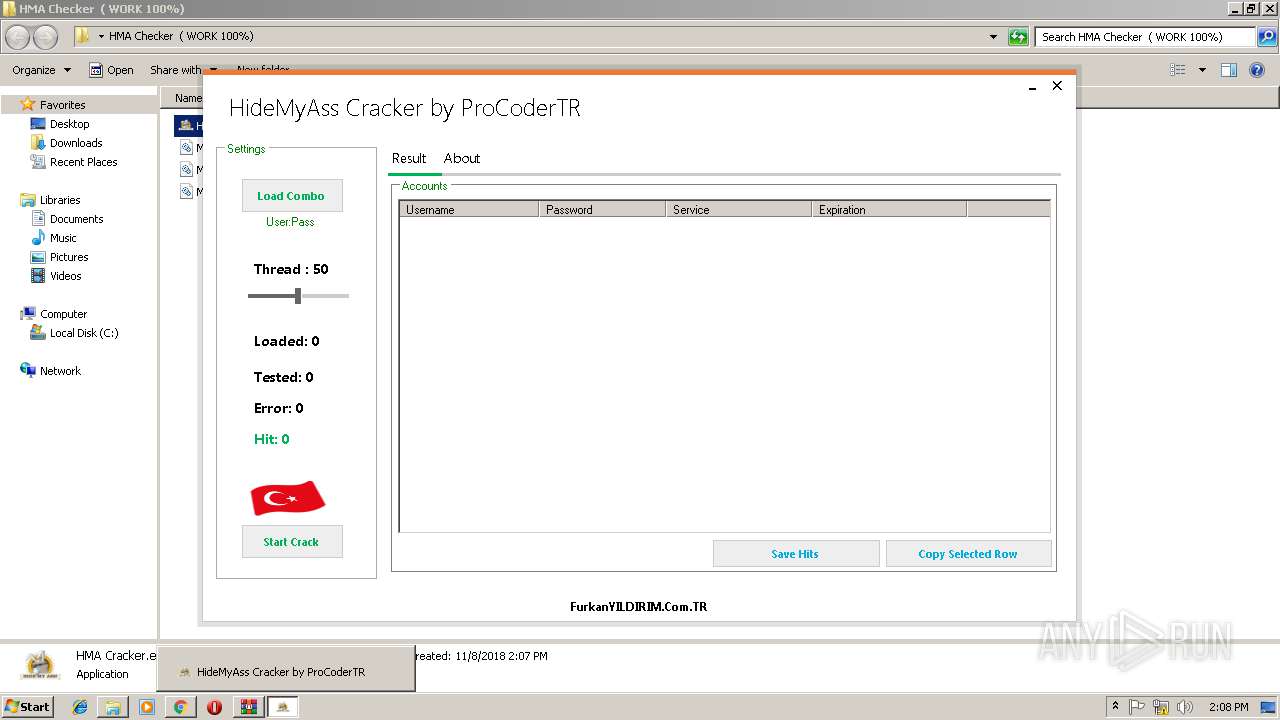
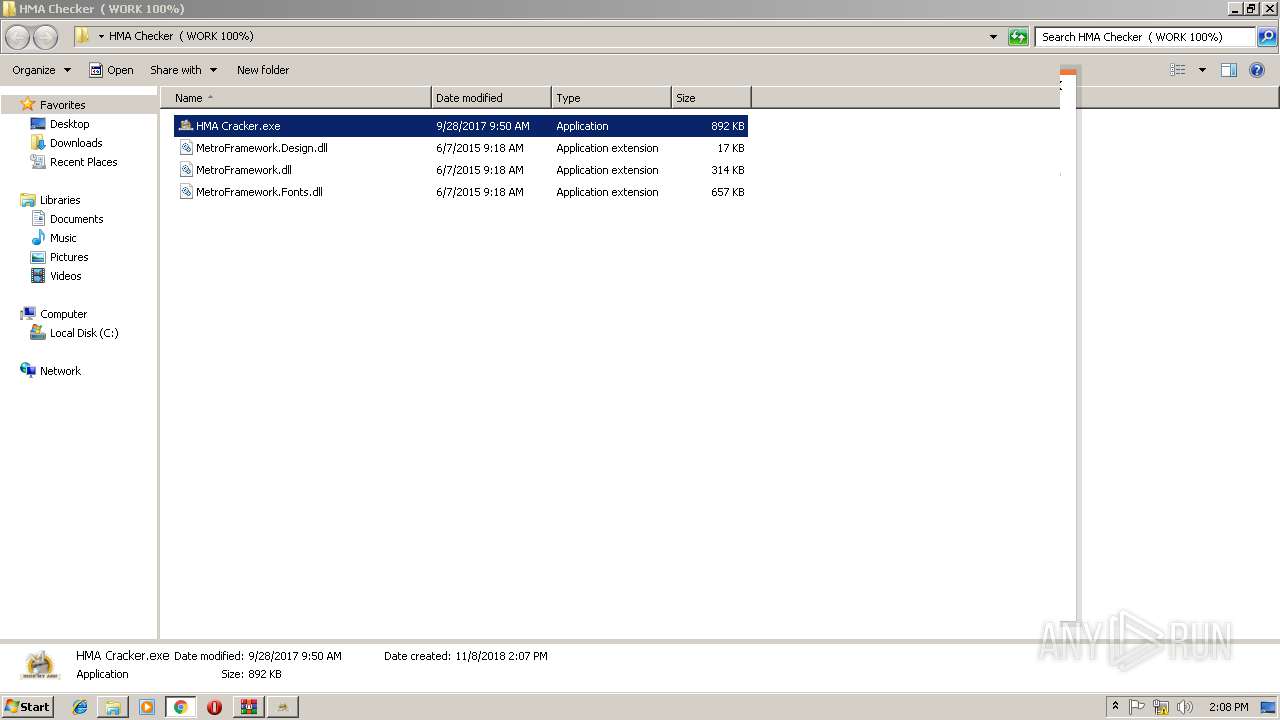
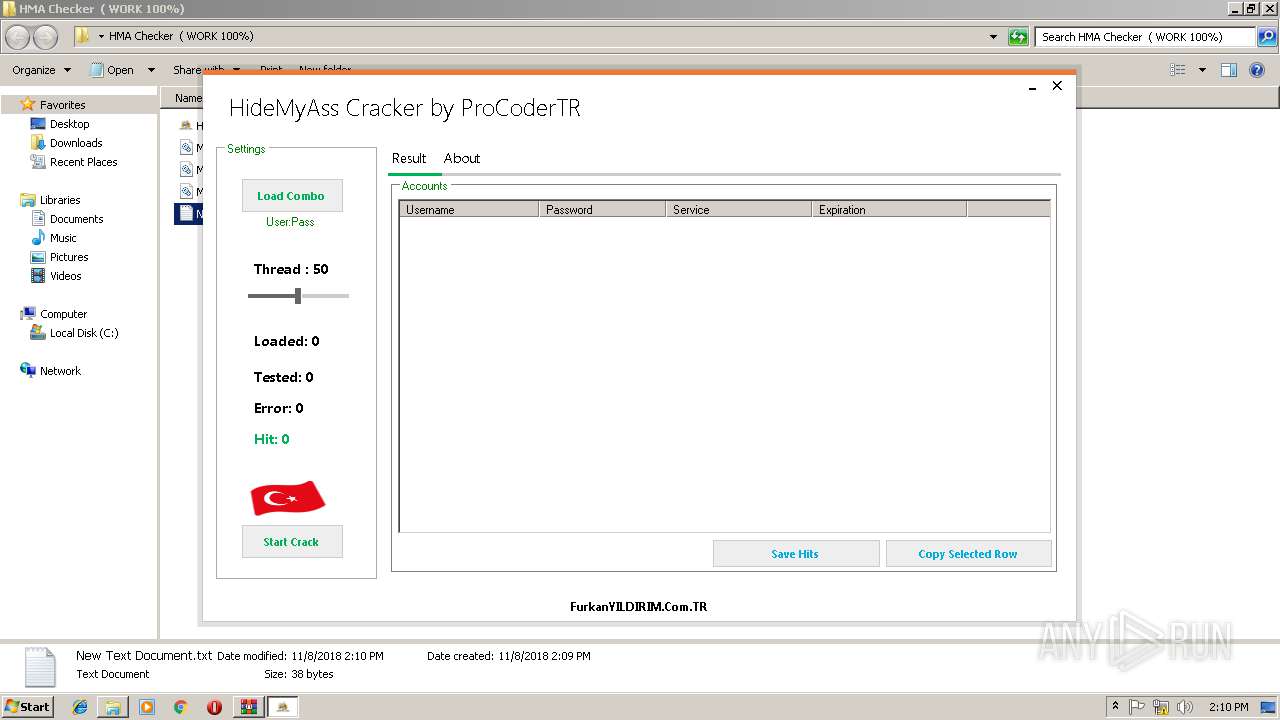
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.3560\HMA Checker ( WORK 100%)\HMA Cracker.exe | — | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.3560\HMA Checker ( WORK 100%)\MetroFramework.Design.dll | — | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.3560\HMA Checker ( WORK 100%)\MetroFramework.dll | — | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.3560\HMA Checker ( WORK 100%)\MetroFramework.Fonts.dll | — | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d16cb578-63ff-4af2-b5b4-6b7824f8764f.tmp | — | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9d027ba1-9fc3-459c-b606-58879587d7a3.tmp | — | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
47
DNS requests
34
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
408 | chrome.exe | GET | 200 | 104.17.167.186:80 | http://6.adsco.re/ | US | — | — | whitelisted |
408 | chrome.exe | GET | 200 | 185.200.118.90:80 | http://778d768745b823ff2bbe502057d41713.l.adsco.re/ | GB | — | — | malicious |
408 | chrome.exe | GET | 200 | 38.132.109.186:80 | http://l778d768745b823ff2bbe502057d41713.n.adsco.re/ | US | — | — | malicious |
408 | chrome.exe | GET | 200 | 185.200.118.90:80 | http://l778d768745b823ff2bbe502057d41713.l.adsco.re/ | GB | — | — | malicious |
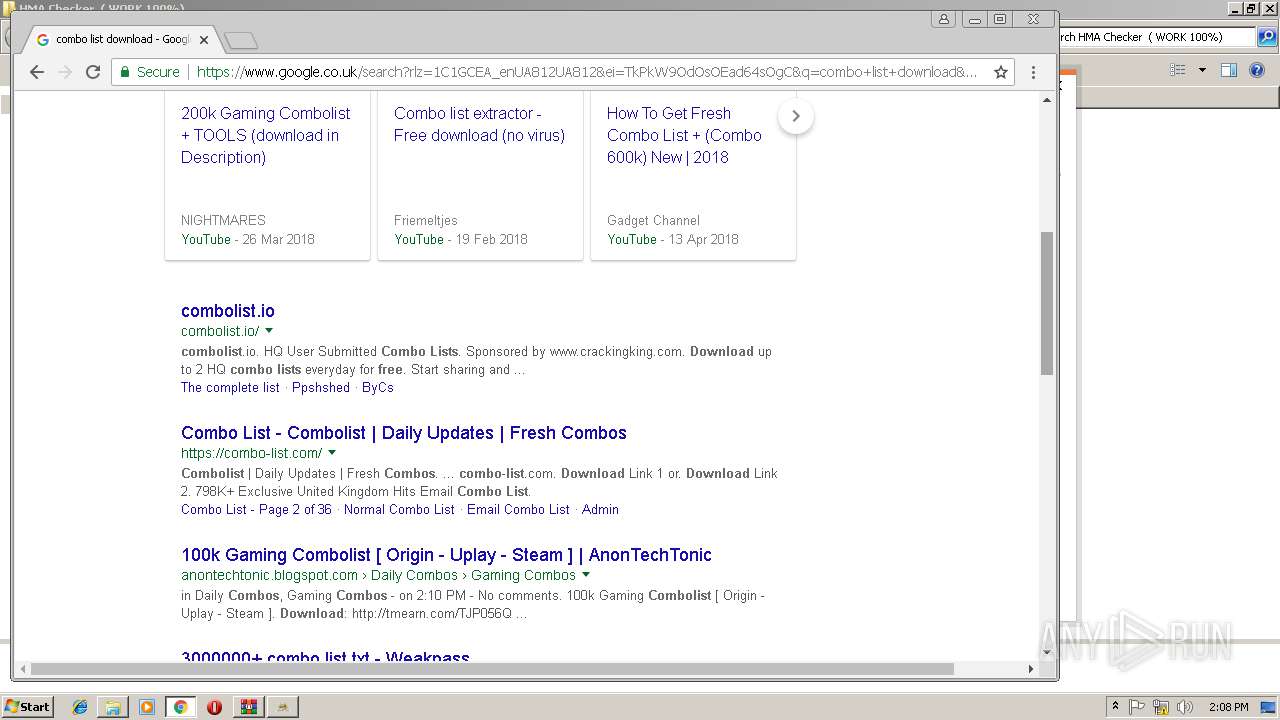
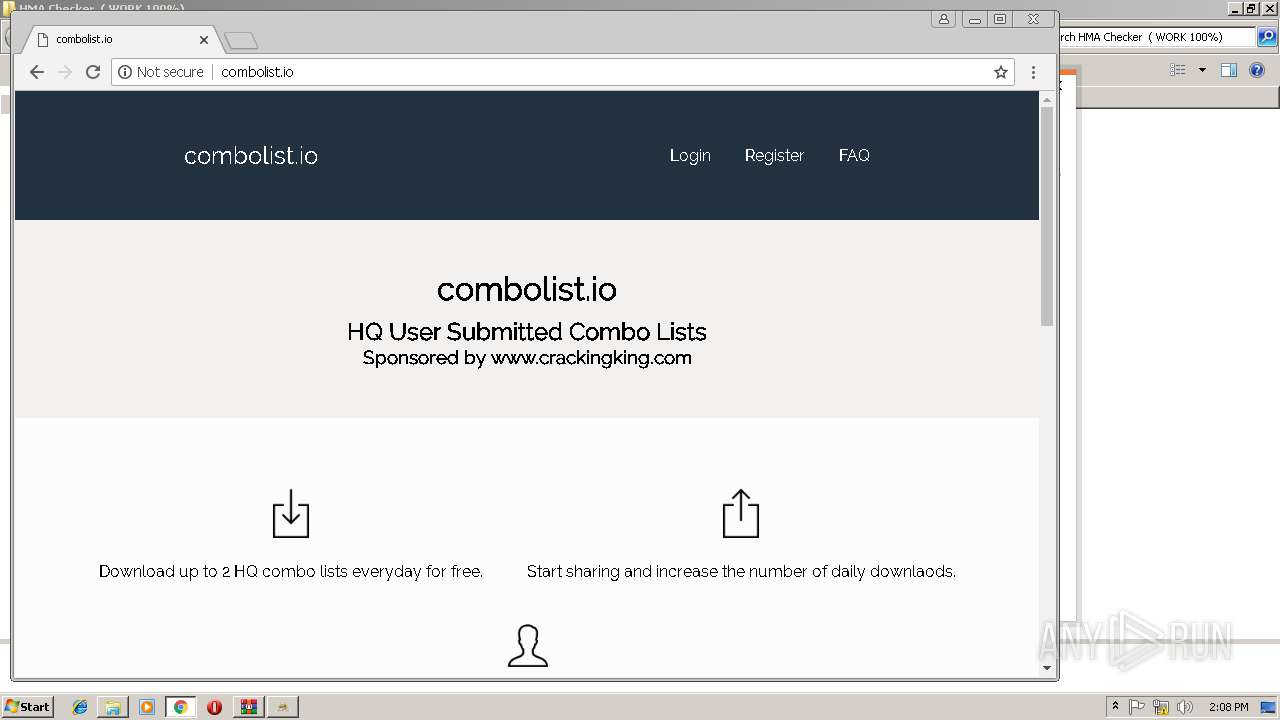
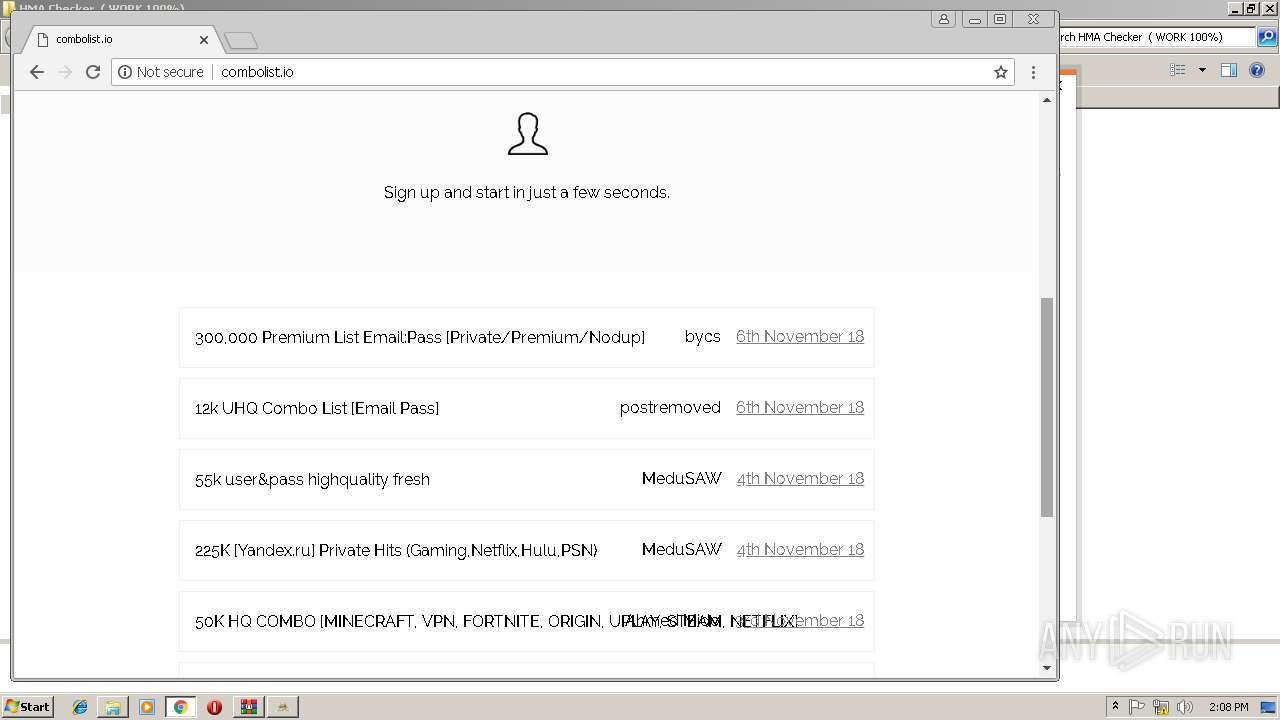
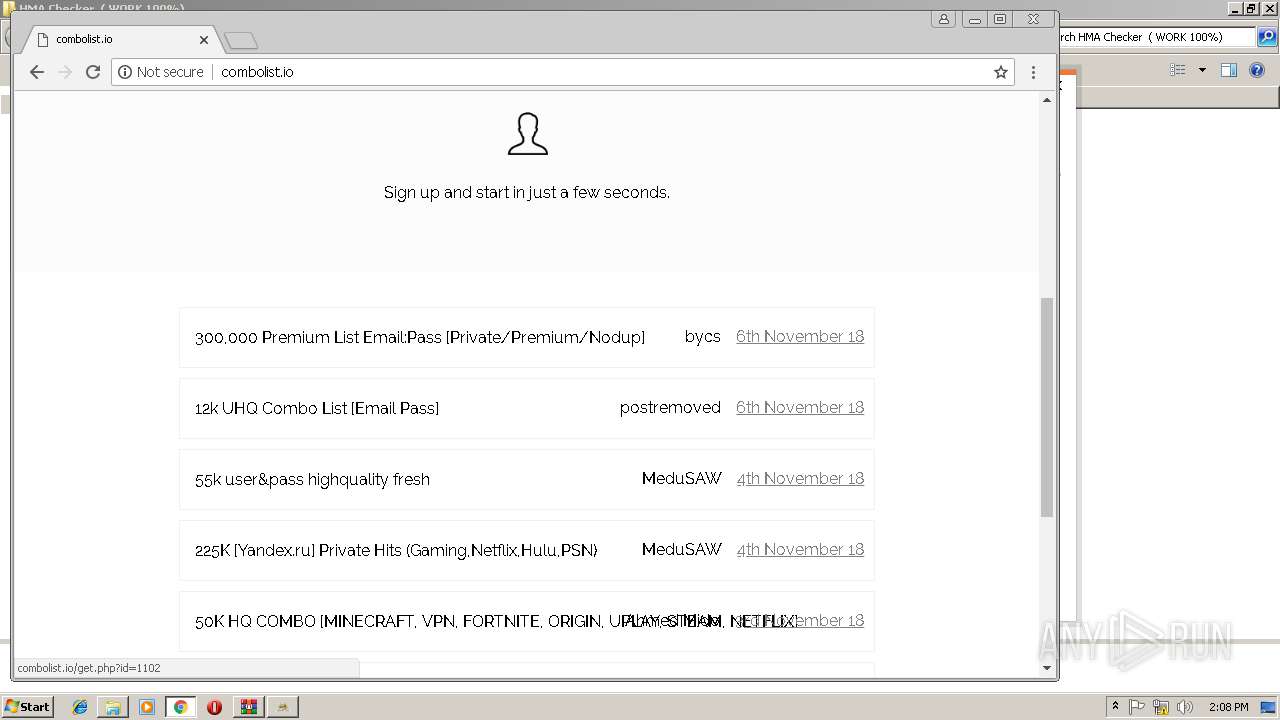
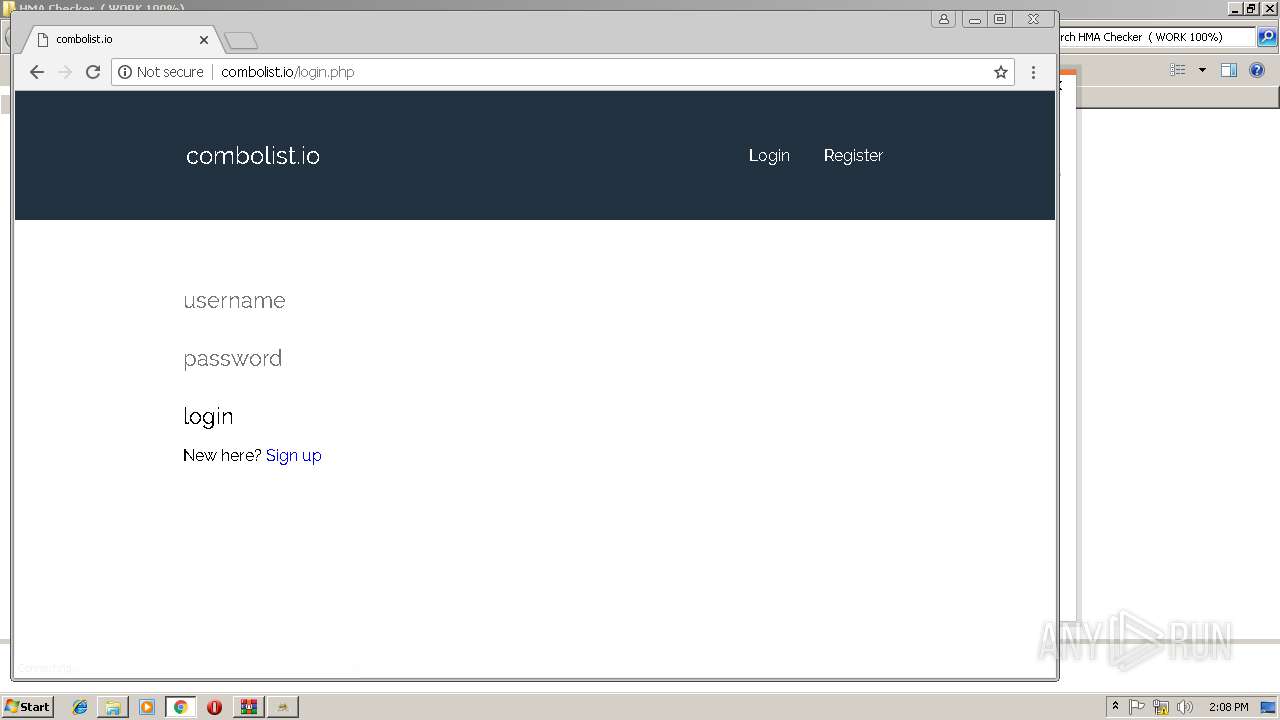
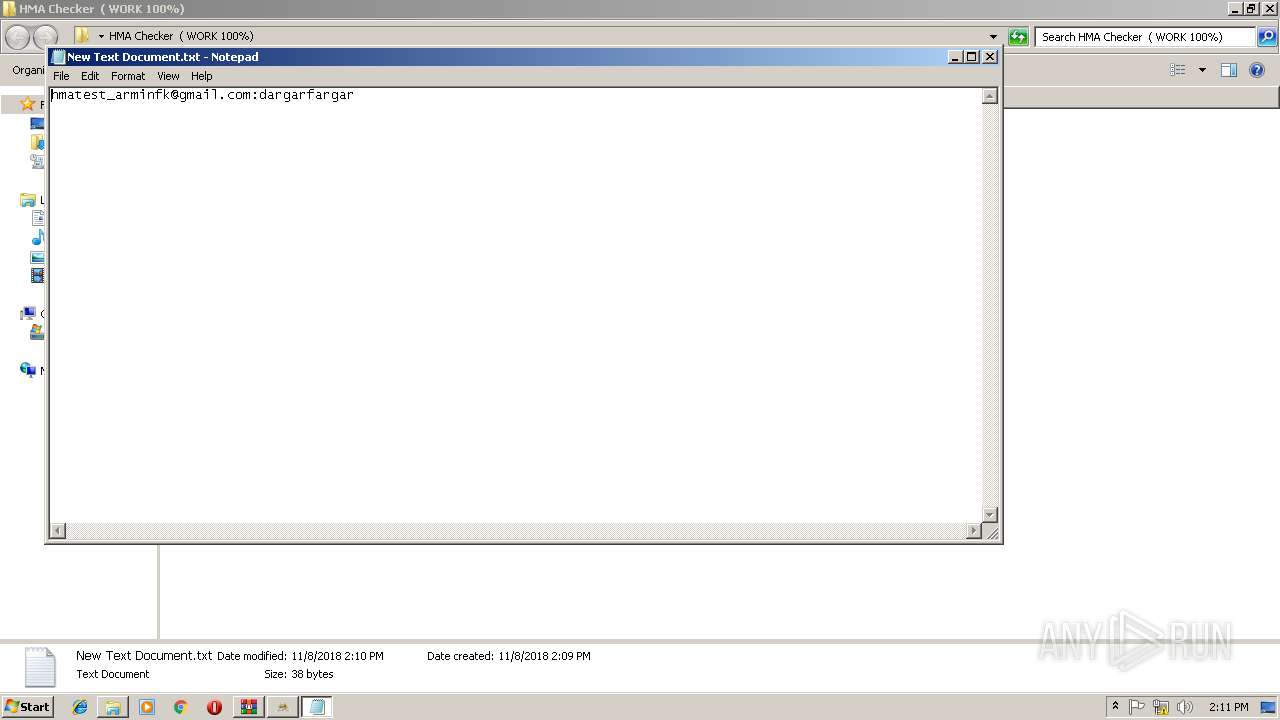
408 | chrome.exe | GET | 200 | 185.11.145.5:80 | http://combolist.io/ | NL | html | 1.74 Kb | malicious |
408 | chrome.exe | GET | 200 | 185.11.145.5:80 | http://combolist.io/ | NL | html | 5.78 Kb | malicious |
408 | chrome.exe | GET | 200 | 216.21.13.10:80 | http://serve.popads.net/c?r=1541686115&v=3&siteId=2905247&minBid=&popundersPerIP=&blockedCountries=&documentRef=http%3A%2F%2Fcombolist.io%2F&s=1280,720,1.01,1292.8,727.2 | US | text | 277 b | whitelisted |
408 | chrome.exe | GET | 200 | 195.181.174.9:80 | http://c1.popads.net/pop.js | DE | text | 27.6 Kb | whitelisted |
408 | chrome.exe | GET | 200 | 185.11.145.5:80 | http://combolist.io/___S___/?rid=5E1e4SiFrcssl9KicOITwGKmhgEoAlAx9BOy1eCKO2TuxbKzaEwiRfmvne9WYi2k&sid=1040&d=combolist.io&tz=1541686175.425 | NL | text | 5.51 Kb | malicious |
408 | chrome.exe | GET | 200 | 185.200.116.90:80 | http://l778d768745b823ff2bbe502057d41713.s.adsco.re/ | SG | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
408 | chrome.exe | 74.125.133.94:443 | www.google.co.uk | Google Inc. | US | whitelisted |
408 | chrome.exe | 172.217.168.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
408 | chrome.exe | 172.217.168.66:443 | adservice.google.co.uk | Google Inc. | US | whitelisted |
408 | chrome.exe | 185.11.145.5:80 | combolist.io | Dotsi, Unipessoal Lda. | NL | suspicious |
408 | chrome.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
408 | chrome.exe | 172.217.168.68:443 | www.google.com | Google Inc. | US | whitelisted |
408 | chrome.exe | 172.217.168.78:443 | apis.google.com | Google Inc. | US | whitelisted |
408 | chrome.exe | 195.181.174.9:80 | c1.popads.net | Datacamp Limited | DE | suspicious |
408 | chrome.exe | 216.21.13.10:80 | serve.popads.net | Total Uptime Technologies, LLC | US | suspicious |
408 | chrome.exe | 162.252.214.4:80 | adsco.re | Total Uptime Technologies, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
apis.google.com |
| whitelisted |
www.google.co.uk |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
408 | chrome.exe | Misc Attack | ET DROP Dshield Block Listed Source group 1 |