| File name: | Scan Copy.xls |
| Full analysis: | https://app.any.run/tasks/4e76fd53-c449-4ee0-8f06-5833d7007d87 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2022, 14:40:30 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: ismail - [2010], Last Saved By: ismail - [2010], Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Aug 9 14:30:37 2021, Last Saved Time/Date: Tue Feb 15 07:21:27 2022, Security: 0 |
| MD5: | 92A78894568E2E7869EF7EC454C52DB3 |
| SHA1: | 6987E216D2B7477F593569576BABBB499AAB2E94 |
| SHA256: | A49BB6F6BE5B597CD7AC592FAA01F857060F3694C1BED69F8C8C0CC029B70069 |
| SSDEEP: | 3072:3lxEtjPOtioVjDGUU1qfDlaGGx+cL2QnA6UfctdlXjWhfThC/KjM6u:VxEtjPOtioVjDGUU1qfDlavx+W2QnA17 |
MALICIOUS
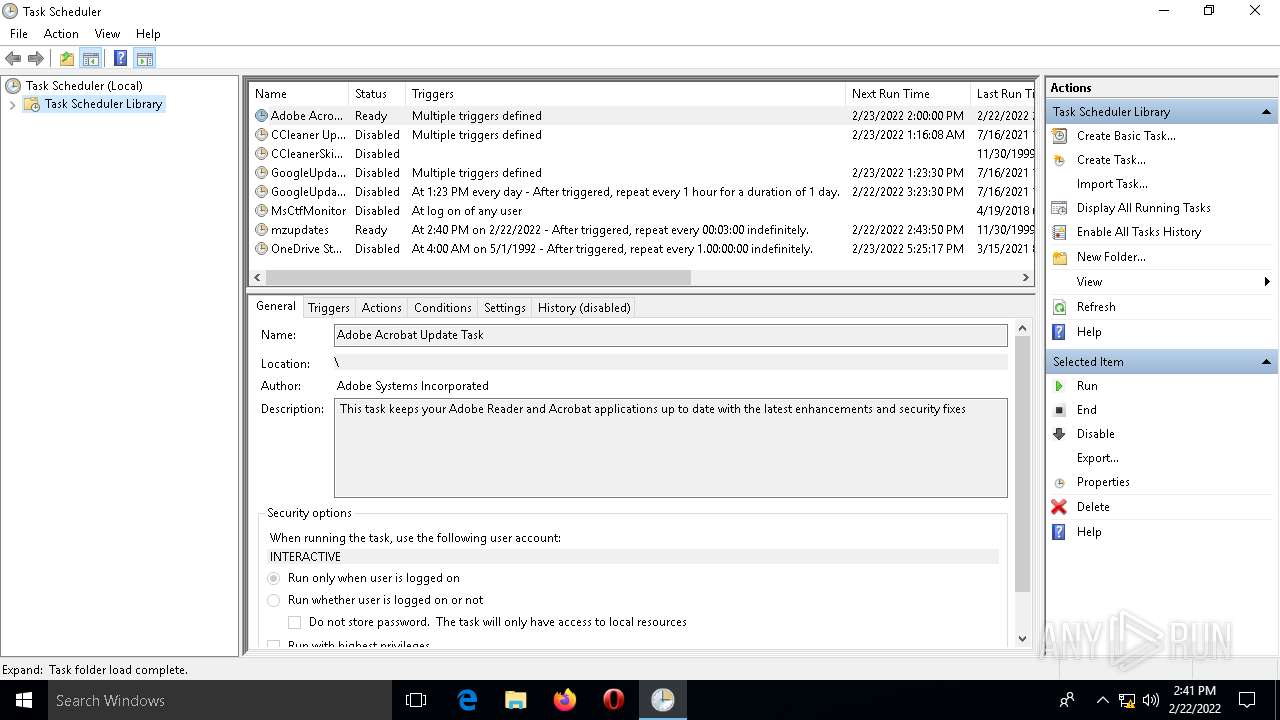
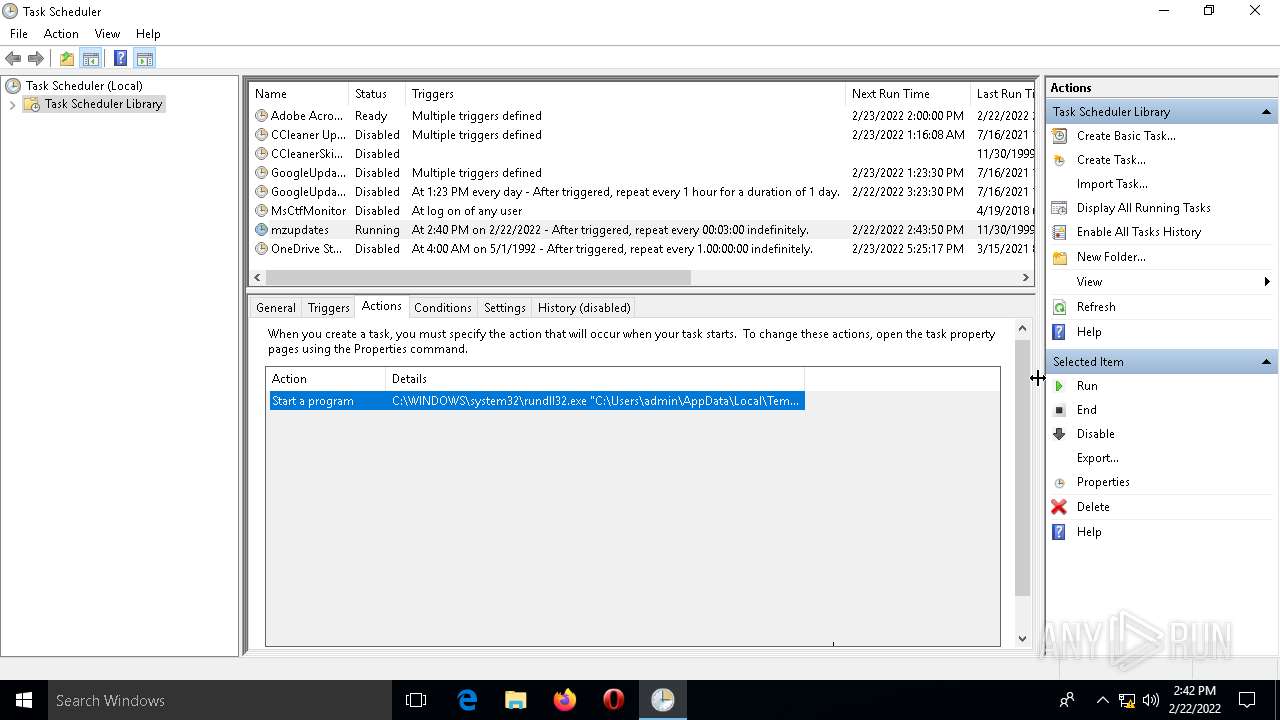
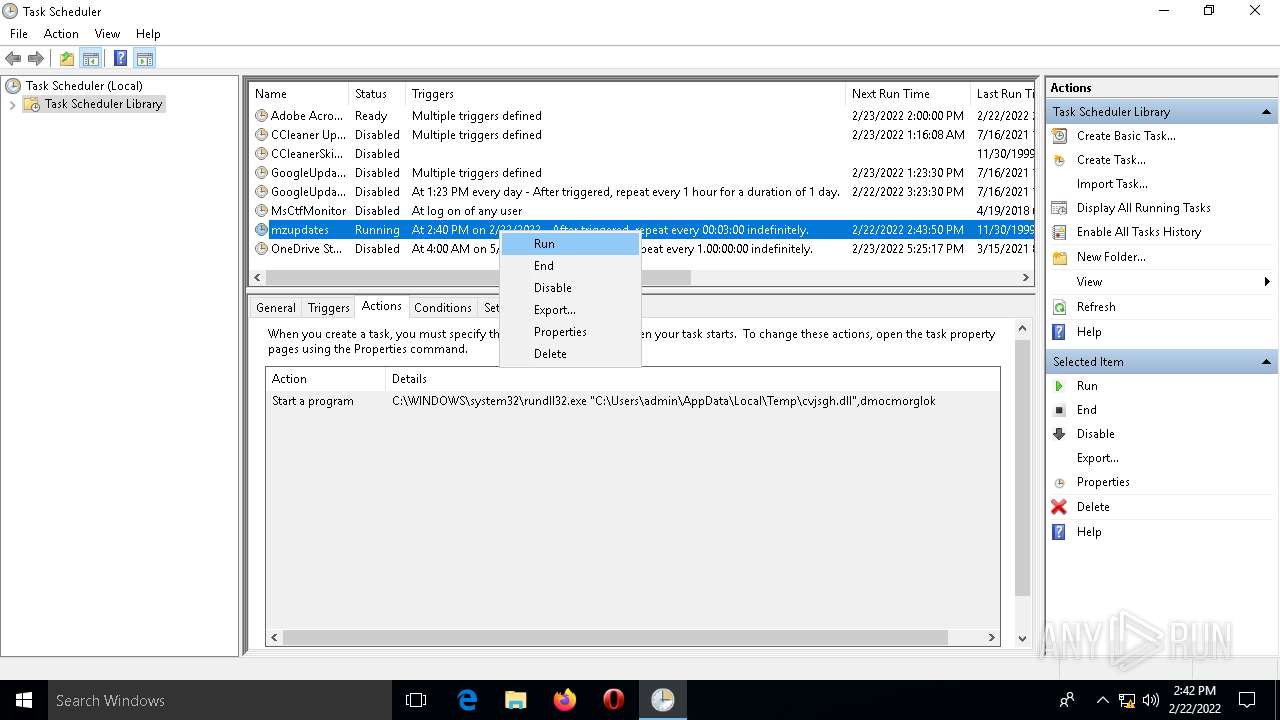
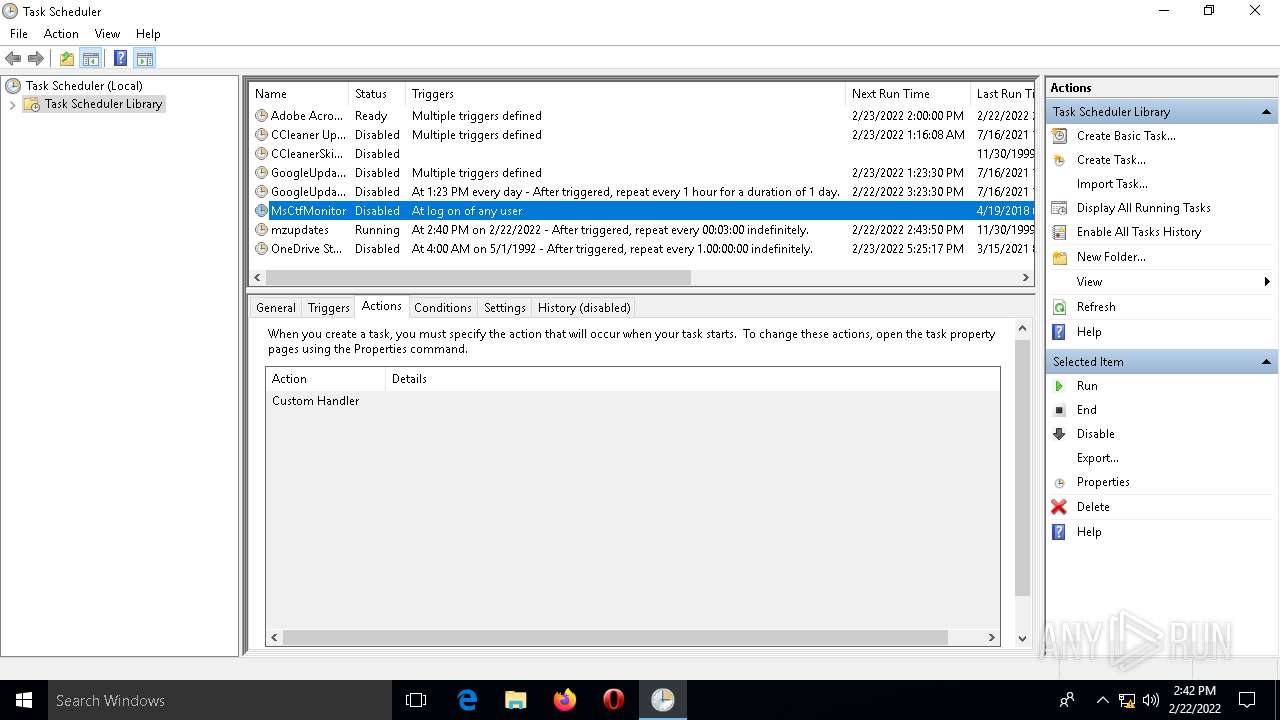
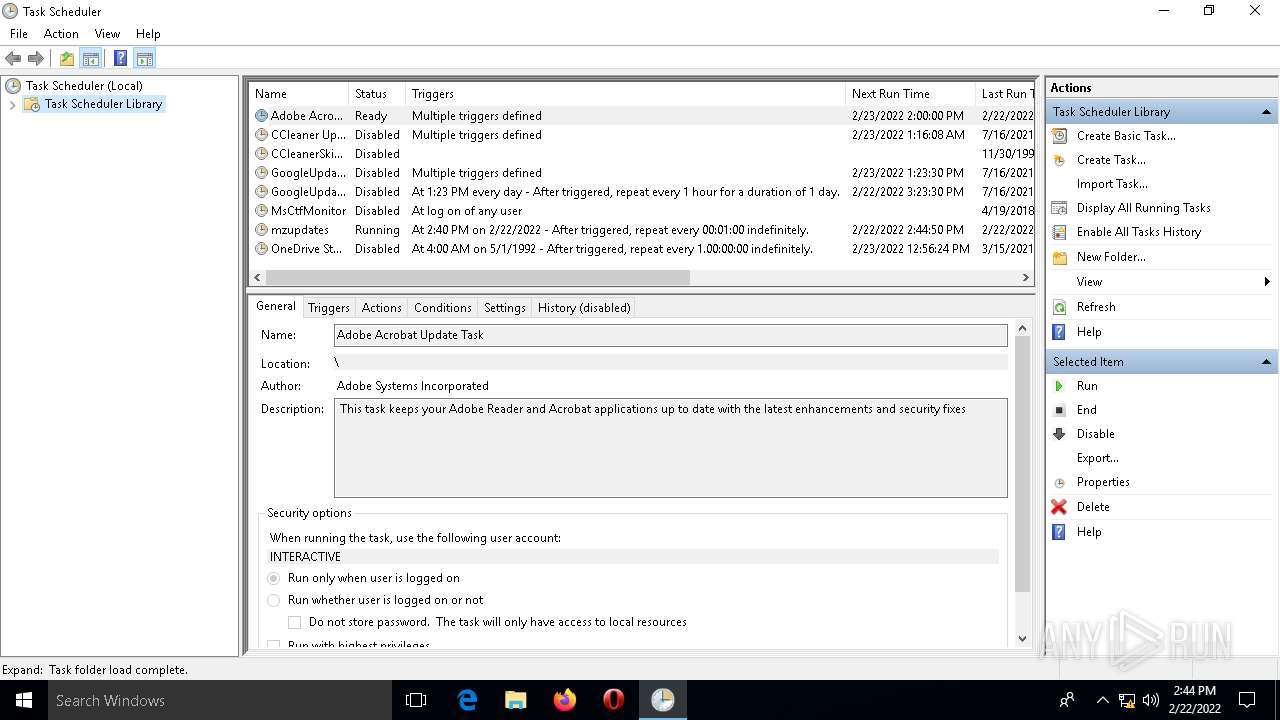
Loads the Task Scheduler COM API
- EXCEL.EXE (PID: 2532)
- mmc.exe (PID: 5688)
- SCHTASKS.exe (PID: 2860)
- mmc.exe (PID: 4772)
Loads dropped or rewritten executable
- EXCEL.EXE (PID: 2532)
- rundll32.exe (PID: 5912)
- rundll32.exe (PID: 5428)
