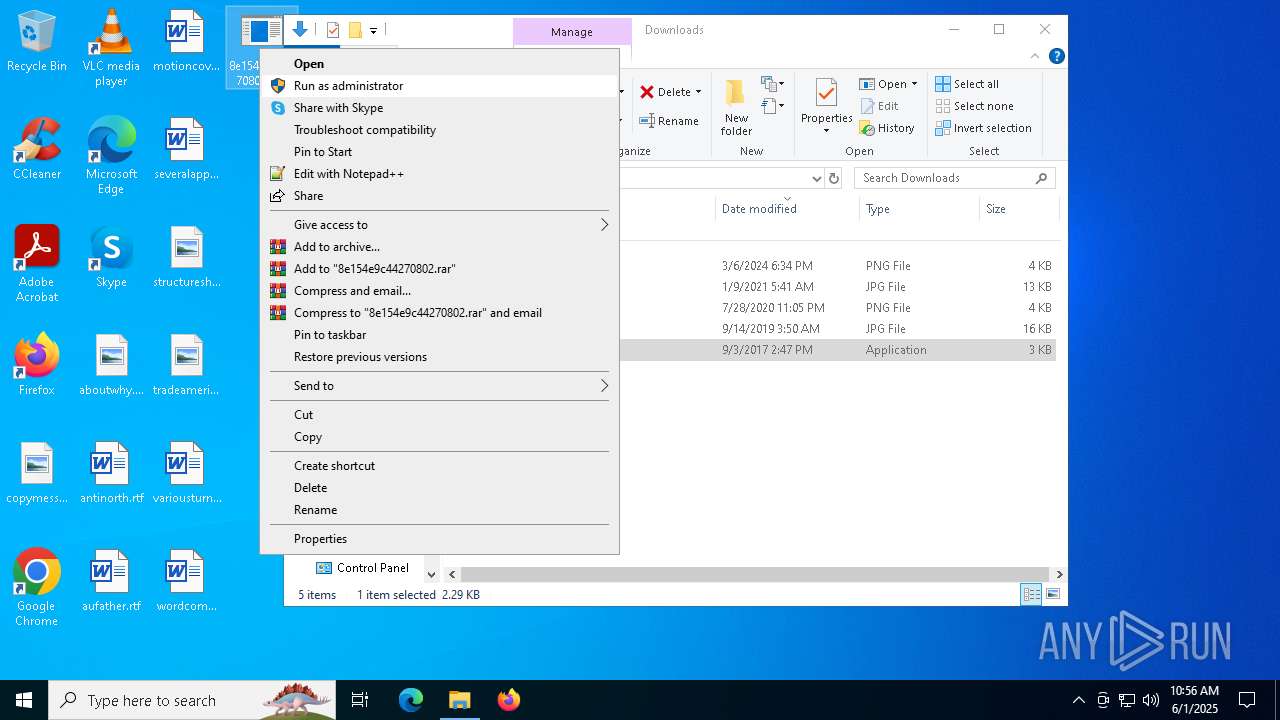
| File name: | 8e154e9c44270802.exe |
| Full analysis: | https://app.any.run/tasks/b1031438-4da6-450a-8627-a94c418344bc |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2025, 10:55:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 13 sections |
| MD5: | F65E2B5E29102CAEE7E1616C6A98B630 |
| SHA1: | D32B006DB524094AA98163B6C63F431A241E434D |
| SHA256: | A4985FF00E98B2230B867609F1753A1BC9F15EE4D53C79F216476D5581DB6297 |
| SSDEEP: | 98304:j3eLBG+DjSdlUlT0OI9hDOS55fjHtU/9P082gEuk875zCnDKbTSV2bDSM+3R/6+W:1r204+5XM6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- 8e154e9c44270802.exe (PID: 1568)
- 8e154e9c44270802.exe (PID: 6700)
Reads the date of Windows installation
- 8e154e9c44270802.exe (PID: 1568)
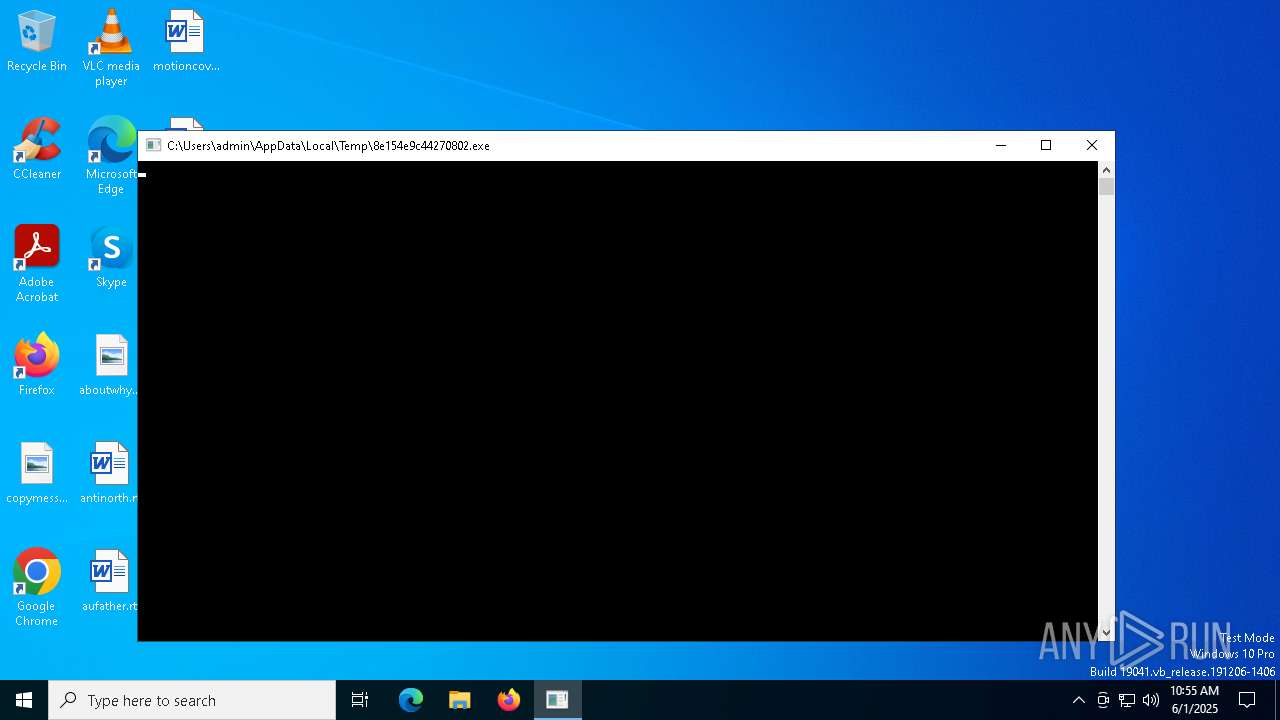
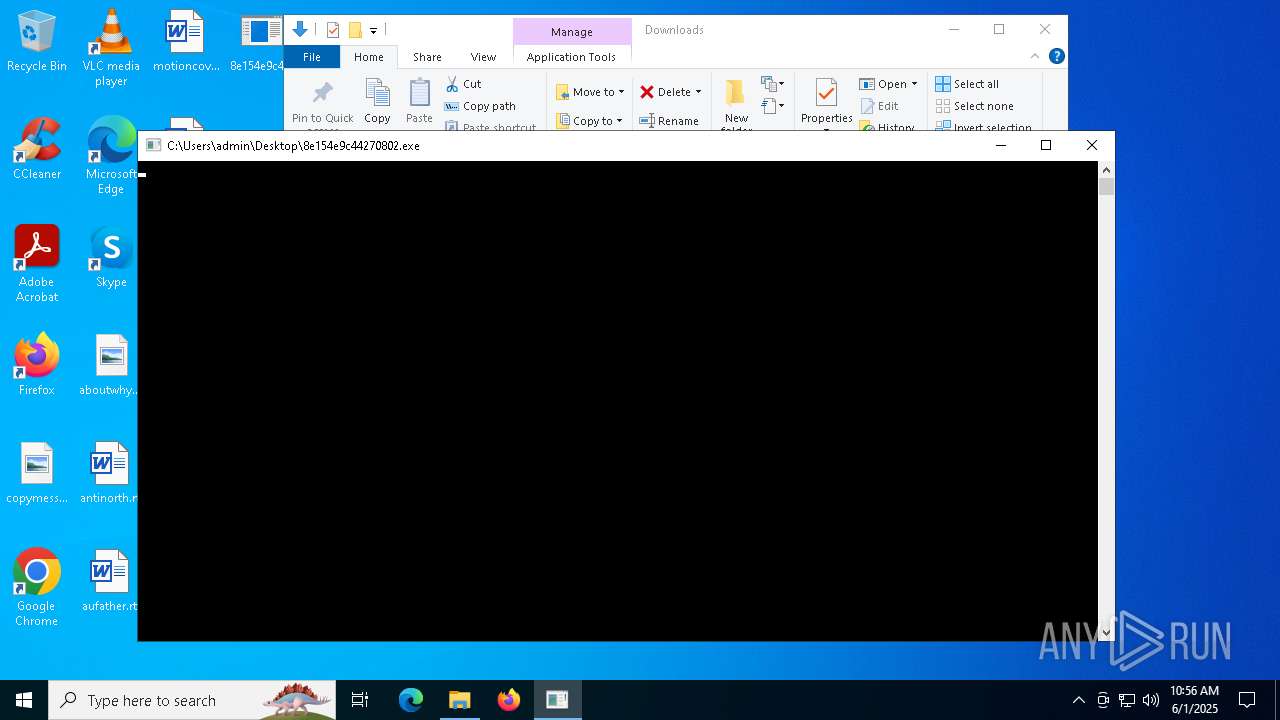
Starts CMD.EXE for commands execution
- 8e154e9c44270802.exe (PID: 1568)
- 8e154e9c44270802.exe (PID: 6700)
- 8e154e9c44270802.exe (PID: 1244)
The executable file from the user directory is run by the CMD process
- 8e154e9c44270802.exe (PID: 6700)
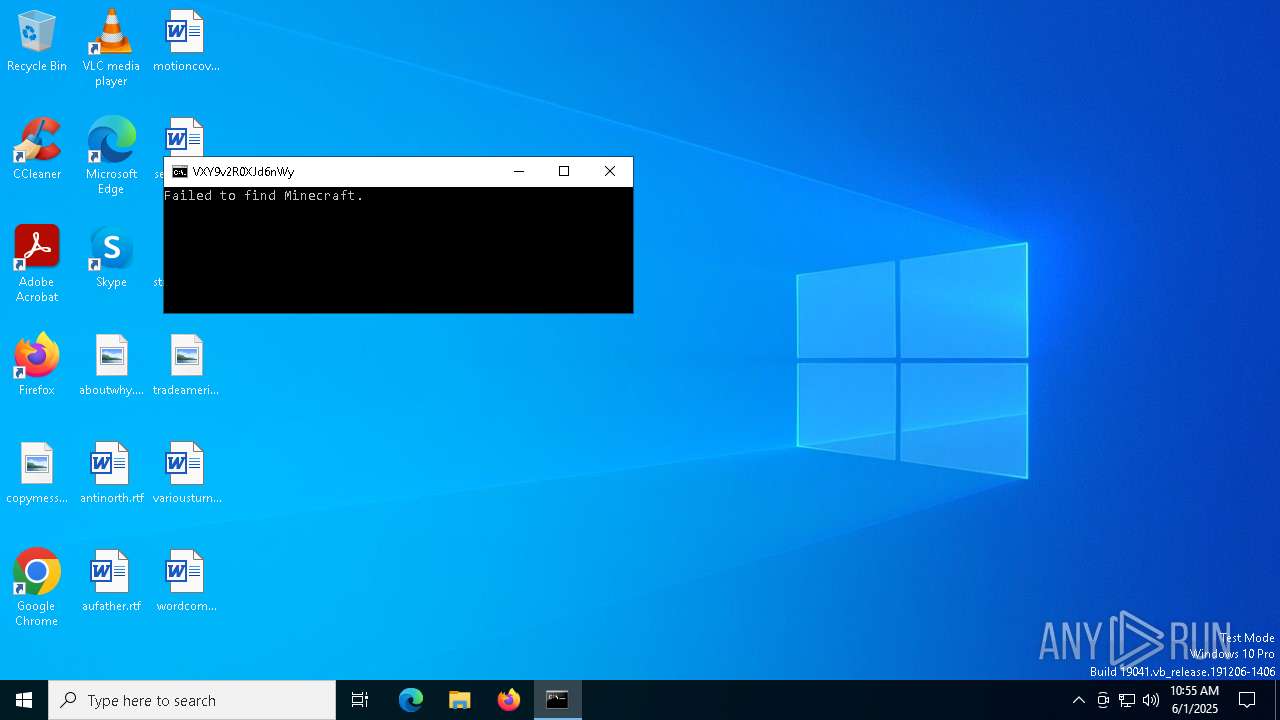
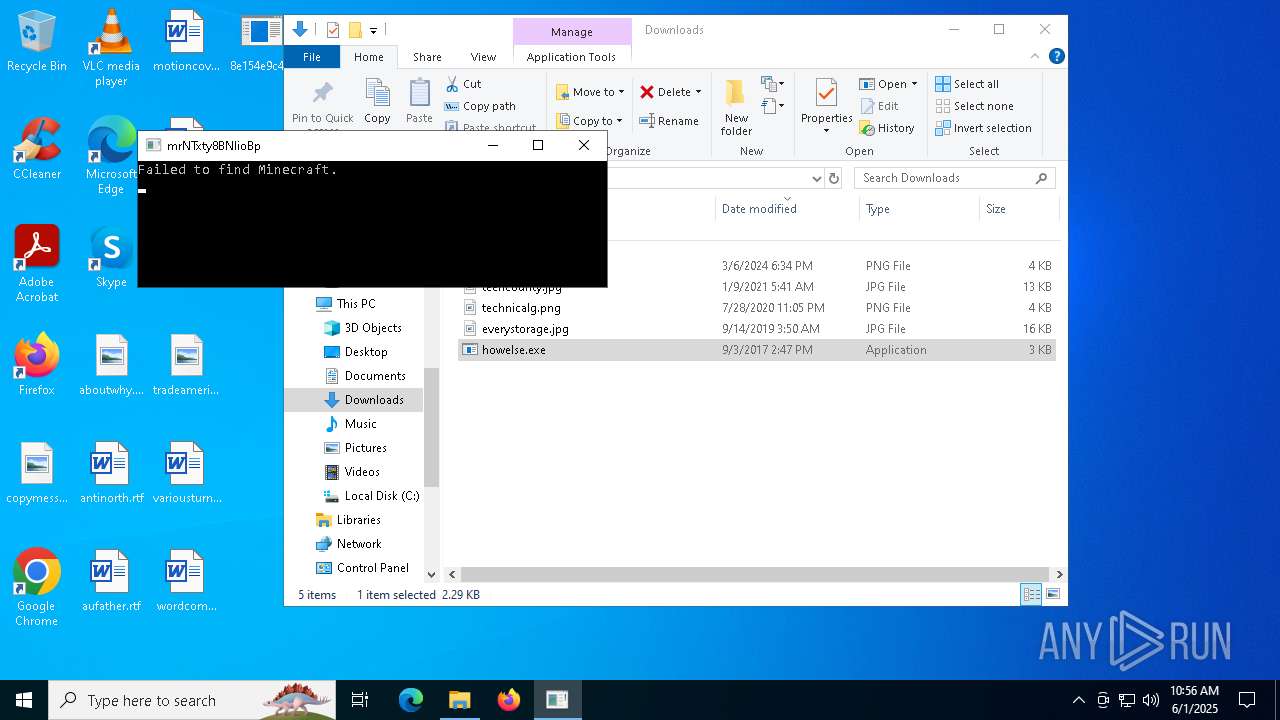
Executes application which crashes
- 8e154e9c44270802.exe (PID: 6700)
- 8e154e9c44270802.exe (PID: 1244)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6476)
- 8e154e9c44270802.exe (PID: 1568)
INFO
Reads the computer name
- 8e154e9c44270802.exe (PID: 1568)
- 8e154e9c44270802.exe (PID: 6700)
- ShellExperienceHost.exe (PID: 6476)
Process checks whether UAC notifications are on
- 8e154e9c44270802.exe (PID: 6700)
Process checks computer location settings
- 8e154e9c44270802.exe (PID: 1568)
Checks supported languages
- 8e154e9c44270802.exe (PID: 6700)
- ShellExperienceHost.exe (PID: 6476)
- 8e154e9c44270802.exe (PID: 1568)
Creates files or folders in the user directory
- WerFault.exe (PID: 6368)
Manual execution by a user
- 8e154e9c44270802.exe (PID: 1244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:01 10:50:17+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.3 |
| CodeSize: | 380416 |
| InitializedDataSize: | 355840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa81058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
150
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | "C:\Users\admin\Desktop\8e154e9c44270802.exe" | C:\Users\admin\Desktop\8e154e9c44270802.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1268 | "C:\Windows\System32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\8e154e9c44270802.exe" | C:\Windows\System32\cmd.exe | 8e154e9c44270802.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | 8e154e9c44270802.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\AppData\Local\Temp\8e154e9c44270802.exe" | C:\Users\admin\AppData\Local\Temp\8e154e9c44270802.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6368 | C:\WINDOWS\system32\WerFault.exe -u -p 6700 -s 1224 | C:\Windows\System32\WerFault.exe | — | 8e154e9c44270802.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | 8e154e9c44270802.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6700 | C:\Users\admin\AppData\Local\Temp\8e154e9c44270802.exe | C:\Users\admin\AppData\Local\Temp\8e154e9c44270802.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 6700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 8e154e9c44270802.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 840
Read events
5 817
Write events
17
Delete events
6
Modification events
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: 6031DFFAD63EF0118001444553540000 | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\8E154E9C44270802.EXE683C3069006D3DB0 |
| Operation: | write | Name: | Name |
Value: 8E154E9C44270802.EXE | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\8E154E9C44270802.EXE683C3069006D3DB0 |
| Operation: | write | Name: | UsesMapper |
Value: 00000000 | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: 8E154E9C44270802.EXE | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Id |
Value: 8E154E9C44270802.EXE683C3069006D3DB0 | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Version |
Value: 00080000 | |||
| (PID) Process: | (6700) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | MostRecentStart |
Value: 107137BDE3D2DB01 | |||
| (PID) Process: | (6368) WerFault.exe | Key: | \REGISTRY\A\{0ed0892e-4721-78e7-a574-2a867b226b98}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6368) WerFault.exe | Key: | \REGISTRY\A\{0ed0892e-4721-78e7-a574-2a867b226b98}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1244) 8e154e9c44270802.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: 8E154E9C44270802.EXE | |||
Executable files
0
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_8e154e9c44270802_f4779ee4c57131e9820c929ec7e661cc4ad9311_cffd6acc_b8c69a9a-a4f1-4241-aa8a-dcb08b0cb69b\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6368 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\8e154e9c44270802.exe.6700.dmp | — | |
MD5:— | SHA256:— | |||
| 7576 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_8e154e9c44270802_f4779ee4c57131e9820c929ec7e661cc4ad9311_cffd6acc_70b2f6ec-25e1-4721-b3b8-4e3efc432b91\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7576 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\8e154e9c44270802.exe.1244.dmp | — | |
MD5:— | SHA256:— | |||
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER142D.tmp.WERInternalMetadata.xml | xml | |
MD5:ADCB8ED152B7DE317A7BD5133254648B | SHA256:2DFA7BDEE3623EA96DB76B929D00301D610908BE0C3ED89F6CC0B356190B3974 | |||
| 7576 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1F82.tmp.dmp | binary | |
MD5:928B995DF1DE066228EC8D810F0C273C | SHA256:464BFE0231FA551713D9B68609FB4EC2FF72A69D89F48211C10A3C68787805C0 | |||
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER12C5.tmp.dmp | binary | |
MD5:7D73BAA50108FAD4264D59D9B648A7F3 | SHA256:6CCA2D93C8627C585D08502F6C7ED44FFF0EFCE970348723C3C534189BABE7B1 | |||
| 7576 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER202E.tmp.WERInternalMetadata.xml | xml | |
MD5:536DA98BFA2B3AA86AD324D570A9BBD0 | SHA256:C727030DBDA81CA404D6FB1C724992F930F3C55CF6837A473C6DEE0A430D635F | |||
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER145D.tmp.xml | xml | |
MD5:B365C439956842094A9CE86EC8222DFE | SHA256:61CEF47E0C466D3A8CCCEDFF5F93B4686E545AF7FE0BB4C686BD0268912AC175 | |||
| 7576 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER205E.tmp.xml | xml | |
MD5:8E6E878AEC75B0F19EDF71772509FA5F | SHA256:6E94D0340DADB220DACAE021AC280183EBCE663B3E2F0450D0C70FECFDF93DBB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2088 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2088 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |