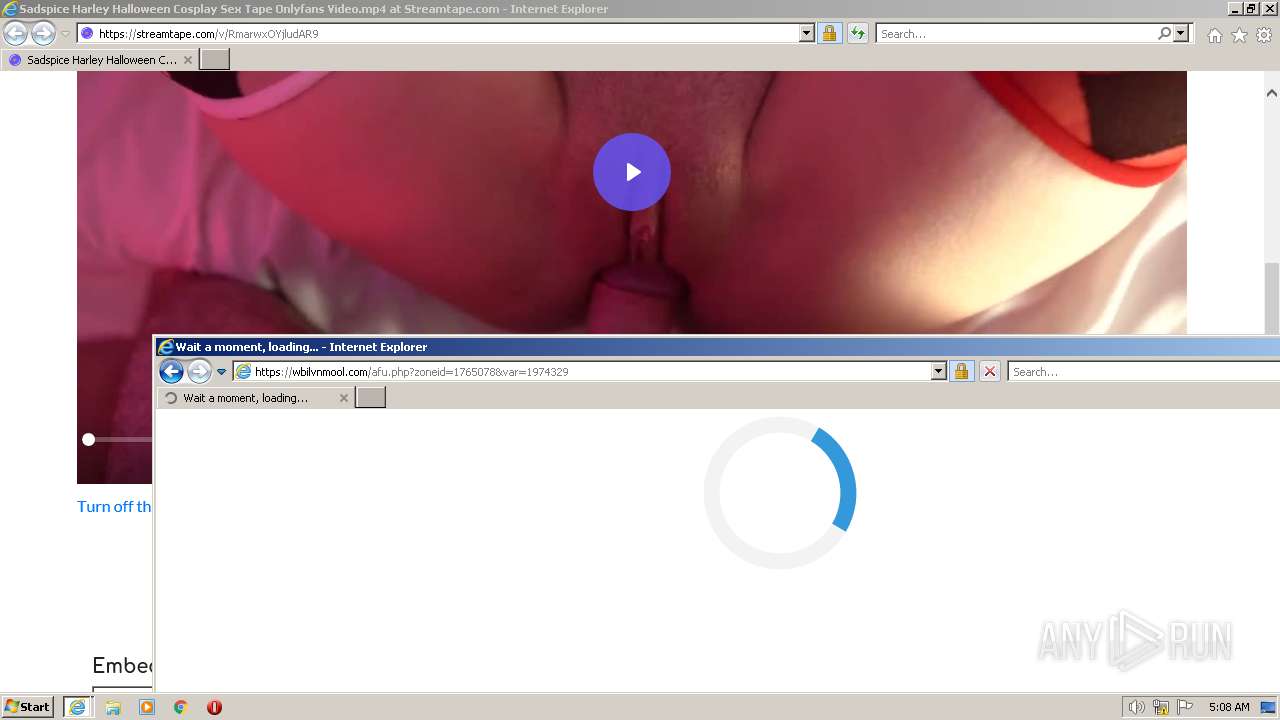
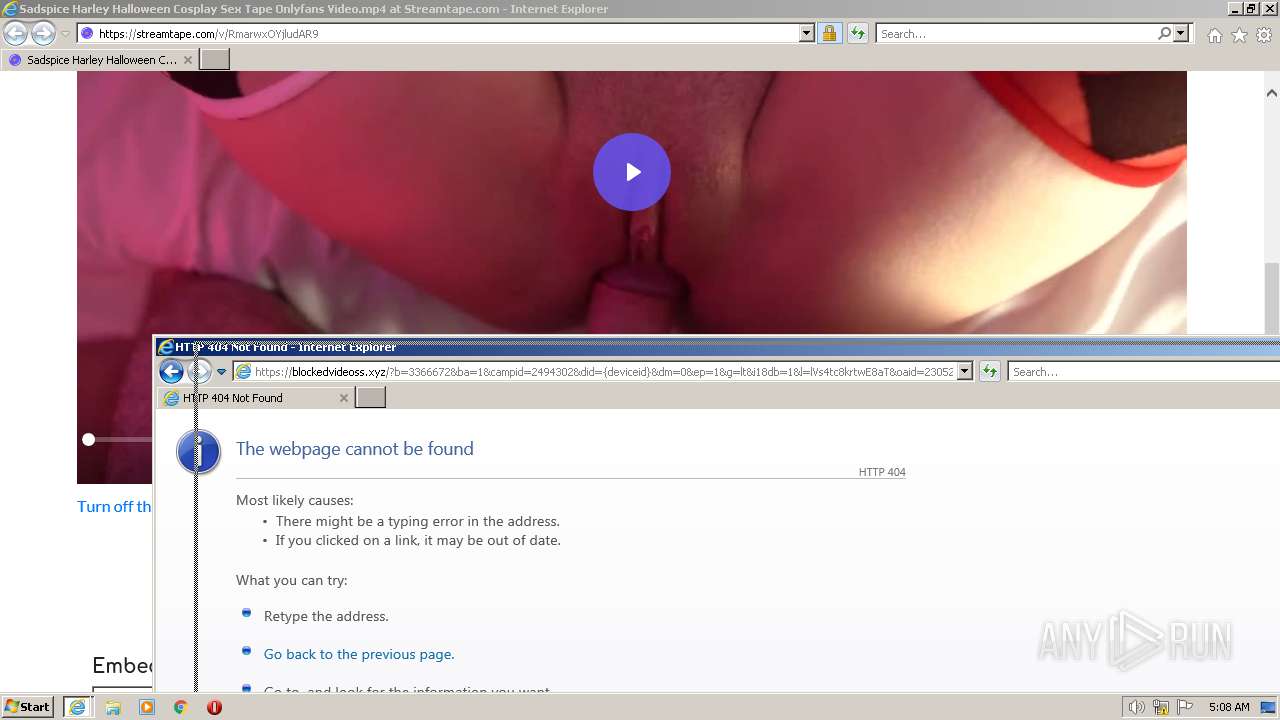
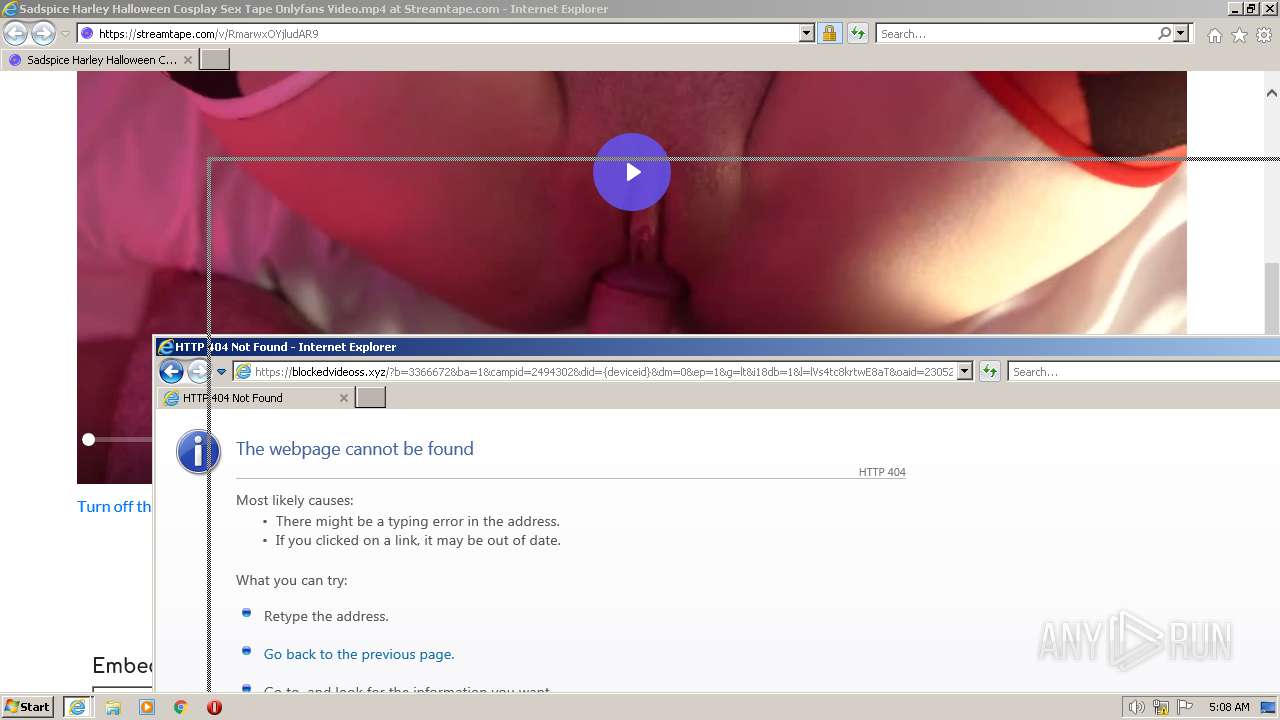
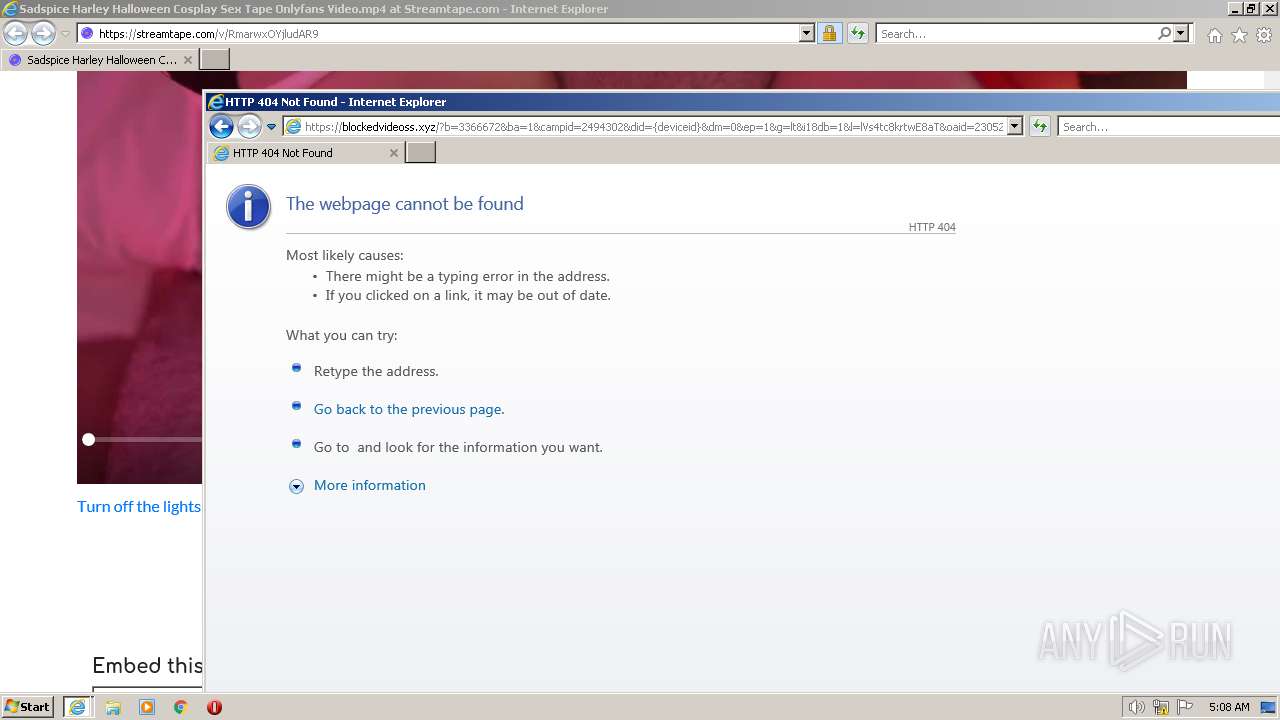
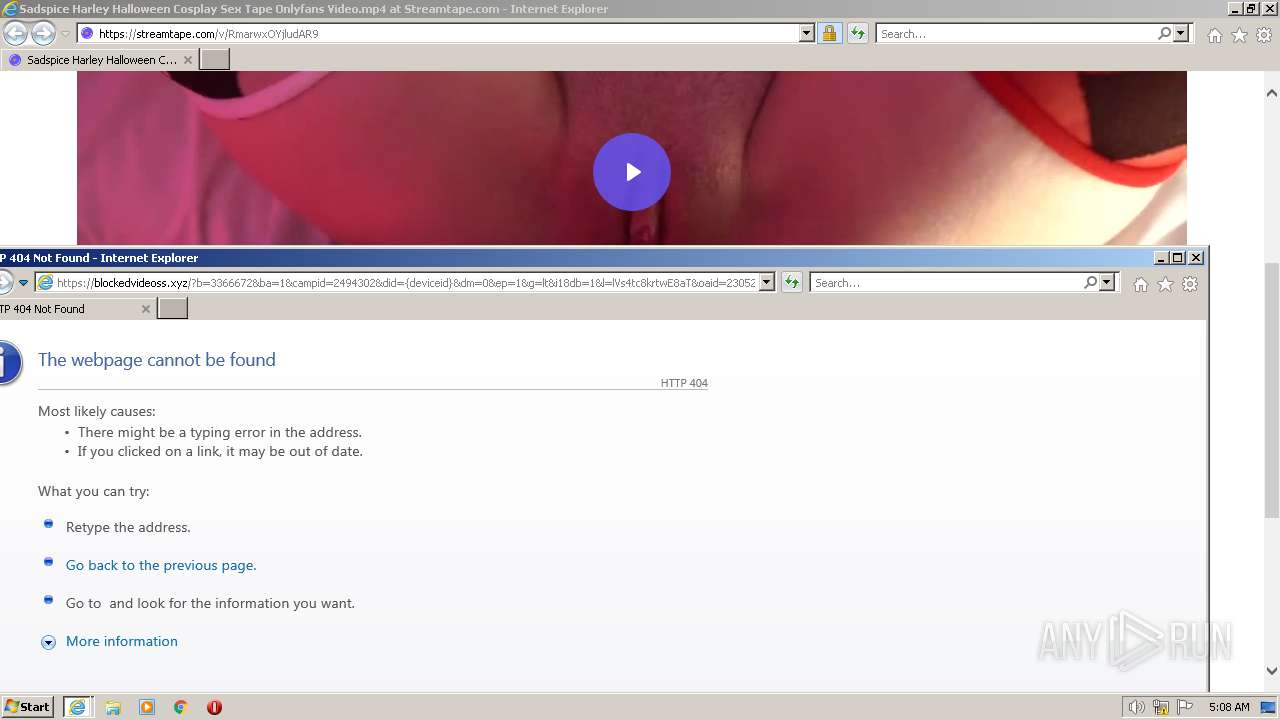
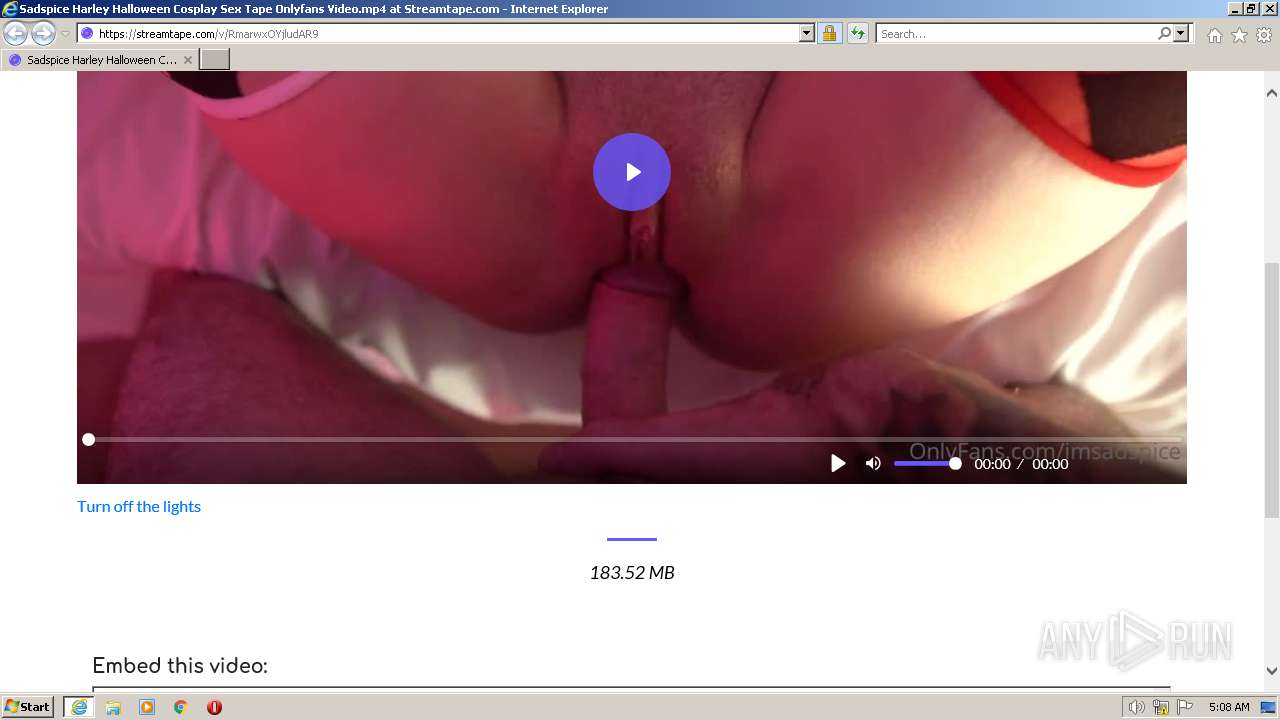
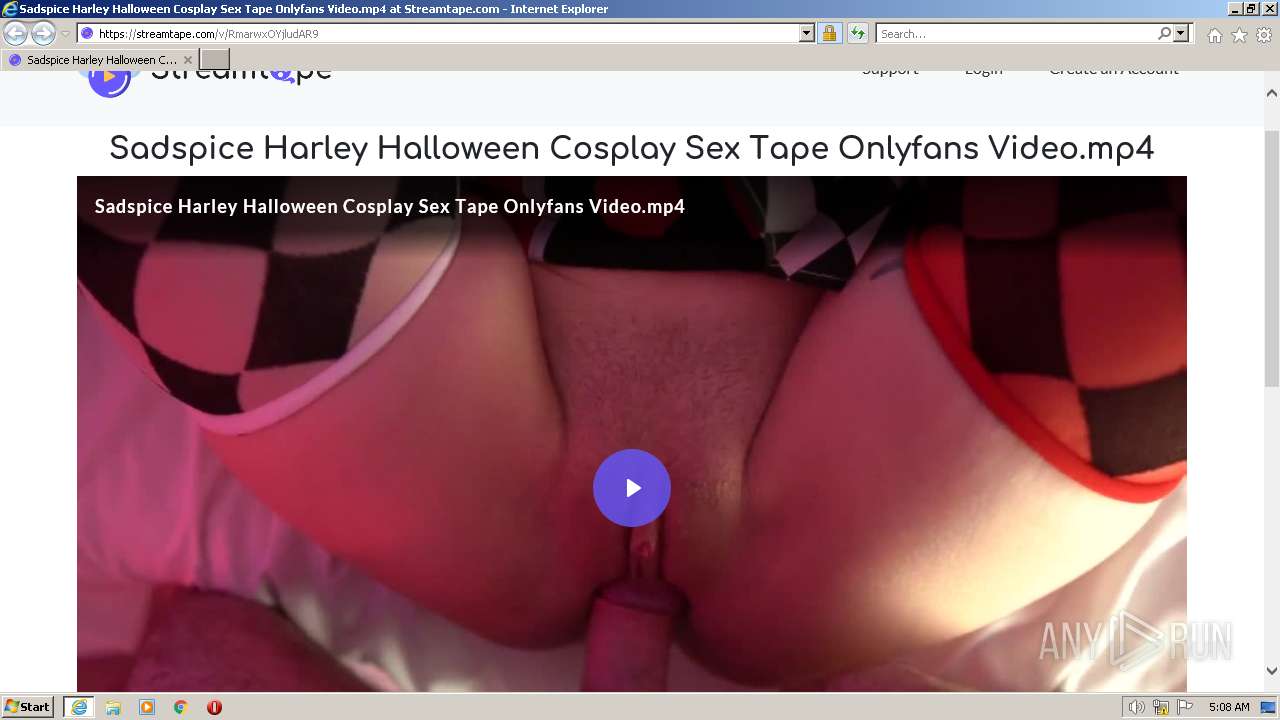
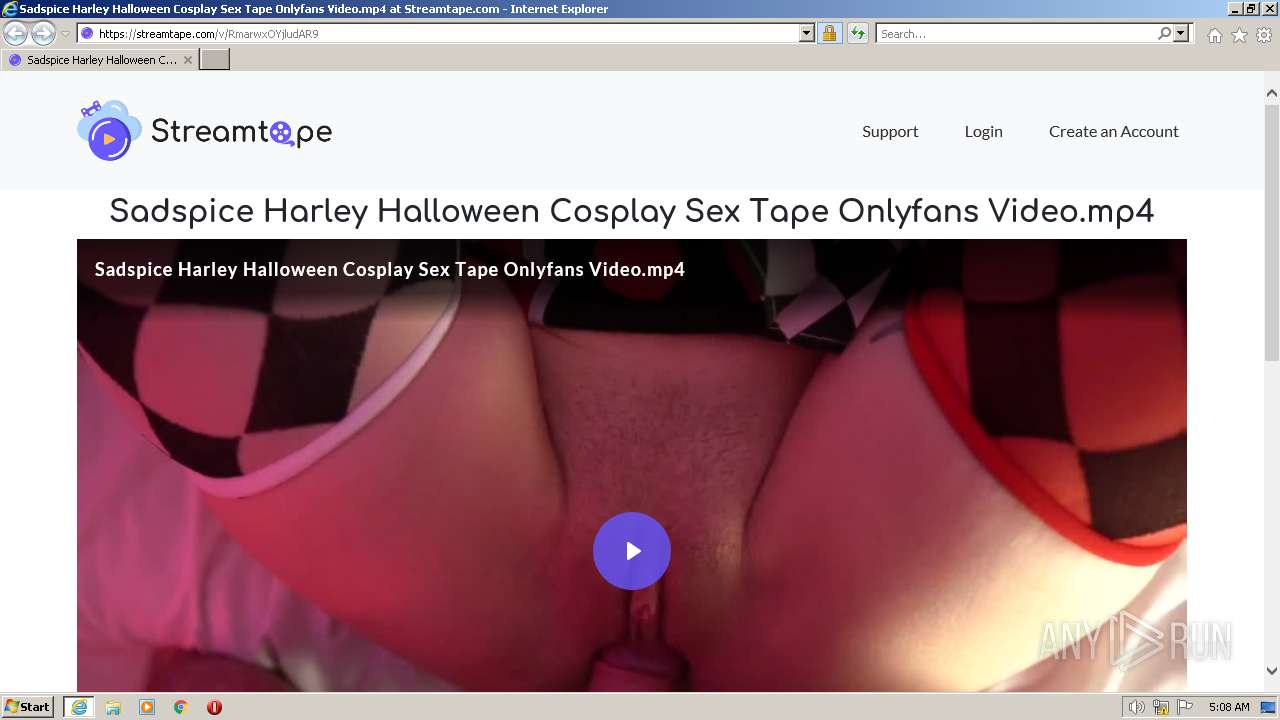
| URL: | https://streamtape.com/v/RmarwxOYjludAR9 |
| Full analysis: | https://app.any.run/tasks/13b7dc97-94b3-4146-82bd-8fb199a3f5f9 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2023, 04:07:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FE08A1F0180DA808DFE75F799D220499 |
| SHA1: | 9B010A40B5D9299E1ED9F9FC4117E7EE158F4E2C |
| SHA256: | A42D65ADDE5CC6CD1524BE5462447C5F5BFD1ED34C05B2B6D1B38B2F63FBD280 |
| SSDEEP: | 3:N8cRPAZ3TK4vvJ2:2cRPpCw |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Create files in a temporary directory
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 1832)
Application launched itself
- iexplore.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:2233614 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3916 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://streamtape.com/v/RmarwxOYjludAR9" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
31 586
Read events
31 366
Write events
216
Delete events
4
Modification events
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
81
Text files
62
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:5C2119AECC7F04C8B7528BA6EDC167E1 | SHA256:C65DD79D1697B09210E413F7770145191C06555E1332B2F646D809CEDC74B80E | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:A70F0C2192A5736A3D42CD5088369EAC | SHA256:66324E2BA602143DE1CB49371BC2EEC8FF1DA6ABC1862DDE2137F8A57CFA0C2C | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:BF678D43BBD236FD060359D91C06C924 | SHA256:7D3443A1A3482744AF95701FB202F91BCB2E28D8F0D9E6CB9CB48AA6DB1561D5 | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:66AA52643E0A1A58E60BC04907E199A3 | SHA256:3A8FDA3FBEA5BE9E84A1E766194DED66211C93770C82FF991B71D84A8E2DEF60 | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\bootstrap.min[1].css | text | |
MD5:7CC40C199D128AF6B01E74A28C5900B0 | SHA256:2FF5B959FA9F6B4B1D04D20A37D706E90039176AB1E2A202994D9580BAEEBFD6 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\popper.min[1].js | text | |
MD5:710021214A23CF8A5A5841A648D65832 | SHA256:3B5EC1C452AD4EDD6DCF3964718C2038DC382B9F47FABD6223C992417BD27F99 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
107
DNS requests
51
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1832 | iexplore.exe | GET | 302 | 198.134.116.30:80 | http://xml.expialidosius.com/redirect?feed=496482&auth=16jDmy&subid=&query=&url=https%3A%2F%2Fa.adforcast.com%2Fsub%2FXrhN0kTsdAMozilla%2F5.0+%28Windows+NT+6.1%3B+Trident%2F7.0%3B+rv%3A11.0%29+like+Gecko | US | — | — | malicious |
1832 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 2.19.126.222:80 | http://ocsp.buypass.com/MEowSDBGMEQwQjAJBgUrDgMCGgUABBRyx0WAUkki6aW2LiOMsWzYh0At3gQUyYB34GKSgvVGnPO690zD3rijrTkCCTL6CDdr8jwgEw%3D%3D | DE | der | 1.66 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4360d7dc5d5bc1ef | US | compressed | 62.3 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDs3X1l9g2LdCe%2FT5Q%2BiODU%3D | US | binary | 471 b | whitelisted |
1832 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | US | binary | 724 b | whitelisted |
1832 | iexplore.exe | GET | 200 | 2.19.126.222:80 | http://ocsp.buypass.com/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBRtM4uveV6ZwbCQeKmCxreldZfyFwQUJ1Kkby0qq0CTkOzWacv%2BfGE7fEICCwUC9%2FFQVl7nAMA%2B | DE | binary | 1.66 Kb | whitelisted |
3916 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | binary | 724 b | whitelisted |
1832 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEAlmoqr%2BTNPdAvjPn2zOG0c%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3412 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3916 | iexplore.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
3916 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3916 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1832 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1832 | iexplore.exe | 172.64.102.2:443 | — | CLOUDFLARENET | US | shared |
1832 | iexplore.exe | 188.114.97.3:443 | zimpolo.com | CLOUDFLARENET | NL | malicious |
1832 | iexplore.exe | 23.109.82.239:443 | kl.worstnumidae.com | SERVERS-COM | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
kl.worstnumidae.com |
| suspicious |
fnbauniukvi.com |
| suspicious |
www.google.com |
| malicious |
zimpolo.com |
| malicious |
a.adforcast.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1832 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |
1832 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |
676 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |
676 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |
676 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |
676 | iexplore.exe | Generic Protocol Command Decode | SURICATA TLS certificate invalid der |