- rundll32.exe (PID: 1284)
- rundll32.exe (PID: 680)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 2532)
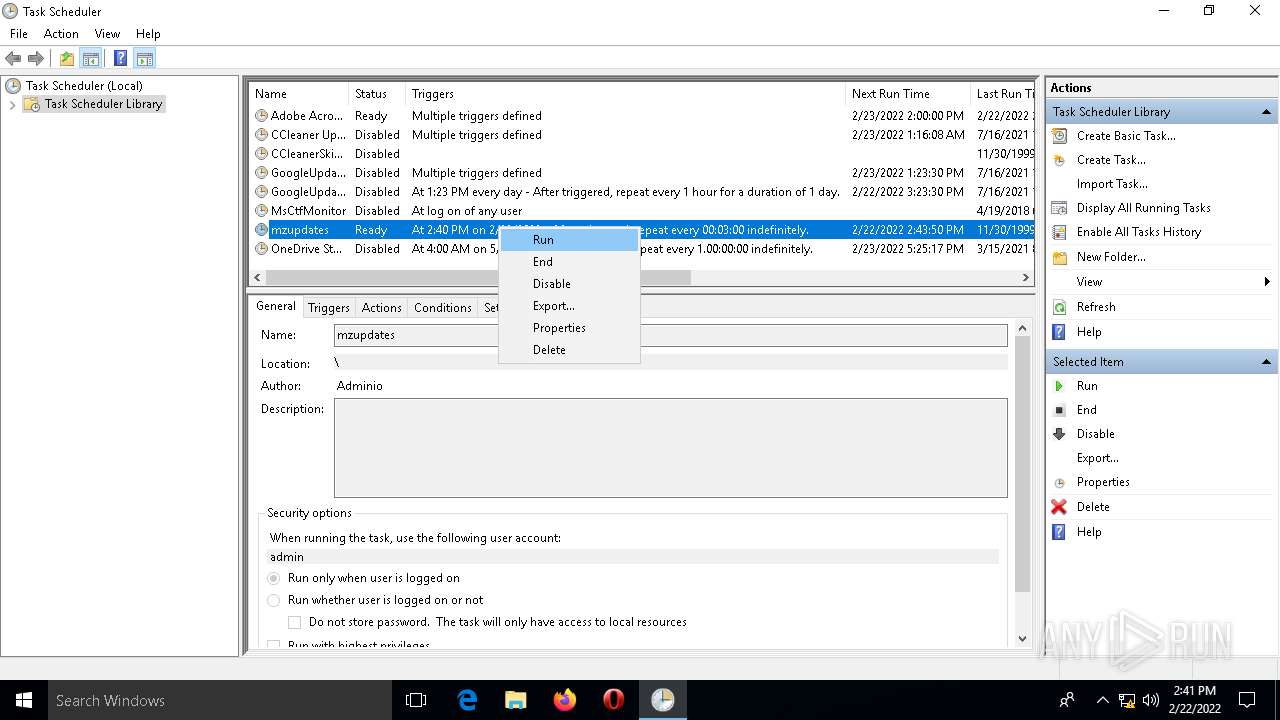
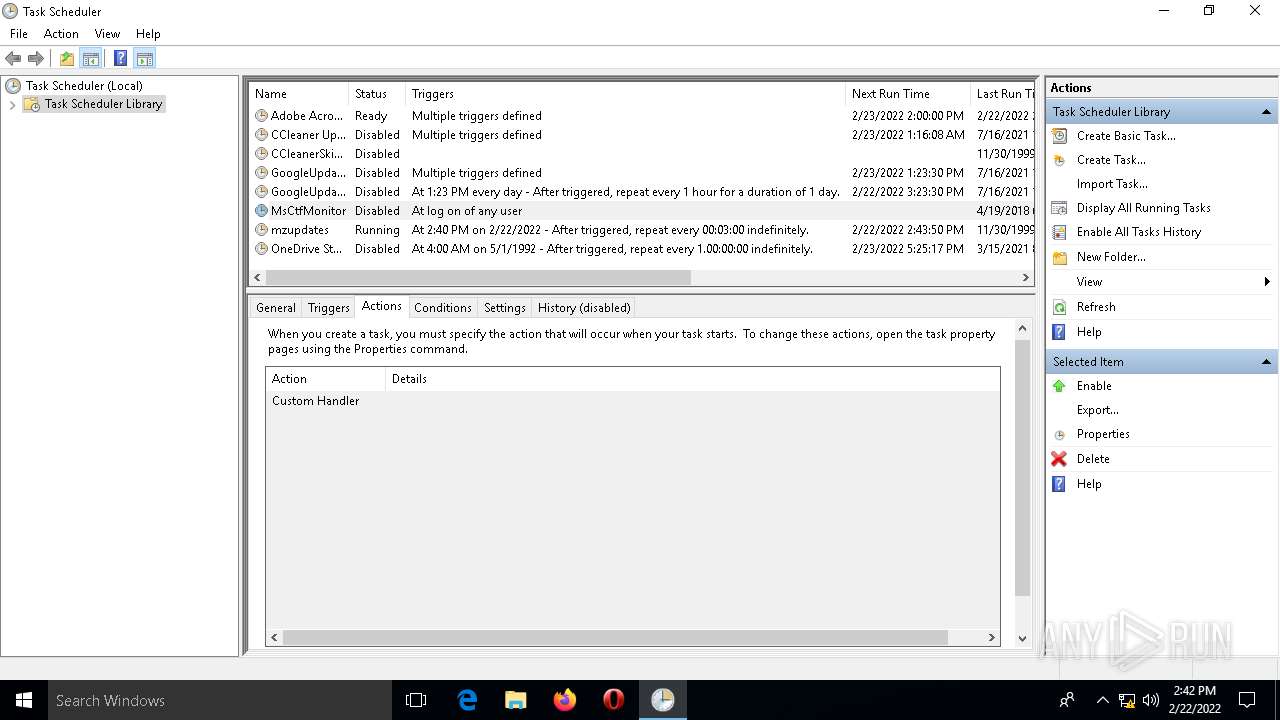
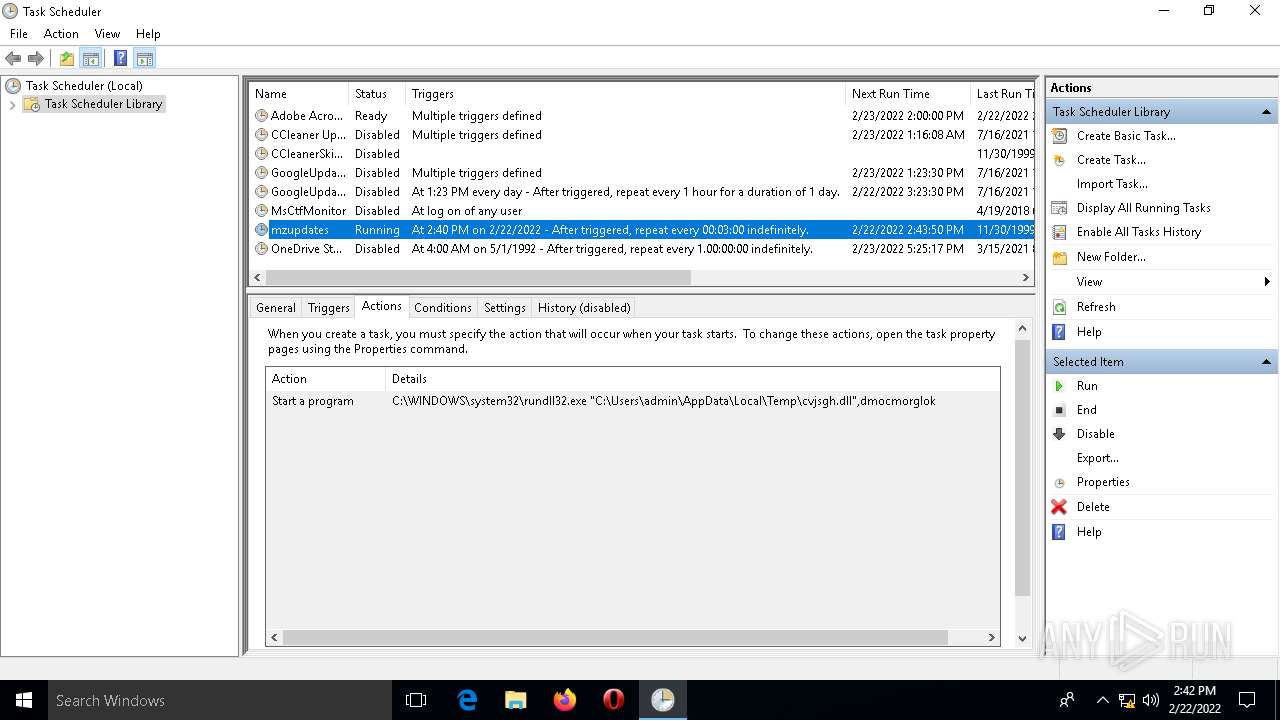
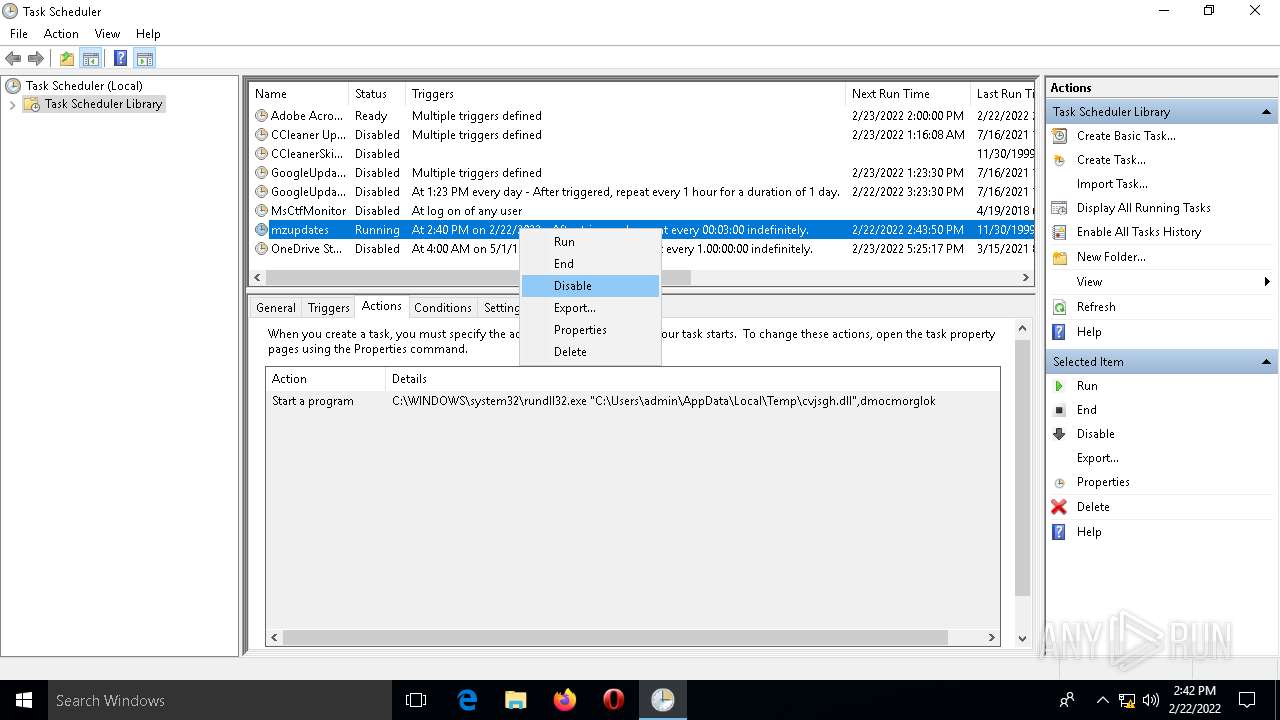
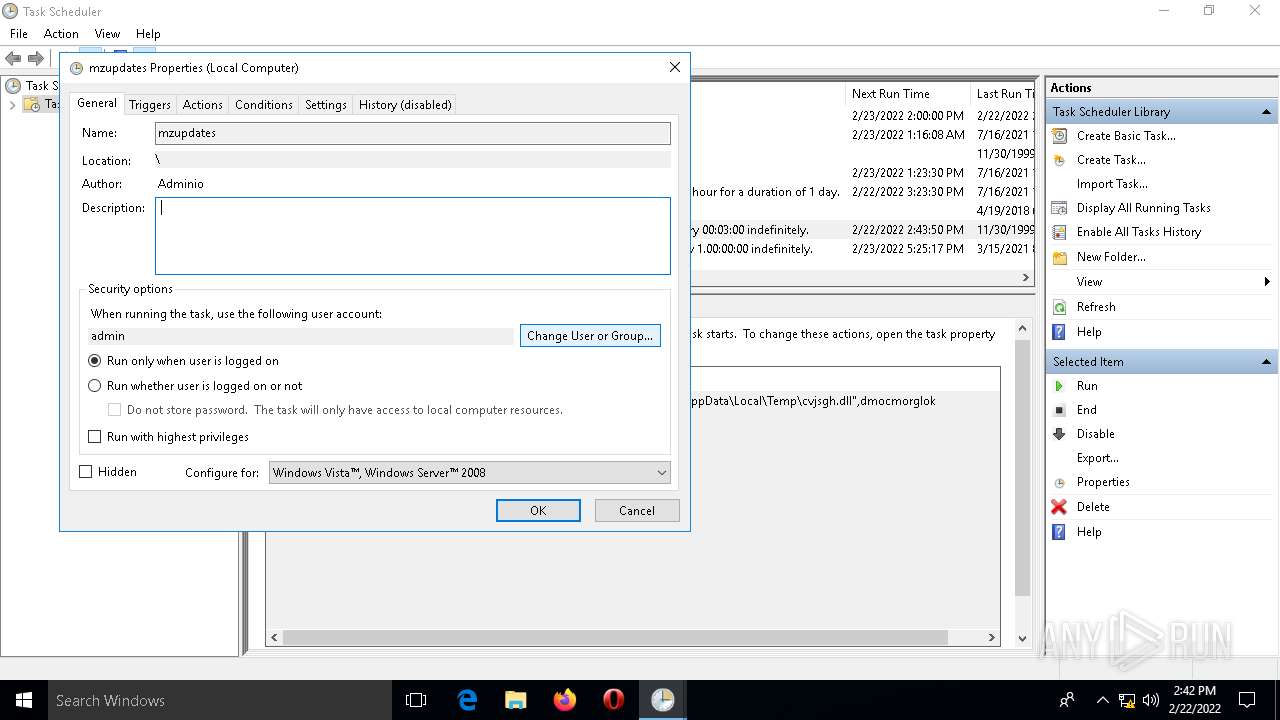
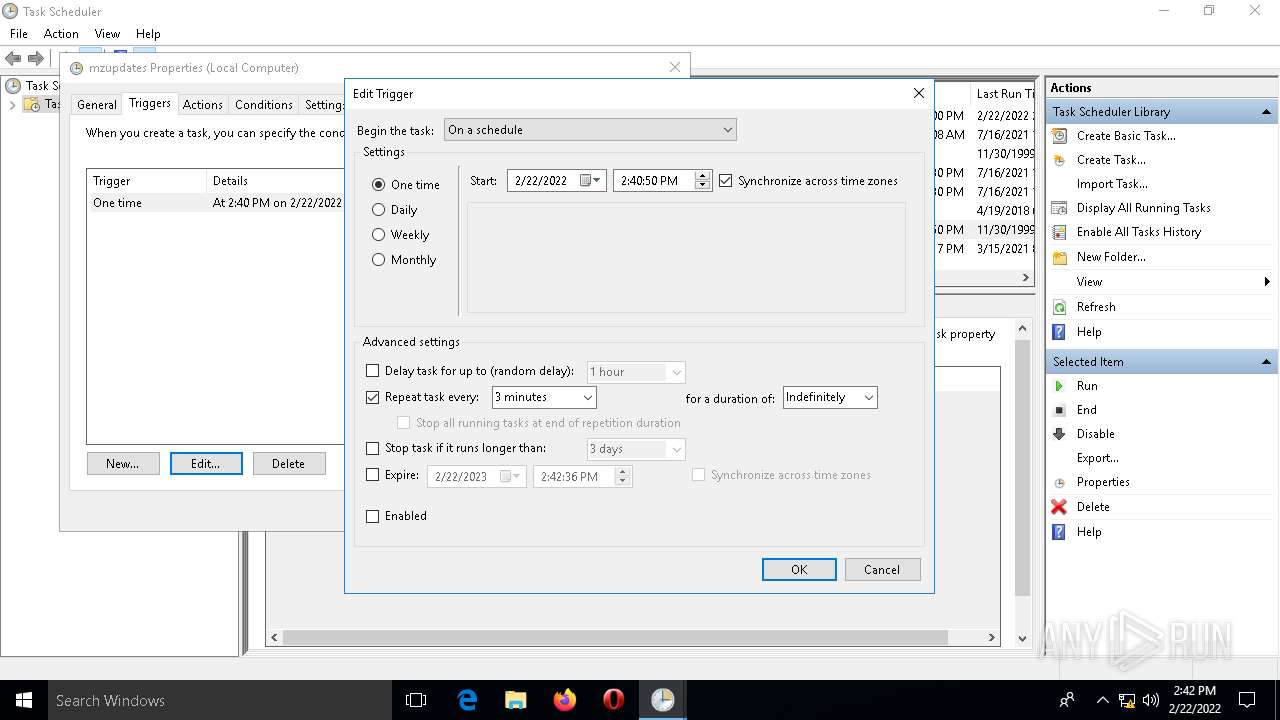
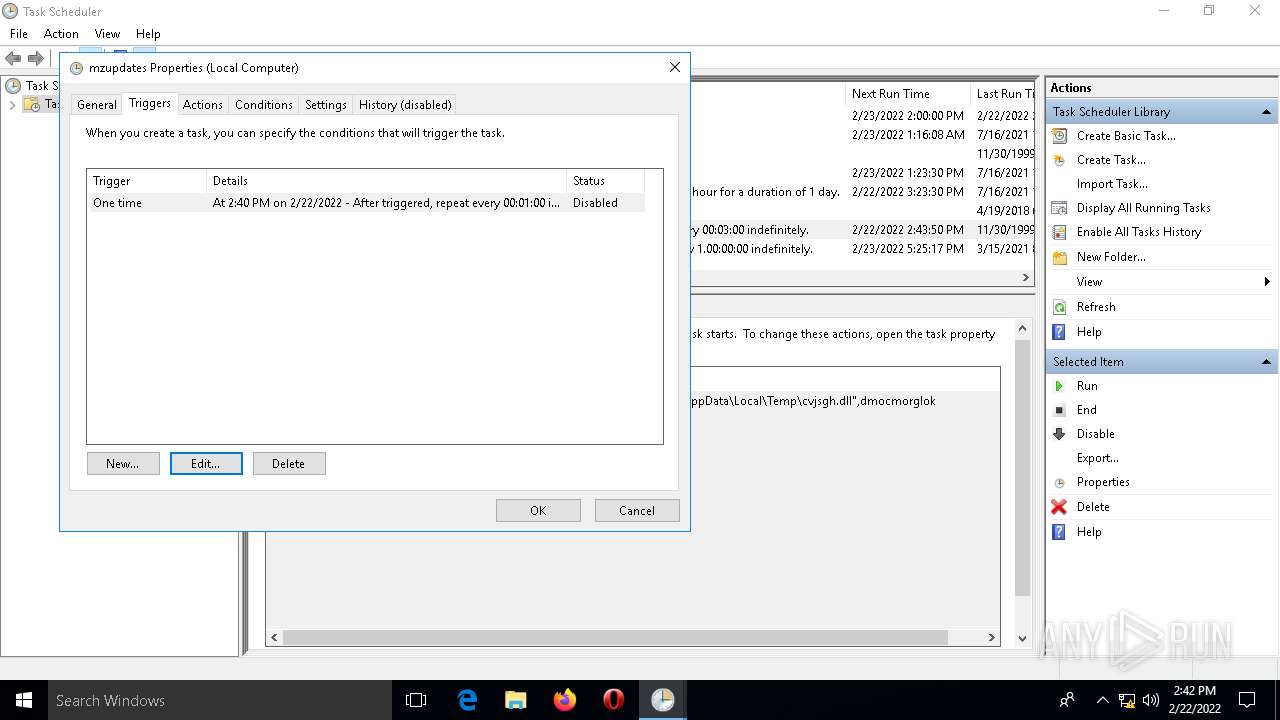
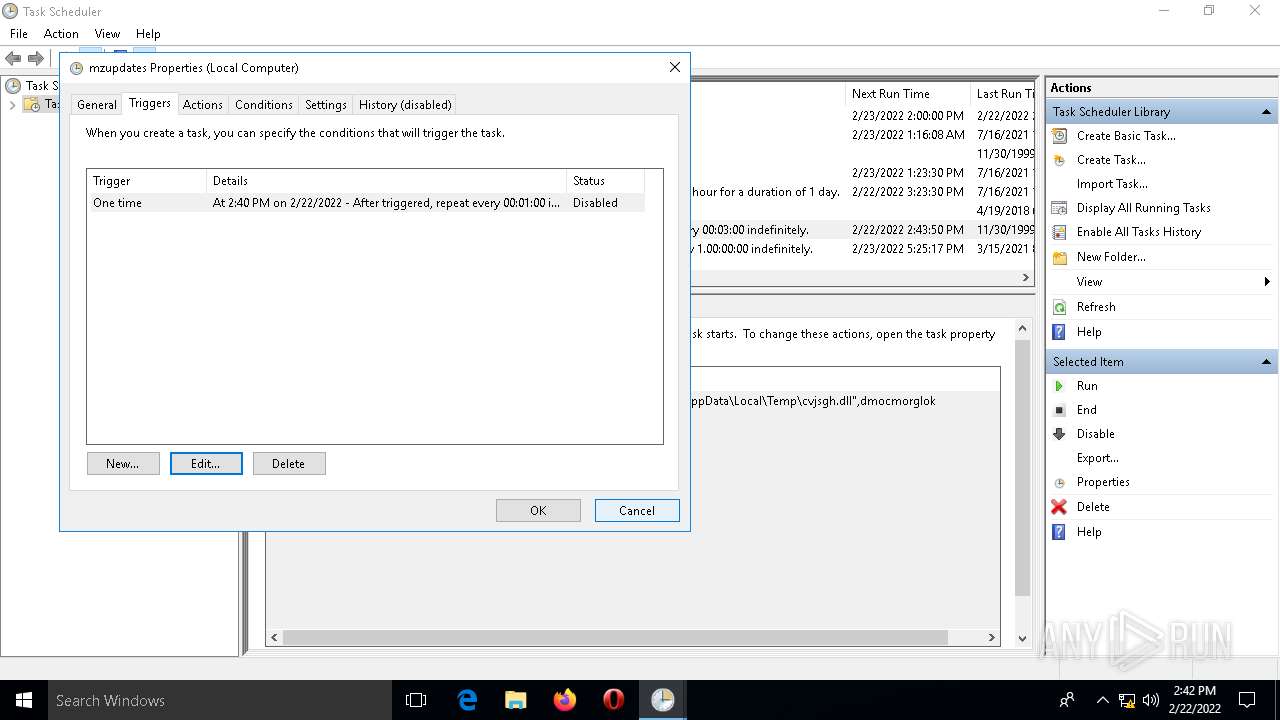
Uses Task Scheduler to run other applications
- rundll32.exe (PID: 5912)
SUSPICIOUS
Reads default file associations for system extensions
- EXCEL.EXE (PID: 2532)
Reads the date of Windows installation
- EXCEL.EXE (PID: 2532)
Drops a file with a compile date too recent
- EXCEL.EXE (PID: 2532)
Checks supported languages
- conhost.exe (PID: 5512)
- cmd.exe (PID: 1208)
- conhost.exe (PID: 2160)
- WMIC.exe (PID: 3384)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 5912)
Reads the computer name
- WMIC.exe (PID: 3384)
- conhost.exe (PID: 5512)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 1208)
Creates files in the program directory
- rundll32.exe (PID: 5912)
INFO
Checks supported languages
- EXCEL.EXE (PID: 2532)
- mmc.exe (PID: 5688)
- SCHTASKS.exe (PID: 2860)
- rundll32.exe (PID: 5912)
- mmc.exe (PID: 4772)
Reads the computer name
- EXCEL.EXE (PID: 2532)
- mmc.exe (PID: 5688)
- rundll32.exe (PID: 5912)
- SCHTASKS.exe (PID: 2860)
- mmc.exe (PID: 4772)
Reads settings of System Certificates
- EXCEL.EXE (PID: 2532)
- rundll32.exe (PID: 5912)
Reads the software policy settings
- EXCEL.EXE (PID: 2532)
- rundll32.exe (PID: 5912)
Scans artifacts that could help determine the target
- EXCEL.EXE (PID: 2532)
Reads Environment values
- EXCEL.EXE (PID: 2532)
Reads CPU info
- EXCEL.EXE (PID: 2532)
Creates files in the user directory
- EXCEL.EXE (PID: 2532)
Dropped object may contain Bitcoin addresses
- EXCEL.EXE (PID: 2532)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 2532)
- rundll32.exe (PID: 5912)
Manual execution by user
- mmc.exe (PID: 5956)
- mmc.exe (PID: 5688)
- mmc.exe (PID: 6092)
- mmc.exe (PID: 4772)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
|---|---|
| CompObjUserTypeLen: | 31 |
| HeadingPairs: |
|
| TitleOfParts: |
|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 14 |
| Company: | home |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | None |
| ModifyDate: | 2022:02:15 07:21:27 |
| CreateDate: | 2021:08:09 13:30:37 |
| Software: | Microsoft Excel |
| LastModifiedBy: | ismail - [2010] |
| Author: | ismail - [2010] |
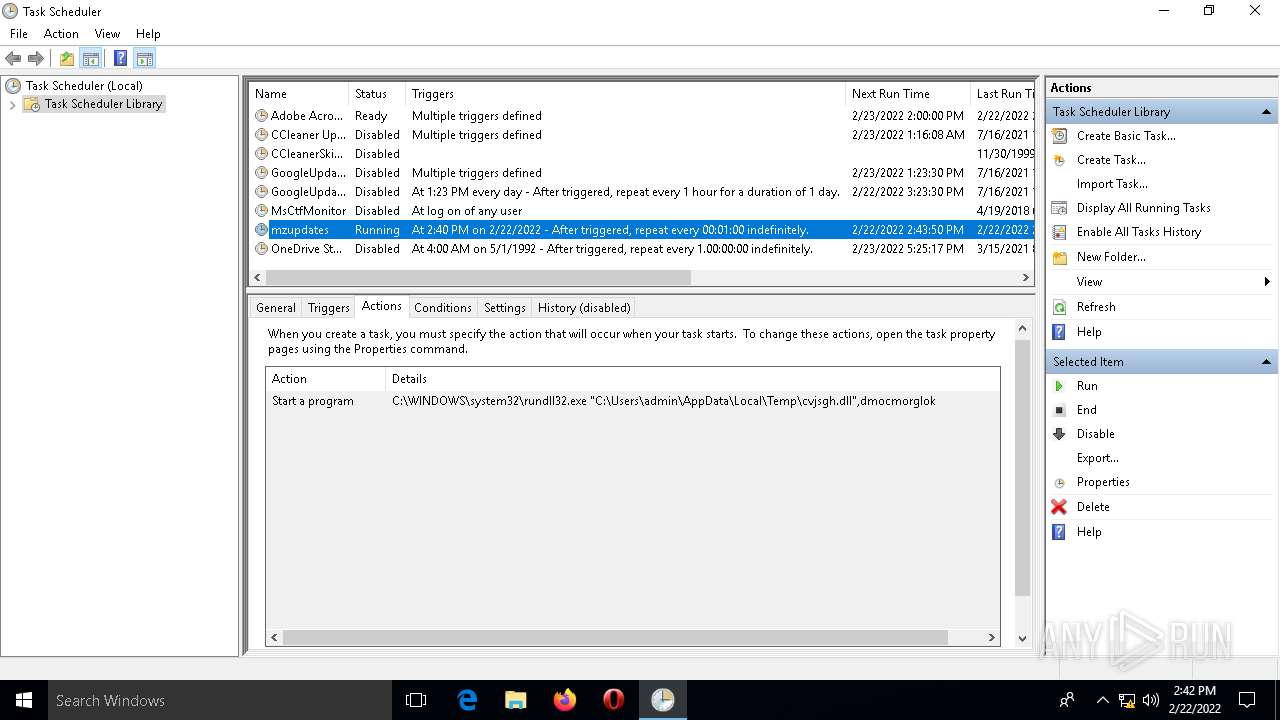
Total processes
219
Monitored processes
14
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
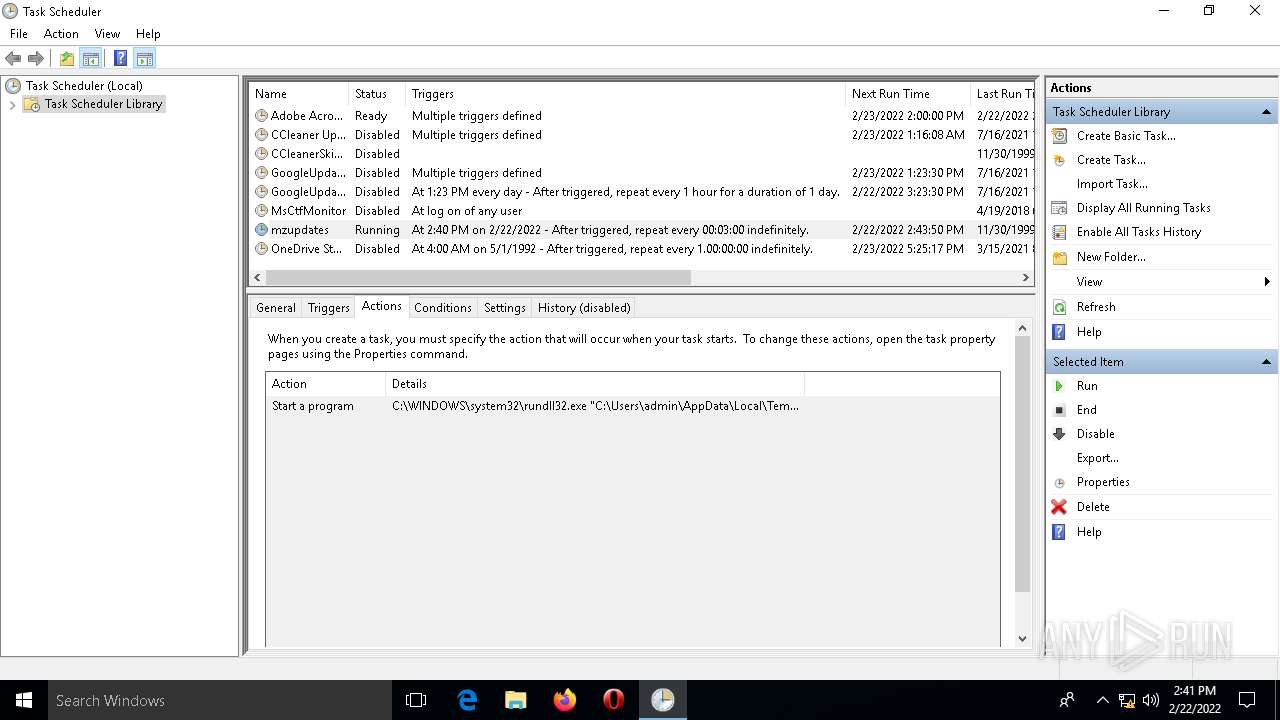
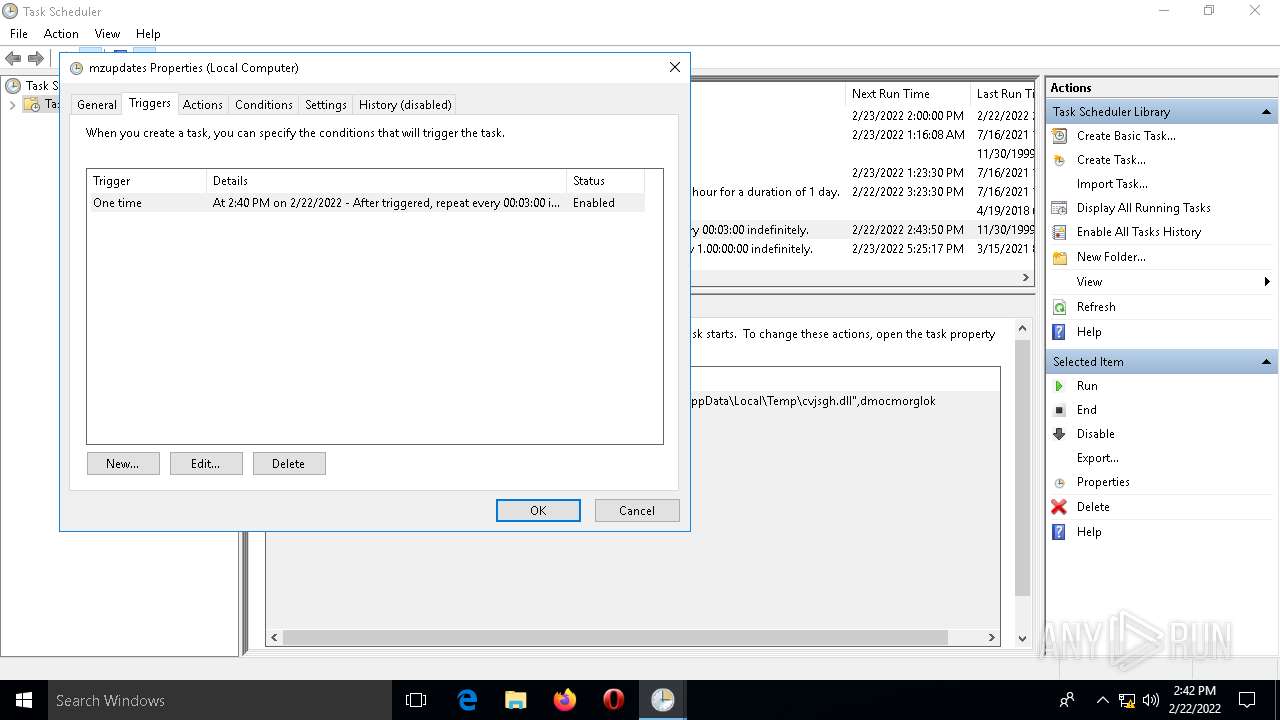
| 680 | C:\WINDOWS\system32\rundll32.exe "C:\Users\admin\AppData\Local\Temp\cvjsgh.dll",dmocmorglok | C:\WINDOWS\system32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | C:\WINDOWS\system32\cmd.exe /c wmic csproduct get name | C:\WINDOWS\system32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1284 | C:\WINDOWS\system32\rundll32.exe "C:\Users\admin\AppData\Local\Temp\cvjsgh.dll",dmocmorglok | C:\WINDOWS\system32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | — | SCHTASKS.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\Scan Copy.xls" | C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 2860 | SCHTASKS /delete /tn Niscor /f | C:\WINDOWS\system32\SCHTASKS.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3384 | wmic csproduct get name | C:\WINDOWS\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4772 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\WINDOWS\system32\mmc.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5428 | C:\WINDOWS\system32\rundll32.exe "C:\Users\admin\AppData\Local\Temp\cvjsgh.dll",dmocmorglok | C:\WINDOWS\system32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
12 370
Read events
12 098
Write events
241
Delete events
31
Modification events
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000284FFA2E01000000000000000500000000000000 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\EXCEL\2532 |
| Operation: | write | Name: | 0 |
Value: 0B0E106C89AAB2A52C5F4F98514D46741D109B230046F3AFAFBBA2FF89EC016A0410240044FA5D64A89E01008500A907556E6B6E6F776E00 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
14
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\CBFEEBB5-E8F4-4967-8DDB-0F10F75CD646 | xml | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Scan Copy.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\wincore.dll | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\CO4CFRDU\sERtJRTb9aBbiGe3KmbZpxYParKXhzKqxc1KzKGU6aTAoGcC[1].mp4 | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\G91AFSNL\sERtJRTb9aBbiGe3KmbZpxYParKXhzKqxc1KzKGU6aTAoGcC[1].png | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\cvjsgh.dll | executable | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF7400E638074DC85D.TMP | atn | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
31
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2532 | EXCEL.EXE | GET | 200 | 52.109.88.177:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.12026&crev=3 | NL | xml | 141 Kb | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v2/Office/excel/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bB2AA896C-2CA5-4F5F-9851-4D46741D109B%7d&LabMachine=false | US | text | 178 Kb | malicious |
368 | svchost.exe | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | US | xml | 1.25 Kb | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 52.109.8.19:443 | https://nexusrules.officeapps.live.com/nexus/rules?Application=excel.exe&Version=16.0.12026.20264&ClientId=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&OSEnvironment=10&MsoAppId=1&AudienceName=Production&AudienceGroup=Production&AppVersion=16.0.12026.20264& | US | xml | 296 Kb | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 168.100.10.242:80 | http://font.backuplogs.xyz/jiuTeOjl3XBvhWzc/sERtJRTb9aBbiGe3KmbZpxYParKXhzKqxc1KzKGU6aTAoGcC.mp4 | US | binary | 324 Kb | suspicious |
368 | svchost.exe | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | US | xml | 11.0 Kb | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 168.100.10.242:80 | http://font.backuplogs.xyz/jiuTeOjl3XBvhWzc/sERtJRTb9aBbiGe3KmbZpxYParKXhzKqxc1KzKGU6aTAoGcC.png | US | binary | 4.87 Kb | suspicious |
368 | svchost.exe | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | US | xml | 11.0 Kb | whitelisted |
368 | svchost.exe | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | US | xml | 11.0 Kb | whitelisted |
368 | svchost.exe | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | US | xml | 1.91 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2412 | OfficeClickToRun.exe | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
2532 | EXCEL.EXE | 52.109.88.177:443 | officeclient.microsoft.com | Microsoft Corporation | NL | suspicious |
2532 | EXCEL.EXE | 52.109.68.14:443 | roaming.officeapps.live.com | Microsoft Corporation | FR | whitelisted |
2532 | EXCEL.EXE | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
2532 | EXCEL.EXE | 52.109.8.19:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
2532 | EXCEL.EXE | 104.102.28.73:443 | fs.microsoft.com | Akamai Technologies, Inc. | US | suspicious |
5912 | rundll32.exe | 91.198.174.192:443 | en.wikipedia.org | Wikimedia Foundation, Inc. | NL | malicious |
5912 | rundll32.exe | 162.33.178.47:443 | srvrfontsdrive.xyz | Coretel America, Inc. | US | unknown |
2416 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | Microsoft Corporation | GB | whitelisted |
368 | svchost.exe | 40.126.31.1:443 | login.live.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
config.edge.skype.com |
| malicious |
fs.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
font.backuplogs.xyz |
| suspicious |
self.events.data.microsoft.com |
| whitelisted |
messaging.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2532 | EXCEL.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2532 | EXCEL.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |