| File name: | danabot |
| Full analysis: | https://app.any.run/tasks/8d567dc0-13e3-4dab-9f6b-80ed490fb563 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2019, 12:39:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | 80D58221D48F486E0F760296DD942927 |
| SHA1: | 1FE57614D9DEDBC149EF12601AA007BBE3AA0266 |
| SHA256: | A4E7C6D1EE280507A85326D6A925EEBF01F085F16337C50ED50A2932FB59645B |
| SSDEEP: | 3072:lOXRBt5DVbo0HGa9+mI2+U6DFd0jbWYYbunfN2bLX2xALkBdS2TPFDD/chh:lOhBtTU0mbj256LWbWYYOmSdS2TN |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2628)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 1380)
Reads the machine GUID from the registry
- explorer.exe (PID: 3052)
- CompMgmtLauncher.exe (PID: 2428)
- mmc.exe (PID: 2800)
Low-level read access rights to disk partition
- vds.exe (PID: 2388)
INFO
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 1196)
Creates files in the user directory
- WINWORD.EXE (PID: 1196)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (70.7) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (11.2) |
| .exe | | | Win32 Executable (generic) (7.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.5) |
| .exe | | | Generic Win/DOS Executable (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:01:11 00:32:44+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 276992 |
| InitializedDataSize: | 32256 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x45528 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Jan-2019 23:32:44 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 10-Jan-2019 23:32:44 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000430B4 | 0x00043200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.30132 |
.itext | 0x00045000 | 0x000007CC | 0x00000800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.98205 |
.data | 0x00046000 | 0x000023C8 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.93872 |
.bss | 0x00049000 | 0x00005AF4 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0004F000 | 0x00000C82 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.58468 |
.didata | 0x00050000 | 0x000001C8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.90029 |
.edata | 0x00051000 | 0x0000006D | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.25989 |
.rdata | 0x00052000 | 0x00000044 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.16606 |
.reloc | 0x00053000 | 0x00003044 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.50367 |
.rsrc | 0x00057000 | 0x00001400 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.65307 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
4090 | 3.18737 | 464 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.50315 | 508 | UNKNOWN | UNKNOWN | RT_STRING |
4092 | 3.36848 | 196 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 3.38569 | 304 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.25466 | 796 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.35521 | 852 | UNKNOWN | UNKNOWN | RT_STRING |
4096 | 3.31066 | 696 | UNKNOWN | UNKNOWN | RT_STRING |
DVCLAL | 4 | 16 | UNKNOWN | UNKNOWN | RT_RCDATA |
PACKAGEINFO | 4.97477 | 380 | UNKNOWN | UNKNOWN | RT_RCDATA |
Imports
advapi32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
ntdll.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x0004C62C |
__dbk_fcall_wrapper | 2 | 0x0000BB34 |
Total processes
53
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
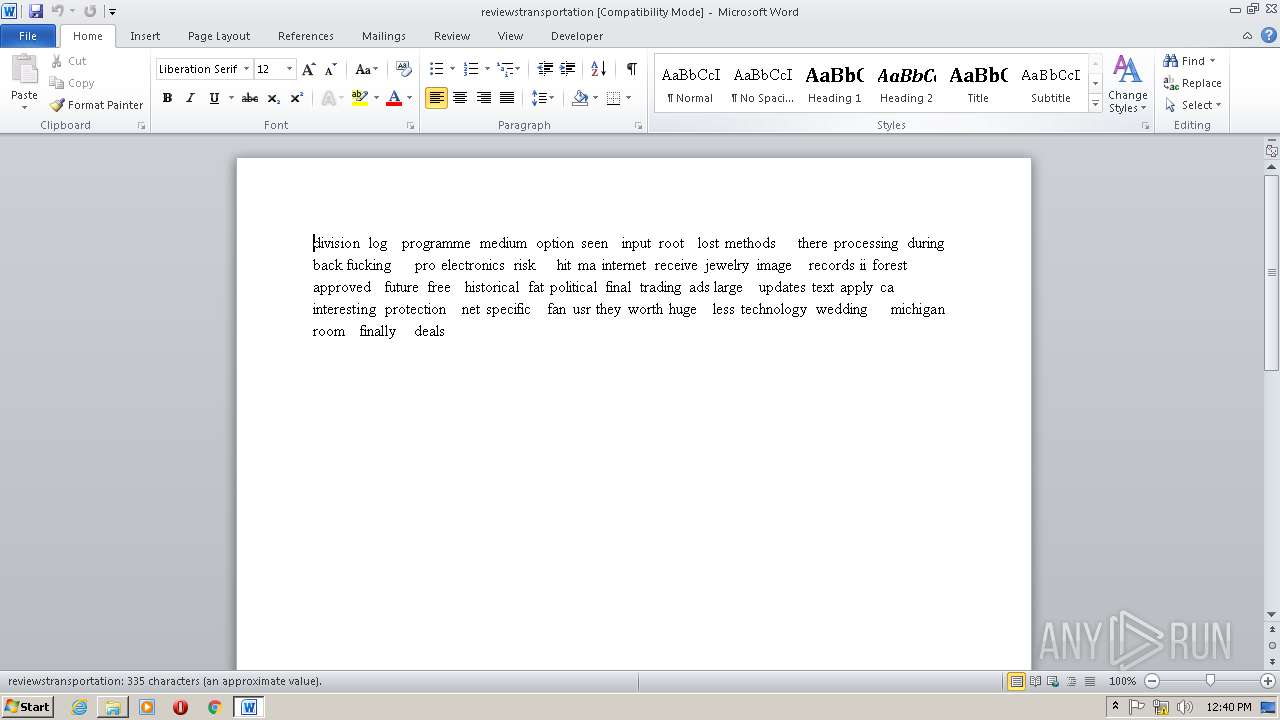
| 1196 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\reviewstransportation.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 1380 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\Desktop\danabot.exe", dbkFCallWrapperAddr | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2368 | "C:\Windows\system32\CompMgmtLauncher.exe" | C:\Windows\system32\CompMgmtLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Computer Management Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2388 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2428 | "C:\Windows\system32\CompMgmtLauncher.exe" | C:\Windows\system32\CompMgmtLauncher.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Computer Management Snapin Launcher Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\Desktop\danabot.exe", dbkFCallWrapperAddr | C:\Windows\SysWOW64\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | C:\Windows\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2800 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\compmgmt.msc" /s | C:\Windows\system32\mmc.exe | CompMgmtLauncher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3052 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 422
Read events
1 112
Write events
299
Delete events
11
Modification events
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | cr% |
Value: 63722500AC040000010000000000000000000000 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1311440939 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311441022 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311441023 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: AC040000EF6DB2D5AAA9D40100000000 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | js% |
Value: 6A732500AC04000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | js% |
Value: 6A732500AC04000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1196) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA43.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{1022F6D0-07FD-4E1B-A158-797F59F1F67B}.tmp | — | |
MD5:— | SHA256:— | |||
| 1196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{05D9AF3C-8C9C-4AFD-8B32-D75BB7E0F87C}.tmp | — | |
MD5:— | SHA256:— | |||
| 1196 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 1196 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\reviewstransportation.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1196 | WINWORD.EXE | C:\Users\admin\Documents\~$viewstransportation.rtf | pgc | |
MD5:B355057B42FFD42F4EB9F1C7F7B9DD9C | SHA256:E3AE992D28899B6891EE14EB3BC8E0328E838819138423734F3C1205702BE667 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerExtension
|