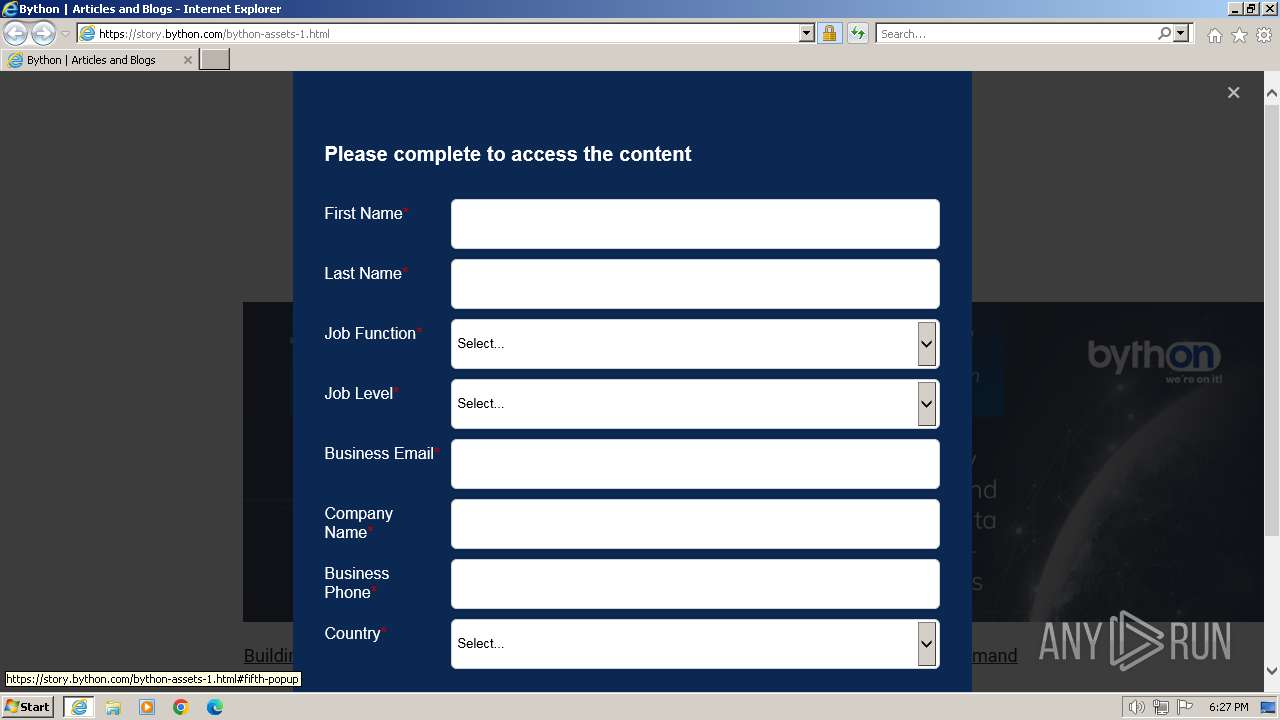
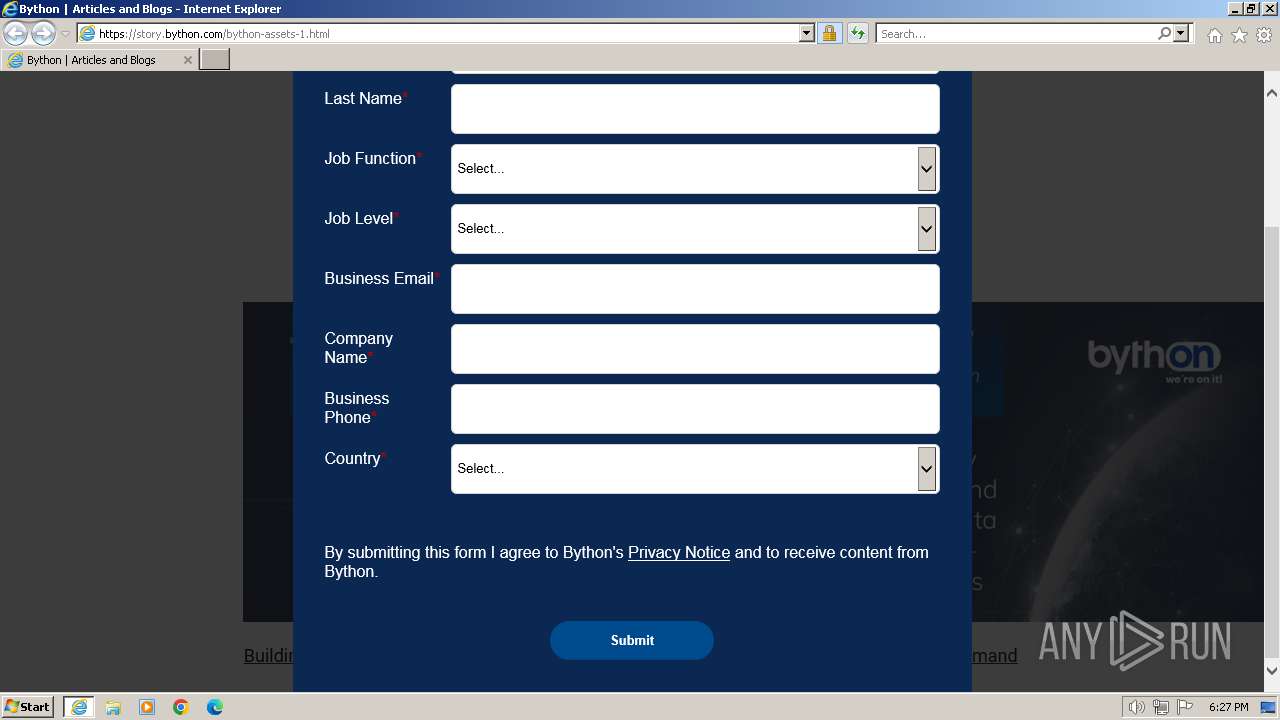
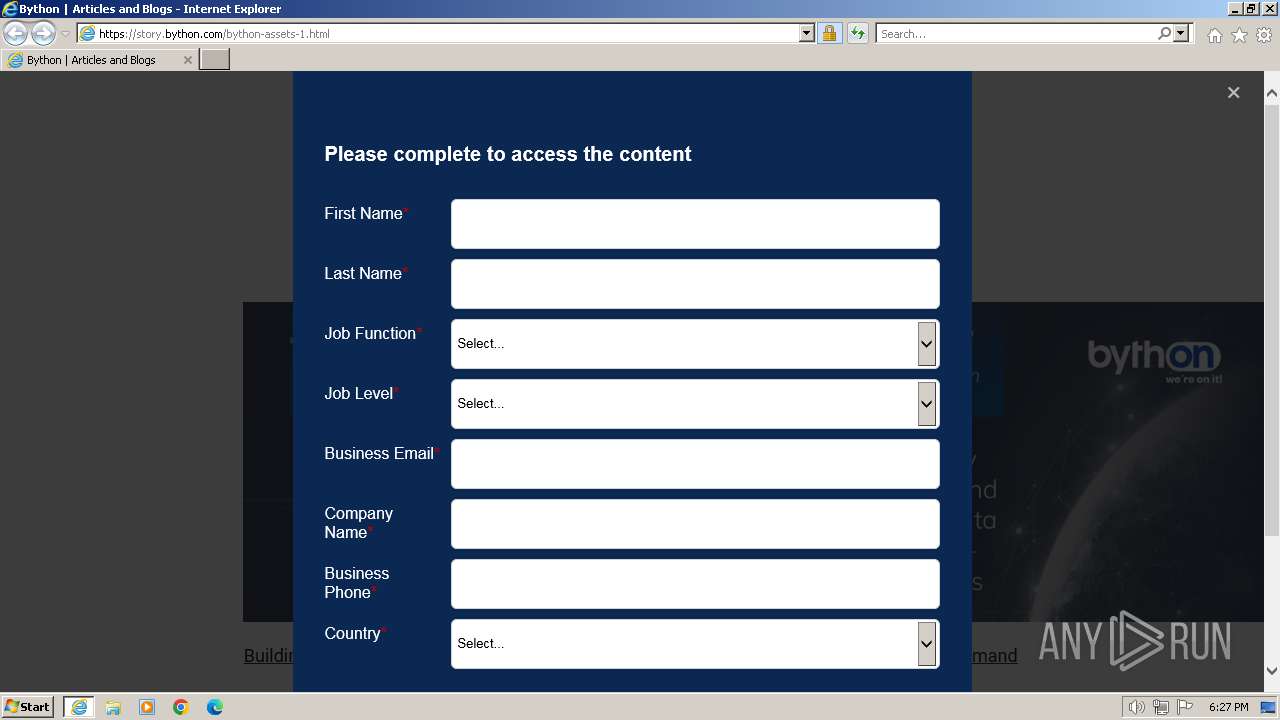
| URL: | https://story.bython.com/bython-assets-1.html?mkt_tok=NjQ4LU1ZSy0yMjYAAAGRBLMKlyP_LHcR9Q7c-GCxc8LaZEoLauRt0dWcuIQjWQS7dEb |
| Full analysis: | https://app.any.run/tasks/74b49146-80c3-466b-801f-ce650bd6e919 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2024, 18:26:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ECACD70822FFFE525040B0382A71BB85 |
| SHA1: | 886EF4057AE89D0F7967FE0D3232E04ABC7A5C02 |
| SHA256: | A503AB7B10F5044D30E7C130B3385DF49FB8B2F890B31B19FBAFD0099E39BB00 |
| SSDEEP: | 3:N8cMcLoGgXWoeBCPukiXplcc7EmpsVPn2rn:2cM6olXWa2rHImYP2rn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://story.bython.com/bython-assets-1.html?mkt_tok=NjQ4LU1ZSy0yMjYAAAGRBLMKlyP_LHcR9Q7c-GCxc8LaZEoLauRt0dWcuIQjWQS7dEb" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2736 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:752 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
18 644
Read events
18 502
Write events
133
Delete events
9
Modification events
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
77
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:782510ED6610E97792C7AD72DC7EE281 | SHA256:DBFF03E3ECF052A89D3D2F9D07D5B7F1970367BE0A45EF1002D5EFF049DEF970 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\stripmkttok[1].js | text | |
MD5:19CFAD3D14D21907820AD1A443F75427 | SHA256:F7545B96ED2740220C349AE9DEB614FAF1F0F211D4CF710788E0790F74CC9715 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:D6F628A1812FC142C846258811286797 | SHA256:4EEA0452BA1BA0C20990D219ACF90A9A4527172C57573B657E68EC94F5D4A1A2 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\mktLPSupportCompat[1].css | text | |
MD5:A48B035B7ED2384E818069850F707C3C | SHA256:CC27845C4BA2580588D37B6D48939E7B833FAEEFA237E927860054226A0AD6F9 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bython-logo-blue-300[1].png | image | |
MD5:BCF06381877269FA9445653EB639CB74 | SHA256:7ECE3FB5B3B0B6B1B1149464B9F320A27C43AB24AFB64B6712EA9BC14FF67BF0 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YC3GKRMJ.txt | text | |
MD5:4B98F0B1B92171F718DF3E488D5B0F0C | SHA256:F19D1F24F4C5DE938A0127732E9BD4C684C678309BB7DDEB630F92A159C8C885 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:13C937F5EA283FBDC6644089827190BA | SHA256:F15C2278365C7D58021FD8B1213031217FCF2E051BC91CFFB6F7D5457C005B6E | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bython-assets-1[1].htm | html | |
MD5:3FDC3F0B4B03DC2754D0A6E17CAE5650 | SHA256:52E88D4733ED88E82A32F33F0E15653F27E977B8FC1BAD6BCDC66A630BB43F21 | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\magnific-popup[1].css | text | |
MD5:30B593B71D7672658F89BFEA0AB360C9 | SHA256:45D1F5F6CF913746C45DD697B1A8F3B719C02D8B3F678DC7FC2766D54E1AAF6E | |||
| 2736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\jquery.min[1].js | text | |
MD5:7F9FB969CE353C5D77707836391EB28D | SHA256:2051D61446D4DBFFB03727031022A08C84528AB44D203A7669C101E5FBDD5515 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
118
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2736 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?58b09451c6662268 | unknown | — | — | unknown |
2736 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c23cd8118a42bc | unknown | — | — | unknown |
2736 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2736 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | binary | 471 b | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGbSiPAo8Qj1CbnbR%2FpRjKM%3D | unknown | binary | 471 b | unknown |
2736 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEE80yiW5Mf2wCipGbb3nZn0%3D | unknown | binary | 471 b | unknown |
2736 | iexplore.exe | GET | 200 | 18.165.185.120:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
2736 | iexplore.exe | GET | 200 | 18.165.184.219:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
2736 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | binary | 1.37 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2736 | iexplore.exe | 104.16.95.80:443 | story.bython.com | CLOUDFLARENET | — | shared |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2736 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2736 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2736 | iexplore.exe | 142.250.185.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2736 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | unknown |
2736 | iexplore.exe | 142.250.185.106:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
2736 | iexplore.exe | 16.182.71.208:443 | s3.amazonaws.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
story.bython.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdn-static.bizzabo.com |
| whitelisted |
s3.amazonaws.com |
| shared |
eum.instana.io |
| whitelisted |
munchkin.marketo.net |
| whitelisted |