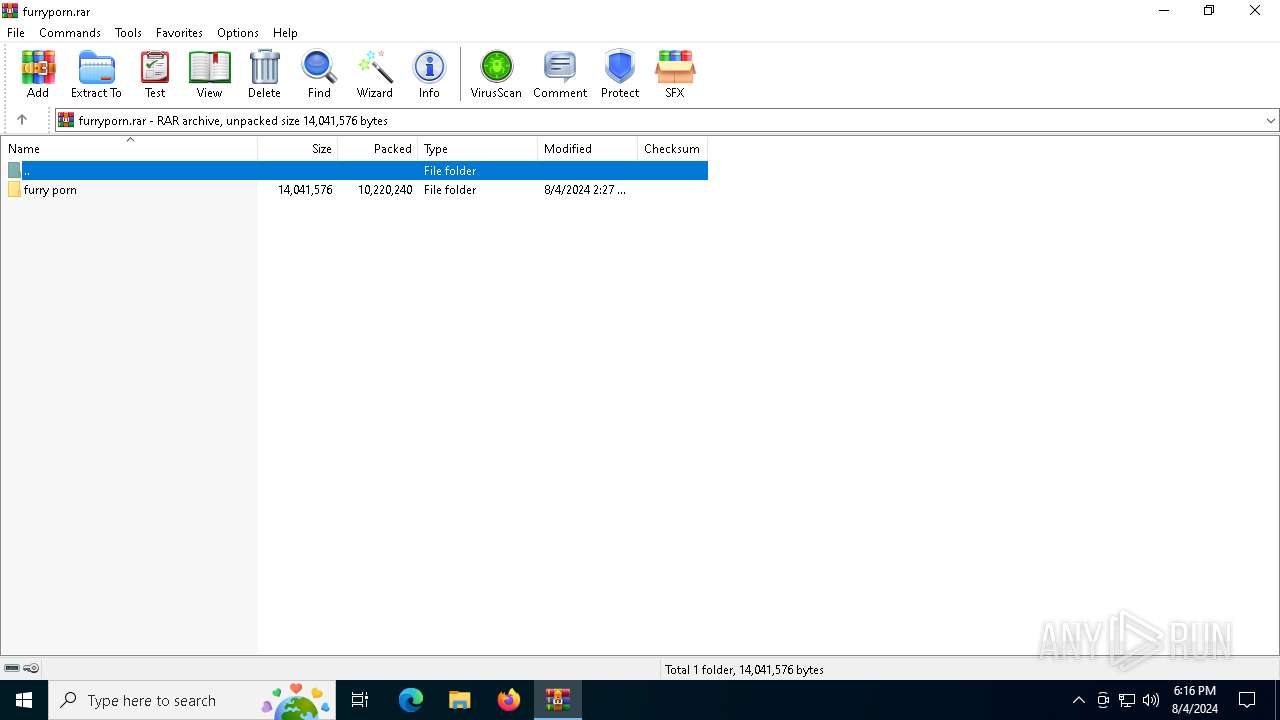
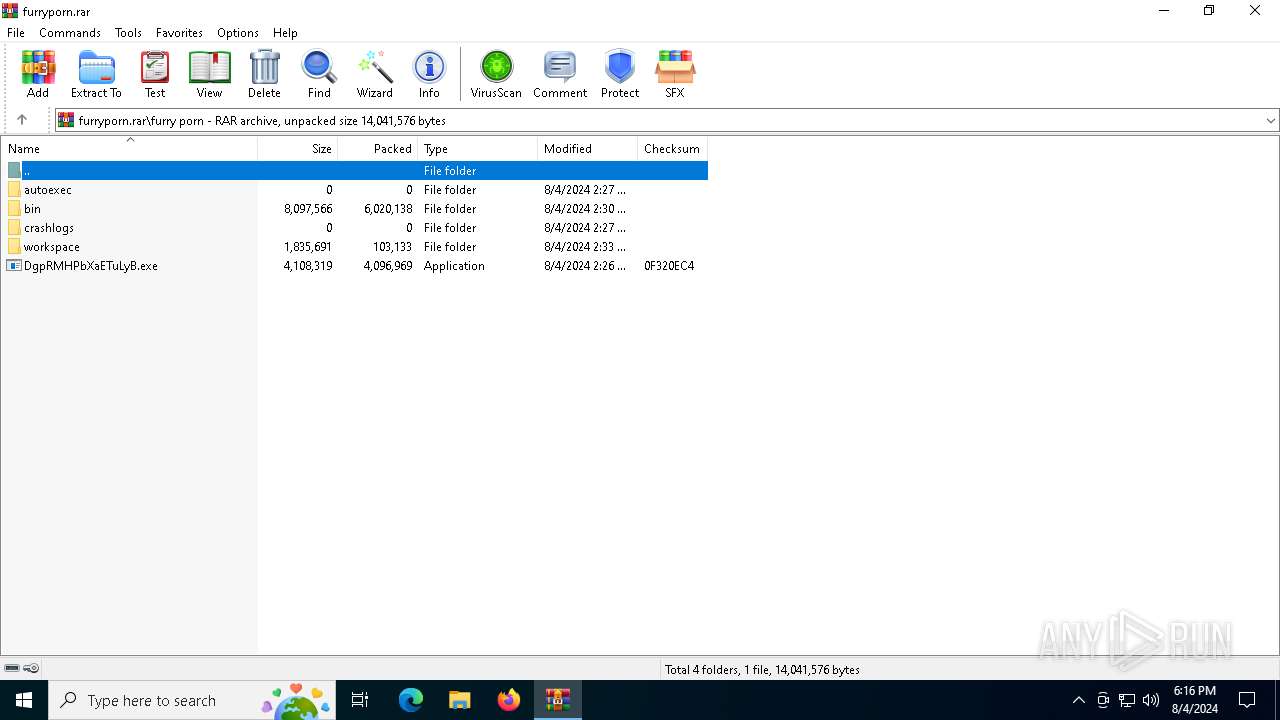
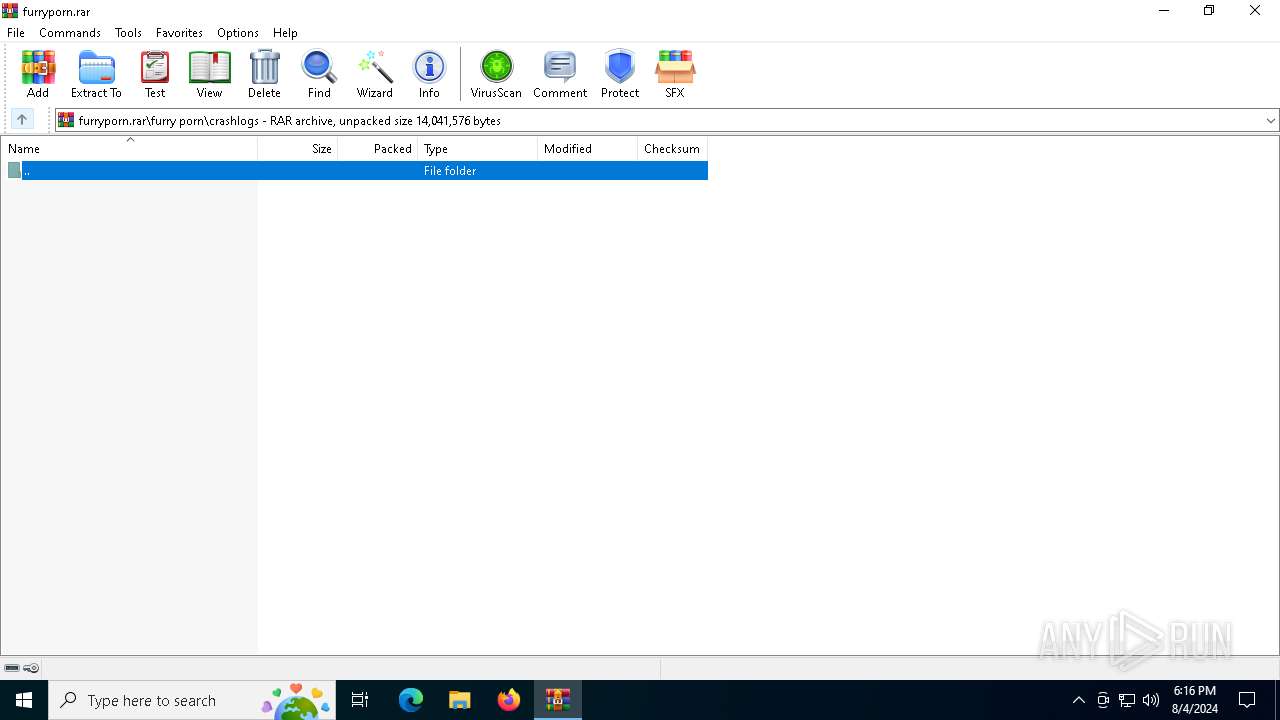
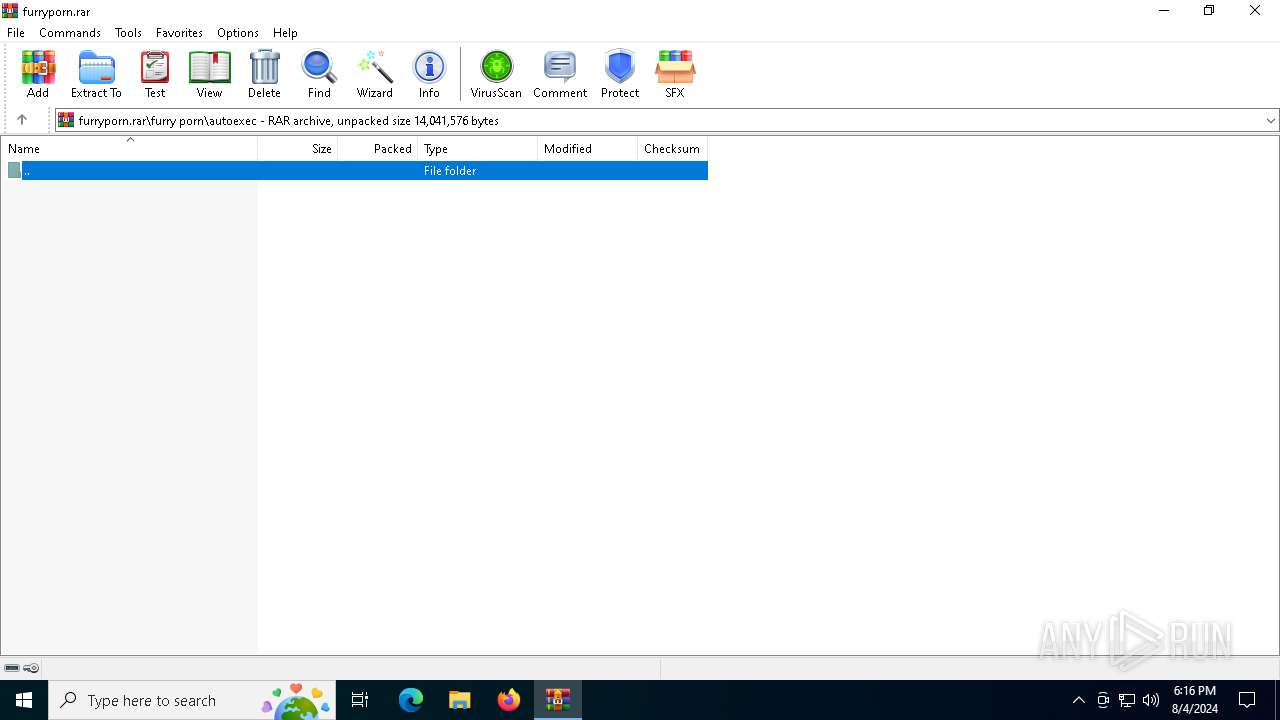
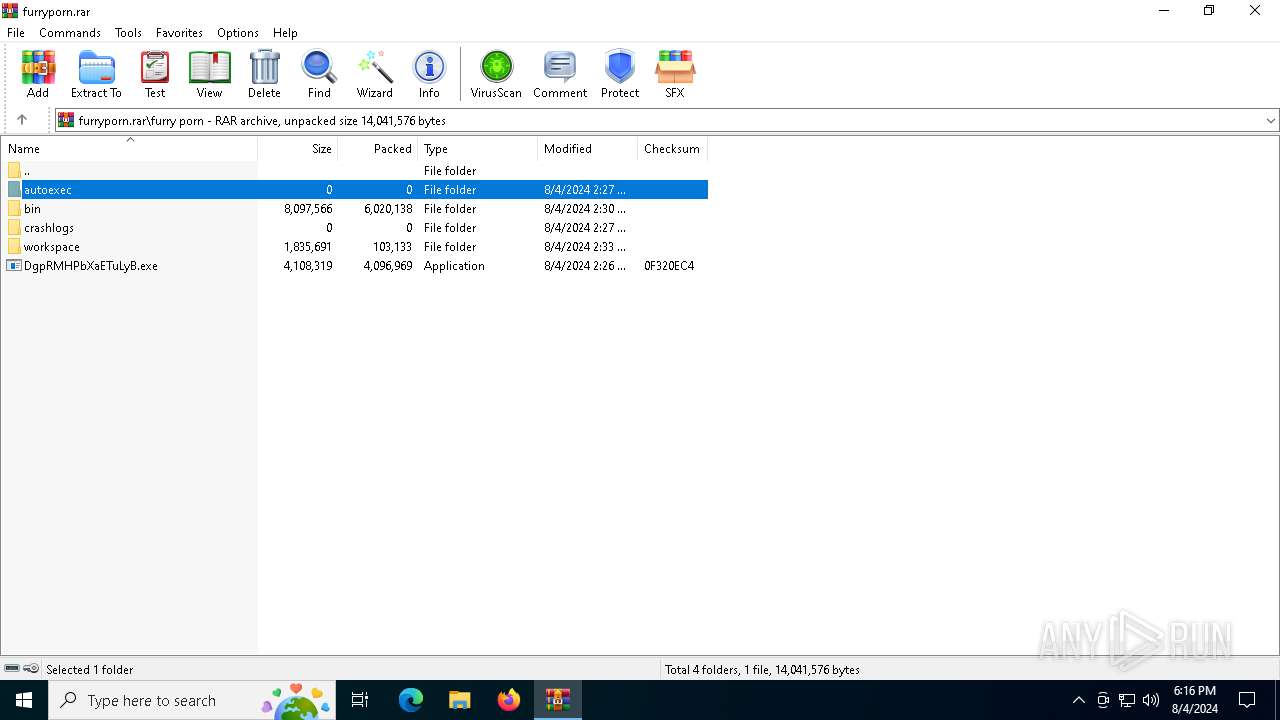
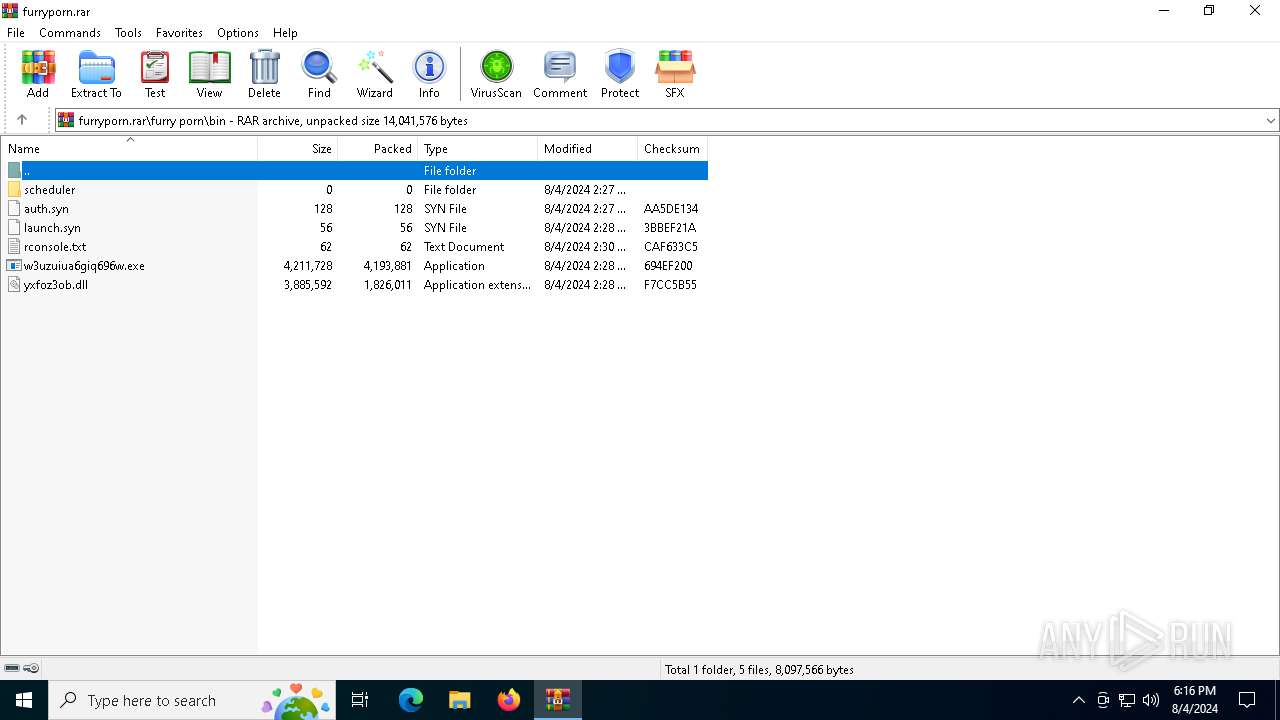
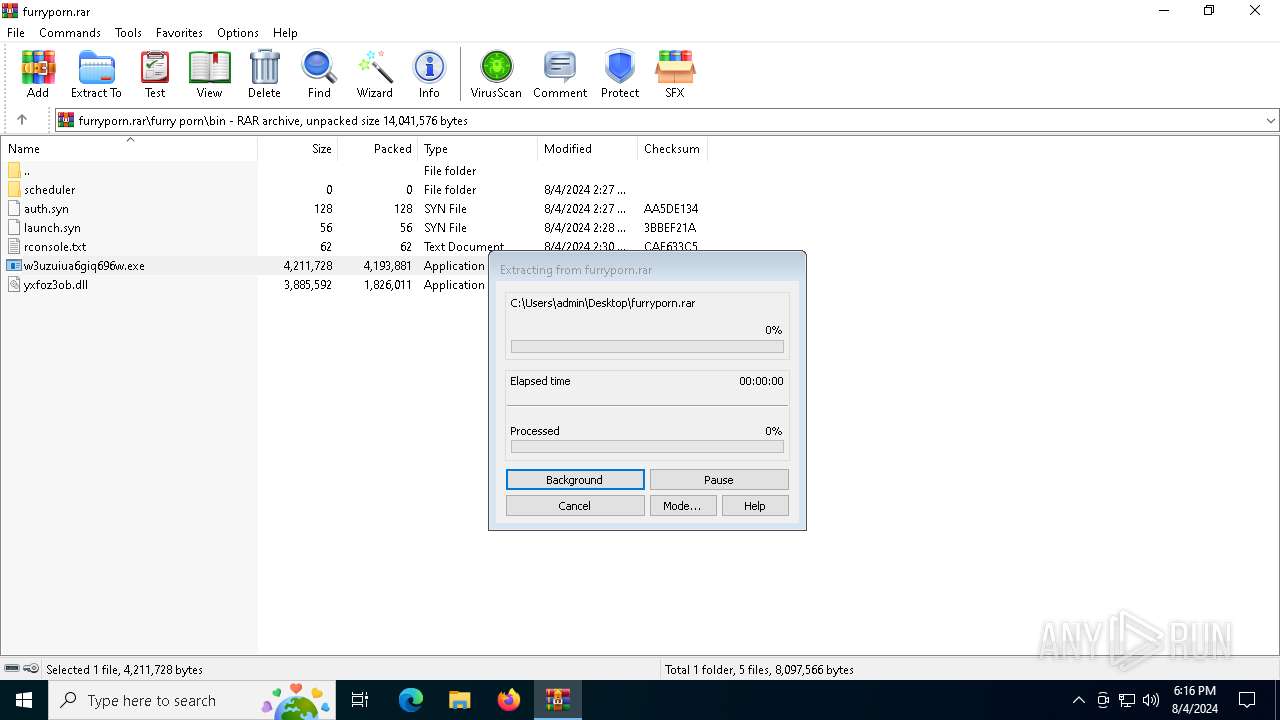
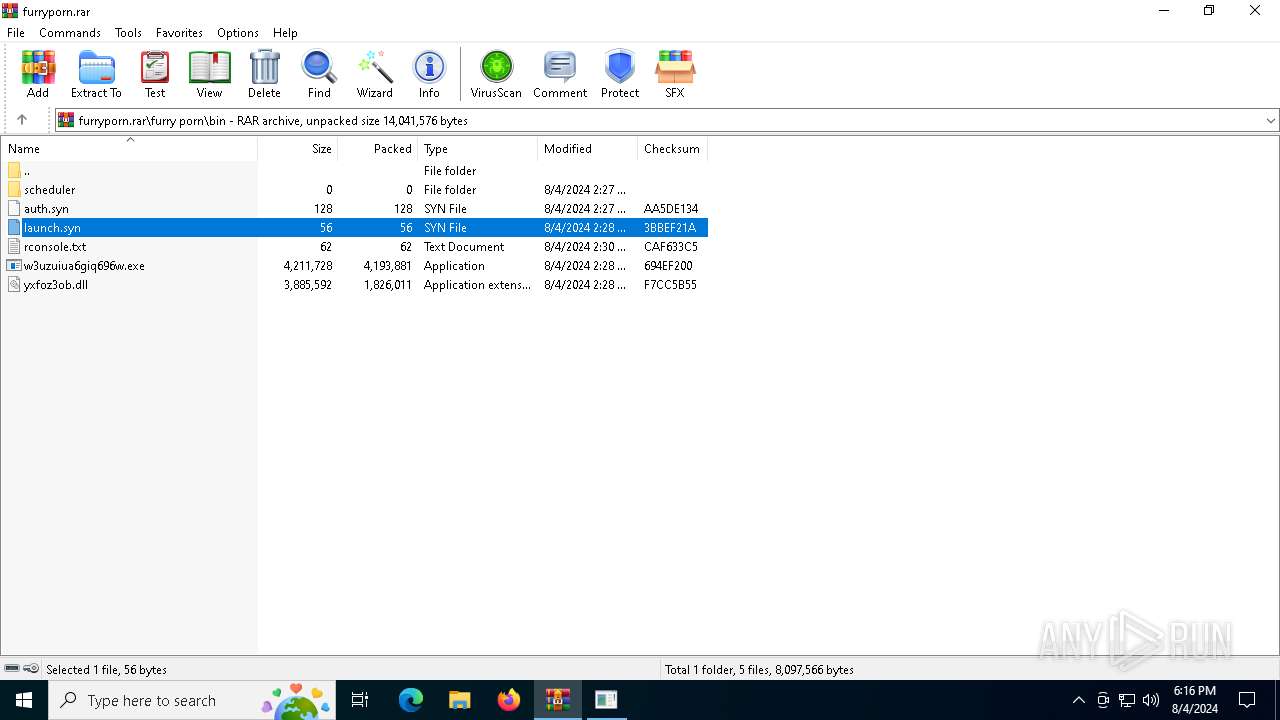
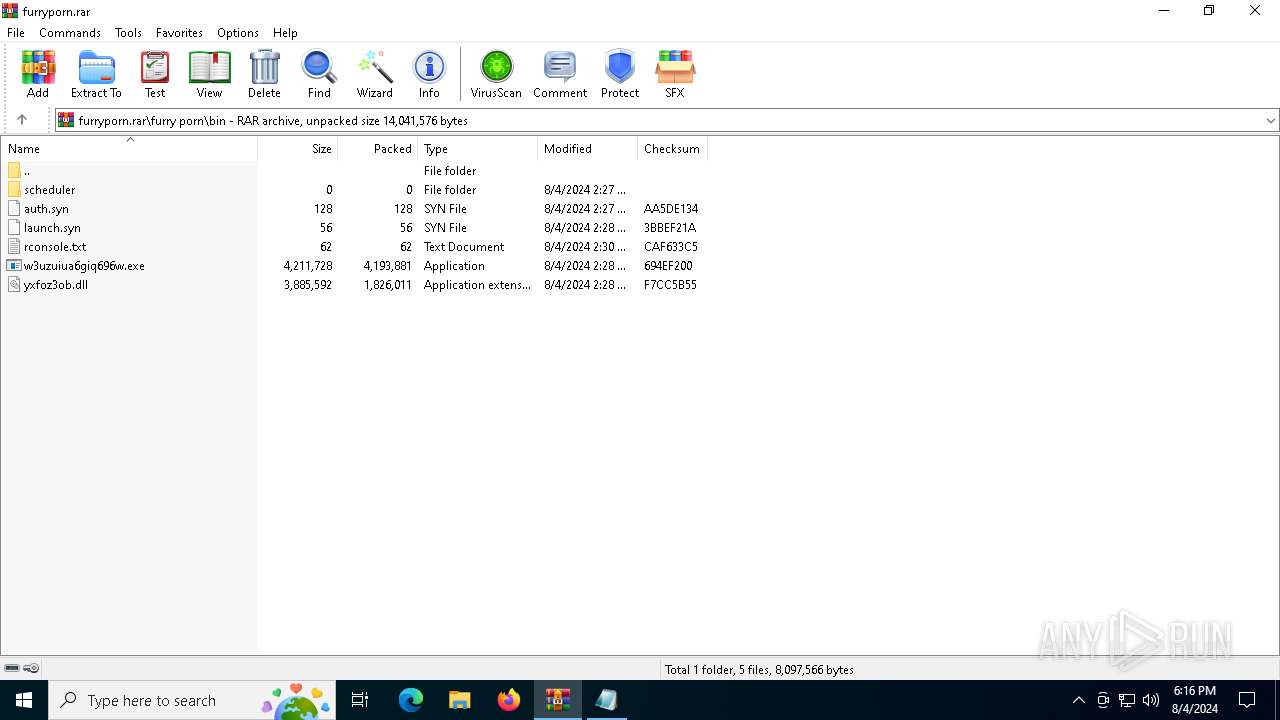
| File name: | furryporn.rar |
| Full analysis: | https://app.any.run/tasks/6769fd92-20e0-4fbc-a11e-65d5c8e7c45d |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 18:16:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0BABBCF0C9080200BD6815074E31BAE0 |
| SHA1: | D7862890ED84B1FBAE238FB1A000F9ABE2FA07CE |
| SHA256: | A4E356DDADF65E0F358EAE4213EBEF5B2704DE280C9097CEC2E3DE79348A5B92 |
| SSDEEP: | 98304:Vth7/Con9VEWJWhscRZ4gaRL8ibQteZzKnHKbDa6vO9fXLF83pEbGCn7EsA7txft:fEtUPmtjIsYVWjrE |
MALICIOUS
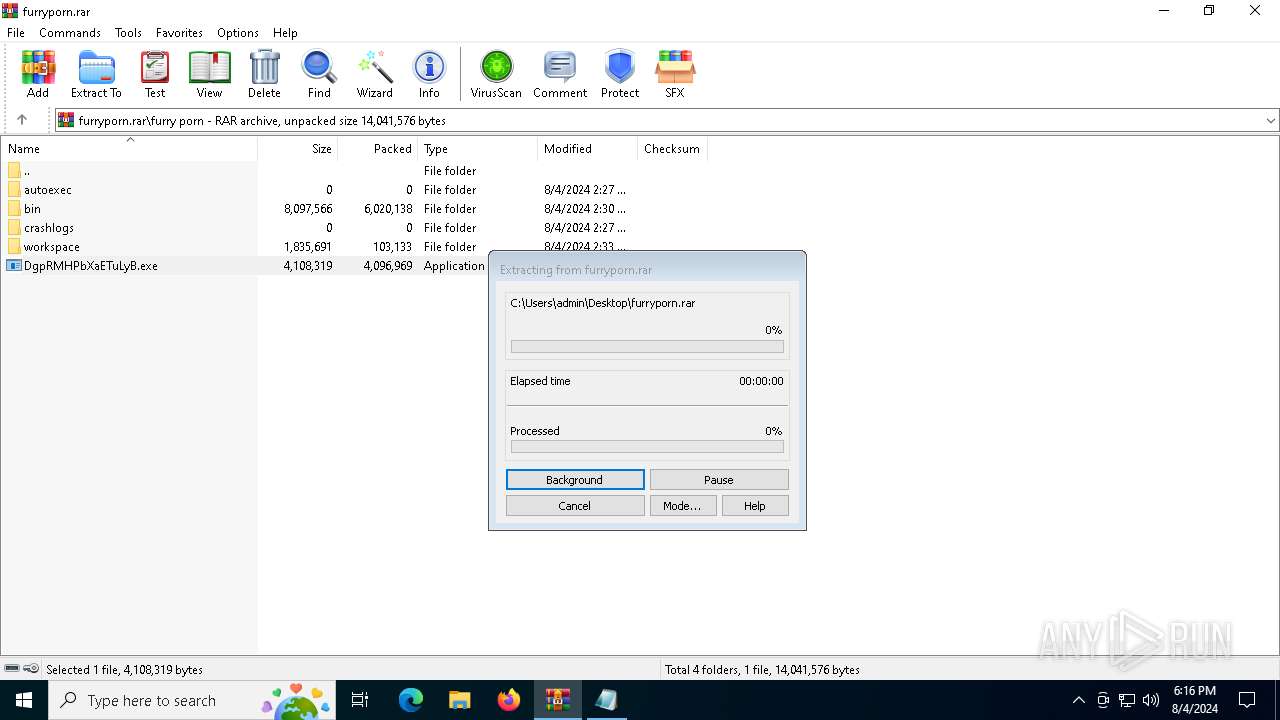
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6384)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6384)
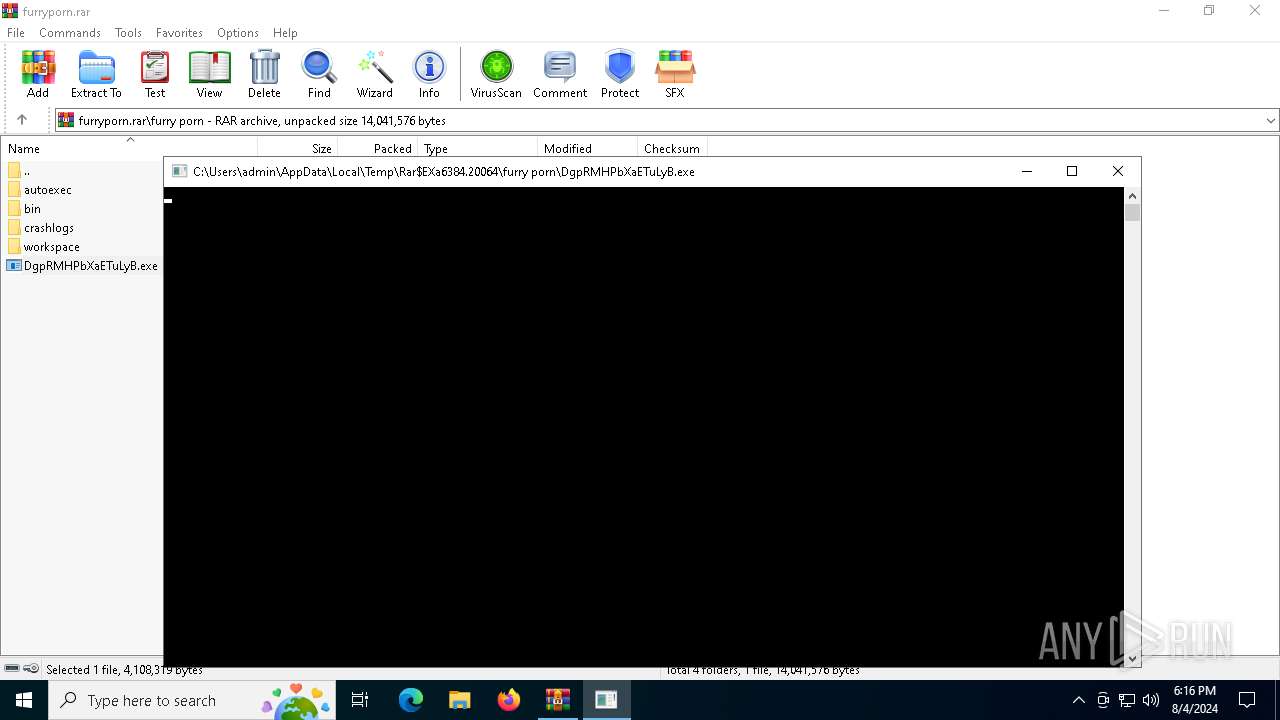
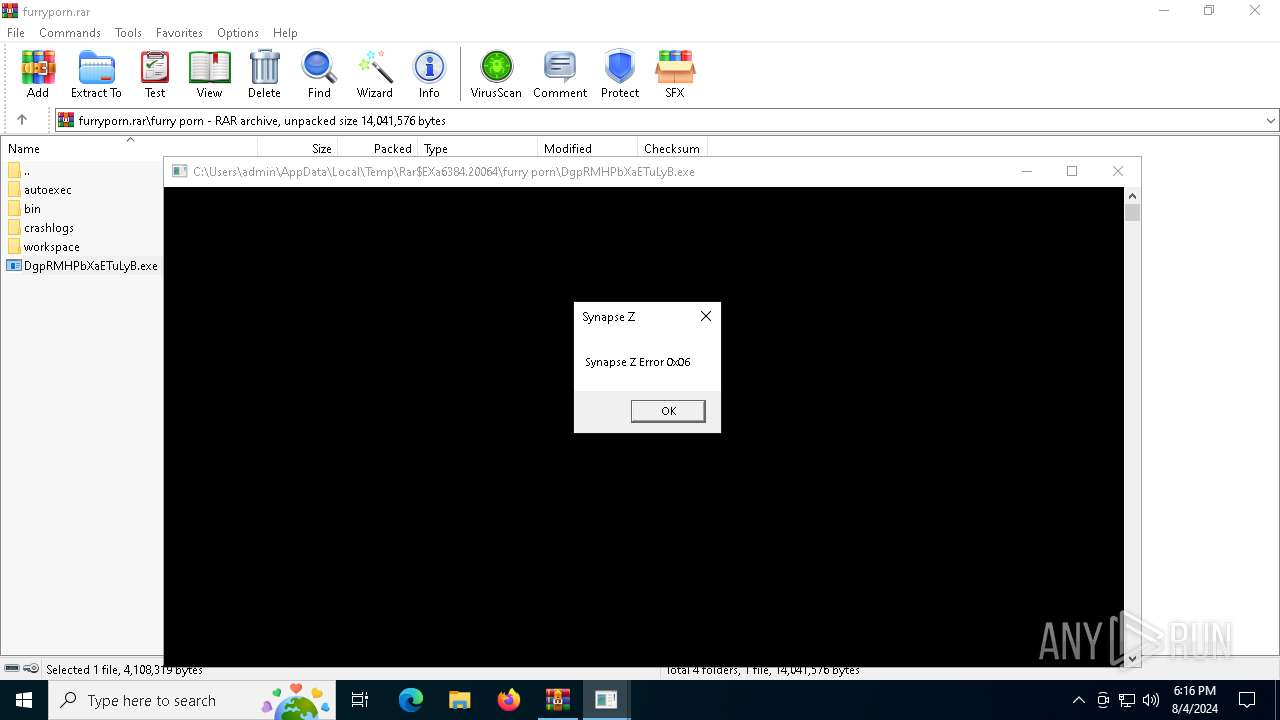
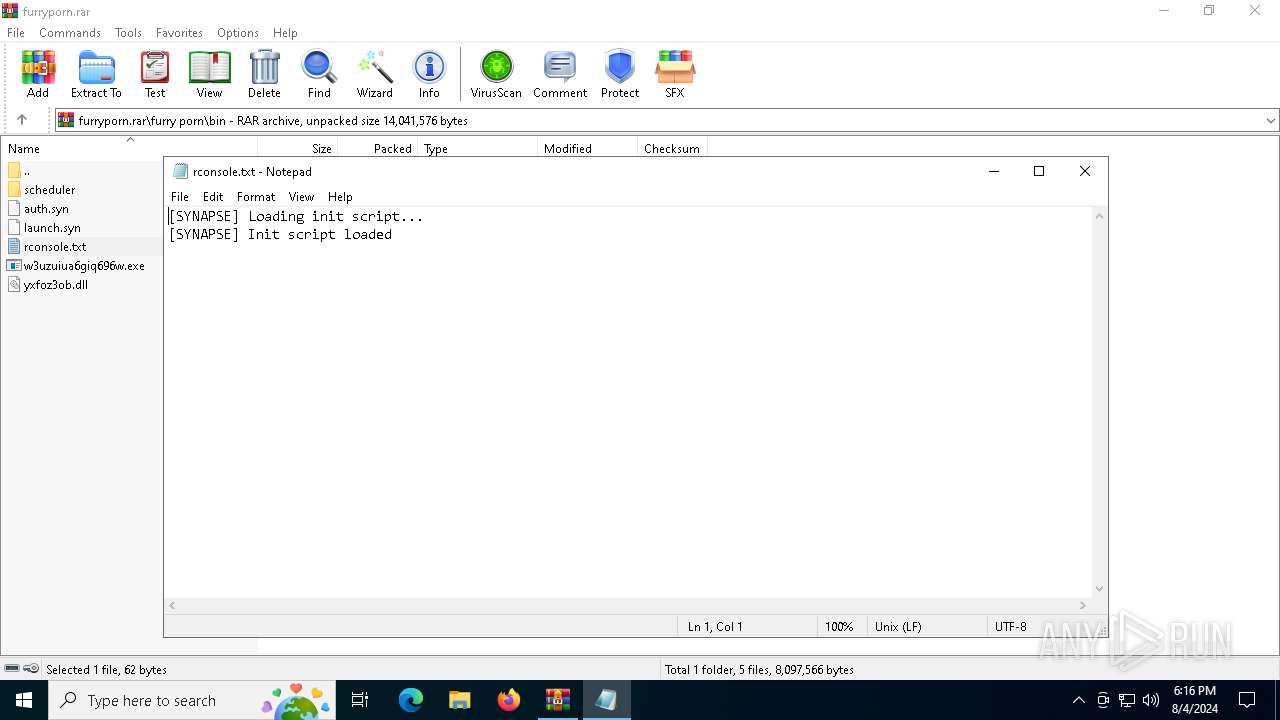
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6384)
Reads the BIOS version
- w3uzuiua6giq696w.exe (PID: 7028)
- DgpRMHPbXaETuLyB.exe (PID: 3180)
- DgpRMHPbXaETuLyB.exe (PID: 6892)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6384)
Checks supported languages
- DgpRMHPbXaETuLyB.exe (PID: 6892)
- w3uzuiua6giq696w.exe (PID: 7028)
- DgpRMHPbXaETuLyB.exe (PID: 3180)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 6384)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7140)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6384)
Reads the machine GUID from the registry
- DgpRMHPbXaETuLyB.exe (PID: 3180)
- DgpRMHPbXaETuLyB.exe (PID: 6892)
Reads the computer name
- DgpRMHPbXaETuLyB.exe (PID: 3180)
- w3uzuiua6giq696w.exe (PID: 7028)
- DgpRMHPbXaETuLyB.exe (PID: 6892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
125
Monitored processes
8
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DgpRMHPbXaETuLyB.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.22553\furry porn\DgpRMHPbXaETuLyB.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.22553\furry porn\DgpRMHPbXaETuLyB.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\furryporn.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6892 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\DgpRMHPbXaETuLyB.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\DgpRMHPbXaETuLyB.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DgpRMHPbXaETuLyB.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\w3uzuiua6giq696w.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\w3uzuiua6giq696w.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | w3uzuiua6giq696w.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7140 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa6384.22109\rconsole.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 421
Read events
7 404
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\furryporn.rar | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
9
Suspicious files
3
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\bin\w3uzuiua6giq696w.exe | executable | |
MD5:193F91181492BA319D598FC904189459 | SHA256:1D1BBD3CDB73685B9E4B9805E9A02134FAD60B16A6304B7D506E2CD70E7C2C49 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\auth.syn | text | |
MD5:FA29B137AF8AB1EF82F686A395024493 | SHA256:3E5FED92976D8258D67BF53B1C935D28FAD036A9788D9C5A08E63B4AB8FC6CB6 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\bin\yxfoz3ob.dll | executable | |
MD5:98440C3C2B623FA950802EA5D781572C | SHA256:16CECE2C20CCCA62D59BFA1BD792EC9199F1FC8095FAAFC64FCBE38ED60C7080 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\launch.syn | text | |
MD5:621179B6726812851D8A9658AF8346E5 | SHA256:02CA01ABD8A4360B8046AA3FE2BB5346A4CC815F3ED70AA71108791EEEB0F3ED | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\workspace\IY_FE.iy | binary | |
MD5:291D5636A434C4F1CEB0F3F776C2A51F | SHA256:73BB58BA5B81960CAF5A8E66675CC89B5761B77DB99C6CEB9435F7211D400452 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\DgpRMHPbXaETuLyB.exe | executable | |
MD5:6336D798F8DA31297D8206BBE0BEECDA | SHA256:F48B31C74516B152AE1CE2B2CF794B726BEA80D85211F2D5FDE1C8460D244E48 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\rconsole.txt | text | |
MD5:9E1ABC908A55B80E58413580AFF4A45E | SHA256:80028F2D78938E9CC6A049BF87C6D7951EB3A5D4055DD0B357B604631E9F8E5A | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\bin\launch.syn | text | |
MD5:621179B6726812851D8A9658AF8346E5 | SHA256:02CA01ABD8A4360B8046AA3FE2BB5346A4CC815F3ED70AA71108791EEEB0F3ED | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.21350\furry porn\bin\w3uzuiua6giq696w.exe | executable | |
MD5:193F91181492BA319D598FC904189459 | SHA256:1D1BBD3CDB73685B9E4B9805E9A02134FAD60B16A6304B7D506E2CD70E7C2C49 | |||
| 6384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.20064\furry porn\bin\rconsole.txt | text | |
MD5:9E1ABC908A55B80E58413580AFF4A45E | SHA256:80028F2D78938E9CC6A049BF87C6D7951EB3A5D4055DD0B357B604631E9F8E5A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
16
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2532 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5028 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2532 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
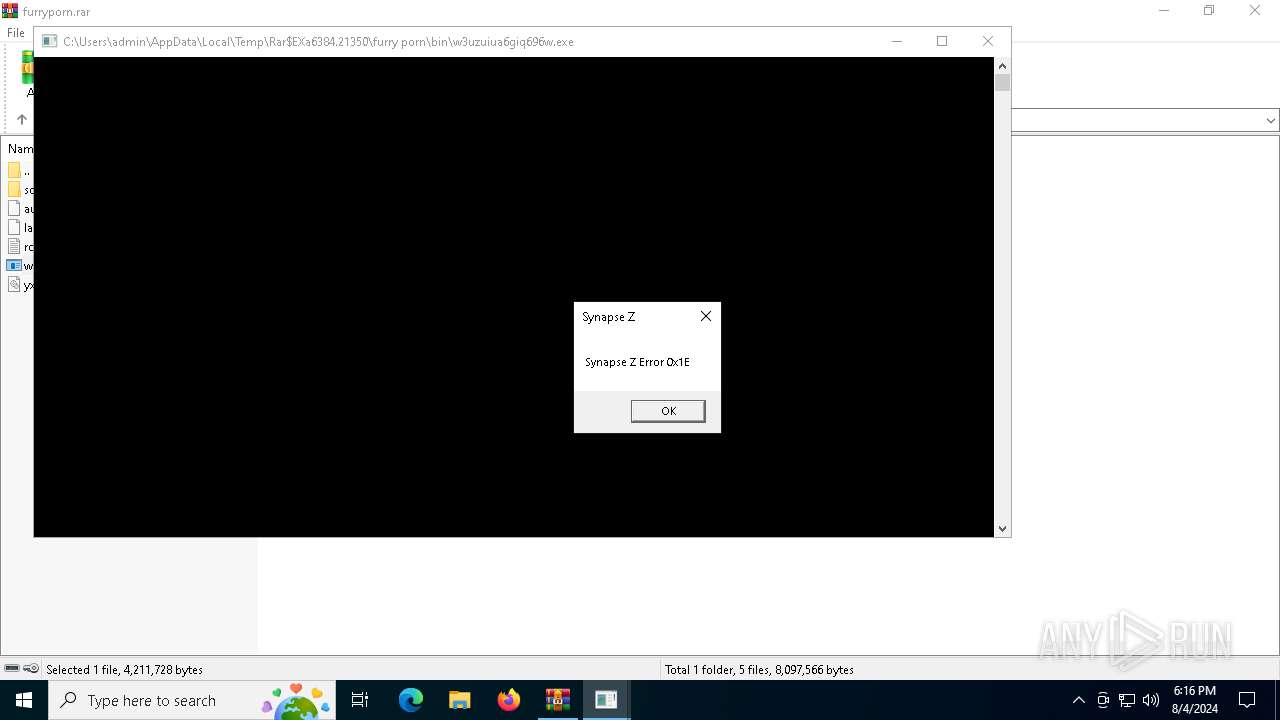
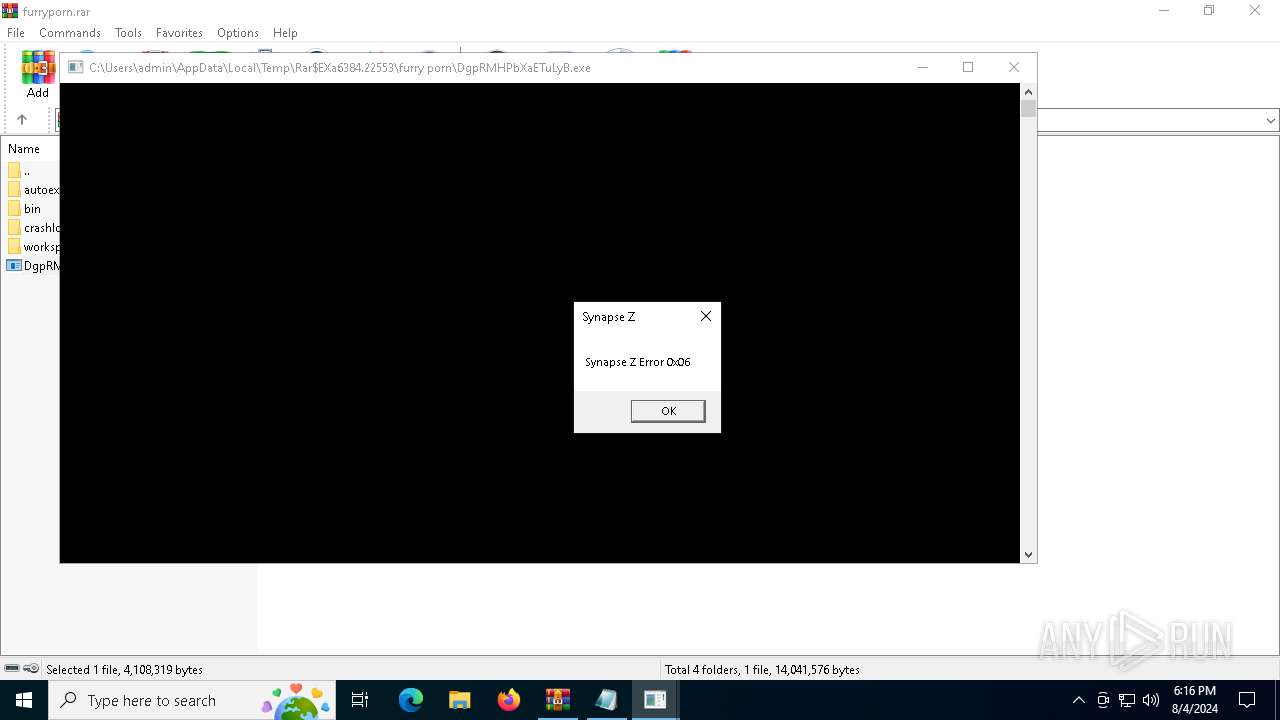
6892 | DgpRMHPbXaETuLyB.exe | 35.156.224.161:443 | synapse-z.netlify.app | AMAZON-02 | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
synapse-z.netlify.app |
| malicious |