| File name: | installer.exe |
| Full analysis: | https://app.any.run/tasks/d4f50a32-d644-48c5-af66-c7cb84a41bf3 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 05:11:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 20 sections |
| MD5: | 2A9A1558EEA83BF4F39A50294AFB7FFA |
| SHA1: | 3967CB3C27FE4301148F8A35FD6619F263FB88E8 |
| SHA256: | A448D219AF19E1D11AB4541D9001466B98E6F650858CE44E4DD543652C7A477D |
| SSDEEP: | 1536:YPtGpaeqNMWlMmKYpVKXJdWr7vrSlmWnUssy4LcjC1W3KD/PnPmsTVrw+WAJlTEk:YPtGpadNplM0VsJ4y4mDMP2xa8Gpwtw |
MALICIOUS
No malicious indicators.SUSPICIOUS
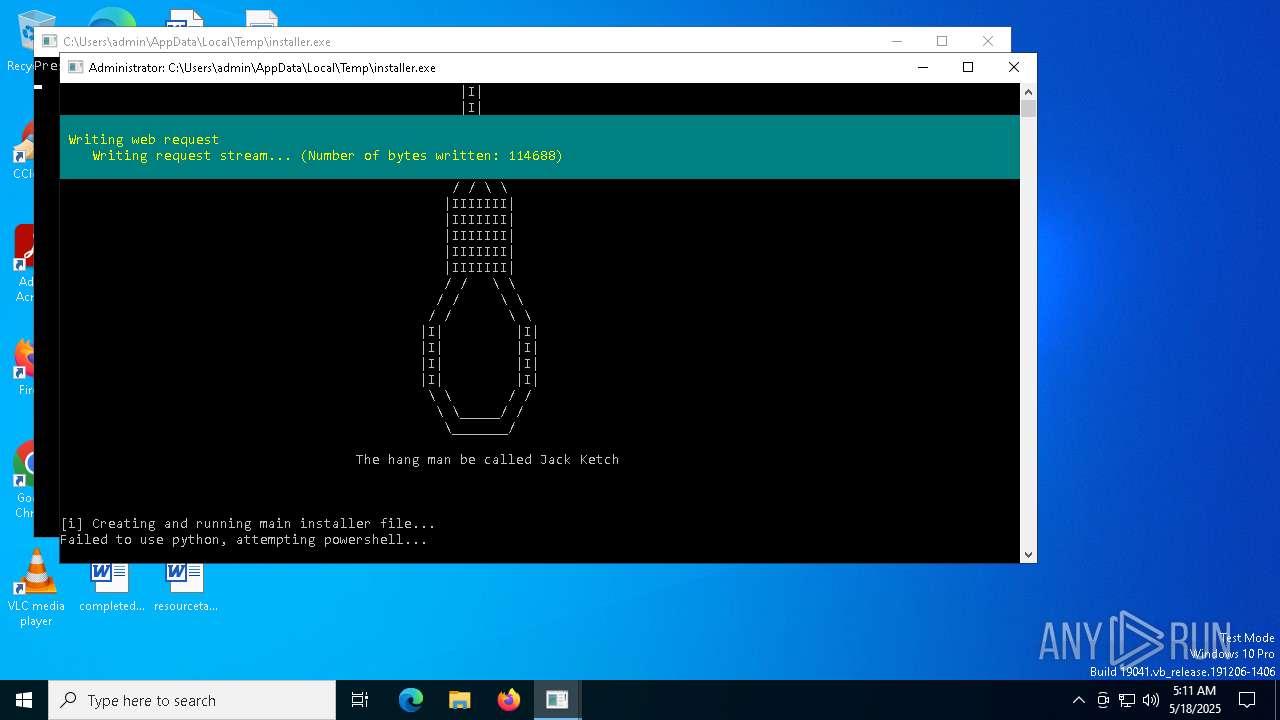
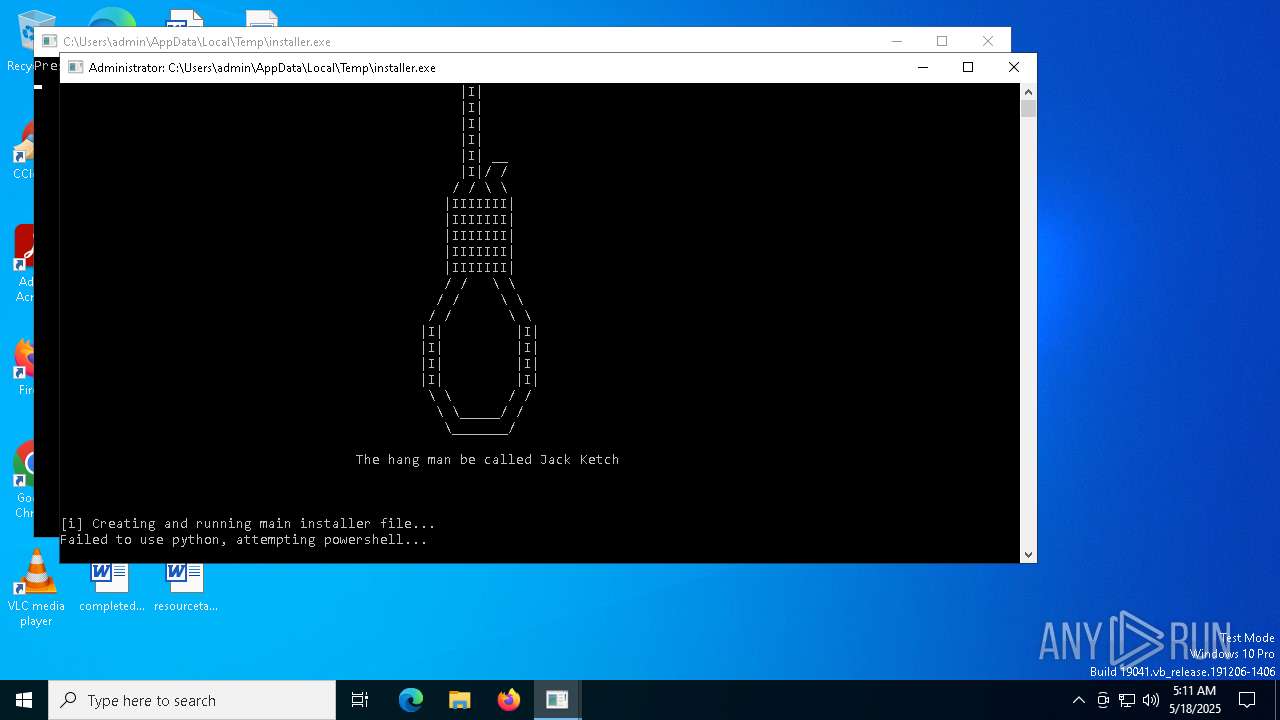
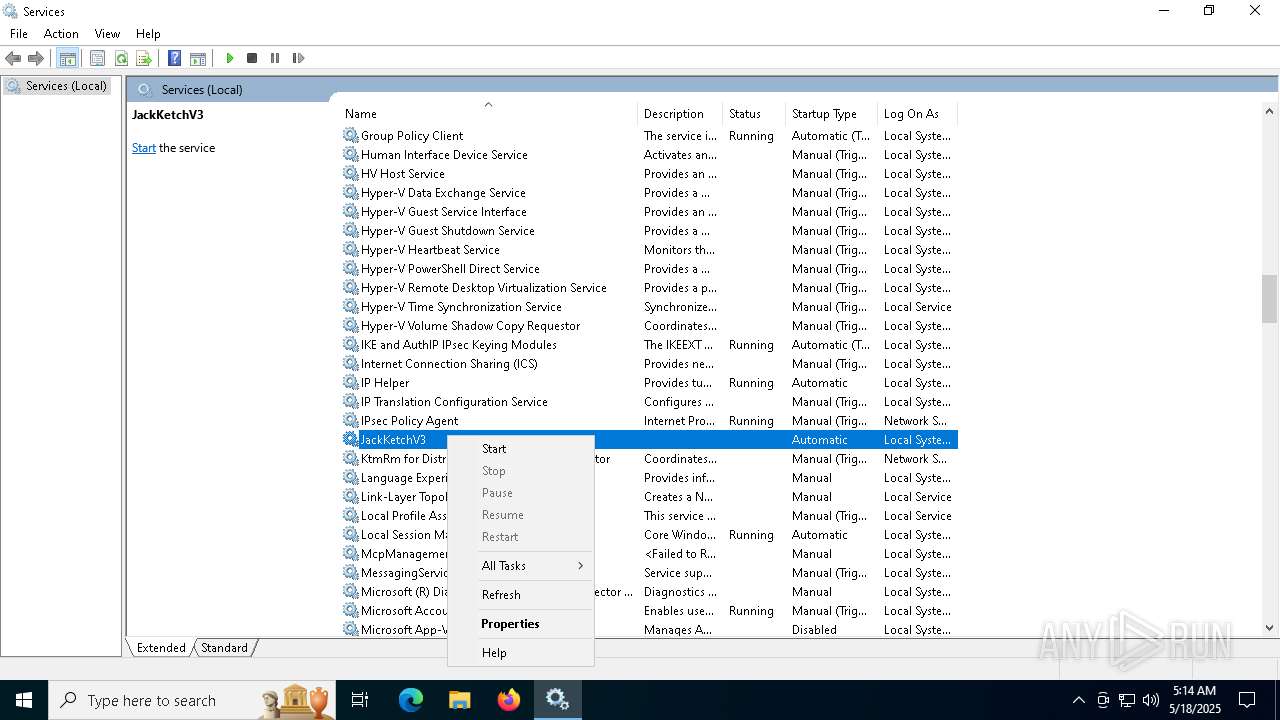
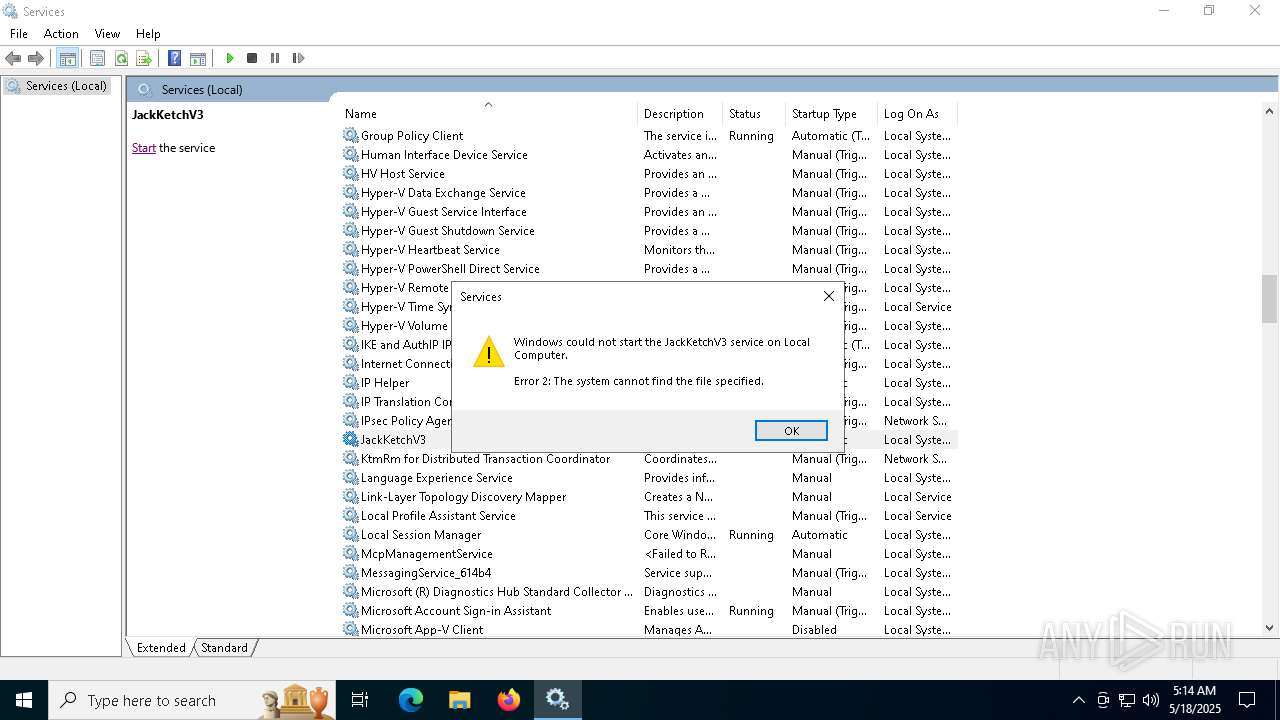
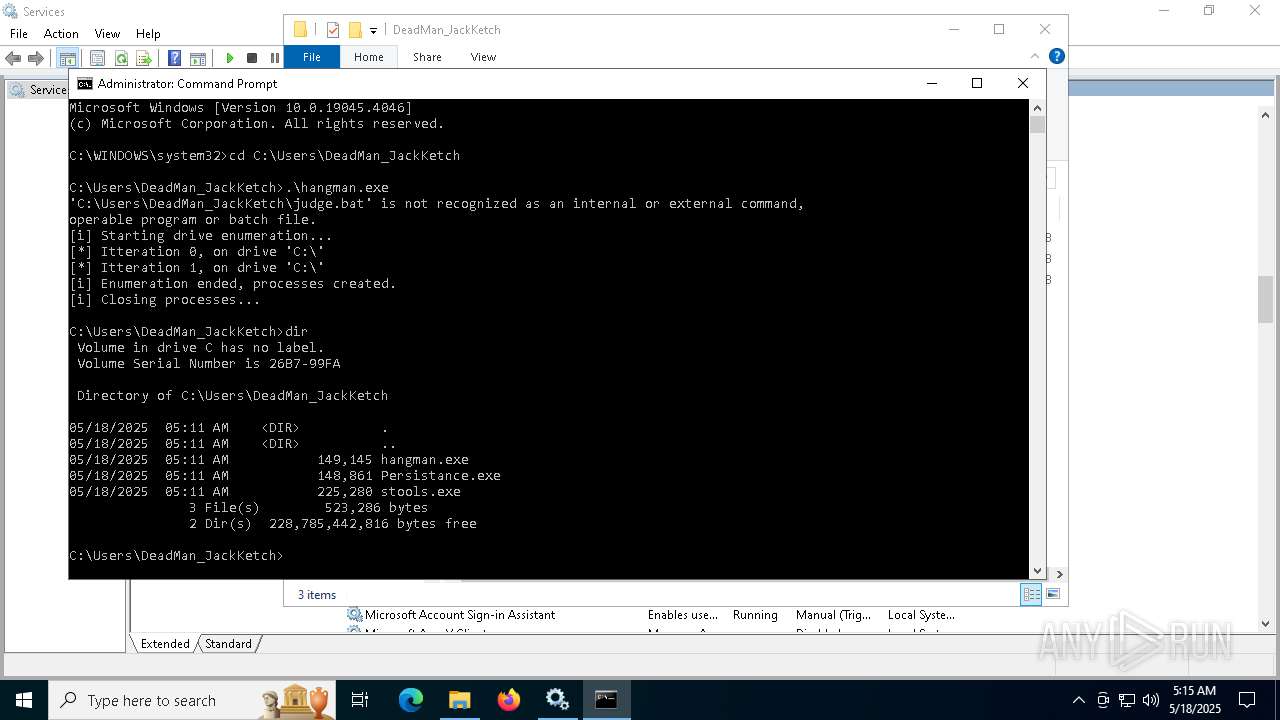
Starts CMD.EXE for commands execution
- hangman.exe (PID: 1692)
- installer.exe (PID: 2136)
- hangman.exe (PID: 5596)
Executing commands from a ".bat" file
- hangman.exe (PID: 5596)
- hangman.exe (PID: 1692)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 7896)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4128)
Reads Internet Explorer settings
- mmc.exe (PID: 7896)
INFO
Checks supported languages
- installer.exe (PID: 2136)
- hangman.exe (PID: 5596)
Manual execution by a user
- mmc.exe (PID: 6708)
- cmd.exe (PID: 7724)
- mmc.exe (PID: 7512)
- mmc.exe (PID: 7896)
- mmc.exe (PID: 6596)
- svchost.exe (PID: 1936)
- svchost.exe (PID: 2044)
- svchost.exe (PID: 1392)
- cmd.exe (PID: 6748)
Reads security settings of Internet Explorer
- mmc.exe (PID: 7896)
Creates files or folders in the user directory
- mmc.exe (PID: 7896)
Reads the software policy settings
- slui.exe (PID: 7432)
Checks proxy server information
- mmc.exe (PID: 7896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:18 05:11:10+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.41 |
| CodeSize: | 13312 |
| InitializedDataSize: | 30720 |
| UninitializedDataSize: | 512 |
| EntryPoint: | 0x13f0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
317
Monitored processes
23
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | C:\WINDOWS\system32\cmd.exe /c powershell -Command "Start-Process -FilePath 'C:\Users\admin\AppData\Local\Temp\installer.exe' -ArgumentList: '1' -Verb RunAs" | C:\Windows\System32\cmd.exe | — | installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wuauserv | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
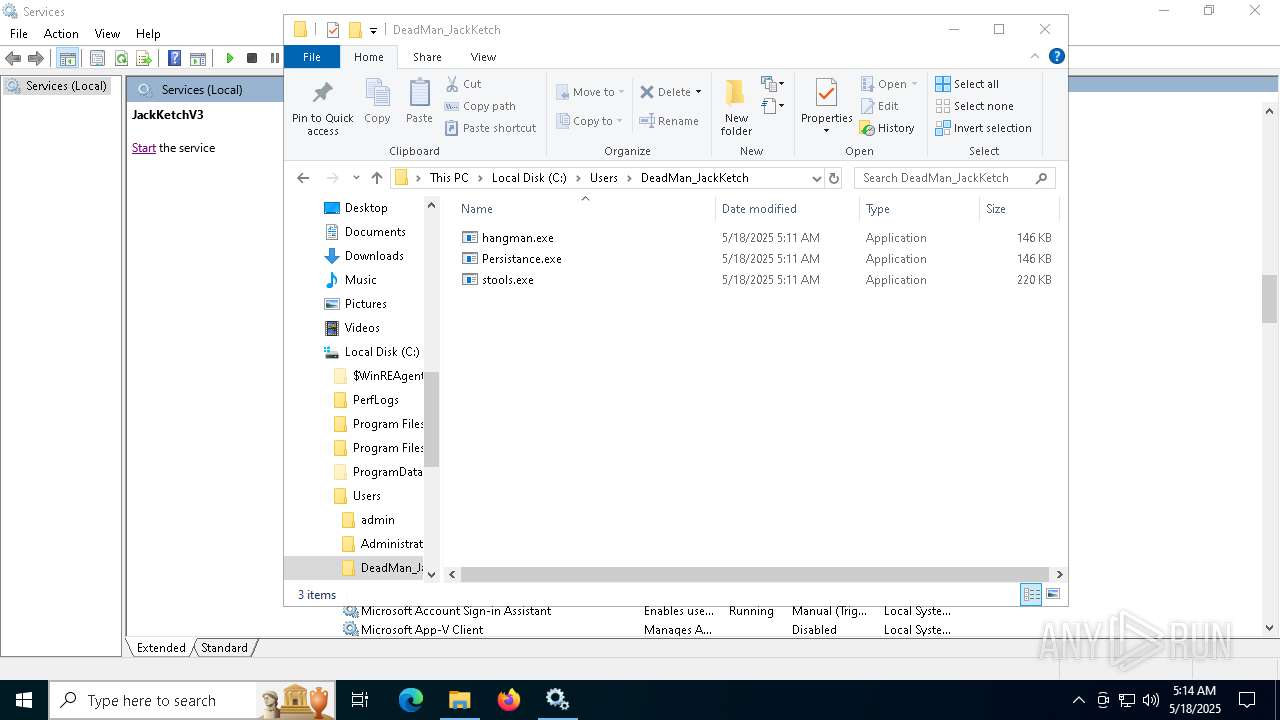
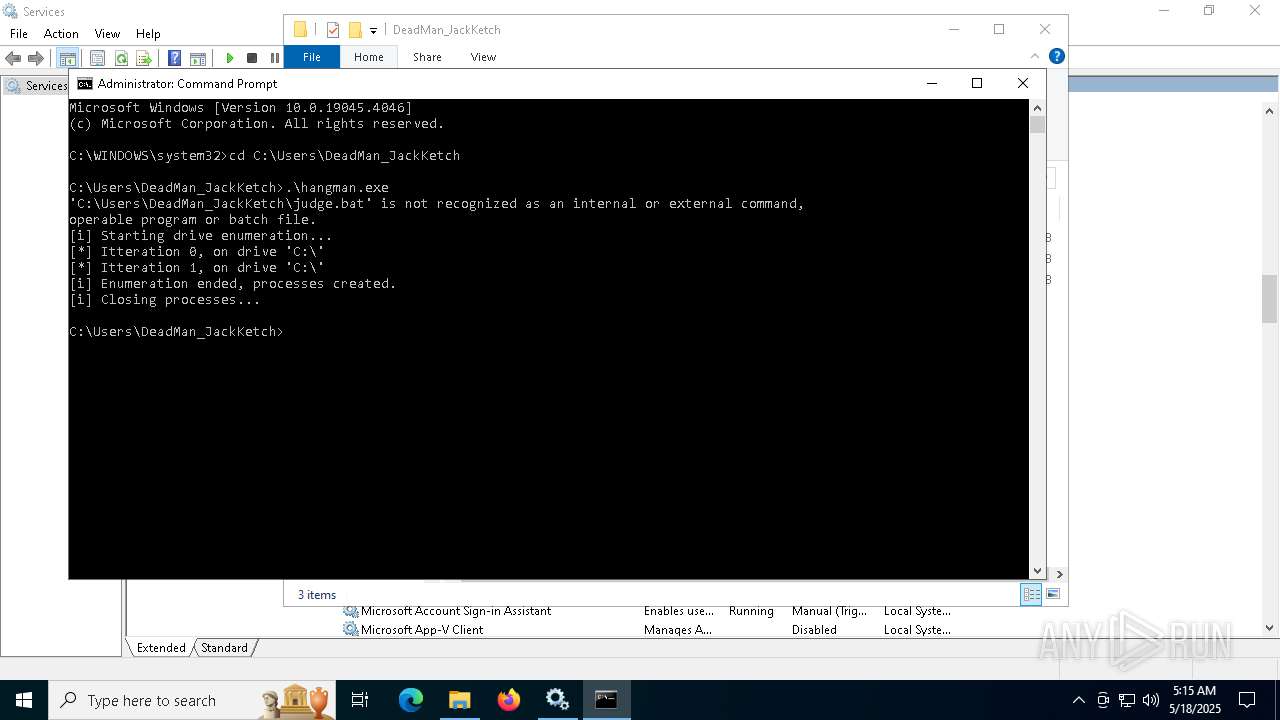
| 1692 | .\hangman.exe | C:\Users\DeadMan_JackKetch\hangman.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1820 | C:\WINDOWS\system32\cmd.exe /c C:\Users\DeadMan_JackKetch\judge.bat | C:\Windows\System32\cmd.exe | — | hangman.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s wscsvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Temp\installer.exe" | C:\Users\admin\AppData\Local\Temp\installer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\System32\svchost.exe -k NetworkService -p -s WinRM | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 508
Read events
3 500
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7896) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7896) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7896) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6708) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6708) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6708) mmc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1936) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center |
| Operation: | write | Name: | cval |
Value: 0 | |||
| (PID) Process: | (1936) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center |
| Operation: | write | Name: | cval |
Value: 1 | |||
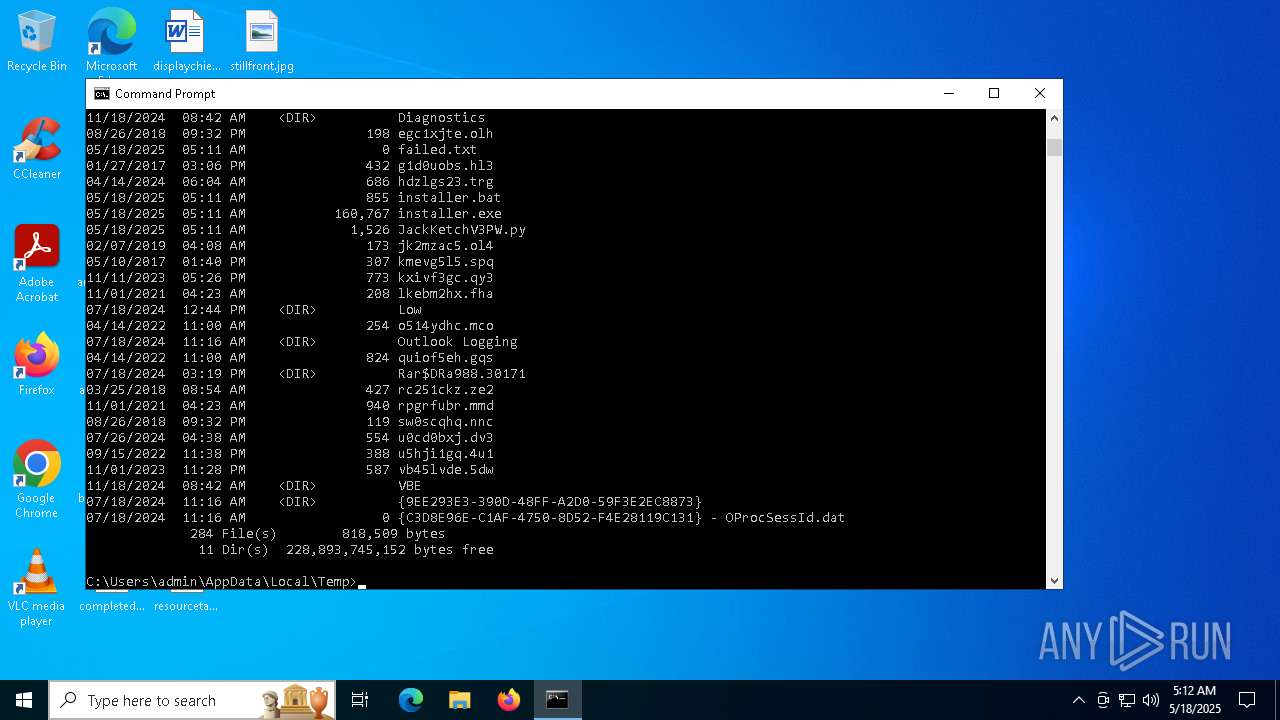
Executable files
0
Suspicious files
44
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | binary | |
MD5:B53B2070E686FFB1FBC8B06994E7C8D7 | SHA256:A3ABD06F4E40CB700B1908AB6BCD2E27455E13EF076E0BF2345BB2FA369EF802 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:8A2BDE0EAFA7E946196A1B114AB636E9 | SHA256:1C338CBDD9316D7FD8F208341466FEDC554A04D489B3A86C736EC3831A2F2BA2 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.030.etl | binary | |
MD5:4558A195AA3B11F3AF5D839B627BF95A | SHA256:C6F97F8924A2199569D3B36355531D342FDDC2F84DADF410F34E0D7E8C5A50B2 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:F9485F2BA891697F8B6CF8FB1E7F42C0 | SHA256:69146D4AAEFB8609745B6CA780B48ABC66054AA3CDB8061248CF7B32F3B32617 | |||
| 4128 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.034.etl | binary | |
MD5:DCB94F822B793FF178C7332174A89DFB | SHA256:4AB418FA76DFA333D37F7401B40B0B0F0E806876C79AB2F36CD3FD7CCAD8665B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
82
DNS requests
44
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.3.109.244:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5168 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5848 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5284 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5448 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.3.109.244:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7844 | powershell.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |