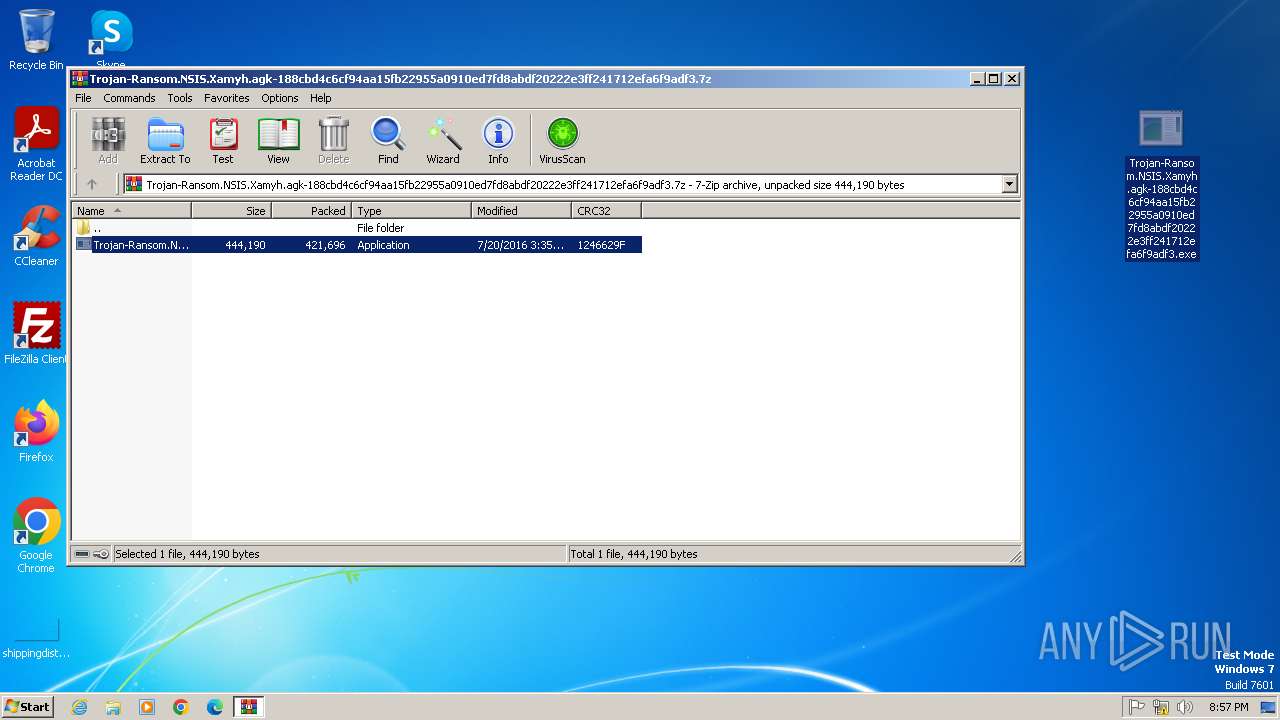
| File name: | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.7z |
| Full analysis: | https://app.any.run/tasks/0479346a-aa6a-43fe-acdd-656b4f358226 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2025, 19:57:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 220052D29E55E1DED49282B3BD7F0F10 |
| SHA1: | 3F464D97AADD649FFB03CE5DD3710D327151D3C4 |
| SHA256: | A472323E23CA726E99ABB56BD4D7DCFAECC3DE380A9F511304097160A0B6885A |
| SSDEEP: | 12288:HbtYfT0RpnOW7nx9ar9EEsujlTuwjpI/G3lTr3trvE9ILEimw:7tYfT0RpnOQx9ar9ENujtuwjpI/G3tz5 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2840)
Changes the autorun value in the registry
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
SUSPICIOUS
Executable content was dropped or overwritten
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
INFO
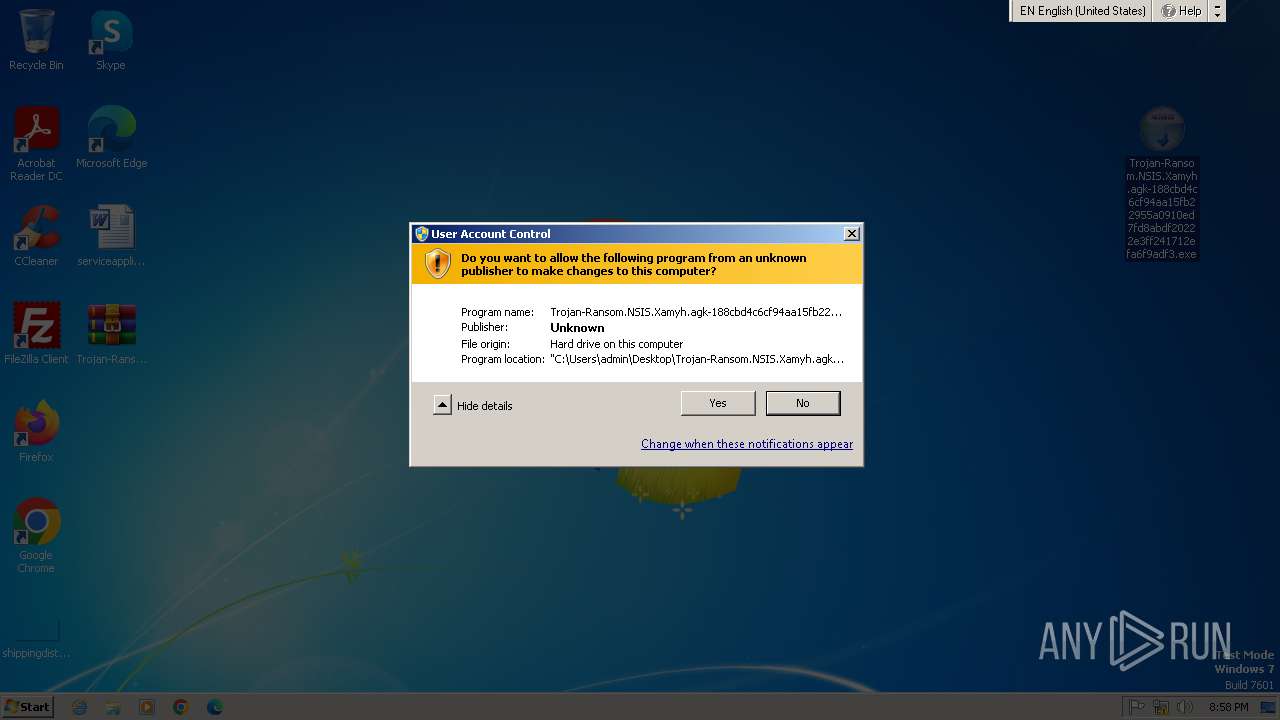
Manual execution by a user
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
- iexplore.exe (PID: 2412)
Creates files or folders in the user directory
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
Create files in a temporary directory
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
Checks supported languages
- launcher.exe (PID: 328)
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
Reads the computer name
- Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe (PID: 2740)
Application launched itself
- iexplore.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2016:07:20 14:35:36+00:00 |
| ArchivedFileName: | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe |
Total processes
44
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
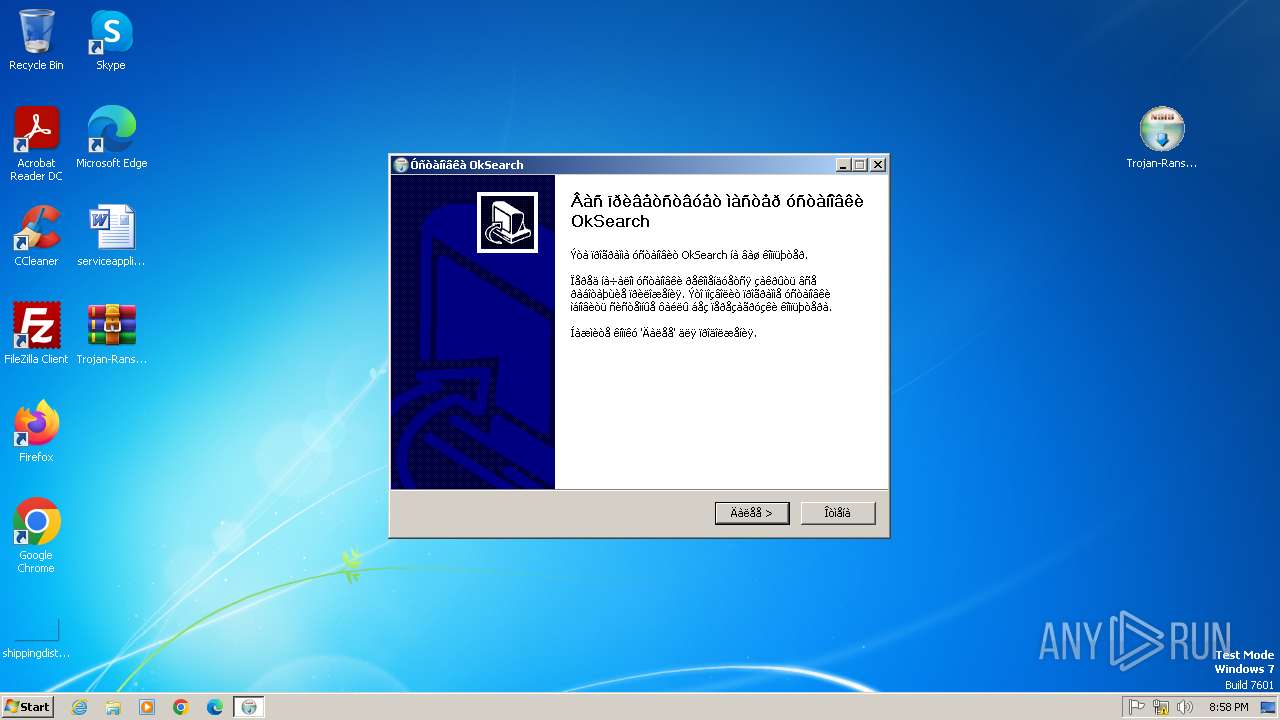
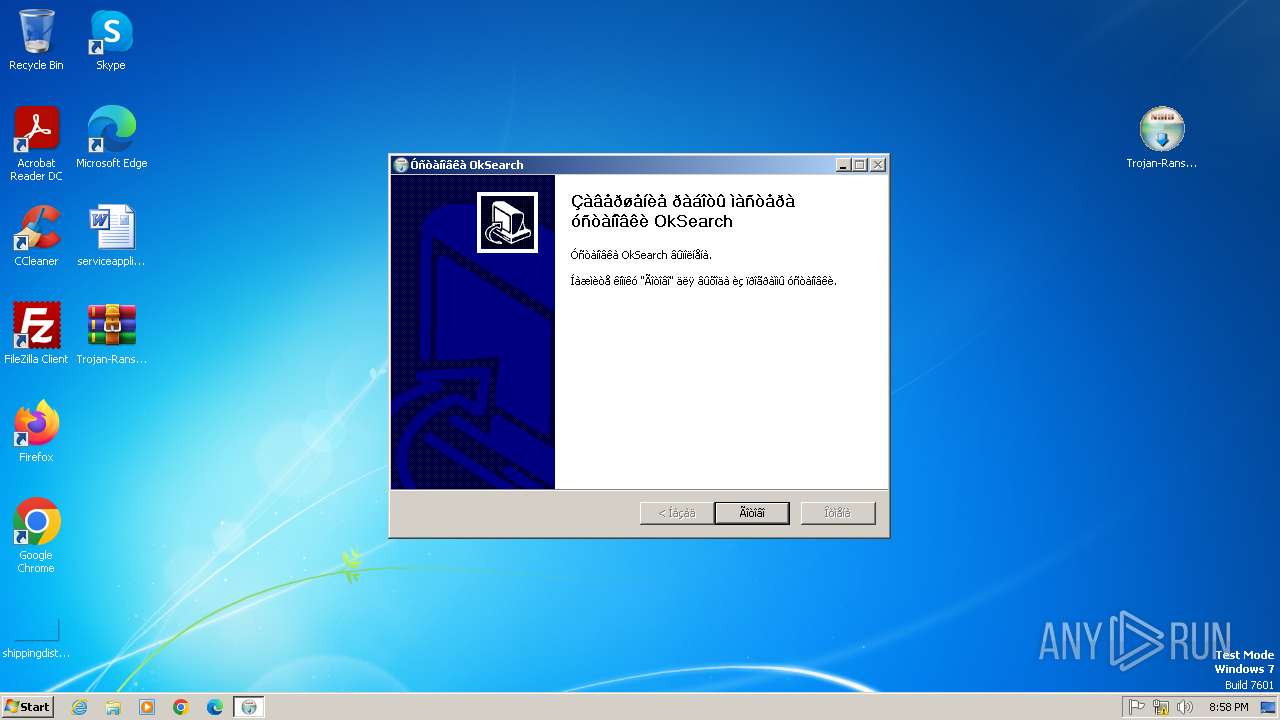
| 328 | "C:\Users\admin\AppData\Roaming\OkSearch\launcher.exe" 28800000 | C:\Users\admin\AppData\Roaming\OkSearch\launcher.exe | — | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2412 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2740 | "C:\Users\admin\Desktop\Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe" | C:\Users\admin\Desktop\Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
18 205
Read events
17 966
Write events
145
Delete events
94
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.7z | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
6
Suspicious files
46
Text files
85
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\config.json | binary | |
MD5:802BF3ADFE4A3BBC674FB4B5E8FA44E9 | SHA256:0FF0513139C4CB4B42D06D79E575339FABFDF9242C9CA663266B1B211CECE708 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Local\Temp\nsk40DD.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Local\Temp\nsk40DD.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\launcher.exe | executable | |
MD5:05398E895A1D2751AC56F2D39FF194B7 | SHA256:50AA5F04D8621863AB19AF4DBF6954D5FC7E9A525CBF38CD04463D23AB12C588 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\stub.exe | executable | |
MD5:AED84ED8C65F82CBE293181CECDEB489 | SHA256:625E2C66C2B1E7FB68DA887810E453B302BEB981E0BCFA8415C076FFB998EB1D | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\chromium\hilbjnajfehfhggoadmonbjbnliofolg.json | binary | |
MD5:5DAC7258BD374EA2A6341AE0AEC06D6A | SHA256:5E0A37630B69FEF6CA4D1DA8FFBBA99C72F6D447F3EF992CC50284F8949070D5 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\chromium\hilbjnajfehfhggoadmonbjbnliofolg\_metadata\computed_hashes.json | binary | |
MD5:B714B0E75B9DD91B60ADCFCF3A397108 | SHA256:1DFDC273E2F23957EAE10460EE5A1490C4F136F2D6FC483B9A1F0718F20C8D33 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\chromium\hilbjnajfehfhggoadmonbjbnliofolg\manifest.json | binary | |
MD5:341E1AC7C35CE759B2BAF177529011A4 | SHA256:E371094628D0648EFE507A7818B8C30E6F97DCB7C4E6790849BFA57B120DFC92 | |||
| 2740 | Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | C:\Users\admin\AppData\Roaming\OkSearch\chromium\hilbjnajfehfhggoadmonbjbnliofolg\icons\icon_128.png | binary | |
MD5:DF8409D9614CBFC002611CE80A005FC7 | SHA256:0B25C4F15D152B1FF952996D7E0DEADFFFE75C9CB0A28E4C9BFBF4D5B23B9185 | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2840.48642\Trojan-Ransom.NSIS.Xamyh.agk-188cbd4c6cf94aa15fb22955a0910ed7fd8abdf20222e3ff241712efa6f9adf3.exe | executable | |
MD5:2F69DB5DCC896A889A91F75AA2D9ED52 | SHA256:188CBD4C6CF94AA15FB22955A0910ED7FD8ABDF20222E3FF241712EFA6F9ADF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
26
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2412 | iexplore.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?814920b3045b6e65 | unknown | — | — | whitelisted |
2412 | iexplore.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2412 | iexplore.exe | GET | 200 | 208.89.74.19:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3ea76c6146e84486 | unknown | — | — | whitelisted |
1560 | iexplore.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2412 | iexplore.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
2412 | iexplore.exe | 208.89.74.19:80 | ctldl.windowsupdate.com | — | US | whitelisted |
2412 | iexplore.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1560 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1560 | iexplore.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1560 | iexplore.exe | 150.171.28.10:443 | bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bing.com |
| whitelisted |
r.bing.com |
| whitelisted |