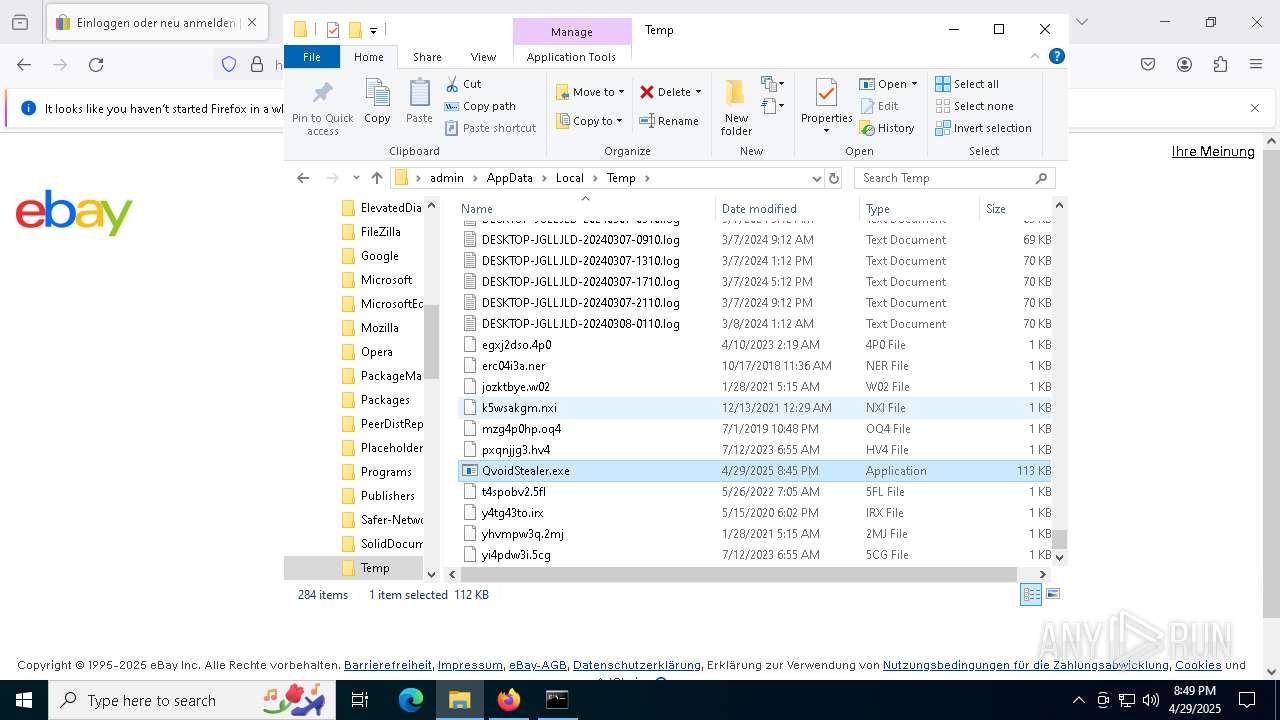
| File name: | QvoidStealer.exe |
| Full analysis: | https://app.any.run/tasks/1e25bf3b-75b0-46d7-aaf9-159965ed964f |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 20:45:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 3EC7AB0F4D9EB2CBE0F741BB2DDE09F6 |
| SHA1: | 7C285D5539CAD6B4E967609A3FFFAA4A6EC63E9D |
| SHA256: | A52B33C2572C422EC71D9814DE6223B9B54BD71F0FAD14C0DF3E86676FC913CC |
| SSDEEP: | 1536:CV9NdPptrAq88bibxyzyErLZZZYLX9YvMbpydGBVj8ThUkX0Z/Kvd:kyr2io1LZZZsXdb0oVj8ThUkXCq |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes application which crashes
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
- QvoidStealer.exe (PID: 5384)
- QvoidStealer.exe (PID: 7484)
INFO
Checks supported languages
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
Reads the computer name
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
Reads Environment values
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
Reads the machine GUID from the registry
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
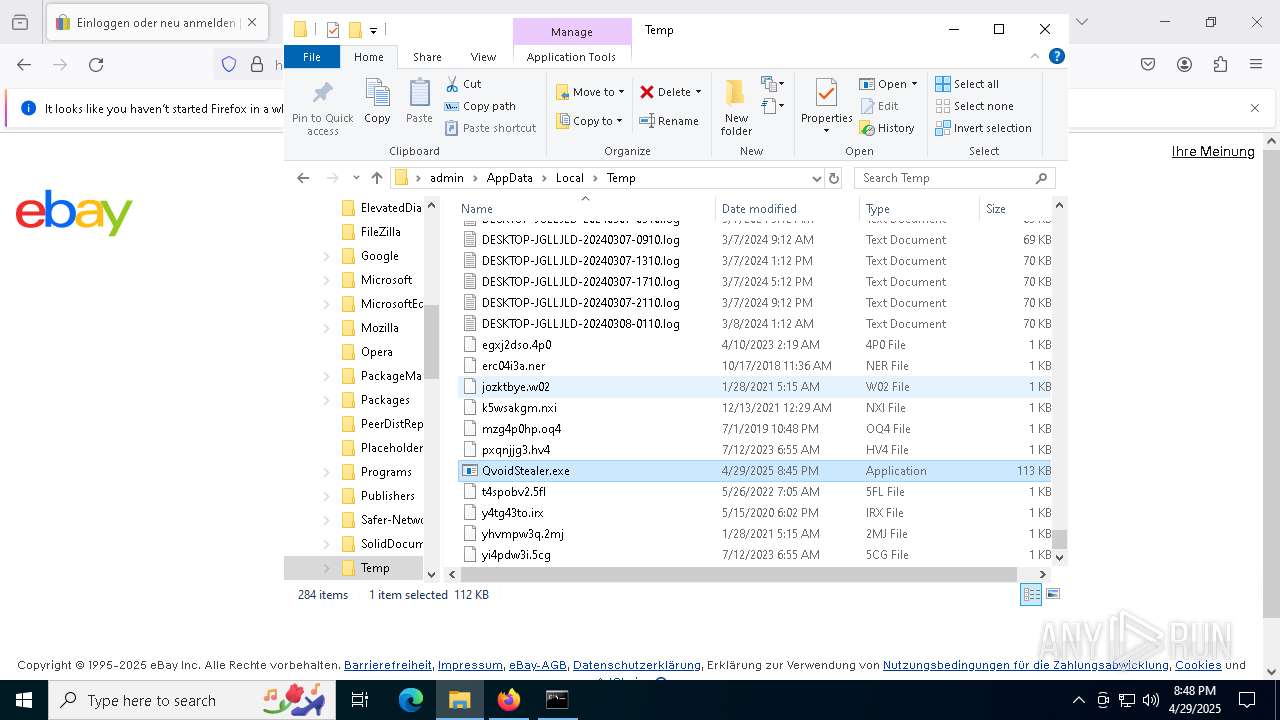
Create files in a temporary directory
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
Creates files or folders in the user directory
- WerFault.exe (PID: 5588)
- WerFault.exe (PID: 3180)
Attempting to use instant messaging service
- QvoidStealer.exe (PID: 6488)
- QvoidStealer.exe (PID: 1600)
Reads the software policy settings
- slui.exe (PID: 7052)
Manual execution by a user
- QvoidStealer.exe (PID: 1600)
- cmd.exe (PID: 3140)
- firefox.exe (PID: 4436)
- QvoidStealer.exe (PID: 5384)
- QvoidStealer.exe (PID: 7484)
Application launched itself
- firefox.exe (PID: 4436)
- firefox.exe (PID: 6028)
Connects to unusual port
- firefox.exe (PID: 6028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:29 20:36:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 112640 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d57e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | QvoidStealer.exe |
| LegalCopyright: | |
| OriginalFileName: | QvoidStealer.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
169
Monitored processes
32
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "C:\Users\admin\AppData\Local\Temp\QvoidStealer.exe" | C:\Users\admin\AppData\Local\Temp\QvoidStealer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6644 -childID 10 -isForBrowser -prefsHandle 6612 -prefMapHandle 6836 -prefsLen 31647 -prefMapSize 244583 -jsInitHandle 1480 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {88ea35b5-06ca-4a47-8916-2a6226ddfcb8} 6028 "\\.\pipe\gecko-crash-server-pipe.6028" 2a03b291150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5144 -childID 4 -isForBrowser -prefsHandle 5152 -prefMapHandle 5156 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1480 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1724bacb-ec75-459a-87a9-92472f82d2d8} 6028 "\\.\pipe\gecko-crash-server-pipe.6028" 2a0382a8d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5096 -childID 3 -isForBrowser -prefsHandle 5088 -prefMapHandle 4604 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1480 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {15338136-0c3c-4a99-991b-1c86eedc529a} 6028 "\\.\pipe\gecko-crash-server-pipe.6028" 2a0382a8bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2172 -parentBuildID 20240213221259 -prefsHandle 2164 -prefMapHandle 2152 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {806fe235-c147-4857-95c2-e947e5e3d657} 6028 "\\.\pipe\gecko-crash-server-pipe.6028" 2a021c82710 socket | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3140 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | C:\WINDOWS\system32\WerFault.exe -u -p 1600 -s 1740 | C:\Windows\System32\WerFault.exe | — | QvoidStealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4376 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4200 -childID 2 -isForBrowser -prefsHandle 4216 -prefMapHandle 4212 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1480 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f9b244fe-3b16-4d0d-ba1b-85c9e1df4a95} 6028 "\\.\pipe\gecko-crash-server-pipe.6028" 2a035c0da10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4436 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
31 796
Read events
31 795
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6028) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
Executable files
0
Suspicious files
258
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5588 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_QvoidStealer.exe_c520b4fb65f785377ebcf68dabf8f7df239b23a6_06315cfb_32121b9c-39b9-4b1e-a971-c4711a33e697\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5588 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\QvoidStealer.exe.6488.dmp | — | |
MD5:— | SHA256:— | |||
| 3180 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_QvoidStealer.exe_c520b4fb65f785377ebcf68dabf8f7df239b23a6_06315cfb_1faf64d3-1046-4600-a55f-e41d3633eb7e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 3180 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\QvoidStealer.exe.1600.dmp | — | |
MD5:— | SHA256:— | |||
| 6028 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5588 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC9BA.tmp.dmp | binary | |
MD5:A369FFC571CBA6FB57F1DAE3759250F8 | SHA256:3F0E0C11F39855EBC4278478DC11000940C1D321529148B8DB50A7E76C60D5AC | |||
| 3180 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER7E11.tmp.dmp | binary | |
MD5:C0894074F37394472657659B32A64CC7 | SHA256:BC3CA8B2800B803AB89368A8ED898554AC594FD195D9B93ED9BA94288AE565FF | |||
| 6028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5588 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCBCF.tmp.WERInternalMetadata.xml | binary | |
MD5:5B68114635F634A8D455E610008A0BDE | SHA256:508750AE8464BF7F27F6C17BC1B027A221CA48D81AE8BC6E180E2C028B6E88AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
214
DNS requests
260
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4560 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4560 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6028 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6028 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6028 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6488 | QvoidStealer.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6488 | QvoidStealer.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1600 | QvoidStealer.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
5384 | QvoidStealer.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7484 | QvoidStealer.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |