| URL: | http://www.gameofwhores.game/ |
| Full analysis: | https://app.any.run/tasks/0948d6d0-387a-4541-ab60-12b59bce6017 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 08:55:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 25107964DF9331A77A8DF018E770C114 |
| SHA1: | B01DC405683233DC7CB2ACB55333A2A0B93C13B3 |
| SHA256: | A4376E98171CD5A610E6FEEC5D17F569FA63B7D8B7776C3B209228995E437A36 |
| SSDEEP: | 3:N1KJS4IDSrMI:Cc4IDSrMI |
MALICIOUS
Connects to CnC server
- chrome.exe (PID: 3896)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3896)
INFO
Application launched itself
- iexplore.exe (PID: 3132)
- chrome.exe (PID: 3896)
Changes internet zones settings
- iexplore.exe (PID: 3132)
Creates files in the user directory
- iexplore.exe (PID: 3044)
- iexplore.exe (PID: 3132)
Reads internet explorer settings
- iexplore.exe (PID: 3044)
Reads Internet Cache Settings
- iexplore.exe (PID: 3044)
Reads settings of System Certificates
- chrome.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
67
Monitored processes
34
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9718548662843332873 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9718548662843332873 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6412293373346521380 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6412293373346521380 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3752 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6883358452709141518 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6883358452709141518 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2508 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=18078857491740548930 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18078857491740548930 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2696 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9336429583995476886 --mojo-platform-channel-handle=4844 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3904 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2784085713617914992 --mojo-platform-channel-handle=3880 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --service-pipe-token=12730067520250260882 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12730067520250260882 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2236 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=11261200101733026141 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11261200101733026141 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,738770015040327455,2354202183365589283,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=803810027002176119 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=803810027002176119 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4144 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 011
Read events
850
Write events
153
Delete events
8
Modification events
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4AE7313F-76EF-11E9-A09E-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3132) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050003000F00080038000F00B500 | |||
Executable files
0
Suspicious files
131
Text files
203
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3132 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\00UYCZ76\gameofwhores_game[1].txt | — | |
MD5:— | SHA256:— | |||
| 3044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\00UYCZ76\gameofwhores_game[1].htm | html | |
MD5:— | SHA256:— | |||
| 3132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE75B9D772DEDA5E9.TMP | — | |
MD5:— | SHA256:— | |||
| 3044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\4RTXMEHB\jsparkcaf[1].php | html | |
MD5:— | SHA256:— | |||
| 3132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF95F2D4CE710DE19B.TMP | — | |
MD5:— | SHA256:— | |||
| 3044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\LALM9O0N\caf[1].js | text | |
MD5:— | SHA256:— | |||
| 3132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF10551D36EB841D98.TMP | — | |
MD5:— | SHA256:— | |||
| 3132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{4AE73140-76EF-11E9-A09E-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
80
DNS requests
61
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
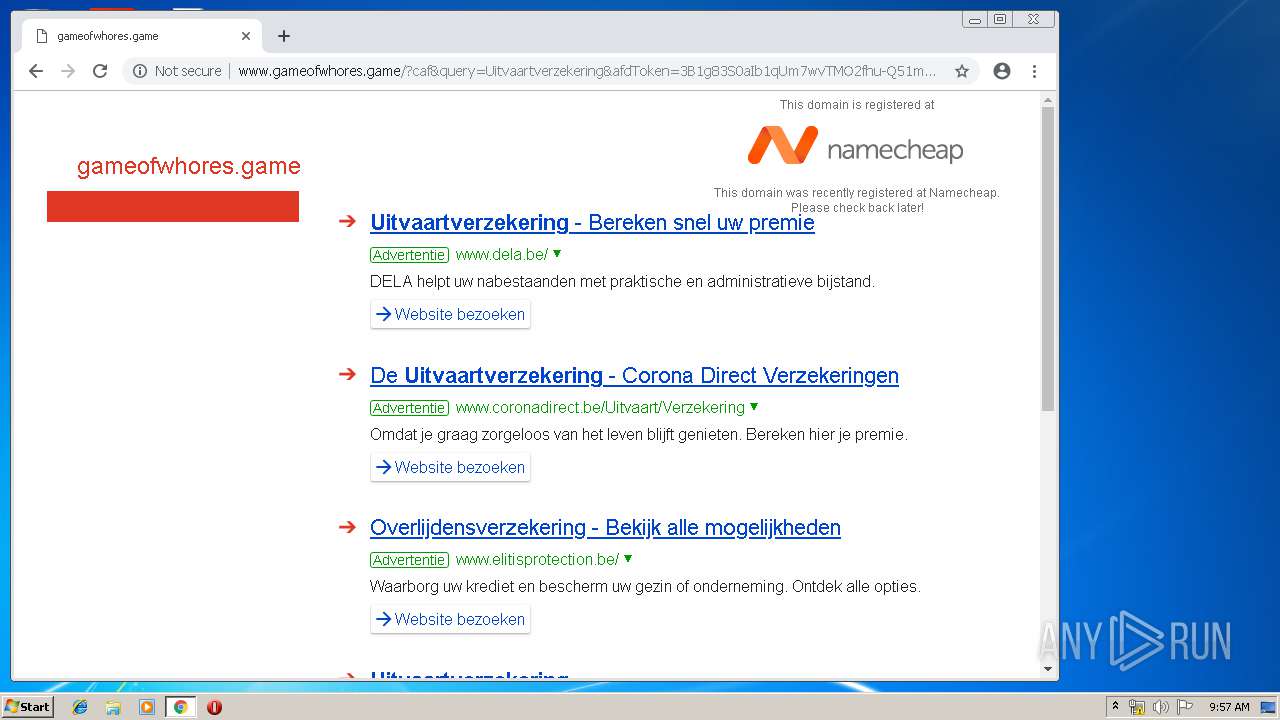
3044 | iexplore.exe | GET | 200 | 198.54.117.197:80 | http://www.gameofwhores.game/ | US | html | 1.58 Kb | malicious |
3896 | chrome.exe | GET | 200 | 198.54.117.200:80 | http://www.gameofwhores.game/ | US | html | 1.58 Kb | malicious |
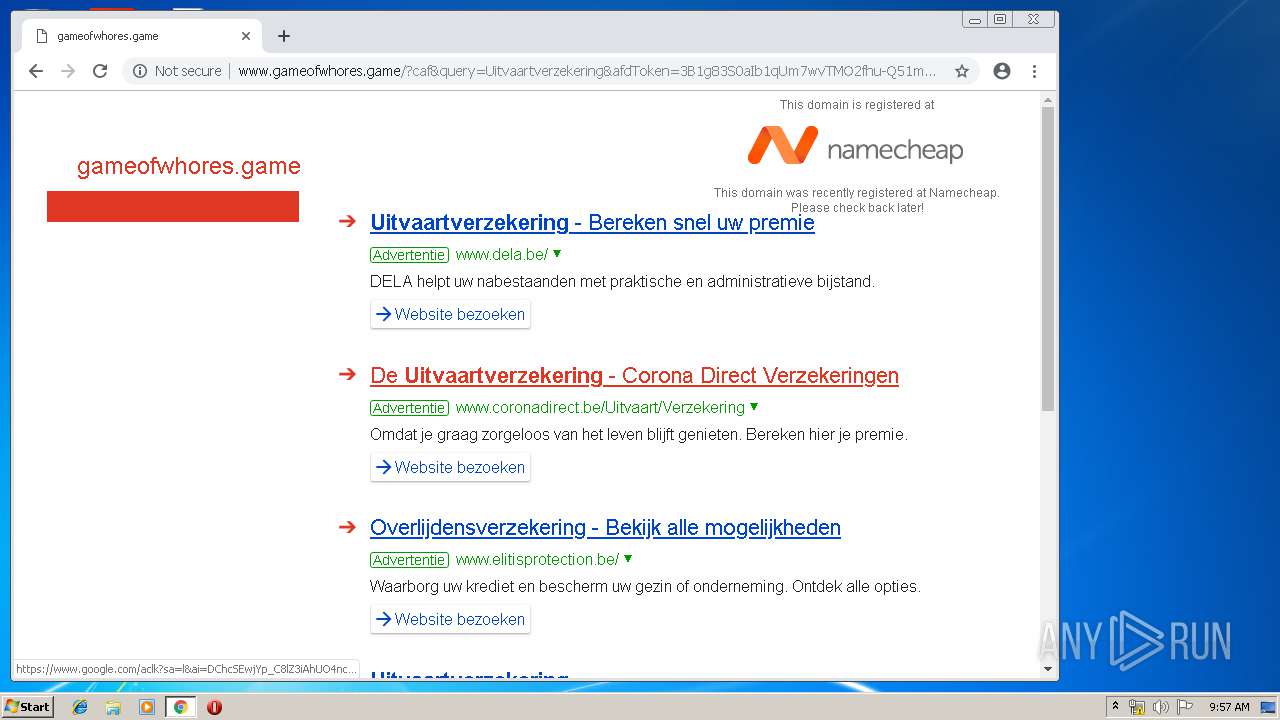
3896 | chrome.exe | GET | 200 | 185.53.179.29:80 | http://parkingcrew.net/jsparkcaf.php?regcn=243142&_v=2&_h=www.gameofwhores.game&_t=1557910632656 | DE | html | 2.54 Kb | whitelisted |
