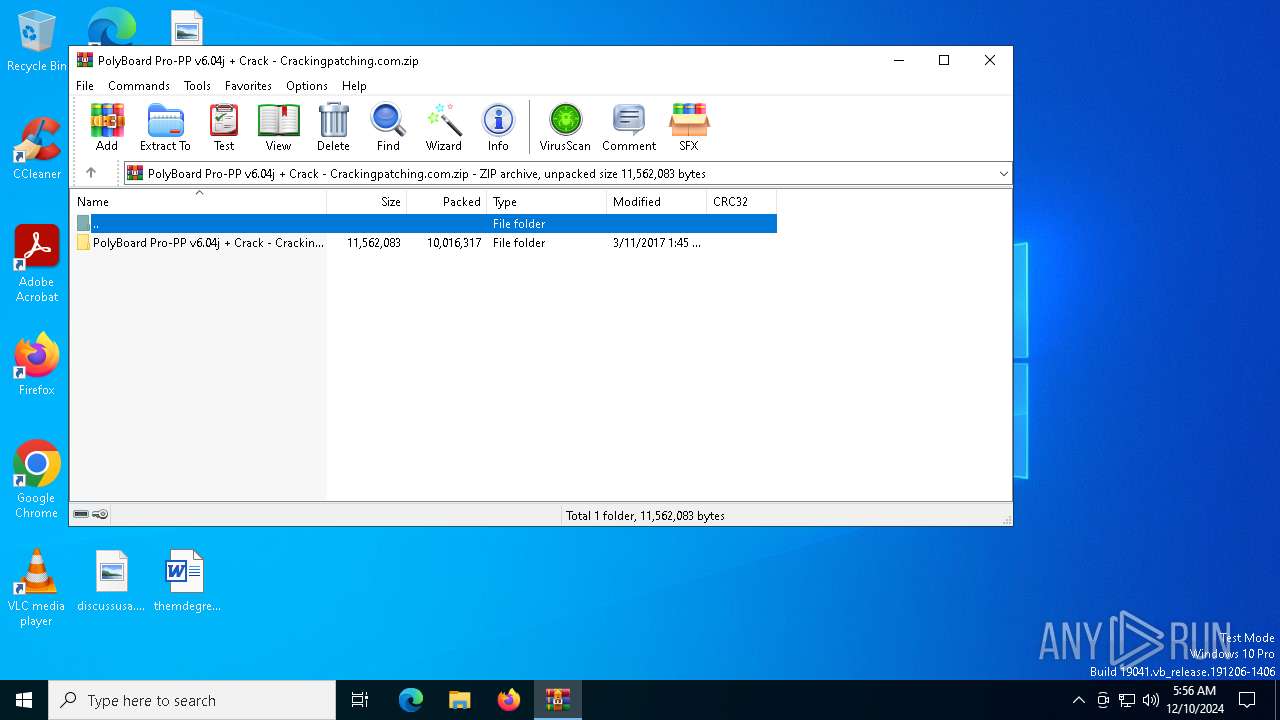
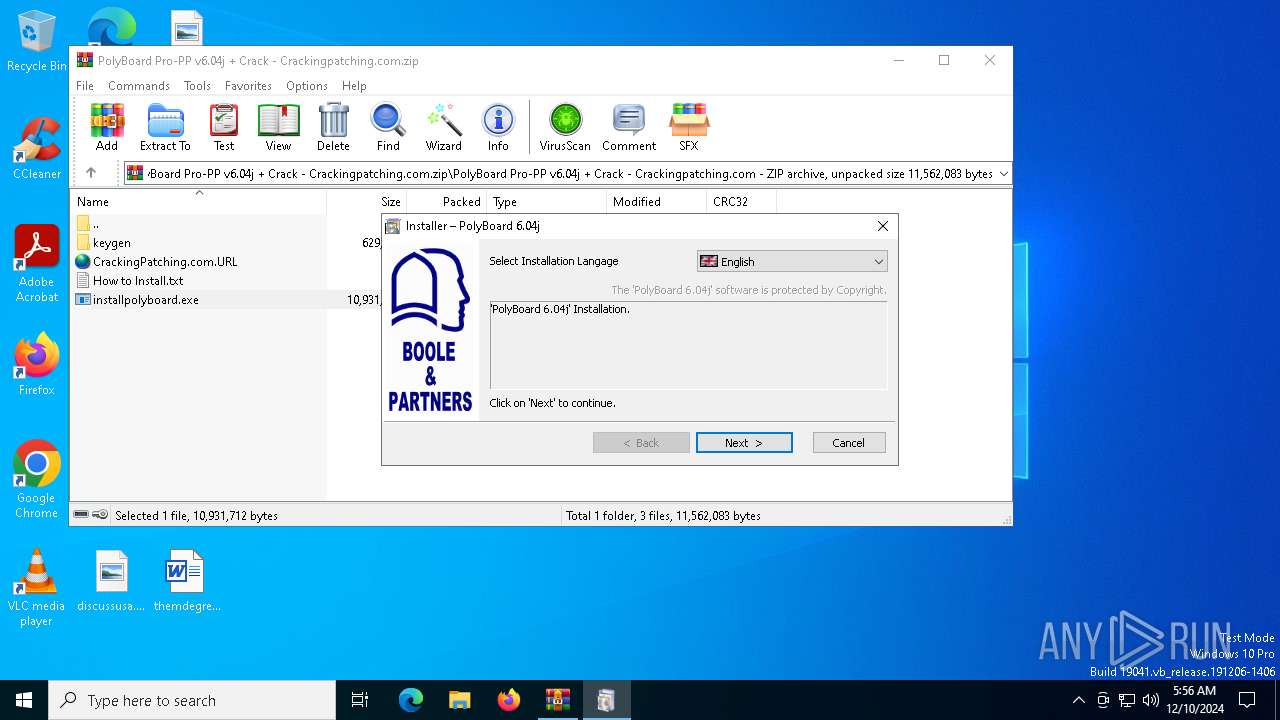
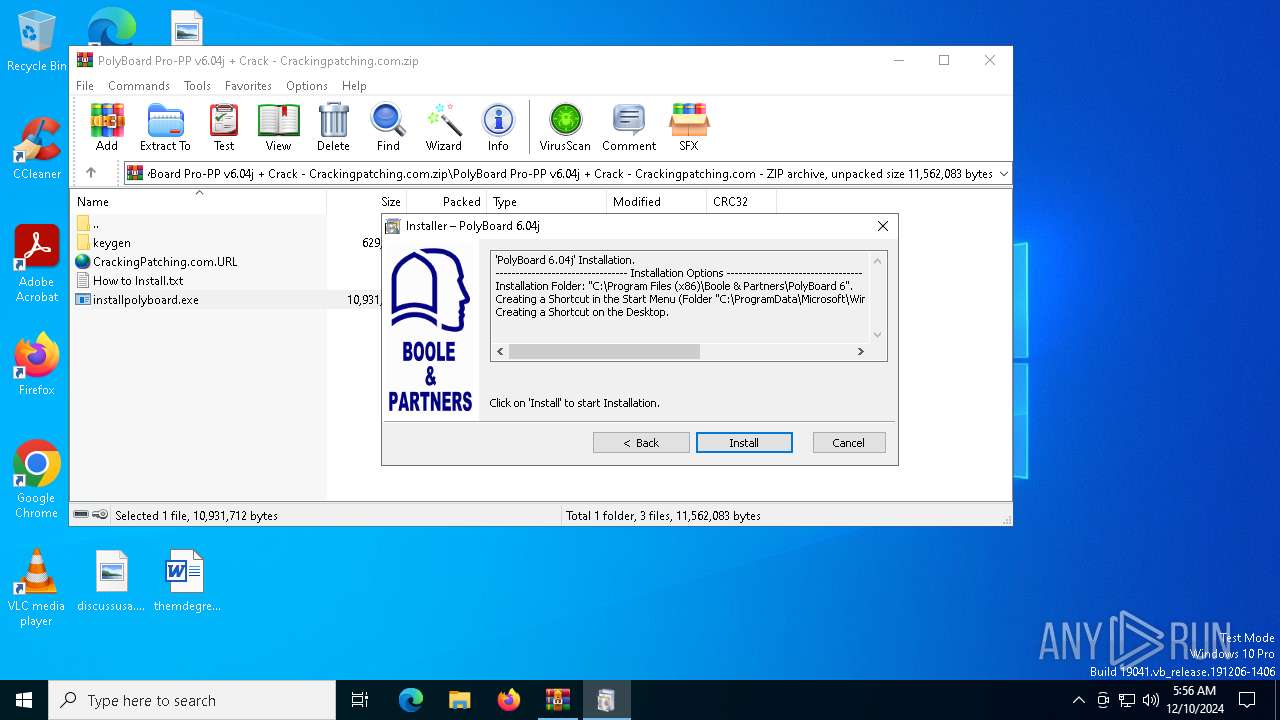
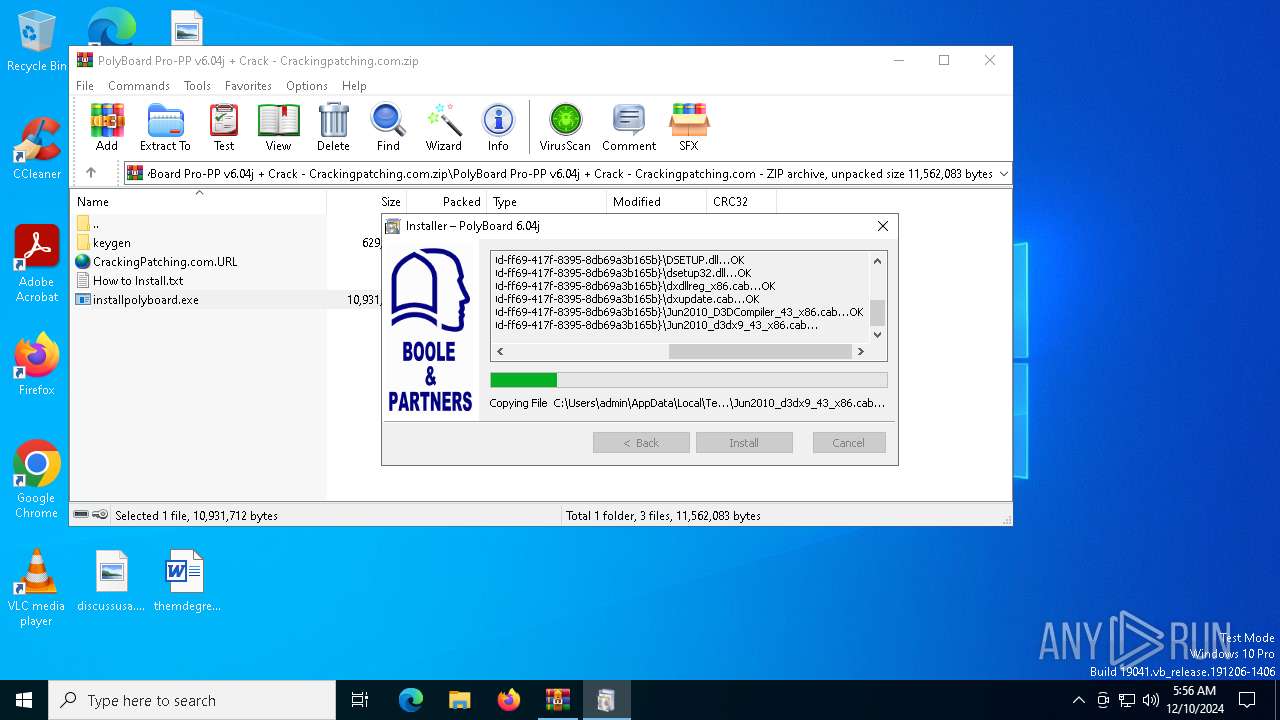
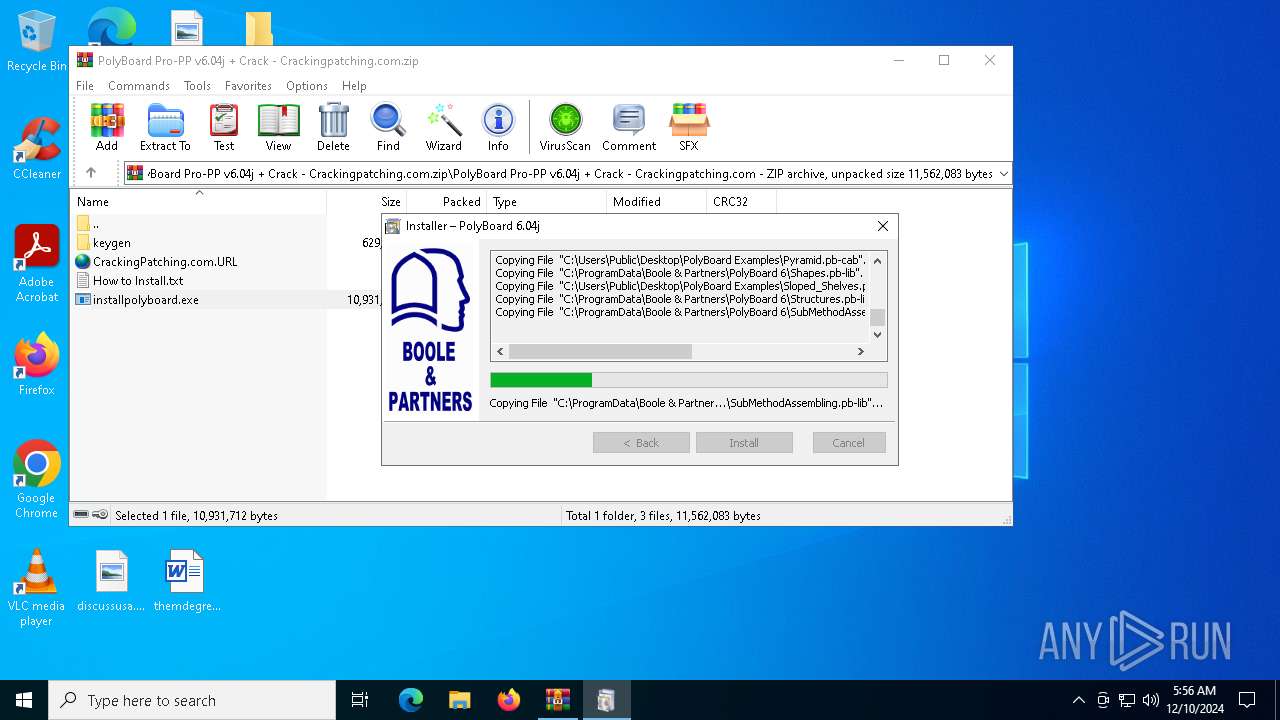
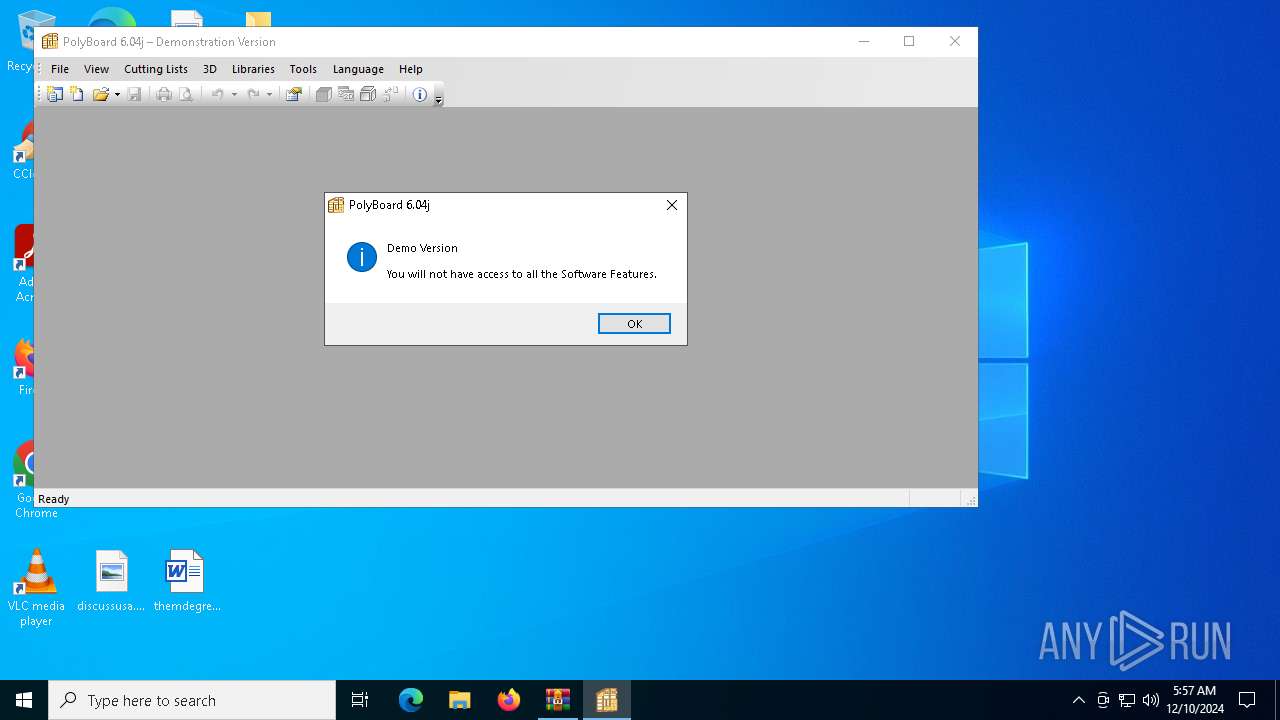
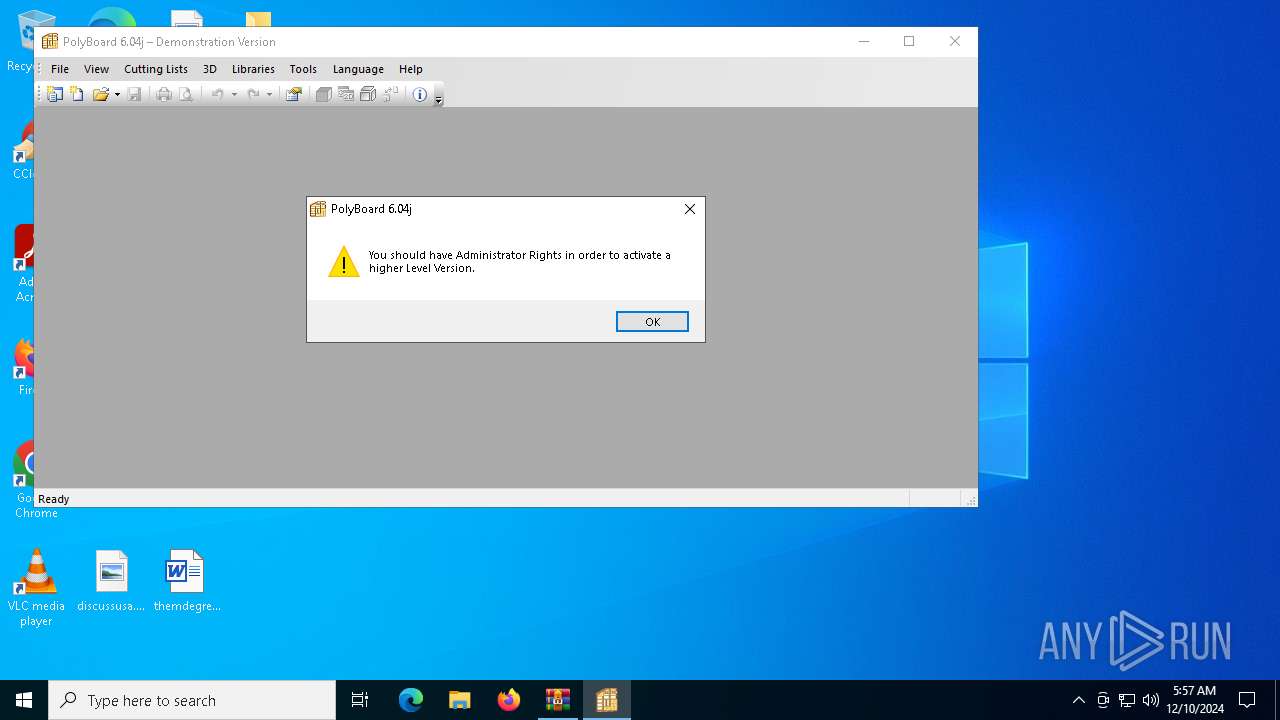
| File name: | PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com.zip |
| Full analysis: | https://app.any.run/tasks/175a19da-1d1d-4a5e-a937-d7c8dd79fd5d |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 05:56:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 607D1C28D4F92293207C764B850001D2 |
| SHA1: | 65593E15F5D4279F4FE2BE8B2C4D43CDA751BA9A |
| SHA256: | A52A59A1480DA1ACF0CFA8268831F99CF4F7CEE2A15FED6B957F3D13064D6E17 |
| SSDEEP: | 98304:YUlQtgZrJ68V6QFZnF10fr3SC4Tb1oZf+lmtvtX21kl0dKuHwdWtdnlqqdPoQs4O:yzsMMvgror2W9SDSLdqdhP |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6564)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6564)
