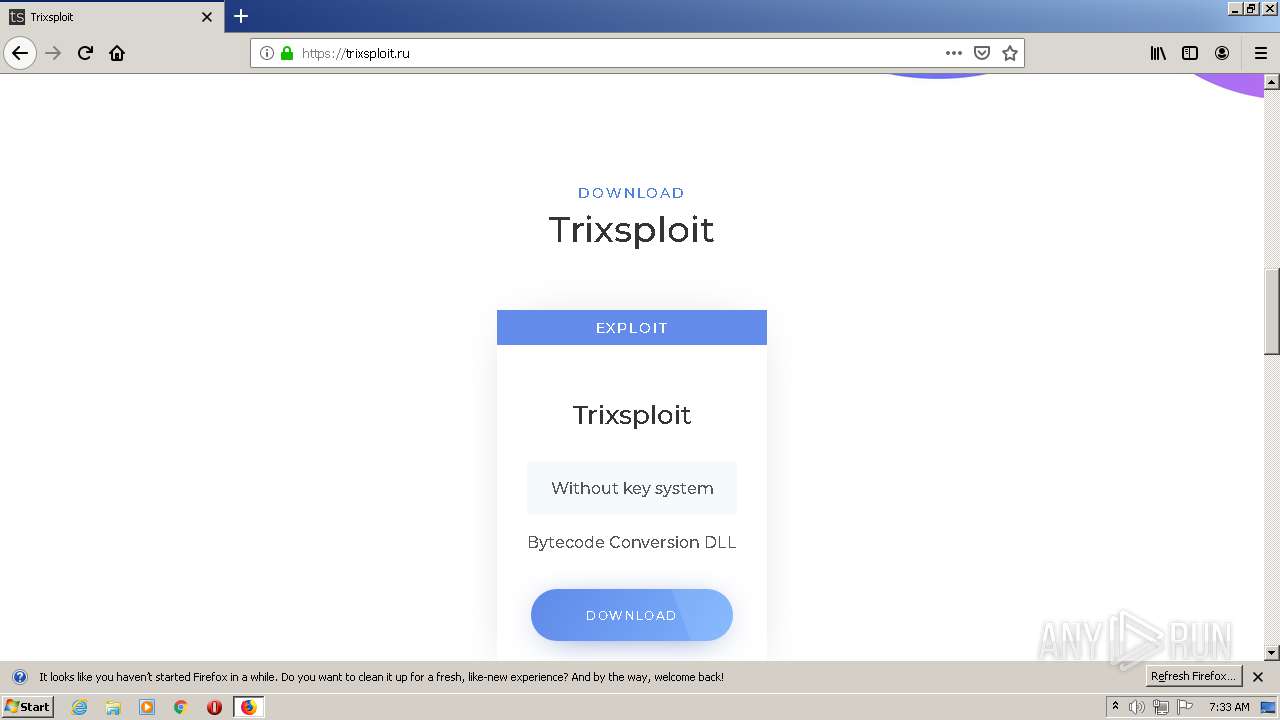
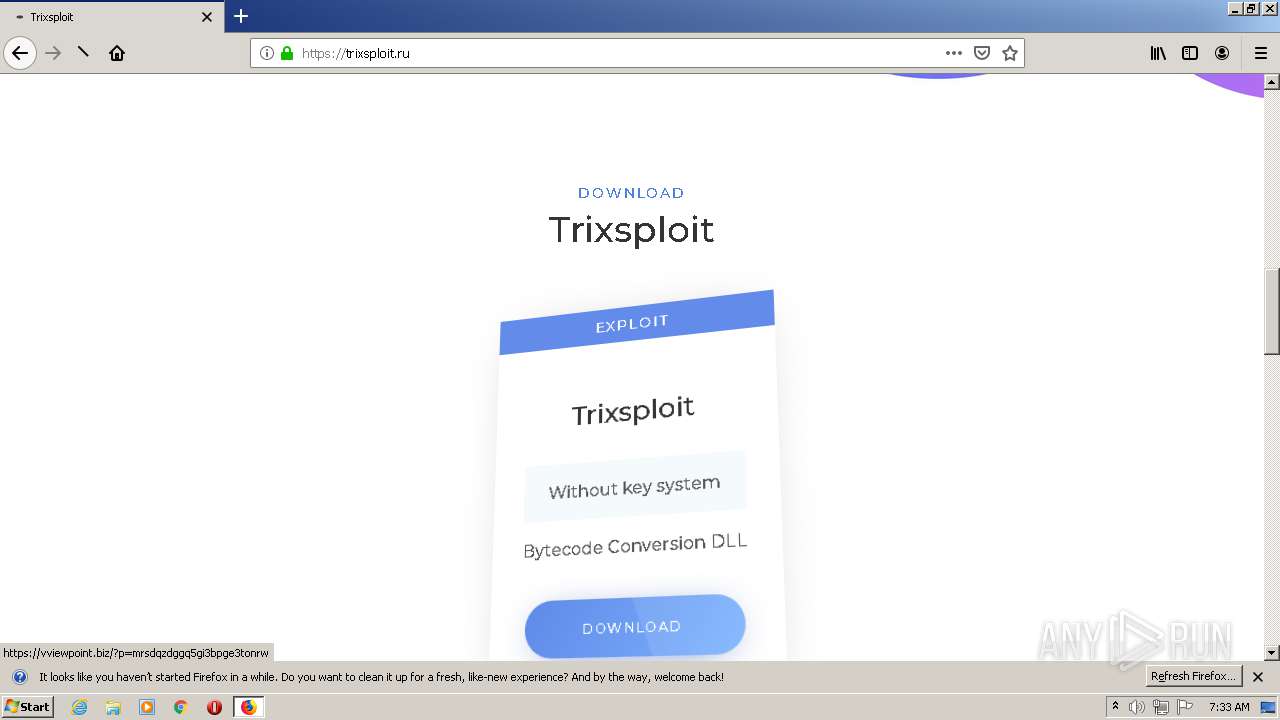
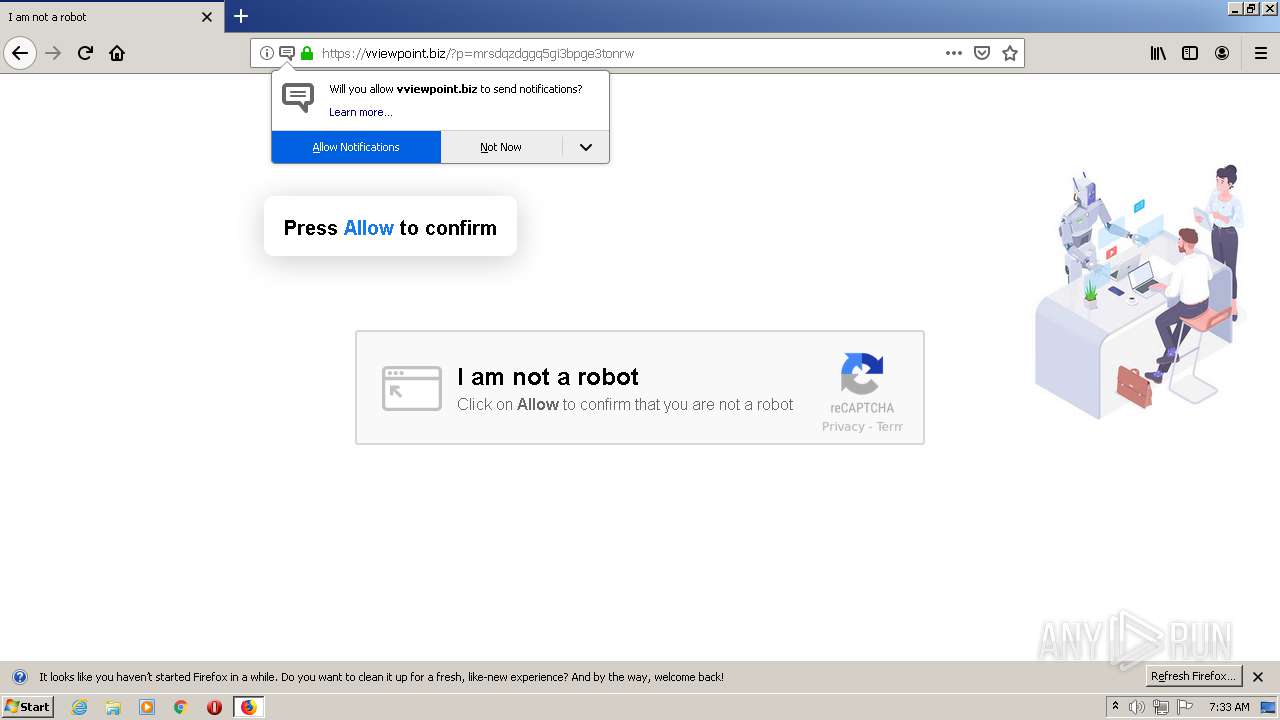
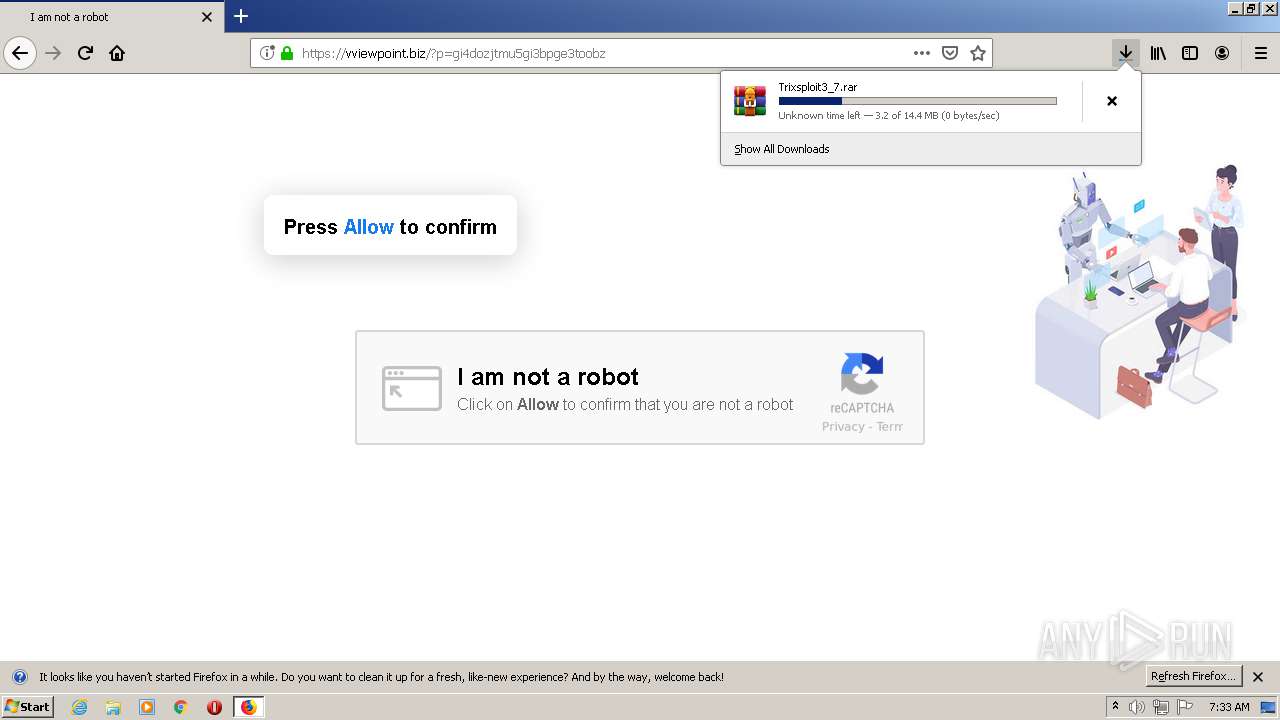
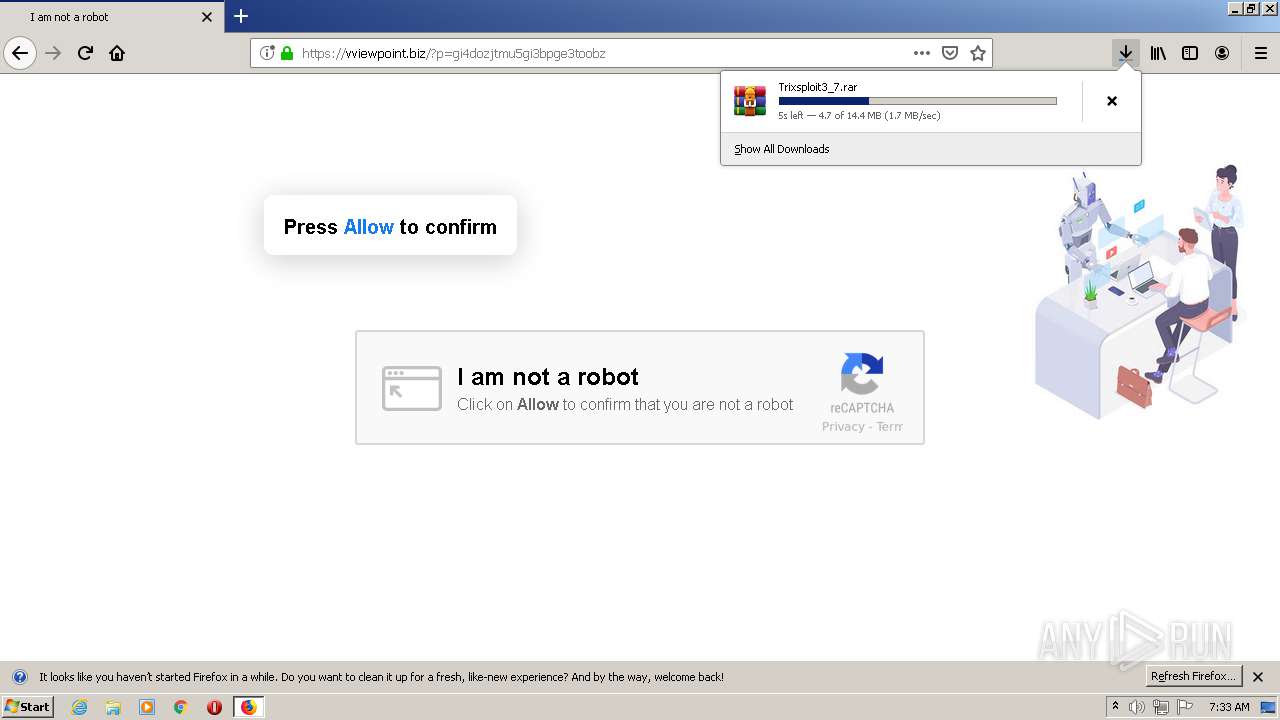
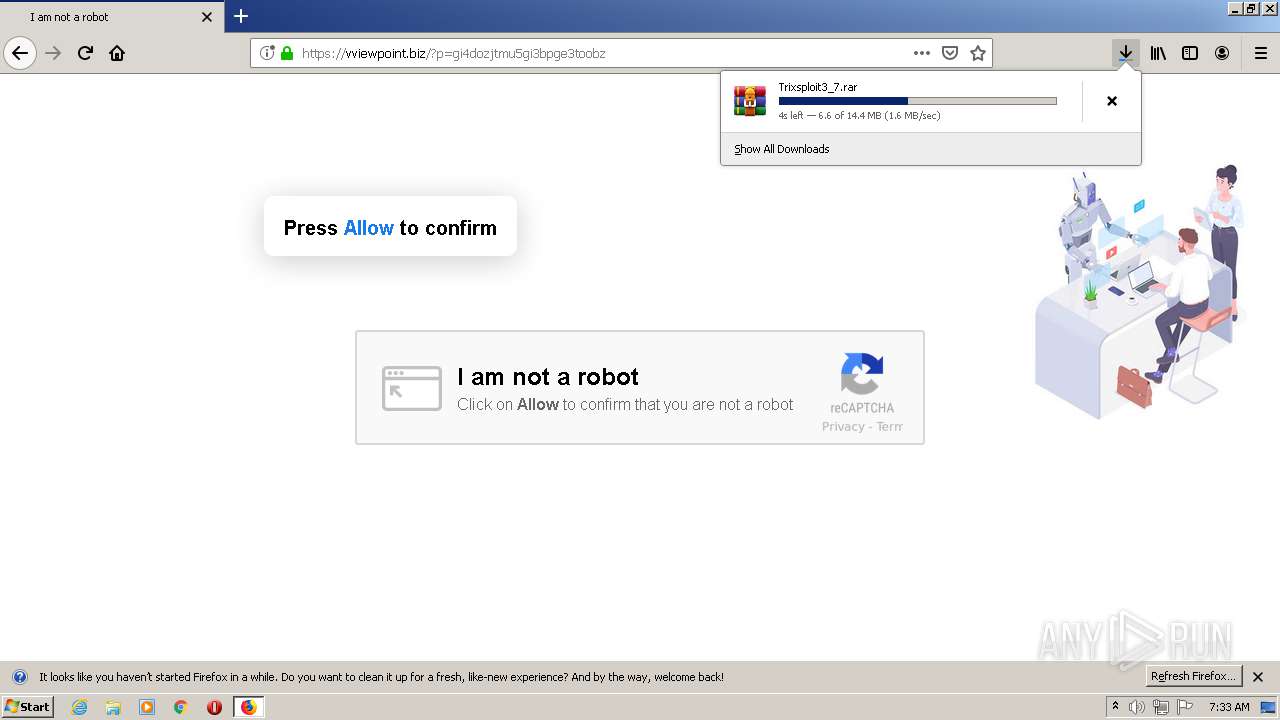
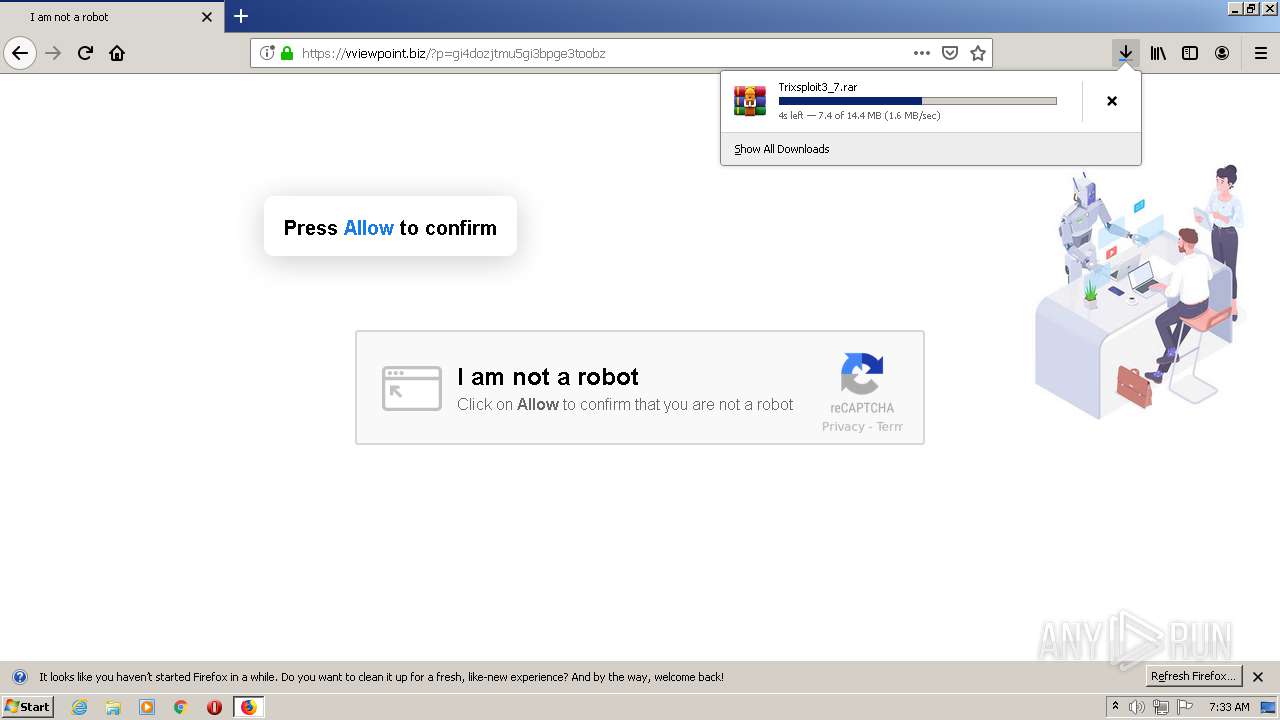
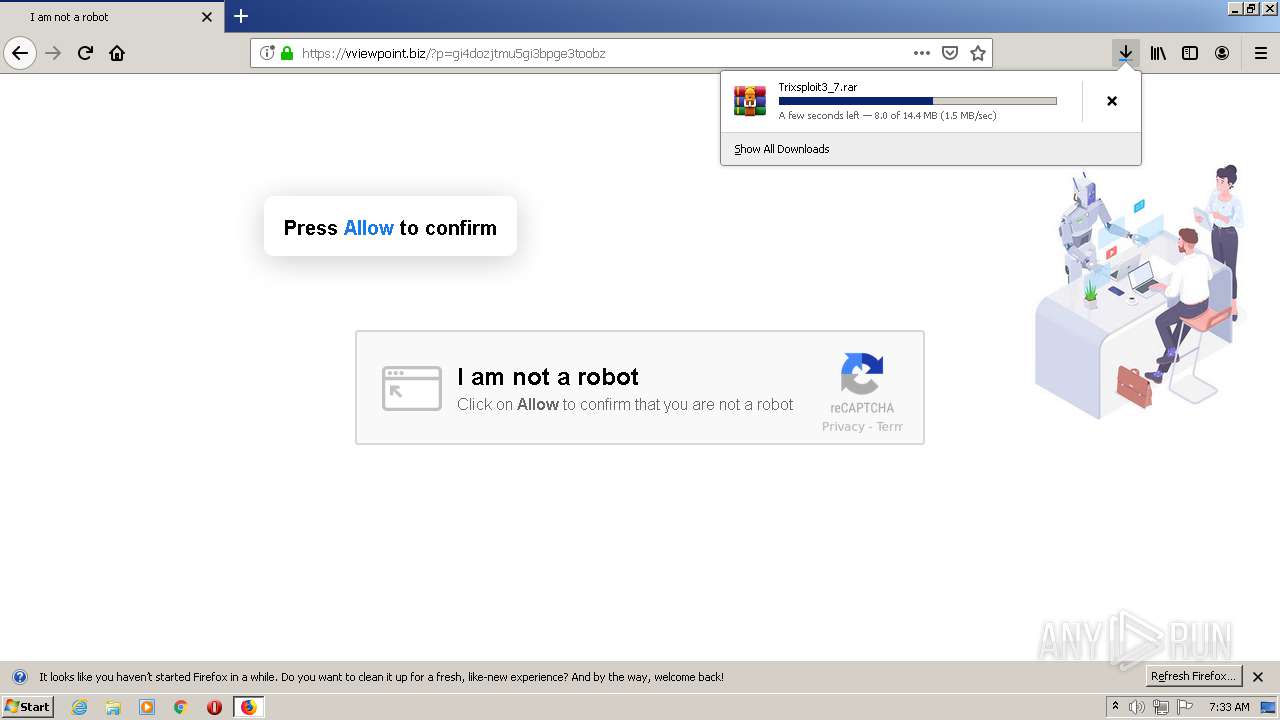
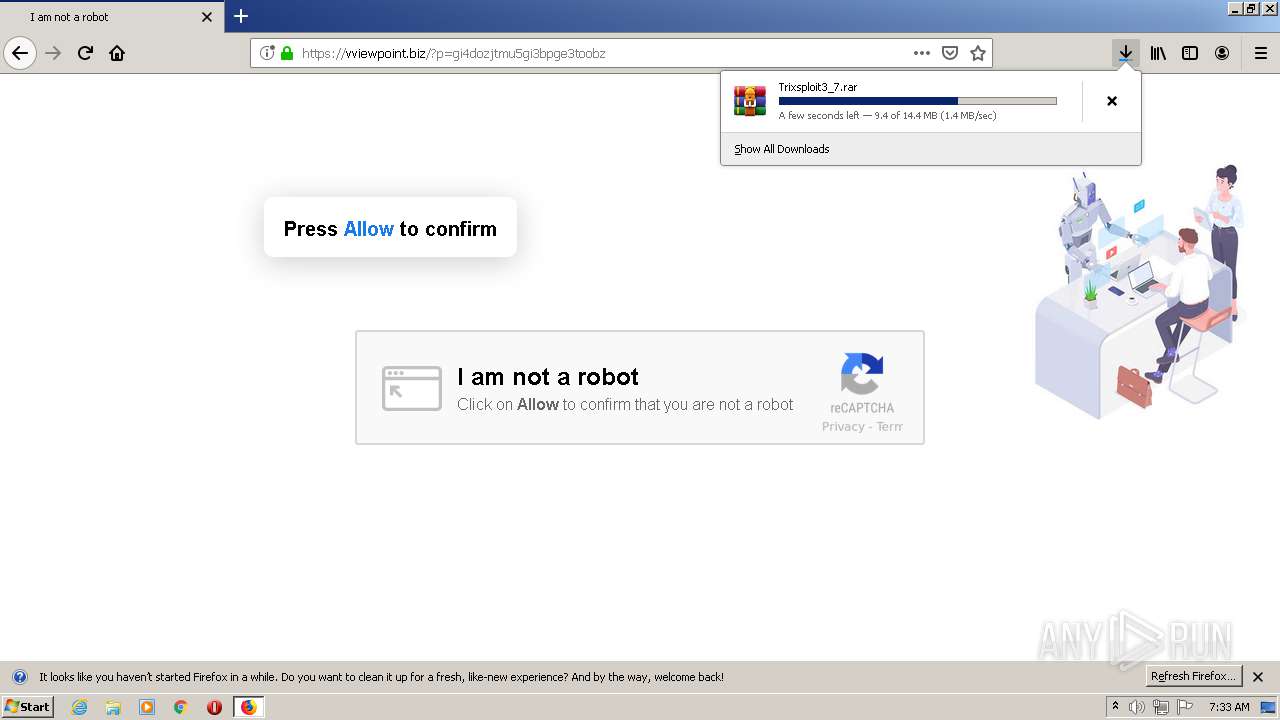
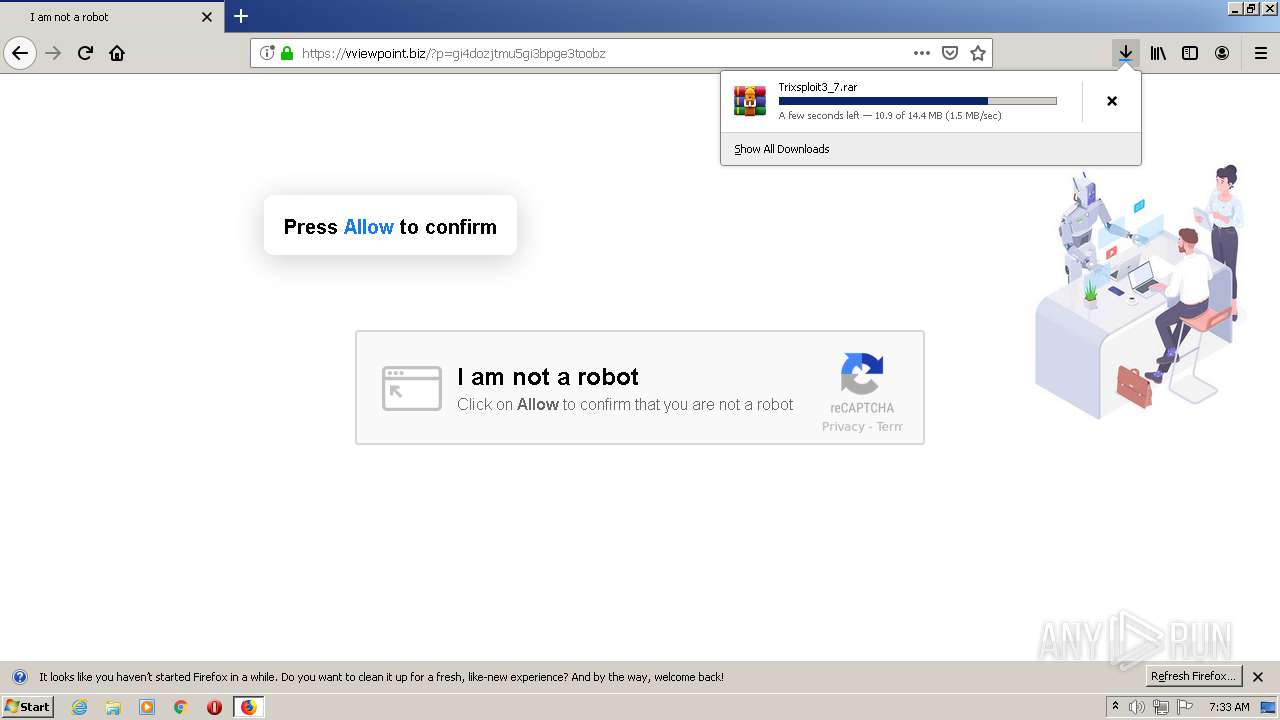
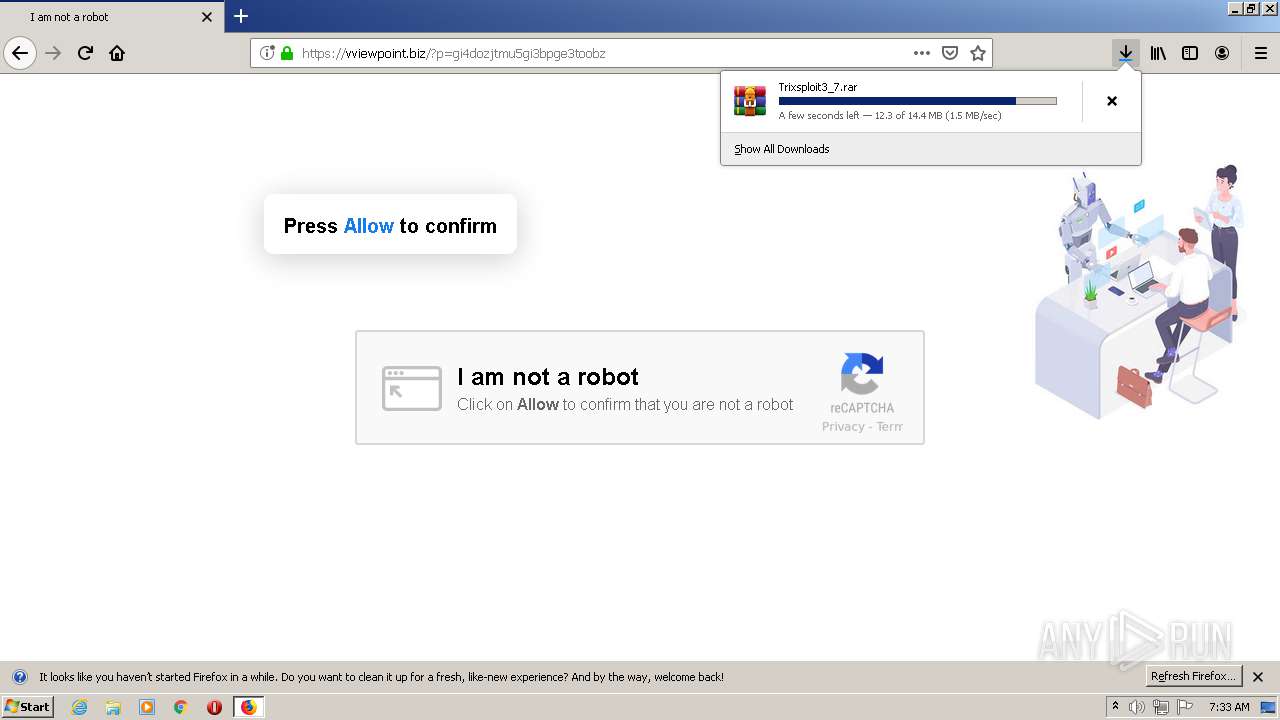
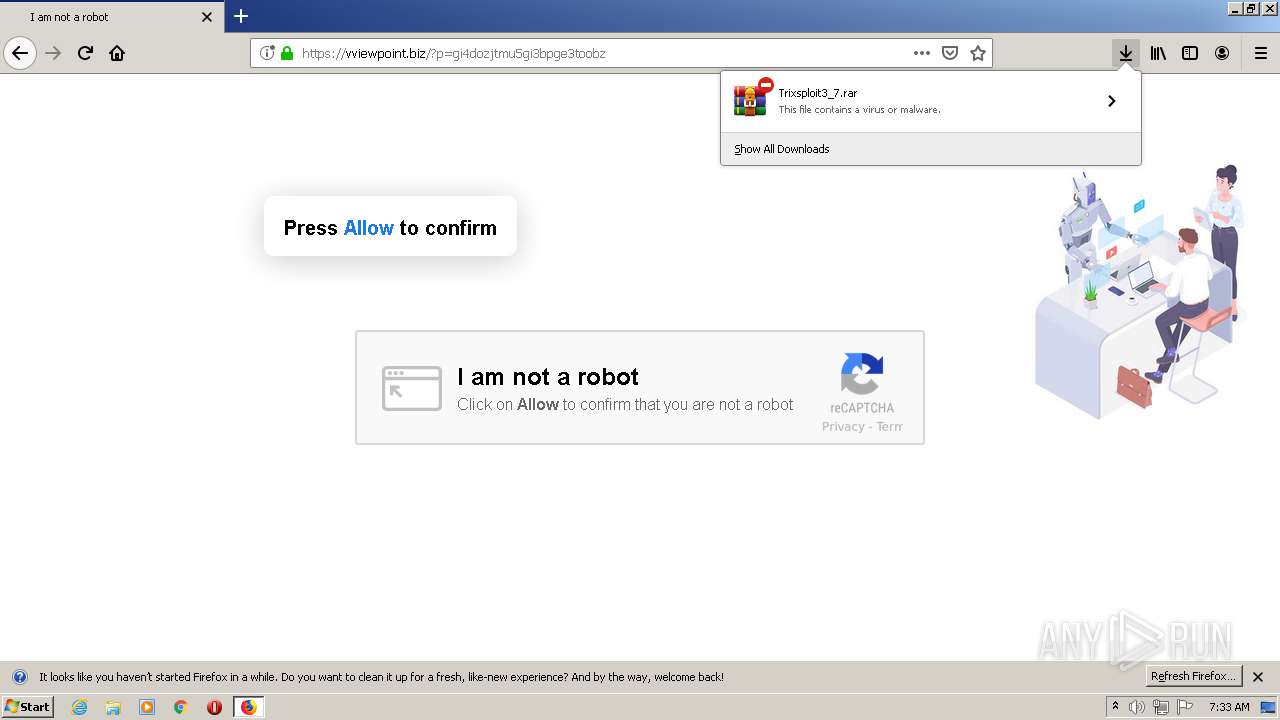
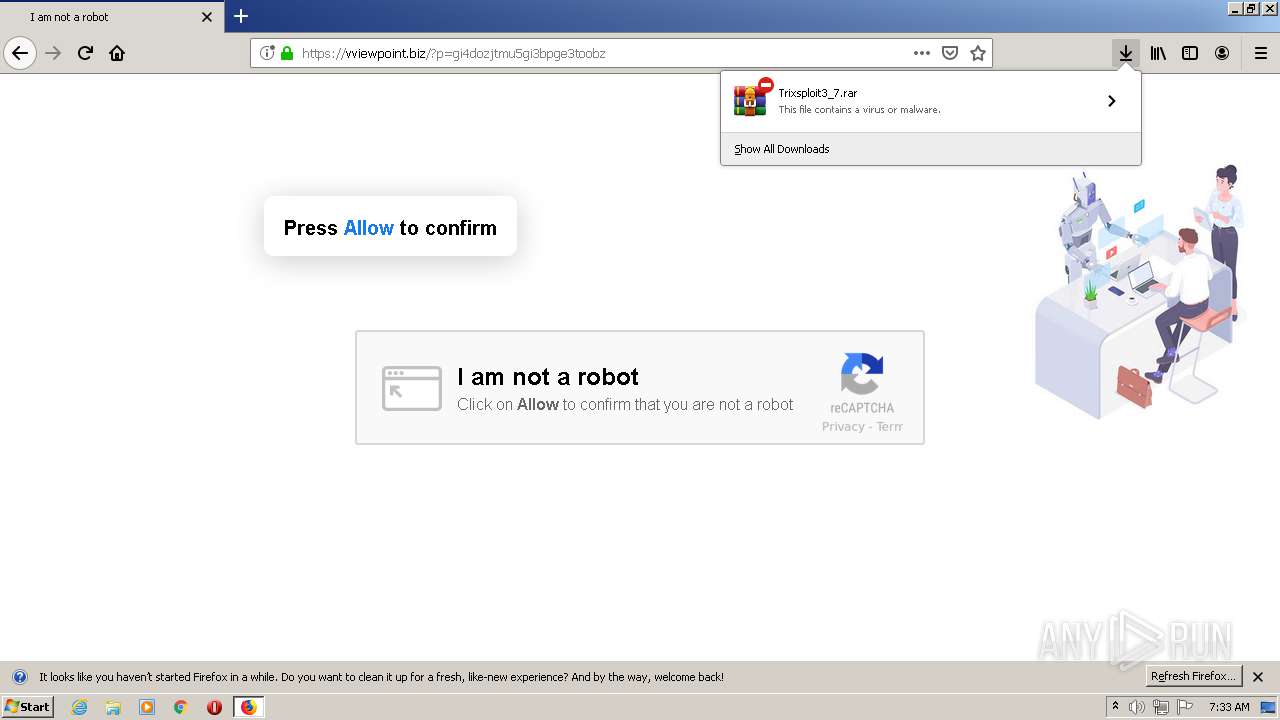
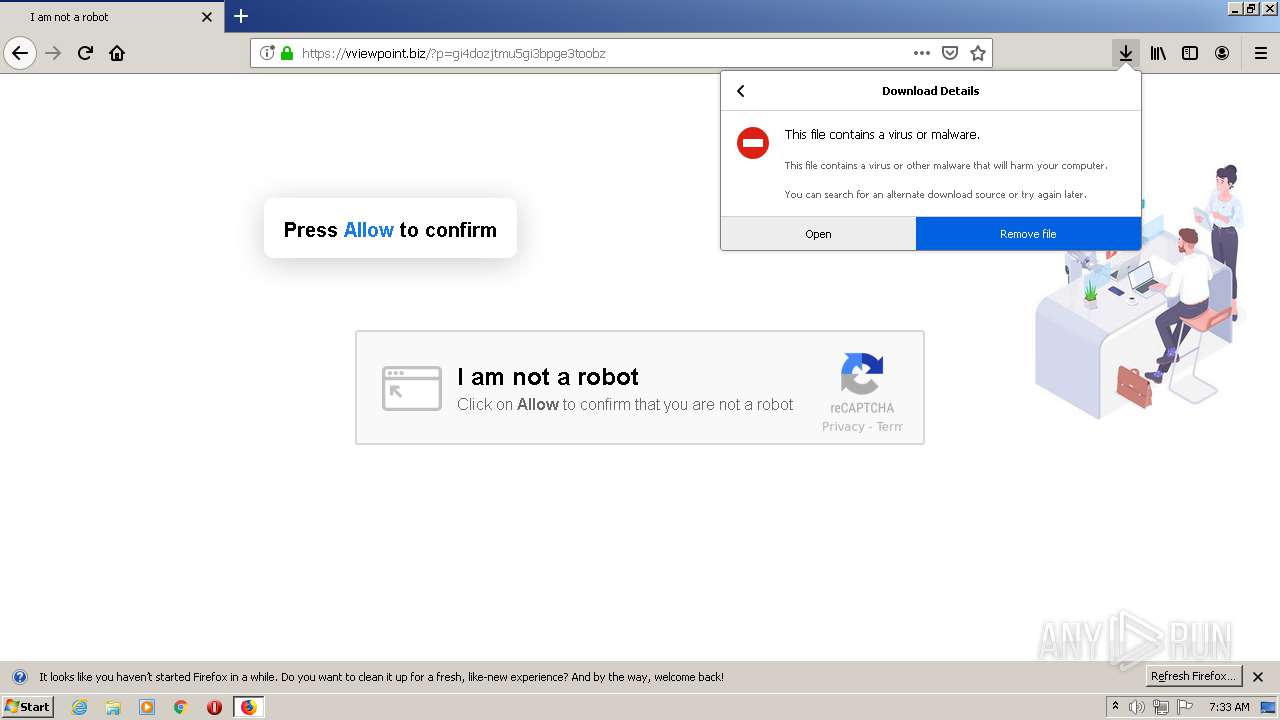
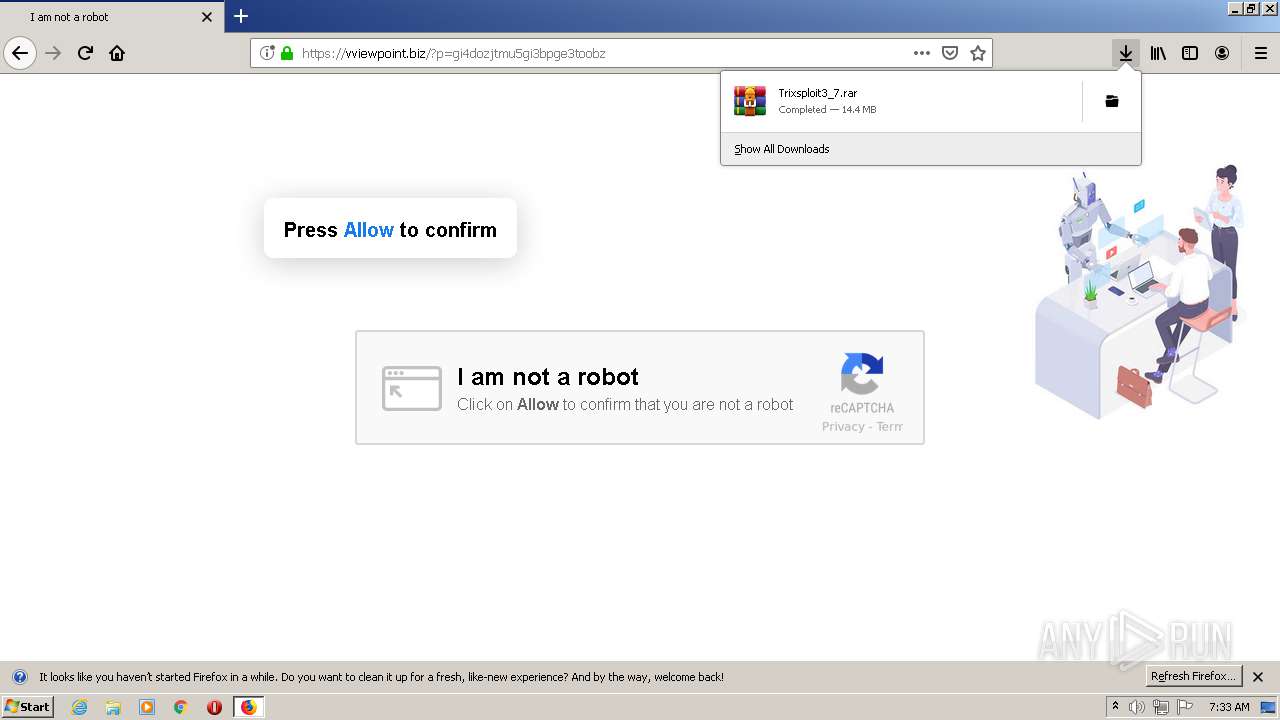
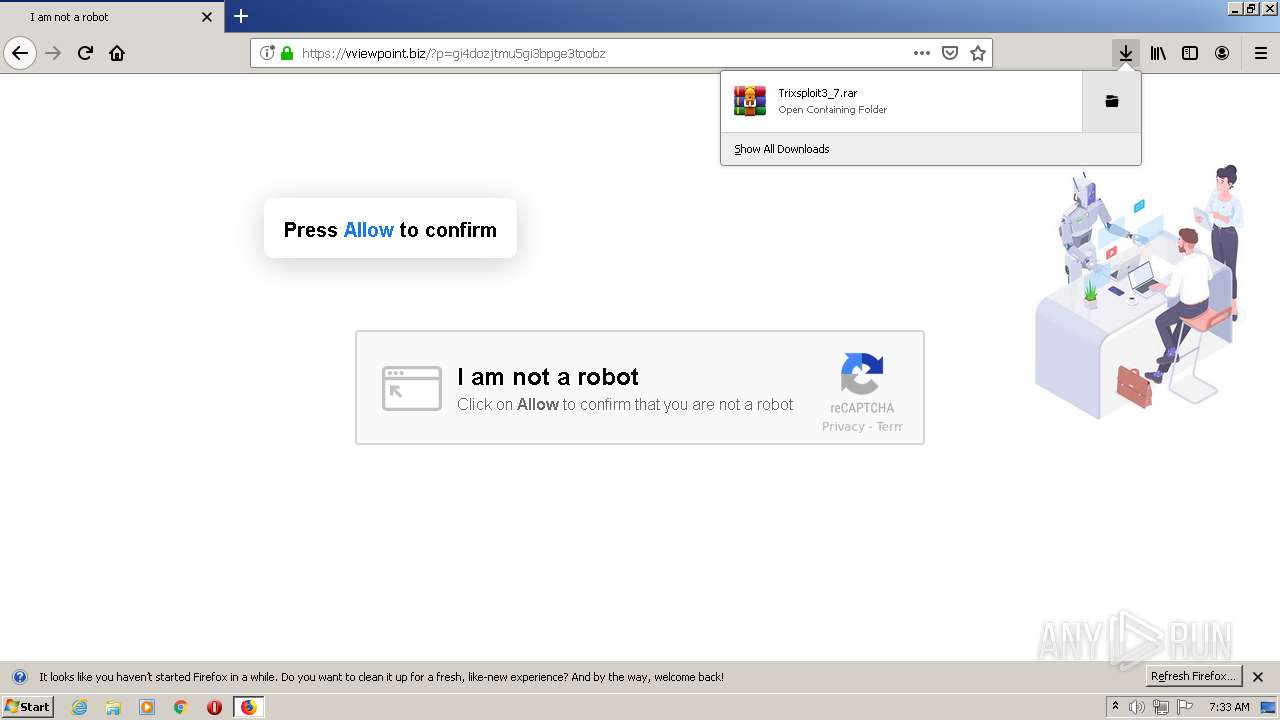
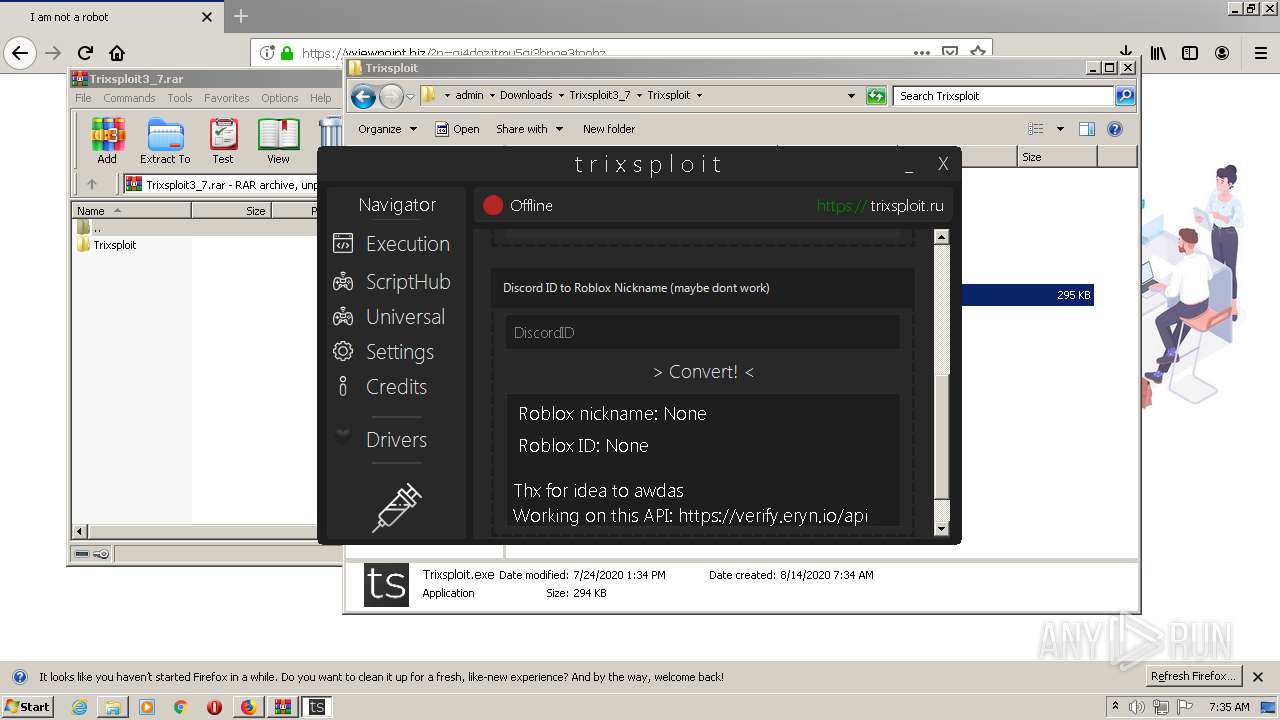
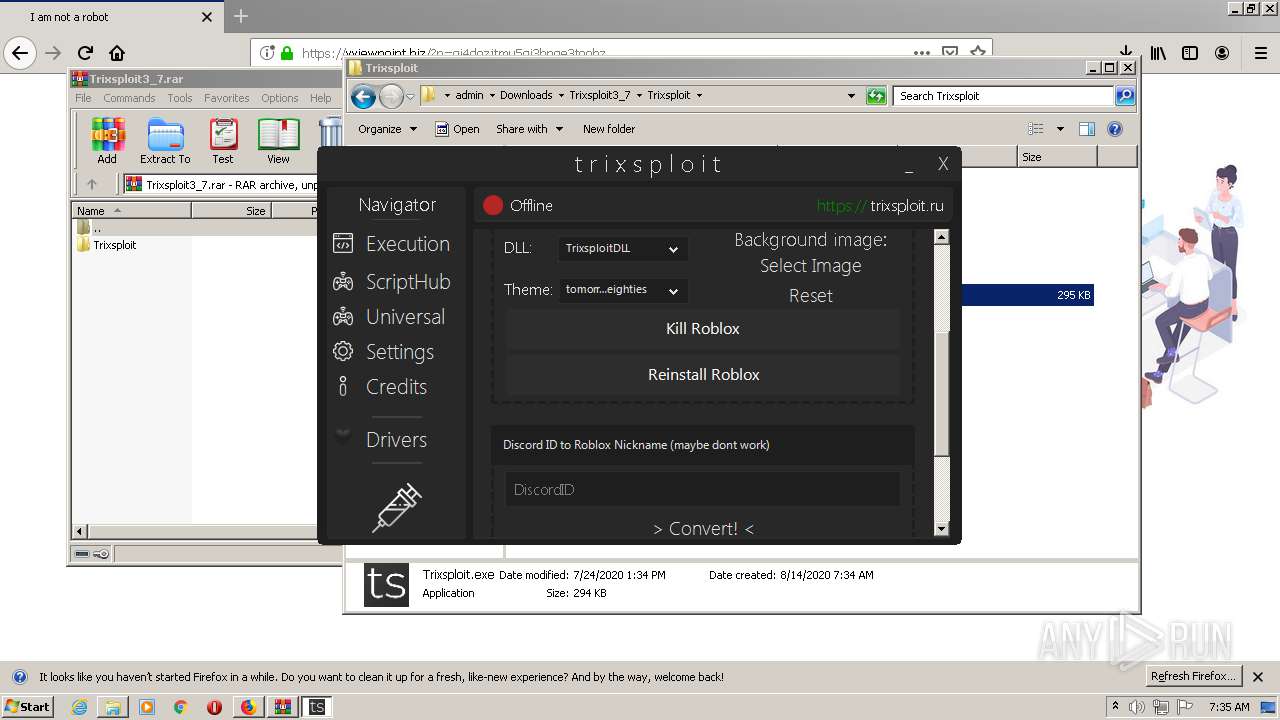
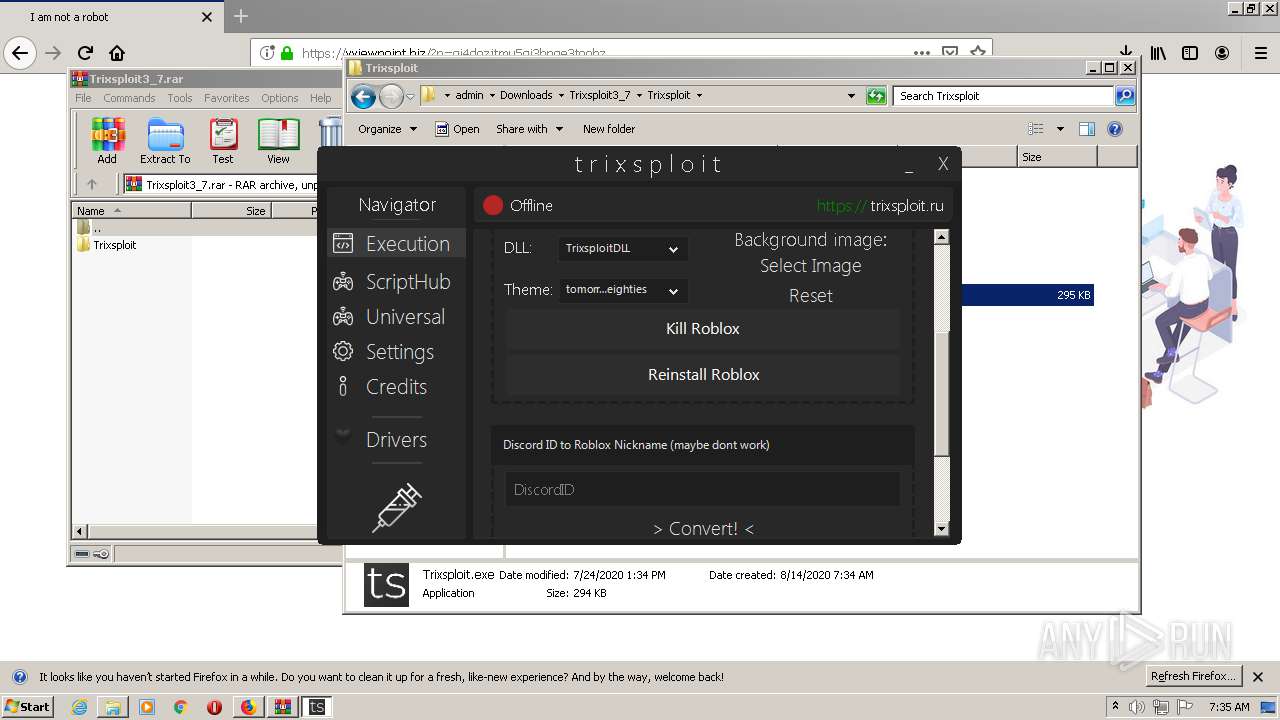
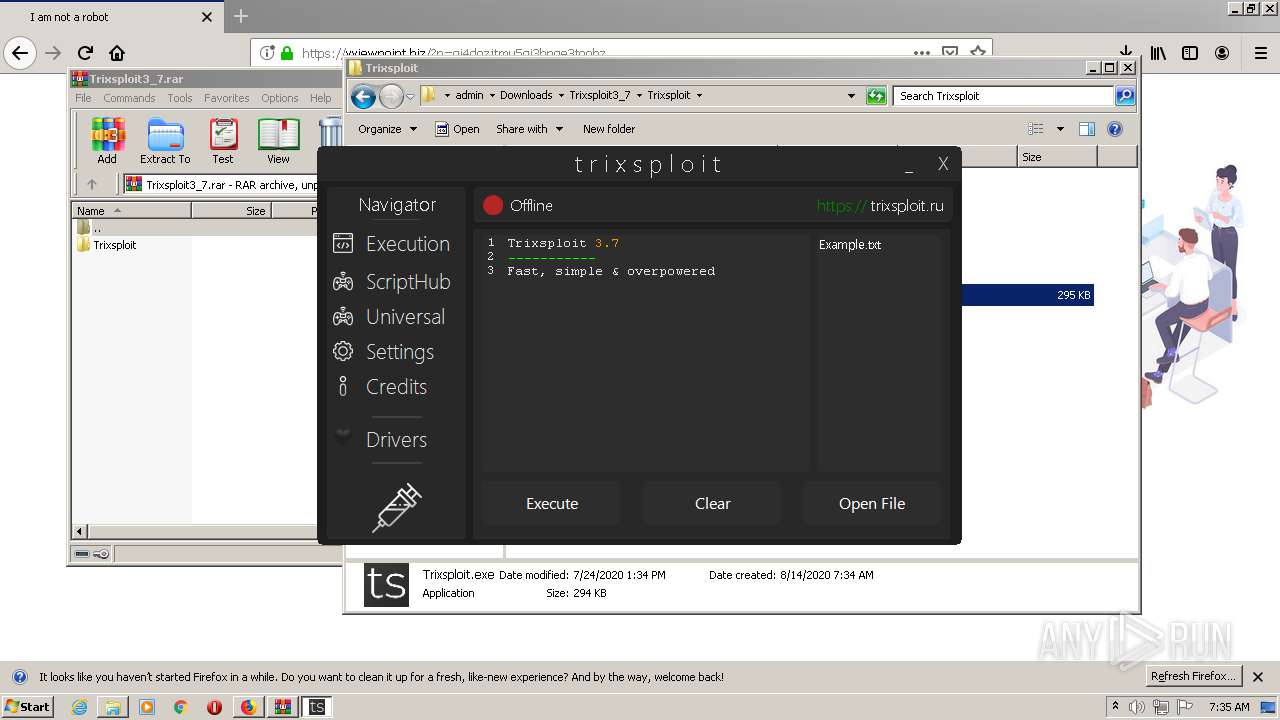
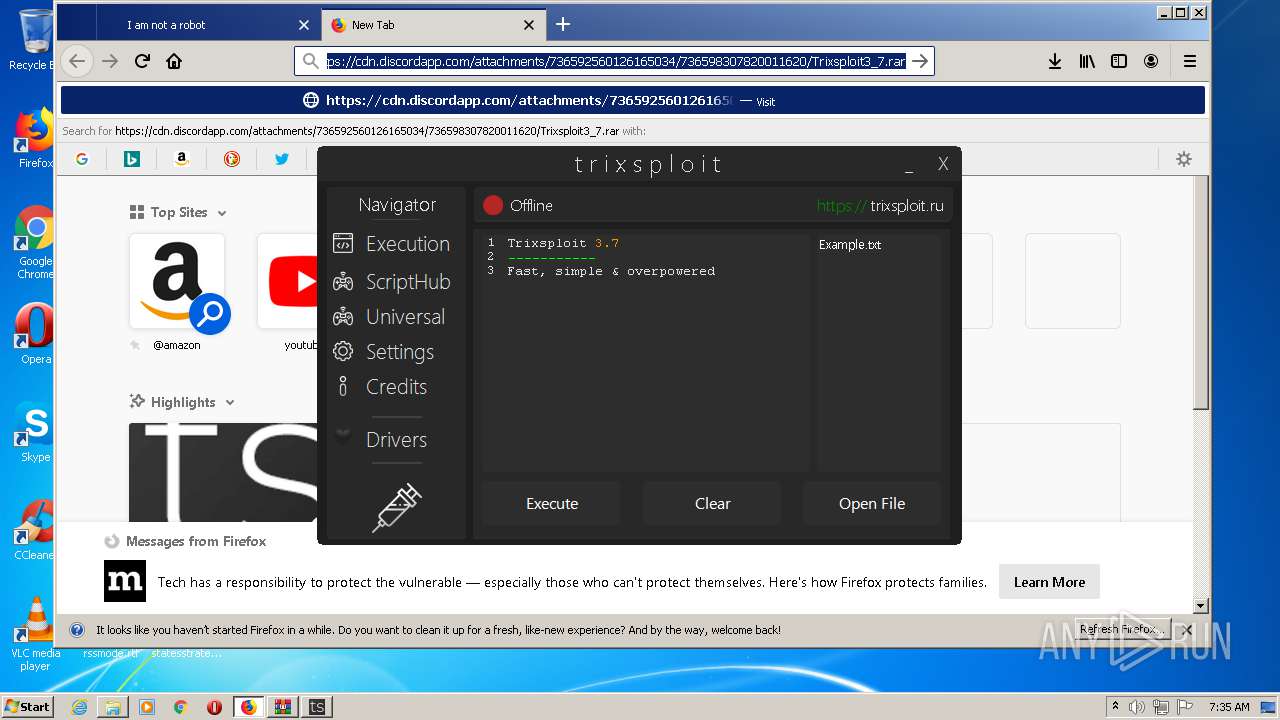
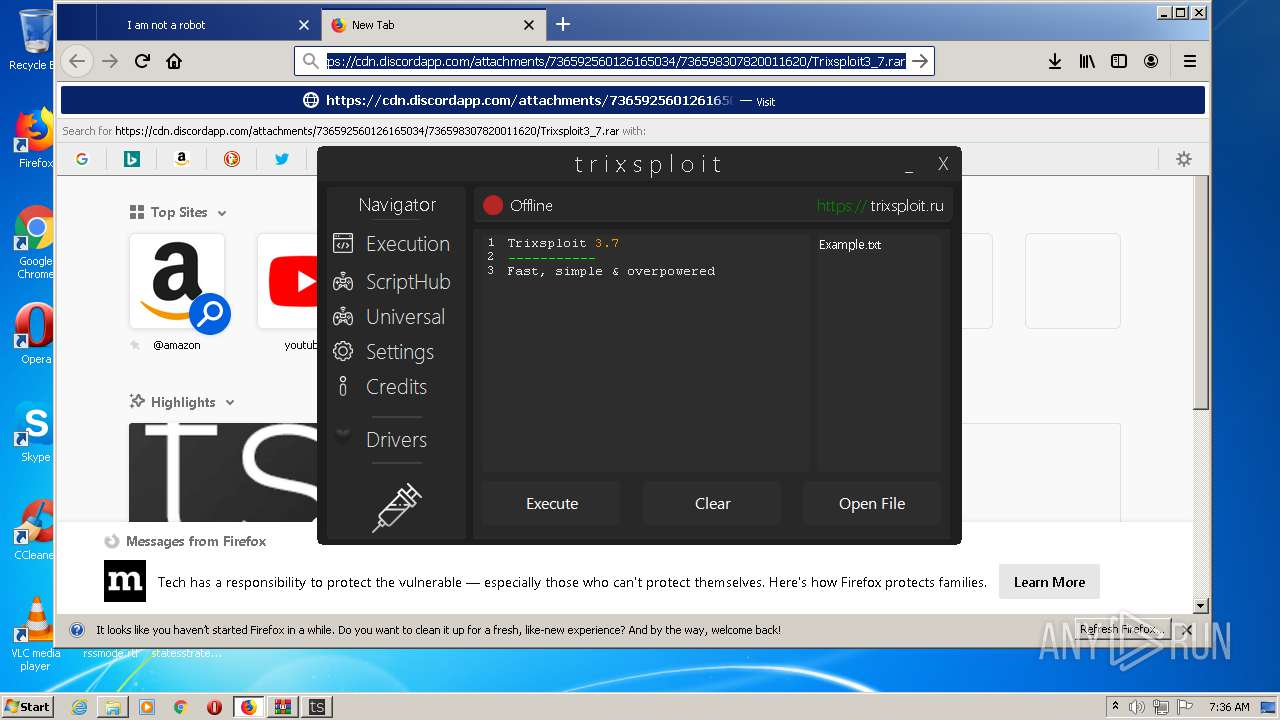
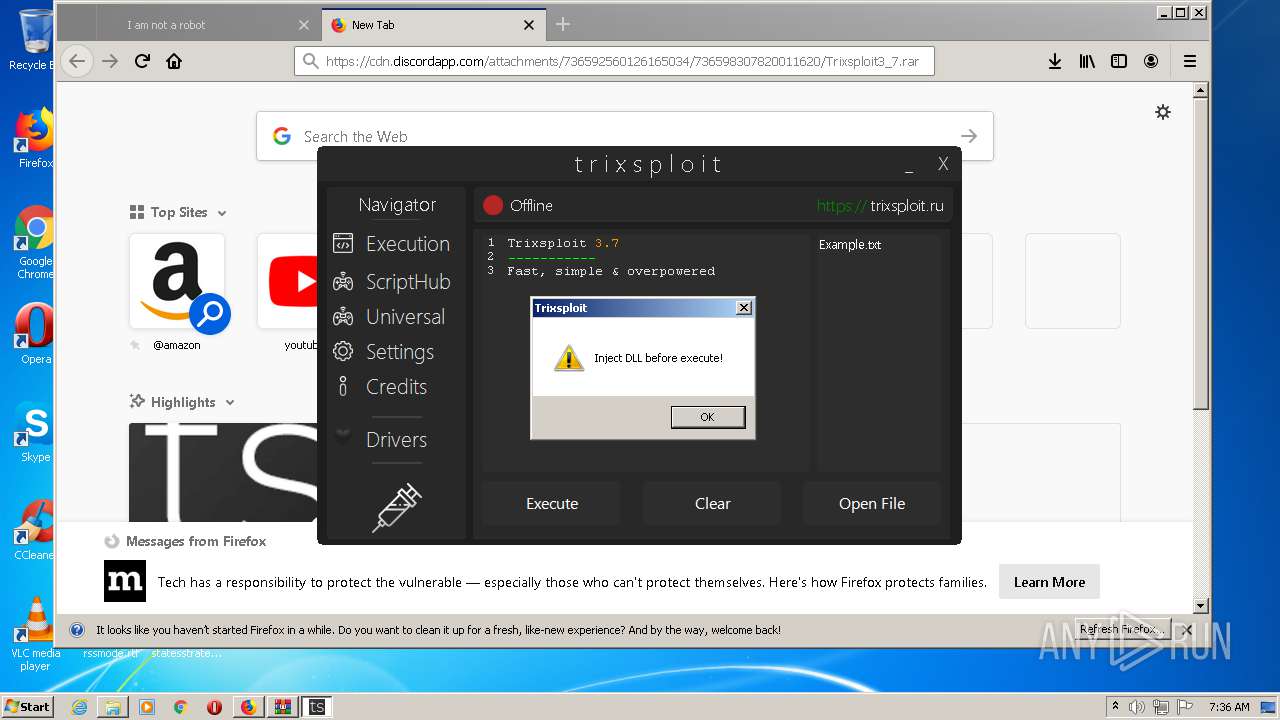
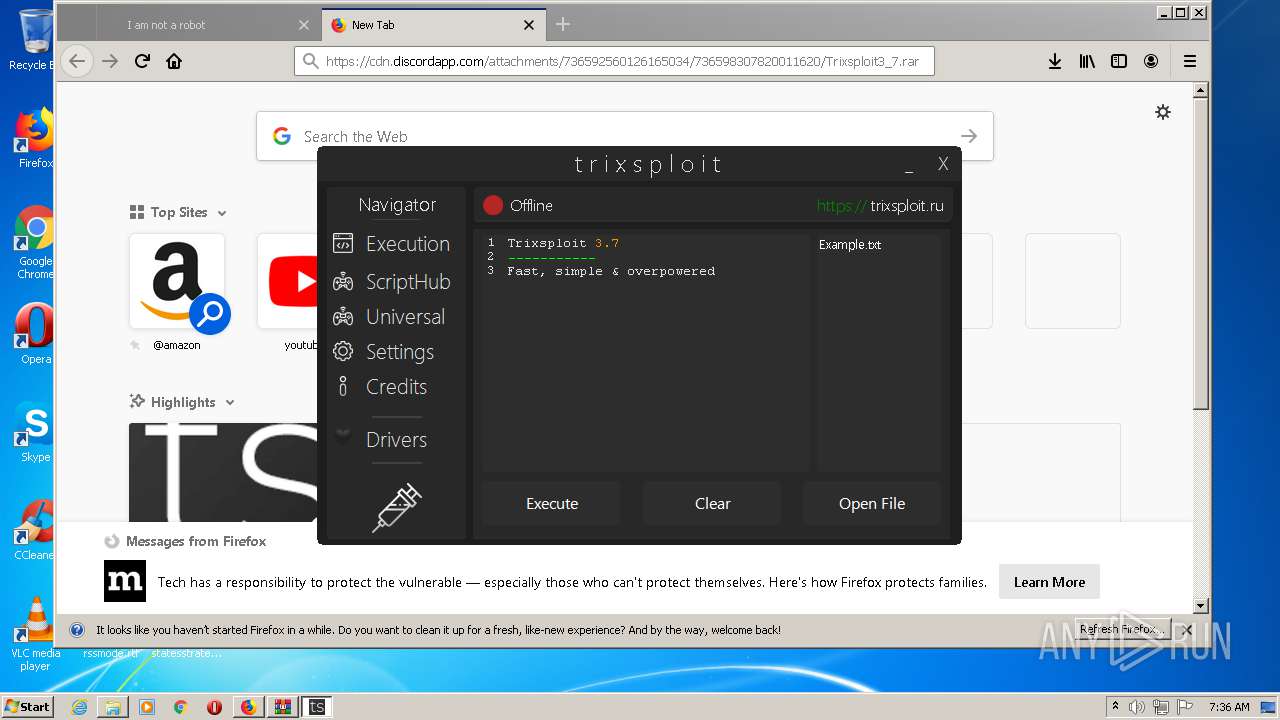
| File name: | index.html |
| Full analysis: | https://app.any.run/tasks/40cd4ef0-9d50-4a2d-911a-4503ffc74987 |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2020, 06:32:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 052273159D4F9EF928E3548E611477A8 |