3896 | chrome.exe | GET | 200 | 13.35.253.80:80 | http://i.cdnpark.com/themes/assets/style.css | US | text | 343 b | whitelisted |
3044 | iexplore.exe | GET | 200 | 13.35.253.65:80 | http://i.cdnpark.com/themes/registrar/style_namecheap.css | US | text | 1.73 Kb | whitelisted |
3896 | chrome.exe | GET | 404 | 198.54.117.200:80 | http://www.gameofwhores.game/favicon.ico | US | html | 185 b | malicious |
3132 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3896 | chrome.exe | GET | 200 | 185.53.178.30:80 | http://js.parkingcrew.net/track.php?domain=gameofwhores.game&caf=1&toggle=answercheck&answer=yes&uid=MTU1NzkxMDYzMi45MzQyOmU2MDRkNDAwZjNmMmRmNGYwNzk2YWZkMjU4ZTk0ZDAxM2NlNzI3MjY5YjY4N2NkMTI4OTJmODc3ZmY0YzJkN2Y6NWNkYmQ0NjhlNDE4Yg%3D%3D | DE | binary | 20 b | whitelisted |
3044 | iexplore.exe | GET | 200 | 185.53.178.30:80 | http://js.parkingcrew.net/assets/scripts/jsparkcaf.js | DE | text | 5.51 Kb | whitelisted |
3896 | chrome.exe | GET | 200 | 13.35.253.80:80 | http://i.cdnpark.com/themes/registrar/style_namecheap.css | US | text | 1.73 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3132 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3132 | iexplore.exe | 198.54.117.197:80 | www.gameofwhores.game | Namecheap, Inc. | US | malicious |
3044 | iexplore.exe | 198.54.117.197:80 | www.gameofwhores.game | Namecheap, Inc. | US | malicious |
3044 | iexplore.exe | 13.35.253.65:80 | i.cdnpark.com | — | US | suspicious |
3044 | iexplore.exe | 172.217.16.132:80 | www.google.com | Google Inc. | US | whitelisted |
3044 | iexplore.exe | 185.53.179.29:80 | parkingcrew.net | Team Internet AG | DE | malicious |
3044 | iexplore.exe | 185.53.178.30:80 | js.parkingcrew.net | Team Internet AG | DE | suspicious |
3896 | chrome.exe | 172.217.23.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3896 | chrome.exe | 172.217.16.195:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3896 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.gameofwhores.game |
| malicious |
i.cdnpark.com |
| whitelisted |
parkingcrew.net |
| whitelisted |
www.google.com |
| malicious |
js.parkingcrew.net |
| whitelisted |
www.google.com.ua |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3896 | chrome.exe | A Network Trojan was detected | ET CNC Zeus Tracker Reported CnC Server group 11 |