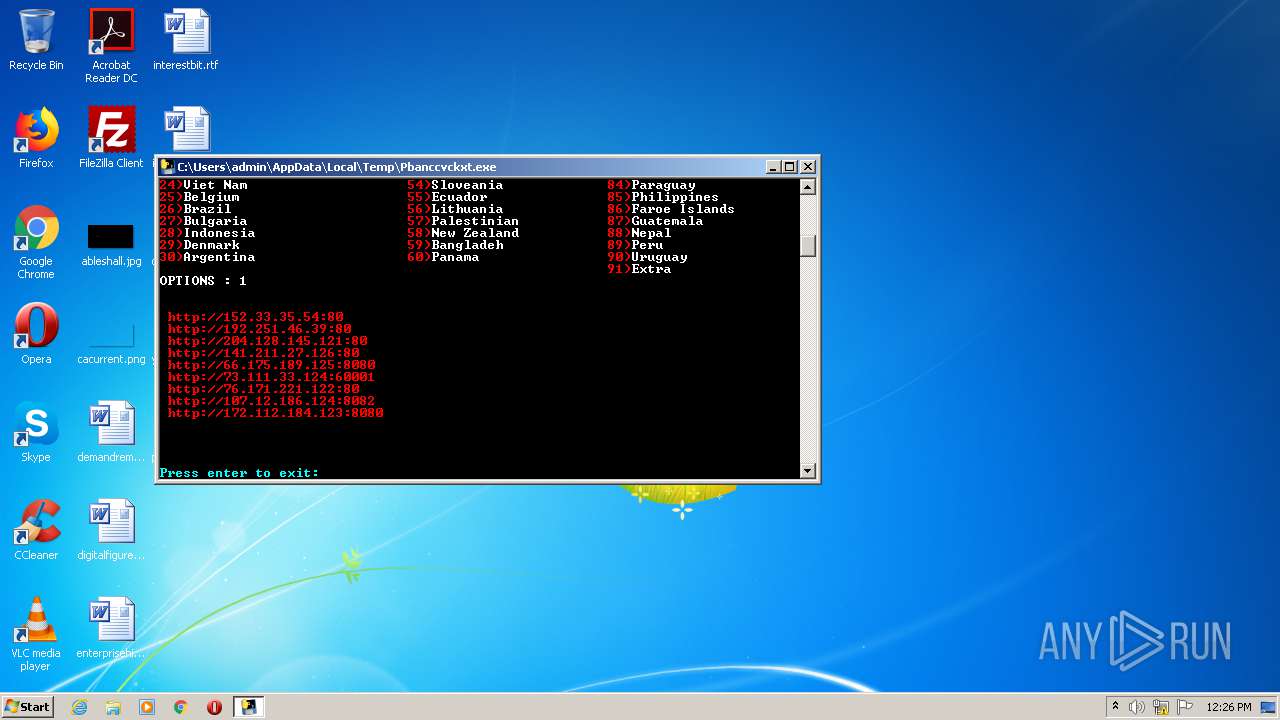
| File name: | IP Camera Hacker.exe |
| Full analysis: | https://app.any.run/tasks/40d0df36-4c65-4260-931c-600a769ffba2 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 11:25:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 0E2A3BA46B9B73C4669301B09BB3FE29 |
| SHA1: | 799CFA43885154E85ACE19E9389E46B987962E9F |
| SHA256: | A4DFA71A80905D73772A6F315C008C1A57B6A59FE01ACD0B61C545FEC4FEBE00 |
| SSDEEP: | 196608:Ggeb1wbrISB9I/woyd9WPatLQl6ygqUtf1C+m3fV89csR:mbSzK/woyFLQlAqUtUbW |
MALICIOUS
Application was dropped or rewritten from another process
- Oskhoajlfv.exe (PID: 3524)
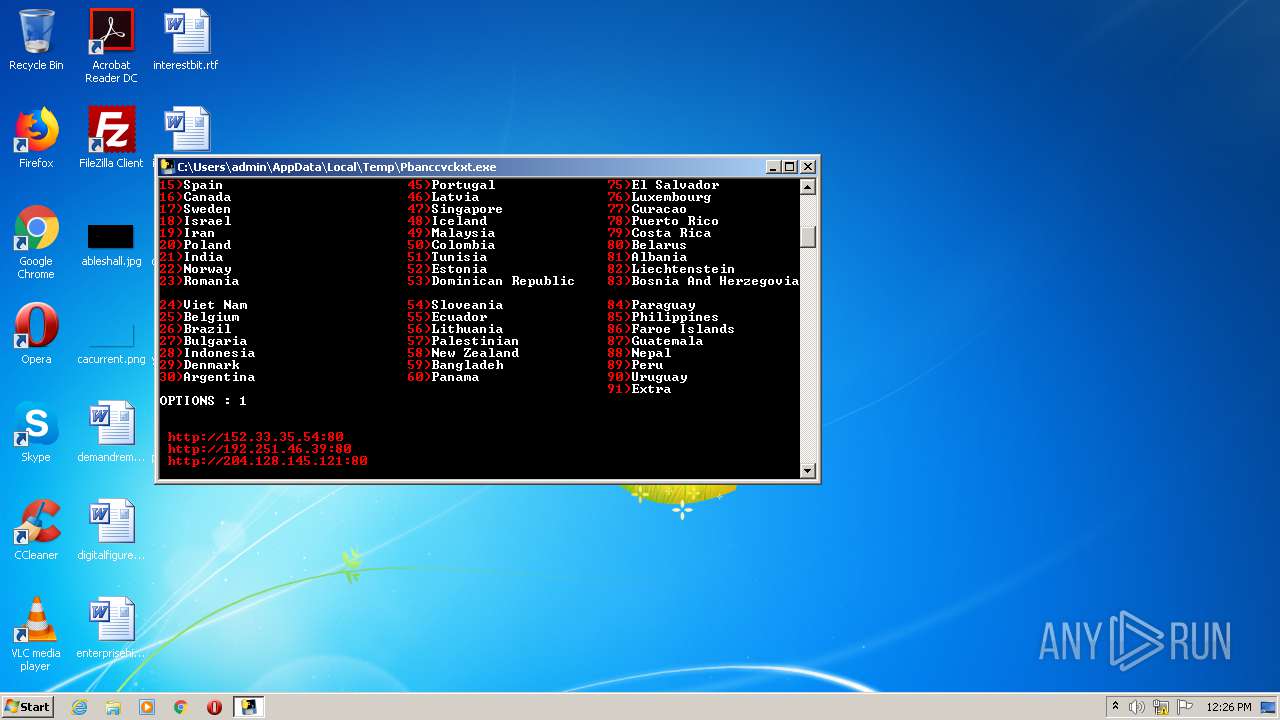
- Pbanccvckxt.exe (PID: 1076)
- Pbanccvckxt.exe (PID: 3972)
- Oskhoajlfv.exe (PID: 1700)
- Oskhoajlfv.exe (PID: 3600)
Loads dropped or rewritten executable
- Pbanccvckxt.exe (PID: 3972)
SUSPICIOUS
Executable content was dropped or overwritten
- IP Camera Hacker.exe (PID: 4084)
- Pbanccvckxt.exe (PID: 1076)
Loads Python modules
- Pbanccvckxt.exe (PID: 3972)
Application launched itself
- Oskhoajlfv.exe (PID: 3524)
- Pbanccvckxt.exe (PID: 1076)
Checks for external IP
- Oskhoajlfv.exe (PID: 3600)
Reads Environment values
- Oskhoajlfv.exe (PID: 3600)
INFO
Dropped object may contain Bitcoin addresses
- Pbanccvckxt.exe (PID: 1076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:27 17:48:01+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 9597440 |
| InitializedDataSize: | 61952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x92901e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | hgjghj.exe |
| LegalCopyright: | |
| OriginalFileName: | hgjghj.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Aug-2020 15:48:01 |
| FileDescription: | - |
| FileVersion: | 0.0.0.0 |
| InternalName: | hgjghj.exe |
| LegalCopyright: | - |
| OriginalFilename: | hgjghj.exe |
| ProductVersion: | 0.0.0.0 |
| Assembly Version: | 0.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 27-Aug-2020 15:48:01 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00927024 | 0x00927200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.99894 |
.rsrc | 0x0092A000 | 0x0000EEF8 | 0x0000F000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.29026 |
.reloc | 0x0093A000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.58652 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 6.05629 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 5.5741 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 7.95079 | 37019 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 5.29119 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 5.43869 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 5.89356 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.72742 | 104 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
41
Monitored processes
6
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1076 | "C:\Users\admin\AppData\Local\Temp\Pbanccvckxt.exe" | C:\Users\admin\AppData\Local\Temp\Pbanccvckxt.exe | IP Camera Hacker.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe" | C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe | — | Oskhoajlfv.exe | |||||||||||
User: admin Company: Free Integrity Level: MEDIUM Description: Free Exit code: 4294967295 Version: 7.2.9.5 Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe" | C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe | — | IP Camera Hacker.exe | |||||||||||
User: admin Company: Free Integrity Level: MEDIUM Description: Free Exit code: 0 Version: 7.2.9.5 Modules
| |||||||||||||||
| 3600 | "C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe" | C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe | Oskhoajlfv.exe | ||||||||||||
User: admin Company: Free Integrity Level: MEDIUM Description: Free Exit code: 0 Version: 7.2.9.5 Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Local\Temp\Pbanccvckxt.exe" | C:\Users\admin\AppData\Local\Temp\Pbanccvckxt.exe | Pbanccvckxt.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\AppData\Local\Temp\IP Camera Hacker.exe" | C:\Users\admin\AppData\Local\Temp\IP Camera Hacker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
429
Read events
403
Write events
26
Delete events
0
Modification events
| (PID) Process: | (4084) IP Camera Hacker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4084) IP Camera Hacker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3600) Oskhoajlfv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Oskhoajlfv_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
26
Suspicious files
3
Text files
916
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4084 | IP Camera Hacker.exe | C:\Users\admin\AppData\Local\Temp\Oskhoajlfv.exe | executable | |
MD5:— | SHA256:— | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_overlapped.pyd | executable | |
MD5:AA428E44A78A280EC8152C43D8284F6F | SHA256:F8FDA2A6E3FF0069E634FEEC4854EE7A8C24134C747DE3211AC2BA26E0188C79 | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_hashlib.pyd | executable | |
MD5:05362ADD80824B06014645A7951337D8 | SHA256:20B3A3D3350B3D4D57911ECFDB15F77512A6E73C3BF72B410724F81C79A5B1AF | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\libffi-7.dll | executable | |
MD5:BC20614744EBF4C2B8ACD28D1FE54174 | SHA256:0C7EC6DE19C246A23756B8550E6178AC2394B1093E96D0F43789124149486F57 | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\libssl-1_1.dll | executable | |
MD5:AD77250DBAA7FAF0C2C9E13D717FAEC7 | SHA256:CCBA760E6607FB6B08215452A8C0B6F84B2CB13937E86514995E9E86352F487A | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_lzma.pyd | executable | |
MD5:54F12E2385A77D825AE4D41A4AC515FE | SHA256:08DE18FBA635822F3BB89C9429F175E3680B7261546430BA9E2ED09BB31F5218 | |||
| 4084 | IP Camera Hacker.exe | C:\Users\admin\AppData\Local\Temp\Pbanccvckxt.exe | executable | |
MD5:F95FB29801EC7411CC6D29ECC035364A | SHA256:9C6CB3E1BF8A2477945E50EFA3497D868E51A840A28238BE4D0181F646E06D07 | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_socket.pyd | executable | |
MD5:CEA329CE0935E99A8BC01070F07FEFAF | SHA256:D1A4D66C557C2FE7DC441614CA62E67F37EC44BEF5A762BAC41BAC15D491A930 | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_ssl.pyd | executable | |
MD5:B9ECF769FC63A542A113CA1552DC7A7B | SHA256:E0BDB16CFFC7B5A19C5AF22D8A33D3C999D55A3117F2DA07ED3171CA9487927E | |||
| 1076 | Pbanccvckxt.exe | C:\Users\admin\AppData\Local\Temp\_MEI10762\_multiprocessing.pyd | executable | |
MD5:8901E96BB7A8EEAD994AF2BDF54A2447 | SHA256:823A96F080A3424F4C5327CF61FF517723E19A69679EBE93EA97061063D8D593 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
9
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3600 | Oskhoajlfv.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 5 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | Pbanccvckxt.exe | 104.18.50.121:443 | www.insecam.org | Cloudflare Inc | US | suspicious |
3600 | Oskhoajlfv.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
3600 | Oskhoajlfv.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
3600 | Oskhoajlfv.exe | 151.101.64.133:443 | raw.githubusercontent.com | Fastly | US | suspicious |
3600 | Oskhoajlfv.exe | 151.101.128.133:443 | raw.githubusercontent.com | Fastly | US | suspicious |
3600 | Oskhoajlfv.exe | 151.101.192.133:443 | raw.githubusercontent.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.insecam.org |
| malicious |
ip-api.com |
| malicious |
raw.githubusercontent.com |
| shared |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3600 | Oskhoajlfv.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3600 | Oskhoajlfv.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3600 | Oskhoajlfv.exe | Misc activity | SUSPICIOUS [PTsecurity] External IP Lookup |