| SHA1: | BFC71687A008E731541228AEA3CFB924140B86E9 |
| SHA256: | A48C2A5D389D01823773E13CBE6E6FDB069FEFD2FB0BDF778F98CEF3DE7BFD43 |
| SSDEEP: | 384:vdhboOOOwmwtOFow7nwLiwPiwtO0fFS03Z3szaFzNJHbgyYLk:vdhboOOOzYoKRXBzYA |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3464)
- Trixsploit.exe (PID: 1560)
Application was dropped or rewritten from another process
- Trixsploit.exe (PID: 1700)
- Trixsploit.exe (PID: 1560)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 4032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1400)
Modifies the open verb of a shell class
- Trixsploit.exe (PID: 1560)
Starts Internet Explorer
- Trixsploit.exe (PID: 1560)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2808)
- iexplore.exe (PID: 2132)
Reads internet explorer settings
- iexplore.exe (PID: 2544)
- iexplore.exe (PID: 1900)
Reads Internet Cache Settings
- iexplore.exe (PID: 2808)
- firefox.exe (PID: 4032)
- iexplore.exe (PID: 2132)
- iexplore.exe (PID: 1900)
Application launched itself
- iexplore.exe (PID: 2808)
- firefox.exe (PID: 2804)
- firefox.exe (PID: 4032)
- iexplore.exe (PID: 2132)
Manual execution by user
- WinRAR.exe (PID: 1400)
- firefox.exe (PID: 2804)
- Trixsploit.exe (PID: 1700)
Changes settings of System certificates
- iexplore.exe (PID: 2544)
- iexplore.exe (PID: 2132)
Reads settings of System Certificates
- iexplore.exe (PID: 2544)
- iexplore.exe (PID: 1900)
- iexplore.exe (PID: 2132)
Reads CPU info
- firefox.exe (PID: 4032)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2544)
- iexplore.exe (PID: 2132)
Creates files in the user directory
- iexplore.exe (PID: 2544)
- firefox.exe (PID: 4032)
- iexplore.exe (PID: 1900)
- iexplore.exe (PID: 2132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| viewport: | width=device-width, initial-scale=1.0 |
|---|---|
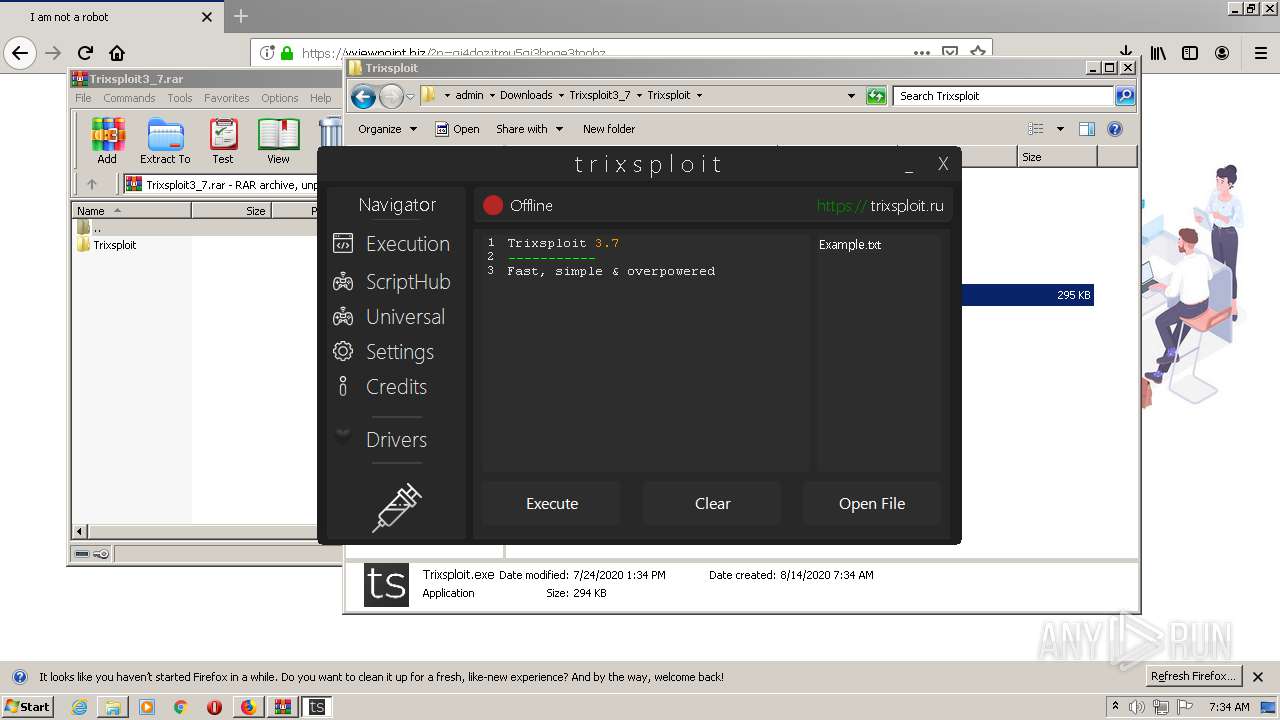
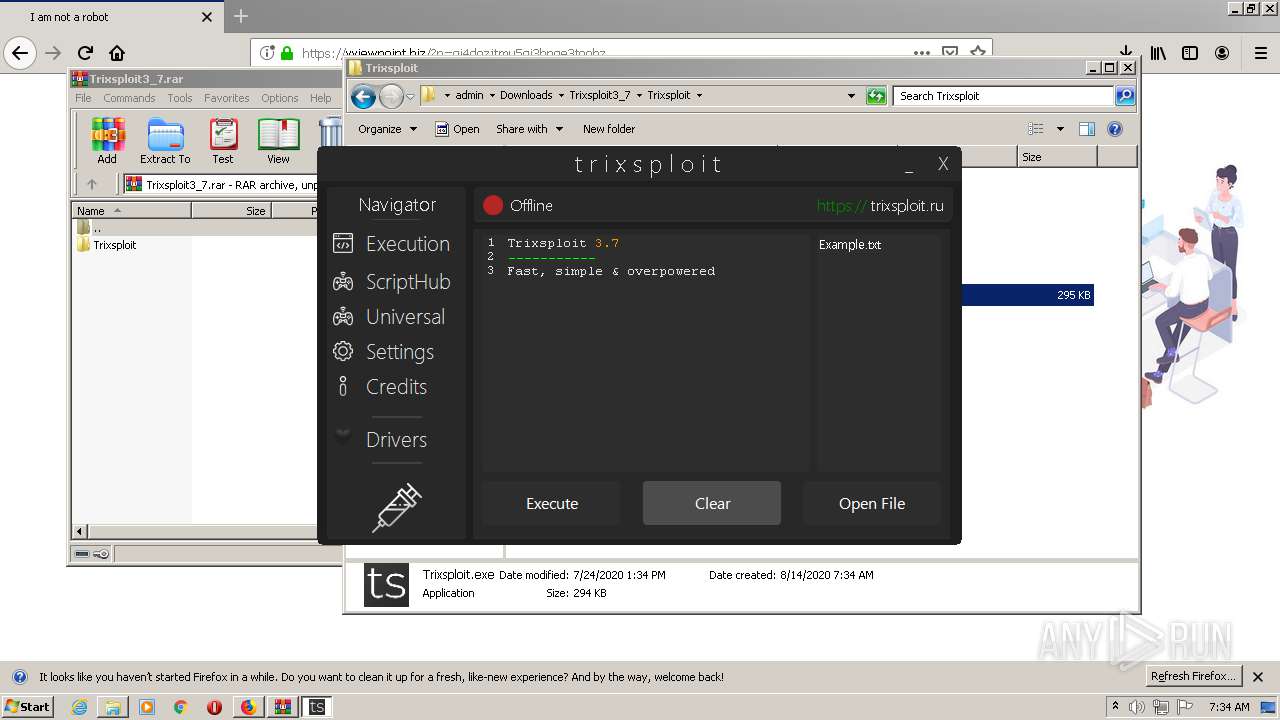
| Author: | Sadtrixio |
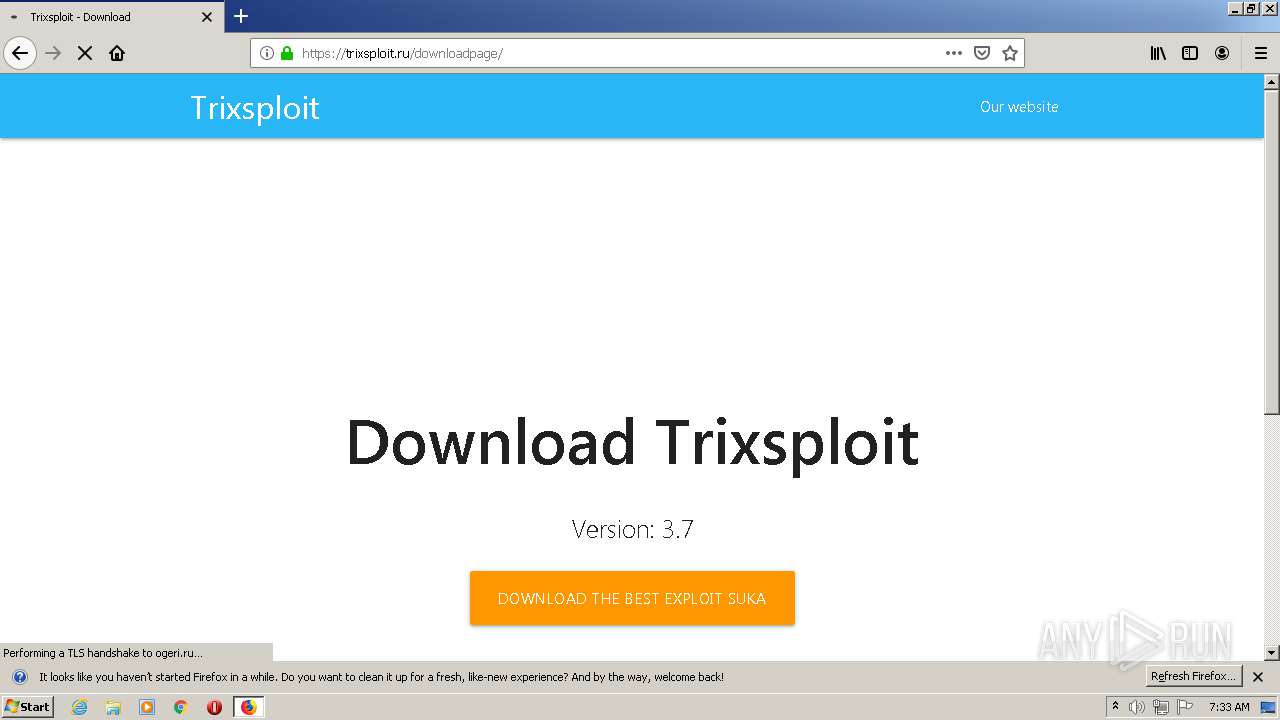
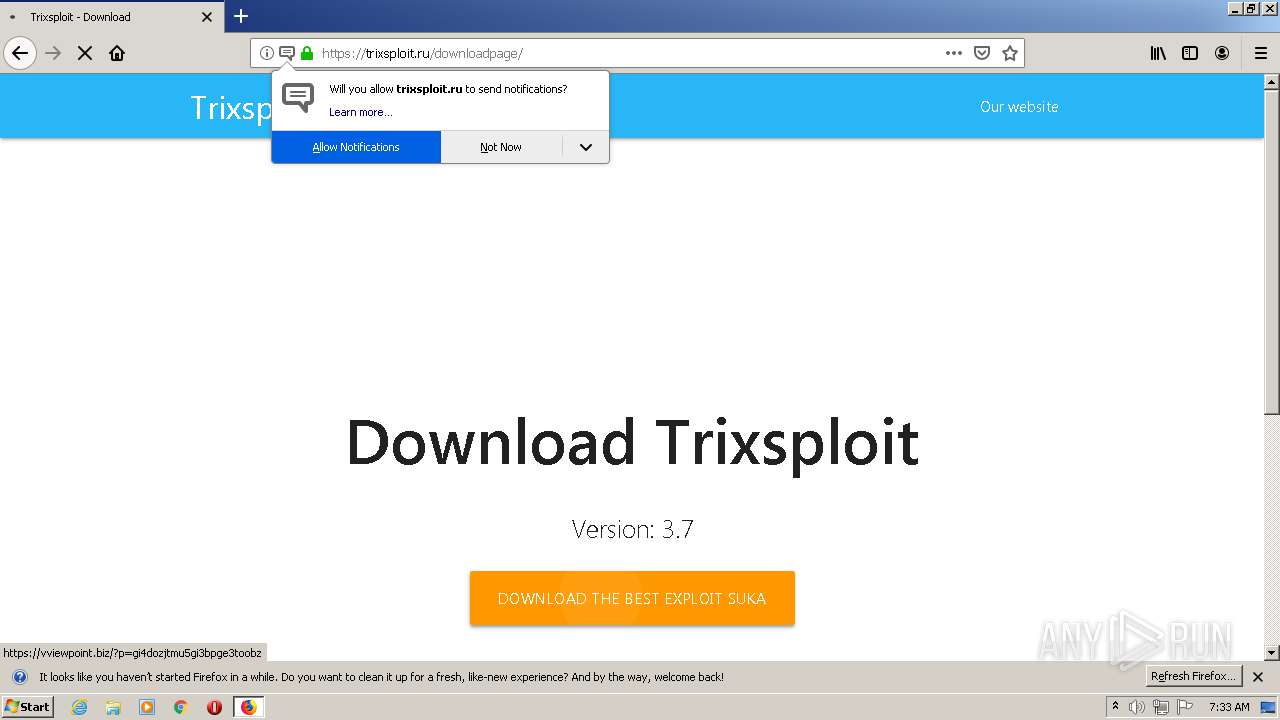
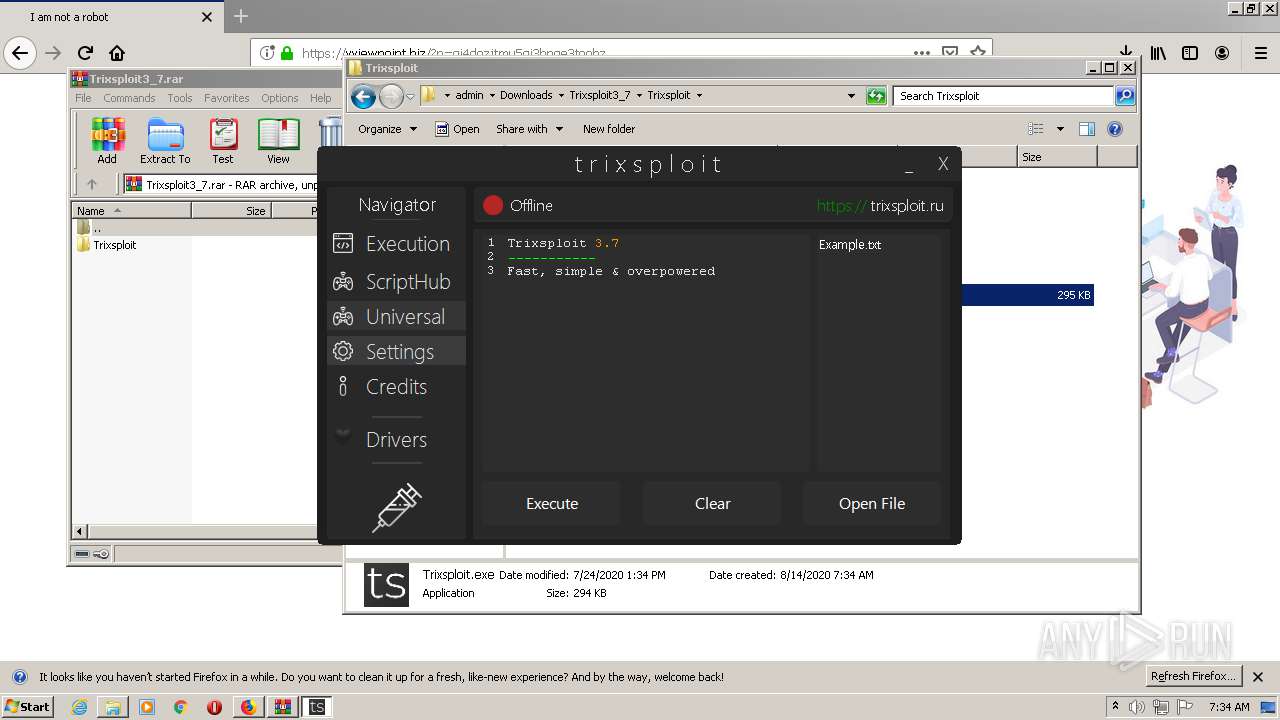
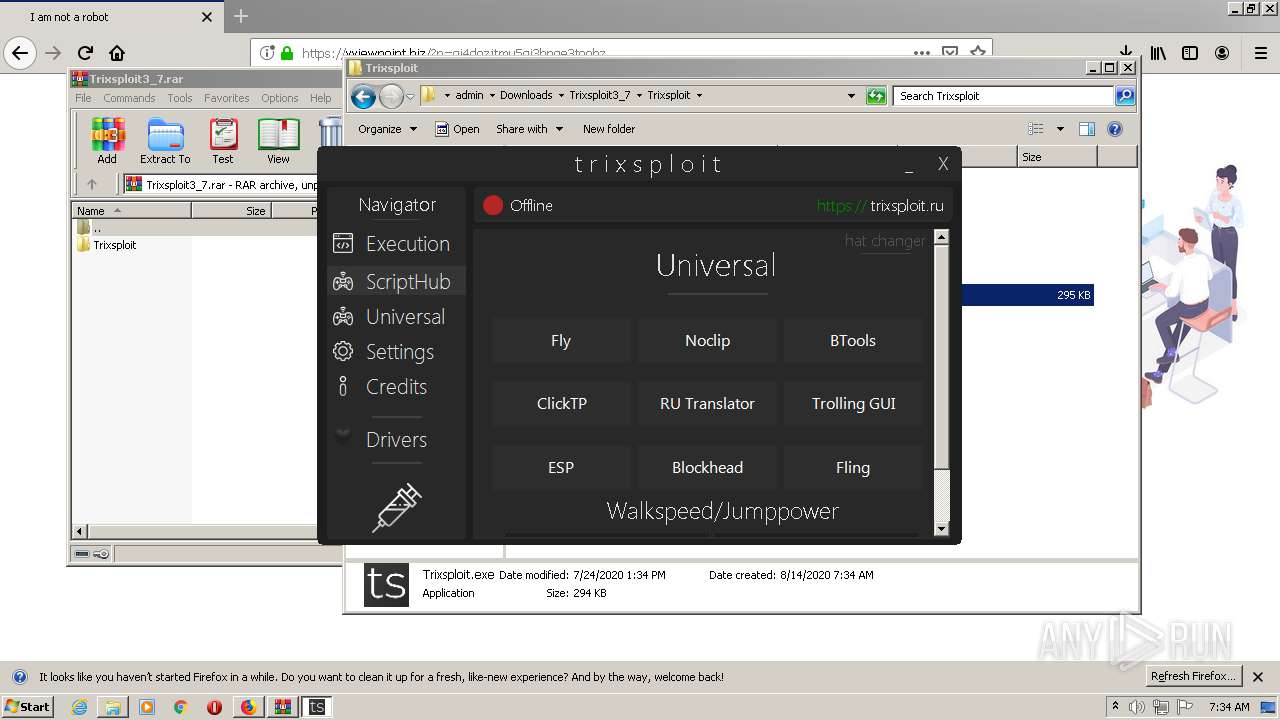
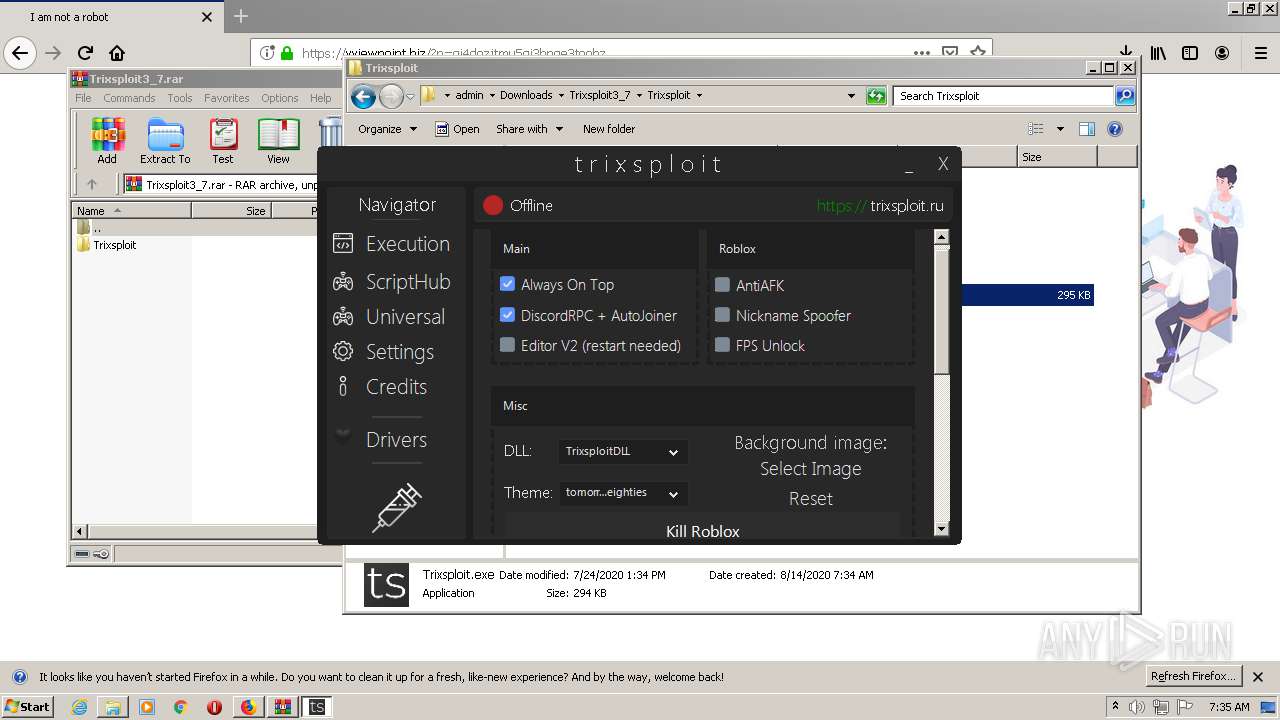
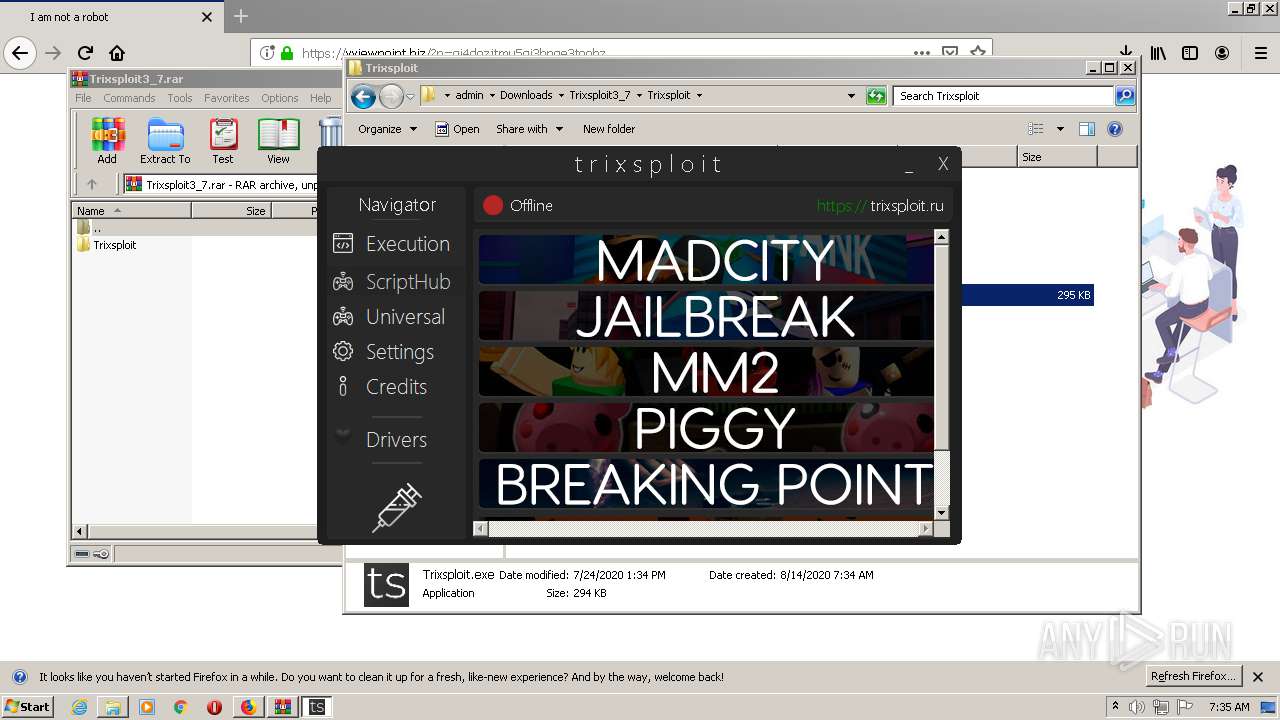
| Description: | Trixsploit. The best exploit for ROBLOX. |
| Keywords: | Trixsploit, Roblox, ROBLOX, Триксплоит, Роблокс, Садтриксио, Садтриксио, чит для роблокс, Exploit, Exploit for ROBLOX, чит для ROBLOX, Sadtrixio, Трихплоит, трикс, чит на роблокс, лучший чит роблокс, чит на роблокс 2020, читы роблокс, взлом роблокс, Roblox чит, роблокс эксплоит, хак роблокс, эксплоит на Roblox, roblox exploit, садриксо, садриксио, cheat roblox, крутой чит на роблокс, читы на roblox, скачать читы роблокс 2019, скачать читы roblox, чит roblox, гей, мер, зе, геймер, алексей, володин, хак, roblox hack 2019, hack robux, hack roblox mad city, free robux 2019, новый чит на мед сити, roblox hack 2018, hack roblox jailbreak, взлом роблокс 2018, чит роблокс 2018, взлом роблокса на робуксы 2018, новый чит на роблокс, новый хак на роблокс, как взломать роблокс, как читерить в роблокс, новый чит на roblox, новый хак на roblox, как взломать роблокс, читы на roblox 2020, new roblox exploit 2020, roblox exploit 2020, new exploit roblox |
| Title: | Trixsploit |
Total processes
58
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
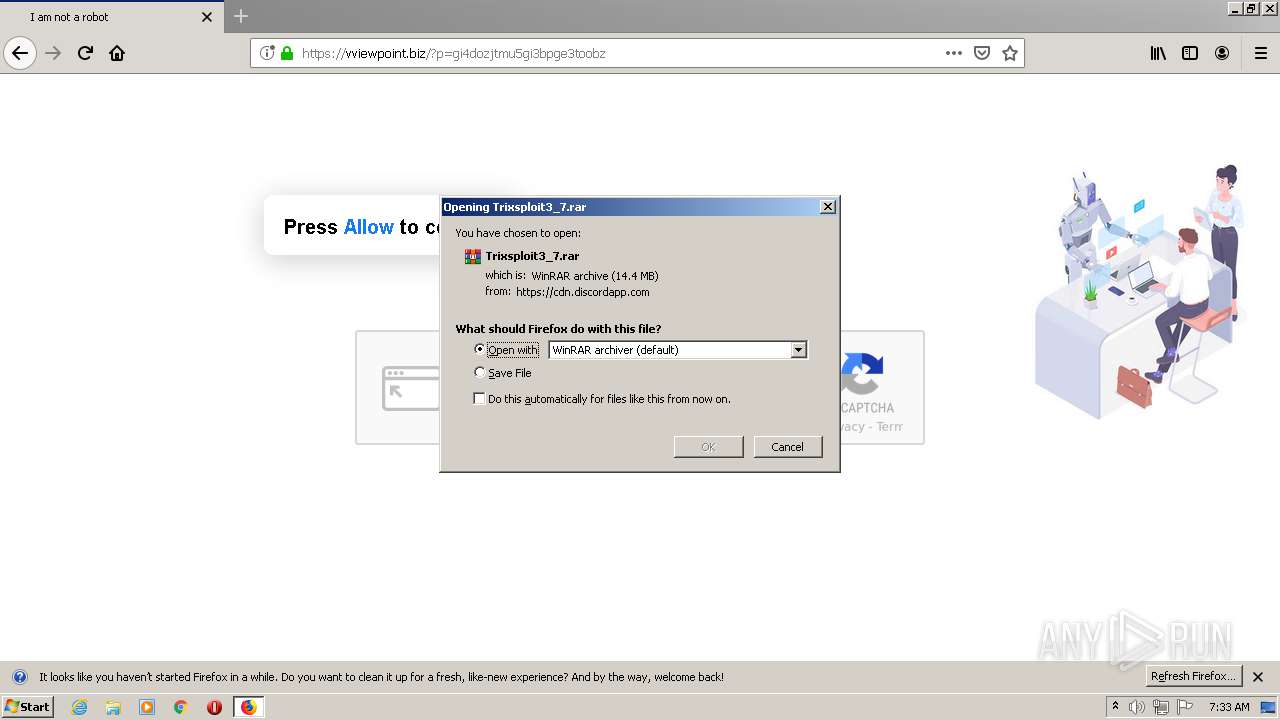
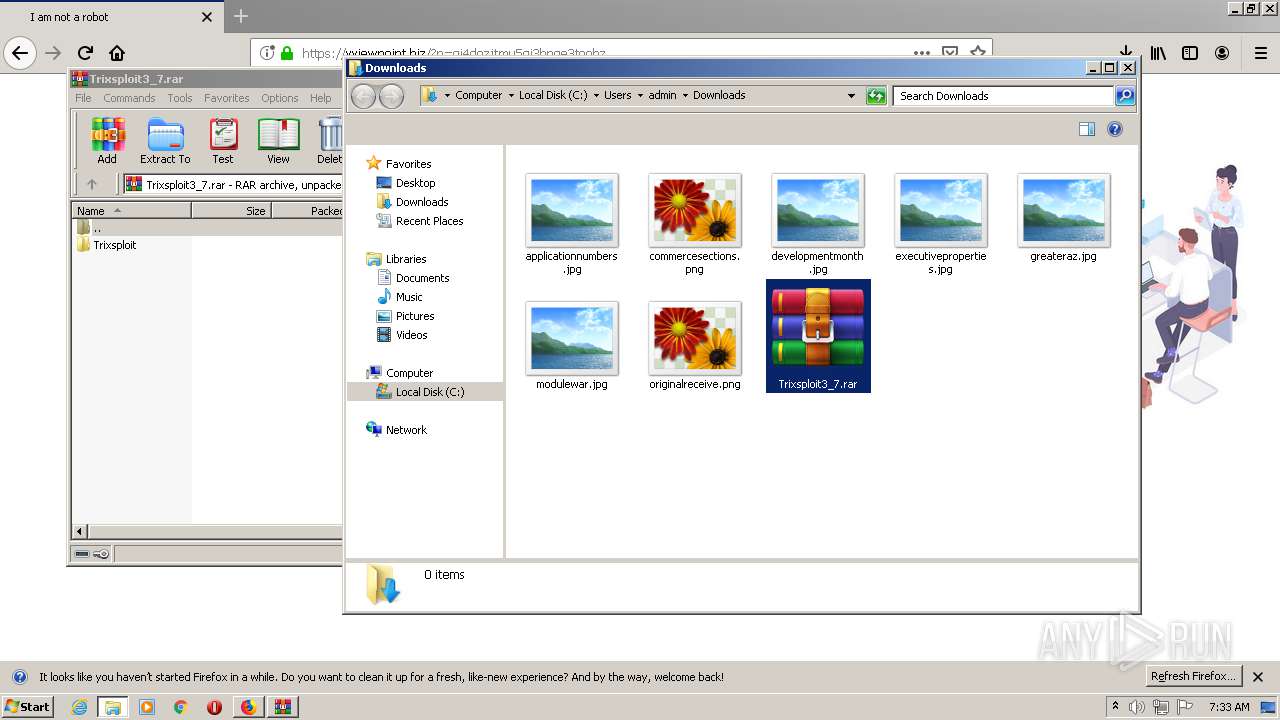
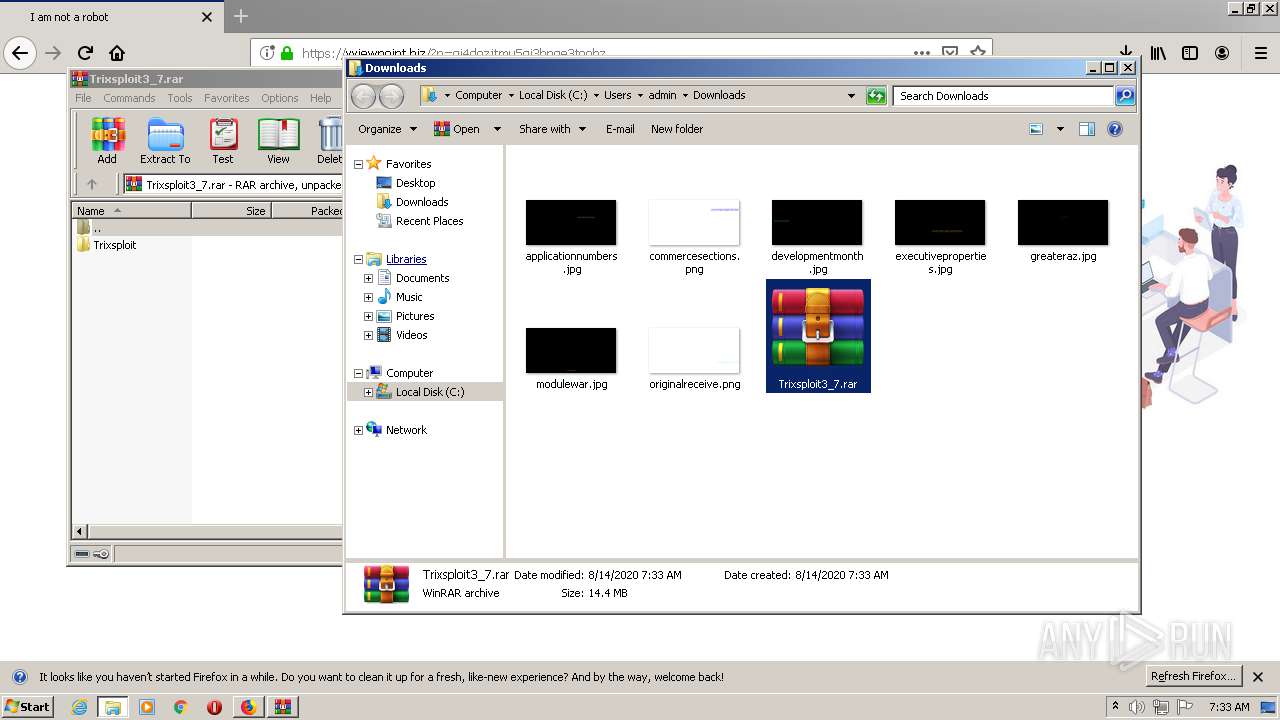
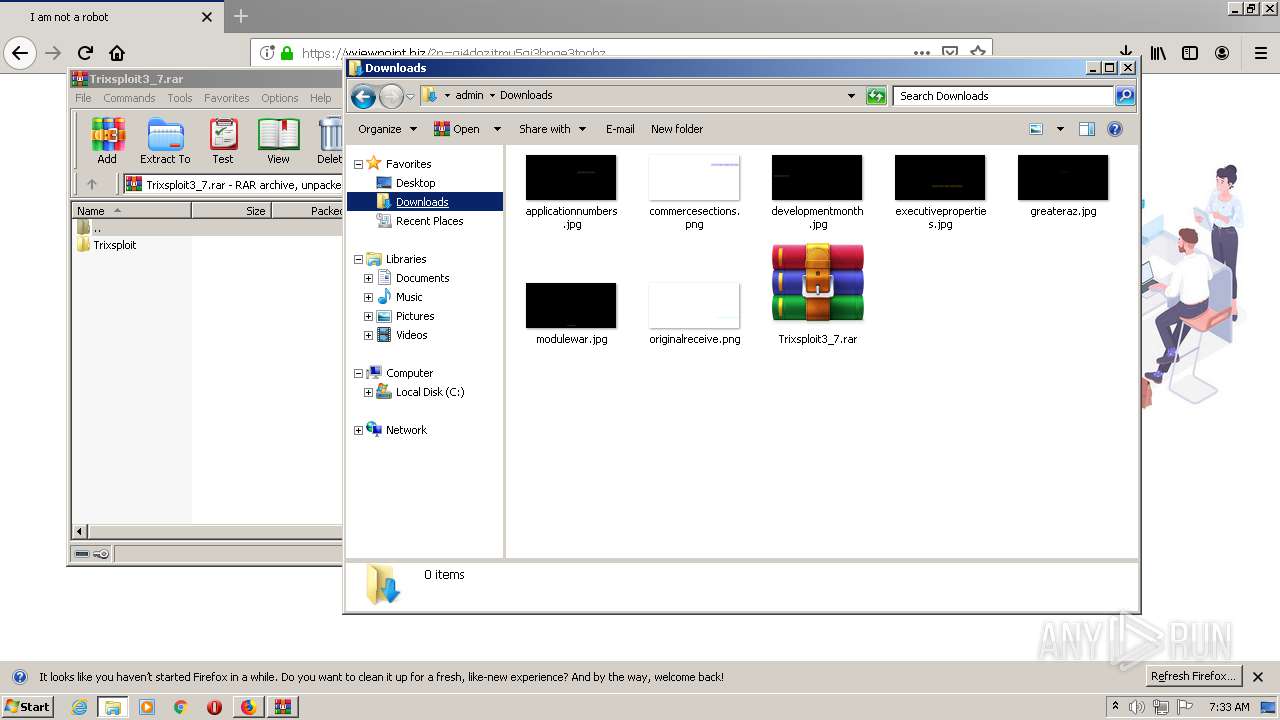
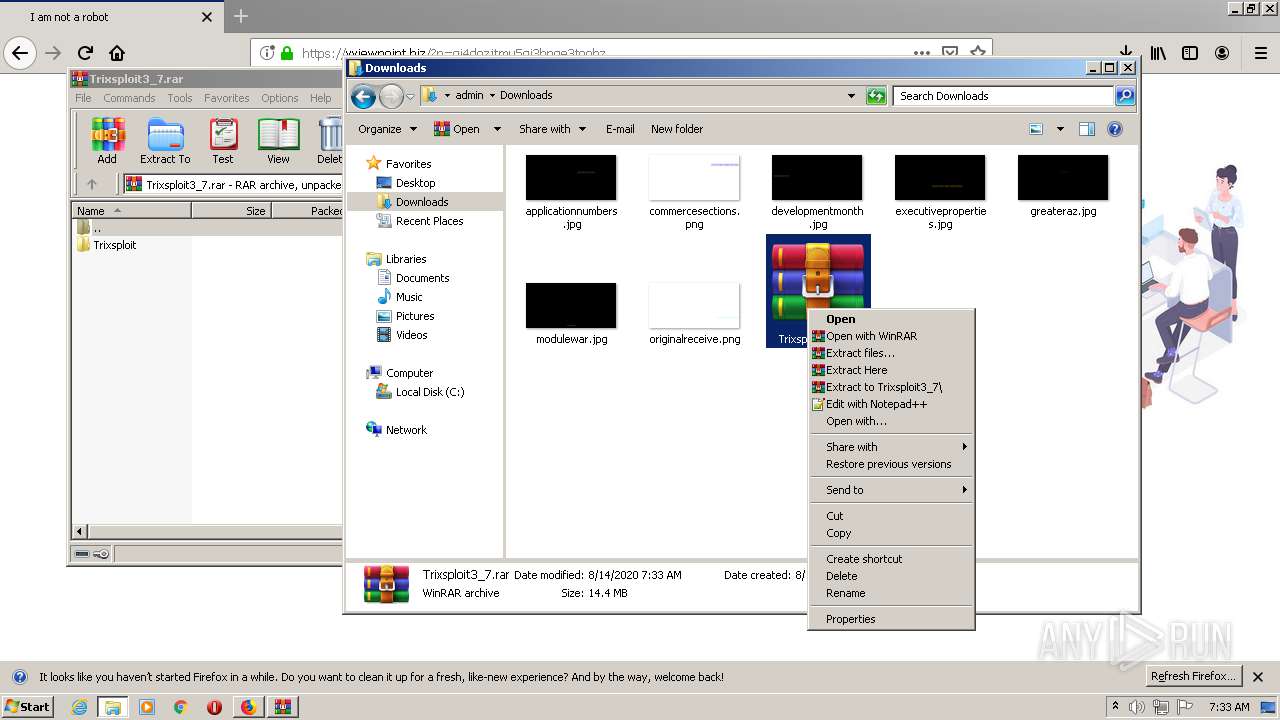
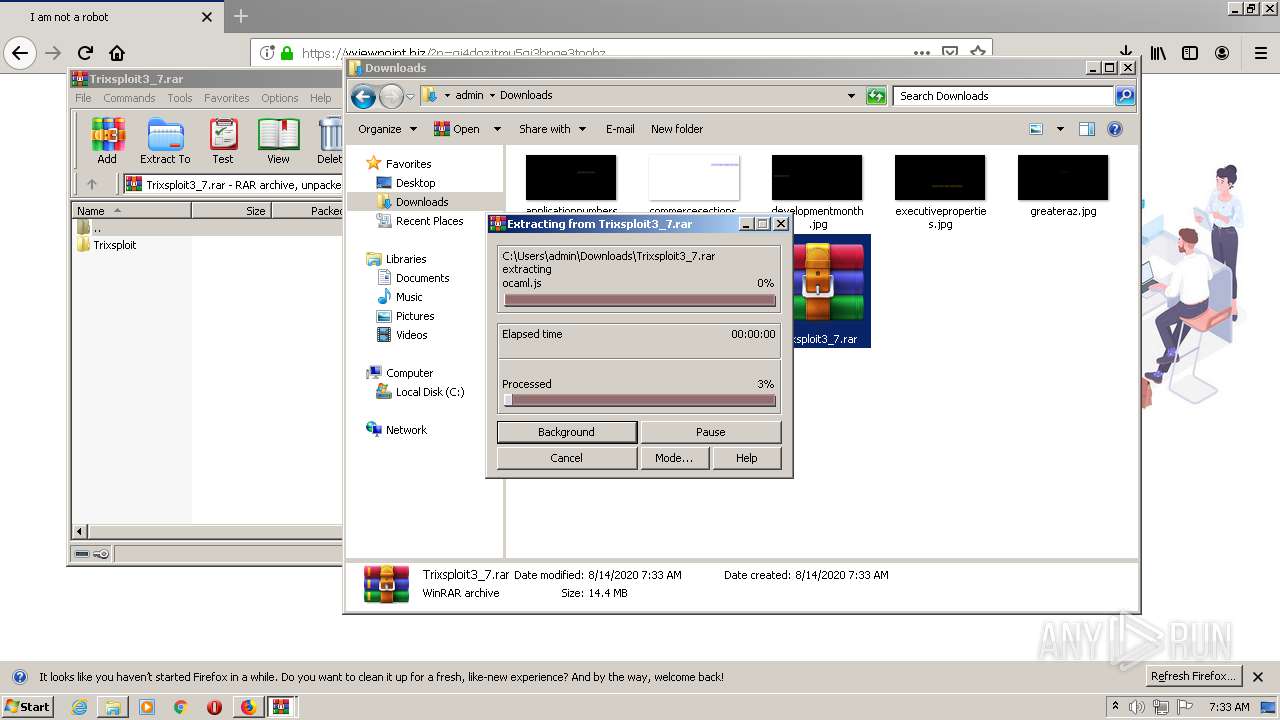
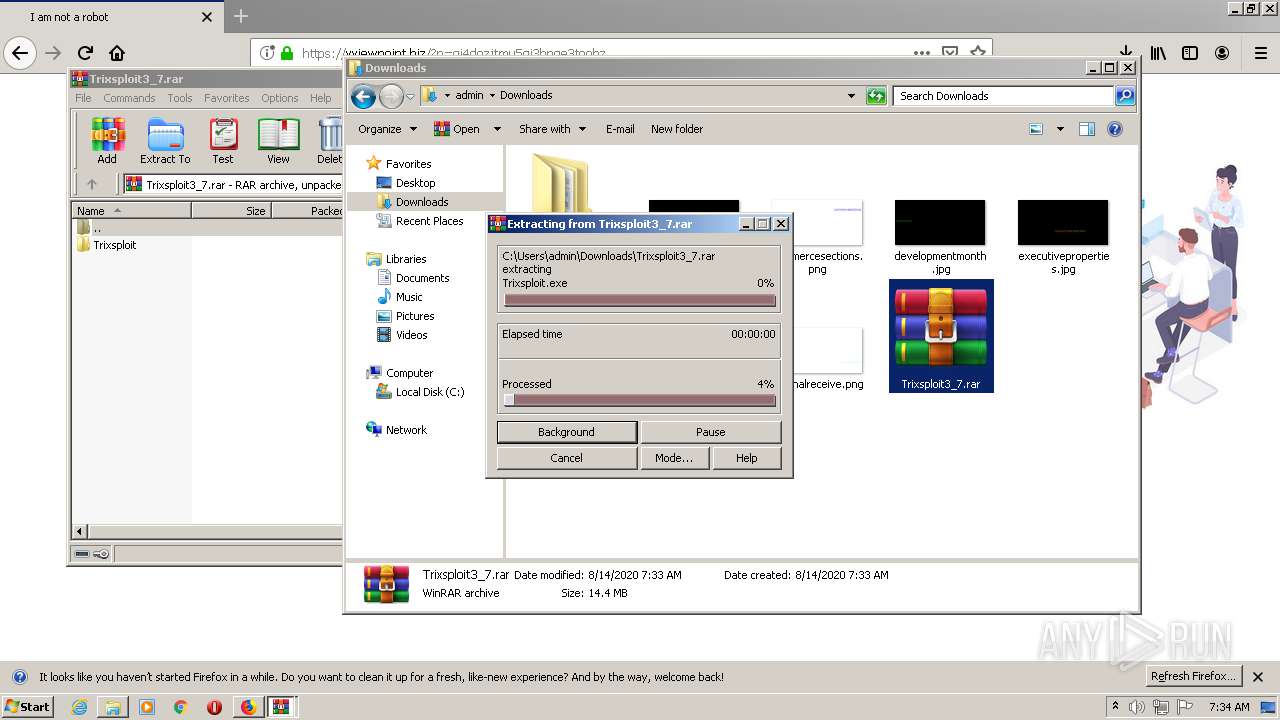
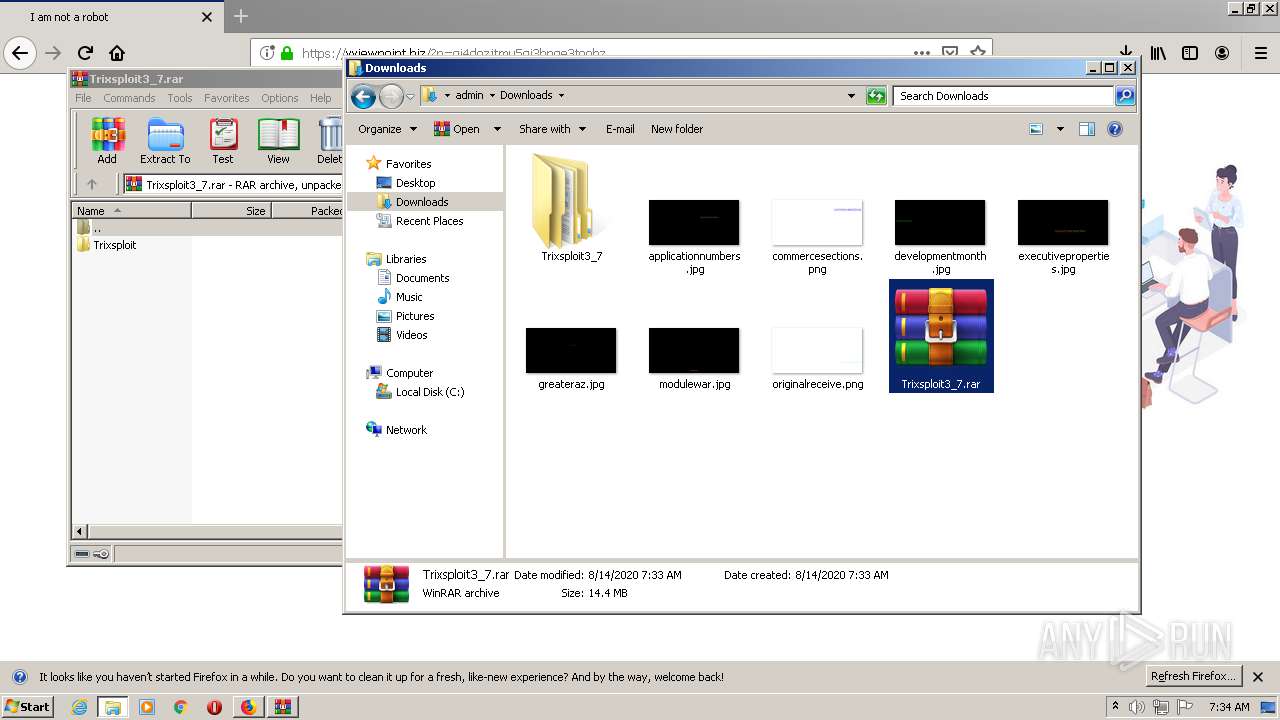
| 1400 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Trixsploit3_7.rar" C:\Users\admin\Downloads\Trixsploit3_7\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
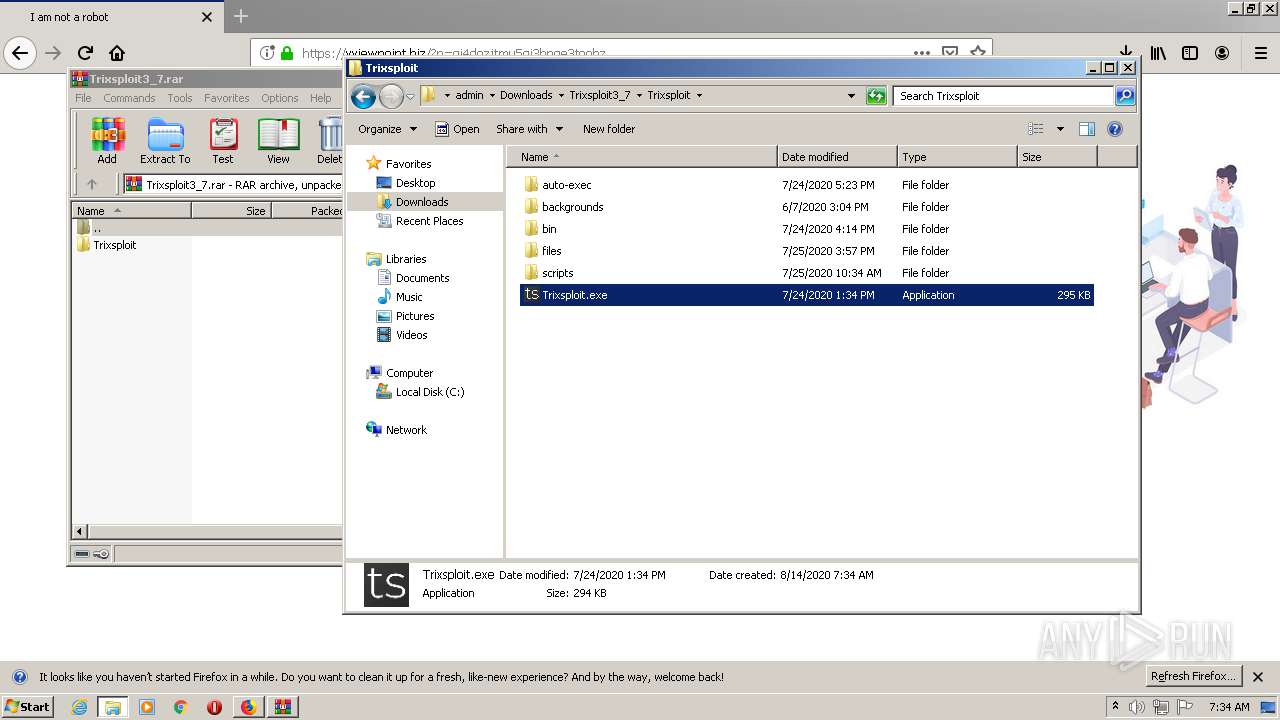
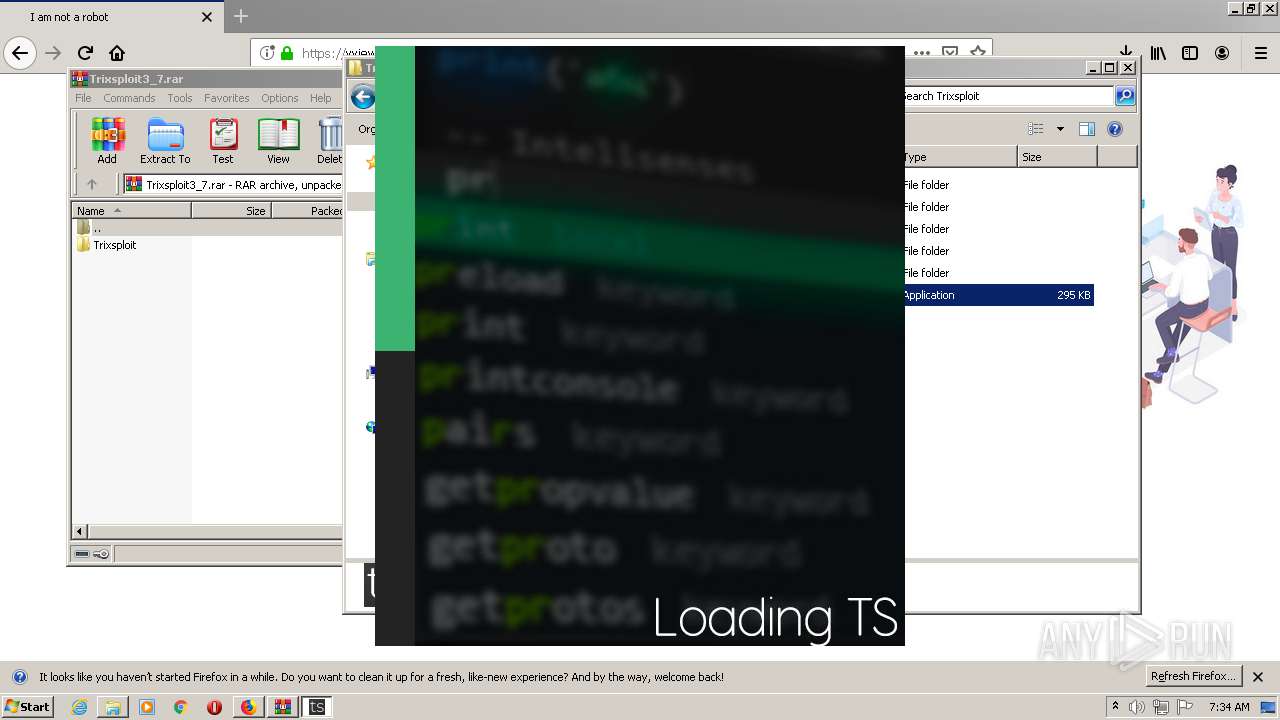
