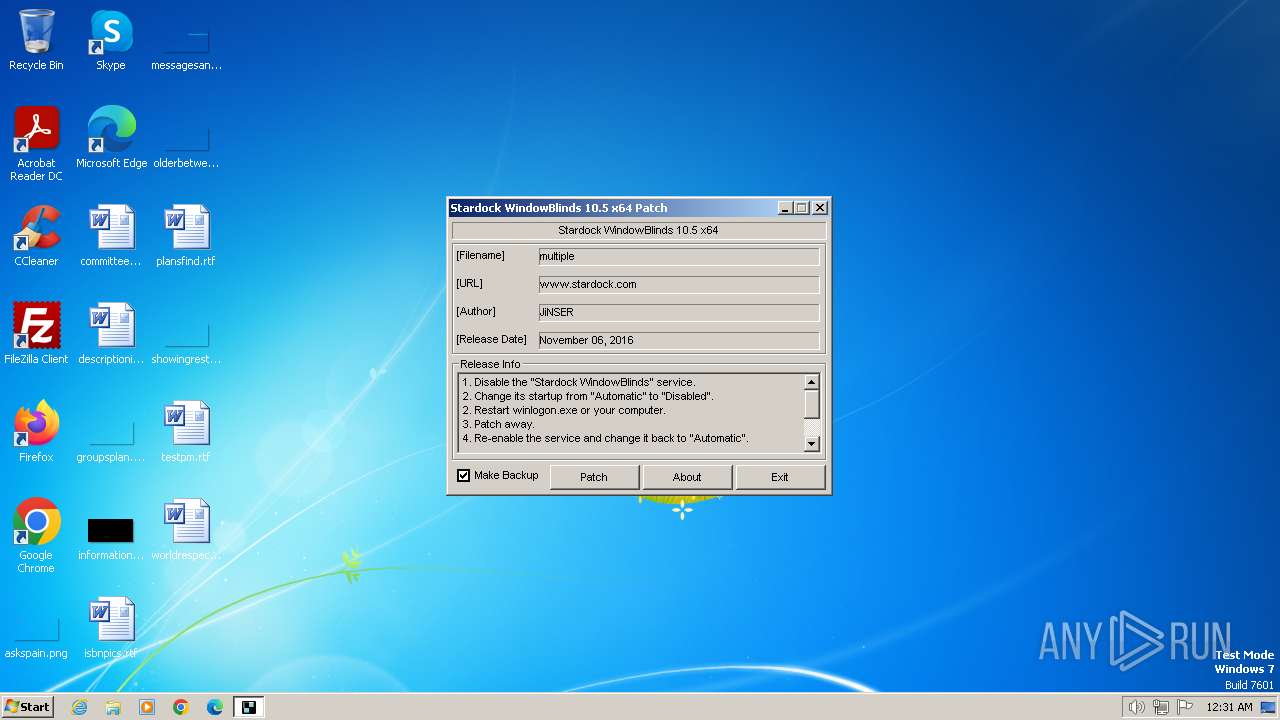
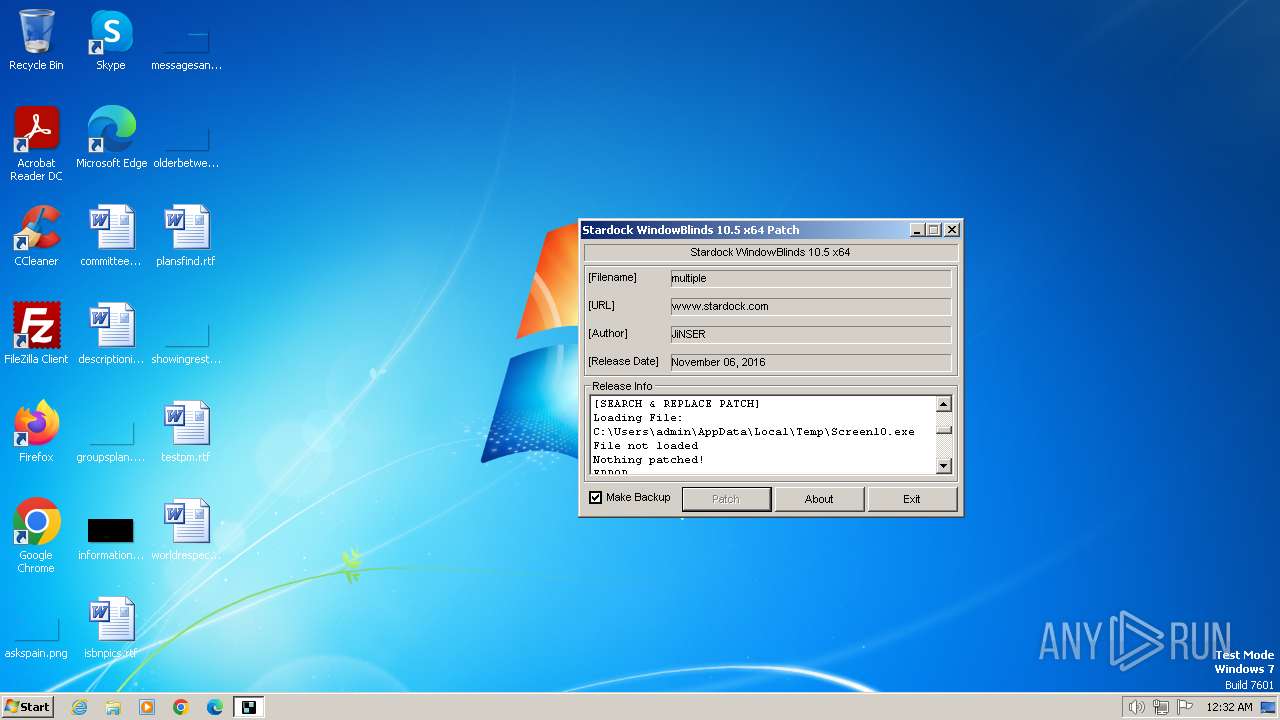
| File name: | patch.exe |
| Full analysis: | https://app.any.run/tasks/3994c681-9d2b-48d0-8238-7b24d337ed48 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2024, 00:31:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6516B21815EAE243574C8172C2B0694B |
| SHA1: | 1FE04166B44304818EA7B1930200F2065ABF149B |
| SHA256: | A526B245BA2E5C72EE0A6F34DEC44BD8C282EFE1D6E8C03BB45EACDB8DB0766C |
| SSDEEP: | 6144:zQmj3TFd3SvM+xQAyPlSxUZ+xtuYsyo8yDHMQIE:zQmjpRSvMUQHE5tuYsj8NPE |
MALICIOUS
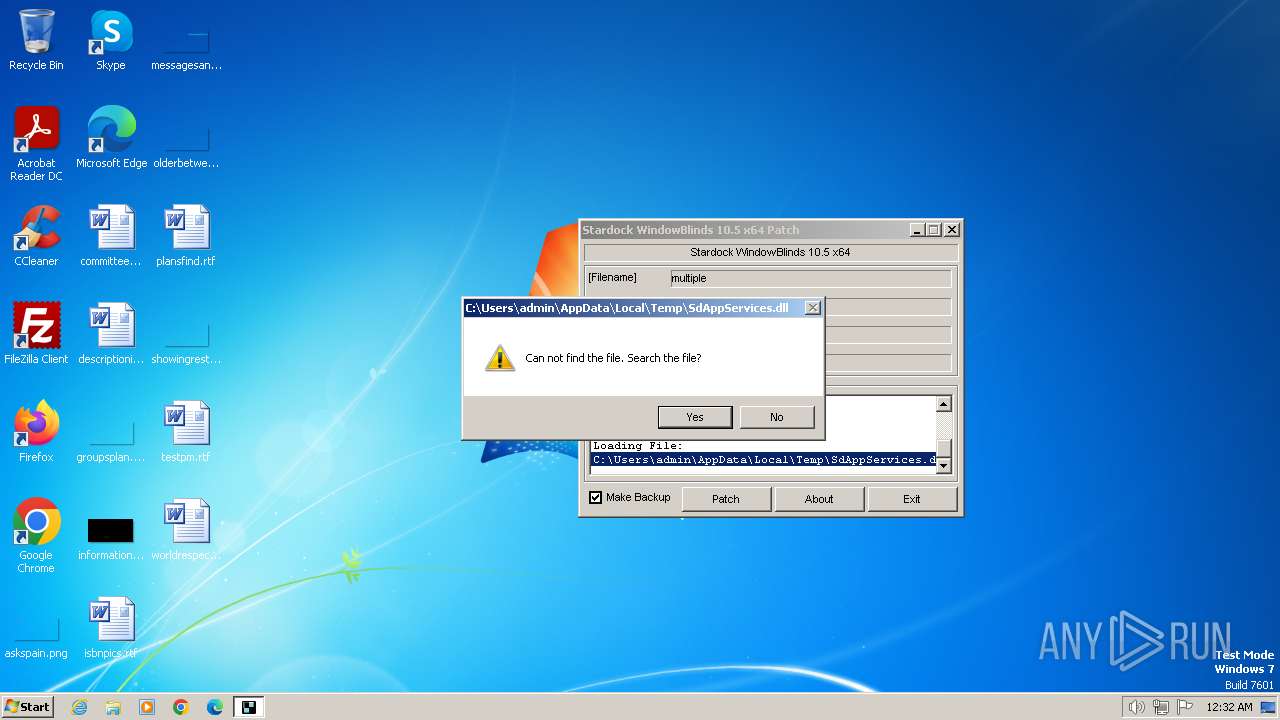
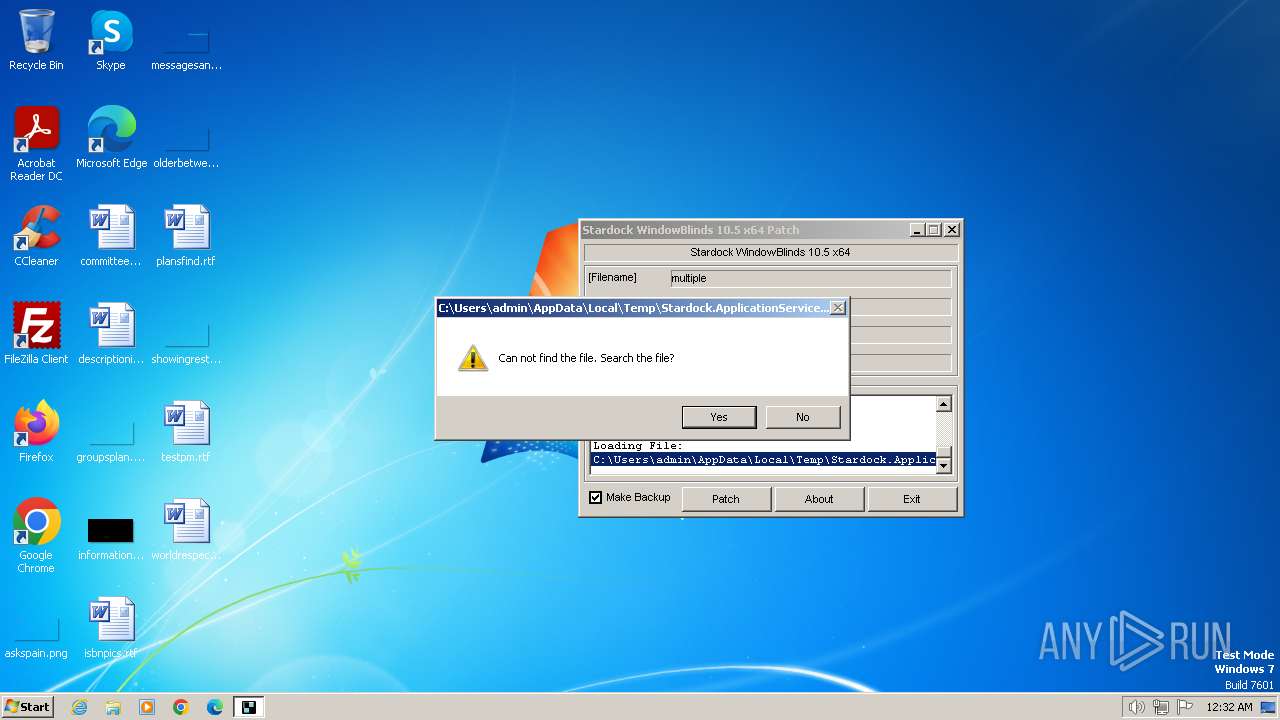
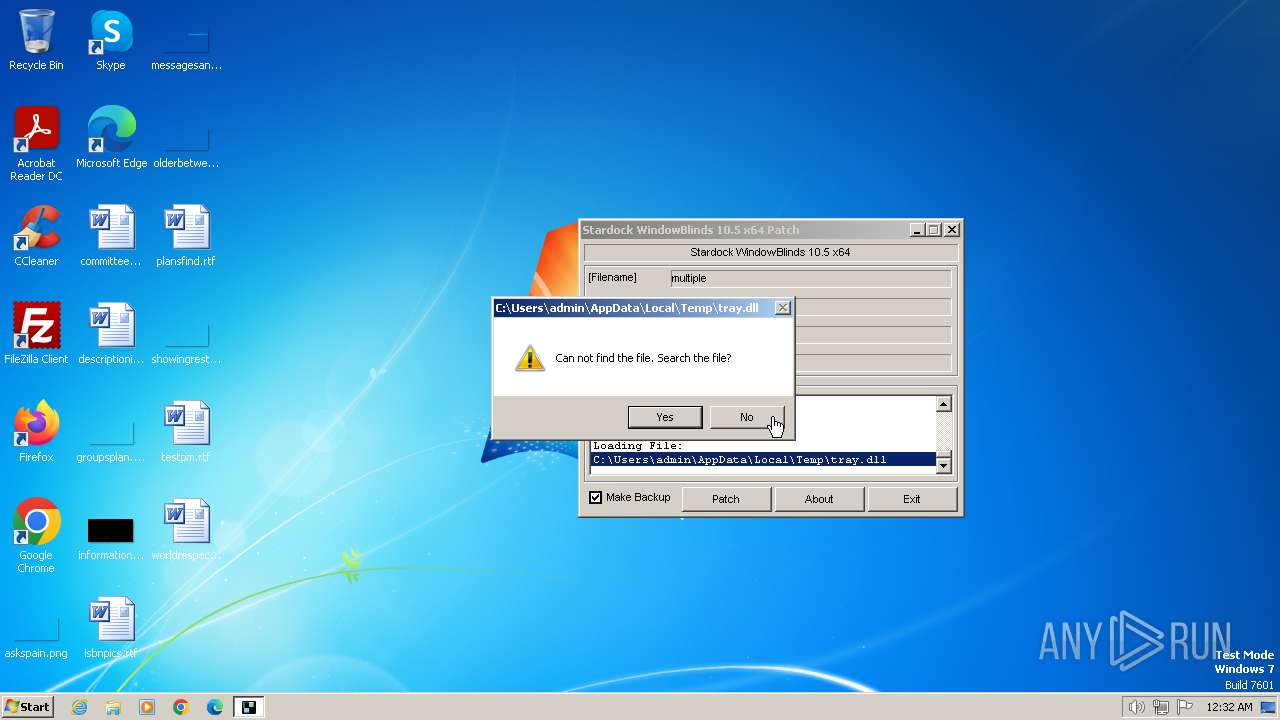
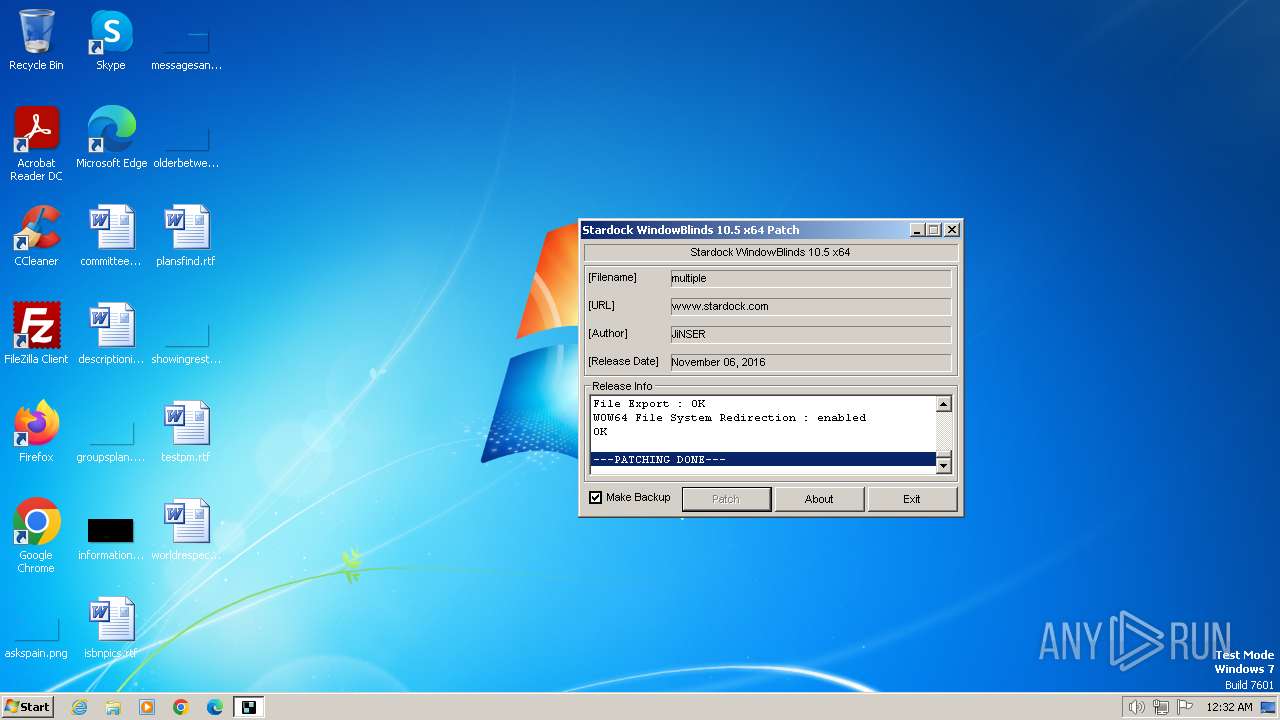
Drops the executable file immediately after the start
- patch.exe (PID: 2692)
SUSPICIOUS
Executable content was dropped or overwritten
- patch.exe (PID: 2692)
INFO
Create files in a temporary directory
- patch.exe (PID: 2692)
Checks supported languages
- patch.exe (PID: 2692)
Reads the computer name
- patch.exe (PID: 2692)
Reads the machine GUID from the registry
- patch.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:21 21:59:46+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 512 |
| InitializedDataSize: | 243200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x102b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2580 | "C:\Users\admin\AppData\Local\Temp\patch.exe" | C:\Users\admin\AppData\Local\Temp\patch.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Local\Temp\patch.exe" | C:\Users\admin\AppData\Local\Temp\patch.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 212
Read events
4 182
Write events
29
Delete events
1
Modification events
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0100000006000000000000000B00000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 070000000100000006000000000000000B000000020000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 700061007400630068002E0065007800650000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000045020000BE000000C50400009E020000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | MRUListEx |
Value: 00000000020000000300000001000000FFFFFFFF | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2692) patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | patch.exe | C:\Windows\wontrust.dll | executable | |
MD5:94F7E554FD2512B4A32A9ED8DA2F6118 | SHA256:571AE7119110D4B6ED6A5B70393AC2BDA5068BAB526E0436AEBD1F0B0D53A595 | |||
| 2692 | patch.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:D12D8819338411B969A24437E1B70406 | SHA256:351B514258CB95C9A5D00CAE48B521A52A2F422FC031E32AB2AFD184319FC28A | |||
| 2692 | patch.exe | C:\Windows\womtrust.dll | executable | |
MD5:D24ADA011A7440B33B625612BD549FDE | SHA256:C5BA737662FF8A5FE634B77B44B0BFA028AB7D756B9CC608026DA3D8B4CDB9BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |