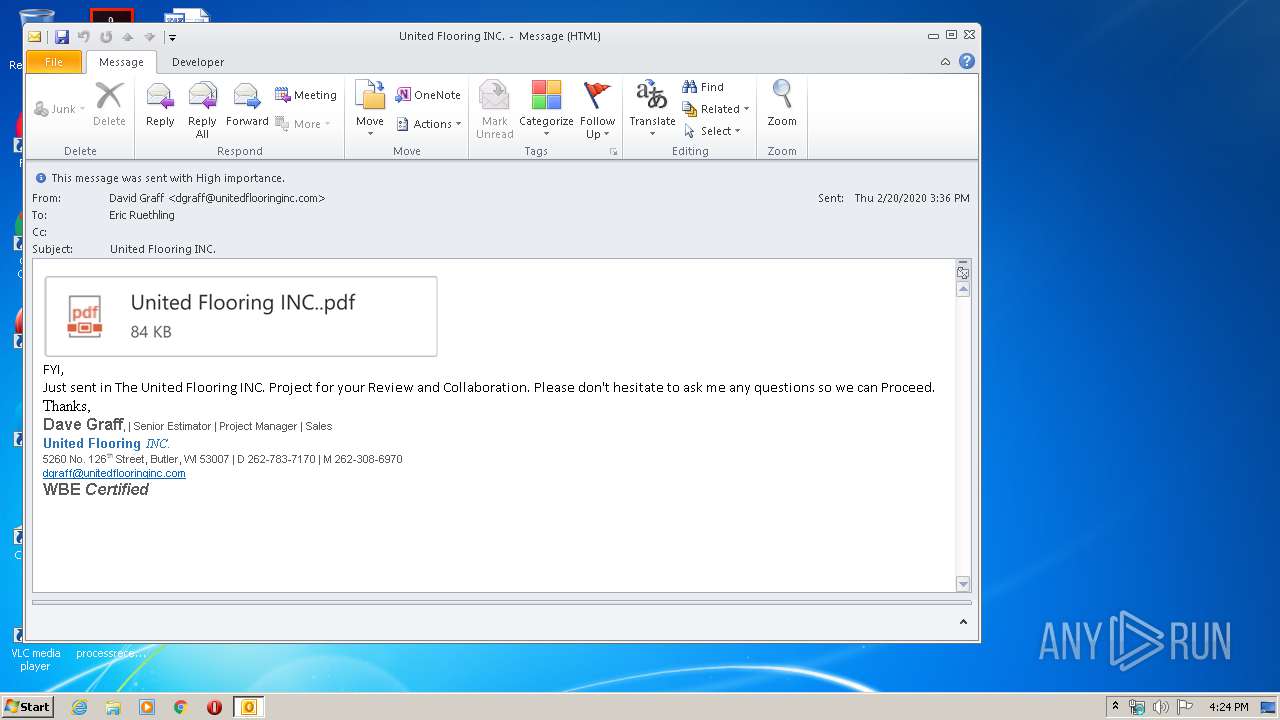
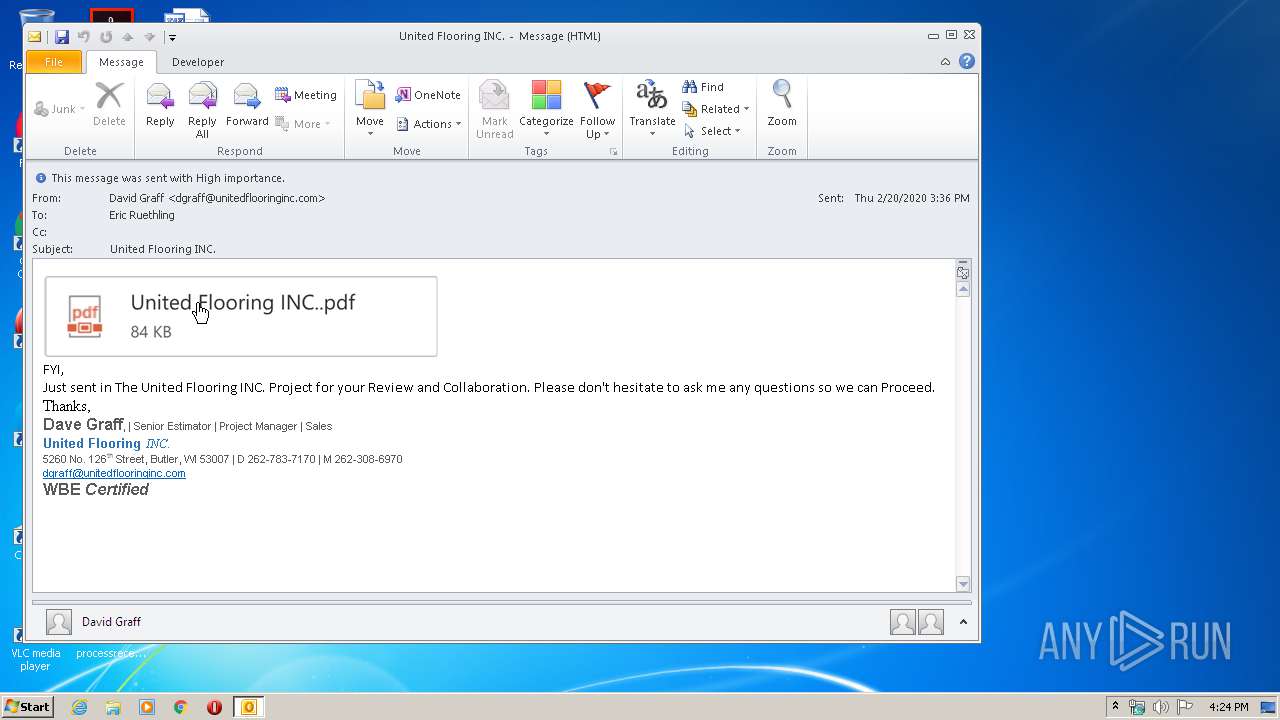
| File name: | United Flooring INC.msg |
| Full analysis: | https://app.any.run/tasks/6b5237dd-2c63-4fdf-8a47-11bfb1b9bc52 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 16:24:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | B2ED7E771CB2C98F6F1C2EB501263F8E |
| SHA1: | 225EC10AD4614FEA9ABBDA2C1E14DF9A0EC64122 |
| SHA256: | A426773B497E173FB8ACC81D00AC15D6BE2E3C4A50BBEBEB10BD546BA645BC28 |
| SSDEEP: | 1536:bizUt5pMHU+2fO+xW9WfBk1zcYtBzp+5RHU+2XJ6Ks2KjecEjz0L:bizUlMHqW+jO1zcYjzp+vHqXds6dz0L |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 780)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 780)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 780)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 780)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3956)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3032)
Application launched itself
- iexplore.exe (PID: 3400)
Reads internet explorer settings
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3956)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 780)
Changes internet zones settings
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3400)
Reads settings of System Certificates
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3956)
- iexplore.exe (PID: 2520)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3400)
Changes settings of System certificates
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
40
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\United Flooring INC.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2520 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3032 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
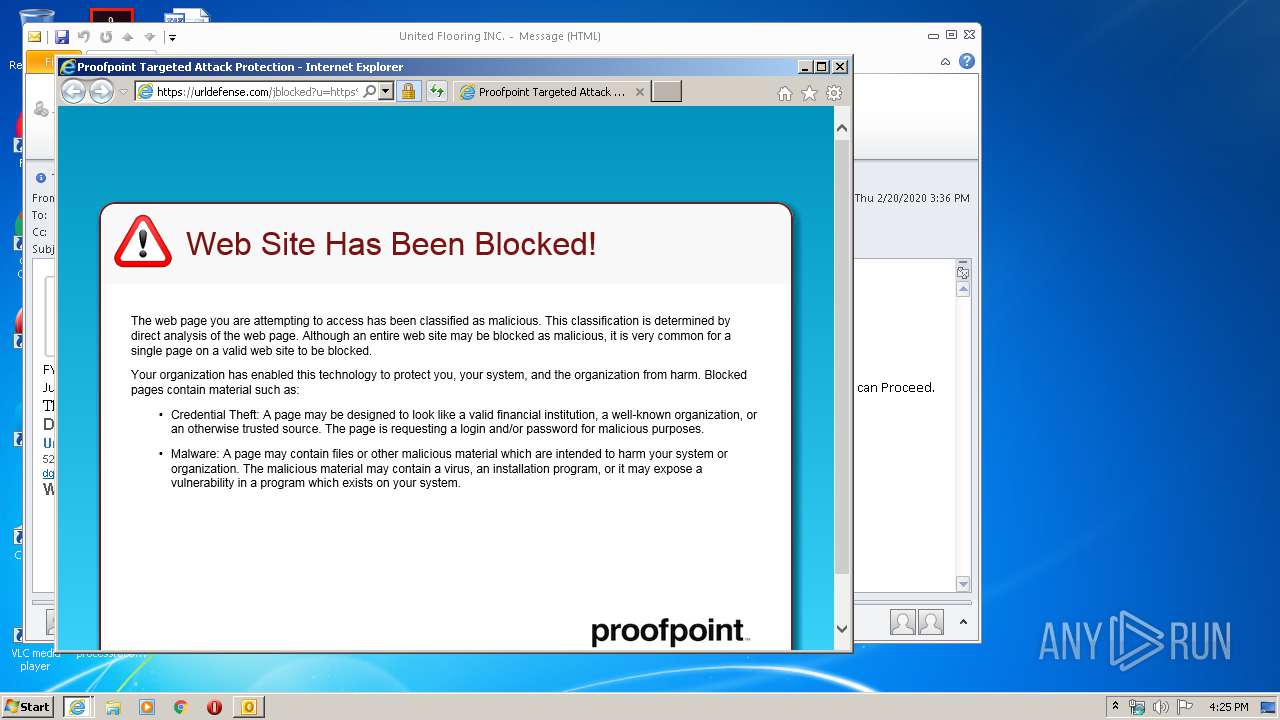
| 3032 | "C:\Program Files\Internet Explorer\iexplore.exe" https://urldefense.com/v3/__https:/onedrive.live.com/view.aspx?resid=90561AD0721456E9!155&authkey=!AAVqbDH9bqSb7BM__;!!DIF6EnXvXQ!K4iYQKxI7-WJucuZfOXhy6_Ever25GkUjVWckiJzIQ2_nIUMD170nKXc2iQ-fsgzptI7vrnIiw$ | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3400 | "C:\Program Files\Internet Explorer\iexplore.exe" https://urldefense.com/v3/__https:/onedrive.live.com/view.aspx?resid=90561AD0721456E9!155&authkey=!AAVqbDH9bqSb7BM__;!!DIF6EnXvXQ!K4iYQKxI7-WJucuZfOXhy6_Ever25GkUjVWckiJzIQ2_nIUMD170nKXc2iQ-fsgzptI7vrnIiw$ | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3956 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3400 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
7 040
Read events
1 764
Write events
3 708
Delete events
1 568
Modification events
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (780) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
15
Text files
31
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 780 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6AA9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9E9A.tmp | — | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9E9B.tmp | — | |
MD5:— | SHA256:— | |||
| 780 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\853754D2.dat | image | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_AD319D6DA1A11BC83AC8B4E4D3638231 | der | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_AD319D6DA1A11BC83AC8B4E4D3638231 | binary | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA39B.tmp | — | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA39C.tmp | — | |
MD5:— | SHA256:— | |||
| 2520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9915FBCE5ECE56452A09FB65EDE2FAD2_18932885610B5B91D0B9280DC39653E2 | binary | |
MD5:— | SHA256:— | |||
| 3032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
15
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
780 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFvn094QJ%2BcWGTwWWEy%2BBXPZkW8AQUo8heZVTlMHjBBeoHCmpZzLn%2B3loCEA53cAOejRmtccb8jN4MVZM%3D | US | der | 471 b | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJaiu8Zb34NbCEEshrmcCs%3D | US | der | 471 b | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJaiu8Zb34NbCEEshrmcCs%3D | US | der | 471 b | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
2520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFvn094QJ%2BcWGTwWWEy%2BBXPZkW8AQUo8heZVTlMHjBBeoHCmpZzLn%2B3loCEA53cAOejRmtccb8jN4MVZM%3D | US | der | 471 b | whitelisted |
3032 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3956 | iexplore.exe | 52.6.56.188:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
2520 | iexplore.exe | 52.6.56.188:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
780 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3032 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3400 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2520 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3032 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
urldefense.com |
| shared |
ocsp.digicert.com |
| whitelisted |
status.thawte.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |