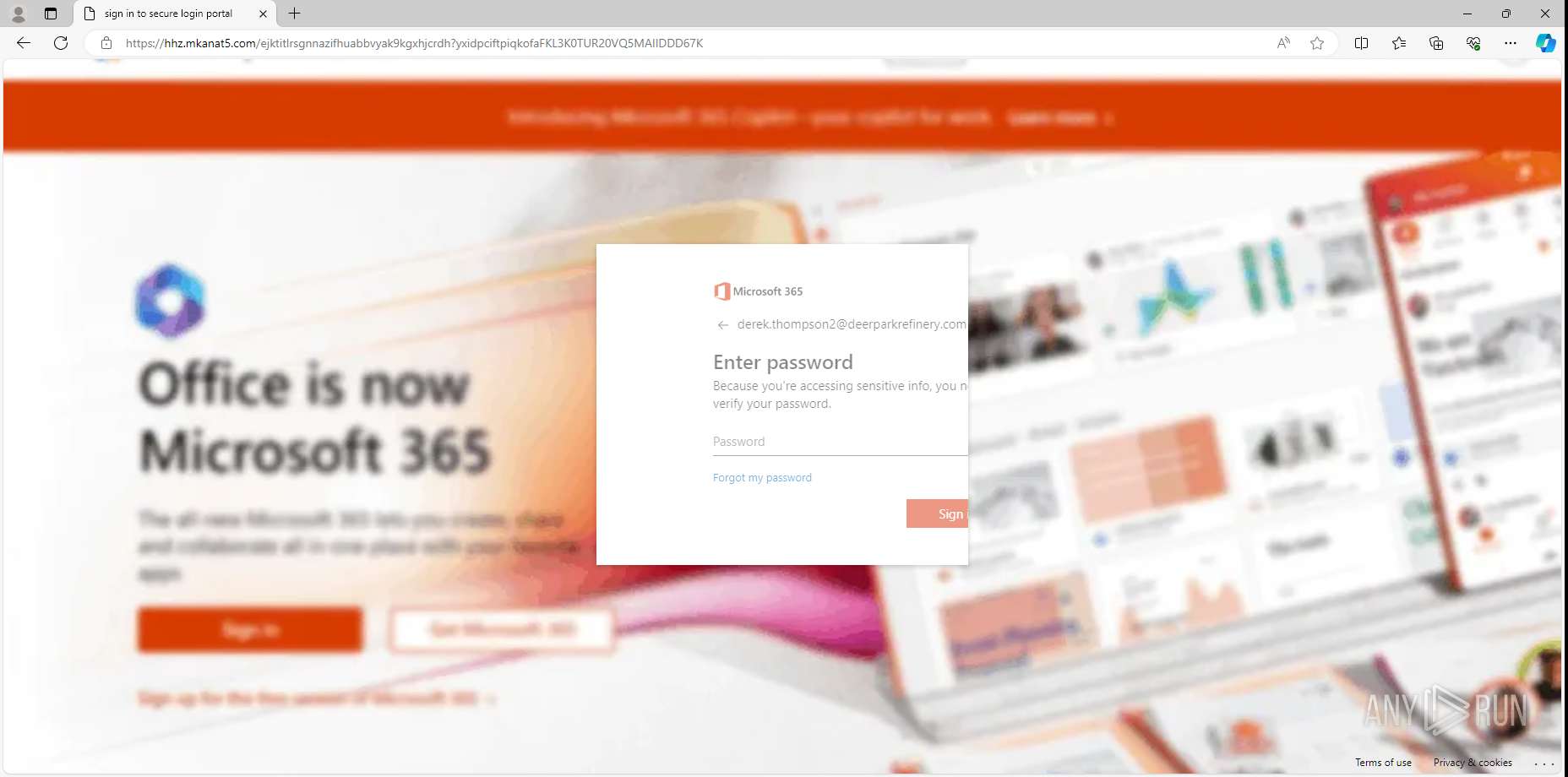
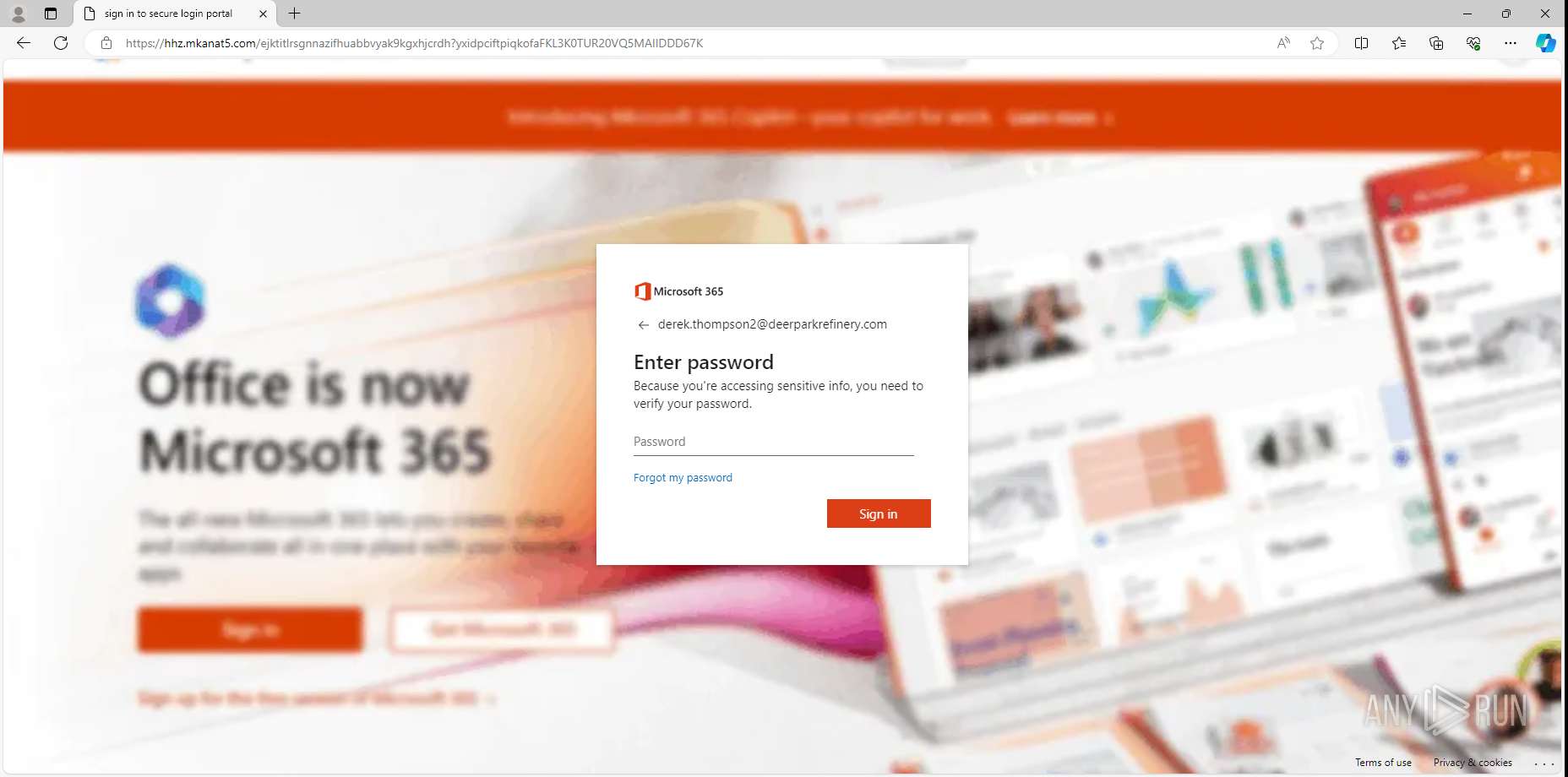
| URL: | https://hhz.mkanat5.com/9iS8P9dY3KtEim2OVzLqY/#[email protected] |
| Full analysis: | https://app.any.run/tasks/7867ca3b-9e9b-4157-9bf6-b07c62a51d45 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 18:38:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3DC05C584452BC391440F8E0F9063C68 |
| SHA1: | AAD988D0693772DB47C1D24886E4D4582BD22FD5 |
| SHA256: | A4C933A783E852917F1FEFB01A14D8DA36B10D25FDA18380CC1A048D97A0A86B |
| SSDEEP: | 3:N8xf/R0t23JpRJqi6brQwdnF+4mMu6K:2ZZnAi6fPdF0Mu6K |
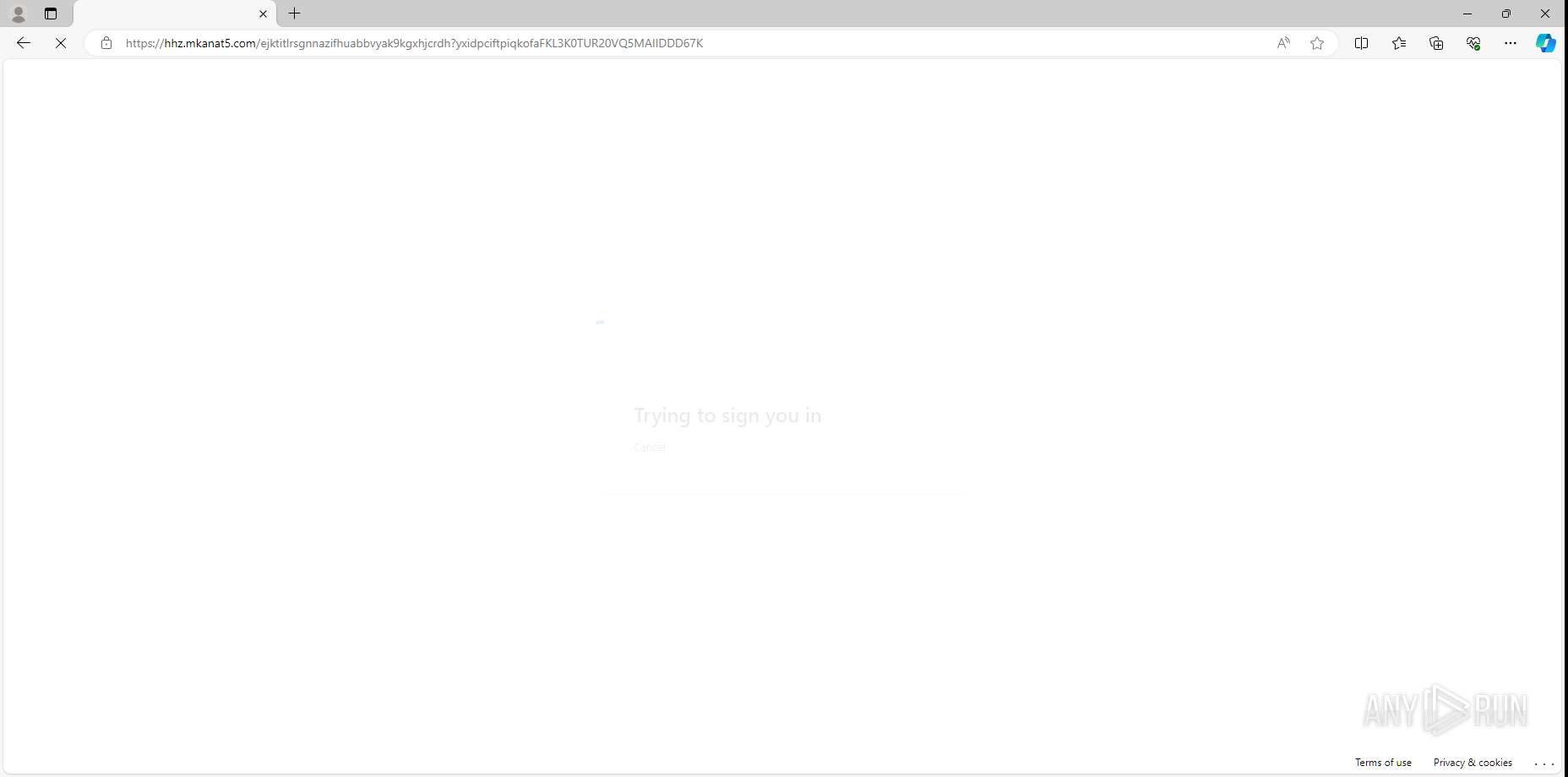
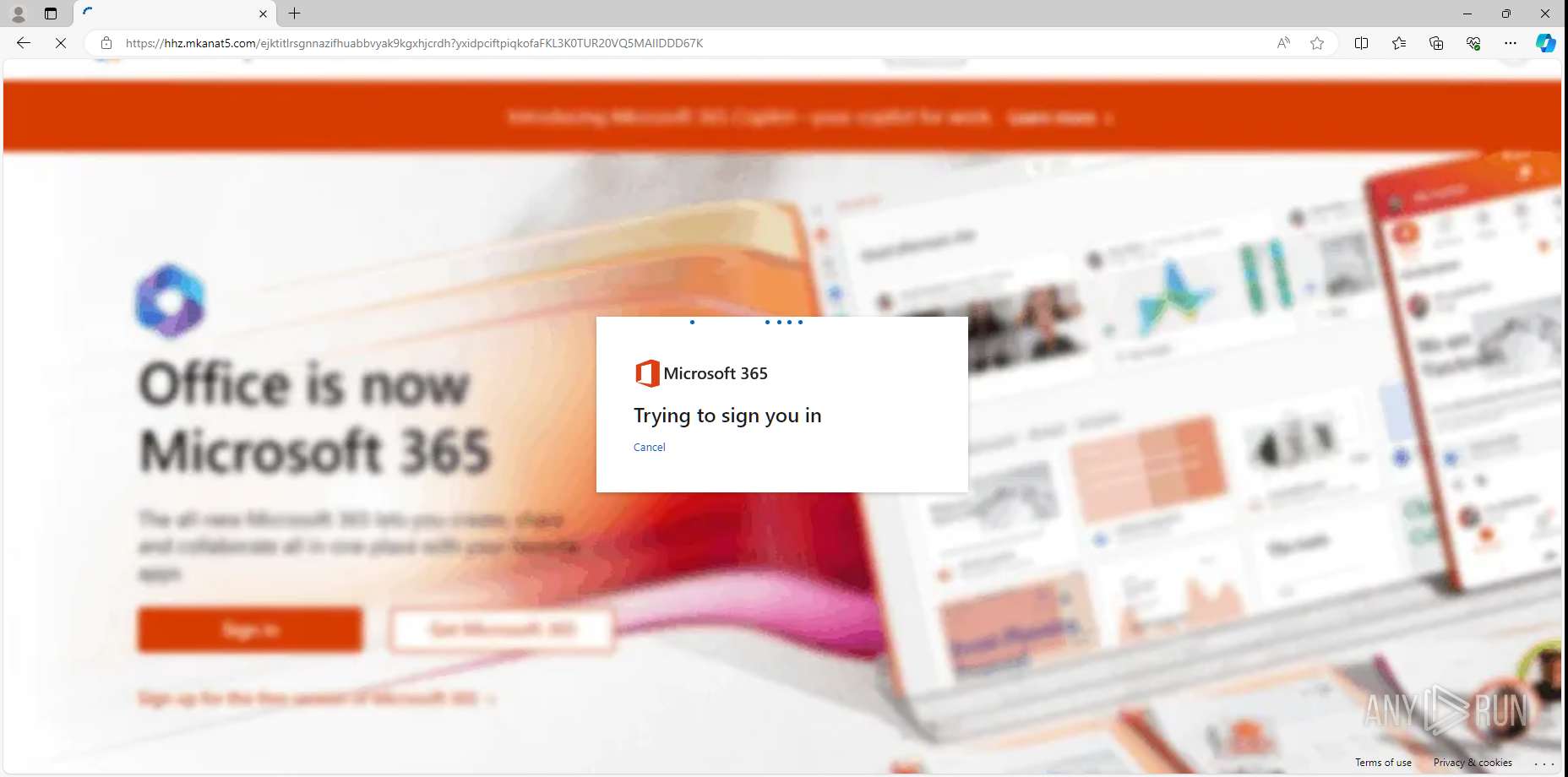
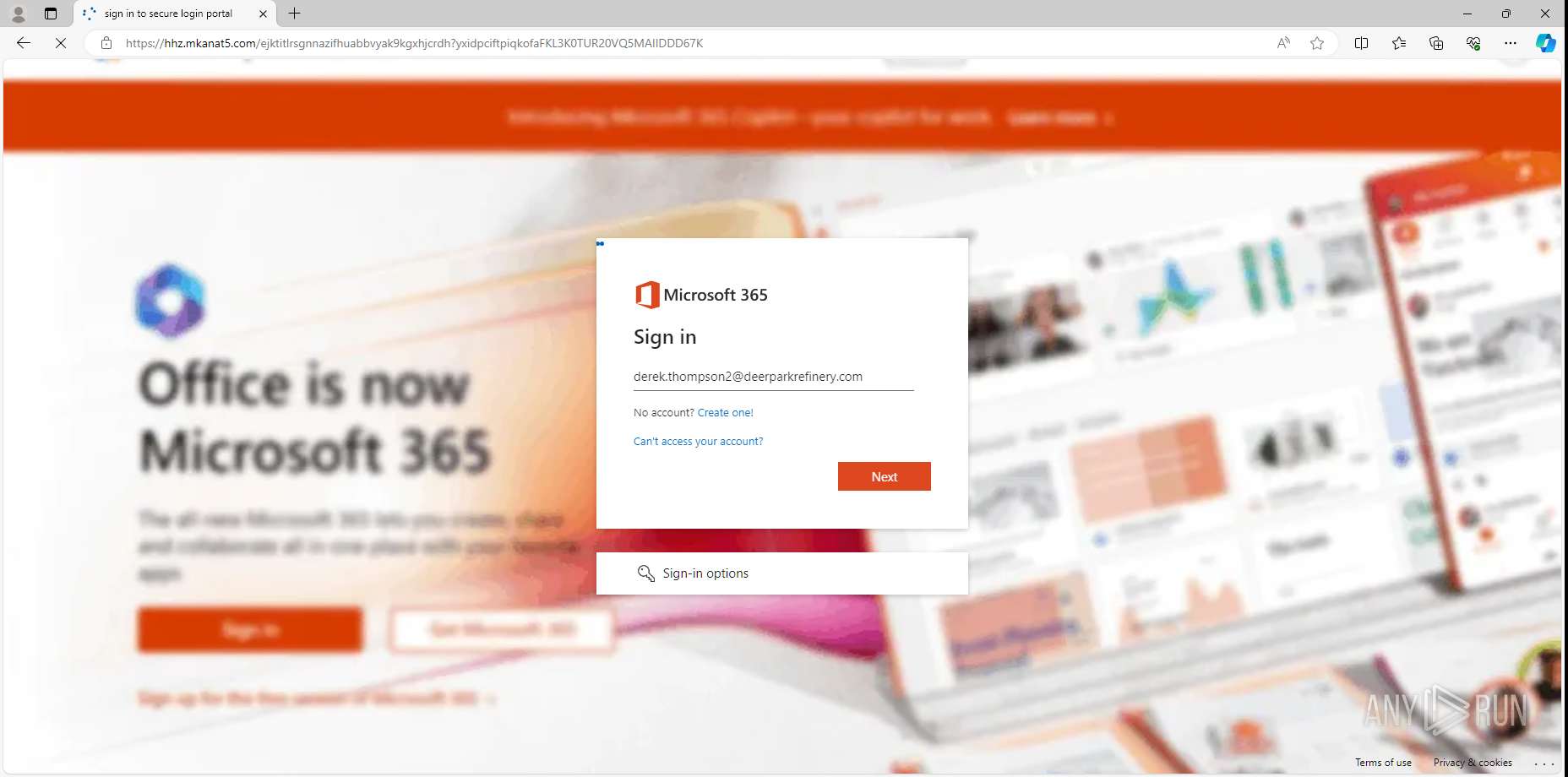
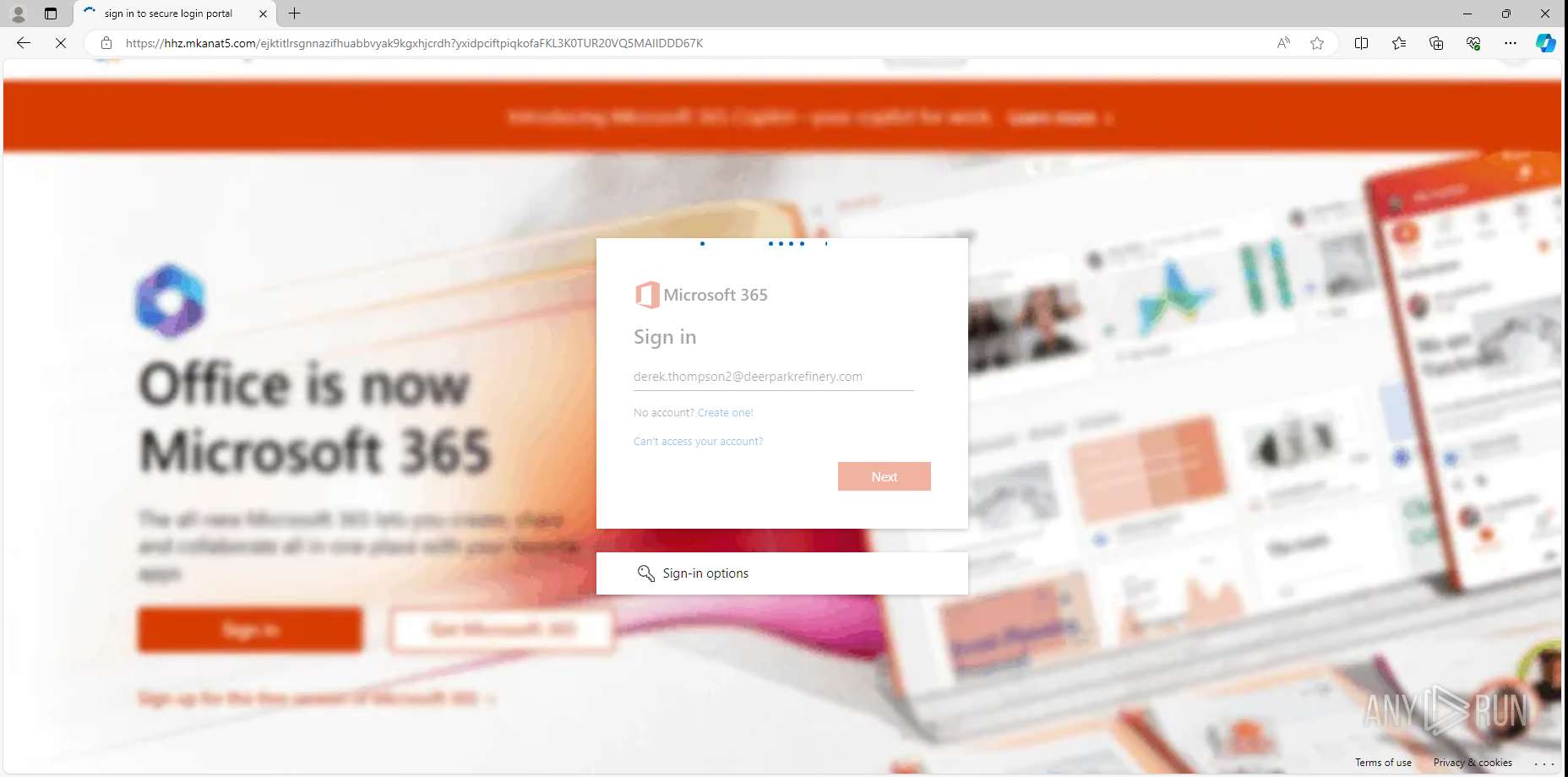
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4792)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
25
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State | binary | |
MD5:ED74D0CC3CAB53CA501F3CD6C50FAA1A | SHA256:331BB0DA5A3BE7843A14503DA9547E7309F3631916C6112882FF36D75025E7EE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c7 | image | |
MD5:4B52ECDC33382C9DCA874F551990E704 | SHA256:CCE050CC3B150C0B370751021BB15018EE2B64AC369E230FE3B571A9B00D4342 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c6 | image | |
MD5:F9A795E2270664A7A169C73B6D84A575 | SHA256:D00203B2EEA6E418C31BAAFA949ADA5349A9F9B7E99FA003AEC7406822693740 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c0 | compressed | |
MD5:65C8E946B531157A11540468B5AC0047 | SHA256:4E8970B4FDC306A25683625031983483FDB8EF809F7F2539C64120D13772EA18 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\c7ad1262-26a6-4787-b5ce-e1c200b06574.tmp | binary | |
MD5:ED74D0CC3CAB53CA501F3CD6C50FAA1A | SHA256:331BB0DA5A3BE7843A14503DA9547E7309F3631916C6112882FF36D75025E7EE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2b5fc2.TMP | binary | |
MD5:2A21453795942FD88CBB06714604B9FD | SHA256:5DFE0384325B556EE4B8668E502312B9BA6ADC298CD9213DDFA528CB959ADC06 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity | binary | |
MD5:BFF96D9F5E50A0E0677A3AD72C67180D | SHA256:C244380400F81655A5FAB5CDE2EE90E54AE89FC06D0240E696E113D6E2081CBF | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c5 | binary | |
MD5:A4BCA6C95FED0D0C5CC46CF07710DCEC | SHA256:5A51D246AF54D903F67F07F2BD820CE77736F8D08C5F1602DB07469D96DBF77F | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c3 | binary | |
MD5:BCD7983EA5AA57C55F6758B4977983CB | SHA256:6528A0BF9A836A53DFD8536E1786BA6831C9D1FAA74967126FDDF5B2081B858C | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bf | binary | |
MD5:17081510F3A6F2F619EC8C6F244523C7 | SHA256:2C7292014E2EF00374AEB63691D9F23159A010455784EE0B274BA7DB2BCCA956 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
61
DNS requests
39
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.213.164.137:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
3804 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6084 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 302 | 104.18.95.41:443 | https://challenges.cloudflare.com/turnstile/v0/api.js?render=explicit | unknown | — | — | — |
3804 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6084 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/fent/randexp.js/releases/download/v0.4.3/randexp.min.js | unknown | — | — | — |
— | — | OPTIONS | 200 | 35.190.80.1:443 | https://a.nel.cloudflare.com/report/v4?s=V4szKsbZG9mFlvY3oUeqLWcnqfqEDp55mo3VTMjPSL2mNIoppM2GubyBqzEynaRQiVEYCl0WtmAbtul5Y5%2BVlbqXTIQUNBHRviPCEAZhsWRQemZyjxNI3yPOTrvICg%3D%3D | unknown | — | — | — |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4792 | msedge.exe | 13.89.179.8:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
3804 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6084 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4304 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4792 | msedge.exe | 188.114.96.3:443 | hhz.mkanat5.com | CLOUDFLARENET | NL | unknown |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4792 | msedge.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | — | — | whitelisted |
4792 | msedge.exe | 104.18.94.41:443 | challenges.cloudflare.com | — | — | whitelisted |
6812 | svchost.exe | 23.213.164.137:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
hhz.mkanat5.com |
| unknown |
fs.microsoft.com |
| whitelisted |
code.jquery.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .mkanat5 .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .mkanat5 .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .avzcafe .ru) |