- installpolyboard.exe (PID: 6908)
Process drops legitimate windows executable
- installpolyboard.exe (PID: 6908)
Executable content was dropped or overwritten
- installpolyboard.exe (PID: 6908)
Executes as Windows Service
- VSSVC.exe (PID: 7036)
Searches for installed software
- dllhost.exe (PID: 6992)
- Polyboard.exe (PID: 5092)
- Polyboard.exe (PID: 6296)
Creates a software uninstall entry
- installpolyboard.exe (PID: 6908)
Checks Windows Trust Settings
- installpolyboard.exe (PID: 6908)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6564)
The process uses the downloaded file
- WinRAR.exe (PID: 6564)
Creates files in the program directory
- installpolyboard.exe (PID: 6908)
Reads the computer name
- installpolyboard.exe (PID: 6908)
Checks supported languages
- installpolyboard.exe (PID: 6908)
- Polyboard.exe (PID: 6296)
- Polyboard.exe (PID: 5092)
Create files in a temporary directory
- installpolyboard.exe (PID: 6908)
- Polyboard.exe (PID: 5092)
Sends debugging messages
- installpolyboard.exe (PID: 6908)
Manages system restore points
- SrTasks.exe (PID: 6304)
Reads the machine GUID from the registry
- installpolyboard.exe (PID: 6908)
Reads the software policy settings
- installpolyboard.exe (PID: 6908)
Manual execution by a user
- Polyboard.exe (PID: 5092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:03:11 13:45:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com/ |
Total processes
128
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5092 | "C:\Program Files (x86)\Boole & Partners\PolyBoard 6\Polyboard.exe" | C:\Program Files (x86)\Boole & Partners\PolyBoard 6\Polyboard.exe | — | explorer.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: MEDIUM Description: PolyBoard Version: 6.4.10.1 Modules
| |||||||||||||||
| 6296 | "C:\Program Files (x86)\Boole & Partners\PolyBoard 6\Polyboard.exe" /Register /Background | C:\Program Files (x86)\Boole & Partners\PolyBoard 6\Polyboard.exe | — | installpolyboard.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: HIGH Description: PolyBoard Exit code: 4294967286 Version: 6.4.10.1 Modules
| |||||||||||||||
| 6304 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
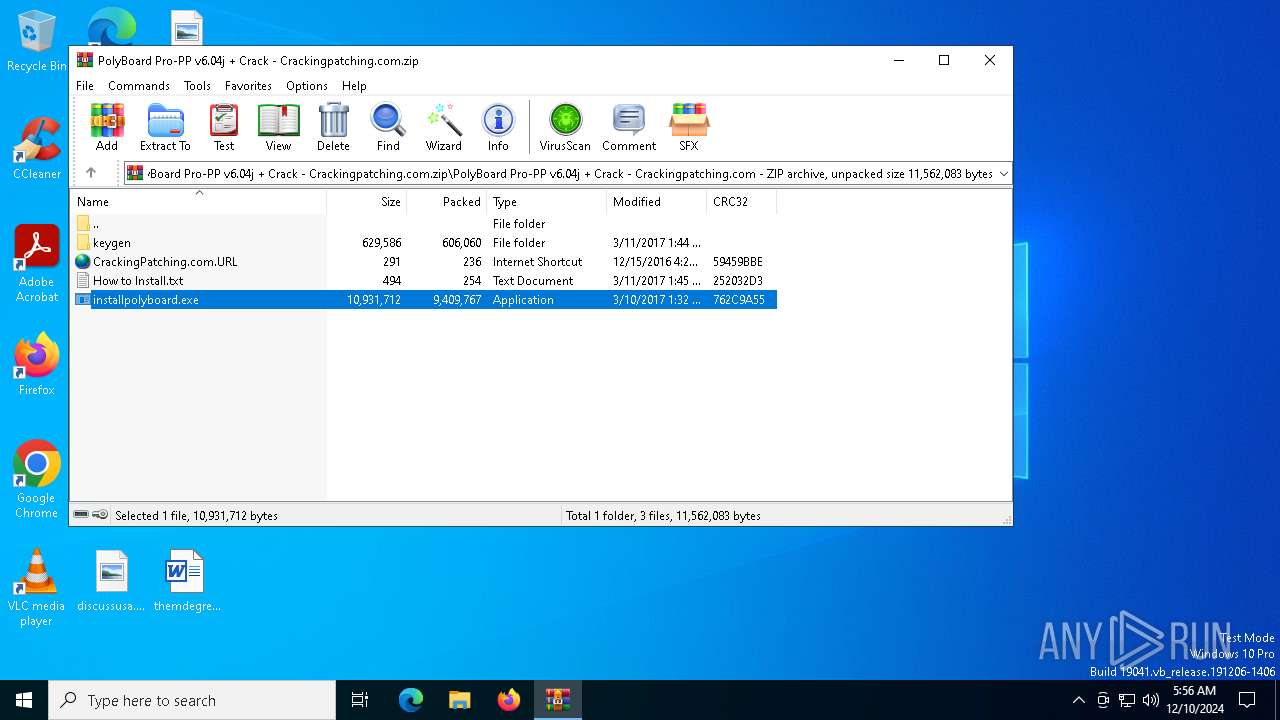
| 6856 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\installpolyboard.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\installpolyboard.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Boole & Partners Integrity Level: MEDIUM Description: Installeur PolyBoard 6.04j Exit code: 3221226540 Version: 2.2.0.3 Modules
| |||||||||||||||
| 6908 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\installpolyboard.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\installpolyboard.exe | WinRAR.exe | ||||||||||||
User: admin Company: Boole & Partners Integrity Level: HIGH Description: Installeur PolyBoard 6.04j Exit code: 0 Version: 2.2.0.3 Modules
| |||||||||||||||
| 6992 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 764
Read events
7 540
Write events
205
Delete events
19
Modification events
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com.zip | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6908) installpolyboard.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000A676A851C84ADB01FC1A0000001B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6992) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000A676A851C84ADB01501B0000681B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
23
Suspicious files
52
Text files
23
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6908 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{85e2170d-ff69-417f-8395-8db69a3b165b}\dsetup32.dll | executable | |
MD5:0F58CCD58A29827B5D406874360E4C08 | SHA256:642D9E7DB6D4FC15129F011DCE2EA087BF7F7FB015AECECF82BF84FF6634A6FB | |||
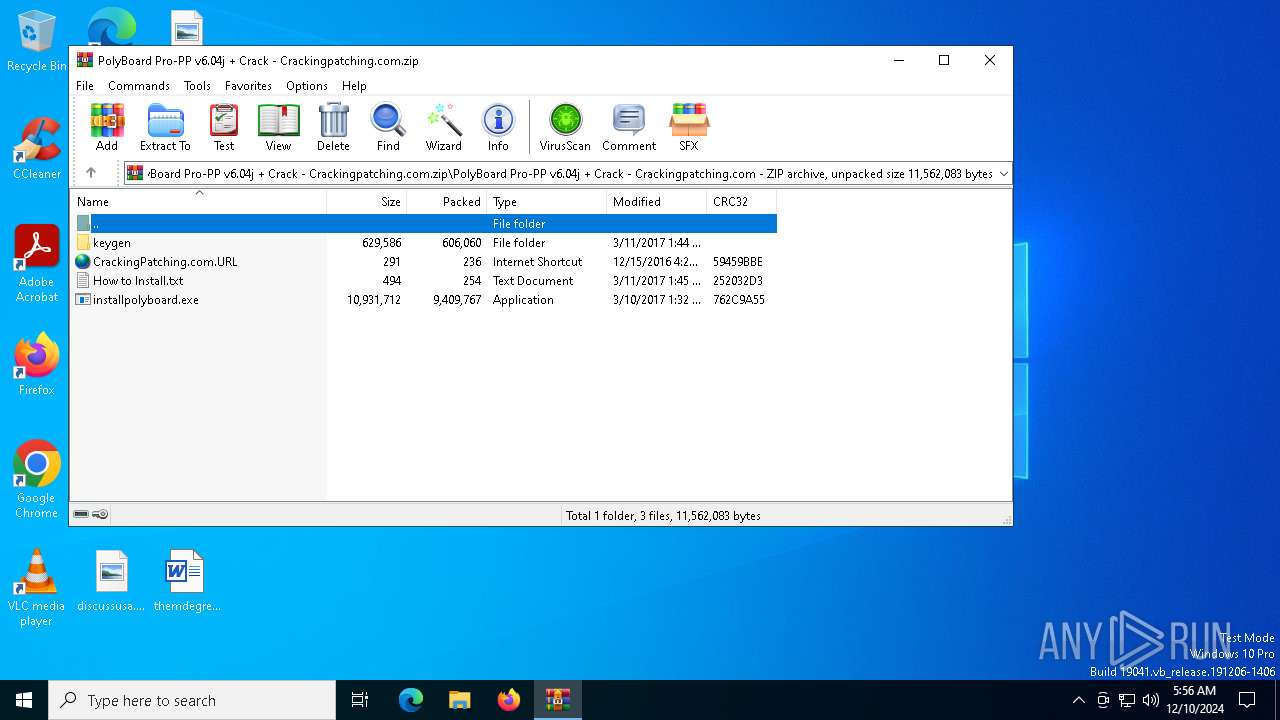
| 6564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\How to Install.txt | text | |
MD5:15DD92ECBC9722045DD3A2756A131337 | SHA256:99FE03F4B0380003A37B0E6B96AFD881EFFE18A79D09C211F86C52D01D6F28F6 | |||
| 6564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\CrackingPatching.com.URL | url | |
MD5:043D08A000F20571B004F1B52A4DA7D7 | SHA256:09DBC34577A8D55FCBE8A4D4759E327574BDEAF1DF7629A3CA50AAC26FBAF07D | |||
| 6564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6564.1258\PolyBoard Pro-PP v6.04j + Crack - Crackingpatching.com\keygen\file_id.diz | text | |
MD5:D3ADB6855B5F70300FCF20F5F8DBD148 | SHA256:7157C0BD33D71A241BACE9A6C79689E99B26BA4F4F98A647755438050E4BB29A | |||
| 6908 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{85e2170d-ff69-417f-8395-8db69a3b165b}\dxdllreg_x86.cab | compressed | |
MD5:A025C67403DC2C2BCD709AA9435FAEB1 | SHA256:8AD77A4D9C76F65CD62337588F847CC1E0CA6CA9735937F3A781F7395E9566A1 | |||
| 6908 | installpolyboard.exe | C:\Windows\INF\sdatabl.sav.bin | binary | |
MD5:373FA1A0BD8CFDEA6637DDE9F3EA8945 | SHA256:ACF6EEB11FB88C7A760631B4ABE6B2A98804F8A93A63549DD7520EA8F7548553 | |||
| 6908 | installpolyboard.exe | C:\Users\Public\Desktop\PolyBoard Examples\3_Drawers.pb-cab | binary | |
MD5:55FF67ED18F4F45DB878BA953449CE87 | SHA256:42250E4C71E0F58407CCCFD9A028913397C30F09D65A97BECC437594BCFD229A | |||
| 6908 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{85e2170d-ff69-417f-8395-8db69a3b165b}\Jun2010_D3DCompiler_43_x86.cab | compressed | |
MD5:F7F554AA613ECCF065575B8C69717EF7 | SHA256:417EEBD5B19F45C67C94C2D2BA8B774C0FC6D958B896D7B1AC12CF5A0EA06E0E | |||
| 6908 | installpolyboard.exe | C:\Users\admin\AppData\Local\Temp\boole_{85e2170d-ff69-417f-8395-8db69a3b165b}\dxupdate.cab | compressed | |
MD5:8ADF5A3C4BD187052BFA92B34220F4E7 | SHA256:13393A91201E69E70A9F68D21428453FFF3951535DEC88F879270269CFE54D6F | |||
| 6908 | installpolyboard.exe | C:\ProgramData\Boole & Partners\Textures\PolyBoard 6\Acajou1.jpg | image | |
MD5:3190489426186C331135CC3086DA1750 | SHA256:14CB474AC44B8C1C1E6E1B35B7459B8858D52906087C414F2EFC62412E306F2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3984 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3984 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6908 | installpolyboard.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
4716 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5892 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.209.177:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
installpolyboard.exe | DLL_PROCESS_ATTACH |
installpolyboard.exe | DLL_PROCESS_ATTACH |
installpolyboard.exe | DLL_PROCESS_DETACH |
installpolyboard.exe | DLL_PROCESS_DETACH |