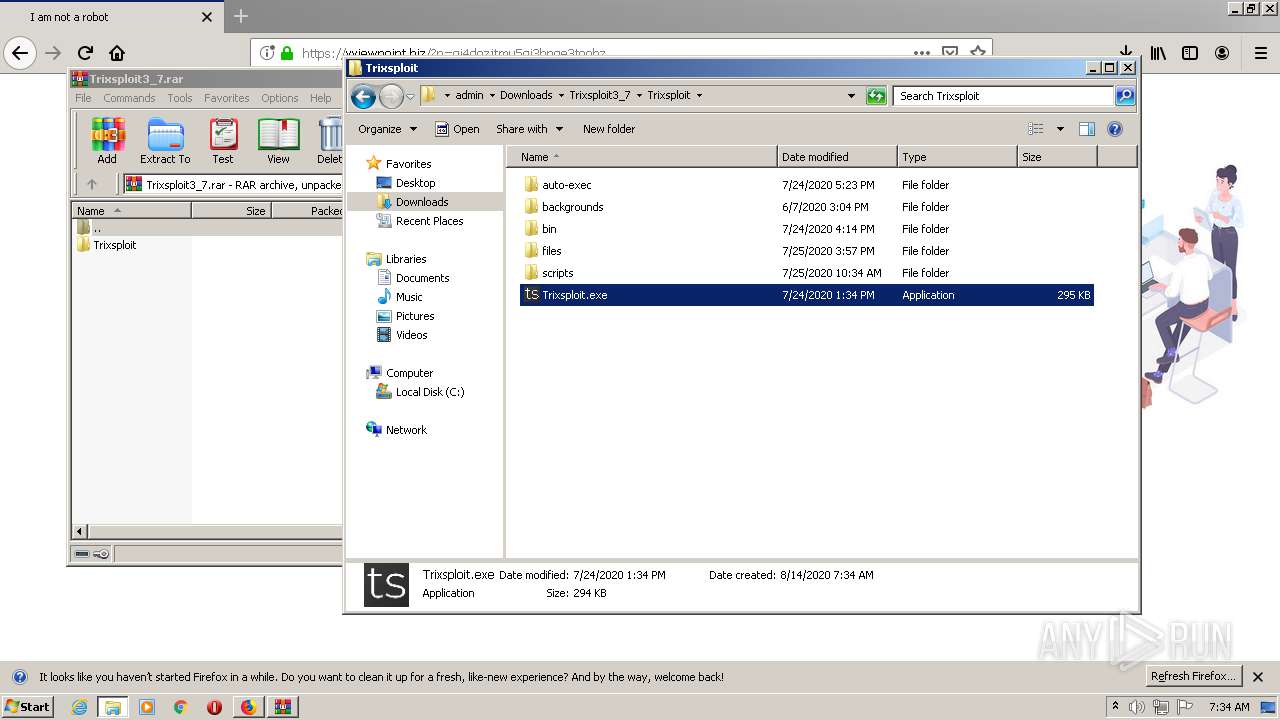
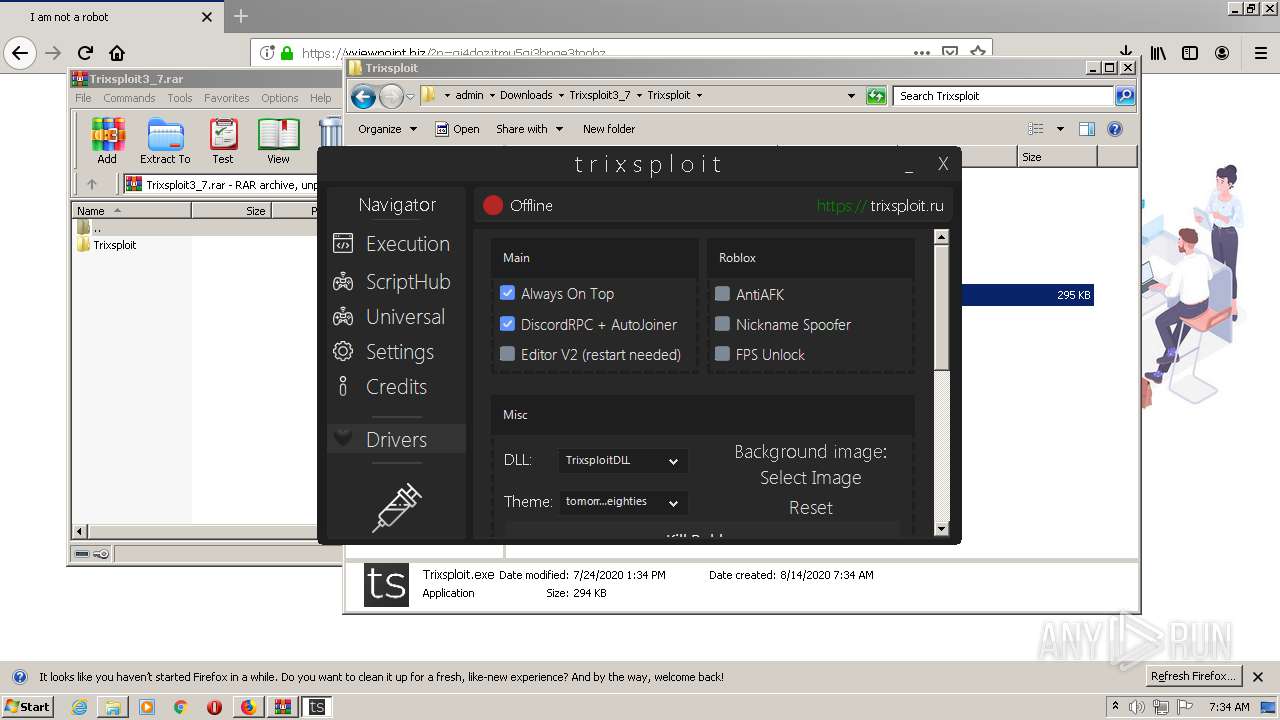
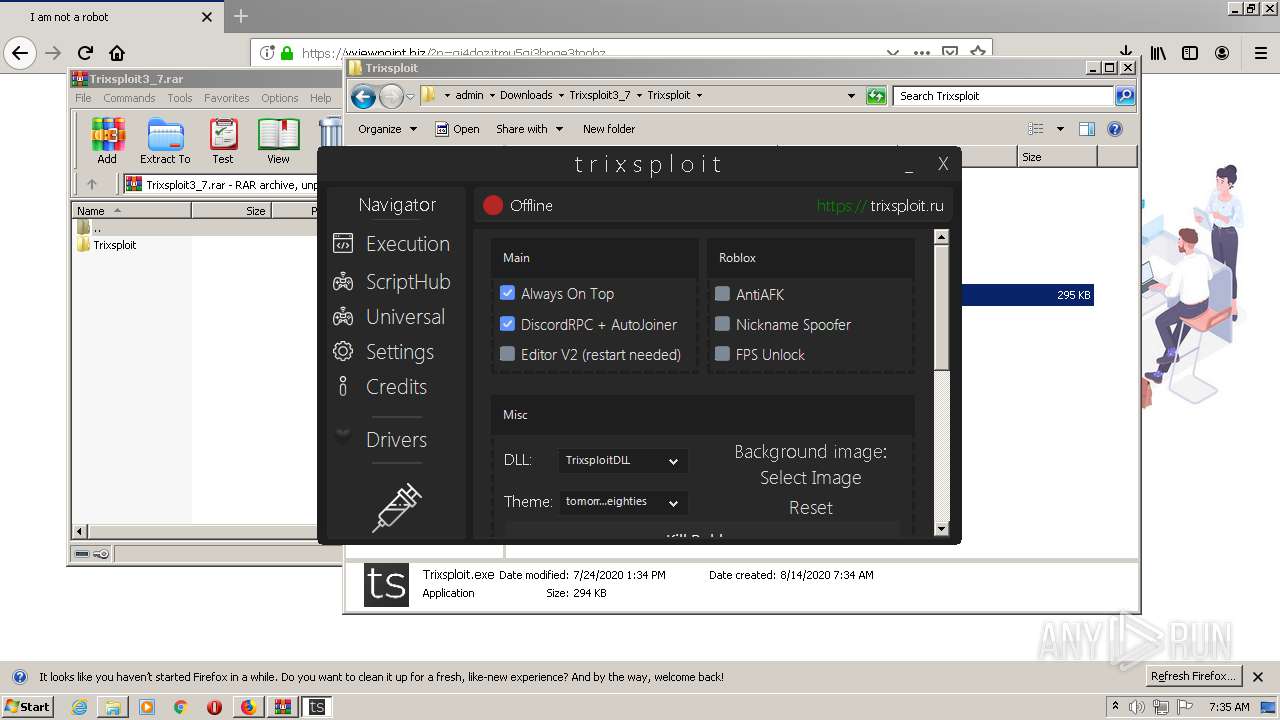
| 1560 | "C:\Users\admin\Downloads\Trixsploit3_7\Trixsploit\files\Trixsploit.exe" | C:\Users\admin\Downloads\Trixsploit3_7\Trixsploit\files\Trixsploit.exe | — | Trixsploit.exe | |||||||||||
User: admin Company: TrixsploitTeam Integrity Level: MEDIUM Description: Trixsploit Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\Downloads\Trixsploit3_7\Trixsploit\Trixsploit.exe" | C:\Users\admin\Downloads\Trixsploit3_7\Trixsploit\Trixsploit.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TrixsploitLoaderUI Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2132 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Trixsploit3_7.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | firefox.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
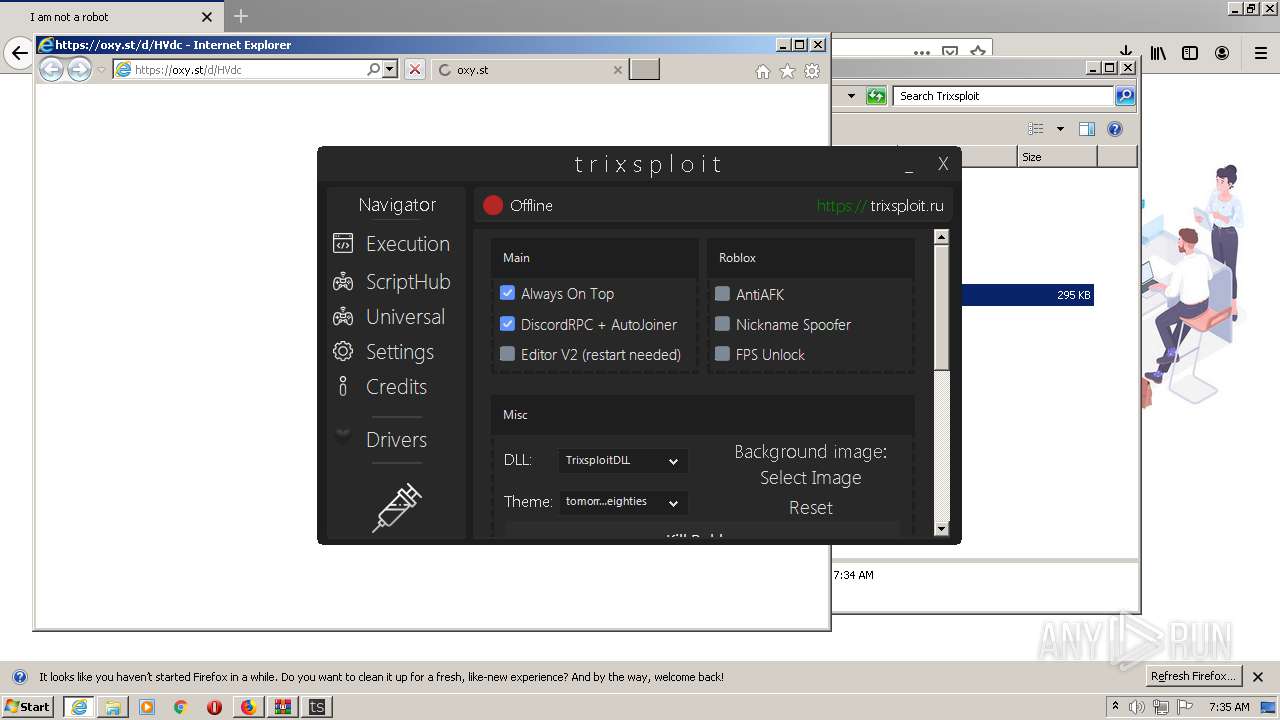
| 2132 | "C:\Program Files\Internet Explorer\iexplore.exe" https://oxy.st/d/HVdc | C:\Program Files\Internet Explorer\iexplore.exe | Trixsploit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4032.0.736031106\1022217499" -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 4032 "\\.\pipe\gecko-crash-server-pipe.4032" 1180 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2444 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4032.20.366804530\757048419" -childID 3 -isForBrowser -prefsHandle 3532 -prefMapHandle 3536 -prefsLen 6718 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 4032 "\\.\pipe\gecko-crash-server-pipe.4032" 3548 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2544 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2808 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4032.27.874396295\1118392567" -childID 4 -isForBrowser -prefsHandle 3468 -prefMapHandle 3472 -prefsLen 8979 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 4032 "\\.\pipe\gecko-crash-server-pipe.4032" 7756 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
Total events
3 567
Read events
3 372
Write events
186
Delete events
9
Modification events
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3276387282 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30831108 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2808) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
9
Suspicious files
340
Text files
381
Unknown types
188
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2808 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab21AD.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar21AE.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_979AB563CEB98F2581C14ED89B8957D4 | der | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\64DCC9872C5635B1B7891B30665E0558_5552C20A2631357820903FD38A8C0F9F | binary | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\091F6C008D0BB73A72ED3FE5724BCED6 | der | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\font-awesome.min[1].css | text | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\64DCC9872C5635B1B7891B30665E0558_5552C20A2631357820903FD38A8C0F9F | der | |
MD5:— | SHA256:— | |||
| 2544 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\170fadab76120c51d0974eaf90094cc4[1].png | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
99
TCP/UDP connections
194
DNS requests
197
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2544 | iexplore.exe | GET | 200 | 195.138.255.16:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.24:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.16:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.24:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.16:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgPsAnGw0%2BoKsmdePdYdPV0BWg%3D%3D | DE | der | 527 b | whitelisted |
2544 | iexplore.exe | GET | 200 | 195.138.255.24:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
2544 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2544 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2544 | iexplore.exe | 172.67.165.8:443 | trixsploit.ru | — | US | malicious |
2544 | iexplore.exe | 104.17.78.107:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2544 | iexplore.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
4 | System | 209.197.3.24:445 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
2808 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 209.197.3.24:137 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
2544 | iexplore.exe | 195.138.255.16:80 | isrg.trustid.ocsp.identrust.com | AS33891 Netzbetrieb GmbH | DE | suspicious |
2544 | iexplore.exe | 195.138.255.24:80 | isrg.trustid.ocsp.identrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
2544 | iexplore.exe | 195.138.255.11:80 | ocsp.int-x3.letsencrypt.org | AS33891 Netzbetrieb GmbH | DE | whitelisted |
2544 | iexplore.exe | 172.217.16.174:443 | www.youtube.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
trixsploit.ru |
| malicious |
cdn.discordapp.com |
| shared |
cdnjs.cloudflare.com |
| whitelisted |
code.jquery.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |