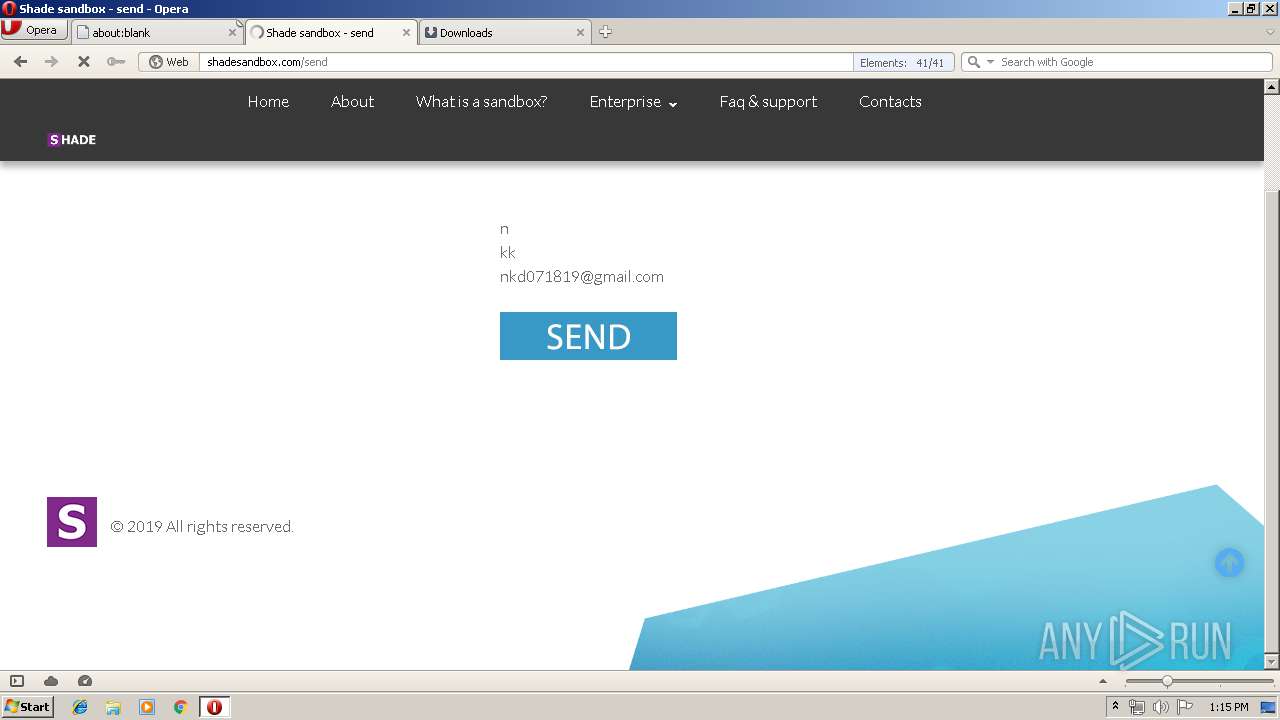
| URL: | https://shadesandbox.com/ |
| Full analysis: | https://app.any.run/tasks/452b727f-c418-47cc-b341-b449e4cdb9f7 |
| Verdict: | Suspicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | August 02, 2019, 12:12:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B6B29DD7C124B21E653B0B11EF62343B |
| SHA1: | 7A4457B54E630571BDD2923CBCC71F2BB9D7226D |
| SHA256: | A5251ACAE4927A8D013D5A486740C7D0E364F115A9FE93CAE875913197DA4C00 |
| SSDEEP: | 3:N8AJxGLGG:2AJw |
MALICIOUS
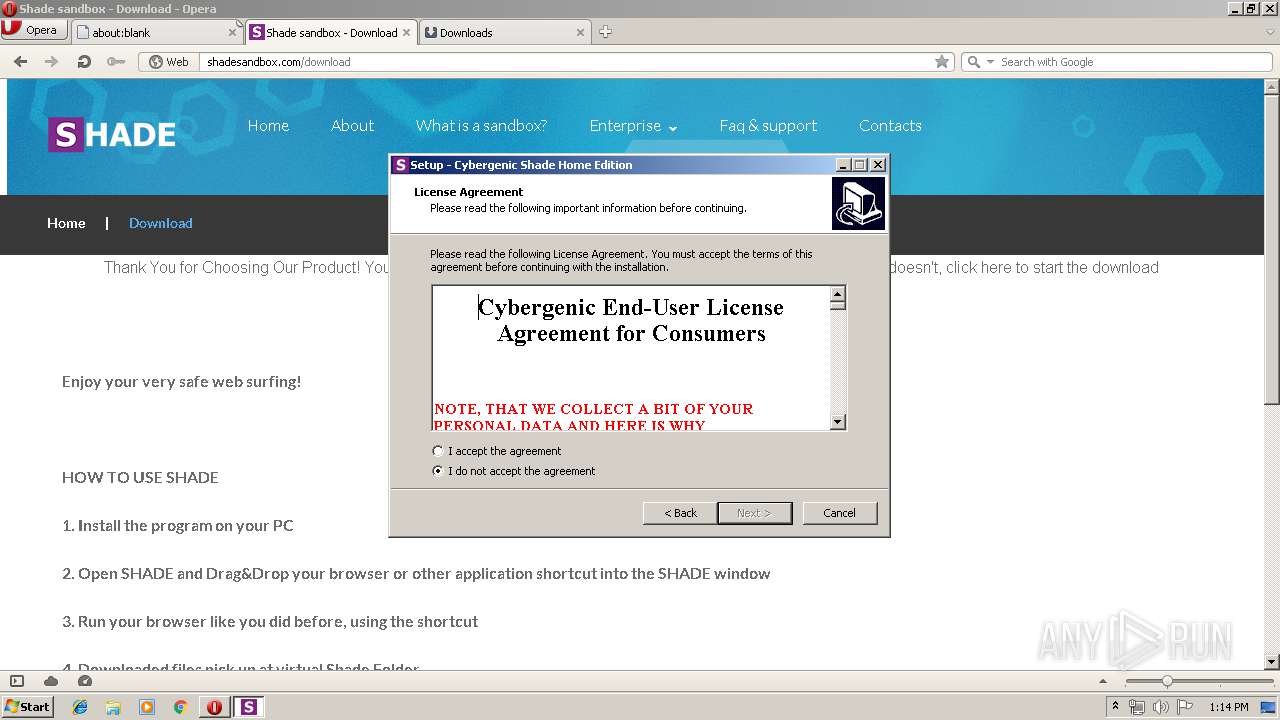
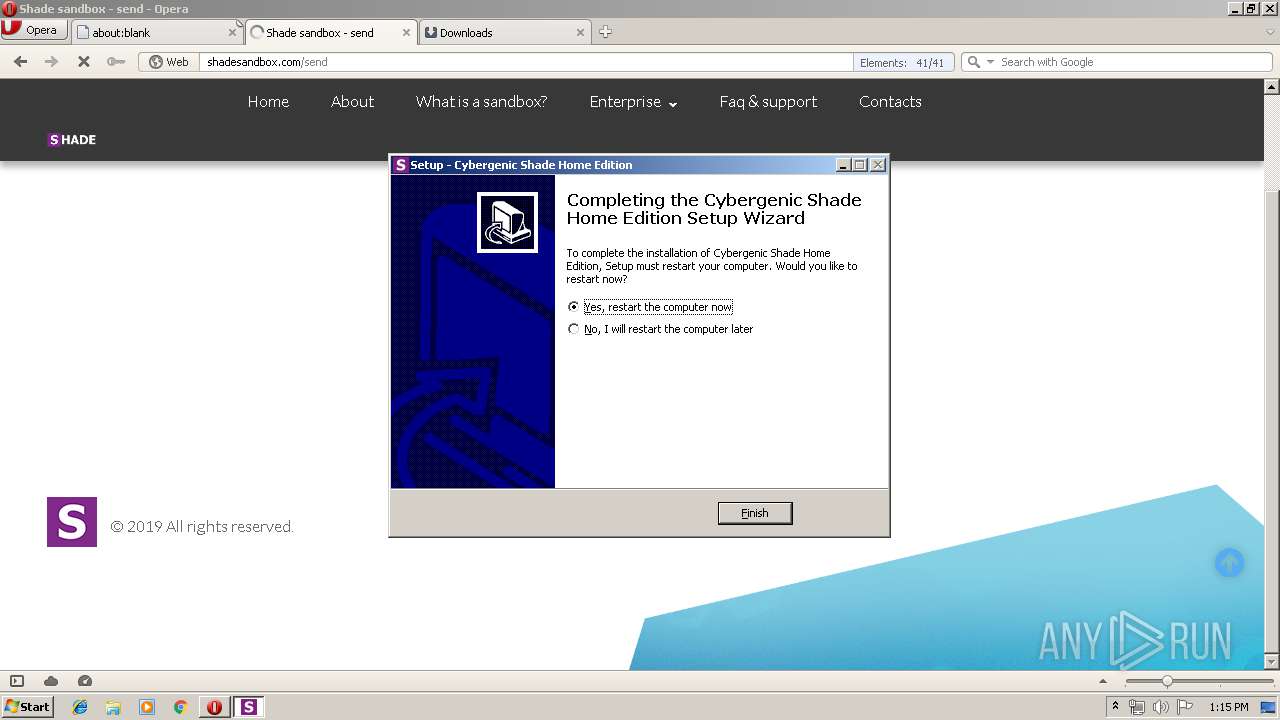
Application was dropped or rewritten from another process
- esc_setup.exe (PID: 272)
- esc_setup.exe (PID: 2876)
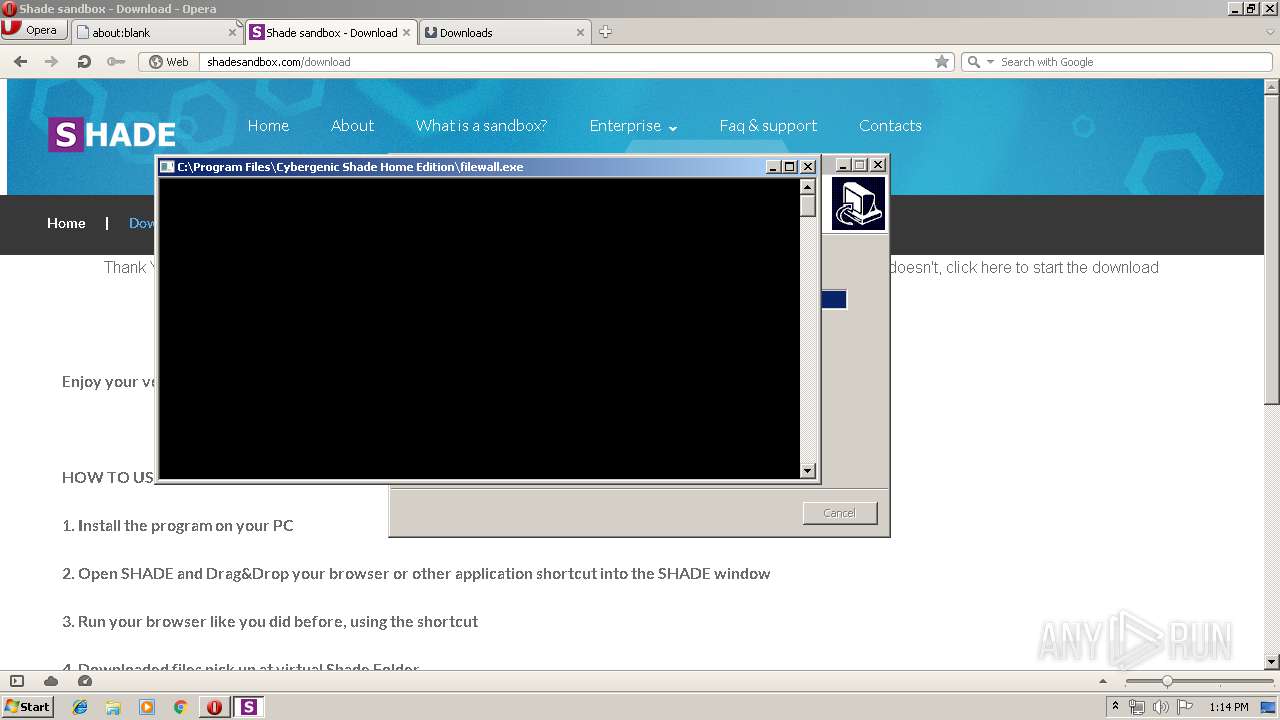
- filewall.exe (PID: 1668)
Downloads executable files from the Internet
- opera.exe (PID: 3244)
Loads dropped or rewritten executable
- filewall.exe (PID: 1668)
Writes to a start menu file
- esc_setup.tmp (PID: 3040)
Changes the autorun value in the registry
- esc_setup.tmp (PID: 3040)
SUSPICIOUS
Reads Windows owner or organization settings
- esc_setup.tmp (PID: 3040)
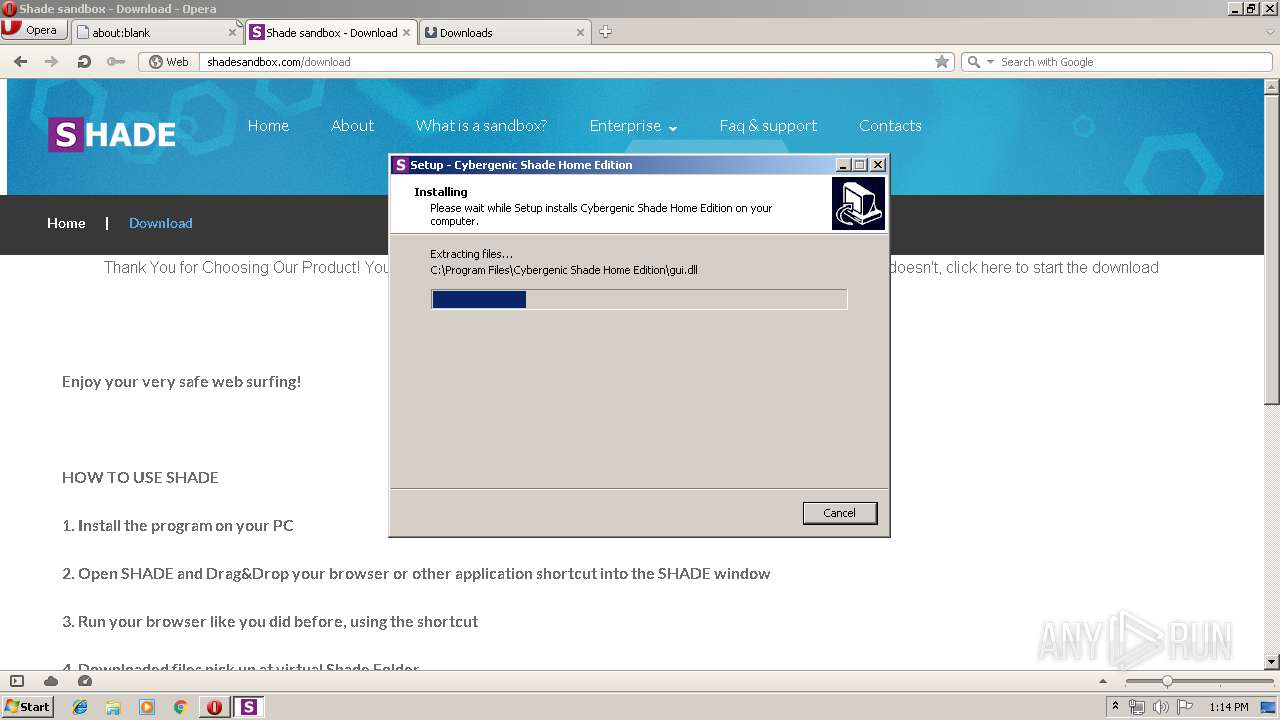
Executable content was dropped or overwritten
- esc_setup.exe (PID: 2876)
- opera.exe (PID: 3244)
- esc_setup.exe (PID: 272)
- esc_setup.tmp (PID: 3040)
- filewall.exe (PID: 1668)
Creates files in the Windows directory
- esc_setup.tmp (PID: 3040)
- filewall.exe (PID: 1668)
Creates files in the user directory
- filewall.exe (PID: 1668)
Reads the Windows organization settings
- esc_setup.tmp (PID: 3040)
Creates files in the driver directory
- filewall.exe (PID: 1668)
INFO
Creates files in the user directory
- opera.exe (PID: 3244)
Application was dropped or rewritten from another process
- esc_setup.tmp (PID: 3208)
- esc_setup.tmp (PID: 3040)
Loads dropped or rewritten executable
- esc_setup.tmp (PID: 3040)
Creates files in the program directory
- esc_setup.tmp (PID: 3040)
Creates a software uninstall entry
- esc_setup.tmp (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
6
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe" | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe | opera.exe | ||||||||||||
User: admin Company: Cybergenic Corp Integrity Level: MEDIUM Description: Cybergenic Shade Home Edition Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Cybergenic Shade Home Edition\filewall.exe" /iq | C:\Program Files\Cybergenic Shade Home Edition\filewall.exe | esc_setup.tmp | ||||||||||||
User: admin Company: Cybergenic Corp. Integrity Level: HIGH Description: Filewall Service Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe" /SPAWNWND=$10019E /NOTIFYWND=$110184 | C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe | esc_setup.tmp | ||||||||||||
User: admin Company: Cybergenic Corp Integrity Level: HIGH Description: Cybergenic Shade Home Edition Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\is-97UBJ.tmp\esc_setup.tmp" /SL5="$D0228,15041513,488448,C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe" /SPAWNWND=$10019E /NOTIFYWND=$110184 | C:\Users\admin\AppData\Local\Temp\is-97UBJ.tmp\esc_setup.tmp | esc_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\AppData\Local\Temp\is-C8U49.tmp\esc_setup.tmp" /SL5="$110184,15041513,488448,C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\esc_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-C8U49.tmp\esc_setup.tmp | — | esc_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Opera\opera.exe" "https://shadesandbox.com/" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
1 218
Read events
1 039
Write events
173
Delete events
6
Modification events
| (PID) Process: | (3244) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "https://shadesandbox.com/" | |||
| (PID) Process: | (3244) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3244) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3244) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: E00B0000F79828DD2B49D501 | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: F34B7E4A06326275824217C4FC0FAC37B39900AB88ACC3868D0A50D39A5D6E61 | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Cybergenic Shade Home Edition\esc.exe | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 8A44EAC3238F106DFE352B35AAD4B94FEC8BF882E606024708966858C6A1F79B | |||
| (PID) Process: | (3040) esc_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Cybergenic\BEST\Shade |
| Operation: | write | Name: | purchase_link |
Value: http://www.shadesandbox.com/#!support-shade/crfb | |||
Executable files
24
Suspicious files
87
Text files
83
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprEFA8.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprEFC9.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprF047.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SNZ6K0TPK1FIFFQQTQCL.temp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr3FF.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00004.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00005.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 3244 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3244 | opera.exe | GET | — | 62.113.216.182:80 | http://simple-activation.com/stuff/send_free_key.php?email=nkd071819@gmail.com&surname=kk&name=n | DE | — | — | suspicious |
3244 | opera.exe | GET | 200 | 172.217.21.227:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 546 b | whitelisted |
3244 | opera.exe | GET | 200 | 2.21.242.245:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgOfTfBfZAkMWGFKRjxyobrLQw%3D%3D | NL | der | 527 b | whitelisted |
3244 | opera.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEHKB437Pif0hmkMomebkBlQ%3D | US | der | 471 b | whitelisted |
3244 | opera.exe | GET | 200 | 62.113.216.182:80 | http://simple-activation.com/upd/esc_setup.exe | DE | executable | 14.7 Mb | suspicious |
1668 | filewall.exe | GET | — | 62.113.216.182:80 | http://cybergenic-activation.us/activation.php?code=NWAG-XBPV-DKPK&hwid=7Ix54L2lx56baY5oRsyaIg%3D%3D&hash=5%2BUvvJeCeQMRayYA1NwUvyNPAHU%3D | DE | — | — | suspicious |
3244 | opera.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEFMFNN6xWiAu2YMi%2B3ckqWU%3D | US | der | 471 b | whitelisted |
3244 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3244 | opera.exe | 151.80.207.170:443 | shadesandbox.com | OVH SAS | FR | unknown |
3244 | opera.exe | 185.26.182.93:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3244 | opera.exe | 185.26.182.94:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3244 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3244 | opera.exe | 185.26.182.111:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3244 | opera.exe | 2.21.242.245:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | NL | whitelisted |
3244 | opera.exe | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
3244 | opera.exe | 172.217.23.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1668 | filewall.exe | 62.113.216.182:80 | simple-activation.com | 23media GmbH | DE | suspicious |
3244 | opera.exe | 172.217.23.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
shadesandbox.com |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
crl4.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.shadesandbox.com |
| suspicious |
crl.pki.goog |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3244 | opera.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
esc_setup.tmp | Total memory in bytes : 3757686784
|
esc_setup.tmp | Required : 1879048192
|