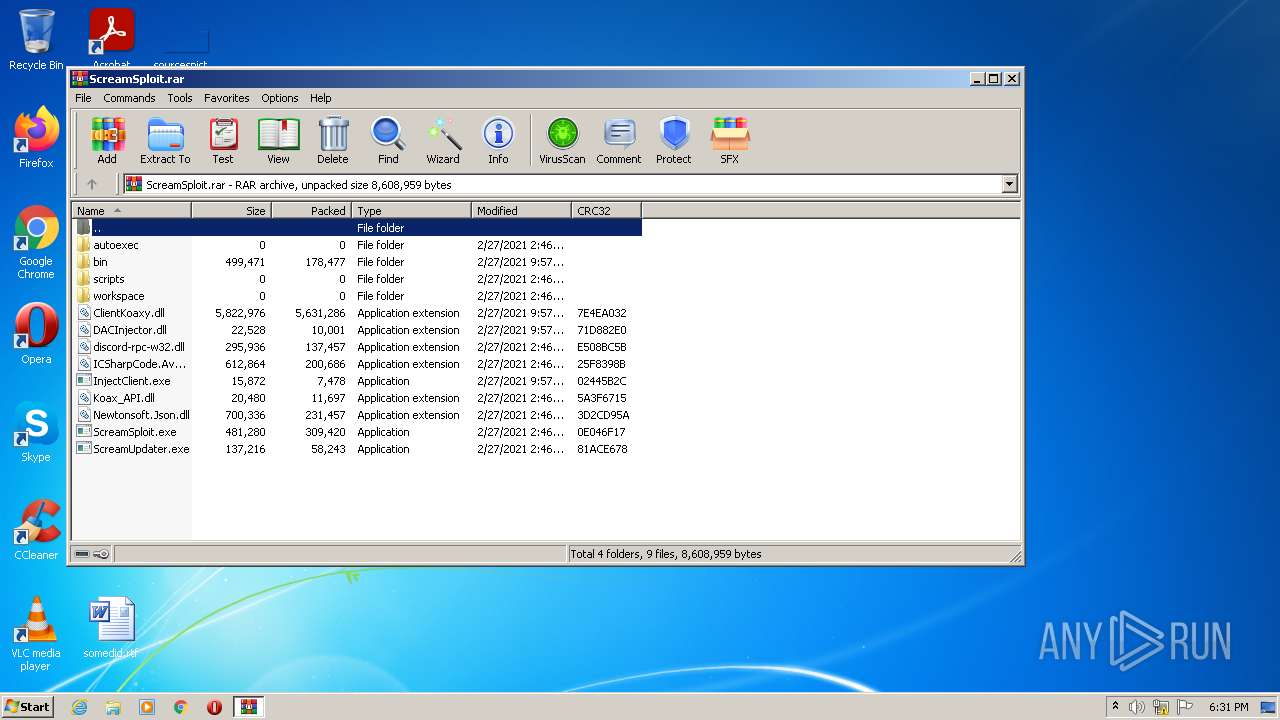
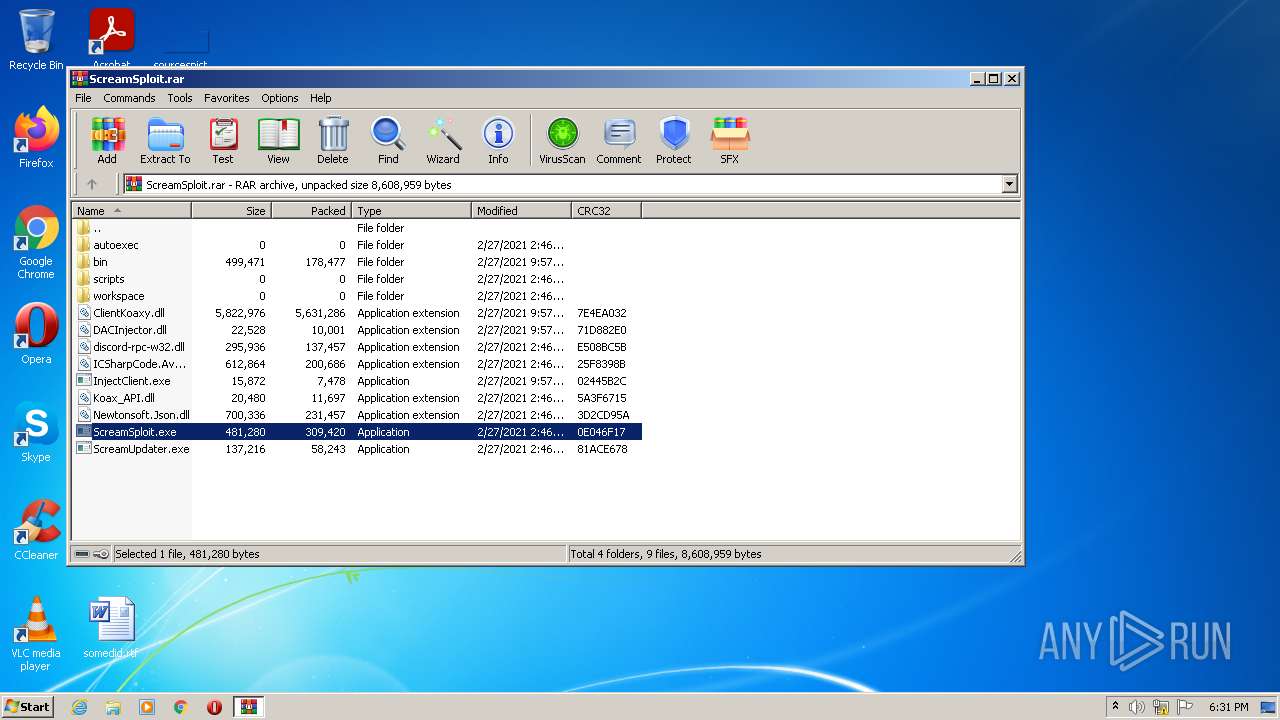
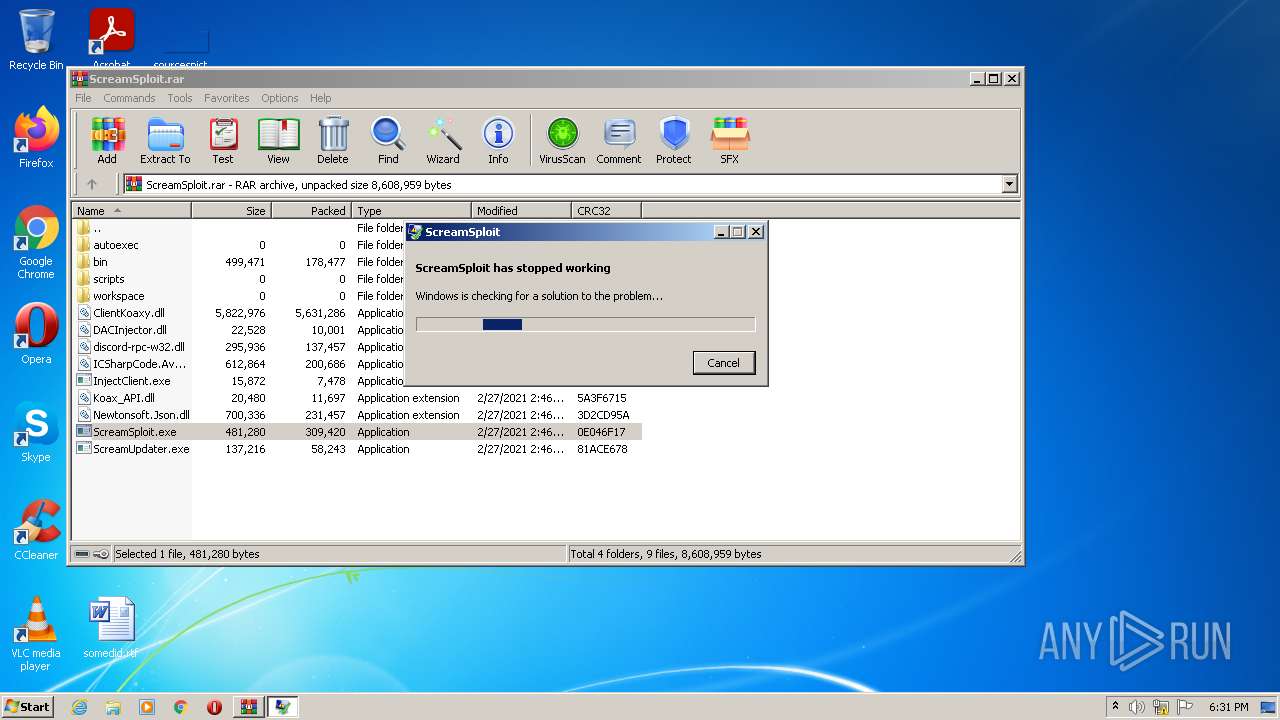
| File name: | ScreamSploit.rar |
| Full analysis: | https://app.any.run/tasks/54bdd423-7b4b-4249-bc19-470f49d25856 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2022, 18:30:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 38C1D5688A42FBFC7CEC86B30226FE4B |
| SHA1: | 1DD1C77B213C8C7AA82FA6EC7D3AAFCE375EDBAA |
| SHA256: | A4ADE98C1CE00D909C690DE906B7D8BBD2D6810031E1C5EB723569A4672E18A2 |
| SSDEEP: | 98304:JR/zj5kgYs0NOMaITTxFhewE/vDEpWj0GIM+HeQzxjeBeZdyOy4aGcg:JR/SgY4XDE89++QzxDyUT |
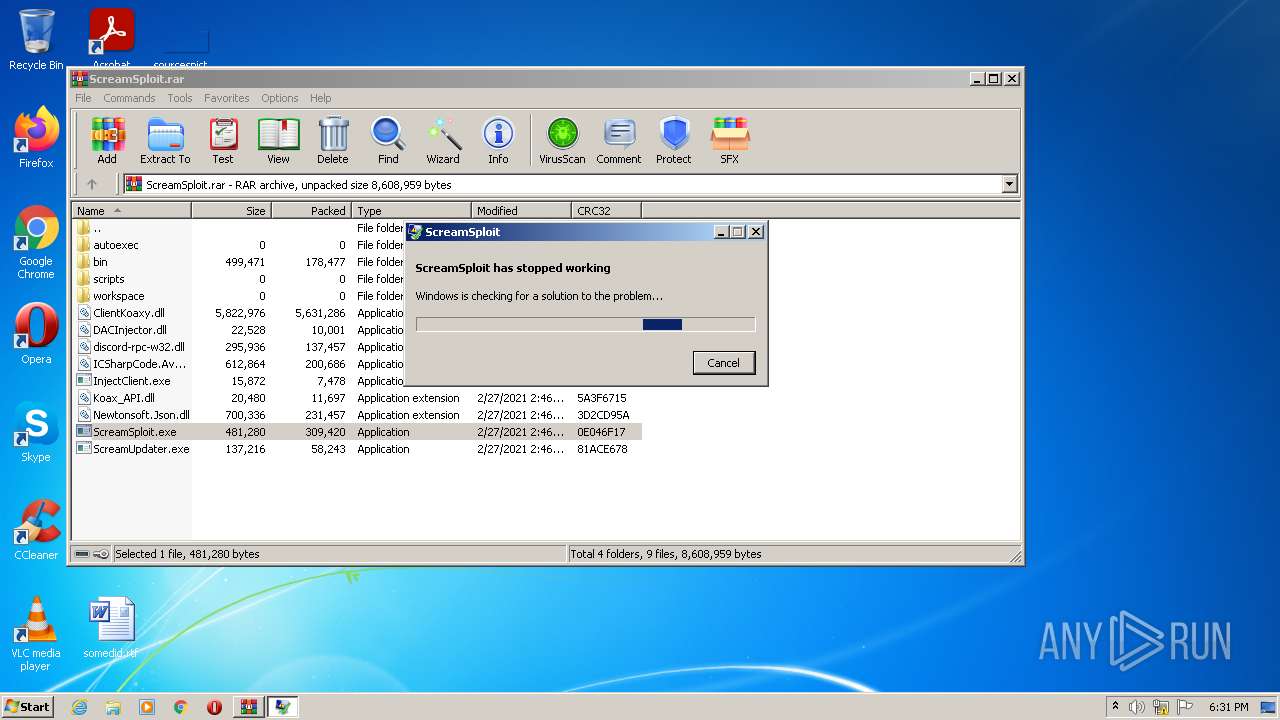
MALICIOUS
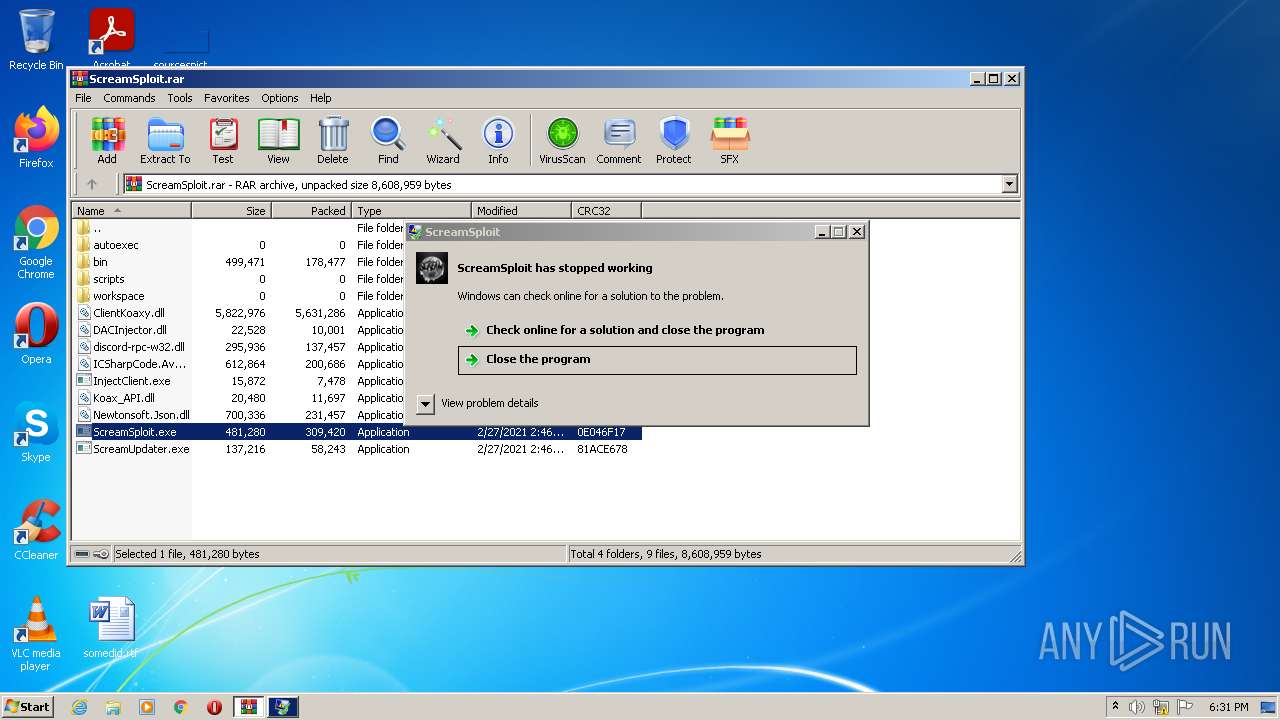
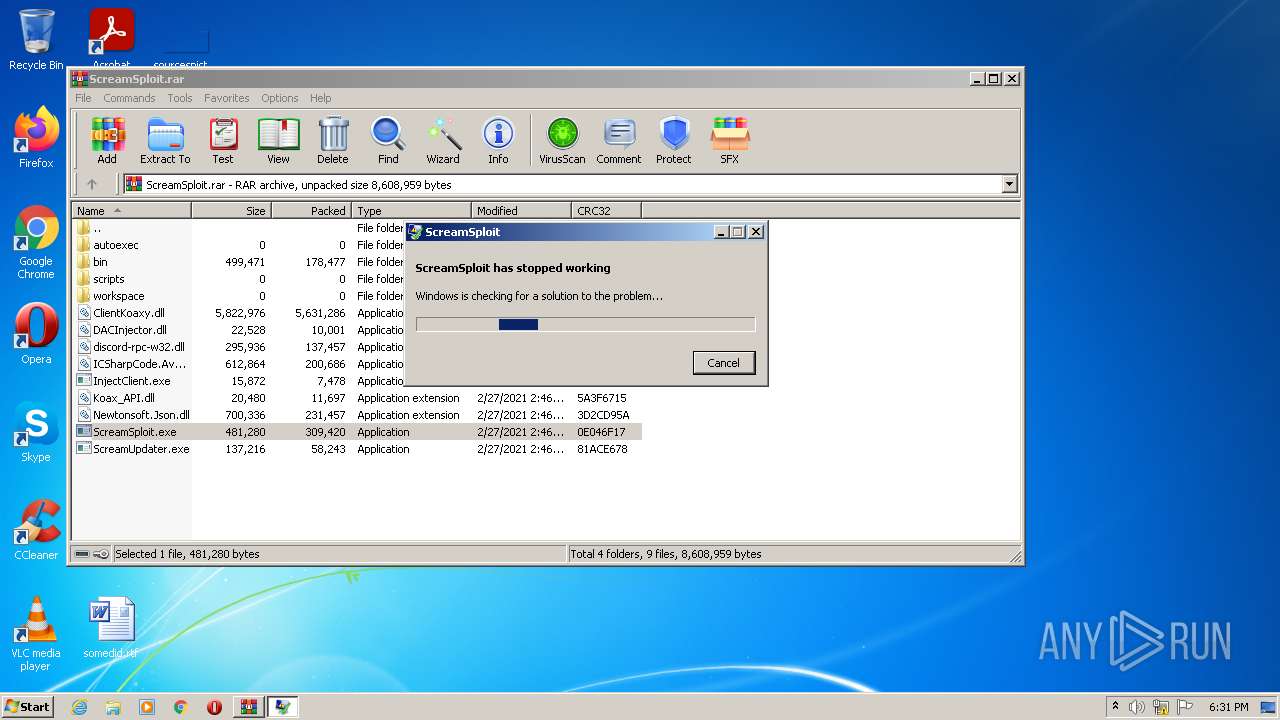
Application was dropped or rewritten from another process
- ScreamSploit.exe (PID: 3992)
Loads dropped or rewritten executable
- WerFault.exe (PID: 1488)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3380)
Checks supported languages
- WinRAR.exe (PID: 3380)
- ScreamSploit.exe (PID: 3992)
Reads the computer name
- WinRAR.exe (PID: 3380)
- ScreamSploit.exe (PID: 3992)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3380)
Reads Environment values
- ScreamSploit.exe (PID: 3992)
- WerFault.exe (PID: 1488)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3380)
INFO
Checks supported languages
- WerFault.exe (PID: 1488)
Reads the computer name
- WerFault.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | C:\Windows\system32\WerFault.exe -u -p 3992 -s 1108 | C:\Windows\system32\WerFault.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3380 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ScreamSploit.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.12482\ScreamSploit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.12482\ScreamSploit.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ScreamSploit Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 030
Read events
2 000
Write events
30
Delete events
0
Modification events
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ScreamSploit.rar | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
10
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERA9DD.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERC286.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_ScreamSploit.exe_407e1e3c47cb3d1773ba269454ddc6eeb5196a67_cab_05c4c3bc\WERA9DD.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_ScreamSploit.exe_407e1e3c47cb3d1773ba269454ddc6eeb5196a67_cab_05c4c3bc\WERC286.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_ScreamSploit.exe_407e1e3c47cb3d1773ba269454ddc6eeb5196a67_cab_05c4c3bc\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\ScreamSploit.exe.3992.dmp | — | |
MD5:— | SHA256:— | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.12482\Koax_API.dll | executable | |
MD5:— | SHA256:— | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.12482\InjectClient.exe | executable | |
MD5:— | SHA256:— | |||
| 1488 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERA9BC.tmp.appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 3380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3380.12482\bin\lua_highlighting.xshd | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1488 | WerFault.exe | 13.89.179.12:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
1488 | WerFault.exe | 52.168.117.173:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
— | — | 13.89.179.12:443 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
3992 | ScreamSploit.exe | 185.199.111.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
watson.microsoft.com |
| whitelisted |